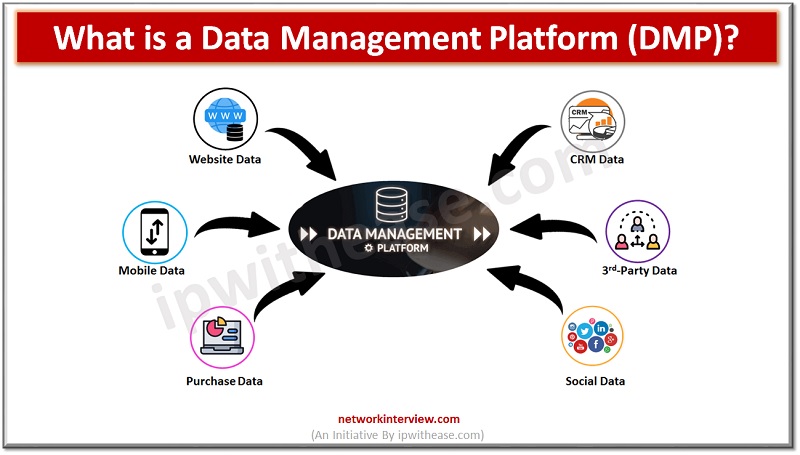
In today’s digital age, data is everything. From businesses to individuals, having access to the right data can make all the difference in making decisions and optimizing processes. Data Management Platforms (DMPs) are powerful systems that enable organizations to manage, …
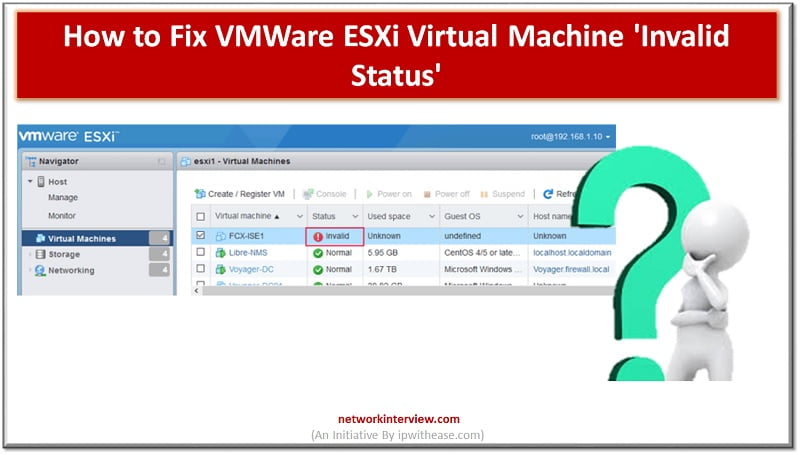
Troubleshooting VMWare ESXi Virtual Machine ‘Invalid Status’ Let’s troubleshoot VM Invalid status You can see multiple “invalid” VM machines in the image below. Here status is showing invalid. Reason of Invalid VM Machine status could be related to the storage …
Overview In our previous article, we studied IPSec VPN Set Up. In this article we will run through CLI commands and GUI steps to configure an IPSec VPN, including the tunnel and route configuration on a Palo Alto Networks firewall. …
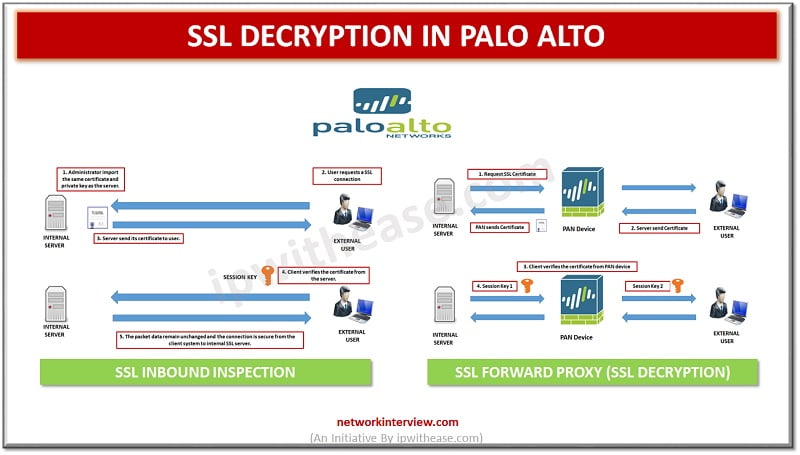
Before digging deep into Palo alto SSL Decryption, let’s first understand what is Decryption? What is Decryption? Palo Alto firewalls can be decrypt and inspect traffic to gain visibility of threats and to control protocols, certificate verification and failure handling. …
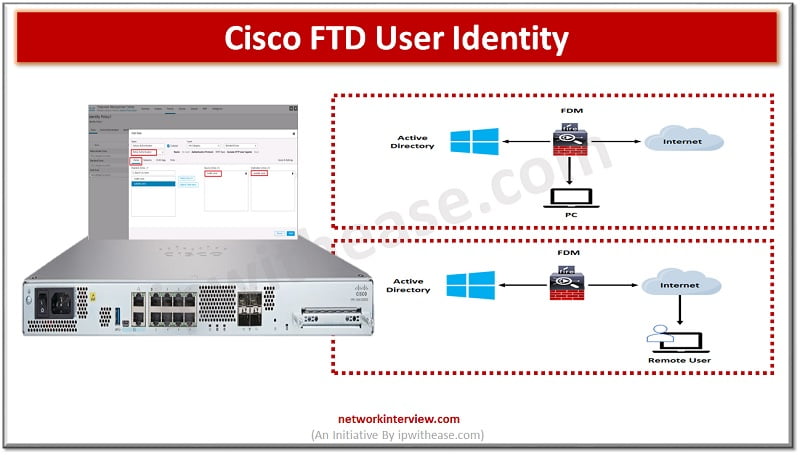
User identity information helps to identify the source of policy breaches, attacks or network vulnerabilities and trace them to specific users. Majority of traffic inspection products support filtering based on IP address. However, Cisco FTD identity policy feature gives the …
