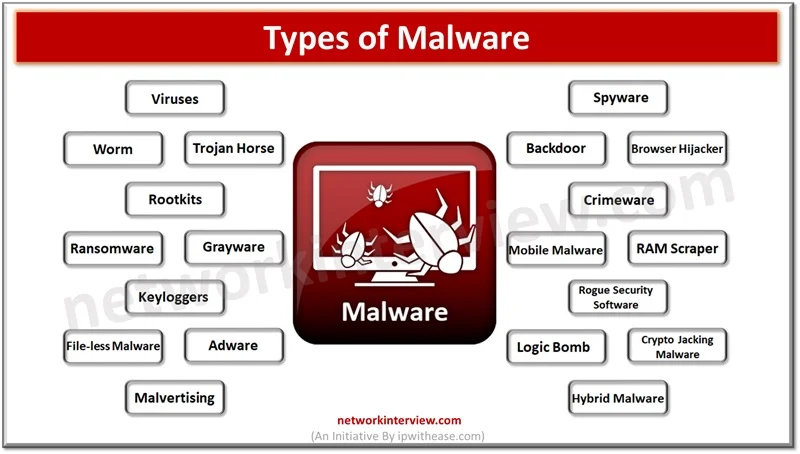
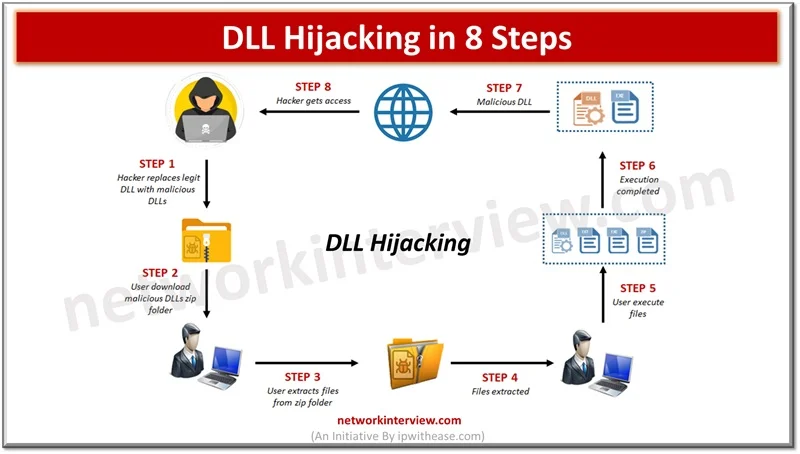
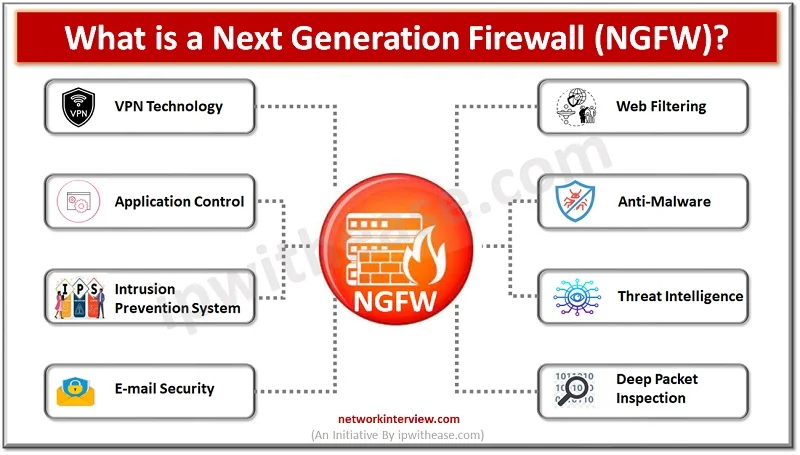
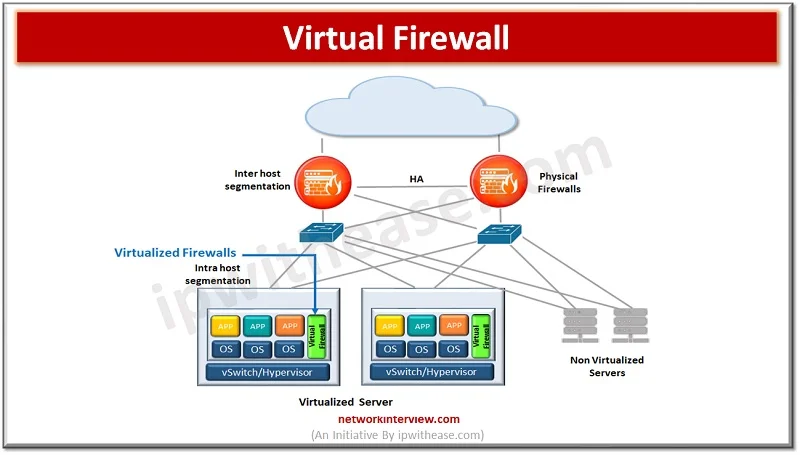
Malware software is a constant concern in the digital age. Cyber criminals continuously come up with innovative ways to break into computer systems and steal personal data, cause disruption to businesses, ask for ransomware, cause data destruction. Malware software is …
Data security is a major concern for enterprises especially dealing with sensitive data. Creating a safe and secure environment becomes top most priority for them. In 2023 cyber attacks worldwide increased by 7%. Each company experiencing on an average 1200+ …
VPN or virtual private networks functions on tunnelling and connection encryption to keep internal activity, location, identity, and IP address hidden from public eyes. VPNs can unblock geo locked and censored content, can bypass statewide firewalls and torrents safely to …
There are various types of Cyber Attacks on rise. As physical boundaries are diminishing rapidly and majority of enterprises rely on Internet and other emerging technologies such as cloud computing, GenAI etc. to run their businesses bad vectors are taking …
Traditional firewalls have come a long way by providing a clear overview of network traffic jams. Allows or blocks traffic according to port, state and protocols and filters traffic as per rules specified by firewall administrators. NGFWs have eventually changed …
