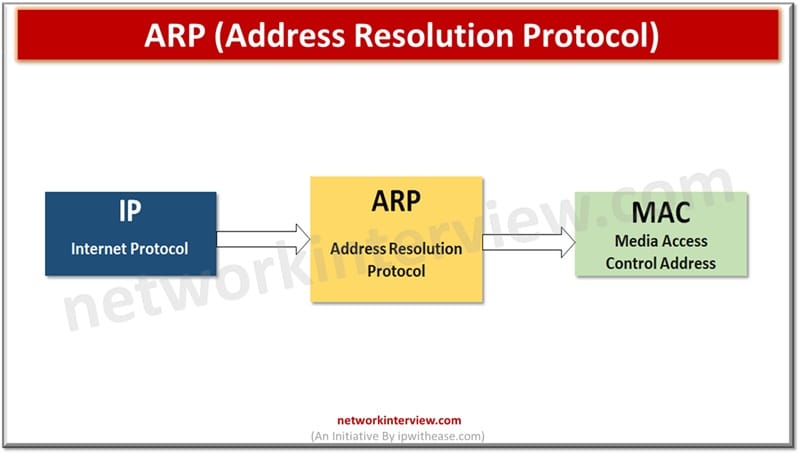
All computer systems and programs use human readable and understandable IP addresses for communication across the network; however, actual communication between systems takes over the MAC or physical address of the device derived at layer 2 data-link layer of OSI …
The information access is made uninterrupted over wired and wireless networks from anywhere, anytime, any device using modern technology. Today end users are mobile and often equipped with digital portable devices and they expect services availability as and when it …
All communication in Internet world is govern by OSI (Open Systems Interconnect) framework. There are seven layers in OSI model and each layer performs a set of functions to ensure data delivery to its intended recipient. The layer 3 or …
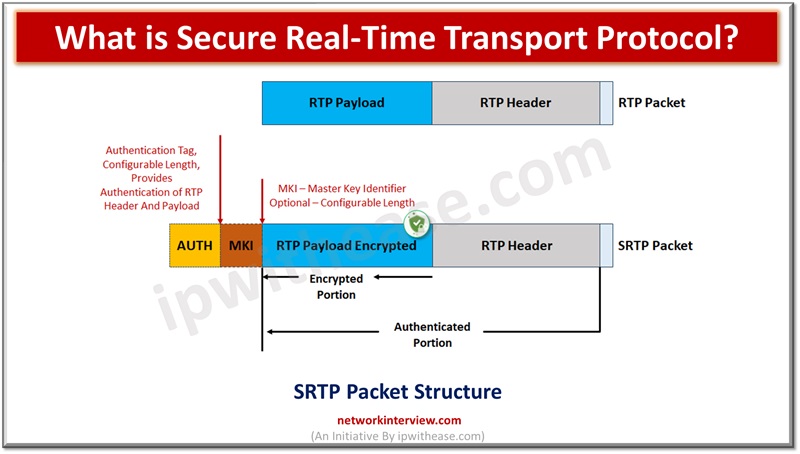
There are a set of protocols which define how real time traffic handling will be taken care of such as audio and video over the Internet. These protocols are known as Real Time Transport protocol (RTP). RTP protocol is used …
You might have heard of such things as SMTP ports and already know that it has something to do with setting up your email software. But what is it exactly, and how do you determine the proper one? This article …
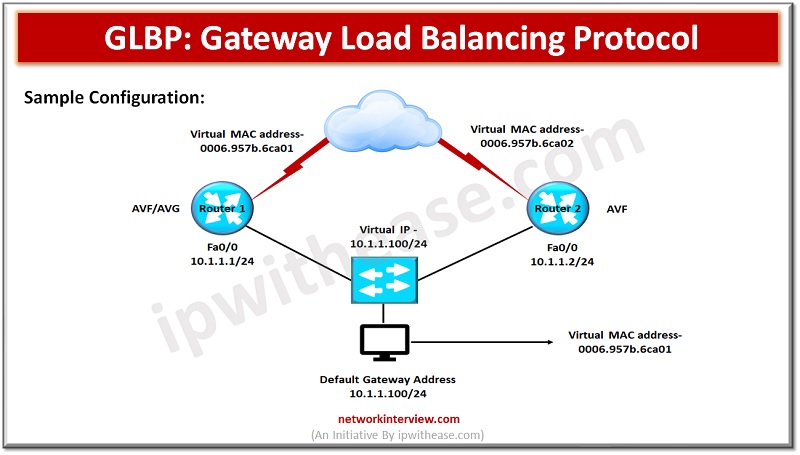
