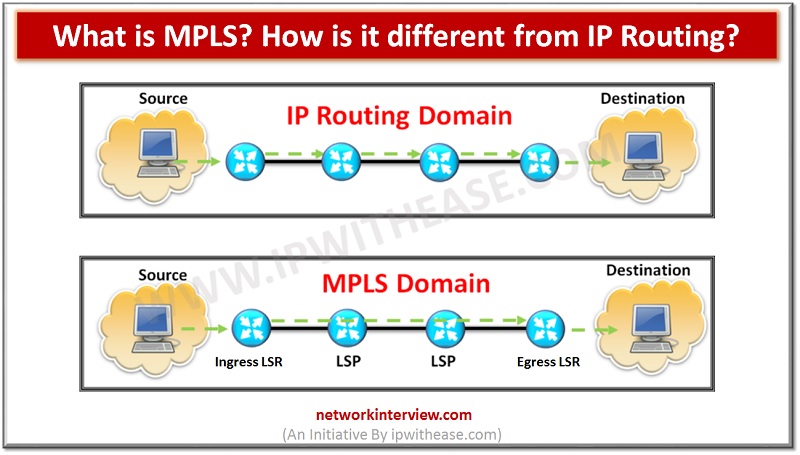
Introduction to MPLS MPLS i.e. Multi Protocol Label Switching (MPLS). It is a technique that is used for the routing of network packets. It is called a Multiprotocol as it supports multiple protocols like Internet Protocol (IP), Asynchronous Transport Mode …
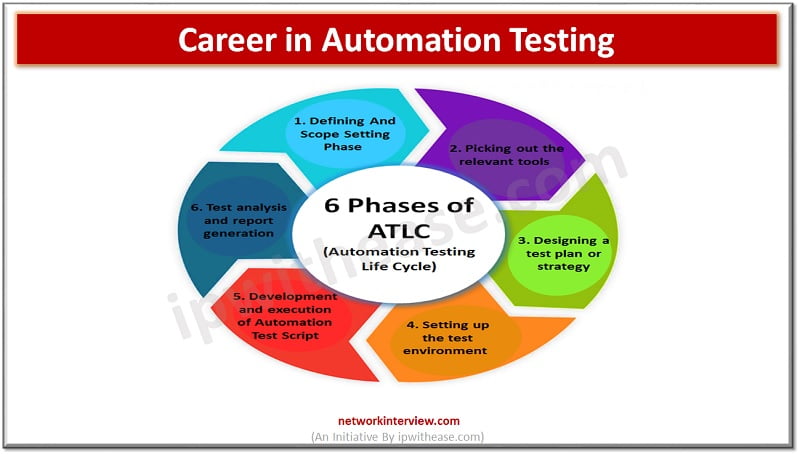
In today’s world, everything is automatic. Whether it is a tech giant or a small business all of them pursue automation to reduce the cost and increase their efficiency. This has created a massive opportunity for technical persons around the …
In the hosting web sector, there is a lot of confusion regarding the technological differences between cloud hosting and VPS hosting. Most people misinterpret the fundamental distinction between the two due to the lack of understanding of the key distinctions …
Agility and innovation are key ingredients for digital transformation. However, agility requirements are hindered by telco-controlled SD WAN or MPLS networks. Slow moving ISPs and need to deploy expensive custom hardware, telco circuits, and VPNs create roadblocks and stop transformation …
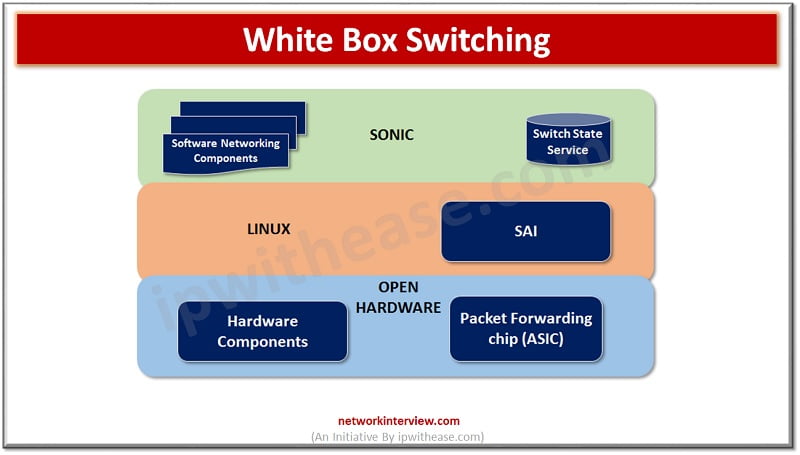
SDN technology detaches dependency on binding both hardware and software. Starting with the SDN network 10 years back, a number of start-ups started to develop open networking systems and white box switches for data centres. In this article we will …
Network switch is the main component of telecommunication networks especially in the case of fiber optics networks. In the traditional switch choice of a specific vendor switch you are bound by software provided by the vendor. The switch market is …