Firewalls have always been the first line of defence, traditional firewalls have a set of rules to keep bad traffic and requests from malicious hackers away from organization networks. The role of traditional firewalls is however changing and getting replaced …
In today’s digital age, the protection of sensitive data and critical assets is paramount, particularly for large enterprises. With sprawling networks, diverse endpoints, and a plethora of applications to manage, the challenges of securing operations at scale are immense. However, …
Firewalls have evolved a lot since their inception. The gatekeeper or epitome of perimeter security used to enhance network security. Initial days firewalls were simple packet filters which examined packets of information passing through them and blocked which did not …
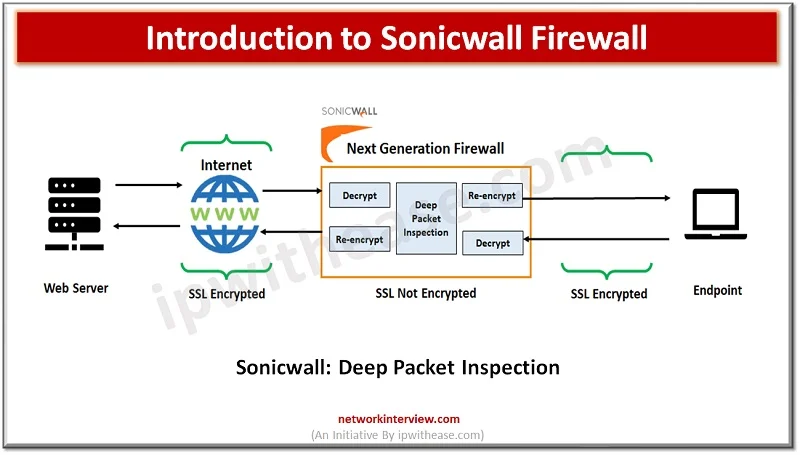
Evolution of Firewalls: Sonicwall Firewall Firewall technologies have evolved at a very rapid pace since its inception and from initial packet filtering firewalls which use to inspect packet traffic and took decision to allow or reject packets, which is then …
Both the proxy and the firewall limit or block connections to and from a network but in a different way. While a firewall filters and blocks communication (ports or unauthorized programs that seek unauthorized access to our network), a proxy …
Authentication is the first step at entry level for ensuring security and it is required for managing user identification and providing access control for seamless operational experience in a secure manner. Individual authentications are not only restricted to passwords and …
