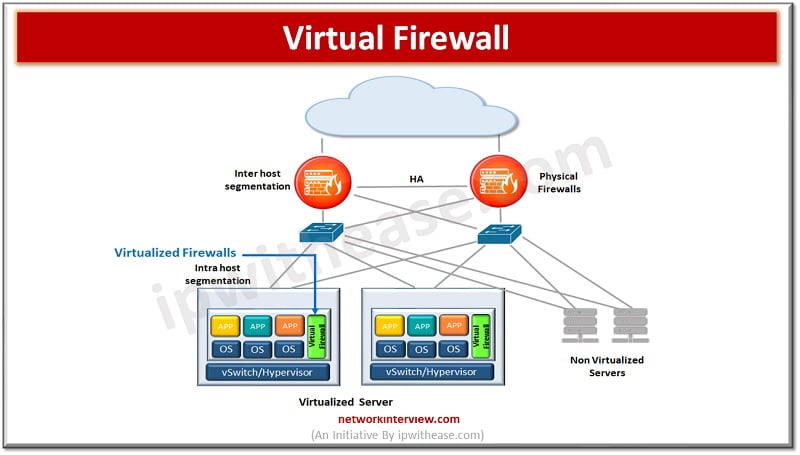
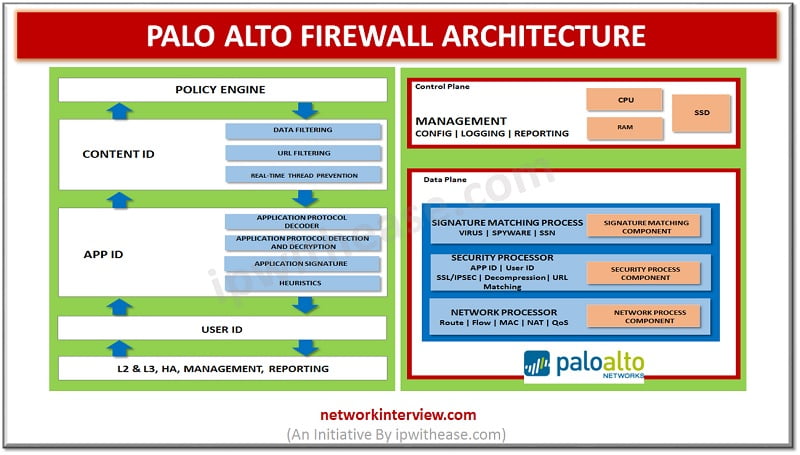
Firewalls have evolved a lot since their inception. The gatekeeper or epitome of perimeter security used to enhance network security. Initial days firewalls were simple packet filters which examined packets of information passing through them and blocked which did not …
The technology sector continues to evolve rapidly, leading to the prominence of several high-paying tech skills. In this blog, we will discuss the top 10 high-income tech skills to be considered as a career option. List of top High-Income Tech …
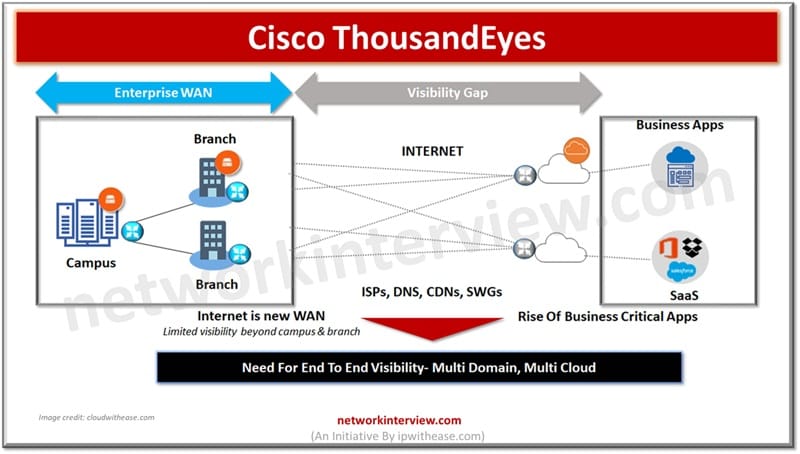
Cisco ThousandEyes is a comprehensive platform for measuring, monitoring, and troubleshooting network performance. It is a cloud-hosted platform that helps organizations ensure reliable and secure user experience and network performance across the globe. ThousandEyes provides insights into the performance and …
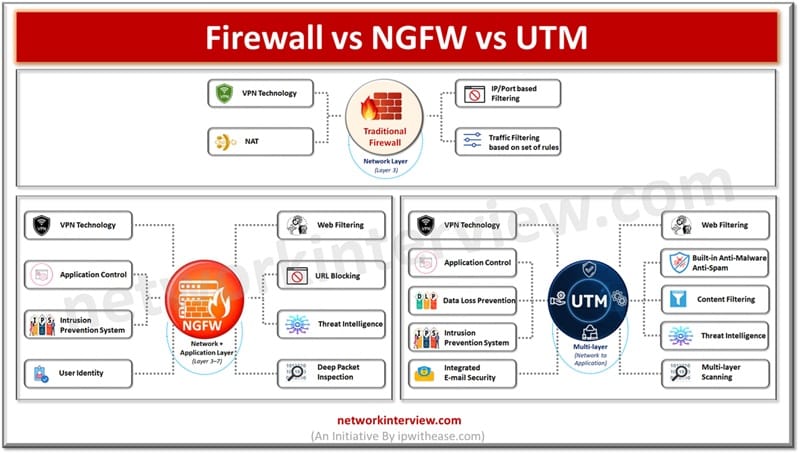
Firewalls are the backbone of all networks and they have come a long way from traditional packet-based filtering firewalls to Next generation firewalls having convention firewall with network device filtering functions involving deep packet inspection, intrusion prevention system (IPS), TLS …
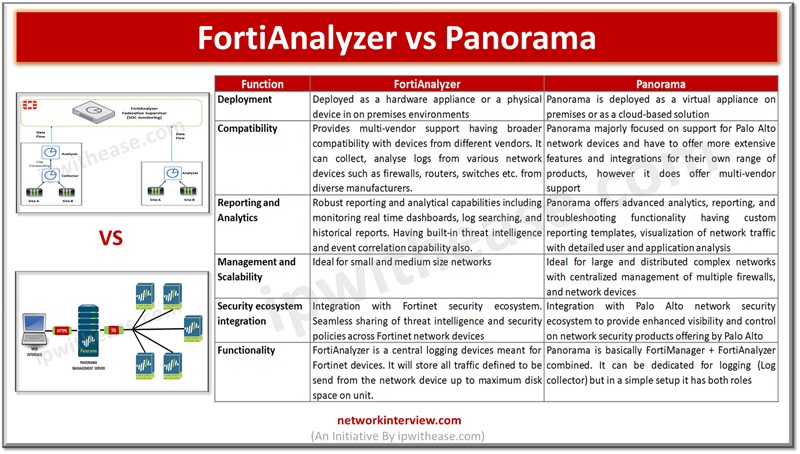
Centralized network management and analysis of network devices is one of the vital requirements of enterprise networks. Individual network component monitoring in larger networks brings a lot of overhead in terms of skills, resources, expertise and not a viable solution …
