As companies use Amazon Web Services, it is essential to manage costs. Given the nature of cloud utilization, the need to watch out for unexpected expenses becomes necessary. This is where AWS Cloud Cost Optimization Tools step in as game …
SEO, or Search Engine Optimization, is the process of optimizing online content and websites to enhance their visibility in search engine results. The main objective of SEO is to attract relevant organic traffic to websites, increasing the likelihood of converting …
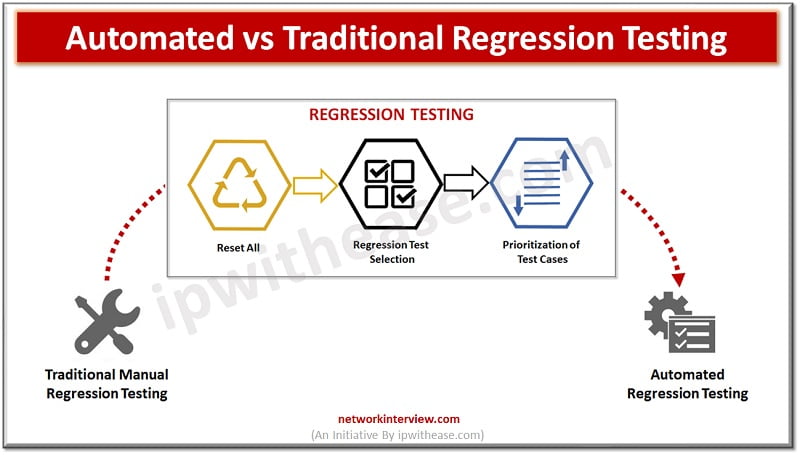
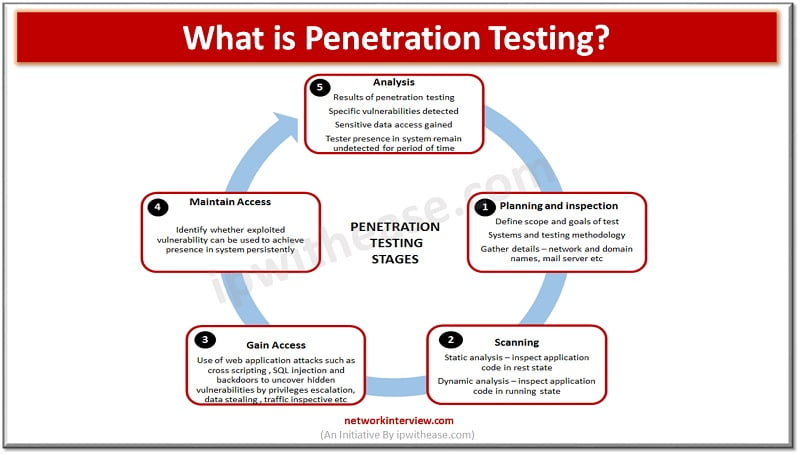
In the field of software development, testing procedures are always changing as a result of the desire to produce high-quality products while preserving agility. Regression testing is one of them and is crucial in verifying that new code changes don’t …
As we move into an increasingly digital world, businesses must collect and manage up-to-date data easily. Manual storage processes are often inadequate and unreliable, especially with large customer datasets, putting organizations at a disadvantage. Fortunately, Master Data Management (MDM) tools …
In today’s digital age, the security of user access rights has become more important than ever before. Managing user access rights is a crucial task in any organization that deals with sensitive data. The rise of distributed systems has made …
Advancements in technology have revolutionized our lives, simplifying the achievement of various goals and tasks. Among these technological advancements, ai voice generator tools play a significant role in enhancing convenience and understanding. TTS ( Text to Speech) enables influencers to …
