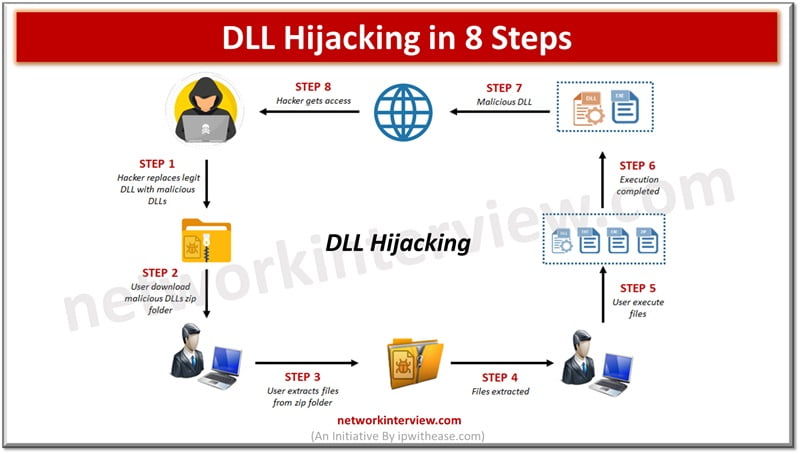
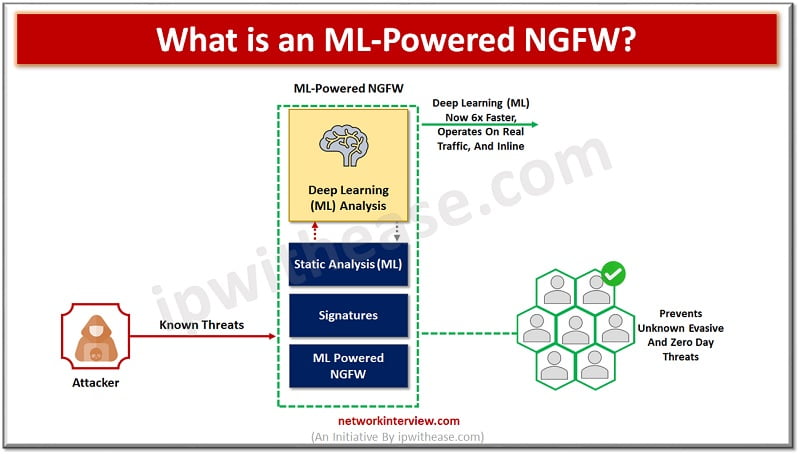
Centralized network management and analysis of network devices is one of the vital requirements of enterprise networks. Individual network component monitoring in larger networks brings a lot of overhead in terms of skills, resources, expertise and not a viable solution …
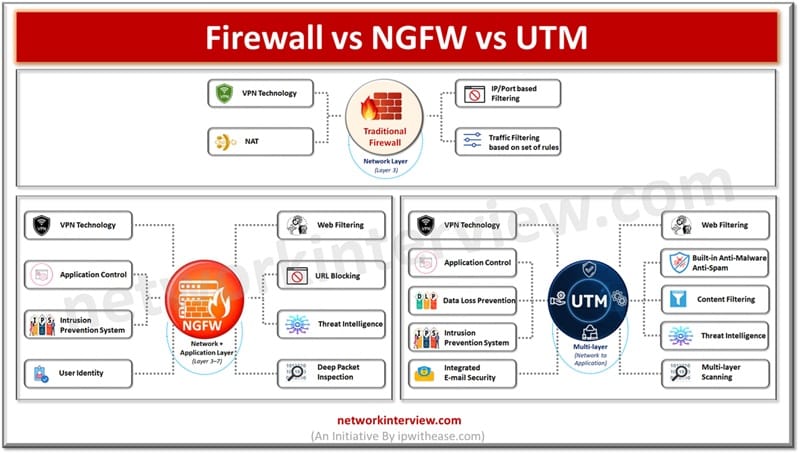
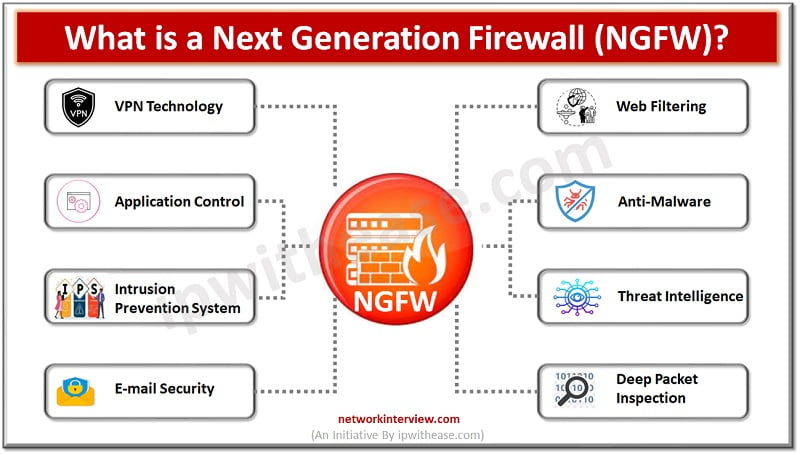
In today’s article we will understand the difference between traditional firewalls, Network generation firewalls (NGFW) and Unified threat management (UTM), their key features. Firewalls sit on the boundary of the network entry point and provide protection against malicious threats originating …
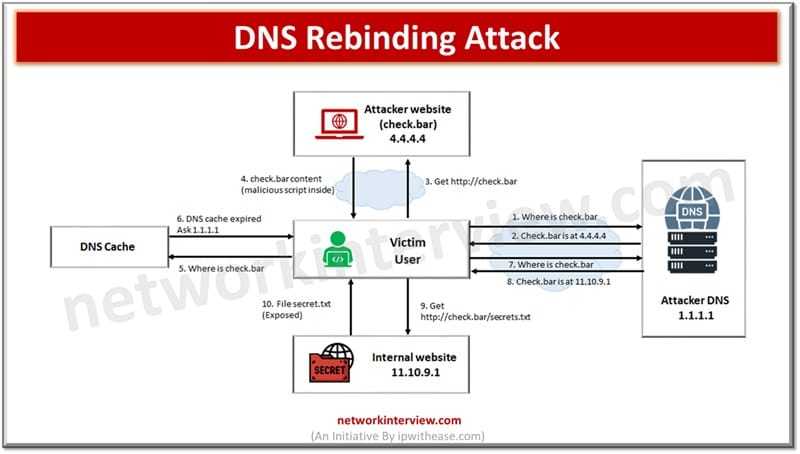
A DNS rebinding attack tricks a browser into bypassing same-origin policy, thereby allowing attackers to access internal networks or devices through malicious DNS responses. In networking systems are addressed with a unique numerical value which is known as IP address. …
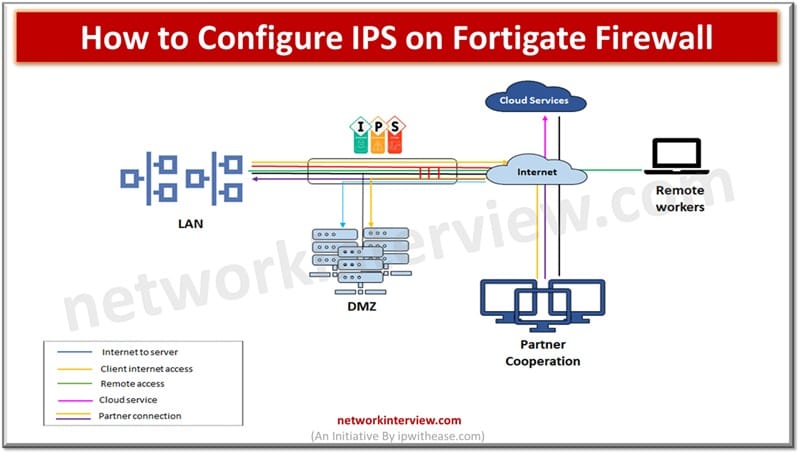
To configure IPS on a FortiGate firewall, enable an IPS sensor in the relevant security policy. Then, apply or customize the sensor under Security Profiles > Intrusion Prevention. Intrusion prevention systems or IPS provide security for the networks and hosts …
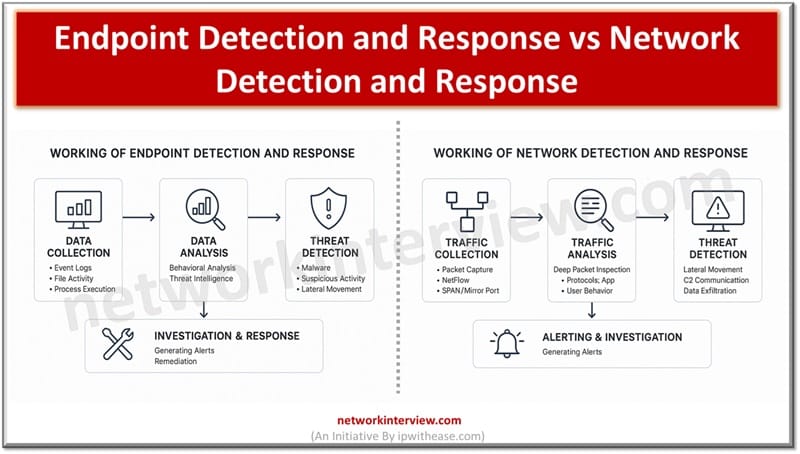
Endpoint Detection and Response focuses on monitoring and responding to threats on individual devices like laptops and servers. Whereas, Network Detection and Response monitors network traffic to detect and respond to threats across the entire network infrastructure. Constant threats and …
