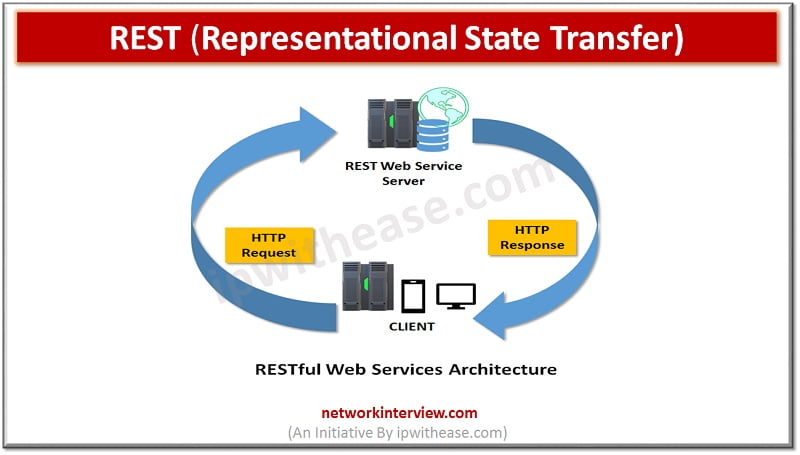
Services are self-contained unit of software which performs specific task. Various architectural styles exist which are created to guide the design and development of the architecture for World Wide Web. REST is one of them which is a software architectural …
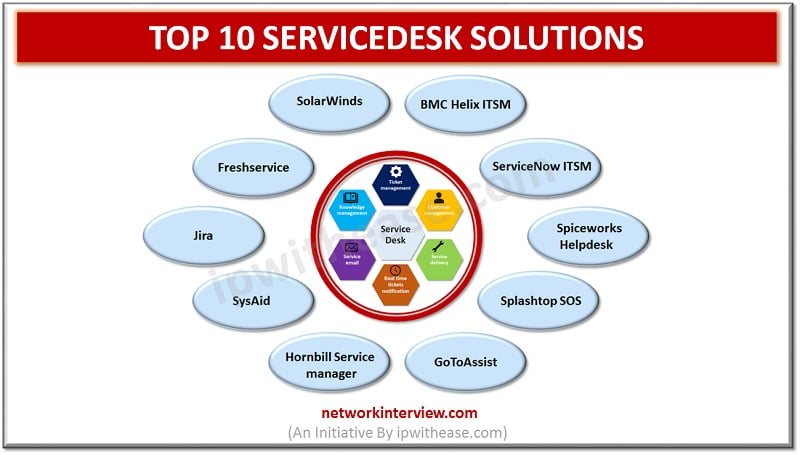
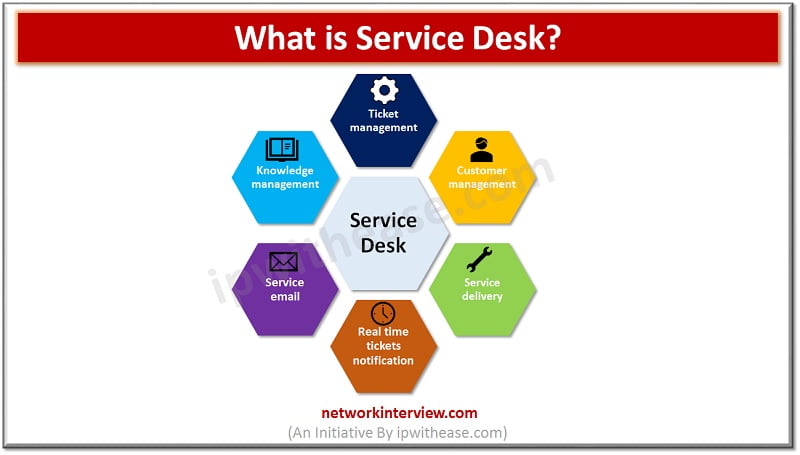
ServiceDesk softwares are designed to provide ticketing platform for internal IT Service management. Service desks are single point of contact (SPOC) within a company to support employees to receive help from IT department or an outsourced agency on submission of …
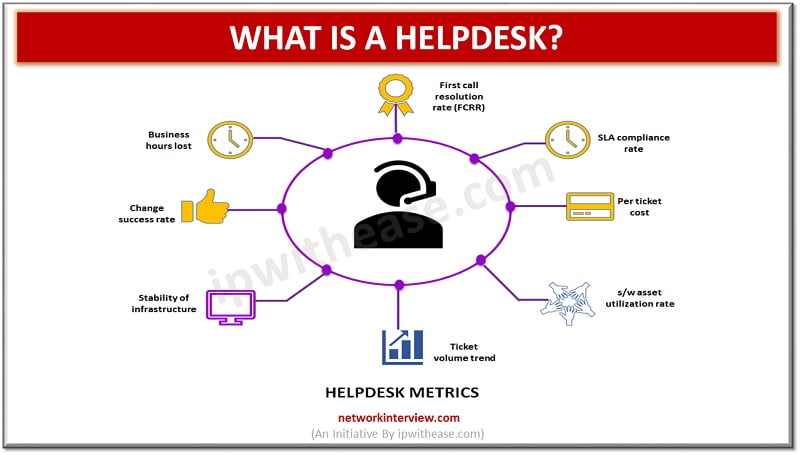
Introduction to Helpdesk Software Helpdesk software are designed to provide customers information and support on company’s product and services. Customer can inquire or submit requests for information or support via multiple communication channels be it email, mobile, phone, social media …
Along with digitization there comes the need of efficient services provisioning for end users. A centralized information center which facilitates customer or end user with information and support related to company’s products and services is crucial for the businesses. Helpdesk …
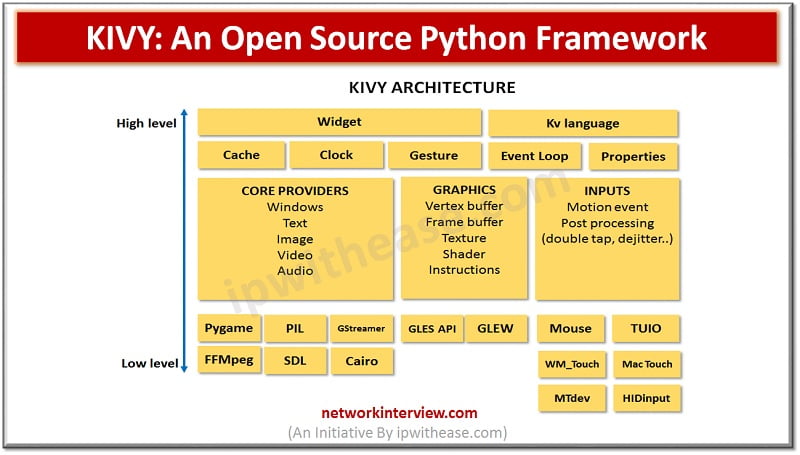
There are several open source and GUI based interface development programs or applications are available in market today. Developers are mostly working on mobile or web applications. These applications or programs help to quickly develop mobile applications and multi touch …