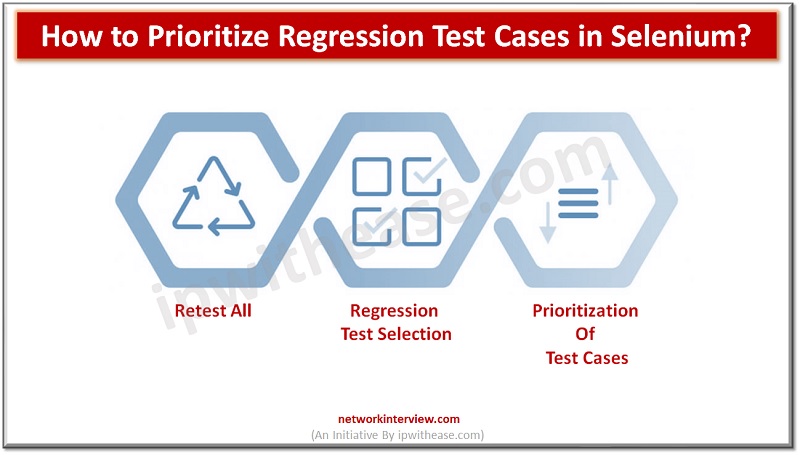
Regression testing plays a critical part in software development by verifying that modifications or upgrades to a program do not generate new faults or disrupt current functionality. However, since regression test suites may frequently be extensive and time-consuming, selecting test …
Selenium Real Device Testing A hugely well-liked open-source framework called Selenium enables programmers and testers to automate web browsers and produce automated tests that perfectly mimic user interactions with web applications. The use of strong error handling and reporting techniques …
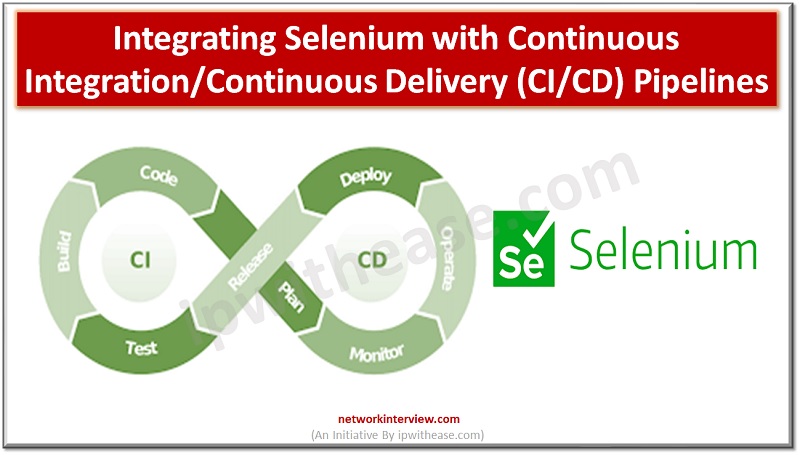
Introduction to Continuous Integration/Continuous Delivery The contemporary practice for application development included separating the development process into three separate stages. These included the development, testing, and the production phase. The application developers separated these phases, which means that the next …
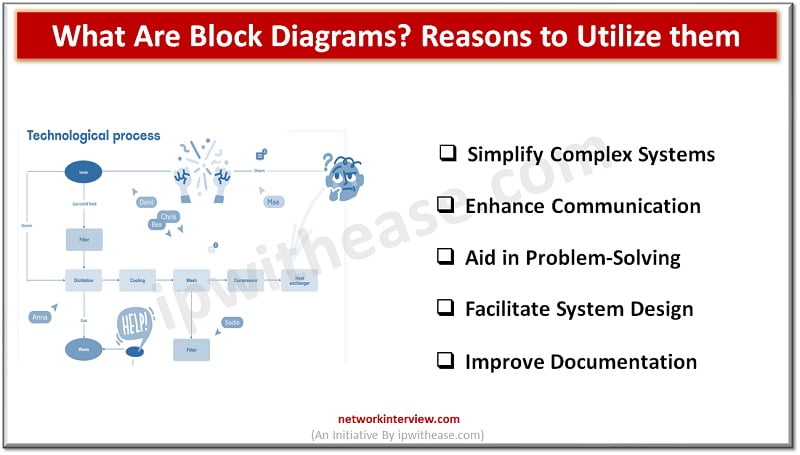
Block diagrams are powerful visual tools that help simplify complex systems and processes by breaking them down into interconnected blocks or functional units. They provide a high-level overview of the components and relationships within a system, enabling teams to better …
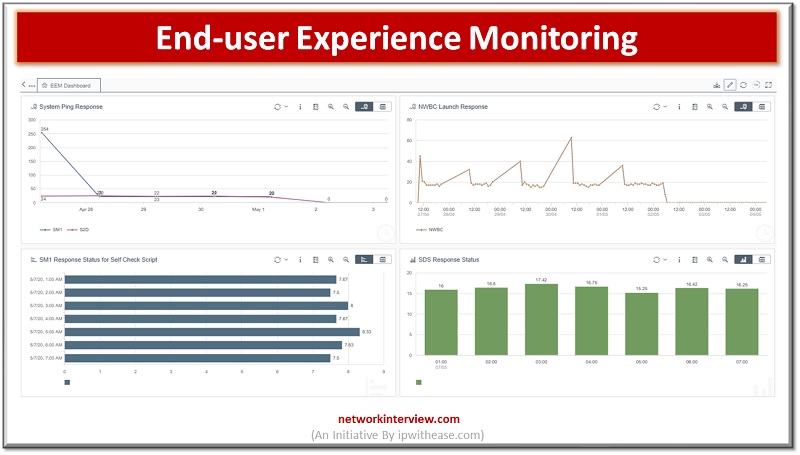
