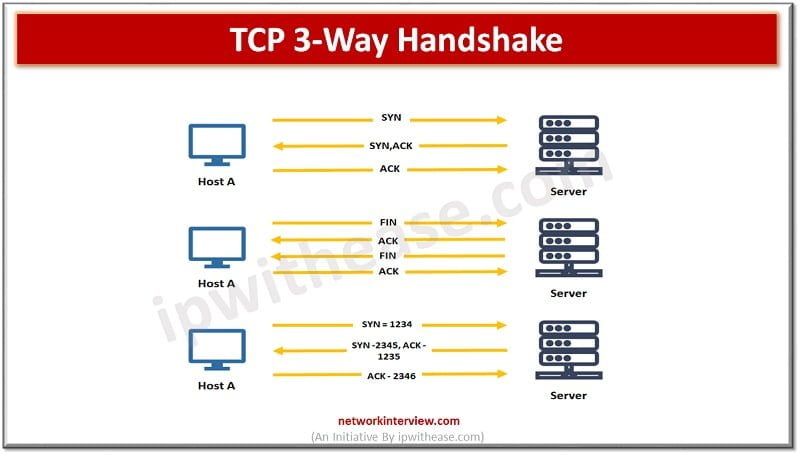
Introduction The Transmission Control Protocol/Internet Protocol (TCP/IP) is a network communication protocol that interconnects the network devices into the internet. It provides a communication between the source and the destination. It specifies how data packets should be broken, addressed, routed, …
The TCP/IP model helps to determine how one computing device would connect to the internet and how data transmission happens between them. It helps to create a virtual network while several computing devices are connected to each other. TCP/IP stands …
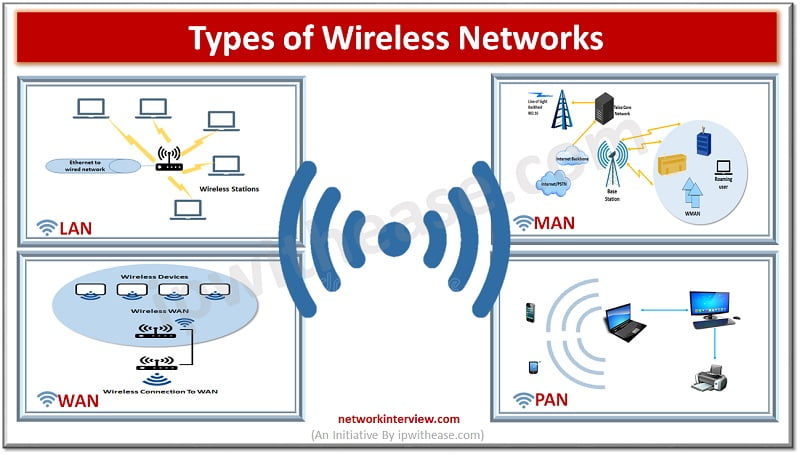
Introduction to Wireless Technology Wireless technology has grown tremendously over the years. New and emerging technologies such as robots, drones, self-driven vehicles, new medical devices are coming into existence which is the need of Internet of Things (IOT) which will …
Network is a collection of systems, software, and hardware which all are connected to provide services to its users and work together. A network comprises systems connected via cables or wireless connectivity. Specialized software, and devices to manage data traffic. …
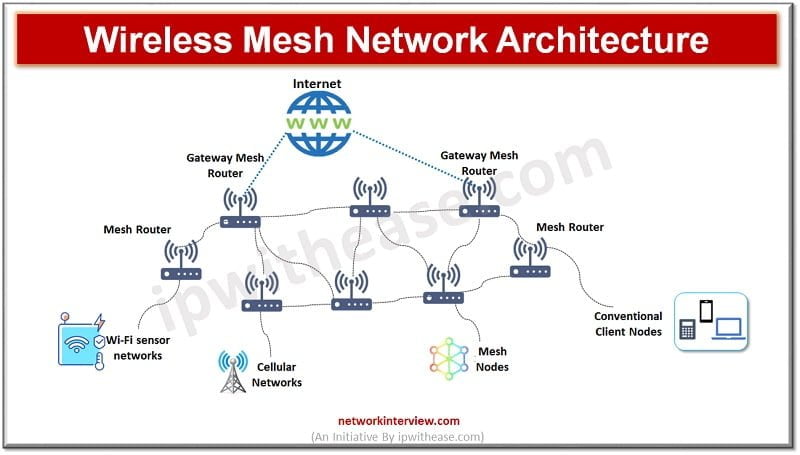
The requirements which demand less mobility and low cost within a radio range are ideal for people connected with the Internet who work in remote areas and operating businesses. These are: self-healing nature and integration with various different networks which …
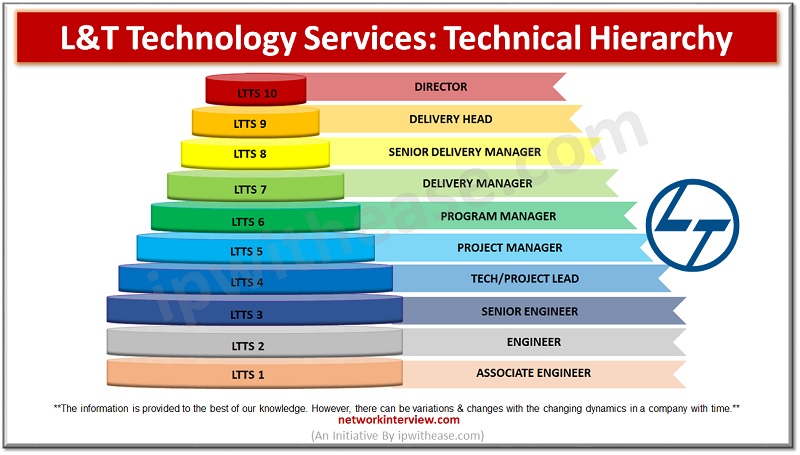