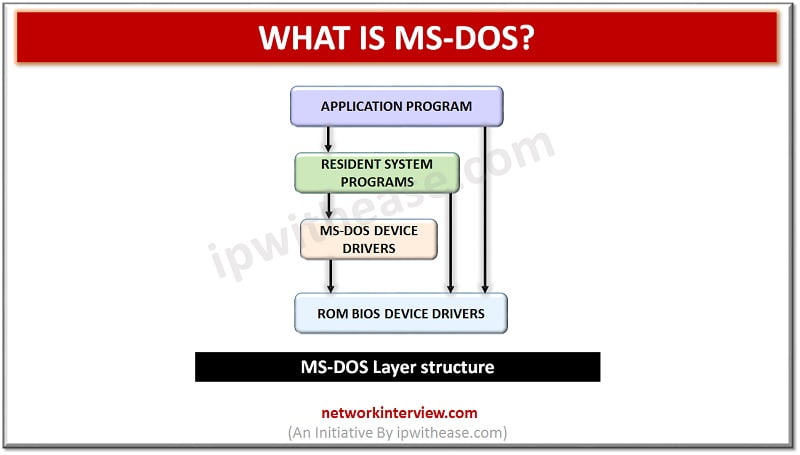
Introduction to MS-DOS An Operating System is a set of programs which controls and coordinates the use of computer hardware among various application programs. It provides an environment to user to execute a command or programs. MS DOS was the …
Introduction: Service Management Managing user expectations and addressing user concerns in real world is the top priority of businesses. Service Desk is an integral part of any organization’s operations. It is relevant for all businesses small, medium, or big and …
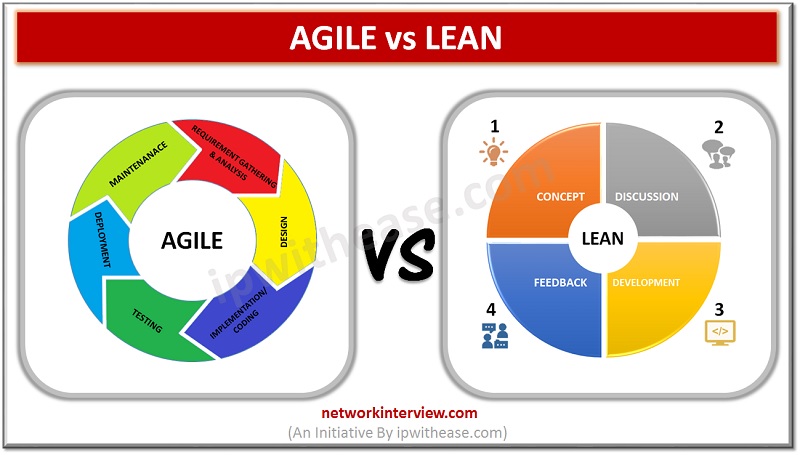
Introduction to Agile & Lean Methodologies Are you planning to develop a carrier in project management or software development? Then you must be aware of the two most popular project management methodologies Lean and Agile. These two methodologies are mostly …
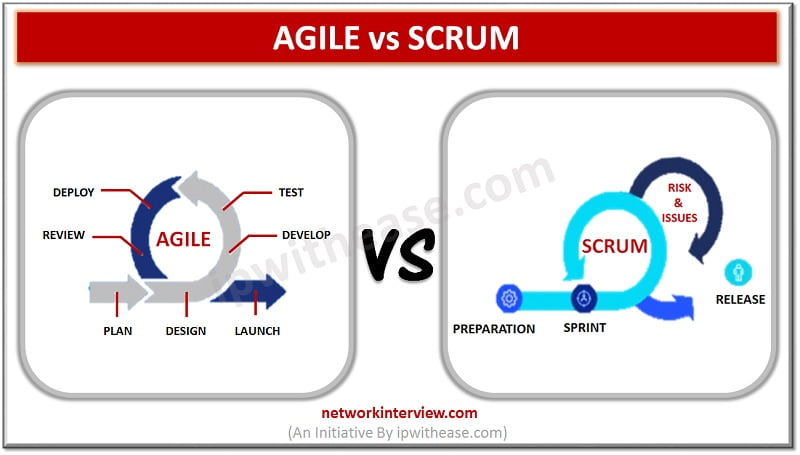
Introduction to Agile & Scrum Methodologies If this the first time you’re learning about the project management and Software Development Life Cycle (SDLC), then it will be confusing for you to keep up with the different terminologies. And especially the …
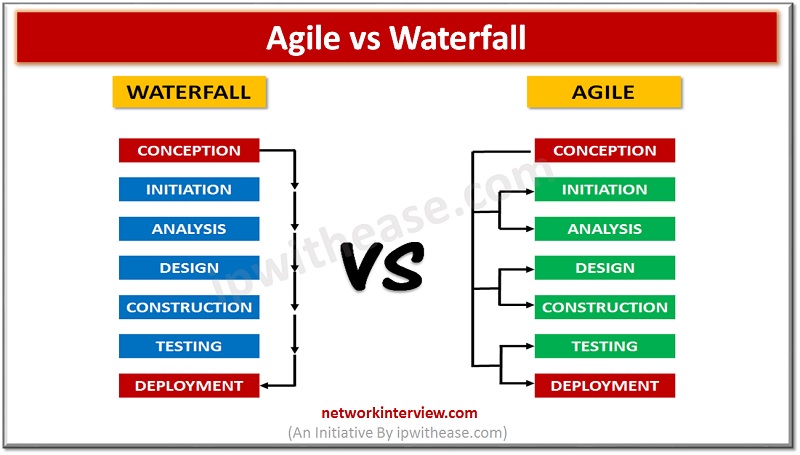
Introduction to Agile & Waterfall Model As a rookie individual developer, you must be confused when you first heard the words Agile and Waterfall. Both of them refer to the software development methodologies which numerous benefits for the final success …
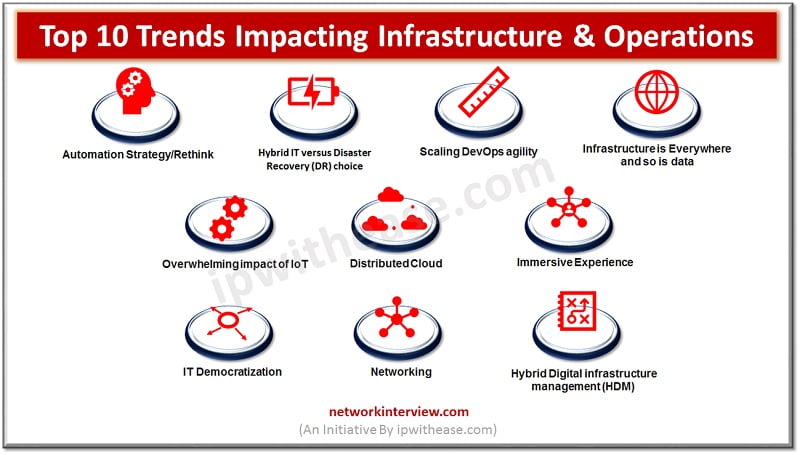