Web development is an area in which companies have taken a serious turn in the past few years. With the help of the Internet and modern techniques, enterprises have become extremely successful and popular among online customers. The world has …
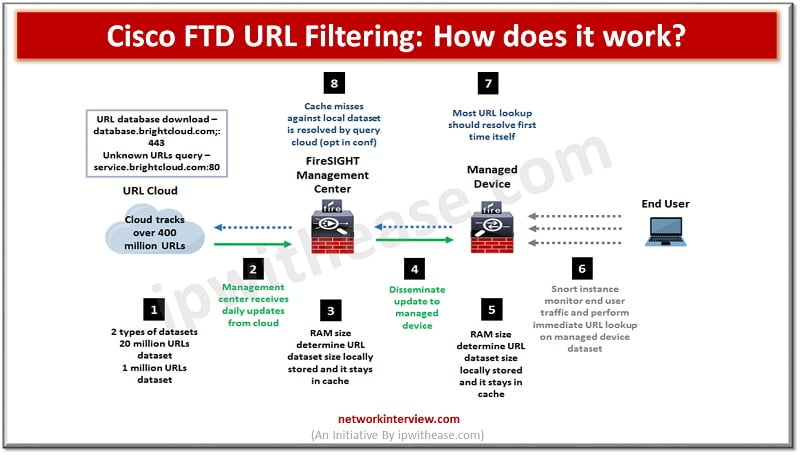
Pic: Showing How Cisco FTD URL Filtering works URL filtering or content filtering is one of the key features of firewalls. It helps to prevent access to harmful and malicious content which could cause data loss, system crash, virus or …
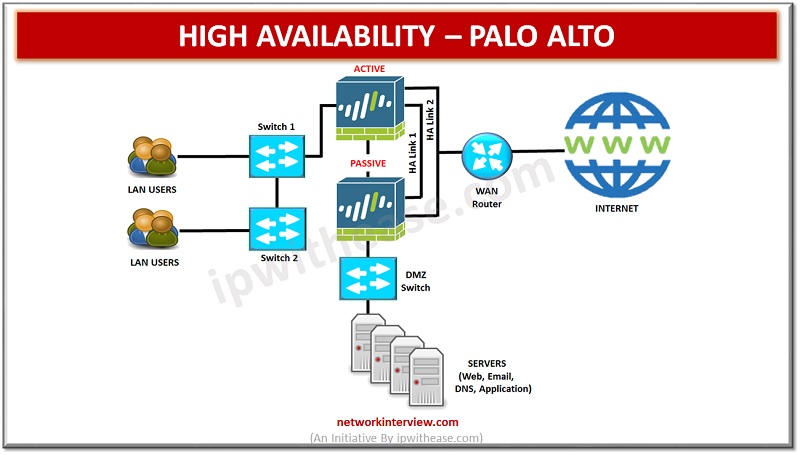
High availability (HA) refers to a system or component that is operational without interruption for long periods of time. High availability (HA) is measured as a percentage, with a 100% percent system indicating a service that experiences zero downtime. High …
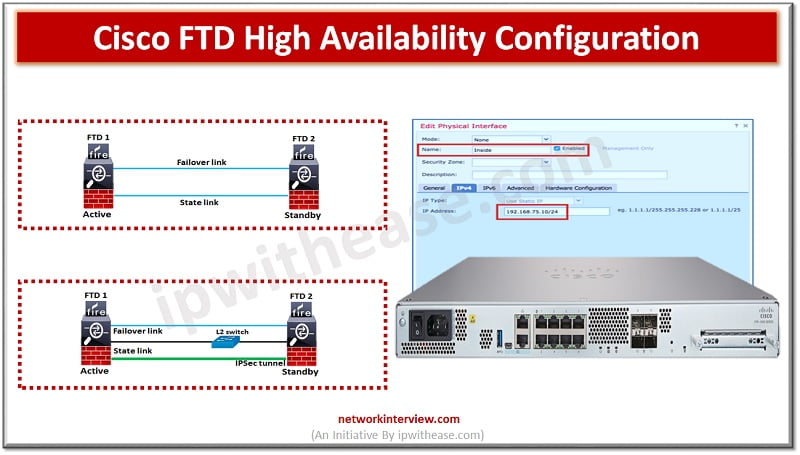
To ensure uptime and continuous availability in the event of disaster is a required key feature for any production environments be it servers, networks and other computing equipment. All Cisco devices majority support high availability (HA) also known as failover. …
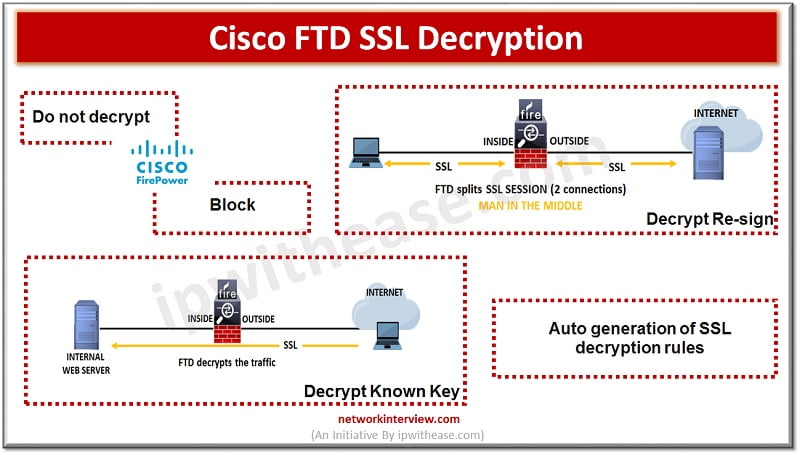
Some protocols like HTTPS use Secure socket layer (SSL), transport layer protocol (TLS) to encrypt traffic for secure transmissions. As the system cant inspect encrypted connections we first must decrypt to apply access roles which consider higher layer traffic characteristics …
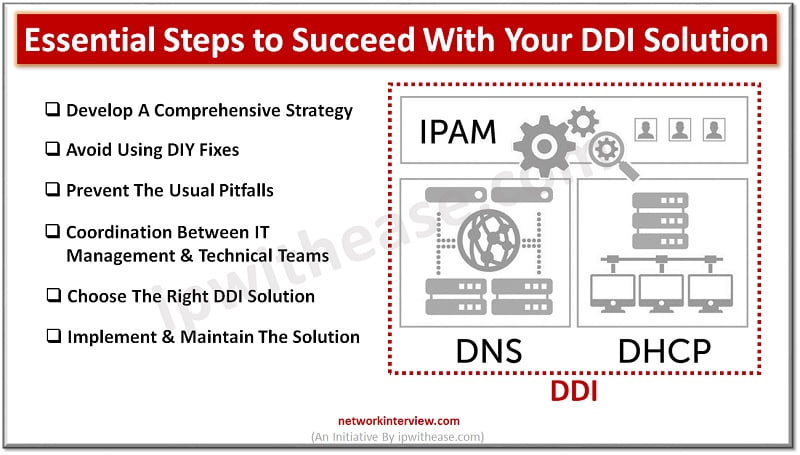