Introduction to Gateway Load Balancing Protocol Load balancing is one of the key requirements in networks and it can be achieved in several ways such as round robin, host dependent and weighted. Protocols supporting load balancing have the capability to …
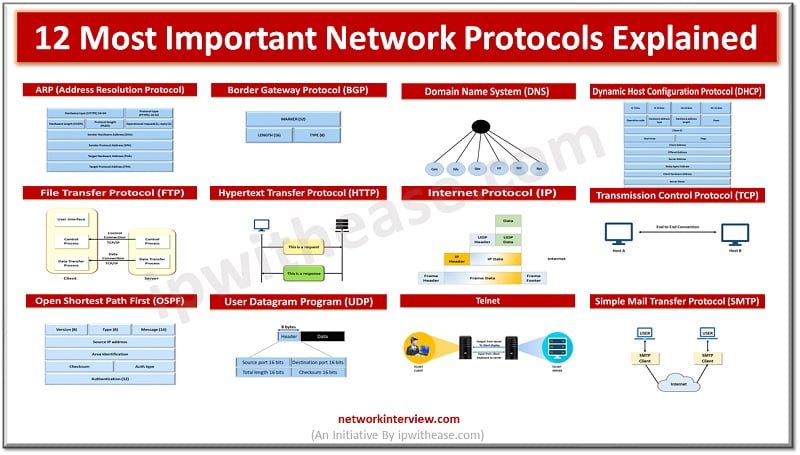
Network protocols establish rules of communication to control and govern exchange of information following secure, reliable methods. These are a set of rules designed to have a standard framework for interchange over networks. There are a variety of network protocols …
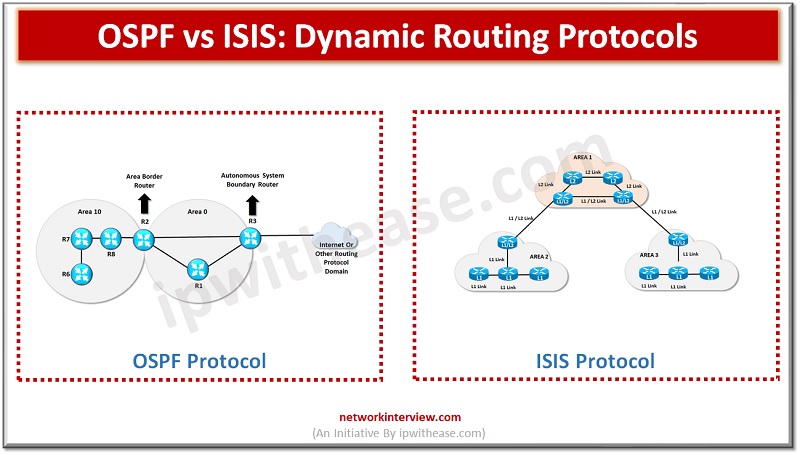
Computer communication networks are growing at a rapid pace, they are based on technology which provides the technical infrastructure, whereas routing protocols are used for transmission of data packets across the Internet. Routing protocols specify how routers communicate with each …
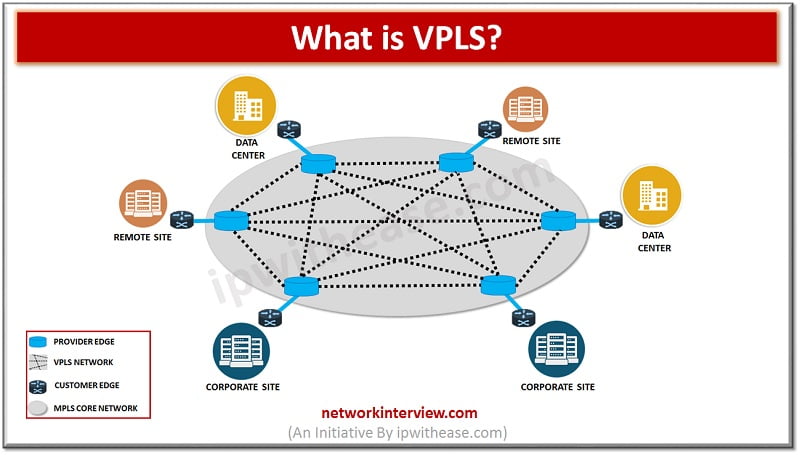
Introduction to VPLS As we have already discussed MPLS in detail in our previous article, so here I will focus on VPLS first and then the differences between the two. VPLS i.e. Virtual Private LAN Service. It is a service that …
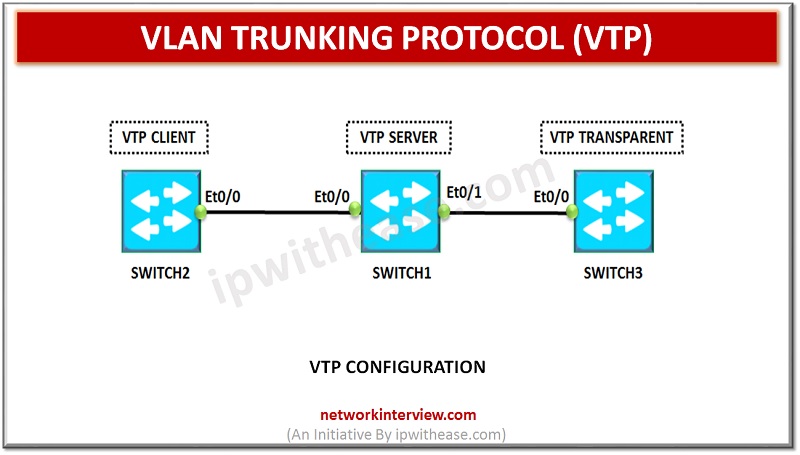