Firewalls are network perimeter security devices which separate internal networks from external public networks such as the Internet to reduce the risk of external attacks. Firewalls use access policies and identify types of information, in addition they also control ports …
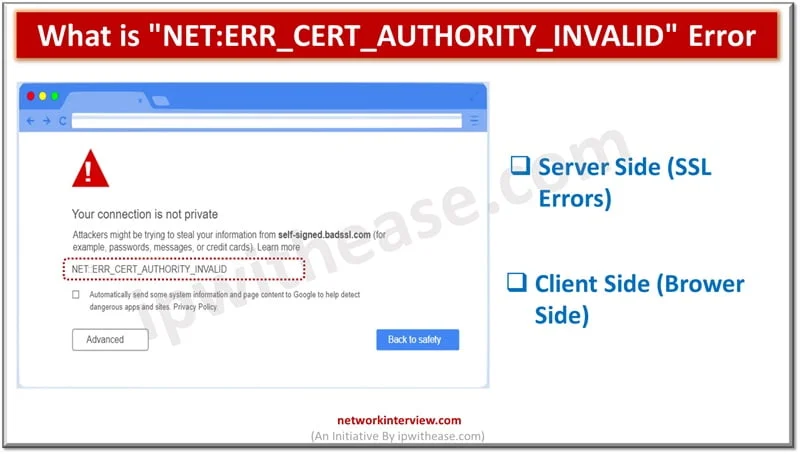
Secure Socket layer (SSL) certificates is one of the most widely used and popular mechanisms for public website security. SSL certificates keep data of users secure, verify ownership for the website, prevent attack vectors from creation of a fake version …
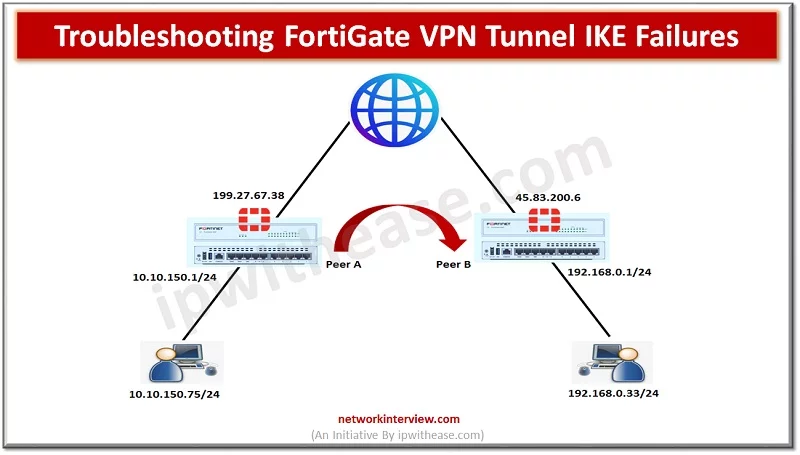
In our previous post, we have already discussed the IPSec VPN Configuration in Fortigate Firewall. Here in this post we will understand how to trouble shoot the FortiGate VPN tunnel IKE failures. We are using below topology to troubleshoot the …
Basically, a proxy anonymizes your connection to the internet by masking or hiding your IP (Internet Protocol) address. How does it hide your IP? When you route a request through a proxy server, it substitutes your IP address with its …
Site to Site VPN is connection between two or more networks used widely by enterprises to leverage Internet connection between private traffic in lieu of using private MPLS circuits. Site to site VPNs used by enterprises offices dispersed across geo …
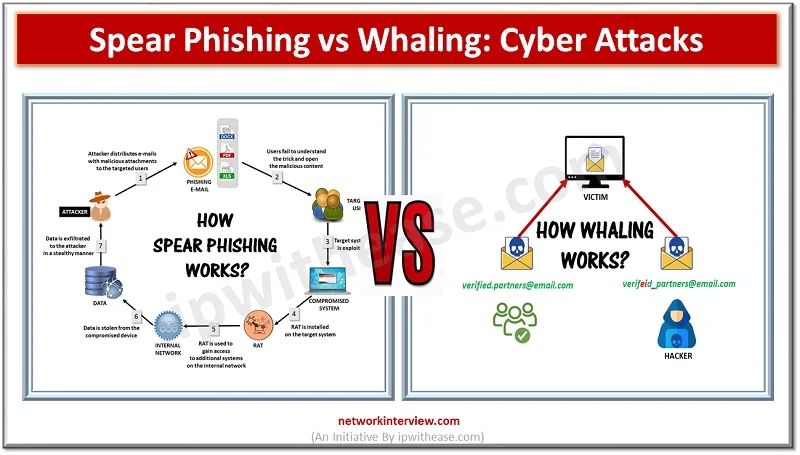
Cyber Attacks Cyber attacks are on rise since Covid 19 at a more rapid pace compared to before. Various forms of cyber attack techniques being used by hackers to gain access to organizations resulting in devastating effects such as unauthorized …