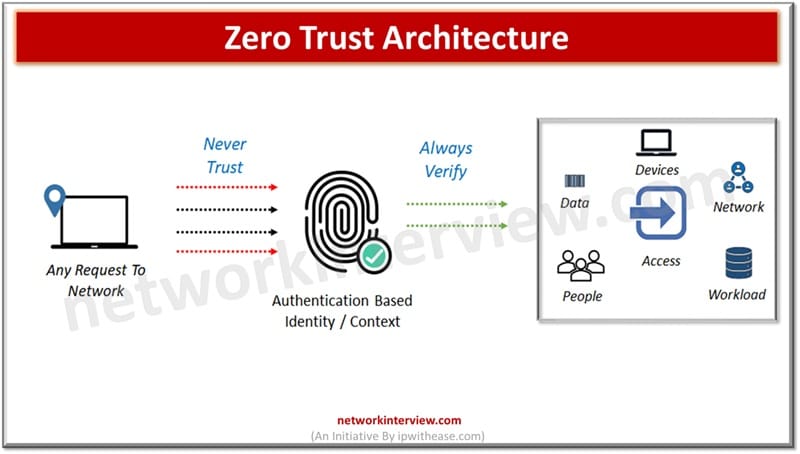
Since organizations are moving away from the traditional IT landscape to cloud computing, cloud-based assets, remote working models, the perimeter based old and traditional model of security is not sufficient enough for protection of data and sensitive systems. The modern …
With increased penetration of cloud computing, AI, machine learning cyber security incidents are on rise. Organizations are working towards reduction of risks associated with new upcoming technologies and trying to strike a balance between business growth and data security. Third …
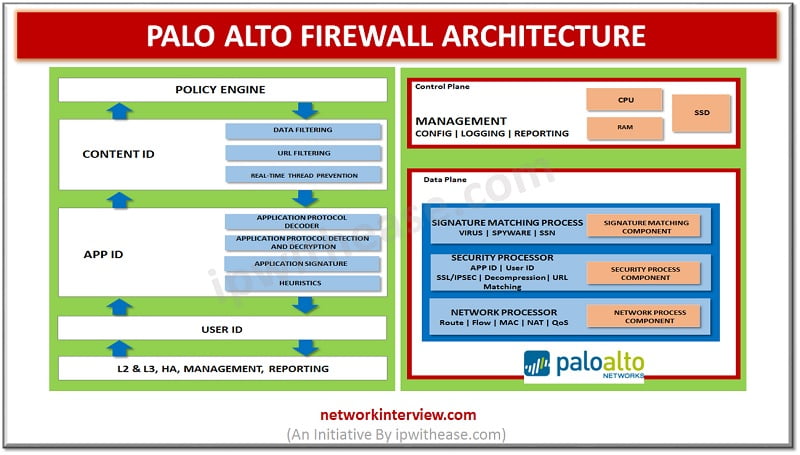
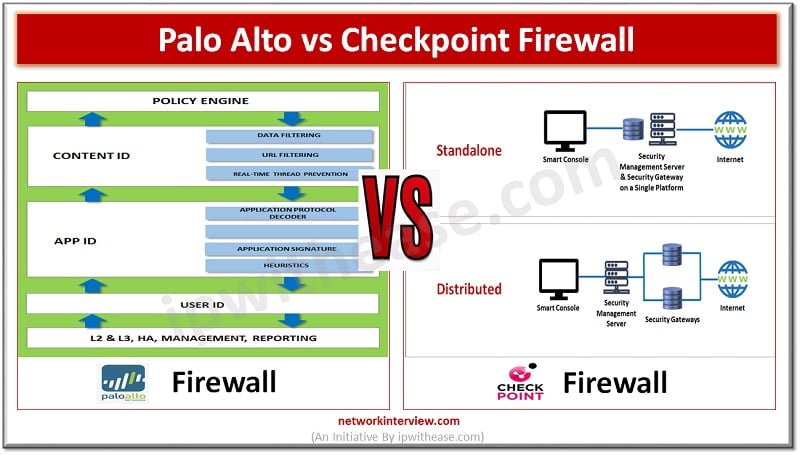
Network architecture refers to the structured approach of network, security devices and services structured to serve the connectivity needs of client devices, also considering controlled traffic flow and availability of services. Network devices typically include switches, routers and firewalls. Palo …
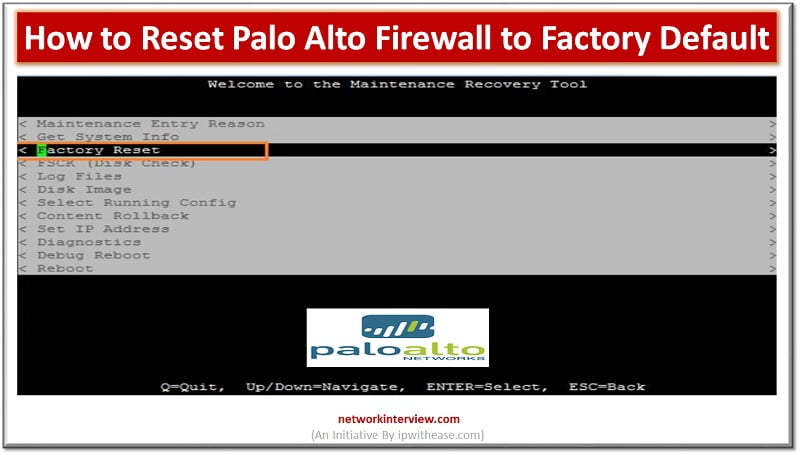
Introduction to Reset Palo Alto Firewall Firewall is a network security device which grants or rejects network access to traffic flowing between untrusted zone (External networks) to trusted (Internal networks) zone. Starting from initial days of Stateful inspection firewalls and …
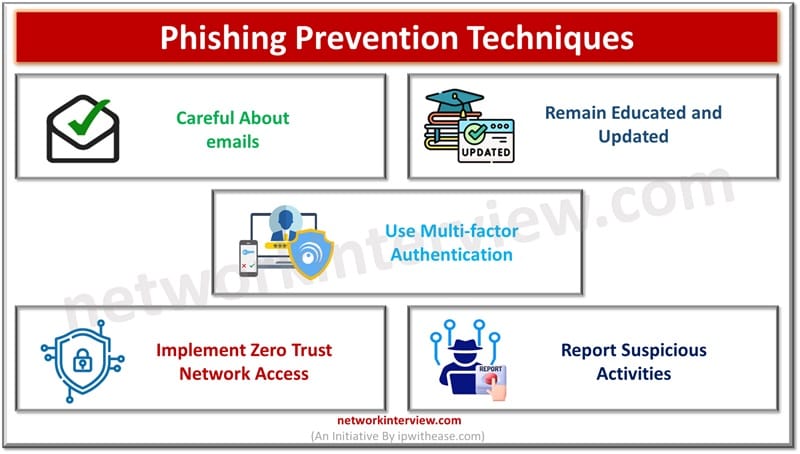
The amount and intensity of cybercrimes is growing exponentially based on social engineering techniques as humans are the weakest link in the chain of security and easy target of compromise. This is further fueled by remote operations. Most companies focus …