Are you planning to join L&T Technology Services after your diploma or graduation? Good choice! but do you know where you will be placed in the long Chain of command of the company? If not, no problem with that. Today, …
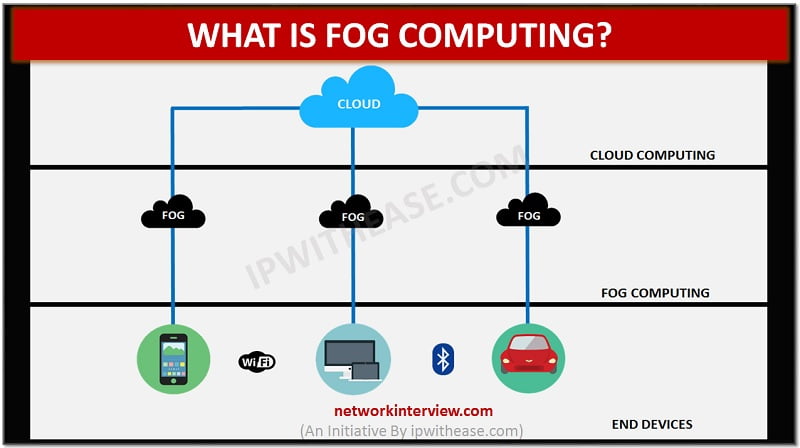
Introduction Fog computing, popularly known as fogging is a concept that was released by Cisco in 2014. It was solely designed to connect the internet to devices at the periphery of the network. The main objective of fogging was to …
Every person will stand at the cross-road where they need to decide between two career paths. So are you one of them, standing at the crossroads at choosing between a career in Cyber Security or Cloud Computing? Most computer major …
To have faster time to market and bring in business agility organizations are more and more relying on technology. Technological advancements have one side facilitated business to grow faster and quickly adapt to changing needs of businesses and on other …
Though it’s been a while since cloud technology was introduced into our world still there is much confusion surrounding Network Security and Cloud Security. If you are one of those who can’t find the difference between these two terms: Network …
Are you planning to get a career as a Web Creator? Then you will be confused between the Web Designer and Web Developer. As there is still a lot of confusion surrounding these job roles. Both of them help to …
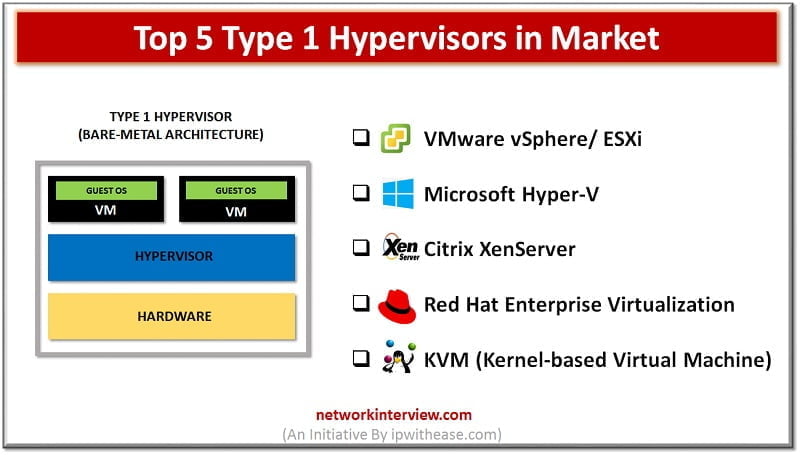
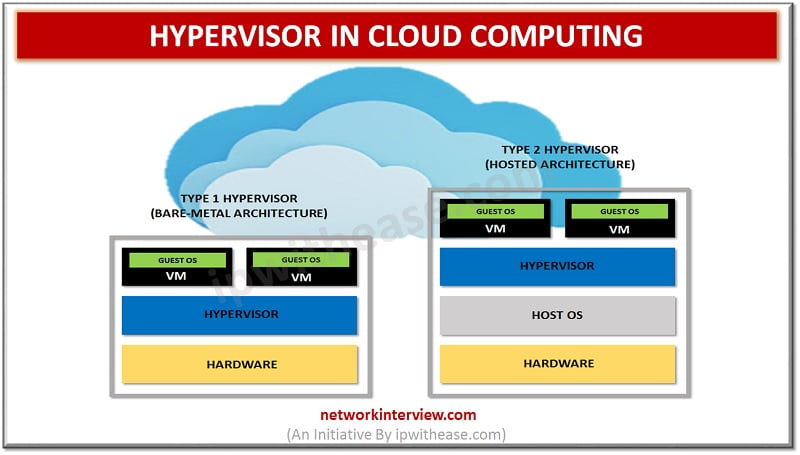