It is not possible to 100% prevent the router attacks. However, there are possibilities of few things that could be done for preventing the occurrence of most common attacks of routers on the network and the system. Widespread attacks are …
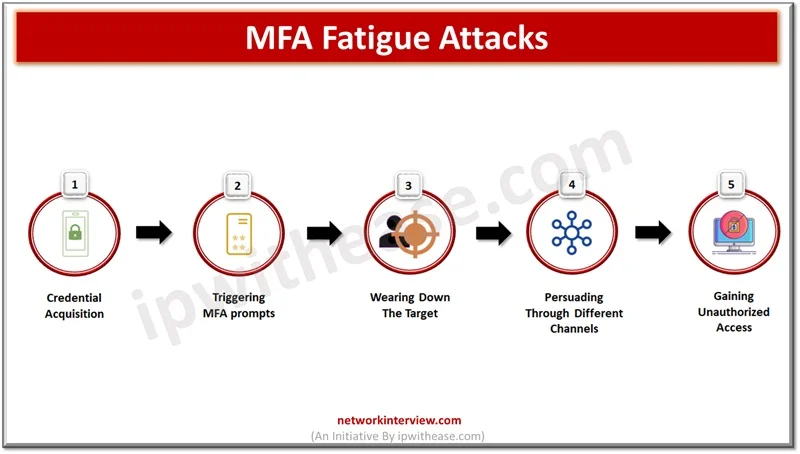
Leaked or stolen credentials are primary sources being used by cybercriminals in breach networks and steel company confidential and sensitive data. Normal authentication involving a username and password is an old technique and no longer provides protection against sophisticated attacks …
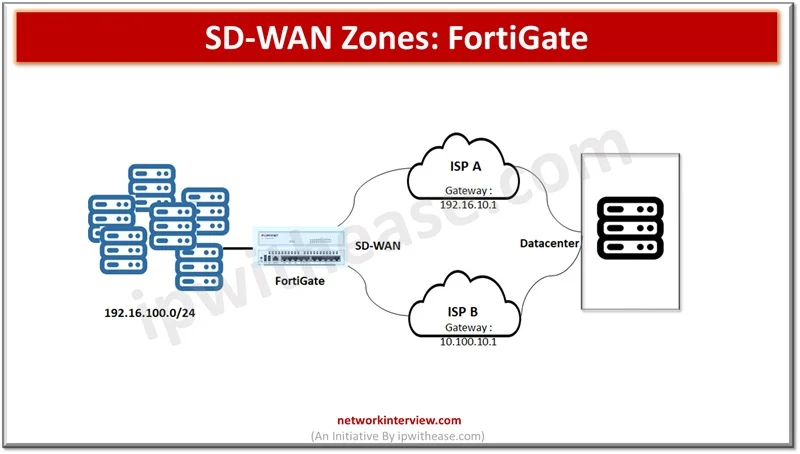
SD-WAN is a software defined networking approach wherein hardware is separated from the control plane. SD-WAN is an ideal technology for cloud and on prem deployments. It is a consolidation of transport connections, underlays, monitor and load balancing traffic across …
Firewalls are the backbone of all networks and they have come a long way from traditional packet-based filtering firewalls to Next generation firewalls having convention firewall with network device filtering functions involving deep packet inspection, intrusion prevention system (IPS), TLS …
Attackers are constantly looking for vulnerabilities to penetrate your networks. Protection against direct, external threats require extensive network security functions deployed on the edge. Protections on the edge are provided by stateful and next generation firewalls (NGFWs) which offer features …
(Diagram depicting Palo Alto vs Fortinet Firewall) Organizations need to keep pace with rapid increase in technology demands such as remote working, anywhere connectivity, lower latency , increased availability along with protection of infrastructure from a never ending list of …