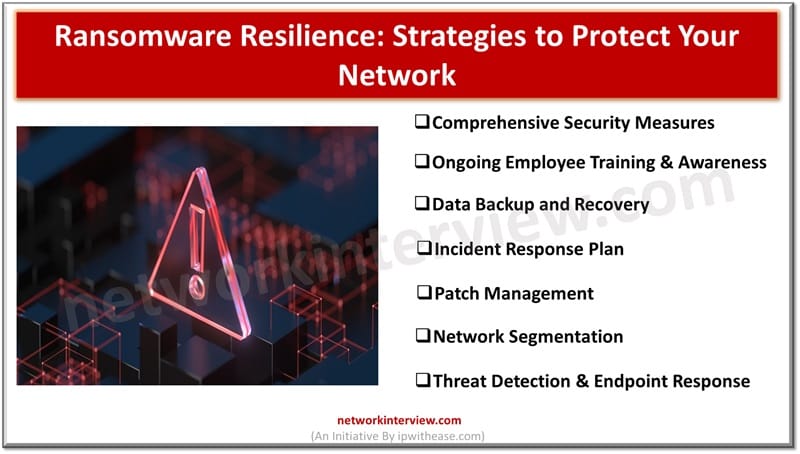
A resilient approach towards security and protection of digital assets is the need of the hour. The approach focuses on protection of hardware infrastructure and business applications to eliminate all vulnerabilities which could impact organizations, customers, and other stakeholders. Businesses …
This is the era of digital dominance and ransomware threat looms largely on enterprises and individuals. It is a kind of digital arrest which has emerged as the most menacing threat in recent years. Cybercriminals have targeted businesses, hospitals, government …
Introduction to Penetration Testing Tools & Software Identifying weaker controls in systems via attack simulation help organizations to gather information about the different ways hackers can gain unauthorised access of systems and sensitive data and information or may get engaged …
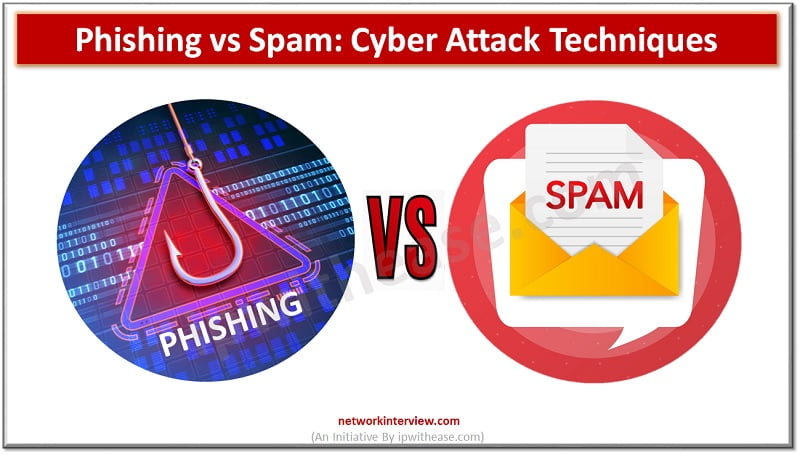
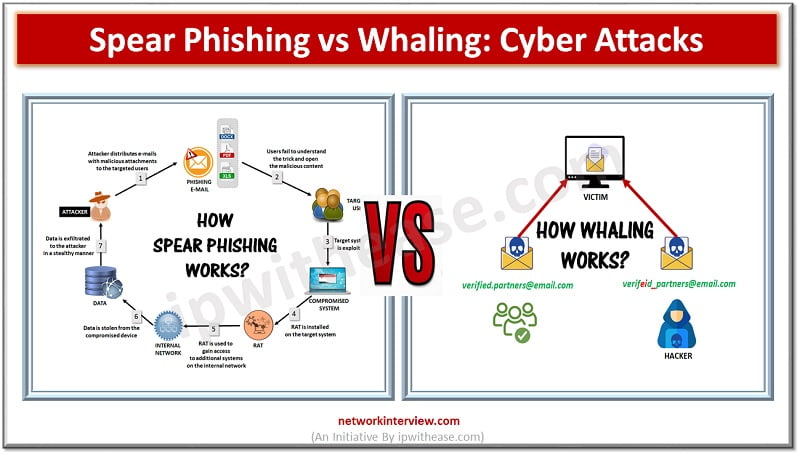
Cyber Attack Technologies Various forms of cyber attacks are prevailing these days and method of attack sophistication has reached new levels where now attackers are not limited only to fake websites, messages or emails but also focus is on theft …
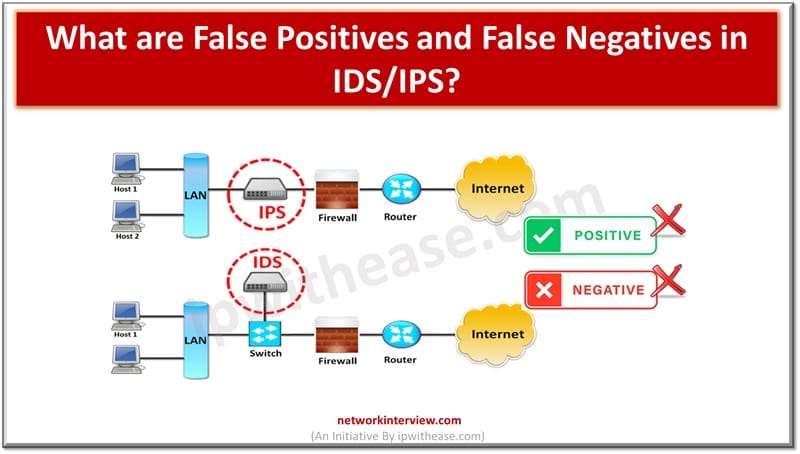
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. **STAY TUNED** Short Interview Questions: Que 13 What are False Positives and False Negatives in …
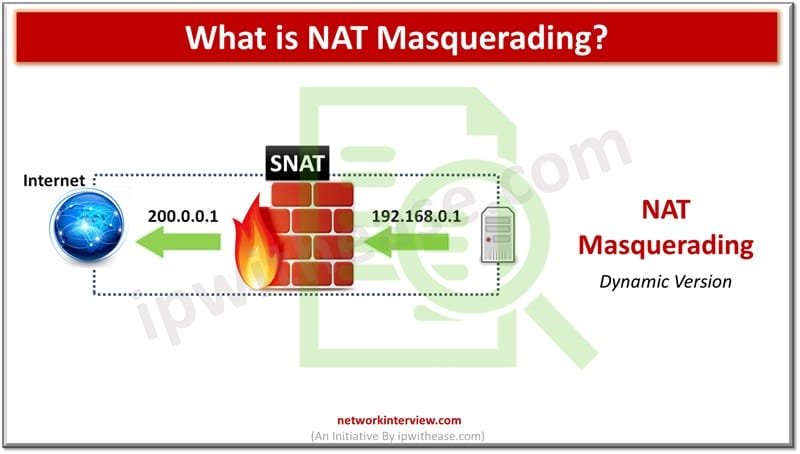
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. **STAY TUNED** Short Interview Questions: Que 12 What is NAT Masquerading?