VLAN Trunking Protocol VLAN Trunking Protocol is used by Cisco switches to exchange VLAN information. In VTP, synchronization of VLAN information, such as VLAN ID or VLAN name can be done with switches inside the same VTP domain. VTP domain is …
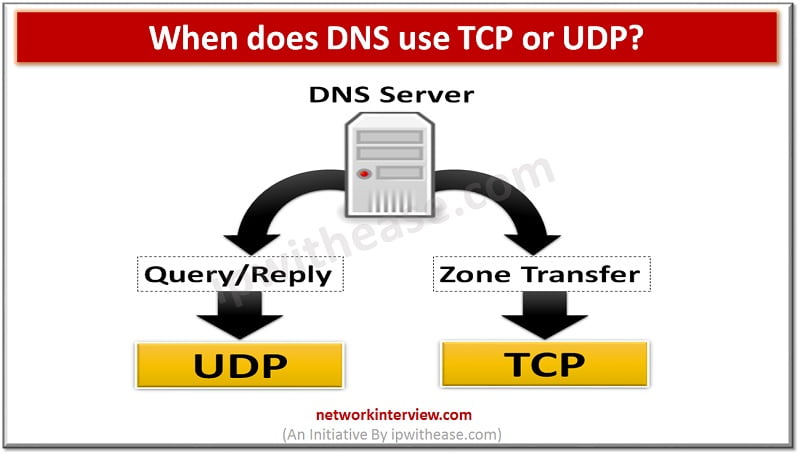
Introduction There are quite is few services which may use both TCP and UDP protocol while communicating. The primary reason is based on type of request/response which needs to be furnished. Before we further drill into detail of protocol type …
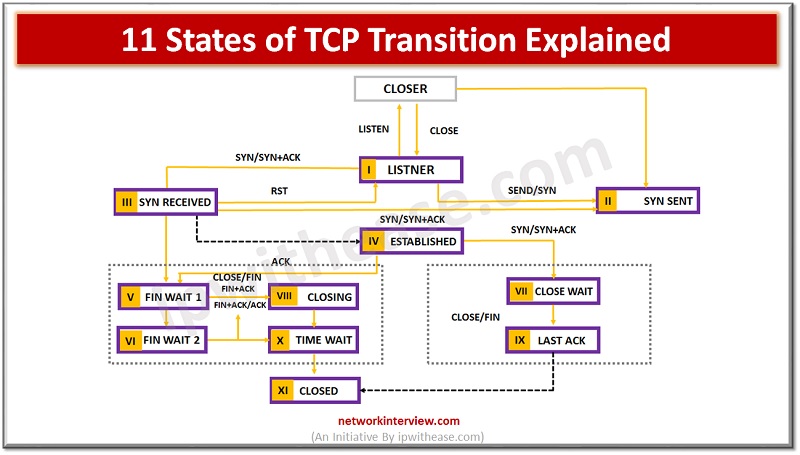
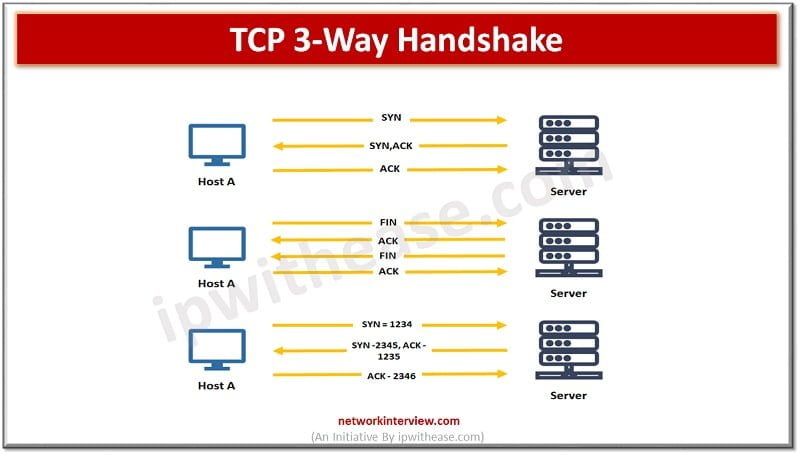
TCP or transmission control protocol operates at the transport layer of the OSI model. It facilitates transmission between packets from source to destination in a reliable manner as it is a connection-oriented protocol. TCP operations are divided into three phases …
Whenever networks are implemented and different devices try to communicate over the network. Some of the other reference models are being referred to which is a standard specification or framework to provide standardization on how implementation, connectivity, communication will happen. …
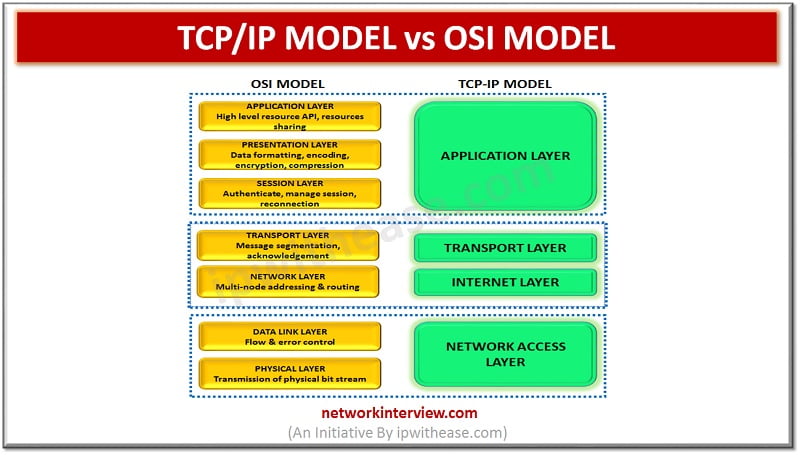
Introduction The Transmission Control Protocol/Internet Protocol (TCP/IP) is a network communication protocol that interconnects the network devices into the internet. It provides a communication between the source and the destination. It specifies how data packets should be broken, addressed, routed, …