The acronym DDI stands for DNS, DHCP, and IP address management (IPAM). The combination of these three crucial networking elements into a single management solution is referred to by this widely used acronym. A DDI solution offers a centralised platform …
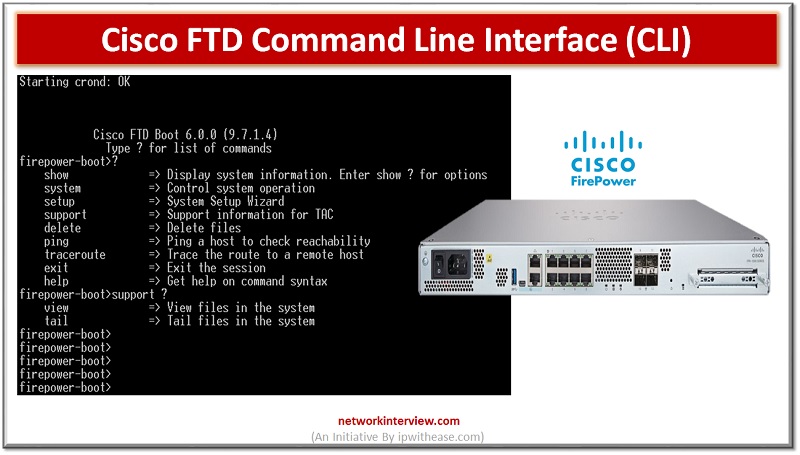
Majority of Cisco devices provide command line interface (CLI) as we call it to configure, manage and troubleshoot devices. Use of CLI allows users to execute Cisco IOS commands directly and simply as well as via remote access. In today’s …
“Cloud is Everywhere.” Yes, if you are reading this article, you are using cloud services directly or indirectly. In other words, cloud computing services are crucial to everyone’s daily lives. In fact, a number of titans of the digital industry …
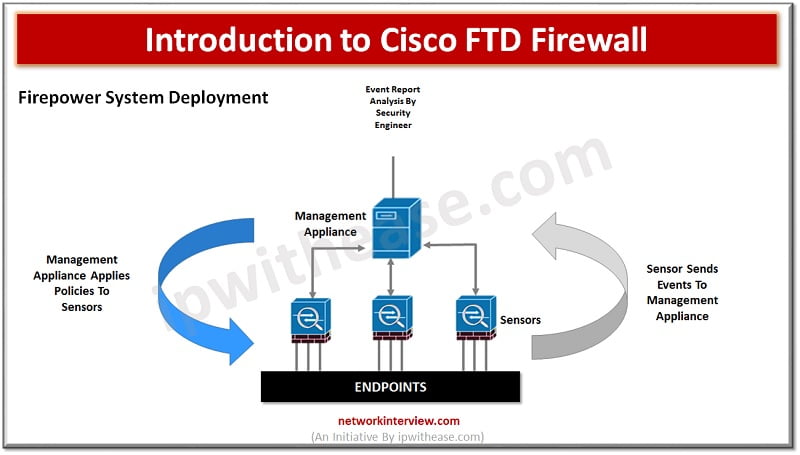
In the evaluation of next generation firewalls (NGFW), the next leap made by Cisco FTD is (Unified Firepower threat defence) software which includes not just NGFW but also Next generation Intrusion prevention systems (NGIP), Advanced Malware protection (AMP) and many …
With the increasing popularity of mobile devices, businesses have been looking for ways to engage their customers more effectively. One of the solutions they have come up with is progressive web apps (PWAs). In this post, we will discuss what …
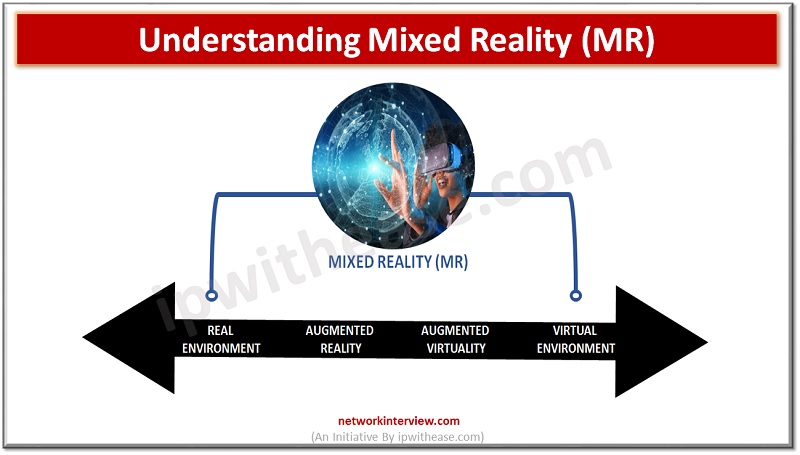
Mixed reality (MR) is a technology that has been gaining traction in recent years and is quickly becoming a powerful tool in various industries. In this blog article, we’ll take an in-depth look at what MR is, the different types …