In today’s article we will understand the difference between traditional firewalls, Network generation firewalls (NGFW) and Unified threat management (UTM), their key features. Firewalls sit on the boundary of the network entry point and provide protection against malicious threats originating …
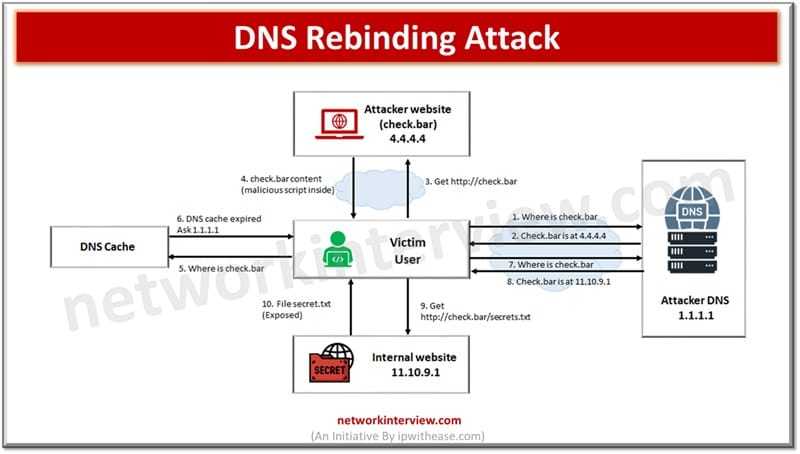
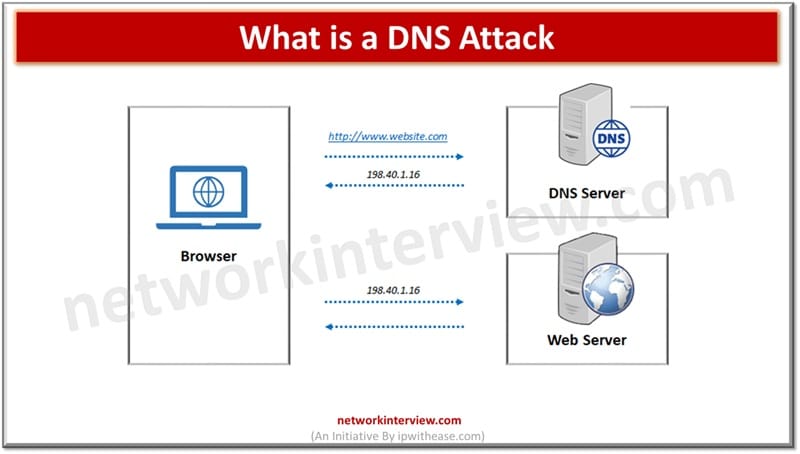
A DNS rebinding attack tricks a browser into bypassing same-origin policy, thereby allowing attackers to access internal networks or devices through malicious DNS responses. In networking systems are addressed with a unique numerical value which is known as IP address. …
RAID is an acronym for Redundant Array of Independent Disks. It is a standard data storage technology that associates multiple physical disks into a single logical unit to provide three fundamental benefits – Data redundancy (protection against disk failures) Throughput/Performance …
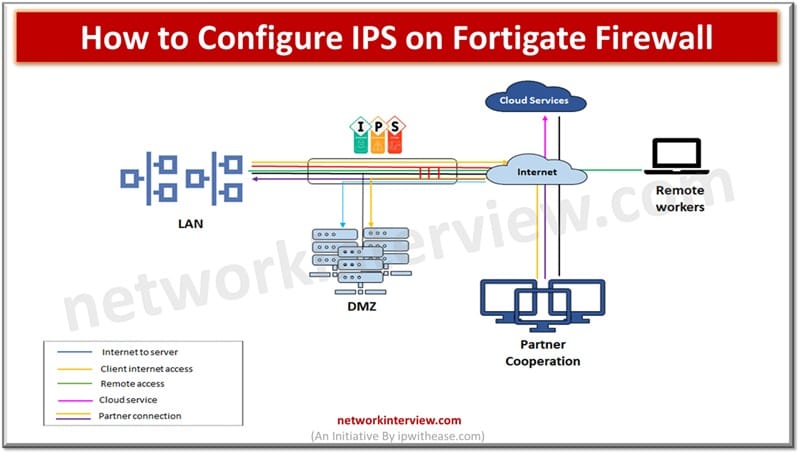
To configure IPS on a FortiGate firewall, enable an IPS sensor in the relevant security policy. Then, apply or customize the sensor under Security Profiles > Intrusion Prevention. Intrusion prevention systems or IPS provide security for the networks and hosts …
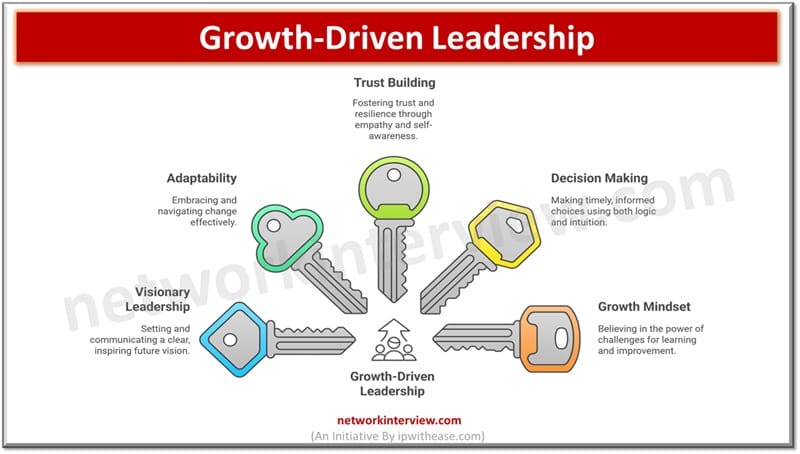
Because businesses change so quickly today, leaders are presented with unique obstacles. Since globalization, technology changes, changing customer expectations, and economic swings exist, leaders need to look past old management tactics. An approach based on agility and vision helps organizations …
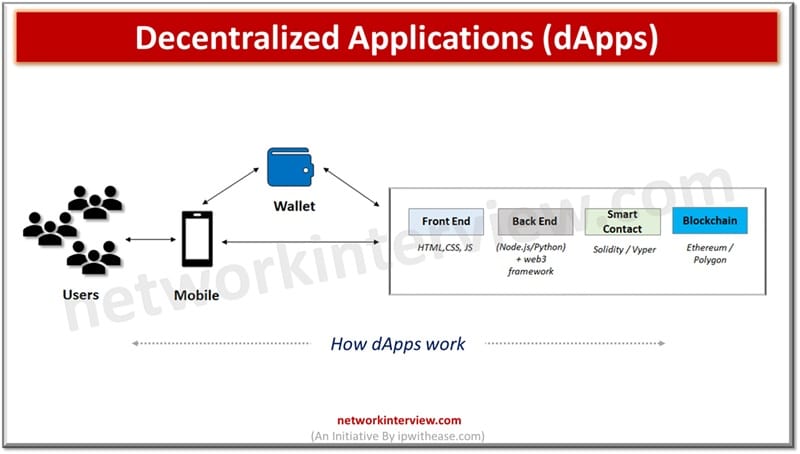
Decentralized Applications are software programs that run on a blockchain or peer-to-peer network, enabling trustless and transparent operations without central control. Web 3.0’s ultimate aim is to move the Internet from centralized model to decentralized model. Currently all big giants …