Application aware security is the need of the IT enterprises. Companies are replacing the old and outdated firewalls with Next generation firewalls which are application aware and this evolution can be attributed to web 2.0 where web-based applications and services …
Data is the key differentiator for businesses and enterprises hold a trove of business secrets, customer personal data, and other sensitive information vital for businesses. Hackers’ prime target is this data for their personal gain , and organizations struggle to …
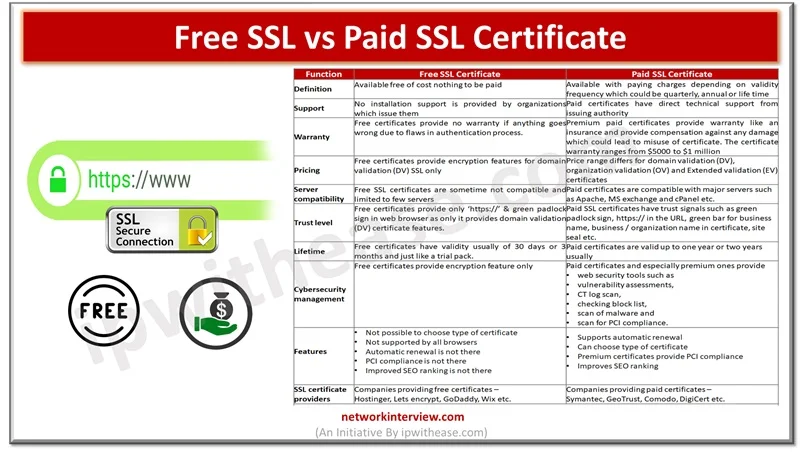
As cyberattacks are on rise and thousands of Internet users and organizations are targeted by attack vectors, safety and security of data is a major cause of concern. The secure socket layer (SSL) certificates are widely used by websites for …
Secure Socket layer (SSL) certificates are used widely by organizations to secure websites and every business needs to have a valid SSL certificate to safeguard client’s security and credibility of brand. Secure Socket layer (SSL) is an encryption protocol and …
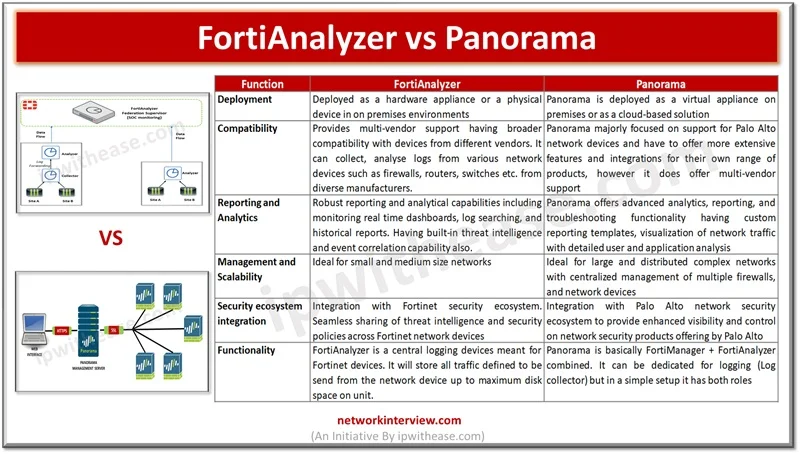
Introduction to Palo Alto Panorama Palo Alto Panorama is the centralized management server that offers a global visibility and control over the multiple Palo Alto Networks next generation firewalls from web interface console. Panorama manage multiple Palo Alto Networks firewalls …
Centralized network management and analysis of network devices is one of the vital requirements of enterprise networks. Individual network component monitoring in larger networks brings a lot of overhead in terms of skills, resources, expertise and not a viable solution …