Are you wondering what all the buzz around Virtual Reality (VR) is about? VR is rapidly becoming a major part of our lives, from gaming to entertainment to education. In this article, we will explore the basics of virtual reality, …
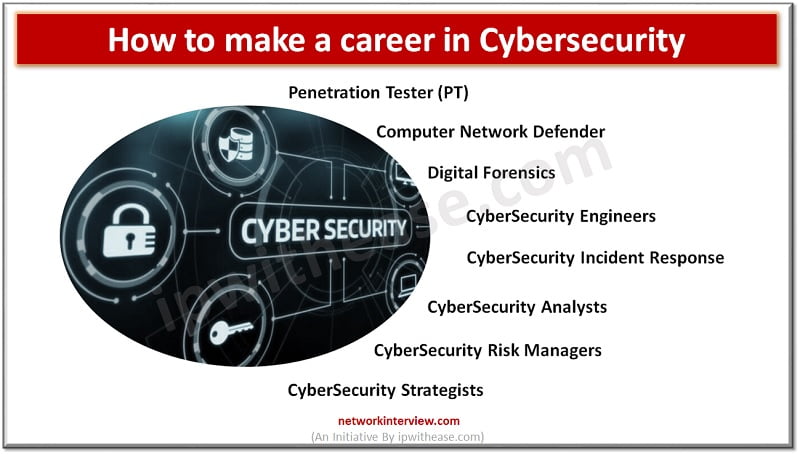
Career in Cybersecurity In this digital world, data is everywhere. This ensures that there are ample opportunities for people who have a passion for ethical hacking, known as “ethical hackers” to find jobs with companies that need their services. A …
Securing incoming and outgoing traffic while keeping track of each link that staff members click might be difficult. Hackers have recently started to pay attention to DNS since any faults could serve as a route for them to exploit vulnerabilities …
Nowadays, websites enable you to connect with people around the world, promote businesses, raise awareness, develop a brand, process payments from clients, and much more. For these reasons, it is important to have a website of your own. In this …
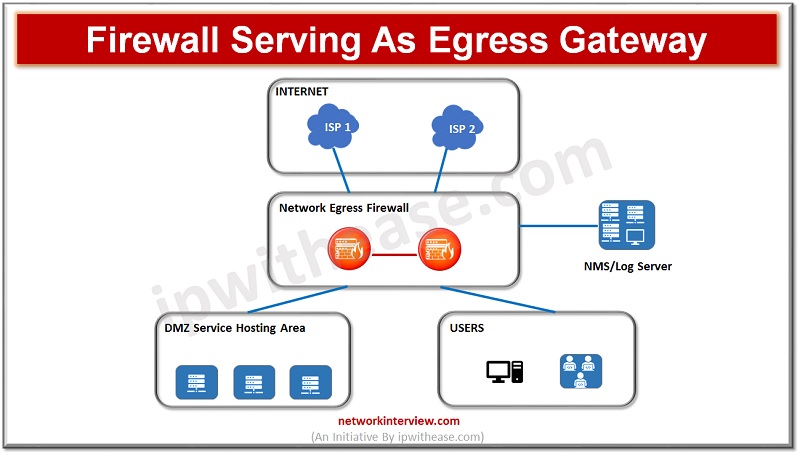
(Diagram depicting firewall acting as Egress Gateway) As enterprises are moving onto cloud their critical business applications, infrastructure services and use of hybrid clouds have evolved, secure networking is the demand of time along with performance and scalability of networks …
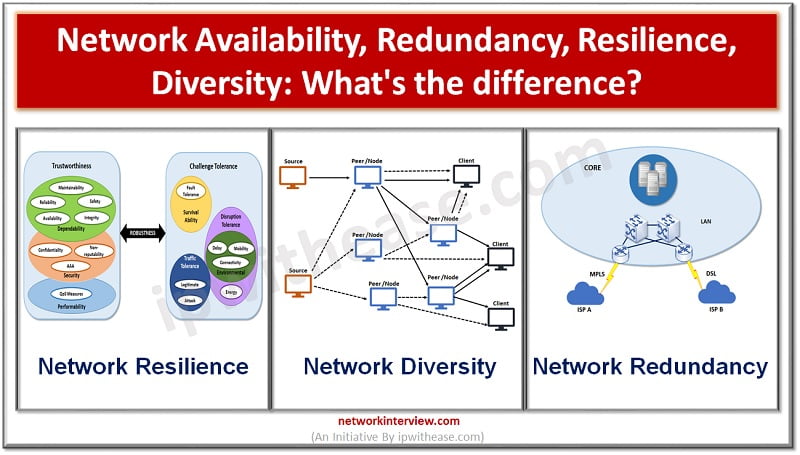
As critical organization infrastructures are moving onto cloud and relying more on Internet networking services it is essential for networks to be resilient having ability to provide and maintain an acceptable level of service in the event of faults and …