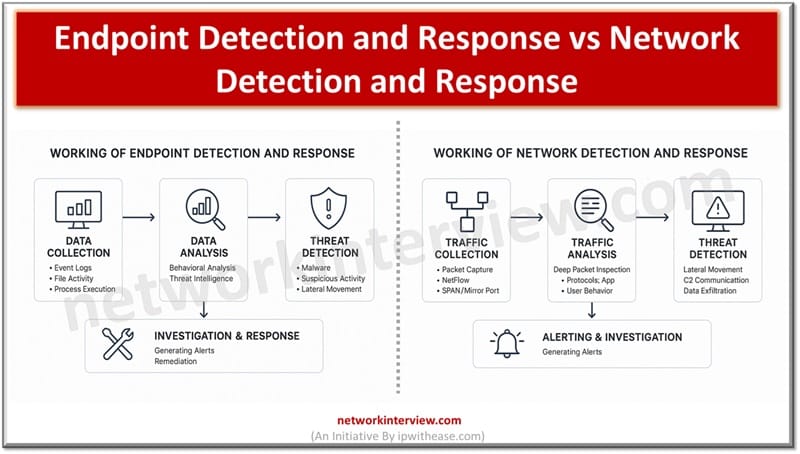
Endpoint Detection and Response focuses on monitoring and responding to threats on individual devices like laptops and servers. Whereas, Network Detection and Response monitors network traffic to detect and respond to threats across the entire network infrastructure. Constant threats and …
Generative AI refers to systems that create new content like text, images, or audio using machine learning models. Whereas, Responsible AI ensures AI systems are developed and used ethically, focusing on fairness, transparency, and safety. Artificial intelligence is reshaping organizations …
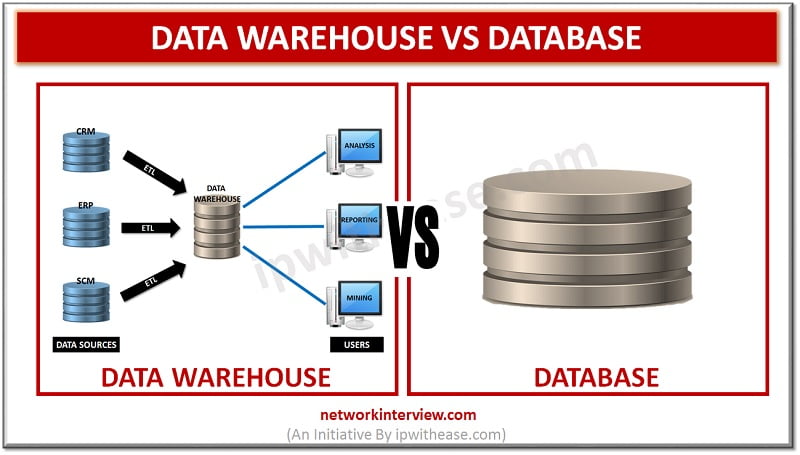
Before discussing difference between Database and Data Warehouse, let’s understand the two terms individually. Data Warehouse The data warehouse is devised to perform the reporting and analysis functions. The warehouse gathers data from varied databases of an organization to carry …
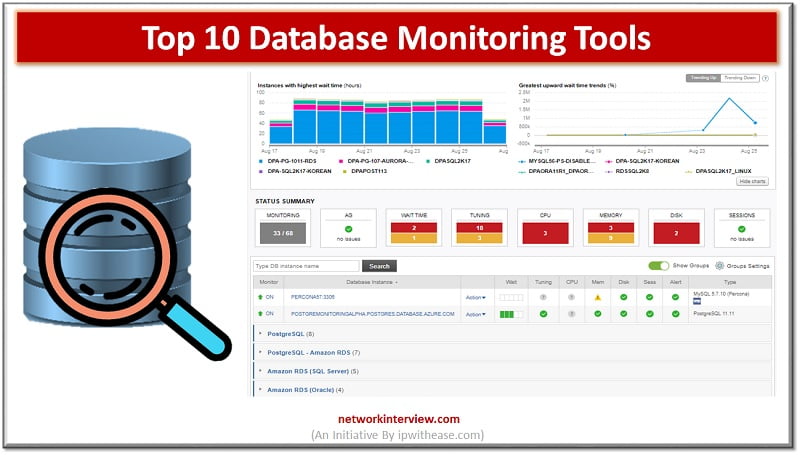
Importance of Database Monitoring In today’s digital world, Data is wealth, Data is Power and Data is everything. Thus a business should give large importance to Users and their data. The Database monitoring tools can help us to a wide …
Database is a structured collection of data managed by a database management system (DBMS) that supports querying, transactions, and indexing. Whereas, a data storage is a more general term for any system used to store and retrieve data, including databases, …
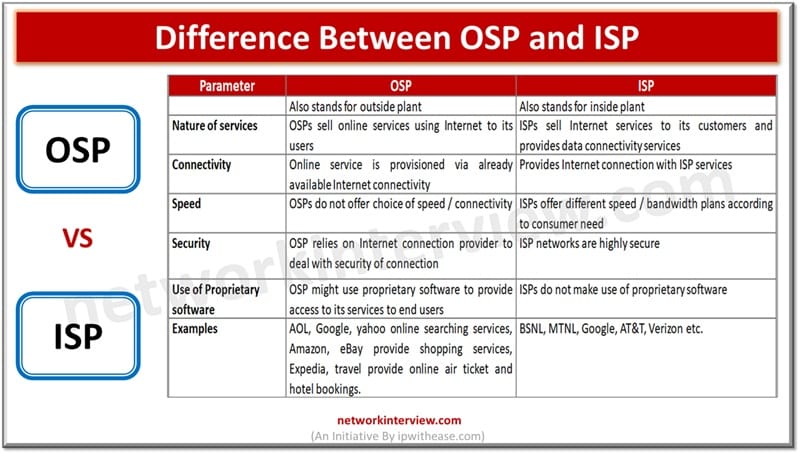