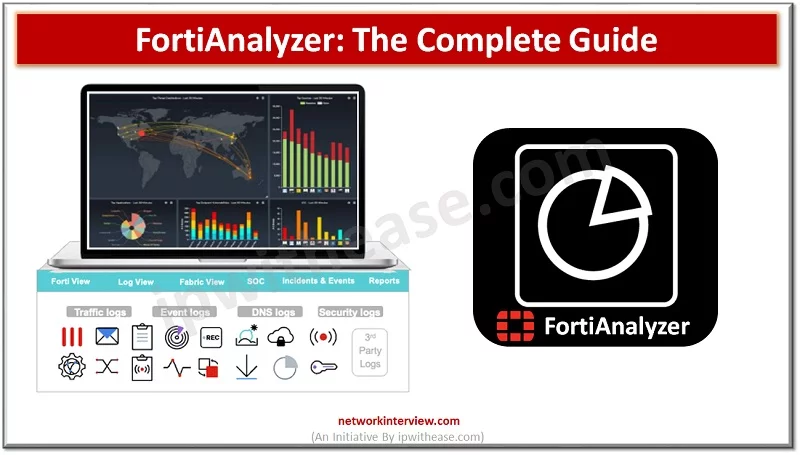
FortiAnalyzer: Security Management Platform FortiAnalyzer aggregates log data from one or more Fortinet devices and creates a single platform to view all the reports and events. It can fetch logs from the Fortinet devices once devices are registered to FortiAnalyzer. …
Managing the cyberthreat landscape is quite a bigger concern for enterprises. As more and more organizations are adopting cloud ecosystems, organizations reliance on security of their data and information for 3rd party SaaS providers is at an all time high. …
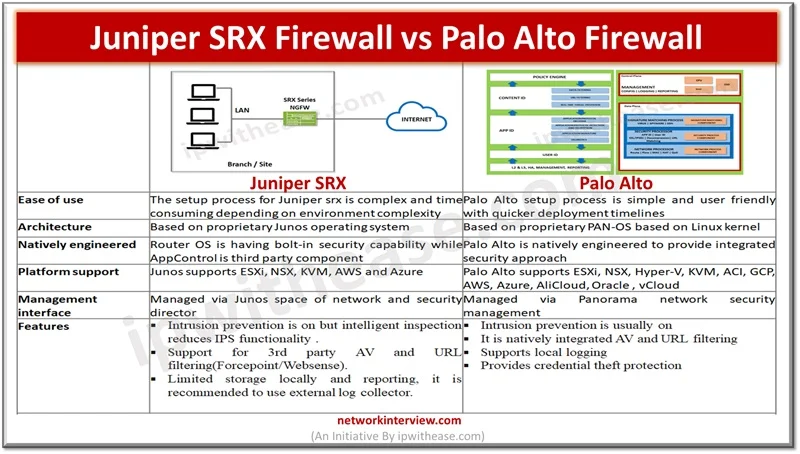
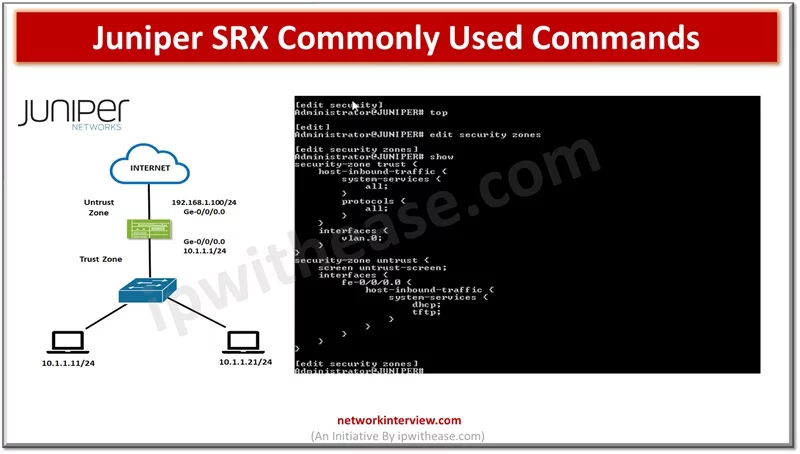
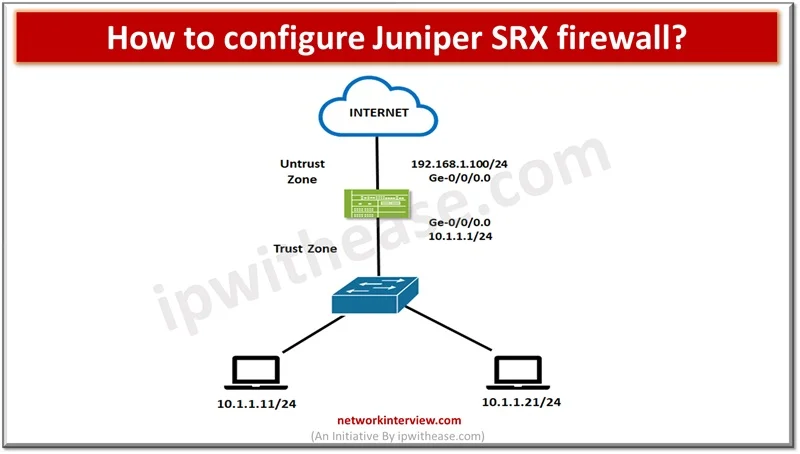
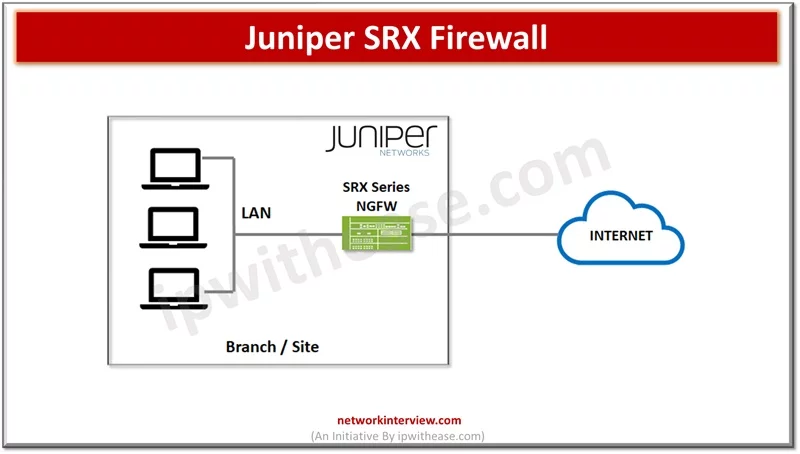
In the previous articles, we have studied the basics of Juniper SRX firewall, its architecture, installation, modes, security policies etc. Today, we will discuss the command line interface of Juniper SRX. Commonly Used Commands: Juniper SRX Here are some commonly …
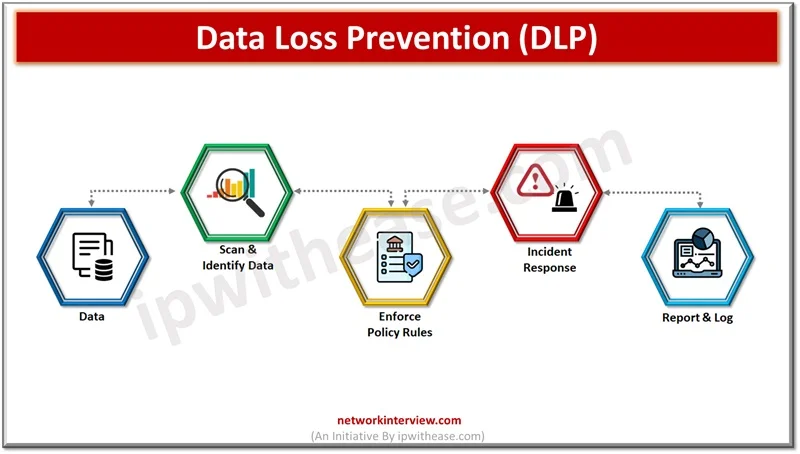
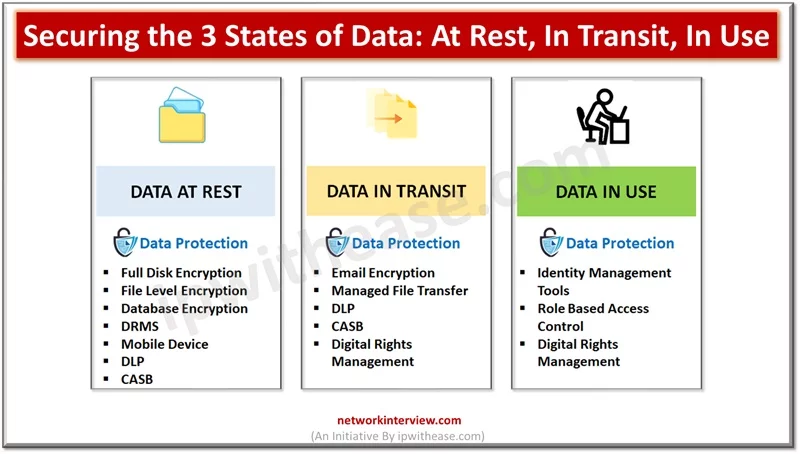
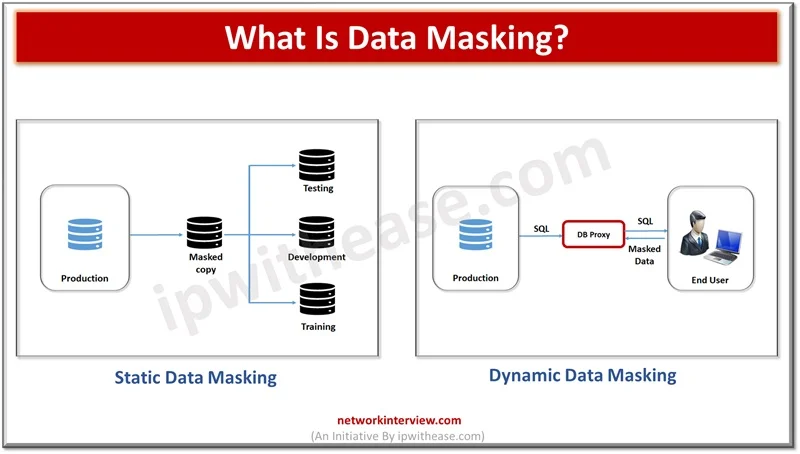
Data is the lifeline of organizations and they rely on a variety of data to run their businesses. Since data is critical to run businesses, it is important to safeguard it from unauthorized access, improper usage. Different approaches are adopted …
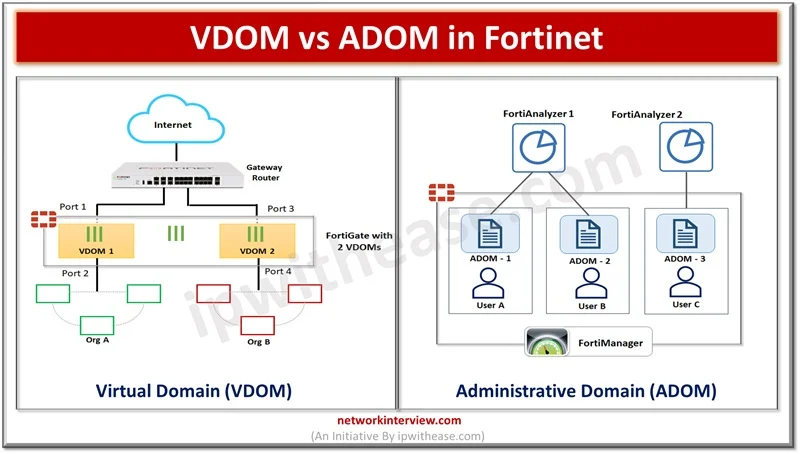