Today, engineering graduates dream of getting a job at a leading Software Development or Information Technology company. But software engineers are not only needed in technical companies but there are also good career opportunities in other firms. One of them …
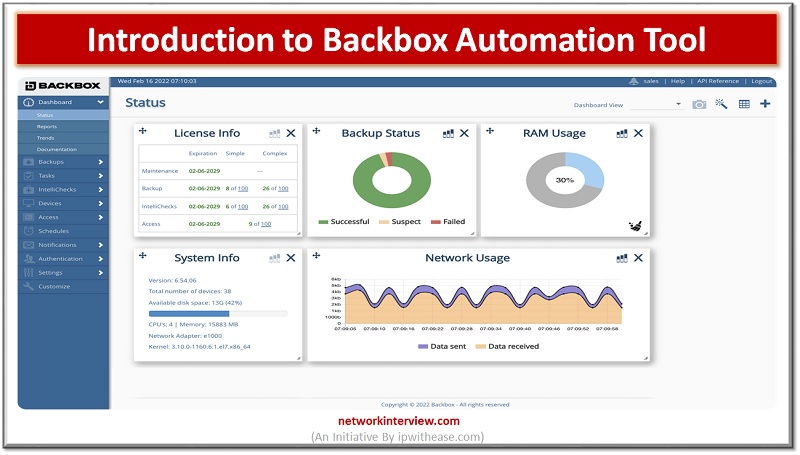
Are you looking to boost your productivity and efficiency as an IT administrator? If so, you’ll love the BackBox Automation Tool. This tool will help streamline your day-to-day operations, increase visibility into your network and accelerate troubleshooting. It’s the perfect …
A huge amount of the work that goes into running a small or medium sized business is related to the management of resources. Resources can include finances, inventoried items, important data and customer information among other things. A company cannot …
If you want to earn a certificate in cloud computing, there’s no doubt that Microsoft is the most popular organisation among others. Azure AZ 500 is one such certified exam that perfectly fits those looking for a career in this …
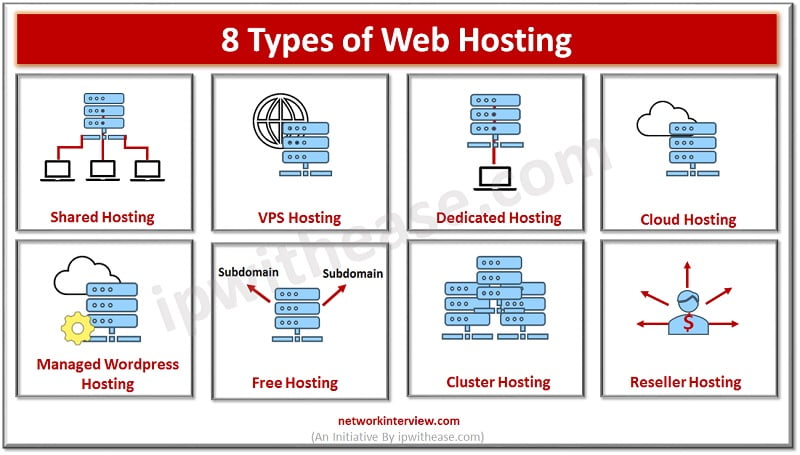
What is Web Hosting? Web hosting services let organizations and persons publish on the Internet or Internet page and plays a critical role in online presence. These websites are stored on systems hosted over the web or Internet. There are …
Why Time Tracking Software? Businesses around the world work hard to improve their management skills and stay competitive in a business world that is increasingly evolving. Presently, technology is by far the most utilized in the world of business. Various …