If you’ve invested in a new gaming laptop, chances are that you want to use it as much as possible and spend all your spare time enjoying your favourite games or trying new ones. However, heat is something that your …
Have you ever bought a Samsung Phone which has a different processor than your friends? Yes, the Samsung Mobiles uses two processors for all their models. The mobiles with Exynos processors are sold in Asian and European countries whereas the …
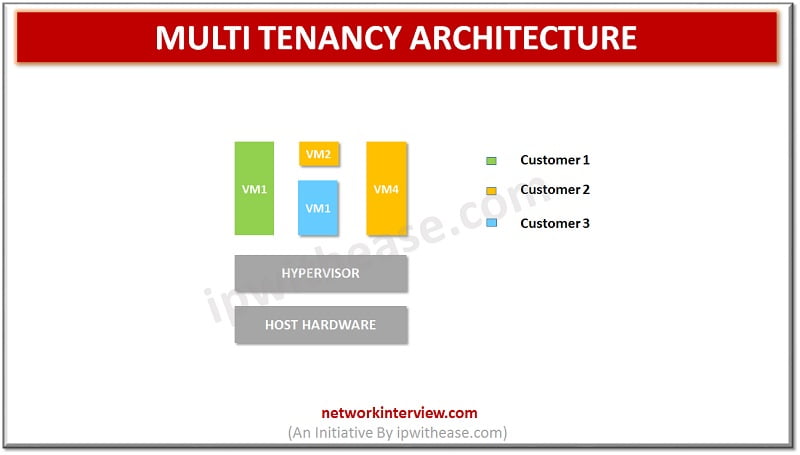
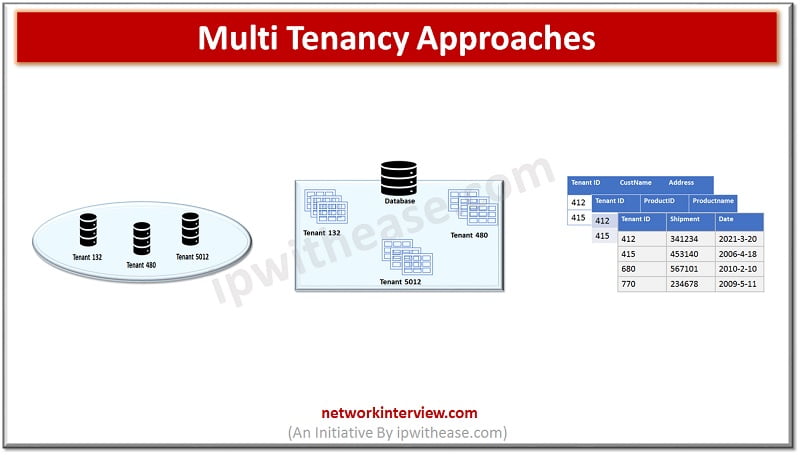
Introduction to Multi Tenancy Advent of cloud computing had brought many new models of delivery and services in Infrastructure services, Application services, Network services and so on. Cloud computing provides a cost-effective way to use computing resources, share applications, share …
In the past few years, video making and editing have gained immense popularity. It’s now easier than ever to shoot impressive videos with your smartphone or a DSLR camera and share them on social media. It has given a platform …
Introduction to Multi Tenancy in Cloud Multi Tenancy offers customers , organizations and consumers which are sharing infrastructure and databases to gain advantages on price and performance front. Service offerings available through cloud involve customers (or ‘tenants’) getting a piece …
Are you dissatisfied with the performance of your internet connection at home? If you have the option of choosing from more than one internet service provider, why not choose the best and the fastest broadband connection. Choosing the best internet …