Types of Hypervisors Virtual Machine Monitor or VMM also called as Hypervisor is a technology that separates software (computer operating system) from hardware. With a hypervisor, a host computer can support and accommodate many other virtual machines by sharing its …
When talking about the internet, there are two different kinds of internet connections that you can have, you could have either a wired connection or a wireless connection. While you are using a wired connection, you need to use a …
Hypervisor in Cloud Computing: For long, Applications were assigned dedicated physical servers and resources like CPU, memory and storage. Growth and demand in the ever changing IT environment stipulated for a cost effective and energy saving solution. Virtualization technology gained …
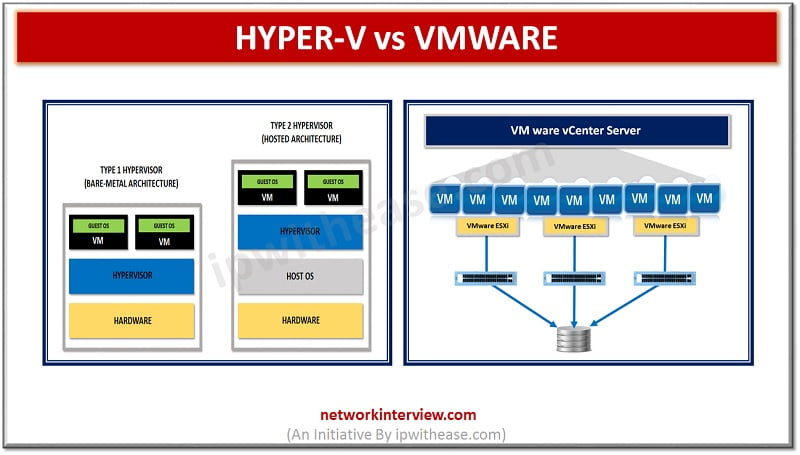
Hyper V vs VMware In computing, virtualization refers to the act of engendering a virtual version of one thing, as well as virtual constituent platforms, storage contrivances, and electronic network resources. On a very broad level, there are 3 styles …
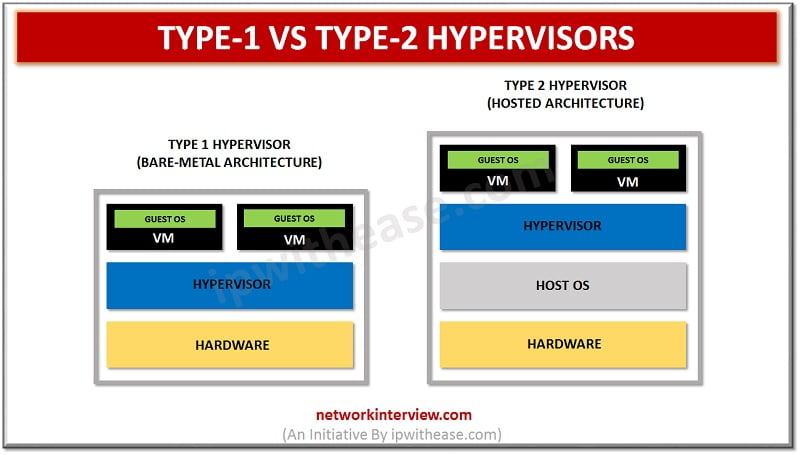
Type-1 vs Type-2 Hypervisors Server virtualization is perhaps the sultriest point in the IT world today. It has been around for a long time, and its ubiquity continues developing, particularly in big business environments. What makes virtualization conceivable in hypervisors? …