Introduction to Infrastructure & Operations Organizations need to support digital infrastructures as infrastructure trends now focusing on new technologies such as Artificial intelligence (AI), Edge computing to support rapidly growing IT infrastructure and support agile business needs parallelly. In this …
Automation testing tools are evolving rapidly as the digitization is growing and organizations needs applications which are easily deployable, agile in nature, can address business requirements in a quick manner, solutions can be developed and tested in a more faster …
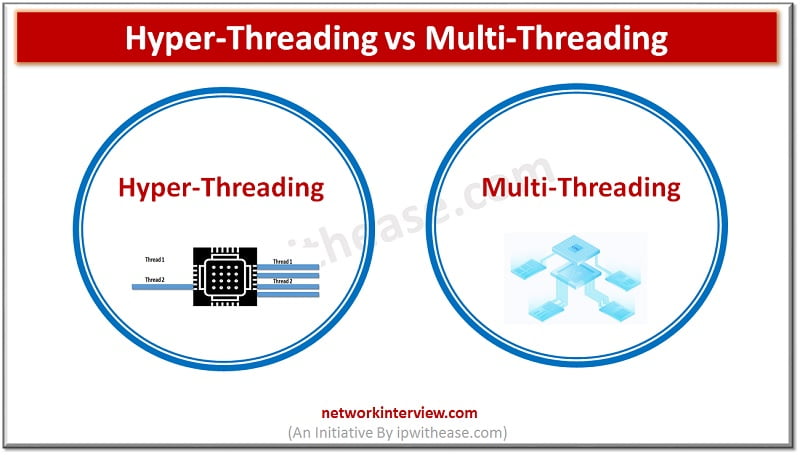
Introduction to Processing Techniques Most CPU manufacturers try to achieve high CPU performance by increasing clock speed and cache sizes but that still does not let full potential utilization of CPU power. To make more efficient use of CPU power, …
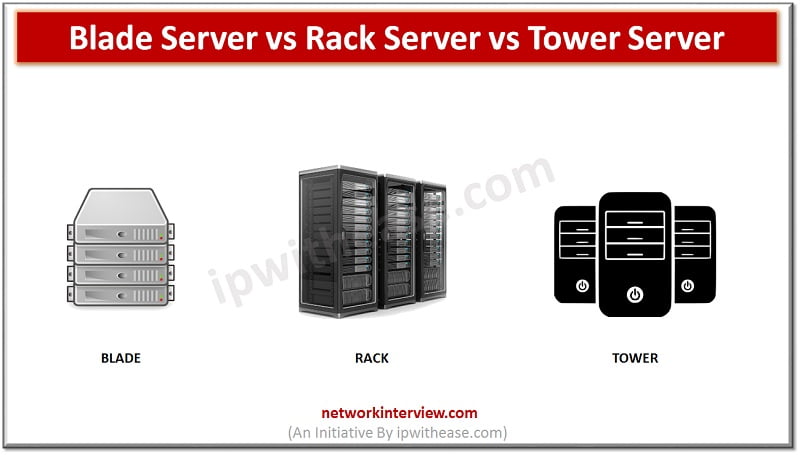
Introduction Servers comes in different shapes, sizes, and configurations. Organizations take decisions about which servers to deploy depending on availability of data center space, performance, budget, and scalability. In this article we will explore more about various types of servers …
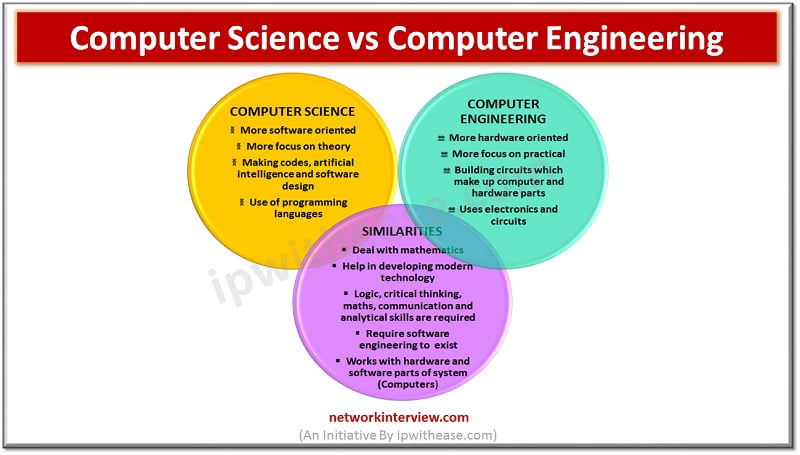
Choosing the right career: Are you confused? Education institutes use near to similar names for the courses which makes it quite confusing for students. Computer science and computer engineering are two such terms. We don’t know do they mean same? …
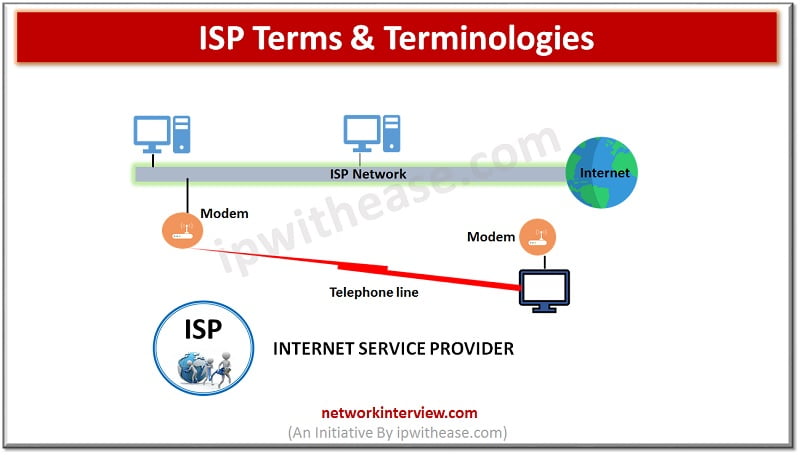
ISP stands for Internet service provider they offer a wide variety of Internet services related to browsing, Email services, faxing capability, audio and video communications and hosting services etc. Let’s look more in detail about Internet service provider (ISP) and …