The Importance of End-User Experience Monitoring End-user experience monitoring is a critical aspect of ensuring a high-quality digital experience. The need for businesses to provide an optimal digital experience to their customers is at its peak, and digital experience monitoring …
In today’s fast-paced and competitive business landscape, small businesses face numerous challenges that can hinder growth and productivity. Limited resources, time constraints, and the need to juggle multiple tasks often leave small business owners overwhelmed and struggling to keep up. …
One of the most popular programs for signing PDFs is Adobe Acrobat Reader DC, which allows you to electronically sign documents on your computer or mobile device. Here’s how to do it: Open the PDF you want to sign in …
Each iPhone and iPad has a set storage capacity, but even the largest storage devices can eventually become filled with the content you acquire through music, apps, photos, and messages. Unfortunately, you cannot increase your device’s storage capacity, but there …
What are infographics and how can they be useful for IT professionals? We’re explaining the answers along with tips on how to make infographics that resonate. Have you heard of infographics? You know about other formats that are great for …
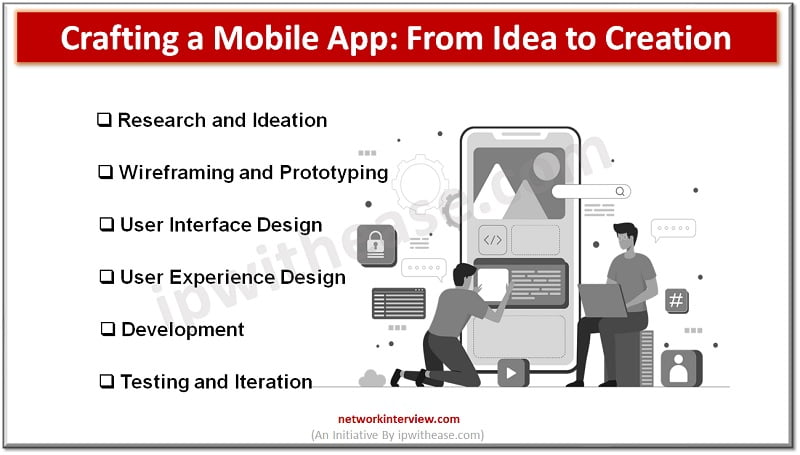
In today’s digital era, mobile apps have become an integral part of our lives. From ordering grub, booking rides, to keeping up with friends, these apps have completely transformed our tech interactions. But have you ever pondered over the process …