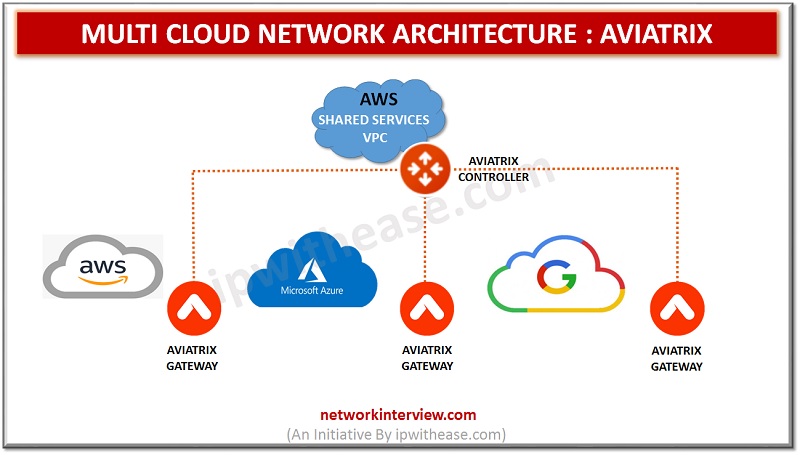
Multi cloud refers to multiple cloud computing and storage services in a single network architecture. Multi Cloud distributes cloud assets, software, applications and more across several cloud environments. Multi cloud network architecture utilizes two or more public clouds as well …
Hey guys, here is another neck-to-neck comparison. Recently Snapdragon and Kirin have announced their new model which has created waves among tech enthusiasts. You can’t decide the winner until they are released, but so far who is the winner? If …
Hybrid Cloud vs Multi Cloud In recent years, with mushroom growth in Cloud technologies, a change has been observed w.r.t where the application Workload and data is hosted. A large number enterprises have started moving their data, applications and related …
When selecting a smartphone or tablet one of the important features to check is the Processor. To be correct they are not processors in the technical circle, it’s called System on a Chip (SOC). The Snapdragon and MediaTek are the …
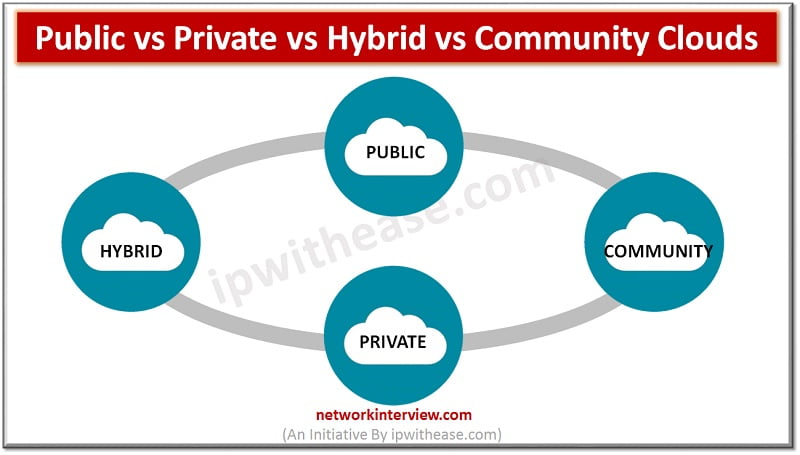
Types of Cloud: All size of businesses receive prominent advantages from cloud computing. When part or all of the computer resources of a company are moved to the cloud, then the decision of most suitable cloud services is also included …
Telco Cloud vs IT Cloud Cloud computing has opened a breath for enterprise and telecom related opportunities to hosting applications and services. While market talk is that somewhere in near future IT Cloud and Telco Cloud will merge to form …
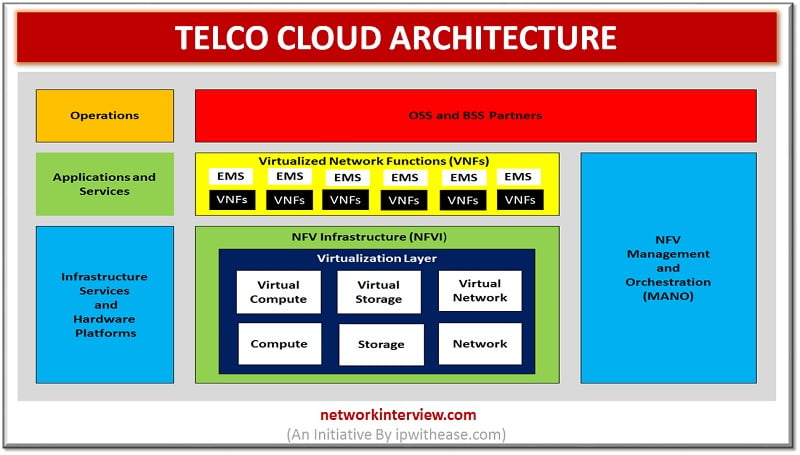