XEN vs KVM Talking about the virtualization concept, hypervisors technology is quite a well-known concept. A hypervisor is used by a person who would wish to merge the server space or run a number of other independent machines with the …
Xen and ESXi are unique form of type-1 hypervisors that are specially built for deploying and serving the virtual computers. There can be various kinds of similarities between the two, but here our aim is to bifurcate both of them …
What is a Placement Guarantee Course? First, let’s take a quick look at some of the kinds of placement guarantee courses that are widely available in the market. By opting for these types of courses, you can now enjoy the …
Introduction to GUI We no longer use Command-Line, after the introduction of graphical systems all the computers started to use GUI as the primary interface. And now a successful application is defined by the simple and easy-to-use user interface. So …
Every new technology or software invented goes under this question “Is it secure?” That’s how security is always considered an important feature in the digital era. But do we understand them clearly? Over time security is classified further into cloud …
Cyber security software is a must for ensuring business and individuals security and privacy. It is a method to protect networks, systems and applications from cyber-attacks. It helps to avoid unauthorized data access, cyber attacks and identify stealing. Application, information …
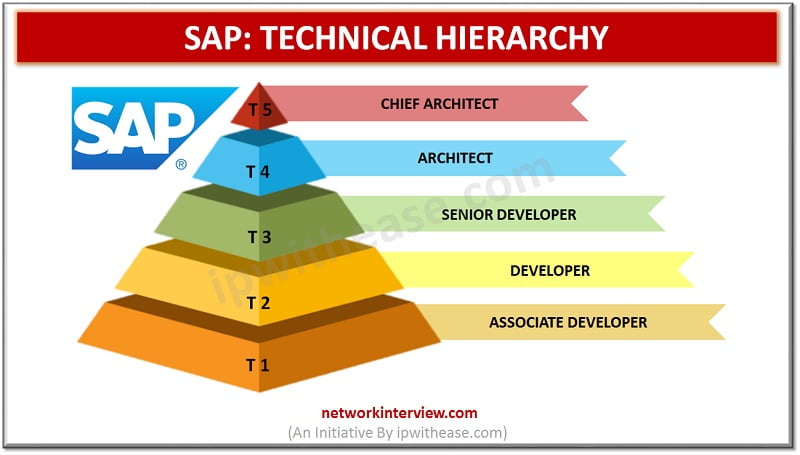