Workday is a Financial Management and Human Capital Management Software that is hosted in the cloud. It’s a Software-as-a-Service (SaaS) model. Workday recognizes the importance of a company’s key operations working together and being integrated. Workday Studio is a fantastic …
These days, most businesses rely heavily on software for their daily operation. This is likely to include industry-specific software as well as a range of general business software programs. It is not hard to imagine how difficult it would be …
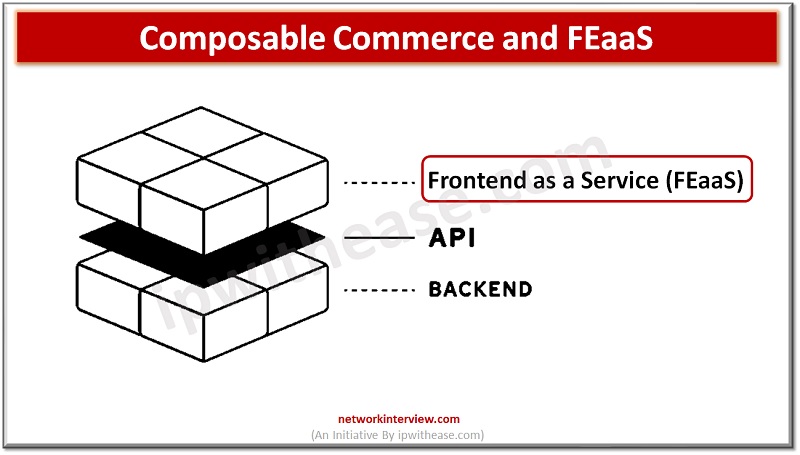
Today’s digital world has opened up a new realm of possibilities for retail businesses. With the introduction of composable commerce and FEaaS (Frontend as a Service), online retailers now have access to tools that can help them drive growth in …
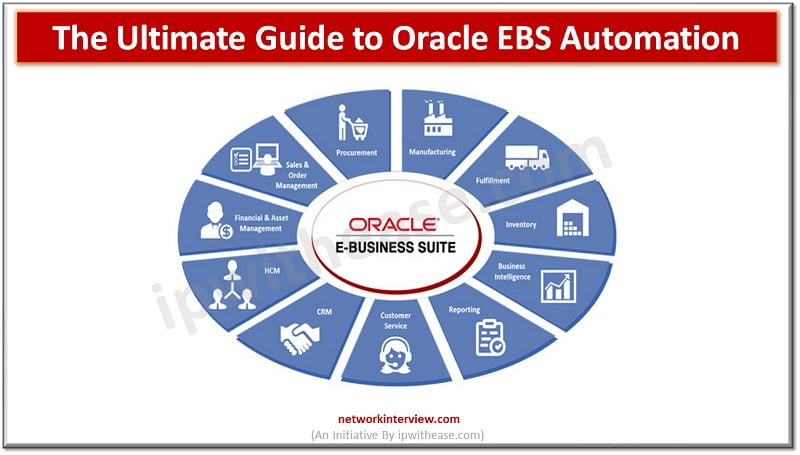
The popular business application known as Oracle E-Business Suite (EBS) is utilized by numerous organizations worldwide. Financial management, human resources management, supply chain management, and customer relationship management are just a few of the departments it aids in the day-to-day …
You can keep tabs on your friends and family with the tap of a button using mobile phone tracking software. Yet, do you understand how these applications function? Or the many different methods that they can assist you in locating …
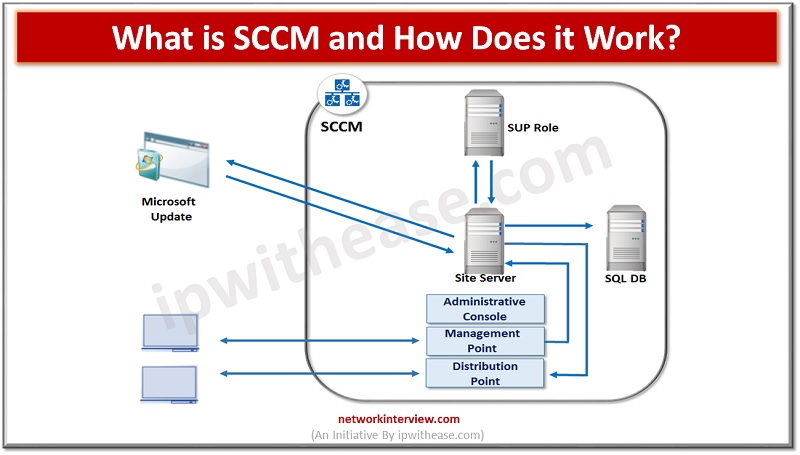
Configuration Manager, commonly known as SCCM, is a powerful and versatile tool created by Microsoft. It provides IT professionals with an integrated platform to manage and deploy software, hardware, and other resources across their networks. In this blog, we’ll take …