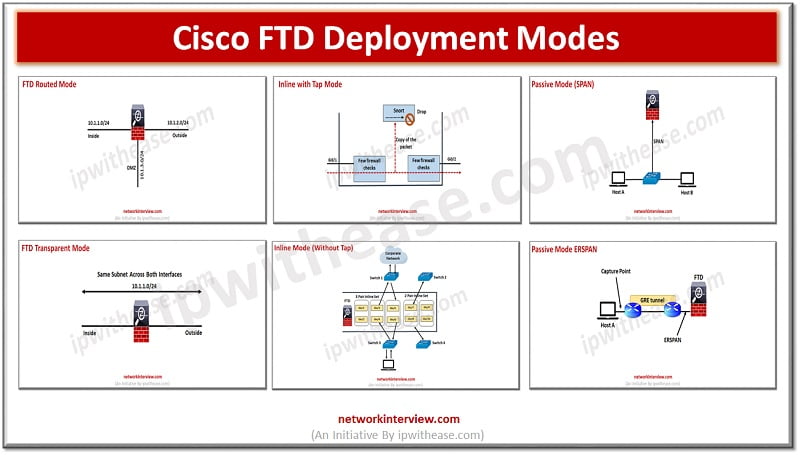
(FTD Deployment Modes: Routed, Transparent, Inline, Inline with tap, Passive SPAN, Passive ERSPAN) Cisco FTD design and deployment implementation involves setting up firewall, SSL inspection, NAT, IPS and active/standby HA. Deployment model determines placement of FirePower into the network as …
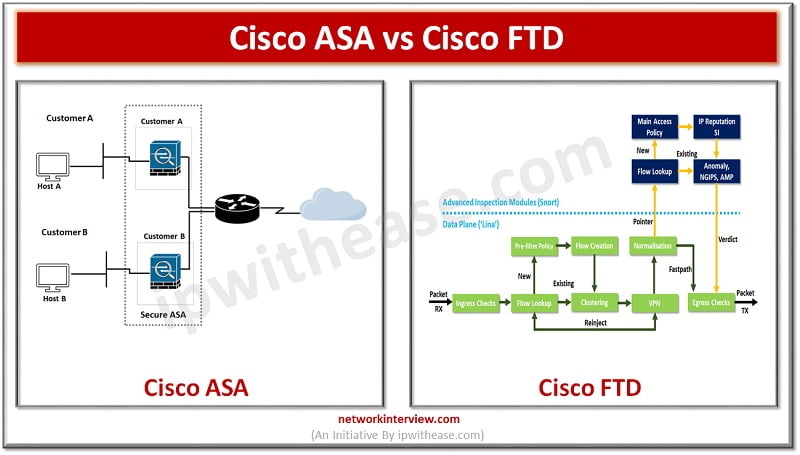
The Cisco Firepower Threat Defense (FTD) and Cisco Adaptive Security Appliance (ASA) are two types of security appliances that provide various features and capabilities to companies. These appliances were created with the intention of safeguarding businesses from cyber threats. Today …
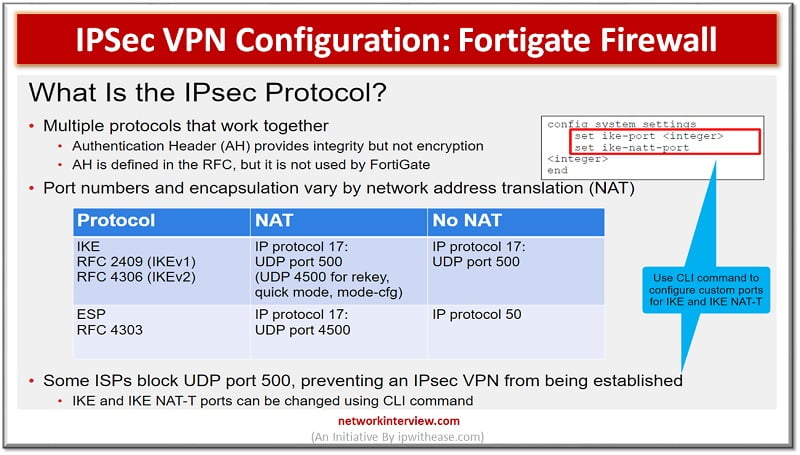
Objectives IPSec IKE Site to Site VPN between two FortiGate Sites Phase I and Phase II Parameters Tunnel Configuration Troubleshooting Commands IPSec VPN Configuration: Fortigate Firewall IPsec: It is a vendor neutral security protocol which is used to link …
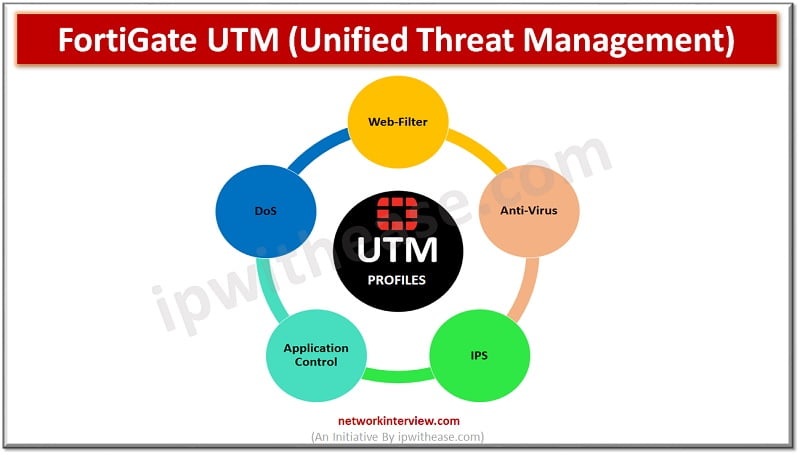
UTM-Unified Threat Management UTM (Unified Threat Management) is a feature of a firewall in which multiple security profiles combine and provide protection from threats and attacks. These features are antivirus, web filtering, IPS, anti-spam etc. UTM is the consolidated solution …
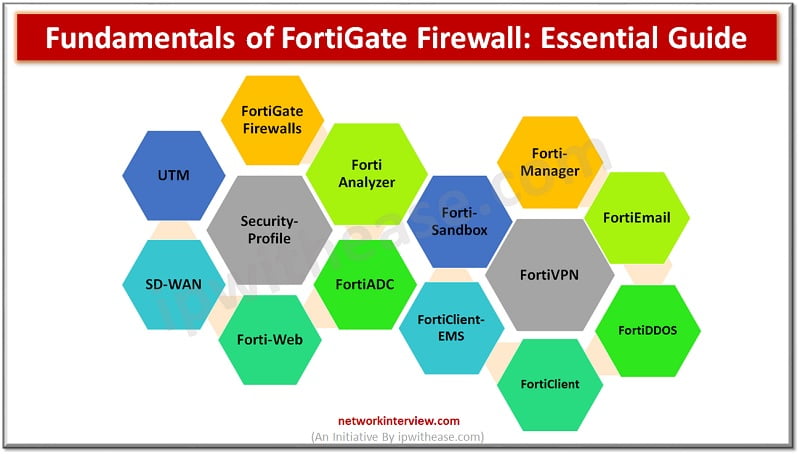
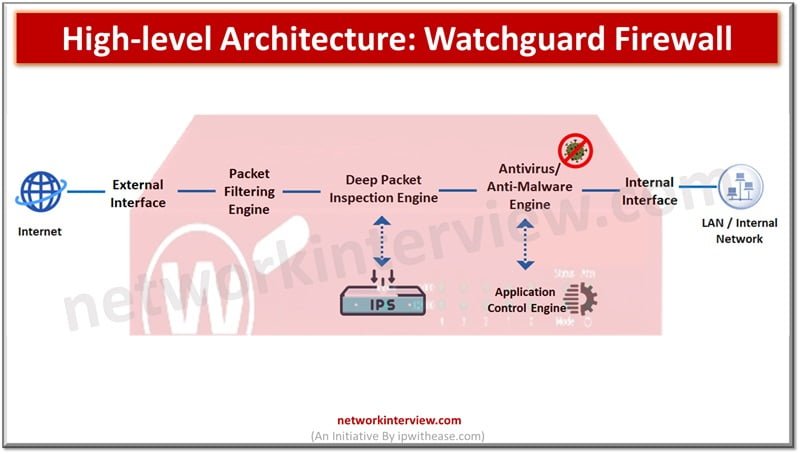
FortiGate fundamentals and principles involve high security infrastructure and provide a secure set up to the client. FortiGate Firewall is the most respected and highly used security product in the market. It uses artificial intelligence and machine learning to achieve …
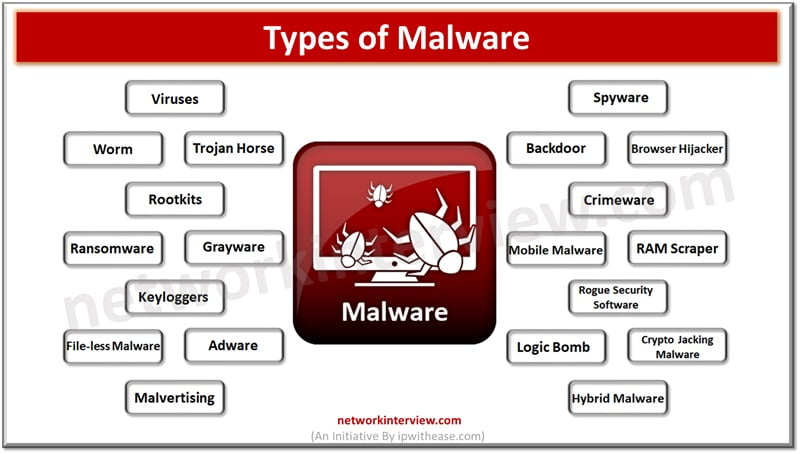