Telco Cloud Architecture Table of Content: Definition of TelcoCloud Definition of Network Function Virtualization (NFV) NFV Architecture Benefits of NFV Application of NFV Conclusion Definition of Telco Cloud Telco cloud represents the Data Center resources which are required to deploy …
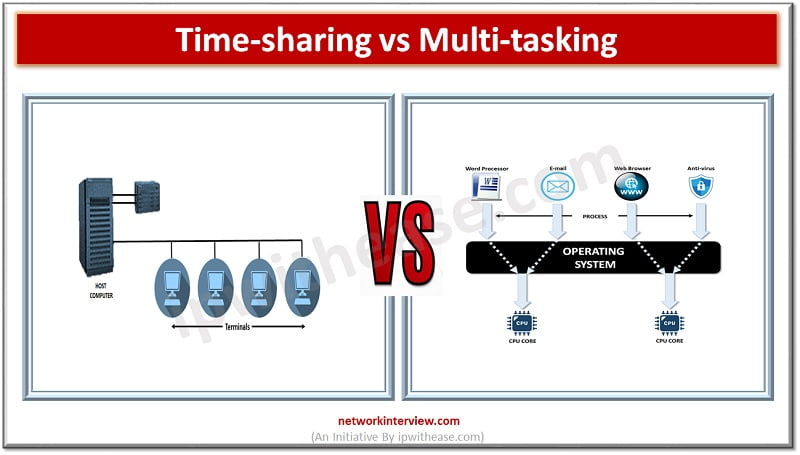
As a modern computer user, you may not know that multi-tasking and time-sharing operating systems are two different things. Though they both are similar and dependent on each other, there are some differences between them. Wait, are you saying they …
Introduction to IT Companies There is no doubt that Software Engineers and IT Consultants are one of the highest-earning personnel in the world. But not all of them are treated as the same. Their pay rate differs based on their …
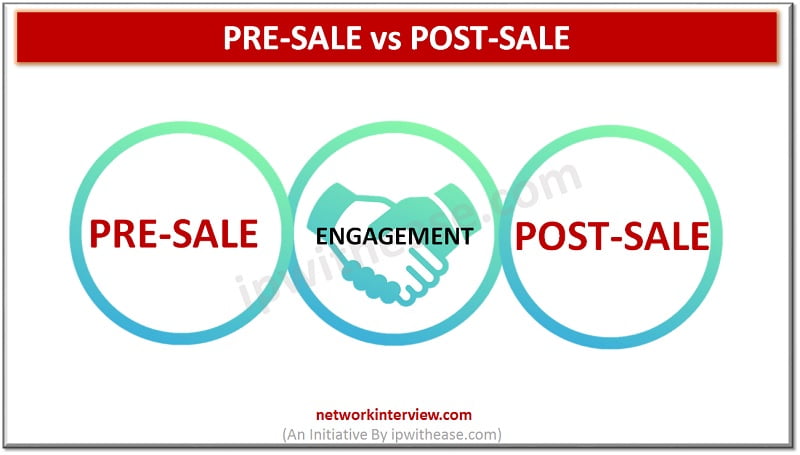
Introduction to Pre-sale & Post-sale Specialization of sales engineers should be in technology and scientifically advanced products. With the help of technical skills, they explain the advantages of the products or services to the potential customers and also tell how …
Nowadays, software engineers have multiple career opportunities after their graduation. This is because of the massive Digitalisation and development of Information Technologies. And these increased opportunities create more confusion in selecting a perfect company for your future. However, over time, …
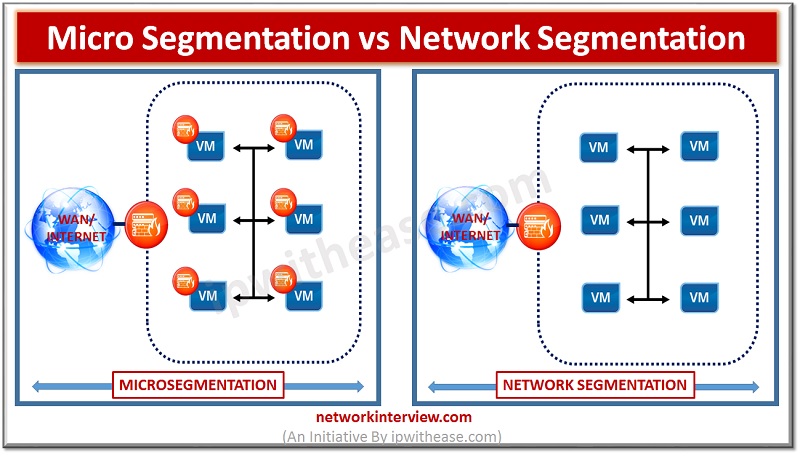
Micro segmentation vs Network Segmentation Over many years, Perimeter security has been considered the key to presenting a robust and secured network ecosystem . This was considered a suitable methodology when the network attacks were not so advanced and North-South …