An ISP provides the physical and network access needed to connect users to the internet. Whereas, an OSP offers internet-based services like email, cloud storage, or social media platforms. Service providers play a major role in providing different kinds of IT …
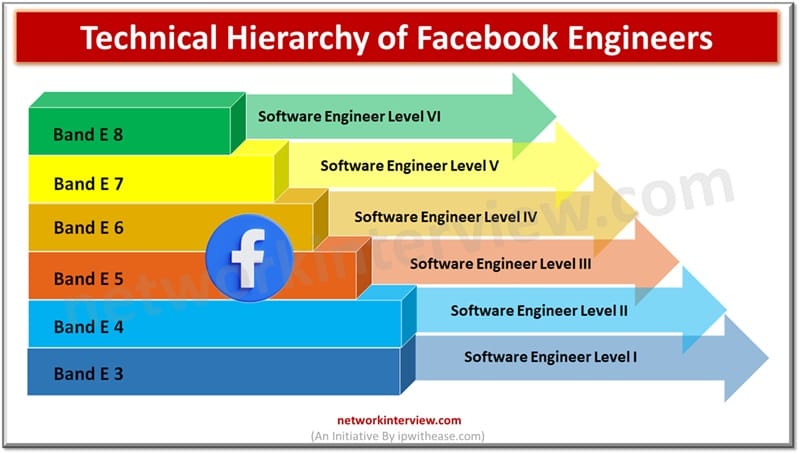
It is a dream goal of the new engineering graduates to get hired in one of the Big 5 Tech companies of the World. And Facebook has a great chance as it is already embedded with our lives. However one …
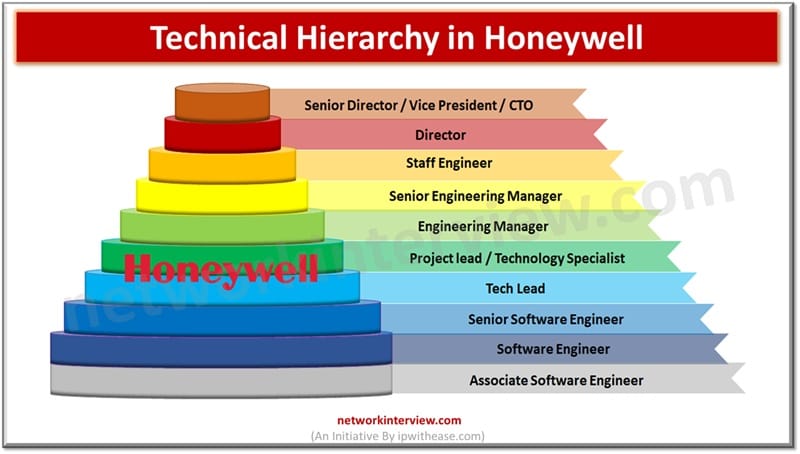
As the name suggests, Honeywell is considered to be the best company to start, whether you’re aiming for a tech, managing, or finance career. The major reason is its friendly work environment and smooth hierarchical chain. Are you planning to …
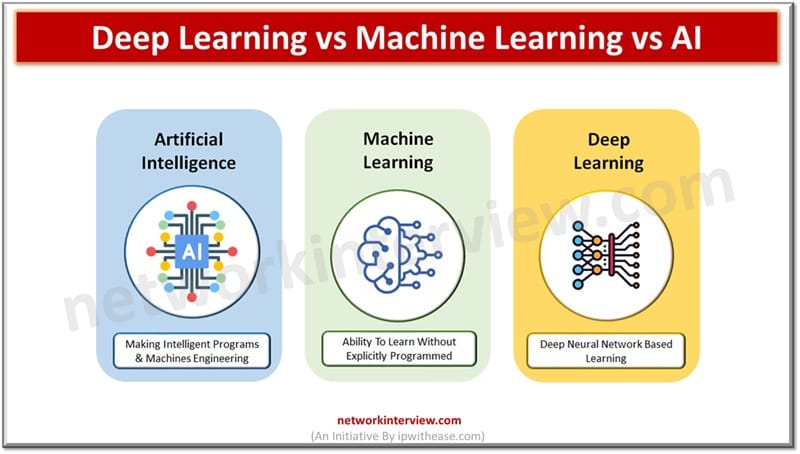
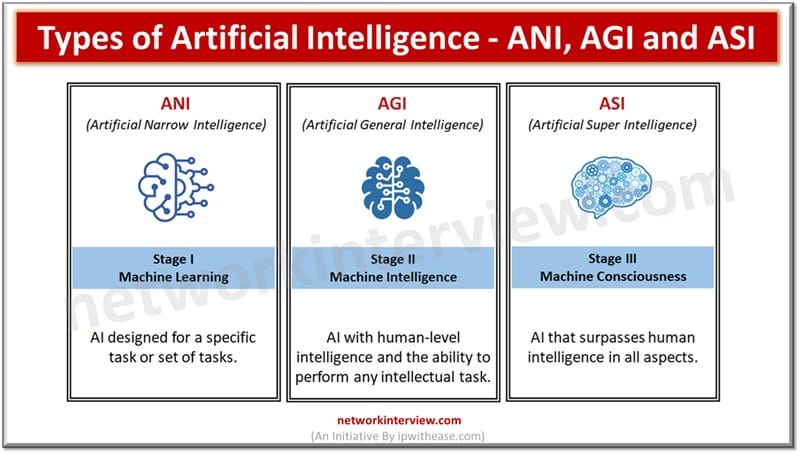
Today we look more in detail about these buzzwords which were estimated to replace 20% to 30% of the workforce in the next few years – Deep learning, Machine learning (ML) and Artificial intelligence (AI). What are the differences, their …
DNS (Domain name system) operates at the layer of OSI model in traditional networking. DNS is a very important protocol and backbone of the Internet, it translates human readable domain names to its corresponding numeric IP address which is used …
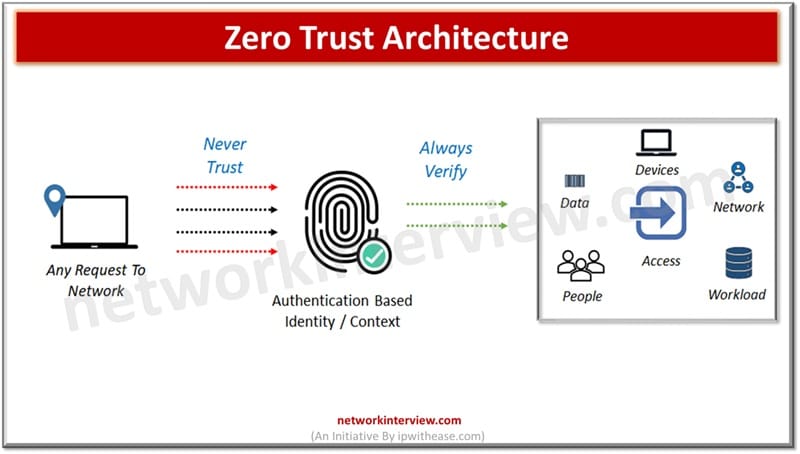
Since organizations are moving away from the traditional IT landscape to cloud computing, cloud-based assets, remote working models, the perimeter based old and traditional model of security is not sufficient enough for protection of data and sensitive systems. The modern …
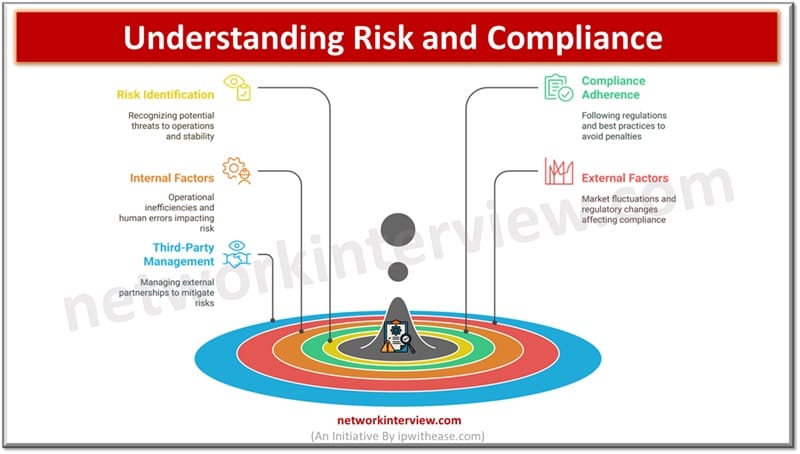
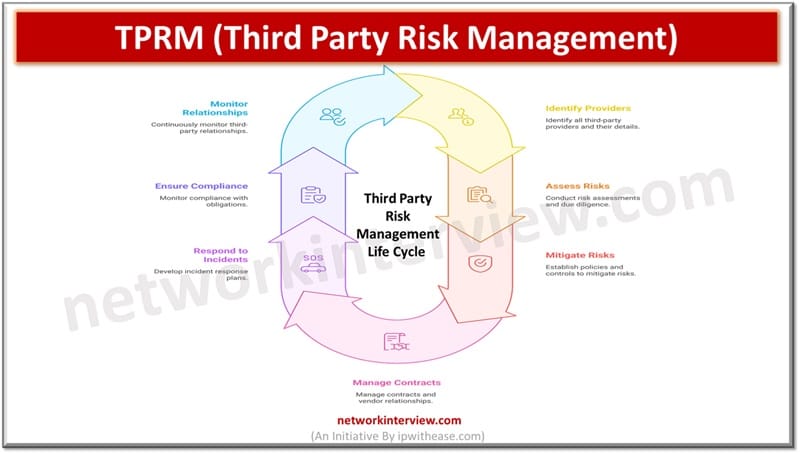