The TCP/IP model helps to determine how one computing device would connect to the internet and how data transmission happens between them. It helps to create a virtual network while several computing devices are connected to each other. TCP/IP stands …
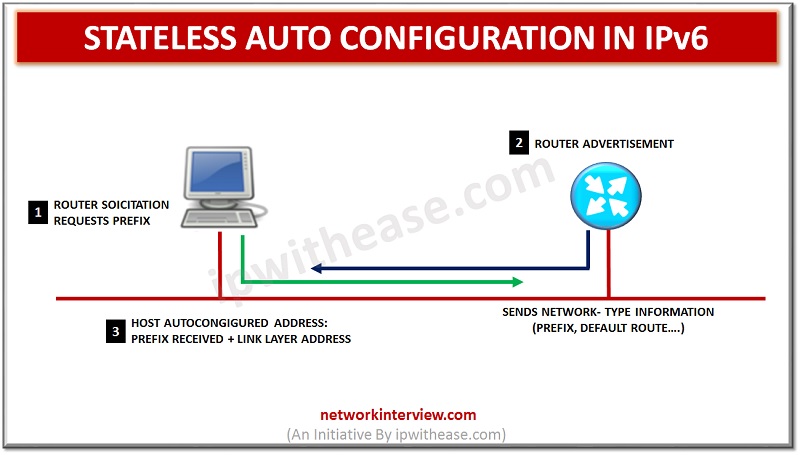
IPv6 Stateless Autoconfiguration enables a local link address which allows the user to access the internet from anywhere. No intermediary IP address or support is needed to be created as the DHCP server. All the devices that are connected with …
Introduction to IPv6 The IPv6 is the abbreviation for the Internet Protocol version 6. The IPv6 is the most updated protocol of network layer which can make the transmission of data possible in packets between two networks. It simply means …
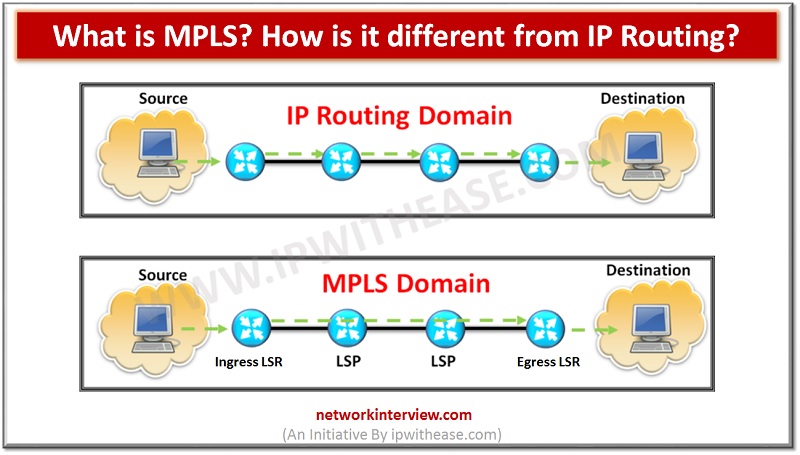
Introduction to MPLS MPLS i.e. Multi Protocol Label Switching (MPLS). It is a technique that is used for the routing of network packets. It is called a Multiprotocol as it supports multiple protocols like Internet Protocol (IP), Asynchronous Transport Mode …
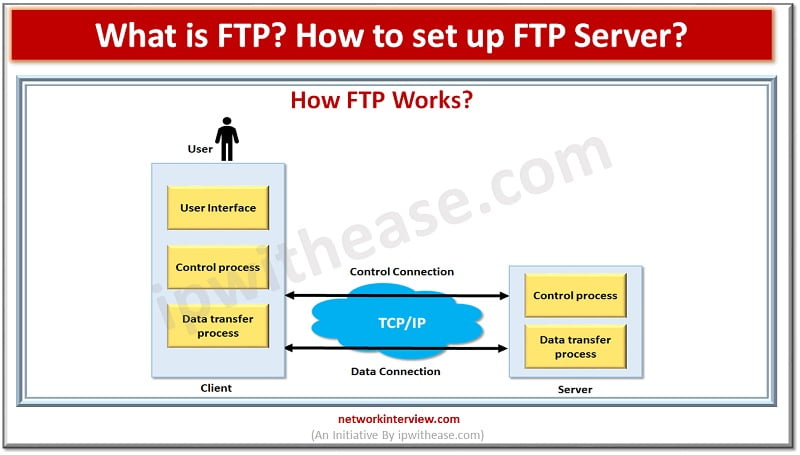
File transfer protocol (FTP) has been around for more time than HTTP and TCP/IP protocol and has more than 40+ years of existence in the industry. Its original specification was written way back in 1971 and initial FTP clients were …