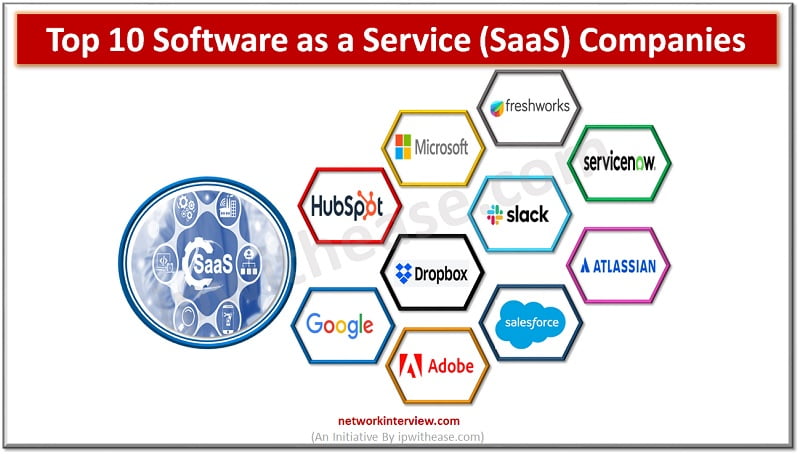
Software as a Service (SaaS) is an umbrella term for cloud-based services delivered to customers over the internet. The software operates on a subscription model, helping businesses reduce capital expenditure and operational expenses by shifting from upfront payments for software …
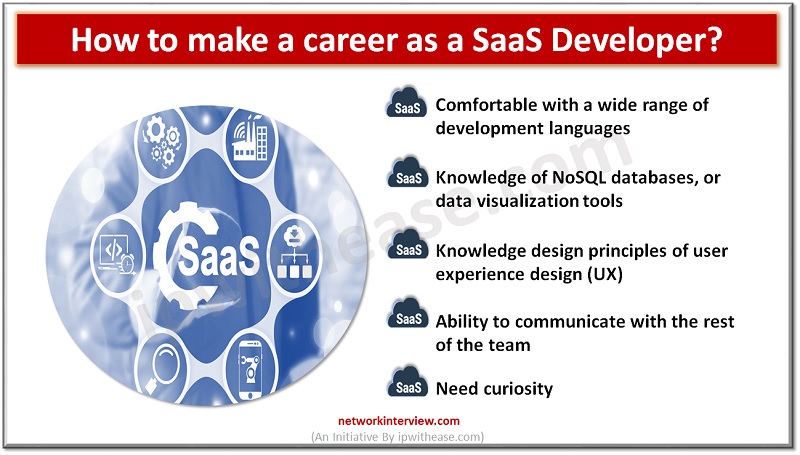
Software as a service (SaaS) is a type of software deployment model that delivers software services to users over the internet. The SaaS model enables third-party vendors to develop and host software applications so they can be accessed by consumers …
Search engine optimization is a field that’s growing more important every day. With the prevalence of search engines like Google, Bing and Yahoo rising, SEO has become an essential practice for any website hoping to attract visitors. Unfortunately, there are …
How do you create a strong resume after being fired? A resume is crucial for your job hunt because it provides one or two pages highlighting your qualifications and relevant skills. Employers use resumes to decide who to hire, and …
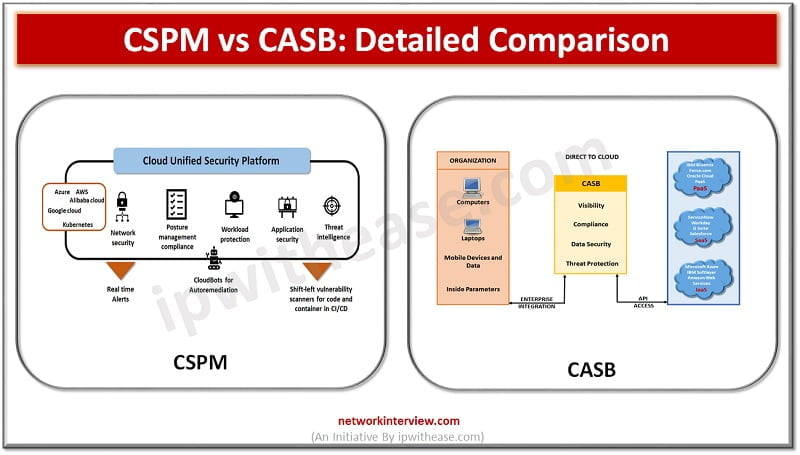
Enterprises are moving their workloads on cloud infrastructure. Gartner forecasts that globally public cloud spending will increase by 18.4% in 2021 to a total of $304.9 billion. As organizations shift IT spend more and more on cloud services, they are …