In today’s fast paced world, organizations are facing a lot of pressure to comply with regulatory standards, manage their risks effectively including third-party induced risks and protect organization’s sensitive data. With the constantly evolving cyber threat landscape and rising compliance …
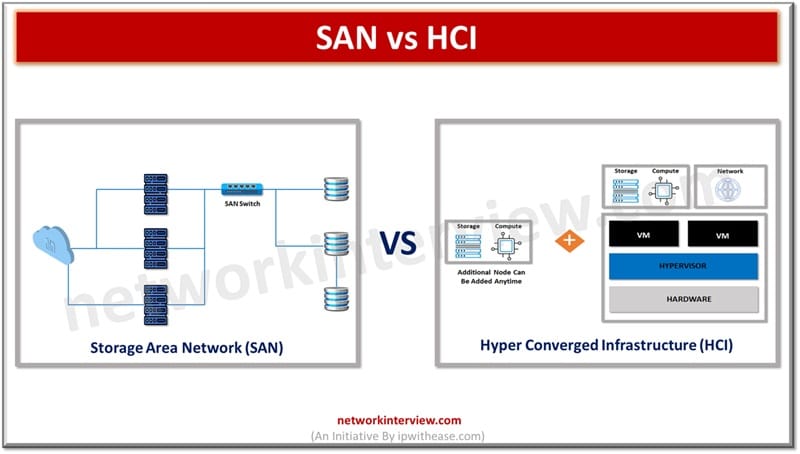
Today’s enterprises demand high speed data access with high volumes of data storage. Storage area network and Hyper Converged infrastructures provide solutions for compute, storage and networking and move past the hardware-based infrastructure limitations to more flexible software-based infrastructure. They …
With increased penetration of cloud computing, AI, machine learning cyber security incidents are on rise. Organizations are working towards reduction of risks associated with new upcoming technologies and trying to strike a balance between business growth and data security. Third …
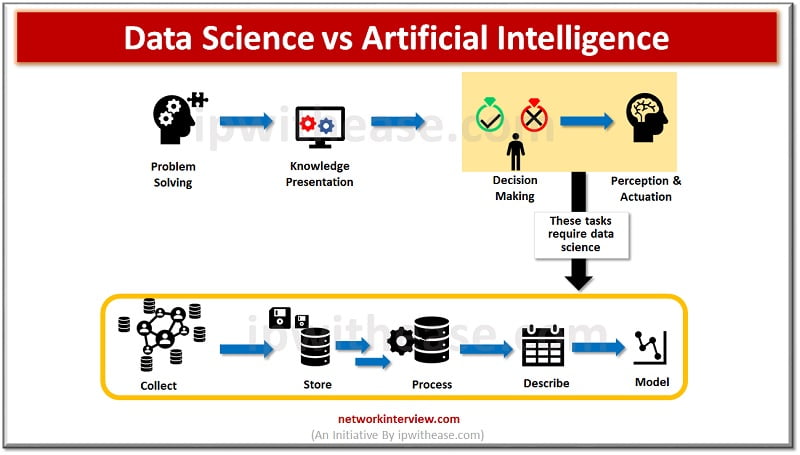
In the last couple of years there has been an explosion of workshops, conferences and symposia , books, reports and blogs which talk and cover the use of data in different fields and variations of words coming into existence such …
In this 21st century, humans rely more on machines than any other thing. So it is important to know about the important technologies that make the machines reliable. Yes, they are automation and artificial Intelligence. Automation has been among humans …
In today’s hypercompetitive market, artificial intelligence (AI) serves as a pivotal force in redefining how businesses operate and grow. From automating mundane tasks to fostering breakthrough innovations, AI is at the forefront of the digital transformation. Companies across the globe …