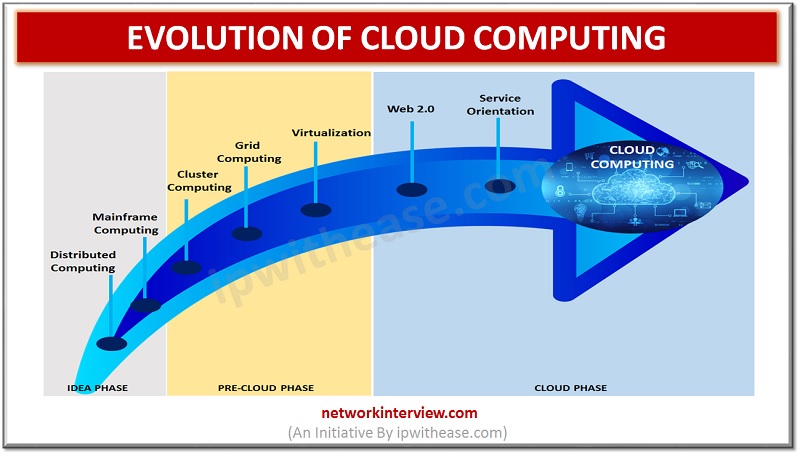
Introduction to Evolution of Cloud Computing Cloud computing is playing an important role in everyone’s life. We cannot imagine a world without Cloud Computing techniques to handle Big Data. But we didn’t reach this level in few years. The evolution …
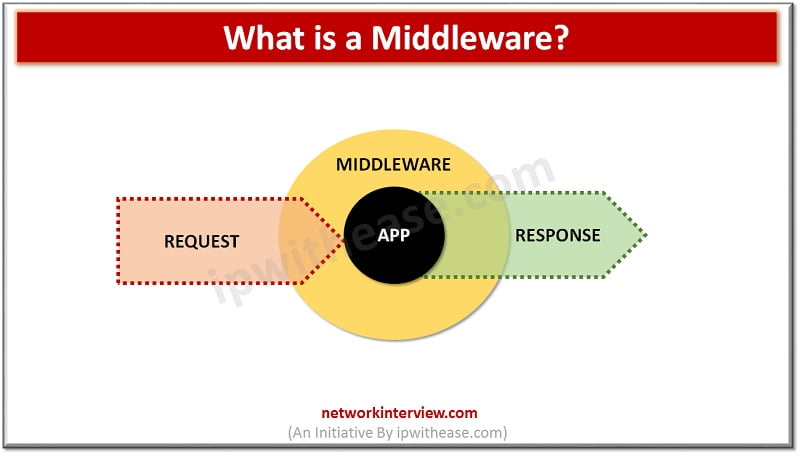
If you are a person interested in Web services and cloud-based networking, then you must have come across the word Middleware. Middleware is adapted to various forms and plays important role in distributed applications. In this article, you will understand …
Introduction to Tomcat Web Server Are you looking for the best Web or Application server software for your website? Then Tomcat is the best choice for you but you cannot select a Web server without knowing about it. Tomcat web …
Introduction to Apache Server If you want to host a website or Application online you will look for a hosting service provider or a web server. But have you ever thought about how this Web server works? There are many …
Are you a small-scale software developer? Want to test run your app or site but you don’t have a server? Then Web Server for Chrome is the best choice for you. In this article, you will get to know about …
The rapid development of technologies and new inventions has affected the environment very much. And this led to the start of the Green Revolution in all the industries including the Information Technology and Tech fields. Now the big companies like …