A common question arises in the mind of IT focals related to Cloud access security broker (CASB) service products such as we already have a web proxy firewall then how is this different? Is CASB a replacement for web proxy/ …
Are you thinking about doing business beyond your domestic market? Making your website accessible to potential customers in foreign markets is key in the international marketing of your product or service. The first thing that springs to mind when considering …
Human mind is built such that it connects to videos on an emotional level much more than any other content type. MiniTool MovieMaker is an easy-to-use free video editing software, that lets users create an amazing movie with their own …
Ever-Emerging New Technologies New technology trends arise every day, but not all of them remain relevant. The same goes for the cloud computing industry. There are some technologies that have solid potential while others will disappear sooner than later. Today, …
Virtual Private Network is referred to as VPN. Your internet traffic is encrypted by VPN software, which also uses a secure connection to deliver your data to a remote server. The info then makes its way to the internet from …
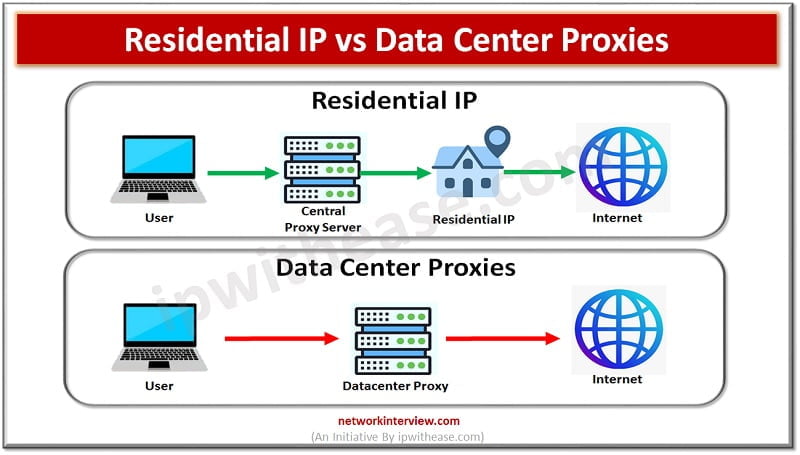
Today, a lot of people use proxy servers to access their accounts, so they may alter their IP addresses and stay out of trouble. The same cannot be said for all IP addresses. There are two types of IP proxies …
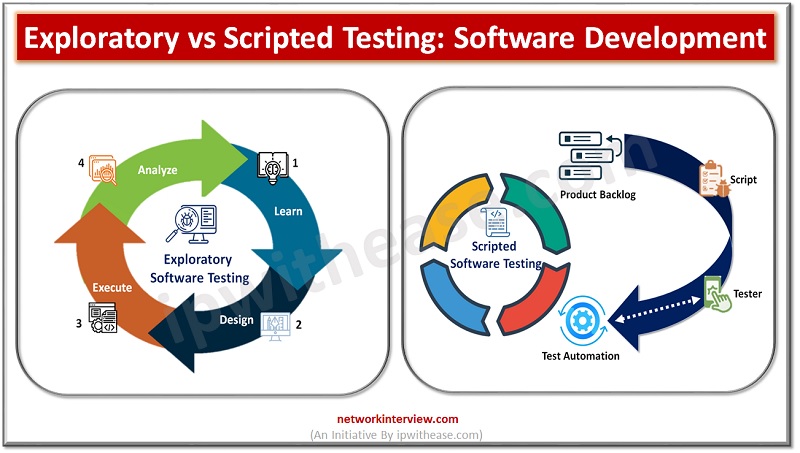