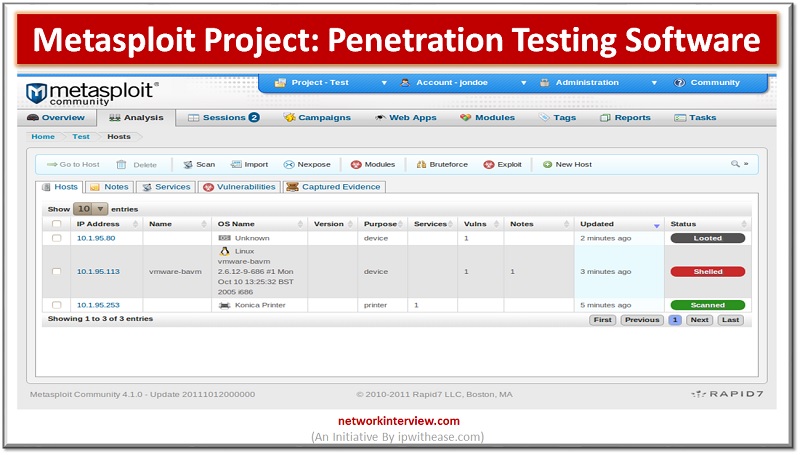
Introduction to Metasploit Project In the worldwide IT security community, we define the Metasploit Project as a computer security project that mainly provides information about security vulnerabilities and helps in penetration testing and development of the IDS Signatures. It is …
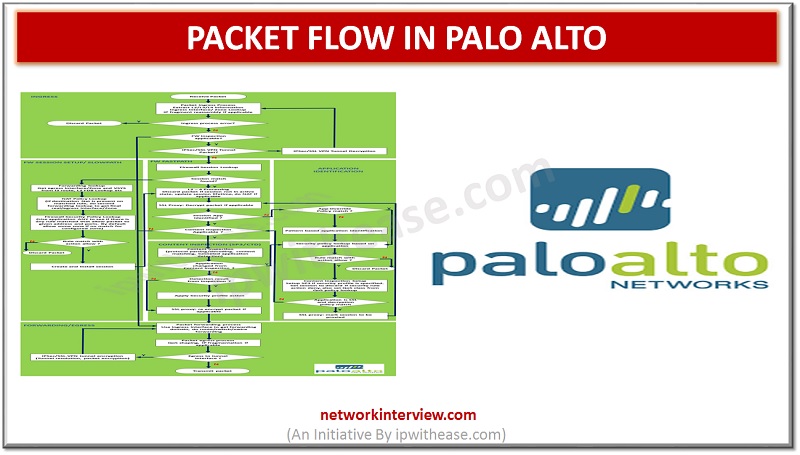
In this article, we will discuss on Packet handling process inside of PAN-OS of Palo Alto firewall. Introduction: Packet Flow in Palo Alto Packet passes through the multiple stages such as ingress and forwarding/egress stages that make packet forwarding decisions on …
Cloud Engineer vs DevOps Engineer Cloud has changed the way how we do Business. Cost savings have led the IT assets, especially compute Infrastructure migration to Cloud. Accompanied by this move, there have been buffet of new roles which have …
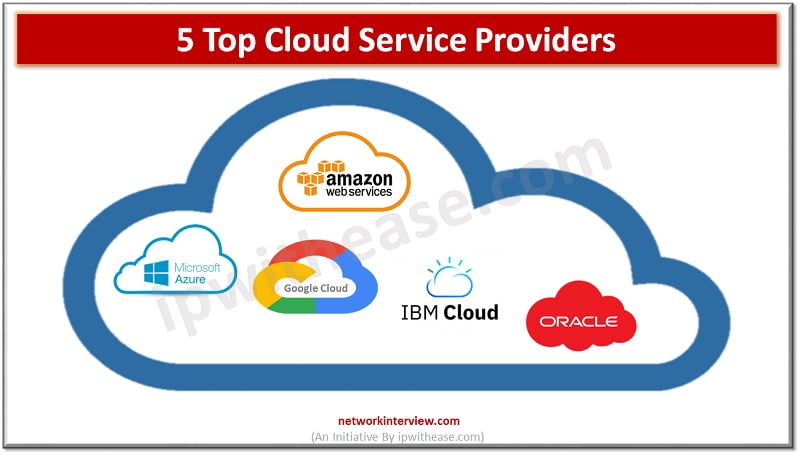
Introduction to Cloud Technology Cloud Technologies has dramatically changed the world in the last decade, the data center has become a private cloud and Container technology has become mainstream, Artificial Intelligence and Cloud Computing are now interlinked industries. Looking back …
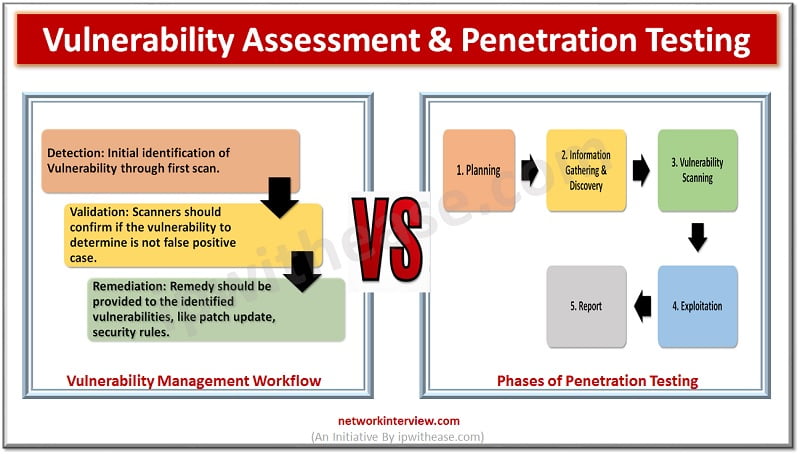
Introduction Vulnerability assessment is the way to identify weakness in the system. Vulnerability itself means “Weakness” and Vulnerability assessment means how to find weakness in a system and create a report accordingly. On the other hand, Penetration testing is used …
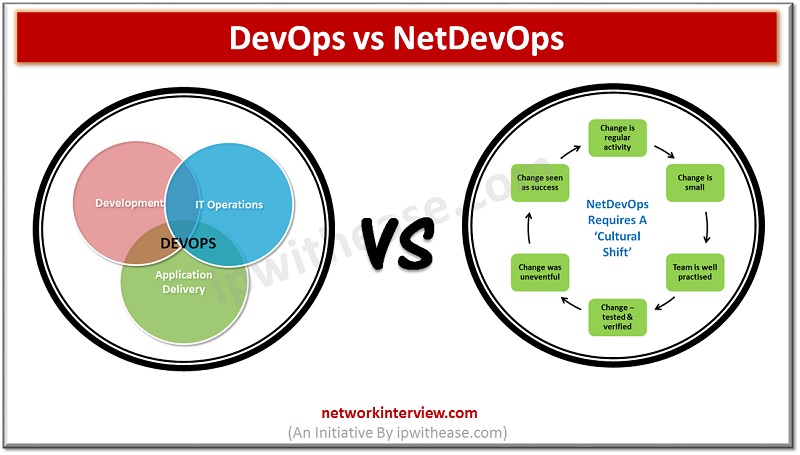