Introduction to Pylint: Python Programming Pylint is defined as a Python static code tool for analysis purposes. Pylint has the ability to scan for programming errors, implement coding standards, identify code violation and provide refactoring proposals. Pylint is fully customizable …
In the late ’90s and early 2000s, it was predicted that the computer era would come to end. But to our surprise, the technology has developed further and taken various forms. One of them is the mainframe computer, shortly called …
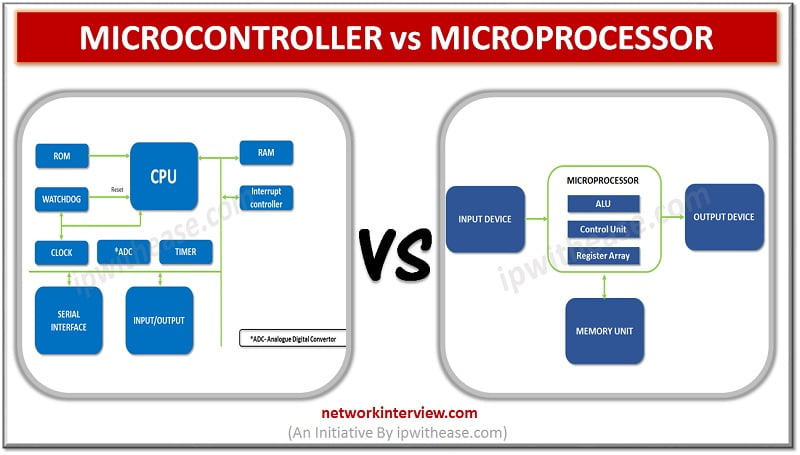
Microcontroller and Microprocessor both are integral part of computers and other components such as automobiles, telephones, appliances etc. In this article, we will understand the differences between the two and about its usage. Microcontroller Microcontroller’s history is dated back to …
Introduction In this article, we will learn about some terminologies associated with computers. There categorization and classification are based on their size and data handling capabilities. Let’s understand the difference between Microcomputer and Supercomputer. What is a Microcomputer? Another name …
Different types of computers are in use today. There classification is based on their functionality, size, speed, and cost. Based on size, speed and functionality computers are classified into four categories. In this article, we will take a look at …
Mainframe dominates 87% of credit card transactions and 71% of fortune 500 companies operations are run through Mainframes. Minicomputers changed the digital landscape and were designed for direct interaction between systems and its users. We would learn today about Mainframe …