Software testing is a critical component of the software development process. When it comes to software testing, there are two main types: exploratory and scripted testing. Both testing methods have their merits and can be used in different scenarios depending …
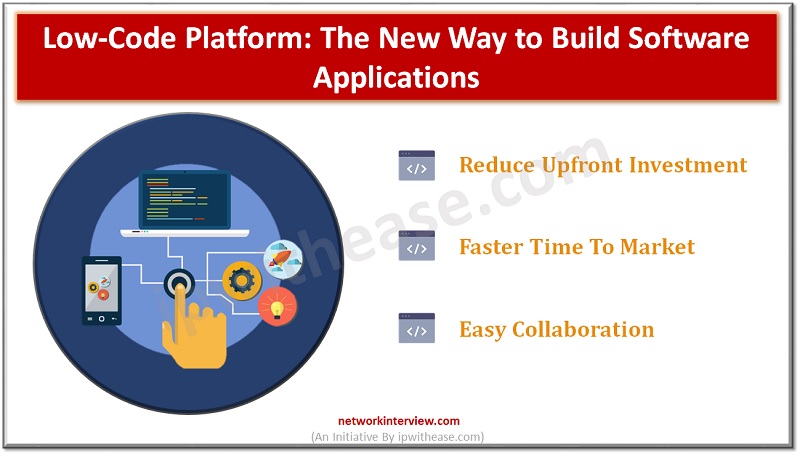
Introduction to Low-code Low-code software is great for users who want to perform complicated tasks quickly and efficiently. In this blog post, you will learn about ten best low-code platforms that you can use for your next project. These solutions …
No-code app builders are a great option for teams that want to rapidly prototype or build software apps without needing to learn code first. They’re also an excellent choice for project teams who need to build and launch new apps …
Data is the key for any Business and its unavailability will be a big disaster. The recovery of data that has been lost, accidentally deleted, corrupted, or inaccessible is referred to as data recovery. In enterprise IT, data recovery refers …
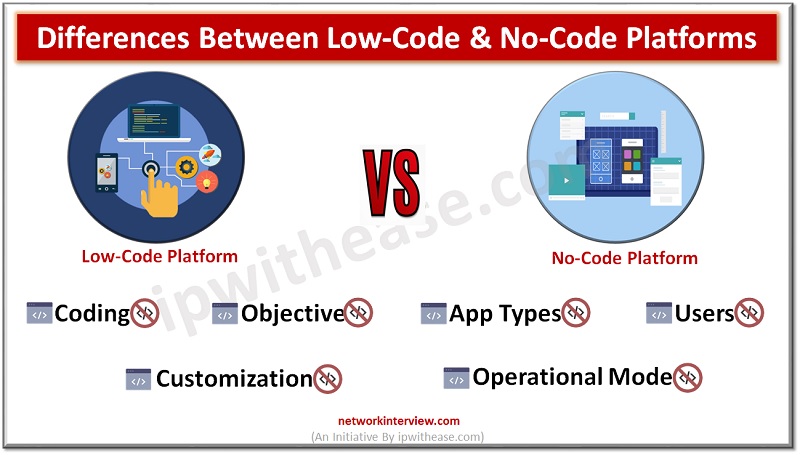
Low-code vs No-code No-code and low-code software are both ways of building apps with limited coding experience. But they each have their own advantages and disadvantages. Choosing the right one for your team and project can help you create an …
In today’s digital world, businesses need software applications to keep pace with their changing needs and requirements. Businesses now look for more efficient ways to build and deploy these applications, without compromising on the quality or functionality. To meet this …