Malware software is a constant concern in the digital age. Cyber criminals continuously come up with innovative ways to break into computer systems and steal personal data, cause disruption to businesses, ask for ransomware, cause data destruction. Malware software is …
Data security is a major concern for enterprises especially dealing with sensitive data. Creating a safe and secure environment becomes top most priority for them. In 2023 cyber attacks worldwide increased by 7%. Each company experiencing on an average 1200+ …
There are various types of Cyber Attacks on rise. As physical boundaries are diminishing rapidly and majority of enterprises rely on Internet and other emerging technologies such as cloud computing, GenAI etc. to run their businesses bad vectors are taking …
Traditional firewalls have come a long way by providing a clear overview of network traffic jams. Allows or blocks traffic according to port, state and protocols and filters traffic as per rules specified by firewall administrators. NGFWs have eventually changed …
Firewalls have always been the first line of defence, traditional firewalls have a set of rules to keep bad traffic and requests from malicious hackers away from organization networks. The role of traditional firewalls is however changing and getting replaced …
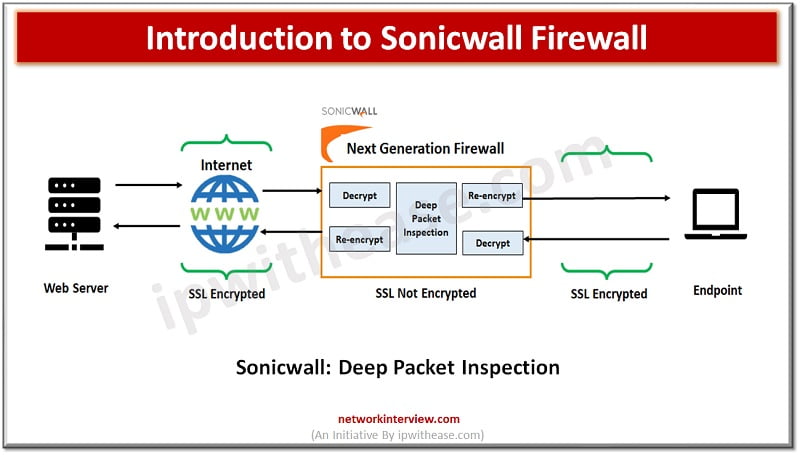
Evolution of Firewalls: Sonicwall Firewall Firewall technologies have evolved at a very rapid pace since its inception and from initial packet filtering firewalls which use to inspect packet traffic and took decision to allow or reject packets, which is then …
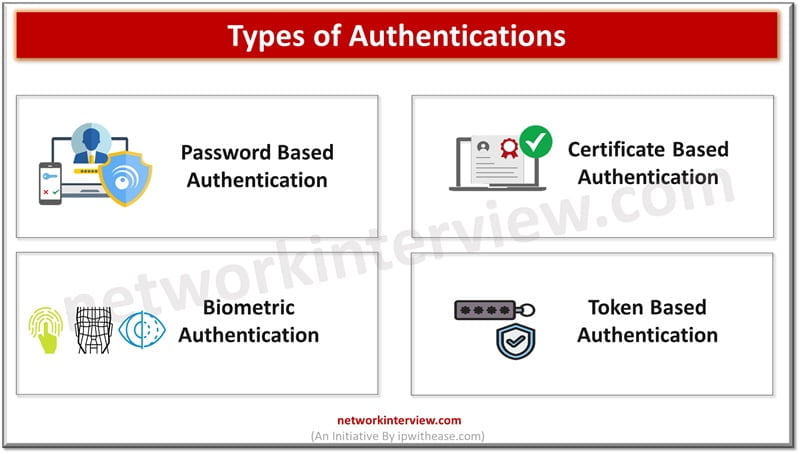