A common query which comes to mind of engineering students is: “What is the difference between a Software Engineer & a Computer Engineer?” Both of them relate to Computer and uses engineering ideas and concepts that is why it is …
What is the difference? What is the difference between Software Development and Web development? It is the computer science bachelor degree holder’s question. Both of them are based on coding but they do have some differences, today in this article …
In this article, we will understand about some terminologies associated with computers. The categorization and classification is based on their size and data handling capabilities. Let’s realise the difference between Microcomputer and Minicomputer. Microcomputer Microcomputers came into existence and become …
Introduction In recent years many development and career opportunities have been introduced in the IT and Computer world. It is even hard for a computer or IT-based companies to hire and select the candidate with an apposite skill set for …
Introduction to Software Development No one can stop technological advancements. We have come across different phases of development; each of them taught and amazed us with different things. Like that the leading IT industry has also undergone major developments and …
Introduction In the past five years, cloud computing has become a new trend in the IT Industry. Many IT companies feel that adopting a cloud-based interface can lower their operating costs and maximize efficiency. Interestingly, this revolution has created many …
Introduction Everyone in the world knows that the IT career has a promising future. To begin a career in IT Security, you can join networking courses that equip you with the skills to design, install, configure, maintain, and troubleshoot computer networks. …
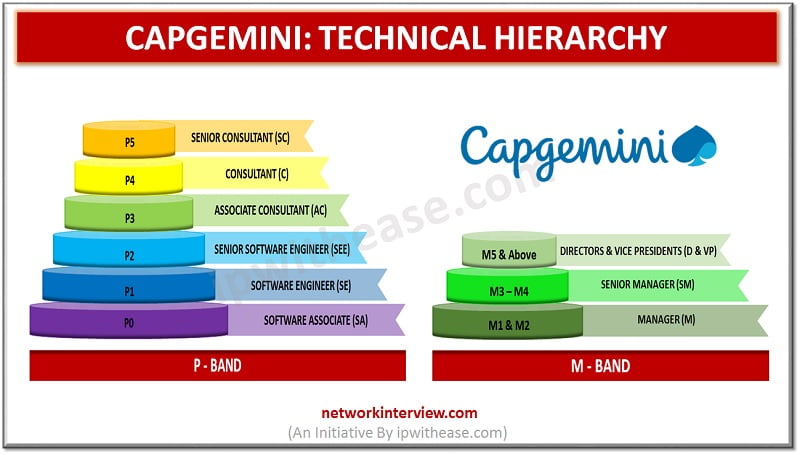
Are you wondering how the Technical Hierarchy in CAPGEMINI is? Do you want to know more about the promotions and higher positions? You are in the right place. It is common to be curious about the organization’s hierarchy where you …
Introduction to IBM 360 Up to early 1960 IBM systems were incompatible – there were inter-operability issues and systems were used different peripherals like tapes, disk drives etc. All these factors were increasing the design and production costs for both …
Introduction to NetBrain Have you heard about NetBrain? It is one of the best Network Operating tools available in the market. If you are a new IT organization then, Network Automation may feel new for you. Today in this article, …
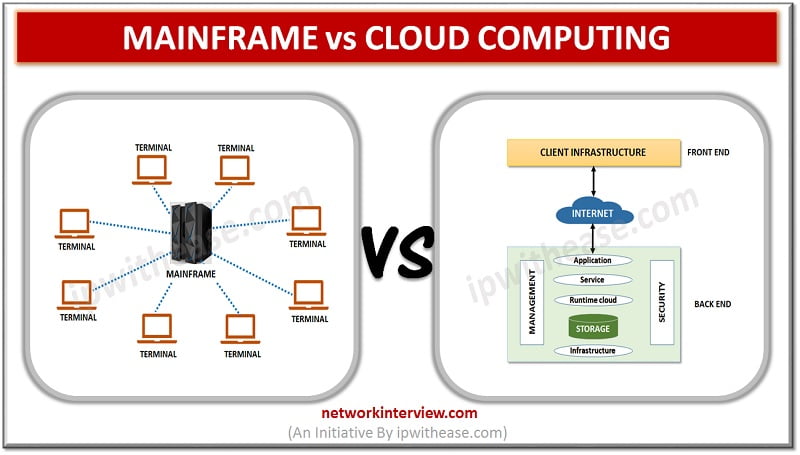
Introduction Centralized architecture with high computing power and centralization of computing resources vs distributed computing architecture are two main directions in which IT technology has moved or progressed with the passing time. Today, we look at two technologies that governed …
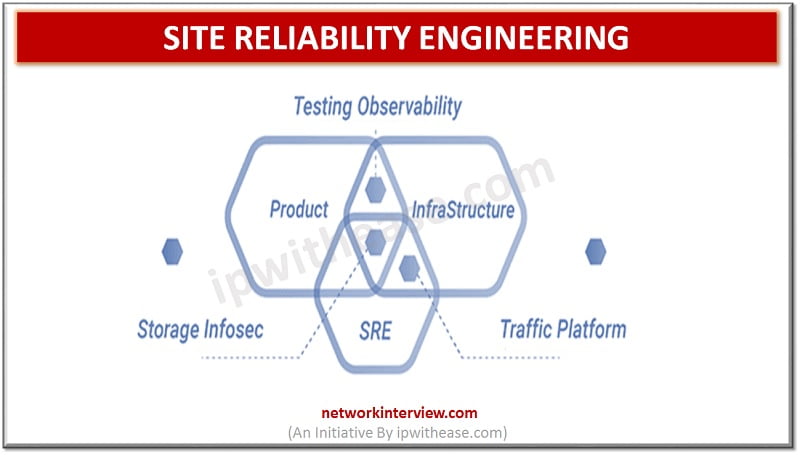