Majority of organizations are moving to cloud based infrastructure to run their IT operations. Cloud service providers require to provide multi-tenancy services and require to have products which support multi-tenant scenarios. Networking is one of the crucial aspects of the …
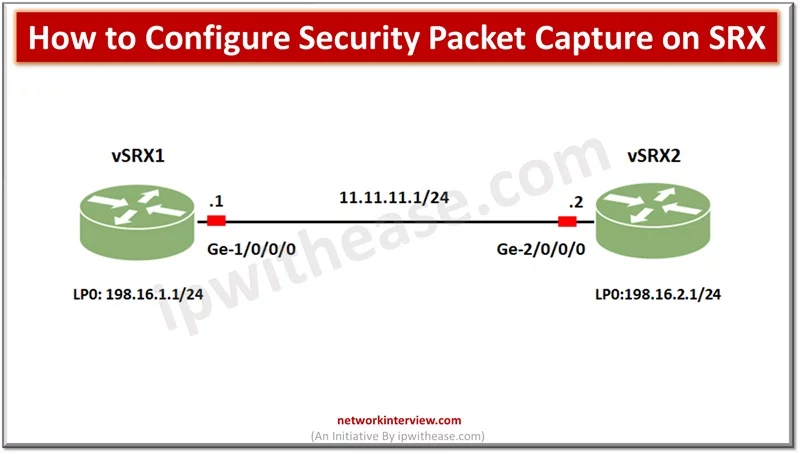
For debugging network issues capturing packet traffic is a very useful utility. It helps to analyse network traffic and help in network monitoring and logging. Packets are captured in binary form without any changes and you can read packet information …
Network protection is enabled from malware by utilizing the SSL proxy component. It is used to prevent malware which is hidden in encrypted traffic. It is used to perform SSL encryption and decryption between server and end client in a …
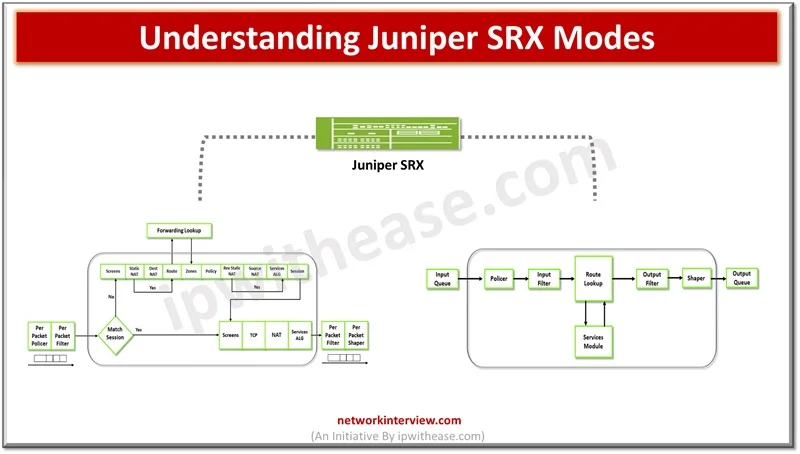
Firewalls perform the processing of traffic for packets which enter and exit a device. Juniper SRX firewalls have a wide variety of filtering and traffic shaping features including policies, screens, network address translation (NAT) and services based on flow. Processing …
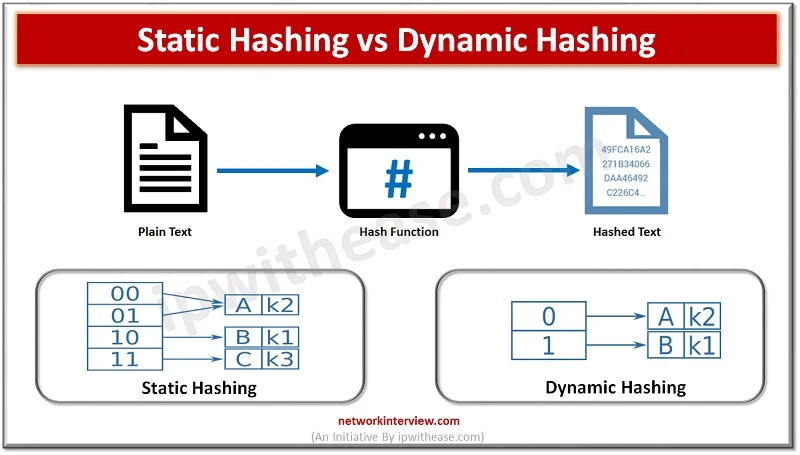
Introduction to Hashing Data structure often contains a lot of data that is difficult to search through. Hashing is an effective solution that can be used to map these large datasets to much smaller tables by utilizing a unique Hash …
To secure networks network administrators create security policies for network resources within the business required to establish security level for network resources. All standard firewalls allow creation or setting up baseline and advanced security policies to enforce rules for transit …