Authentication is the first step at entry level for ensuring security and it is required for managing user identification and providing access control for seamless operational experience in a secure manner. Individual authentications are not only restricted to passwords and …
Firewalls are network perimeter security devices which separate internal networks from external public networks such as the Internet to reduce the risk of external attacks. Firewalls use access policies and identify types of information, in addition they also control ports …
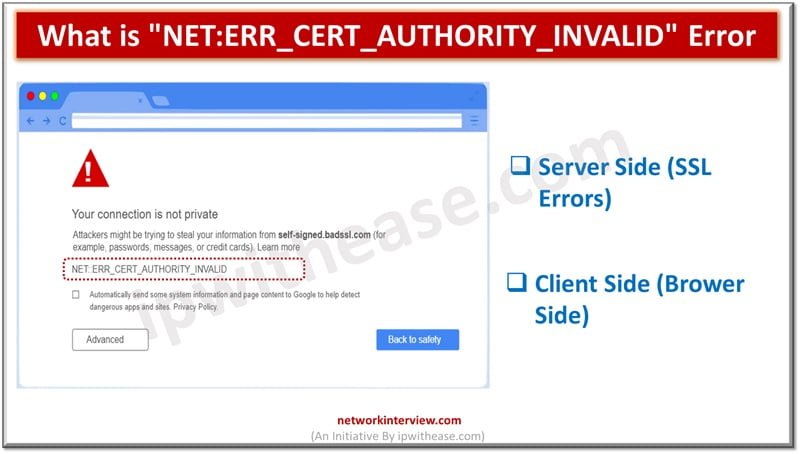
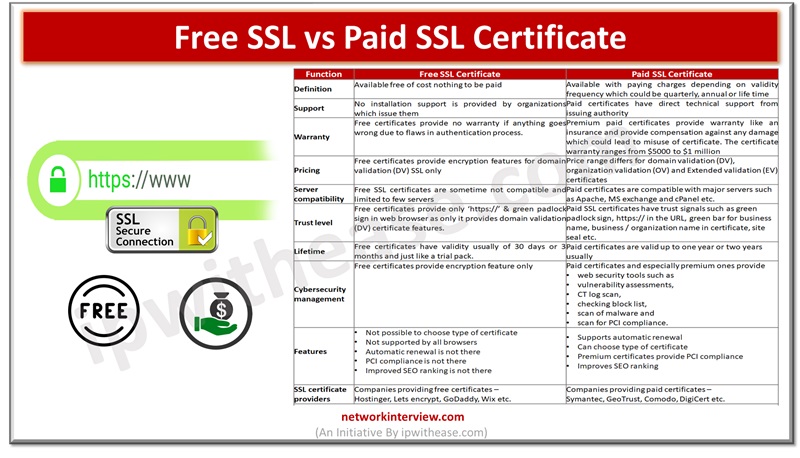
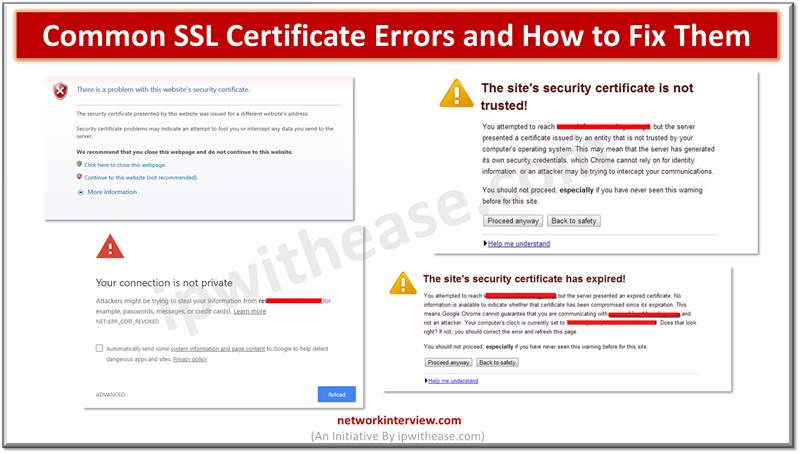
Secure Socket layer (SSL) certificates is one of the most widely used and popular mechanisms for public website security. SSL certificates keep data of users secure, verify ownership for the website, prevent attack vectors from creation of a fake version …
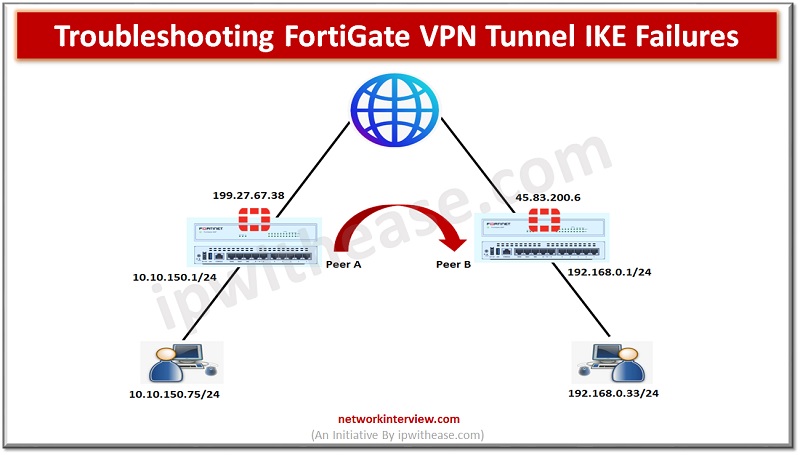
In our previous post, we have already discussed the IPSec VPN Configuration in Fortigate Firewall. Here in this post we will understand how to trouble shoot the FortiGate VPN tunnel IKE failures. We are using below topology to troubleshoot the …
Cyber Attacks Cyber attacks are on rise since Covid 19 at a more rapid pace compared to before. Various forms of cyber attack techniques being used by hackers to gain access to organizations resulting in devastating effects such as unauthorized …
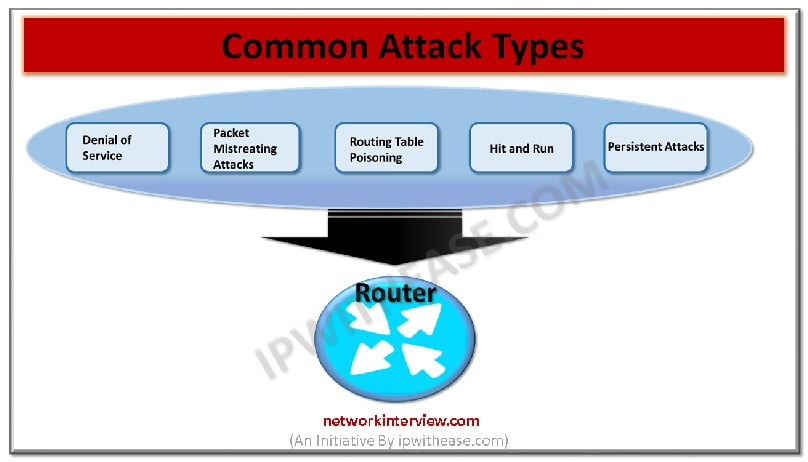
It is not possible to 100% prevent the router attacks. However, there are possibilities of few things that could be done for preventing the occurrence of most common attacks of routers on the network and the system. Widespread attacks are …
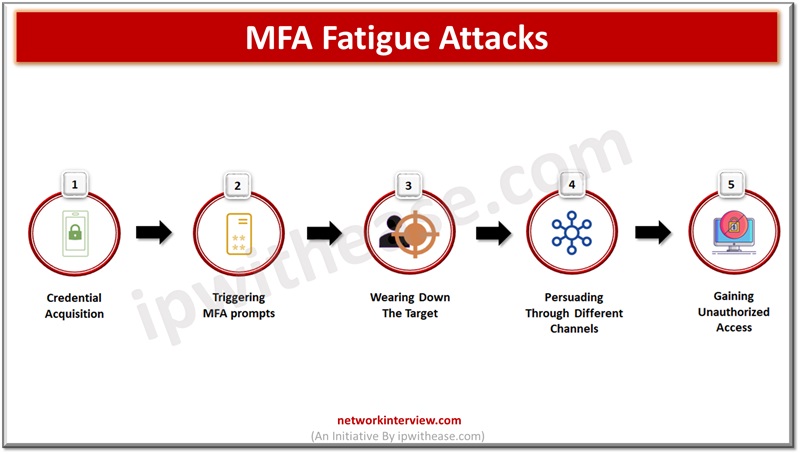