Are you an Engineering graduate looking for a job in SAP? You made the right choice. But do you have any idea where you will be placed among the vast workforce around the world? It is important to know about …
Today’s tech world is all about cloud technologies, so if you are planning to choose a Tech Career it better be something related to Cloud. There are various career opportunities related to cloud computing, and the most famous one is …
Technological advances have changed the dynamics of the healthcare industry. Today, hospitals and clinics prefer using electronic health records (EHR), practice management, billing and patient engagement software to make business processes a breeze. But this technological era has given birth …
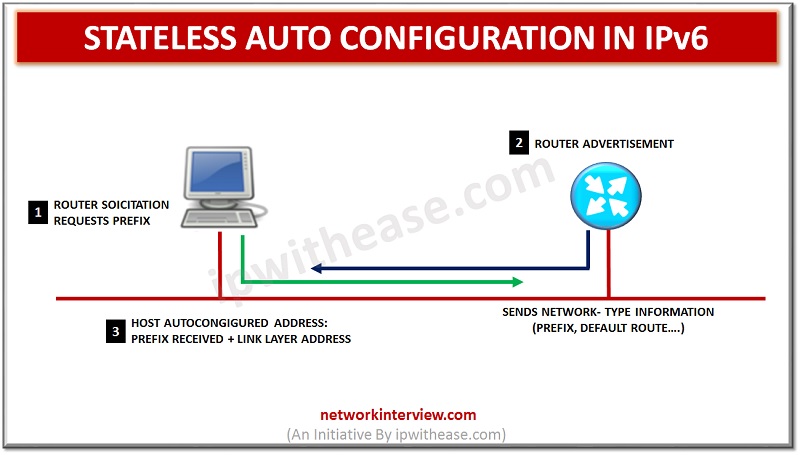
IPv6 Stateless Autoconfiguration enables a local link address which allows the user to access the internet from anywhere. No intermediary IP address or support is needed to be created as the DHCP server. All the devices that are connected with …
Introduction to IPv6 The IPv6 is the abbreviation for the Internet Protocol version 6. The IPv6 is the most updated protocol of network layer which can make the transmission of data possible in packets between two networks. It simply means …
A human resource manager position is a crucial role in a company. They are the ones who lead and guide the Human Resources (HR) department’s daily tasks, especially interviewing and recruiting employees. Hiring trustworthy and reliable employees depends on the …
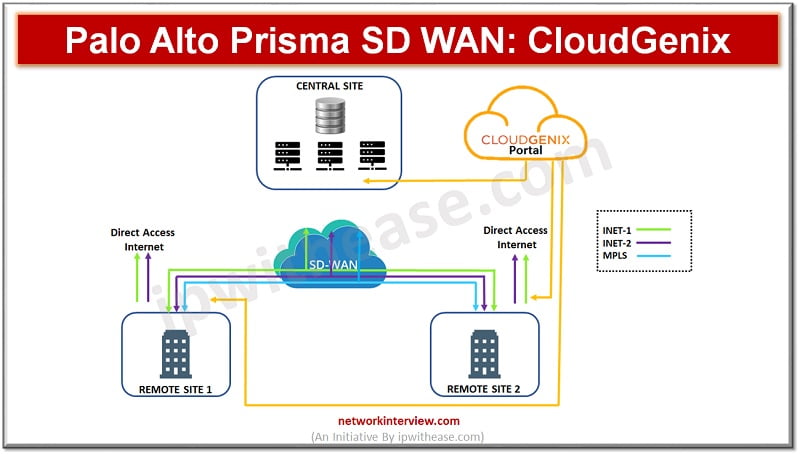