We can’t imagine a network without a firewall, they are the staple of almost every network in the IT landscape. The firewalls provide protection to nearly every network-based transaction. Over a decade the underlying technology has changed rapidly as the …
Network based security landscape is changing drastically and becoming more and more complex and dynamic in operations. New challenges in the cyber security domain related to web based and social network applications, sophisticated cyber-attacks, social engineering attacks are on rise …
Data breaches are costing organizations very expensive and every year exposing millions of people’s sensitive data resulting businesses to lose millions. Data breaches in year 2021 estimated to average cost of $4.24 million. Personally Identifiable and sensitive personal information is …
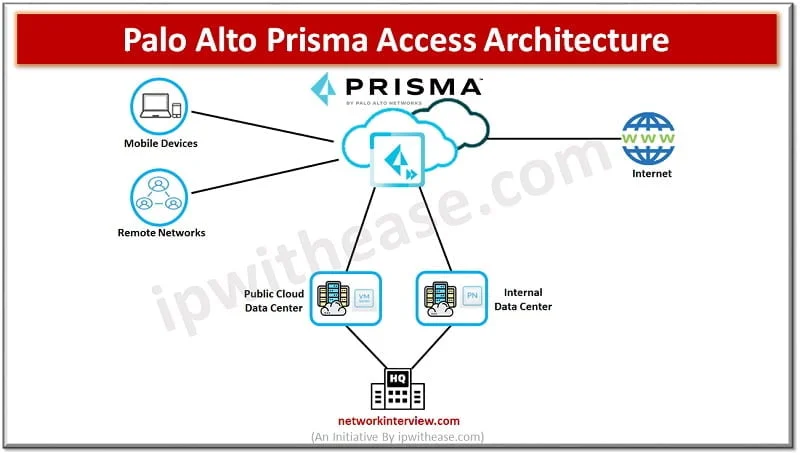
What is Palo Alto Prisma Access? Palo Alto Prisma Access is a Cloud service provided by Palo Alto Networks. This service provides secure access to Internet and business applications that may be hosted on SASE, a corporate headquarters, Data Centres, …
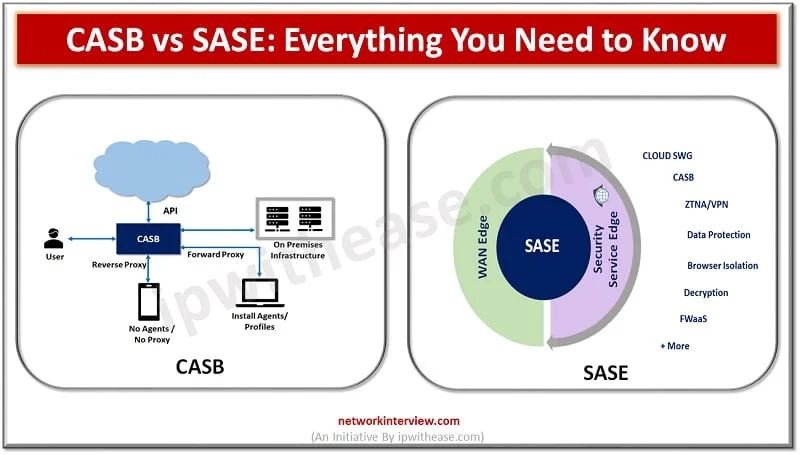
CASB vs SASE: Introduction As more and more data moves onto the cloud new tools and methods are evolving to control data and adhere to security regulations. Coronavirus pandemic is becoming an acceleration factor as all around the world companies …
Today, we are using the internet more than ever before. The usage has increased considerably with the emergence of streaming devices like Firestick, Roku, and Chromecast. Spending time online lets us access the content of our choice. But it also …