Leaked or stolen credentials are primary sources being used by cybercriminals in breach networks and steel company confidential and sensitive data. Normal authentication involving a username and password is an old technique and no longer provides protection against sophisticated attacks …
Attackers are constantly looking for vulnerabilities to penetrate your networks. Protection against direct, external threats require extensive network security functions deployed on the edge. Protections on the edge are provided by stateful and next generation firewalls (NGFWs) which offer features …
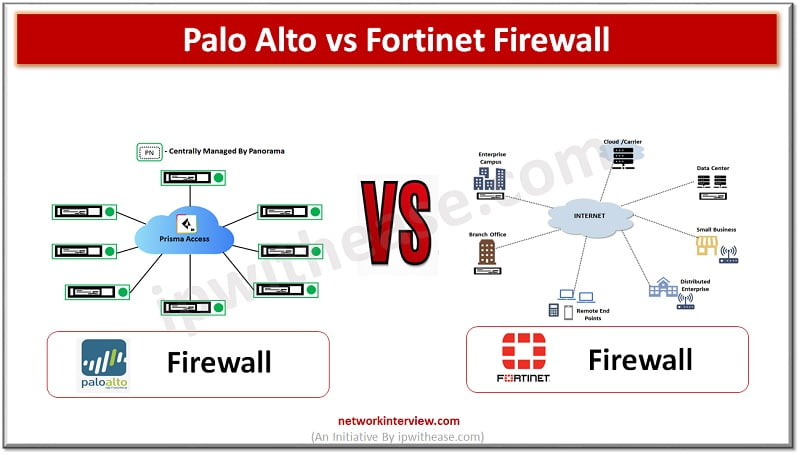
(Diagram depicting Palo Alto vs Fortinet Firewall) Organizations need to keep pace with rapid increase in technology demands such as remote working, anywhere connectivity, lower latency , increased availability along with protection of infrastructure from a never ending list of …
As cyberattacks are on rise and thousands of Internet users and organizations are targeted by attack vectors, safety and security of data is a major cause of concern. The secure socket layer (SSL) certificates are widely used by websites for …
Secure Socket layer (SSL) certificates are used widely by organizations to secure websites and every business needs to have a valid SSL certificate to safeguard client’s security and credibility of brand. Secure Socket layer (SSL) is an encryption protocol and …
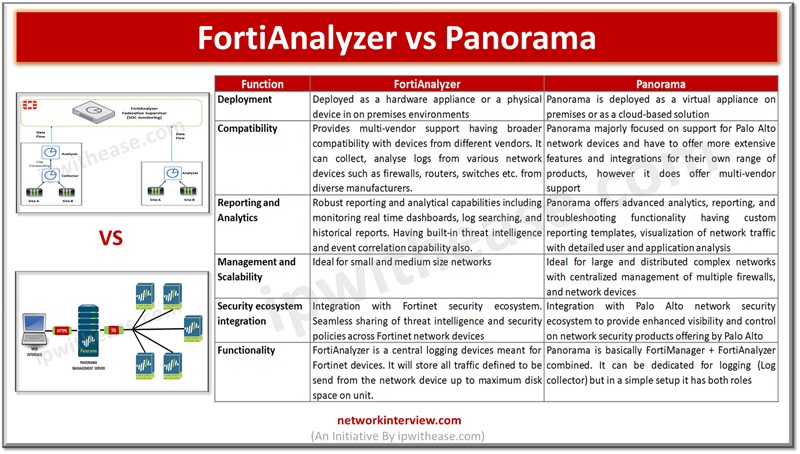
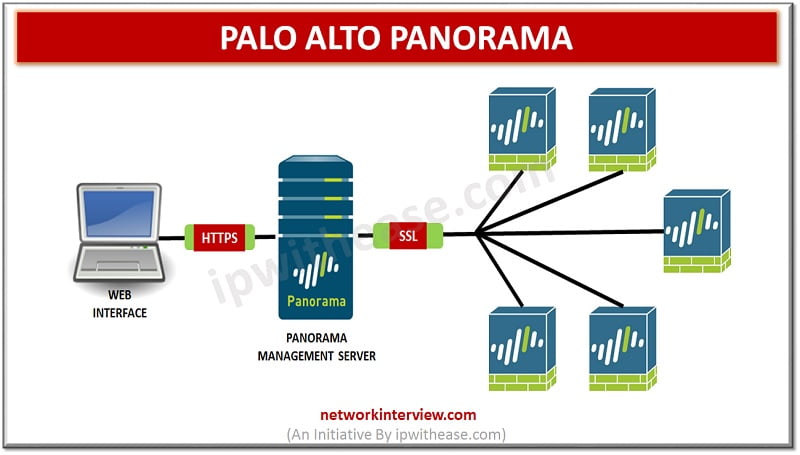
Introduction to Palo Alto Panorama Palo Alto Panorama is the centralized management server that offers a global visibility and control over the multiple Palo Alto Networks next generation firewalls from web interface console. Panorama manage multiple Palo Alto Networks firewalls …
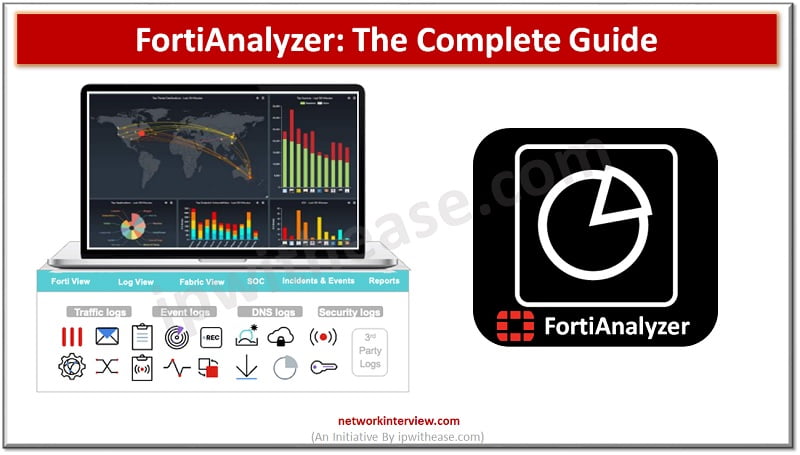