Introduction to Site Reliability Engineering Until recently, there were only a few engineering career paths, but everything is changed now. There are many fields and specializations. The numerous websites on the internet and array of cloud platforms recently lead to …
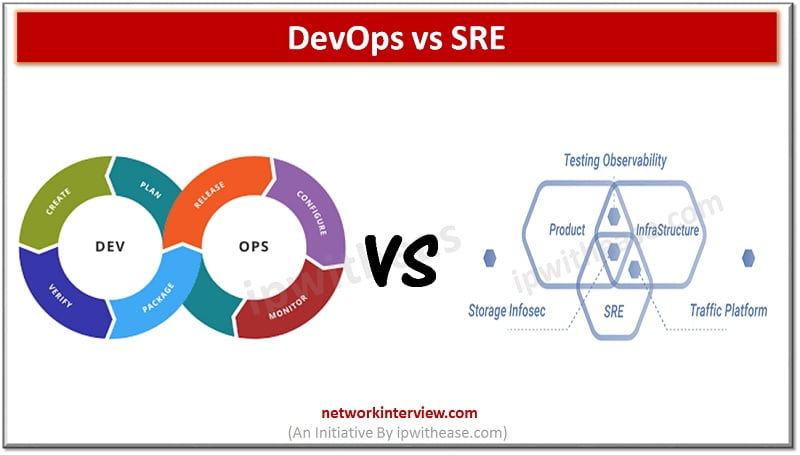
Introduction: DevOps vs SRE After Google introduced Site Reliability Engineer into the software development process, the whole IT industry was confused and had this question “What is the difference between the DevOps and SRE?” In short, there is not much …
When we talk about IT Setups and IT infrastructure we come across some terms and we wonder what the difference between them could be. Today we look at two common terminologies: Data center and Disaster Recovery Center, we come across …
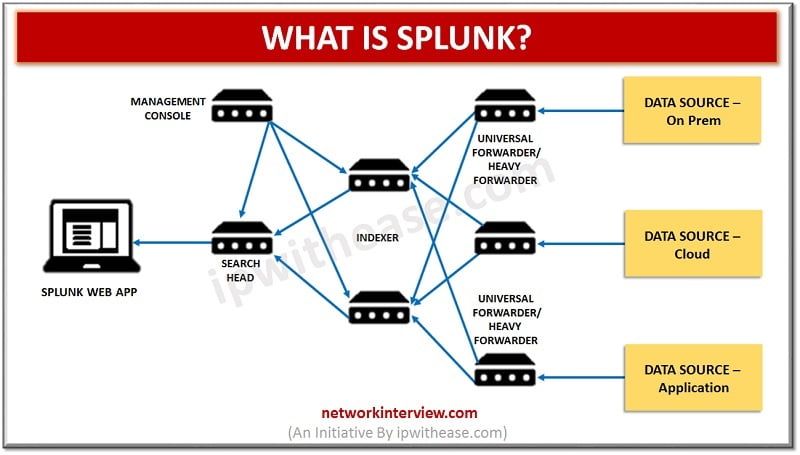
Introduction to Splunk “Splunk” is the product created by an American multinational company based in California that creates software platforms for searching, monitoring, and analyzing data via a Web-style interface. With the general term “Splunk”, it is the “Data to …
Introduction to Cisco Network Assistant (CNA) Cisco Network Assistant/ CNA is an application designed for Windows PC in order to manage networks. It is designed to be compatible with wired and wireless networks and Small-Medium sized organizations. Cisco Network Assistant …
Introduction to CASB Solutions CASB (Cloud Access Security Broker) is an intermediary between cloud users and cloud applications. CASB solution is a software/hardware application that is located inside the network or works as a cloud-native application. Cloud access security broker …