Introduction to Palo Alto Prisma SD WAN More and more organizations are moving towards hosting and running business applications in public cloud such as Microsoft Azure, Amazon AWS, Google cloud etc. Application hosting and running over public cloud has its …
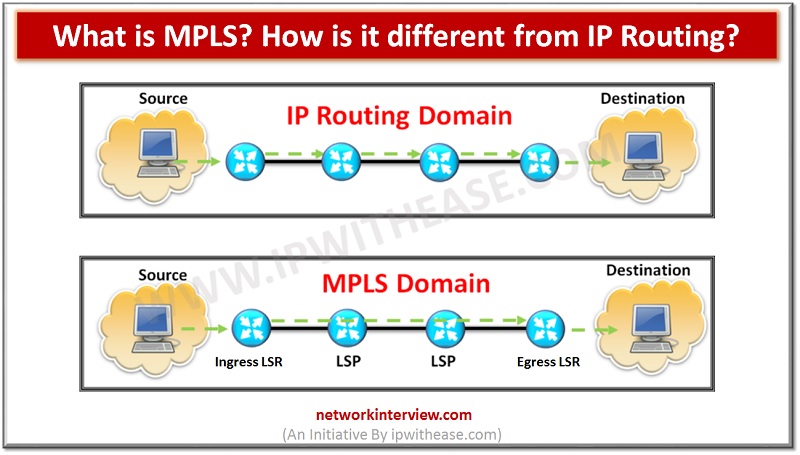
Introduction to MPLS MPLS i.e. Multi Protocol Label Switching (MPLS). It is a technique that is used for the routing of network packets. It is called a Multiprotocol as it supports multiple protocols like Internet Protocol (IP), Asynchronous Transport Mode …
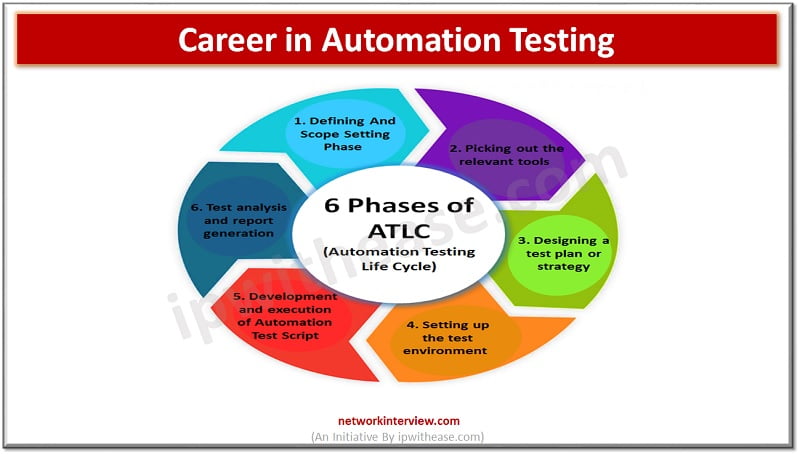
In today’s world, everything is automatic. Whether it is a tech giant or a small business all of them pursue automation to reduce the cost and increase their efficiency. This has created a massive opportunity for technical persons around the …
In the hosting web sector, there is a lot of confusion regarding the technological differences between cloud hosting and VPS hosting. Most people misinterpret the fundamental distinction between the two due to the lack of understanding of the key distinctions …
Agility and innovation are key ingredients for digital transformation. However, agility requirements are hindered by telco-controlled SD WAN or MPLS networks. Slow moving ISPs and need to deploy expensive custom hardware, telco circuits, and VPNs create roadblocks and stop transformation …
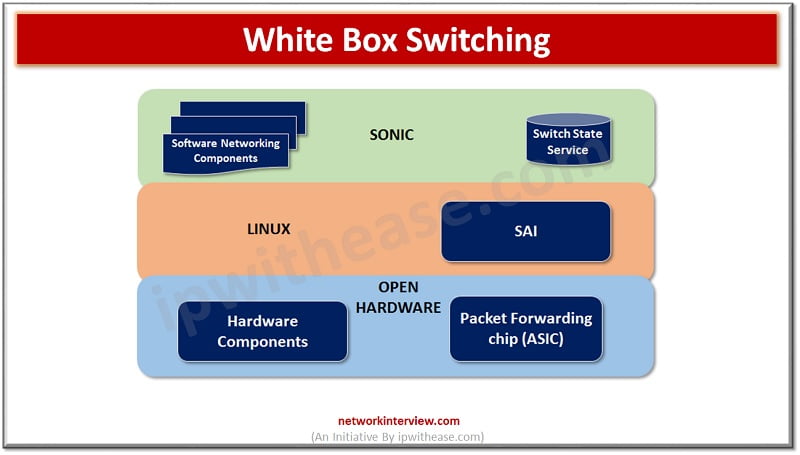
SDN technology detaches dependency on binding both hardware and software. Starting with the SDN network 10 years back, a number of start-ups started to develop open networking systems and white box switches for data centres. In this article we will …