In today’s business space organizations are facing innumerable challenges which impact their financial stability, operations and reputation. Governance, risk and compliance is a methodology and structure which organizations are using to manage risks and address cyber security threats. It also …
No organization, regardless of size or industry, is immune to cyberattacks, including data breaches, ransomware, and advanced persistent threats. A single incident can lead to financial losses, reputational damage, and regulatory penalties. To stop these challenges, organizations need Incident Response …
Troubleshooting Palo Alto packet flow issues can be complex. In this blog, we will discuss some common Palo Alto Packet Flow Troubleshooting issues and troubleshooting steps. Palo Alto Packet Flow Troubleshooting Issues 1. Incorrect Security Policies Issue: Traffic is being …
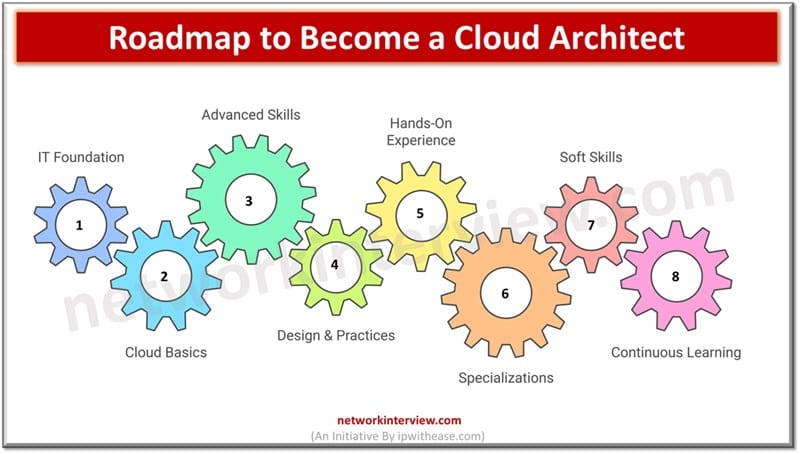
Becoming a Cloud Architect typically requires a mix of education, certifications, hands-on experience, and continuous learning. Step-by-Step Guide to Become a Cloud Architect Let’s go to the step by step roadmap to become a Cloud Architect along with the list …
Network architecture refers to the structured approach of network, security devices and services structured to serve the connectivity needs of client devices, also considering controlled traffic flow and availability of services. Network devices typically include switches, routers and firewalls. Palo …
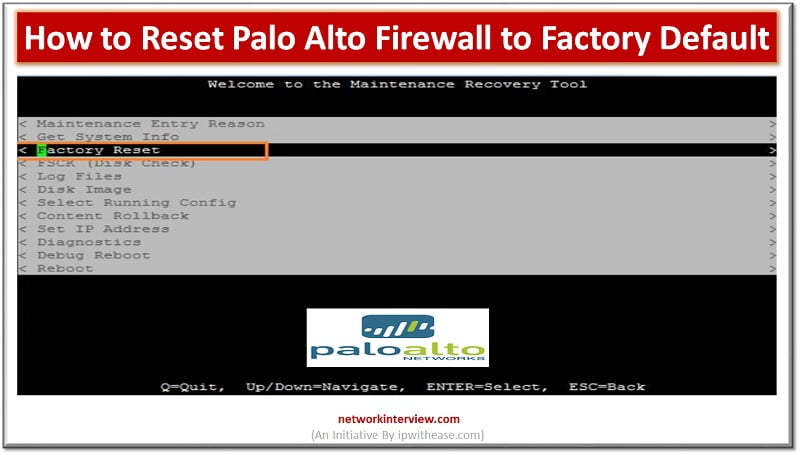