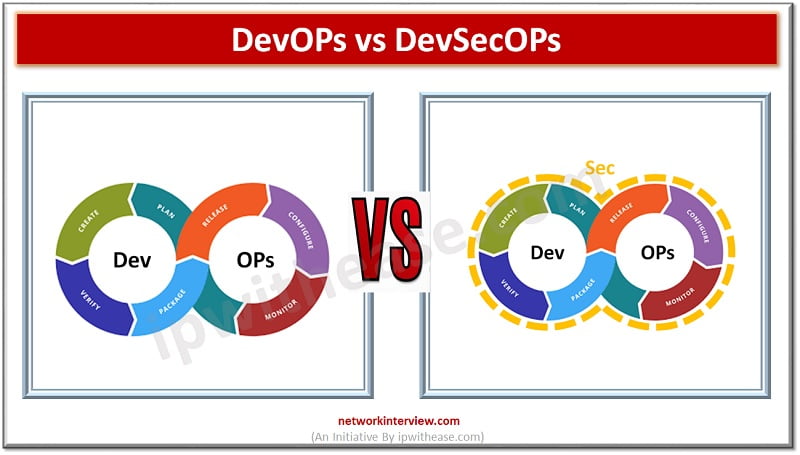
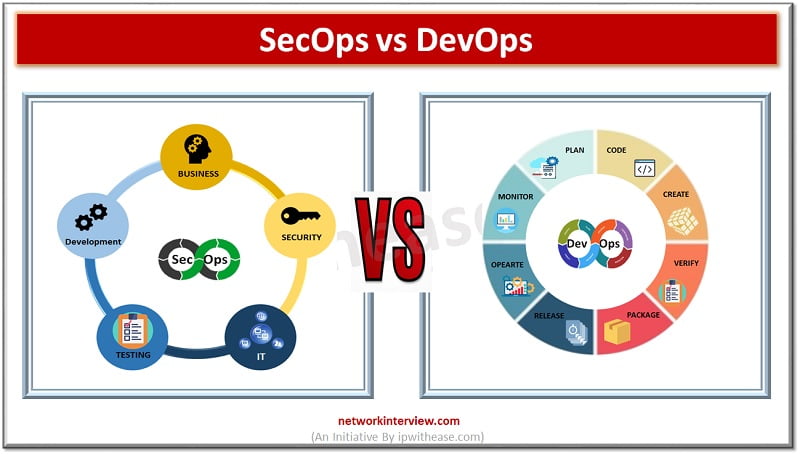
Introduction With the growing advancement in technology there is an increasing need for collaboration and Agility. Software developments require a constant collaboration between programmers and system administrators in the software development process to develop apps which are efficient, secure and …
Software development and operations teams are always striving to establish a consistent environment for development globally. The products are brought from hands of developers to customers however the existence of silos between development, QA and operations teams always create conflicting …
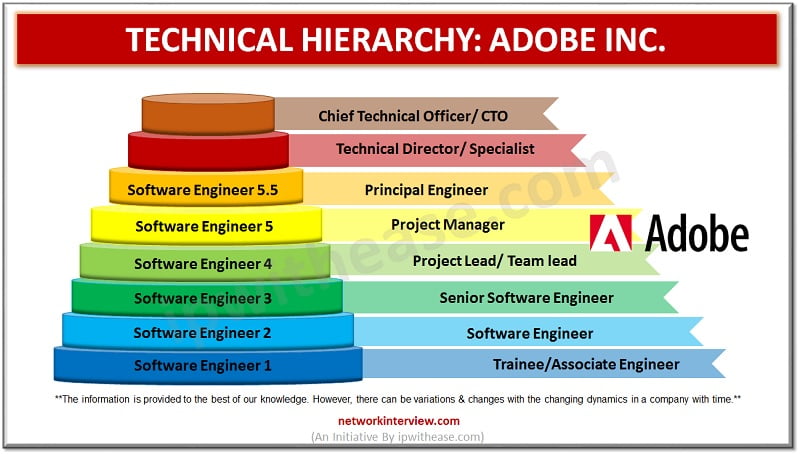
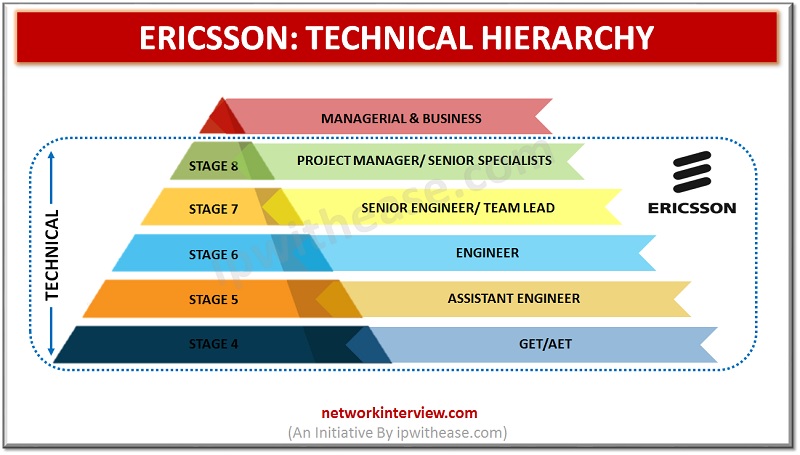
It is important to know about the Hierarchy of the organization. Because the hierarchy level gives you the idea about your future chances and the person who you need to report. It reduces the unwanted hesitation and nervousness within you. …
Infrastructure as a code is one of the greatest changes brought by DevOps in recent times. Complicated provisioning, deployment and release of cloud infrastructure processes which required following complicated steps where cloud resources were created manually is a thing of …
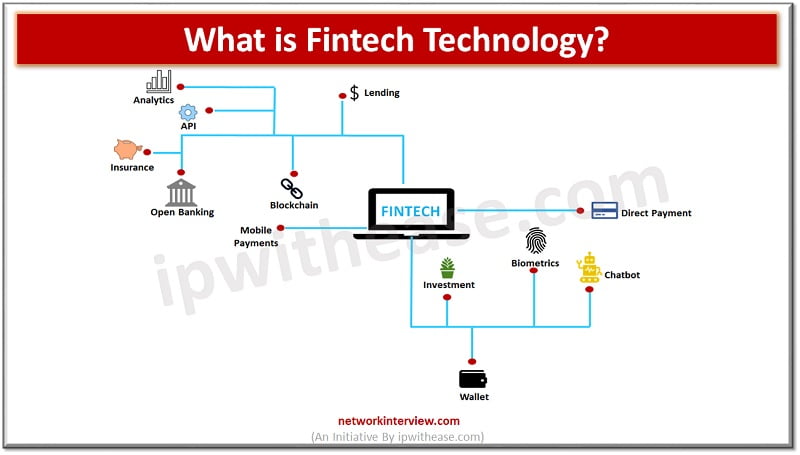
The field of finance is rapidly changing , financial firms, insurance agencies and investment banks are involved at the intersection of data and technology. Big data, machine learning, harnessing algorithms, blockchain technologies are widely spreading to conduct businesses. Financial technology …