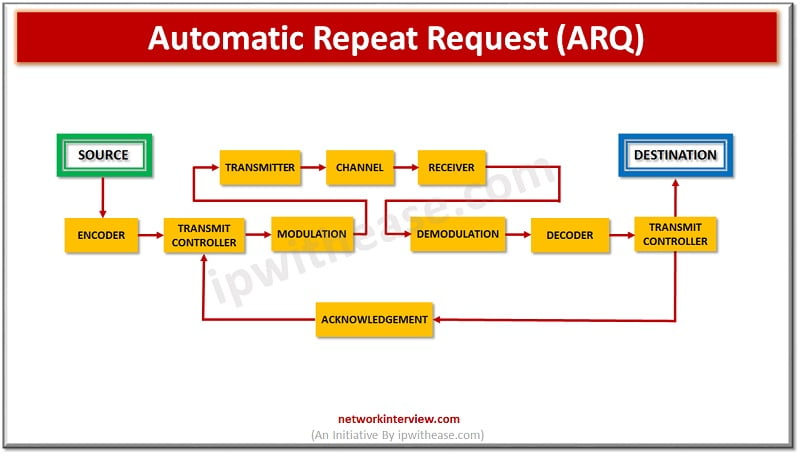
Various techniques are used at the Data link layer to control errors to simply ensure and confirm that all the data frames or packets; i.e., bit streams of data are transmitted and transferred from sender to receiver with accuracy. Using …
Online machine to machine communication is handled by web services. It is used by systems to communicate systems on Internet and only front-end interfaces like websites and applications which reside on end user systems. Data exchange between heterogeneous applications would …
There are several protocols that exist at different layers of OSI and are used for various functions related to data transfer, communication, encryption and so on. OSI model provides a common reference point and universal set of rules which govern …
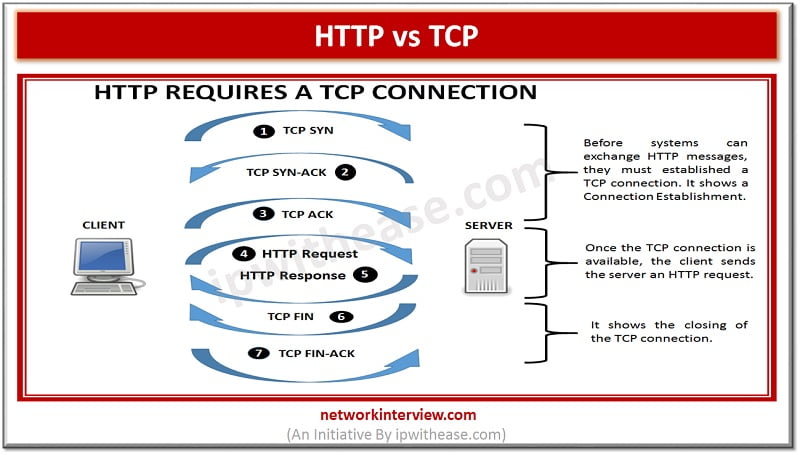
Before discussing the difference, let’s understand the two terms first What is HTTP? HTTP is a Hypertext Transfer Protocol. HTTP works similar to other application services like SMTP and FTP. Like the performance of FTP, it transfers a document using …
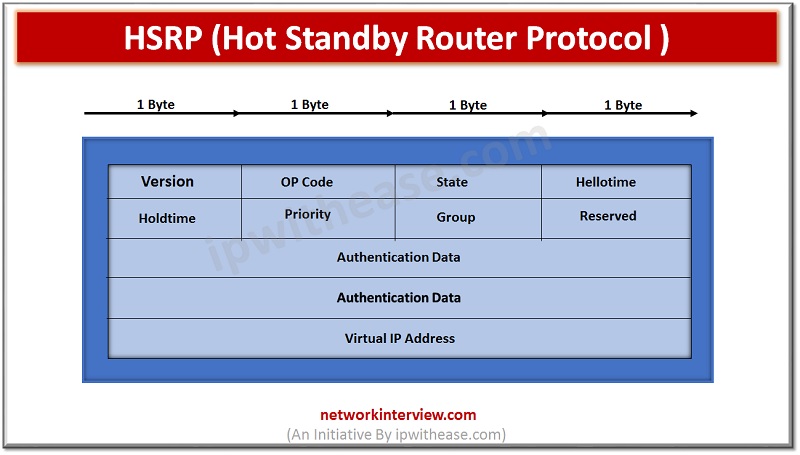