Introduction to Reset Palo Alto Firewall Firewall is a network security device which grants or rejects network access to traffic flowing between untrusted zone (External networks) to trusted (Internal networks) zone. Starting from initial days of Stateful inspection firewalls and …
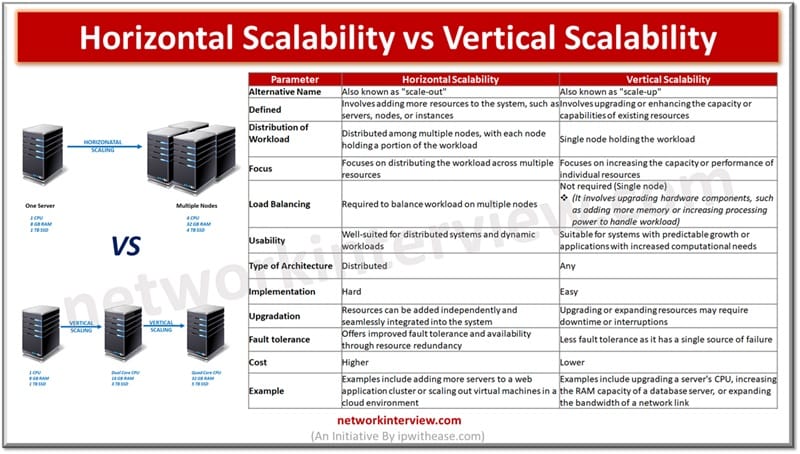
When your business starts to grow and your applications require more accessibility, power, and performance, you may need to consider either scaling up or scaling out. It’s a common question that arises, and the answer depends on your specific needs …
As business environments are changing rapidly third-party relationships are on boom creating a pivotal role in the business success. But it has a flip side too as a third-party introduction in your ecosystem brings a host of risks, cyber security …
Rapid adoption of cloud technology across the globe has accelerated and drastically brought changes in the way enterprises are operating now. The introduction of Artificial intelligence or ‘cognitive technologies’ across enterprises to increase productivity, efficiency and accuracy of business operations …
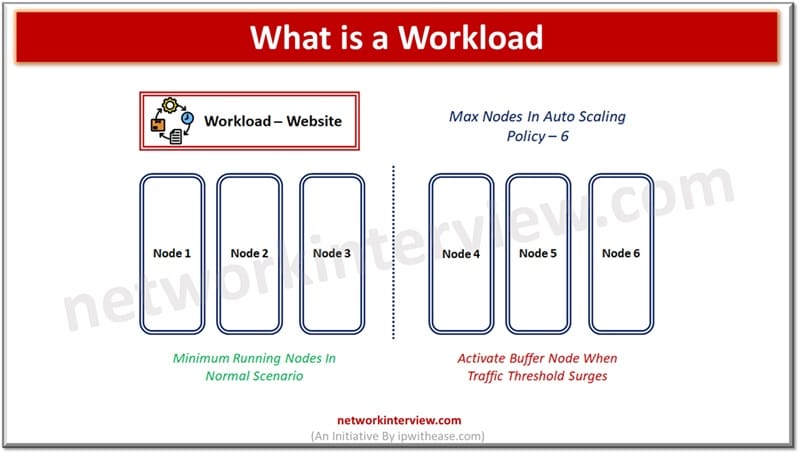
Workload terminology is generally associated with cloud computing. In cloud computing any application or service is deployed over the cloud referred to as workload which is consuming the computer (CPU, memory) and physical storage. Workload term is specifically associated with …
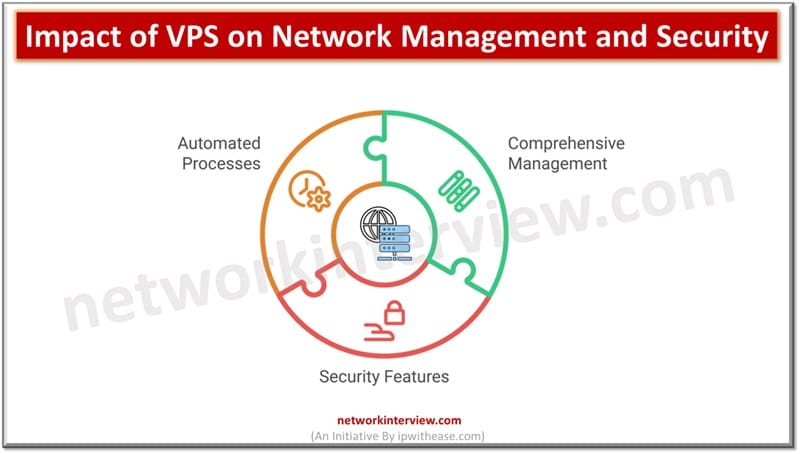
By now, you might have heard how virtual private servers are being utilized across multiple forms of business. Whether or not you’ve decided to make use of them in your own line of work up to this point, it might …
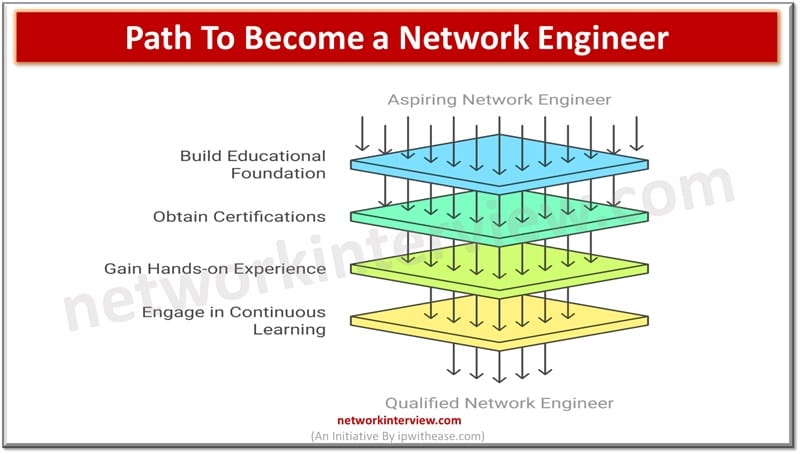