In today’s digital world, the need for brand protection is more important than ever. With the rise of online marketplaces and e-commerce websites, counterfeiters have found a way to exploit brands and make money off of fake products. To combat …
Fans of podcasts are always on the lookout for an incredible platform on which they can listen to their favorite shows without running into any problems. They all want hassle-free apps with appealing features. Inarguably, the number of fans of …
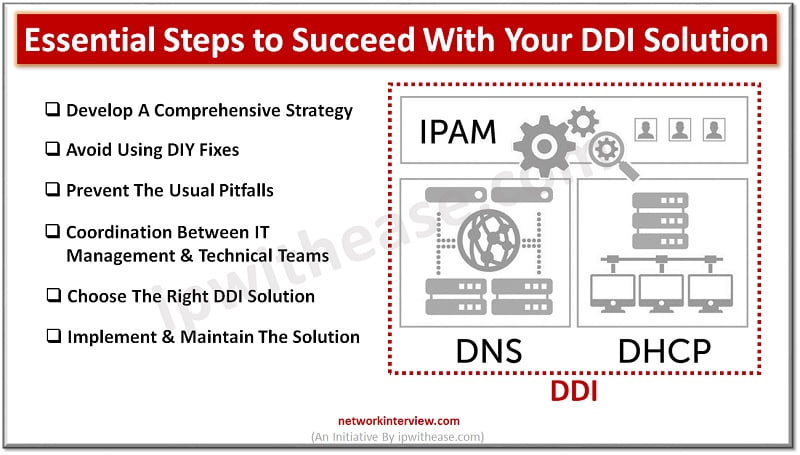
The acronym DDI stands for DNS, DHCP, and IP address management (IPAM). The combination of these three crucial networking elements into a single management solution is referred to by this widely used acronym. A DDI solution offers a centralised platform …
With the increasing popularity of mobile devices, businesses have been looking for ways to engage their customers more effectively. One of the solutions they have come up with is progressive web apps (PWAs). In this post, we will discuss what …
Securing incoming and outgoing traffic while keeping track of each link that staff members click might be difficult. Hackers have recently started to pay attention to DNS since any faults could serve as a route for them to exploit vulnerabilities …
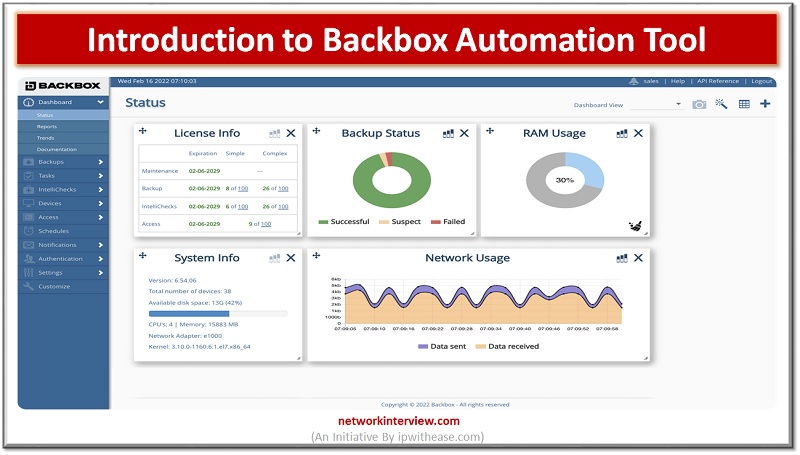
Are you looking to boost your productivity and efficiency as an IT administrator? If so, you’ll love the BackBox Automation Tool. This tool will help streamline your day-to-day operations, increase visibility into your network and accelerate troubleshooting. It’s the perfect …