Are you considering a Digital Marketing career? Digital marketing jobs are some of the most rewarding ones out there. In fact, many digital marketers love their careers. They think doing professional marketing offers great job opportunities. Even better, there are …
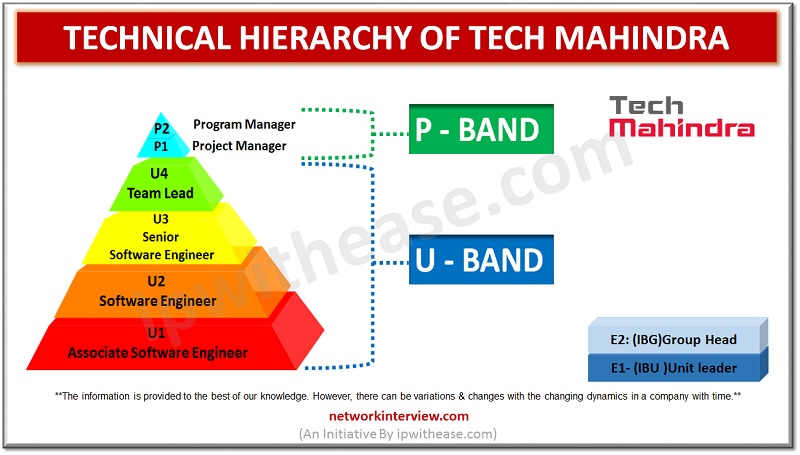
Have you got a job in Tech Mahindra? Are confused about your responsibility and roles? Then you are in the right place. In this article you will have a clear understanding of the Technical Hierarchy of Tech Mahindra and the …
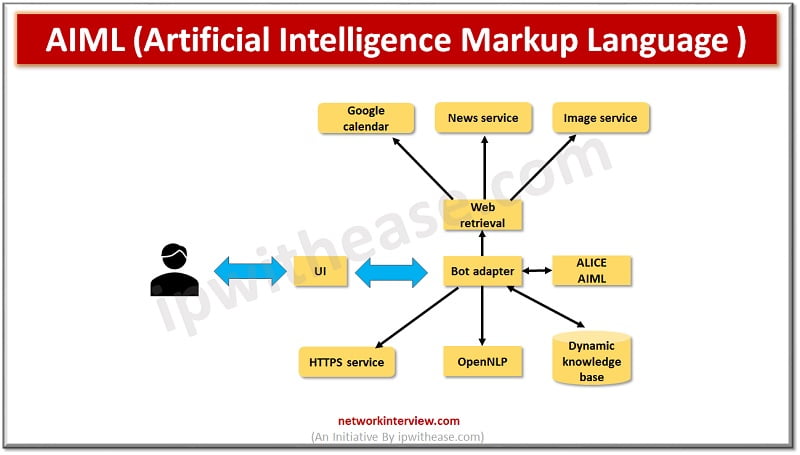
Increased development and spread of information technology and the internet had led to creation of distinct ways to communicate in virtual environments. The cognitive interfaces provide a new form of interaction between humans and systems. The graphical user interface is …
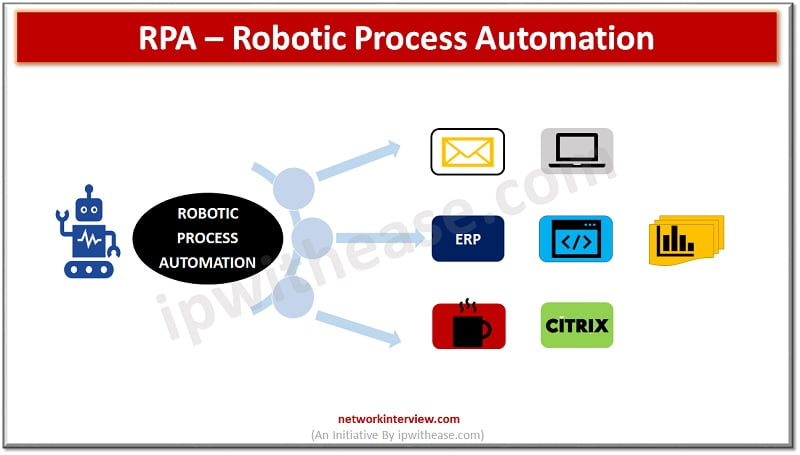
Introduction to RPA Convergence of the physical world and digital world has changed how businesses are interacting with customers nowadays. Robotic Process Automation can be tracked back in early 2000 , it has progressed and developed over a number of years. …
Introduction to Agile Methodologies Most organizations are adopting agile methodology to enable better collaboration between customer and the IT. With Agile the power of teamwork is unleashed. Agile is an iterative approach which concentrates on a continuous delivery framework. The …
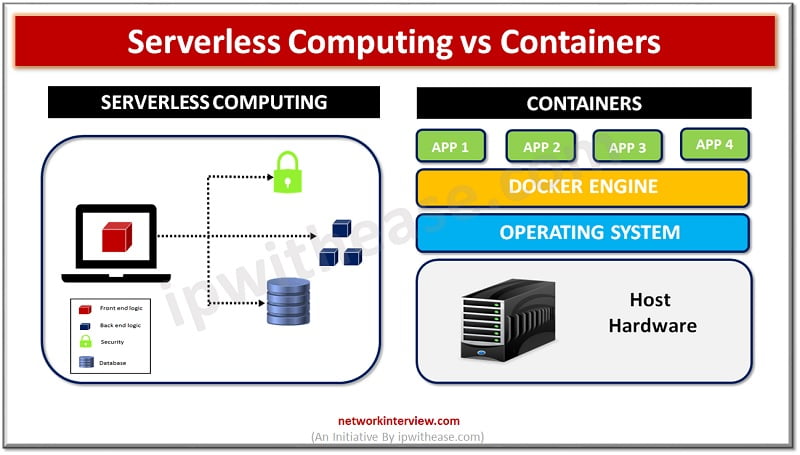
Introduction In the era of enterprise computing organizations are seeking ways to develop, deploy and manage applications in a more efficient , fast and scalable manner. Traditionally applications are tightly linked to servers and the operating systems which executed their …