Hot Standby Router Protocol (HSRP) In this article, we will discuss on HSRP protocol, related terminologies, its operation and configuration. We will cover following points:- Topic Content Understanding FHRP Definition of HSRP HSRP Packet Key Points Operation and Configuration of …
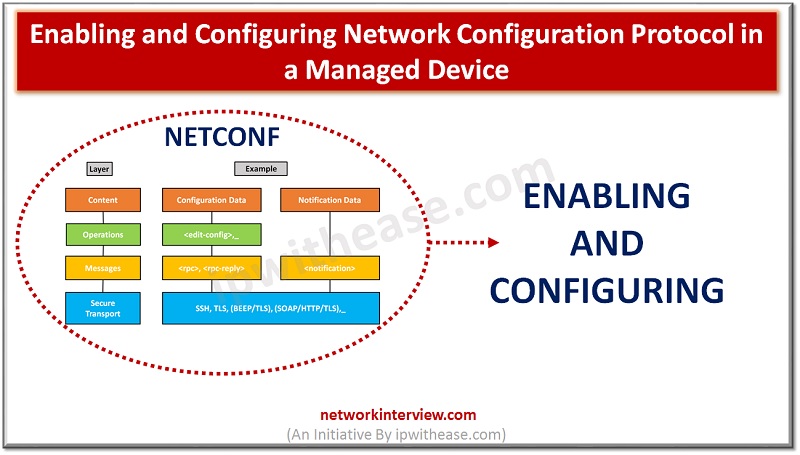
Enabling and Configuring Network Configuration Protocol NETCONF is a protocol that can manage, configure and install new configuration to network device. Its operations are realized on top of an easy Remote Procedure Call (RPC) layer. NETCONF uses Extensible Markup Language …
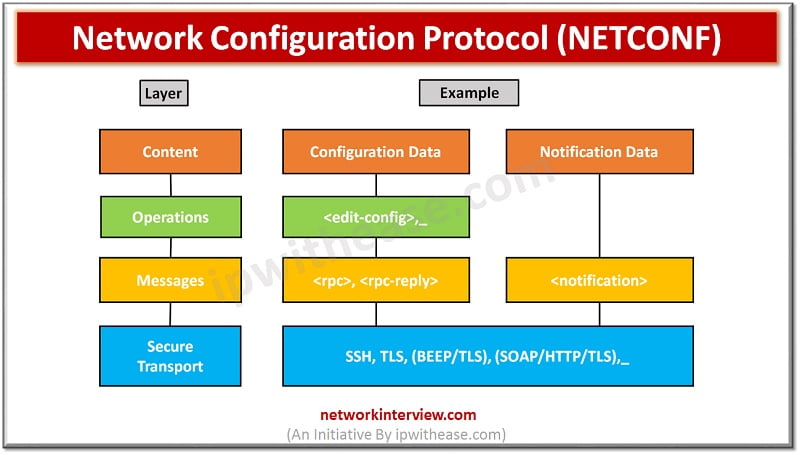
NETCONF Protocol – Network Configuration Protocol Network monitoring systems are tasked with ensuring the availability and performance of computers and network services and can detect and report on failures of devices or connections by deploying NETCONF/SNMP in device. Content of …
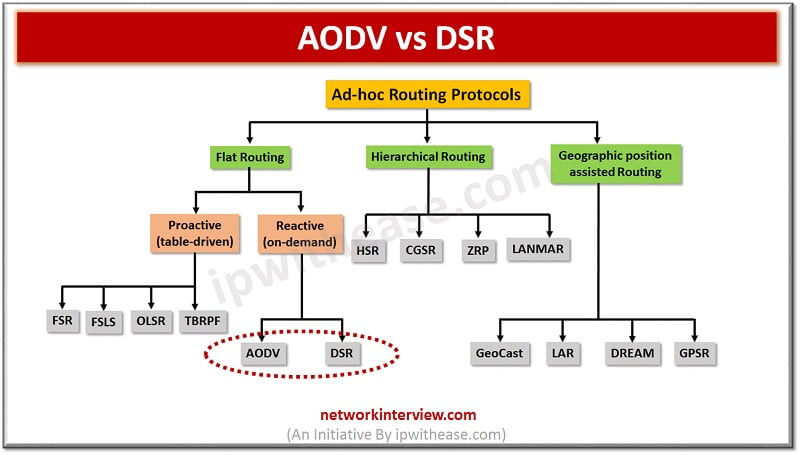
Difference between AODV Routing Protocol and DSR Protocol An ad hoc network or Mobile ad hoc network refers to a network connection established for a single session and does not require a router or a wireless base station. It does …
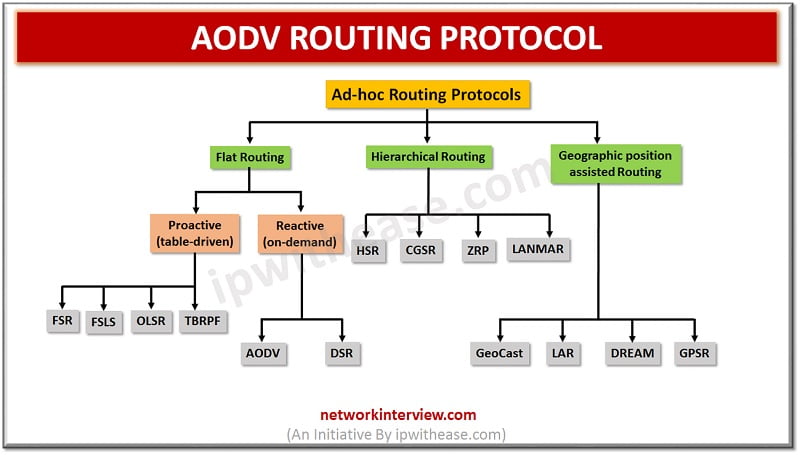
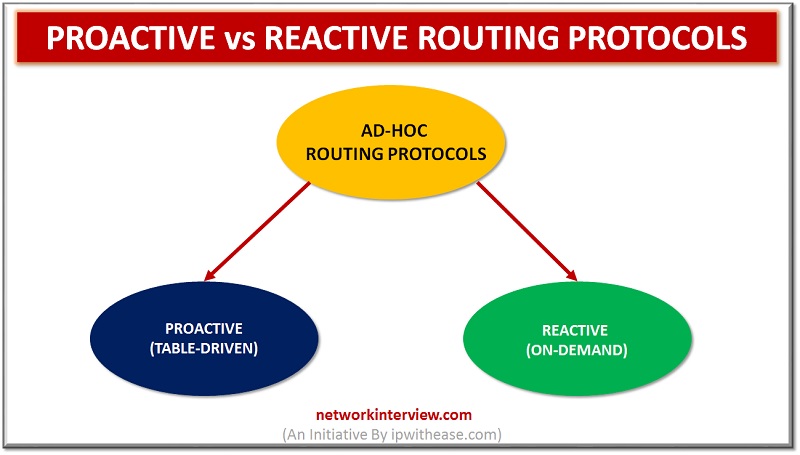