A huge amount of the work that goes into running a small or medium sized business is related to the management of resources. Resources can include finances, inventoried items, important data and customer information among other things. A company cannot …
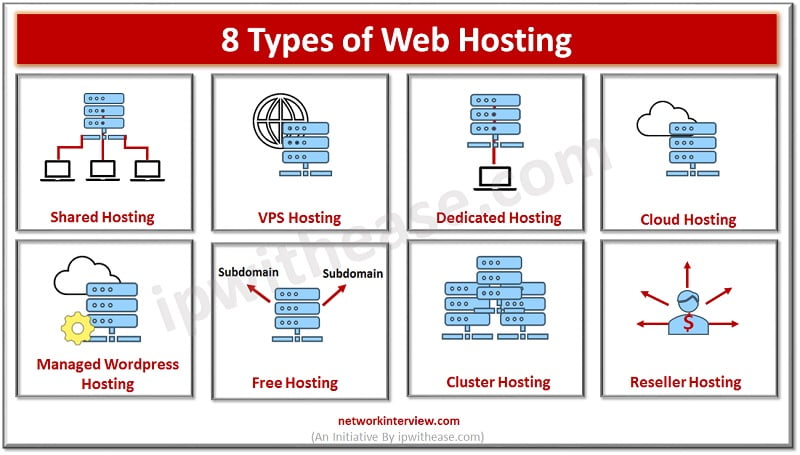
What is Web Hosting? Web hosting services let organizations and persons publish on the Internet or Internet page and plays a critical role in online presence. These websites are stored on systems hosted over the web or Internet. There are …
Why Time Tracking Software? Businesses around the world work hard to improve their management skills and stay competitive in a business world that is increasingly evolving. Presently, technology is by far the most utilized in the world of business. Various …
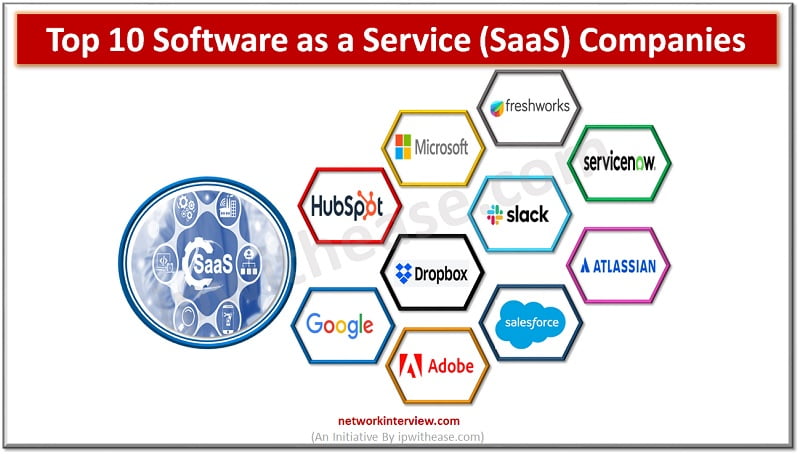
Software as a Service (SaaS) is an umbrella term for cloud-based services delivered to customers over the internet. The software operates on a subscription model, helping businesses reduce capital expenditure and operational expenses by shifting from upfront payments for software …
Are you thinking about doing business beyond your domestic market? Making your website accessible to potential customers in foreign markets is key in the international marketing of your product or service. The first thing that springs to mind when considering …