FortiAnalyzer: Security Management Platform FortiAnalyzer aggregates log data from one or more Fortinet devices and creates a single platform to view all the reports and events. It can fetch logs from the Fortinet devices once devices are registered to FortiAnalyzer. …
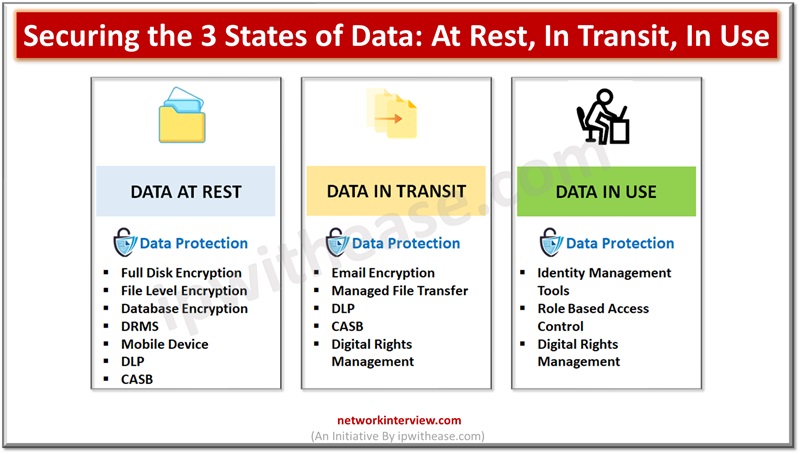
Data is the lifeline of organizations and they rely on a variety of data to run their businesses. Since data is critical to run businesses, it is important to safeguard it from unauthorized access, improper usage. Different approaches are adopted …
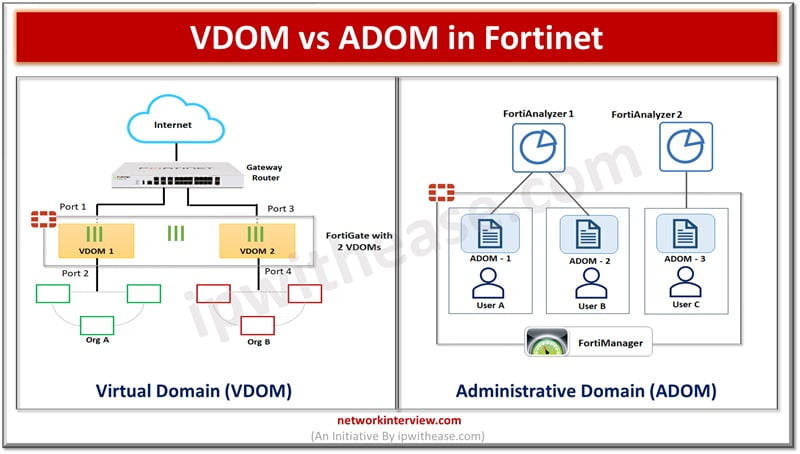
Majority of organizations are moving to cloud based infrastructure to run their IT operations. Cloud service providers require to provide multi-tenancy services and require to have products which support multi-tenant scenarios. Networking is one of the crucial aspects of the …
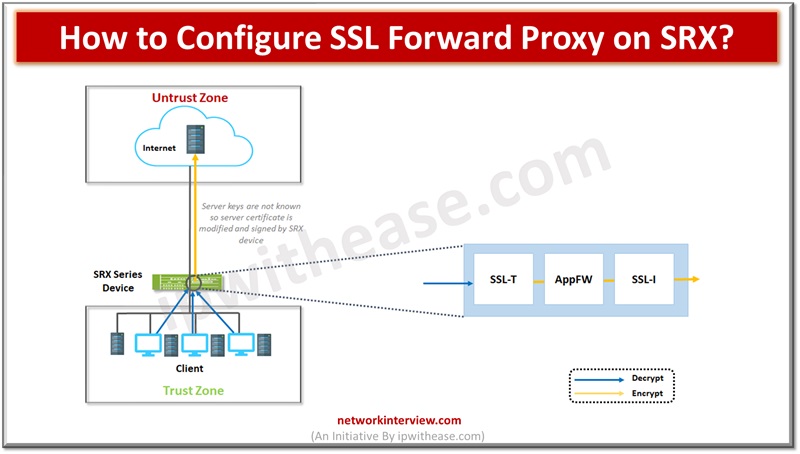
Network protection is enabled from malware by utilizing the SSL proxy component. It is used to prevent malware which is hidden in encrypted traffic. It is used to perform SSL encryption and decryption between server and end client in a …
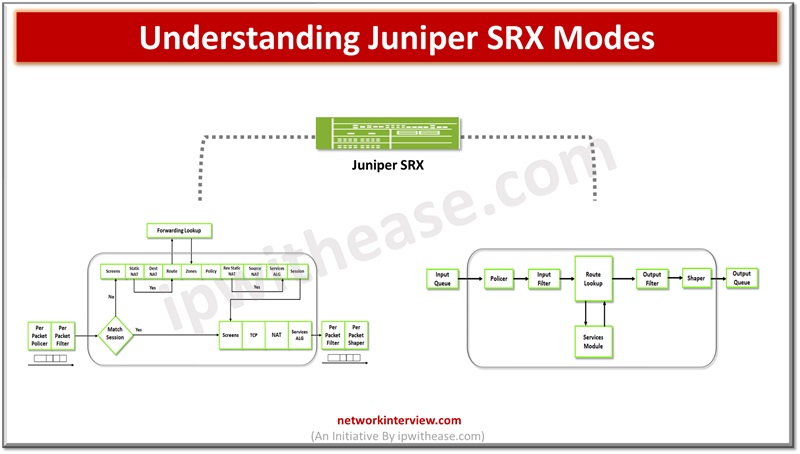
Firewalls perform the processing of traffic for packets which enter and exit a device. Juniper SRX firewalls have a wide variety of filtering and traffic shaping features including policies, screens, network address translation (NAT) and services based on flow. Processing …
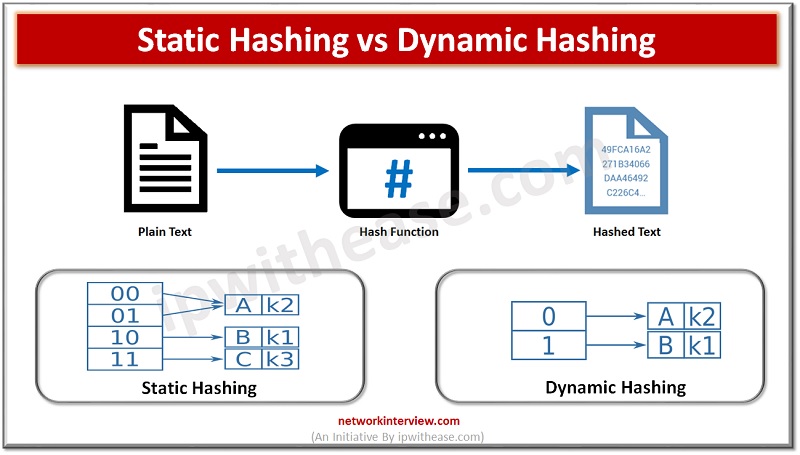
Introduction to Hashing Data structure often contains a lot of data that is difficult to search through. Hashing is an effective solution that can be used to map these large datasets to much smaller tables by utilizing a unique Hash …