Network switch is the main component of telecommunication networks especially in the case of fiber optics networks. In the traditional switch choice of a specific vendor switch you are bound by software provided by the vendor. The switch market is …
If you’ve invested in a new gaming laptop, chances are that you want to use it as much as possible and spend all your spare time enjoying your favourite games or trying new ones. However, heat is something that your …
Have you ever bought a Samsung Phone which has a different processor than your friends? Yes, the Samsung Mobiles uses two processors for all their models. The mobiles with Exynos processors are sold in Asian and European countries whereas the …
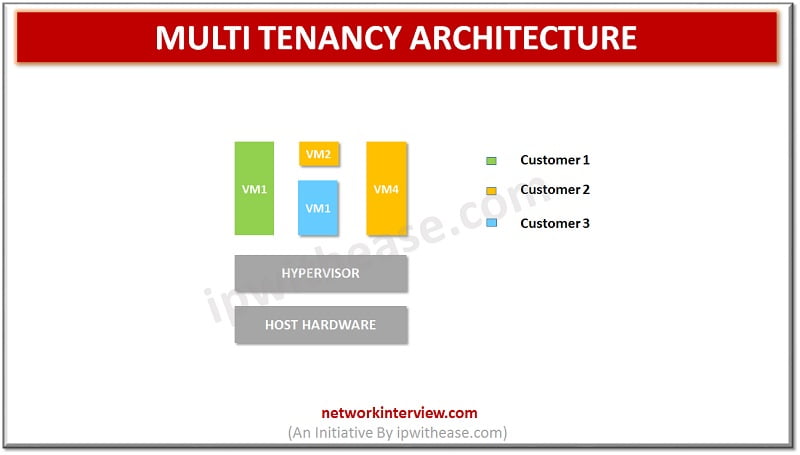
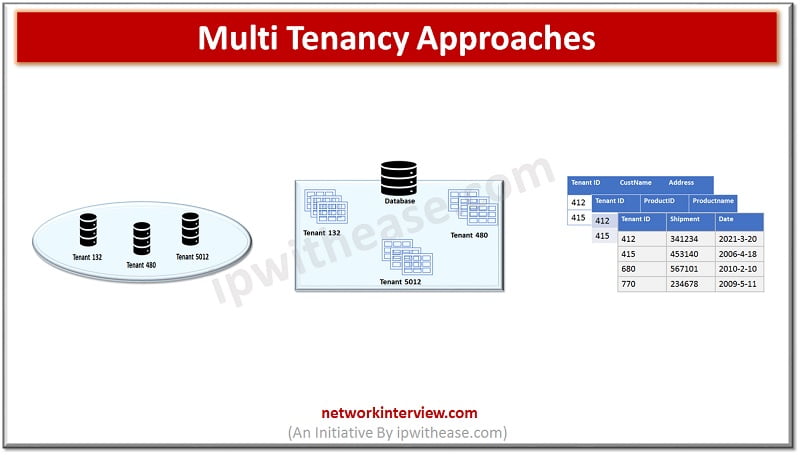
Introduction to Multi Tenancy Advent of cloud computing had brought many new models of delivery and services in Infrastructure services, Application services, Network services and so on. Cloud computing provides a cost-effective way to use computing resources, share applications, share …
In the past few years, video making and editing have gained immense popularity. It’s now easier than ever to shoot impressive videos with your smartphone or a DSLR camera and share them on social media. It has given a platform …