Virtual Private Network is referred to as VPN. Your internet traffic is encrypted by VPN software, which also uses a secure connection to deliver your data to a remote server. The info then makes its way to the internet from …
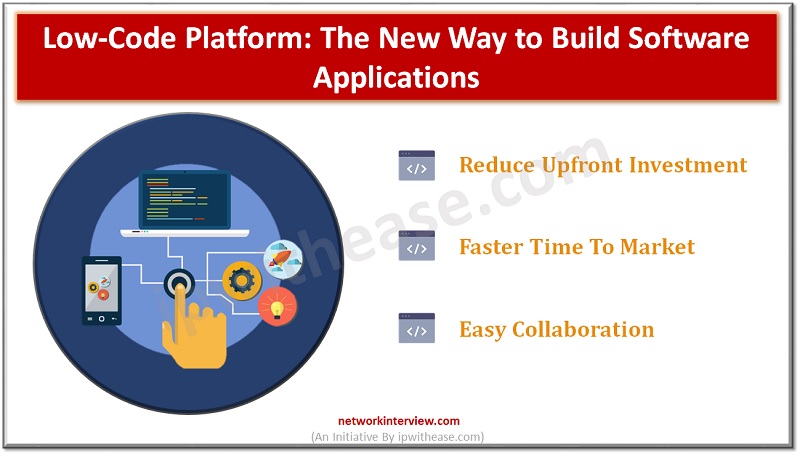
Introduction to Low-code Low-code software is great for users who want to perform complicated tasks quickly and efficiently. In this blog post, you will learn about ten best low-code platforms that you can use for your next project. These solutions …
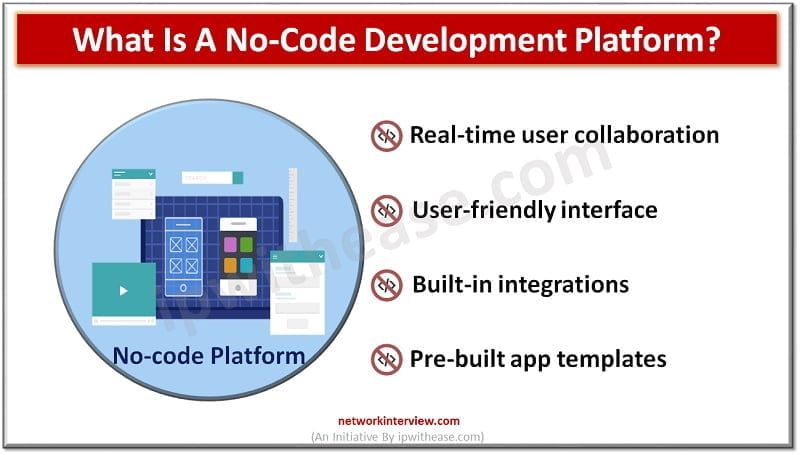
No-code app builders are a great option for teams that want to rapidly prototype or build software apps without needing to learn code first. They’re also an excellent choice for project teams who need to build and launch new apps …
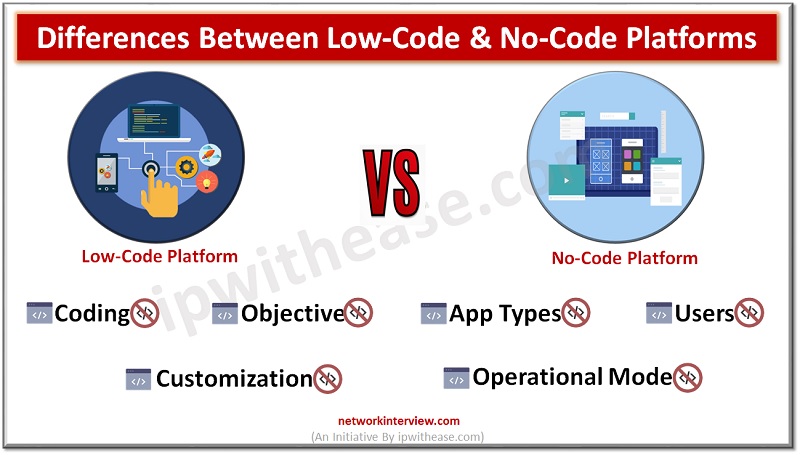
Low-code vs No-code No-code and low-code software are both ways of building apps with limited coding experience. But they each have their own advantages and disadvantages. Choosing the right one for your team and project can help you create an …
In today’s digital world, businesses need software applications to keep pace with their changing needs and requirements. Businesses now look for more efficient ways to build and deploy these applications, without compromising on the quality or functionality. To meet this …
No-code is an emerging trend that allows non-technical users to build custom applications without writing code. In other words, no code means no programming skills are required. Instead, a no-code platform uses natural user interface (NUI) tools to create apps …
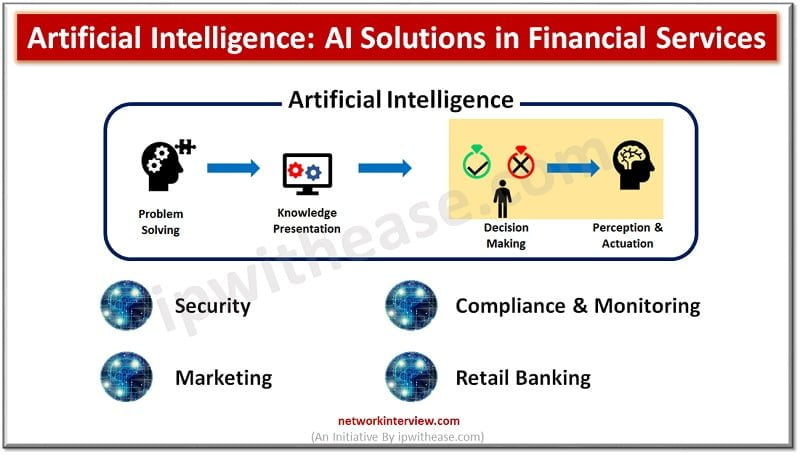
Financial institutions have faced significant challenges in terms of fraud detection, wealth management, investment advice, customer analytics, and so on. These challenges are difficult for human experts to deal with and require an overhauled approach that utilizes artificial intelligence. Artificial …
To have faster time to market and bring in business agility organizations are more and more relying on technology. Technological advancements have one side facilitated business to grow faster and quickly adapt to changing needs of businesses and on other …
Cyber security software is a must for ensuring business and individuals security and privacy. It is a method to protect networks, systems and applications from cyber-attacks. It helps to avoid unauthorized data access, cyber attacks and identify stealing. Application, information …
Have you ever bought a Samsung Phone which has a different processor than your friends? Yes, the Samsung Mobiles uses two processors for all their models. The mobiles with Exynos processors are sold in Asian and European countries whereas the …
In the past few years, video making and editing have gained immense popularity. It’s now easier than ever to shoot impressive videos with your smartphone or a DSLR camera and share them on social media. It has given a platform …
Are you dissatisfied with the performance of your internet connection at home? If you have the option of choosing from more than one internet service provider, why not choose the best and the fastest broadband connection. Choosing the best internet …