How to Configure Security Packet Capture on SRX?
For debugging network issues capturing packet traffic is a very useful utility. It helps to analyse network traffic and help in network monitoring and logging. Packets are captured in binary form without any changes and you can read packet information offline using packet analyzers such as wireshark, tcpdump etc. packet capture is similar to capturing sampled traffic on device and also captures IP fragments.
Today we look more in detail about how to configure security packet capture of SRX firewalls.
Configure Security Packet Capture on SRX
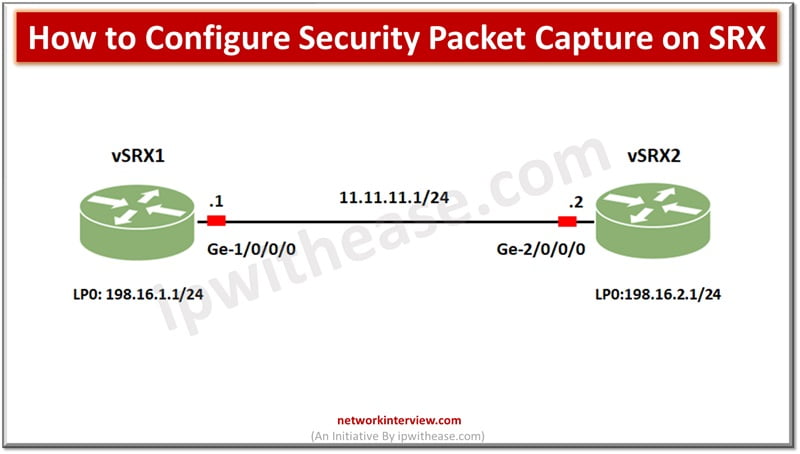
Before we begin configuring security packet capture on SRX we will use a sample topology.
There are two vSRX devices which are connected to each other using ge-01/0/0 interface having IP subnet as 11.11.11.0/24. Loopback interfaces are connected to vSRX1 and vSRX2 having IP address as 198.16.1.1/24 and 198.16.2.1/24.
Scenario: capture traffic with
Protocol : ICMP
Source : 198.16.1.1
Target : 198.16.2.1
With the assumption that routing is already configured on both devices. We want to capture ICMP only traffic from source 198.16.1.1 to 198.16.2.1 unidirectionally.
Related: Palo Alto Packet Capture/ Packet Sniffing
Enable Packet Capture
Enable packet capture and configure the output file to which capture details will be written. The filename is ‘CAPTURE2’.
set forwarding-options packet-capture file filename CAPTURE2
Write Firewall Filter
Now write a firewall filter to match the traffic which is to go in the capture file. Match ICMP traffic from source 198.16.1.1 (vSRX1) loopback interface to target 198.16.2.1 (vSRX2) loopback interface.
Action would be mentioned as ‘Sample’ which means to capture matching traffic. In addition, enable the count of the number of matched traffic.
set firewall filter CAPTURE_FILTER term 1 from source-address 198.16.1.1/32
set firewall filter CAPTURE_FILTER term 1 from destination-address 198.16.2.1/32
set firewall filter CAPTURE_FILTER term 1 from protocol icmp
set firewall filter CAPTURE_FILTER term 1 then count COUNT1
set firewall filter CAPTURE_FILTER term 1 then sample
set firewall filter CAPTURE_FILTER term 2 then accept
Apply firewall filter to interface (ge-1/0/0/0)
set interfaces ge-1/0/0-unit 0 family inet filter input CAPTURE_FILTER
User1@vSRX2# show | compare
[edit interfaces ge-1/0/0 unit 0 family inet filter]
– input FILTER2;
+ input CAPTURE_FILTER;
[edit]
+ forwarding-options {
+ packet-capture {
+ file filename CAPTURE2;
+ }
+ }
[edit firewall]
+ filter CAPTURE_FILTER {
+ term 1 {
+ from {
+ source-address {
+ 198.16.1.1/32;
+ }
+ destination-address {
+ 198.16.2.1/32;
+ }
+ protocol icmp;
+ }
+ then {
+ count COUNT1;
+ sample;
+ }
+ }
+ term 2 {
+ then accept;
+ }
+ }
We have to disable the packet capture when it is not required anymore.
set forwarding-options packet-capture disable
The capture result is stored in “/var/tmp/” directory and with the name of “CAPTURE2.ge-1.0.0” name of interface is auto added to the name which is configured for capture file.
We can use the show firewall command to show the number of packets matched and captured.
User@vSRX2# run show firewall
Filter: __default_bpdu_filter__
…
Filter: CAPTURE_FILTER
Counters:
Name Bytes Packets
COUNT1 512 3
FAQs Related to Juniper SRX Packet Capture
- What is packet capture on Juniper SRX devices?
Packet capture on Juniper SRX devices is a feature that allows you to capture and analyze network traffic passing through the device. It’s useful for troubleshooting network issues, analyzing traffic patterns, and diagnosing security incidents.
- How do I perform a packet capture on Juniper SRX?
Packet capture on Juniper SRX devices can be performed using the monitor traffic command in the CLI (Command-Line Interface). You specify the interface, direction (ingress or egress), and any additional filters to capture specific traffic.
- Can I capture packets based on specific criteria?
Yes, you can apply filters to capture packets based on specific criteria such as source or destination IP address, protocol, port number, etc. This helps in narrowing down the captured packets to focus on relevant traffic.
- Where are the captured packets stored?
Captured packets are typically stored in memory buffers on the Juniper SRX device. You can then view the captured packets directly on the device or export them to an external server for further analysis using tools like Wireshark.
- How much memory is allocated for packet capture?
The amount of memory allocated for packet capture depends on the model and configuration of the Juniper SRX device. You can check the available memory and adjust the capture settings accordingly to avoid running out of memory during capture.
- Can I capture packets for a specific duration?
Yes, you can specify the duration for which you want to capture packets using the duration option with the monitor traffic command. This allows you to capture packets for a specific period, which is useful for troubleshooting intermittent network issues.
- Is it possible to capture packets on multiple interfaces simultaneously?
Yes, you can capture packets on multiple interfaces simultaneously by running multiple packet capture sessions concurrently. This is useful for analyzing traffic between different network segments or troubleshooting complex network configurations.
- Are there any performance impacts of packet capture on Juniper SRX devices?
Performing packet capture on Juniper SRX devices may have some performance impact, especially if capturing a large volume of traffic or applying complex filters. It’s recommended to use packet capture judiciously and only when necessary to minimize any potential performance degradation.
- Can I automate packet capture tasks on Juniper SRX devices?
Yes, you can automate packet capture tasks on Juniper SRX devices using scripting or automation tools that interact with the device’s CLI interface. This allows you to schedule packet captures, retrieve captured packets, and perform analysis programmatically.
- Are there any security considerations when capturing packets on Juniper SRX devices?
When capturing packets on Juniper SRX devices, it’s important to ensure that sensitive information such as passwords or personally identifiable information (PII) is not captured unintentionally. Additionally, restrict access to packet capture functionality to authorized personnel to prevent misuse or unauthorized access to network traffic.
Continue Reading:
How to configure SSL Forward Proxy on SRX?
Understanding Juniper SRX Modes
Tag:Juniper SRX