Introduction to Multi Tenancy in Cloud Multi Tenancy offers customers , organizations and consumers which are sharing infrastructure and databases to gain advantages on price and performance front. Service offerings available through cloud involve customers (or ‘tenants’) getting a piece …
Are you dissatisfied with the performance of your internet connection at home? If you have the option of choosing from more than one internet service provider, why not choose the best and the fastest broadband connection. Choosing the best internet …
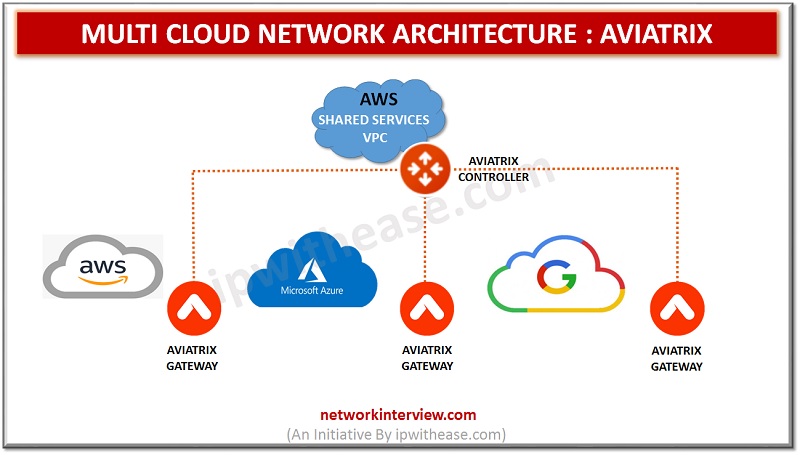
Multi cloud refers to multiple cloud computing and storage services in a single network architecture. Multi Cloud distributes cloud assets, software, applications and more across several cloud environments. Multi cloud network architecture utilizes two or more public clouds as well …
Hey guys, here is another neck-to-neck comparison. Recently Snapdragon and Kirin have announced their new model which has created waves among tech enthusiasts. You can’t decide the winner until they are released, but so far who is the winner? If …
Hybrid Cloud vs Multi Cloud In recent years, with mushroom growth in Cloud technologies, a change has been observed w.r.t where the application Workload and data is hosted. A large number enterprises have started moving their data, applications and related …
When selecting a smartphone or tablet one of the important features to check is the Processor. To be correct they are not processors in the technical circle, it’s called System on a Chip (SOC). The Snapdragon and MediaTek are the …