Becoming a network engineer typically requires a mix of education, certifications, hands-on experience, and continuous learning. Step-by-Step Path to become a Network Engineer Here’s a step-by-step guide to help you on the path: 1. Build a Strong Educational Foundation High …
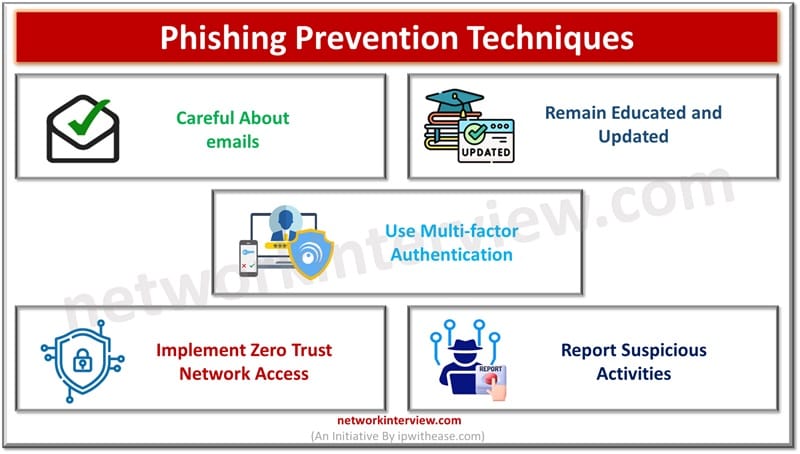
The amount and intensity of cybercrimes is growing exponentially based on social engineering techniques as humans are the weakest link in the chain of security and easy target of compromise. This is further fueled by remote operations. Most companies focus …
A resilient approach towards security and protection of digital assets is the need of the hour. The approach focuses on protection of hardware infrastructure and business applications to eliminate all vulnerabilities which could impact organizations, customers, and other stakeholders. Businesses …
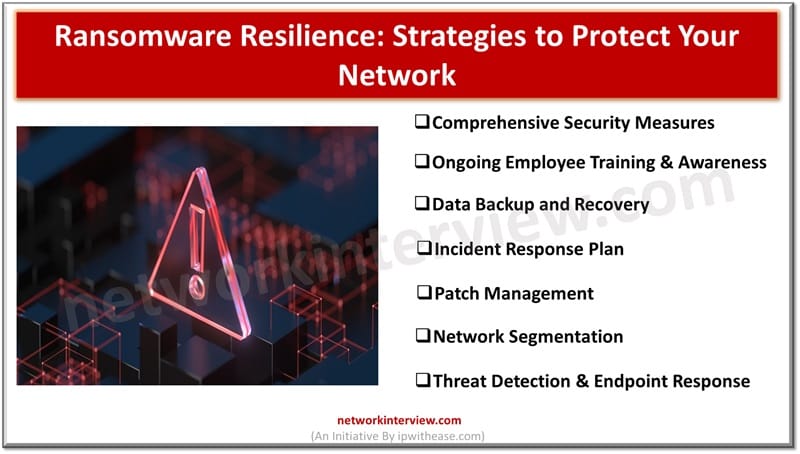
This is the era of digital dominance and ransomware threat looms largely on enterprises and individuals. It is a kind of digital arrest which has emerged as the most menacing threat in recent years. Cybercriminals have targeted businesses, hospitals, government …
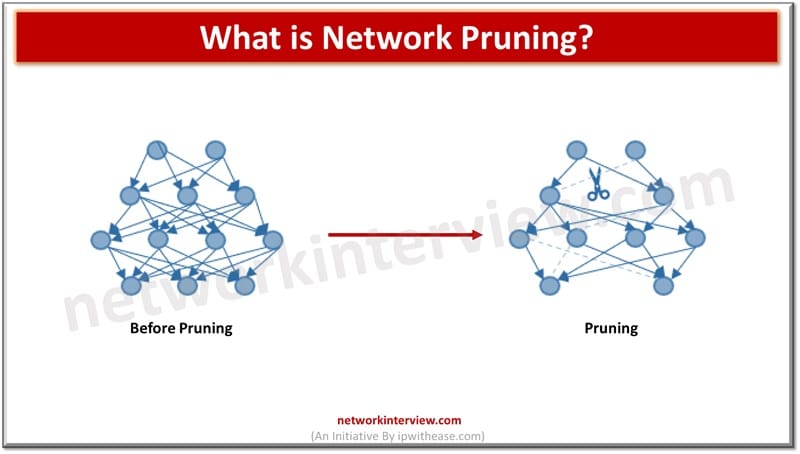
Network pruning is a process of optimizing or simplifying a network by removing unnecessary or redundant elements to improve performance, efficiency, and manageability. Here are some common network pruning techniques: Network Pruning Techniques 1. VTP Pruning VTP (VLAN Trunking Protocol) …
Robotic Process Automation Every company is dealing with increasing volumes of unstructured data and information, which makes it difficult to automate processes. There are plenty of Robotic Process Automation RPA tools that have made it easy for businesses to tackle …