Hierarchy of Ad-hoc routing protocols In this article, we will understand the concept of AODV Routing protocol, which is type of Reactive (On-Demand) protocol. So, before beginning let’s understand what is a reactive protocol. Reactive Protocol Reactive Routing Protocol is …
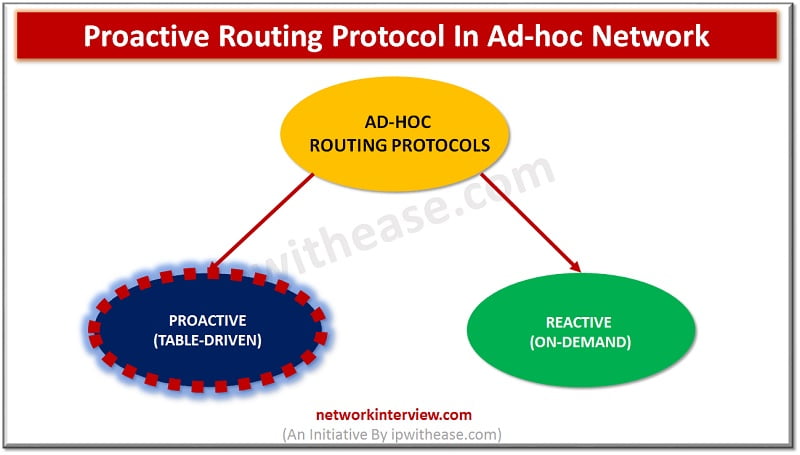
Proactive Routing Protocol Introduction Ad-hoc network is a collection of mobile nodes forming an instant network without a fixed topology. In such a network each node acts as both router and host simultaneously and can join or move out in …
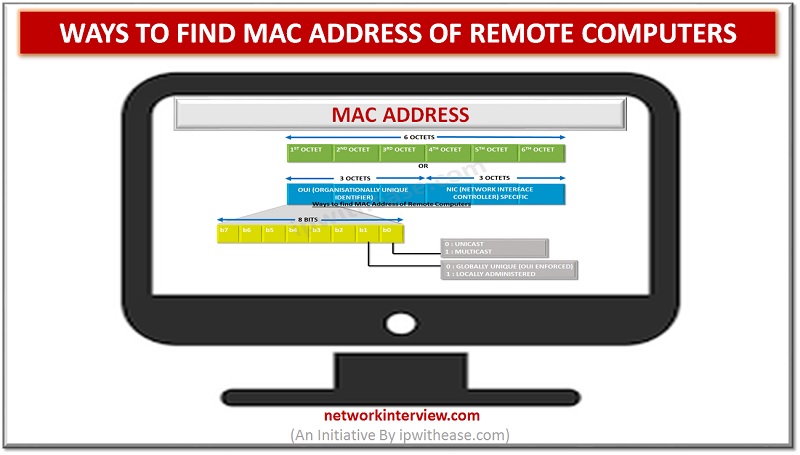
Ways to find MAC Address Network and System administrators are many times caught is issue of finding MAC address of some remote device in network. Physical validation of each device may be time consuming and very tedious activity. In this …
Proactive vs Reactive Routing Protocols Routing protocols are the routes that help to learn dynamic routes. These protocols are organized on routers in regards with exchanging the information related with routing. Using the routing protocols in your network has many …
OpenFlow vs Netconf There are several data programming and configuration protocols that make the flow of information seamless across the networks. Among these protocols, OpenFlow and Netconf are considered to be popular and widely used ones when it comes to …