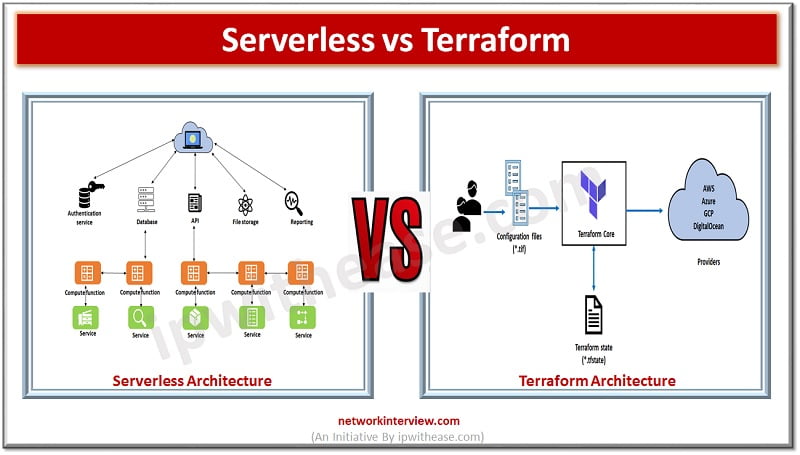
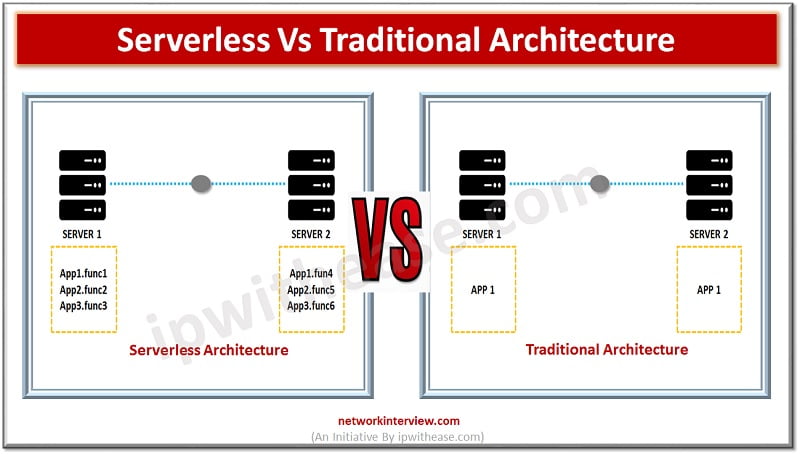
Introduction to Serverless Architecture Over the years organizations have invested money in buying costly servers. The traditional architecture requires large IT staff for maintaining data centres, training and hiring skilled personnel, tracking obsolete hardware and replacing it which would bring …
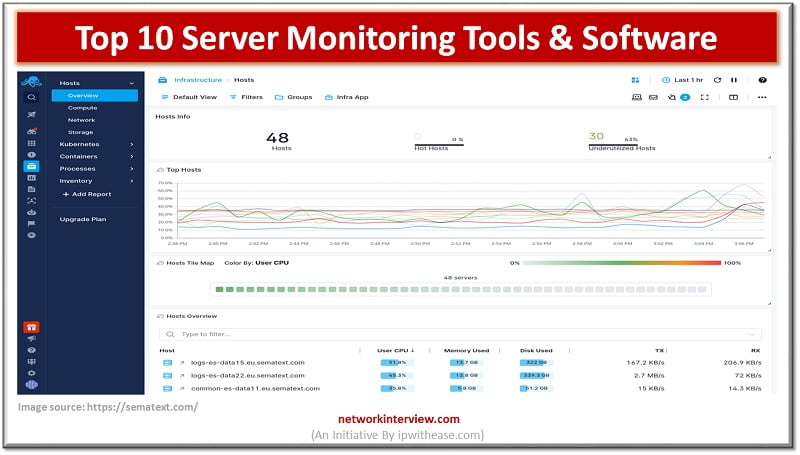
Importance of Server Monitoring Server performance monitoring is an important function that every organization that uses cloud technology should be aware of. The server monitoring makes sure your server resources are being utilized fully and it runs smoothly. In this …
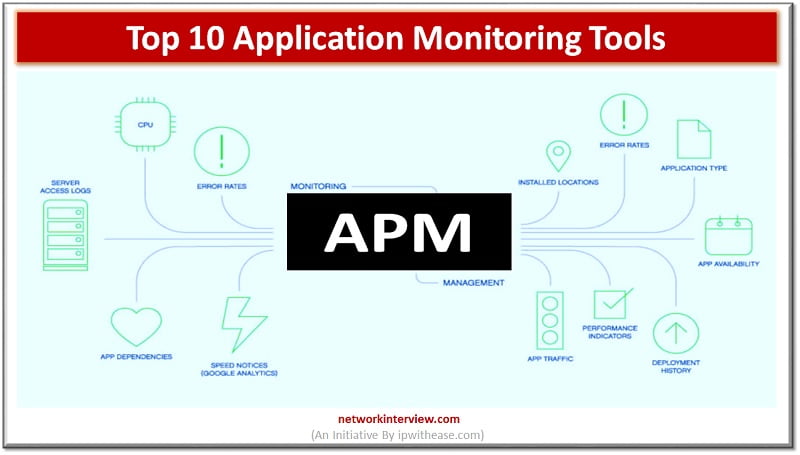
Importance of Application Monitoring The day-to-day life of every person in this world depends on more than one application. This need led to the creation of different types of apps and thus creating the demand for Application Monitoring Tools. Every …
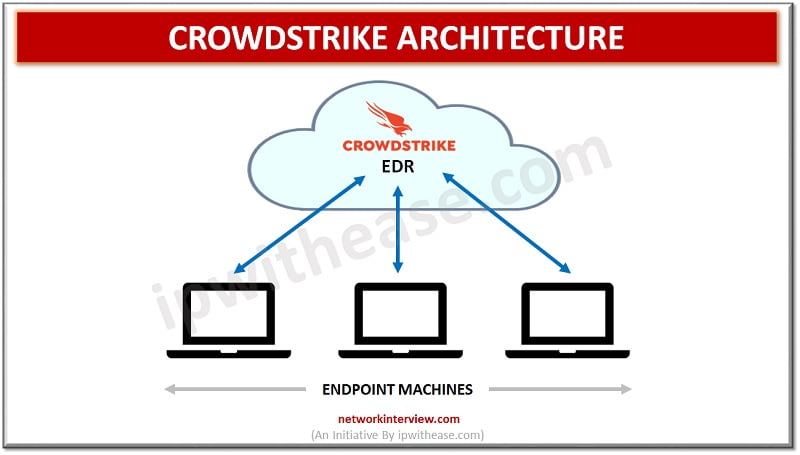
Introduction to Crowdstrike Threat Intelligence and Endpoint Protection is of paramount importance for organizations especially in the scenario where organizations have moved their IT infrastructure over cloud and sophisticated hackers are moving beyond malware to breach organizations. Increasingly relying on …
It is a common interest to know about the position you are going to be hired and its hierarchy in the chain of command. But it is not easy to know the internal workings of organizations. Do you want to …