Windows Management Instrumentation (WMI) is Microsoft’s technological invention intended for taking care of Windows’ varied operational environments. Microsoft has offered set of specifications in the form of WMI for strengthening applications and devices management in the network. The information regarding …
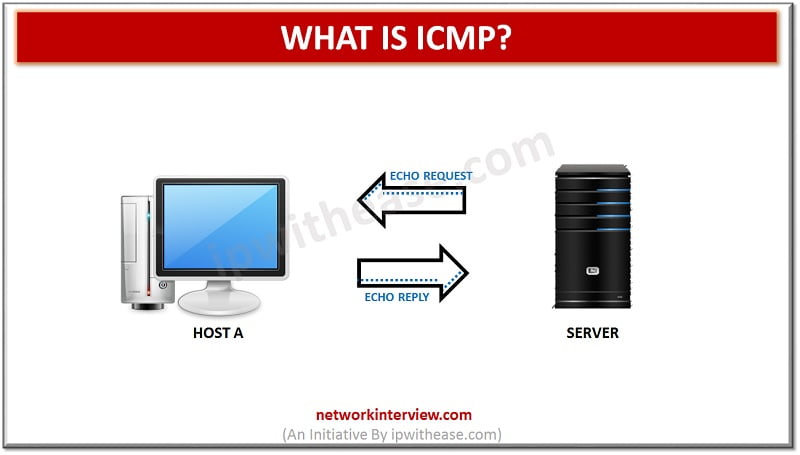
ICMP stands for the Internet Control Message Protocol. It is a primary protocol in the Internet Protocol Suite. It is used by network devices to relay an error message and management queries. It helps to reroute the message to its …
SSH PROTOCOL SSH (or Secure Shell) is a protocol that facilitates secure communications between two systems using a client/server architecture and allows users to connect to a host remotely. Unlike other remote communication protocols such as FTP or Telnet, SSH …
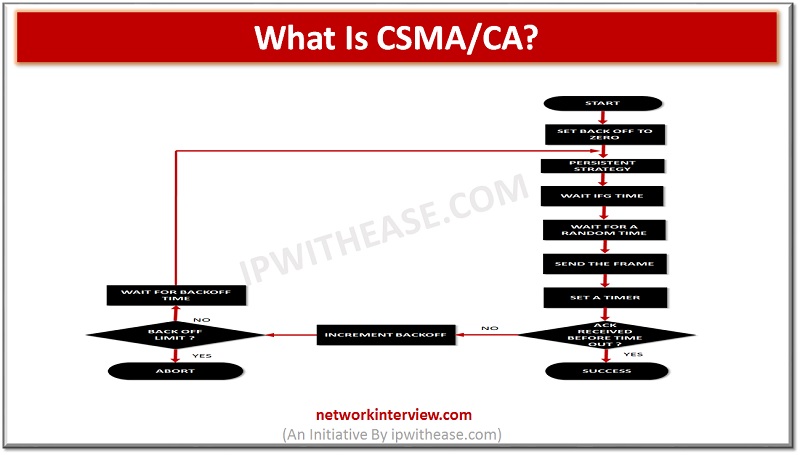
CSMA/CA stands for Carrier Multiple Access/Collision avoidance. It is a technique using which the chances of collision are decreased. In most of the cases, the collision is avoided. It is used to transmit data using 802.11 standards. The similar technique …
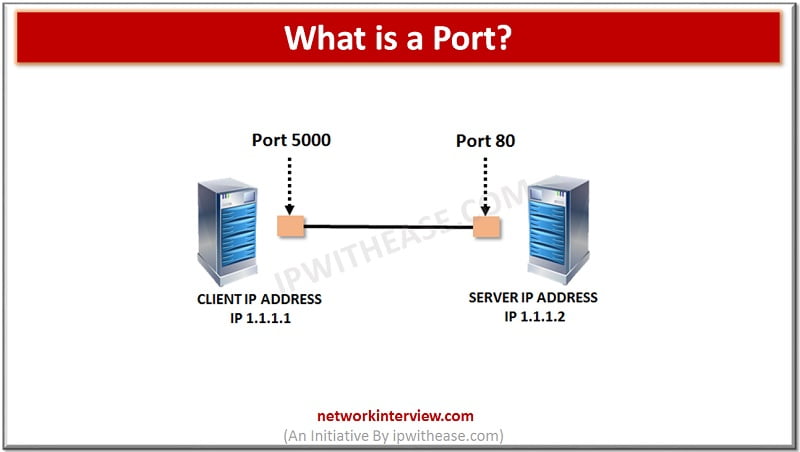
In networking, a port is defined as the endpoint of any data communication. This applies to a kind of data transfer whether they are using a wireless connection or these re physical connections. In the same way, when it comes …
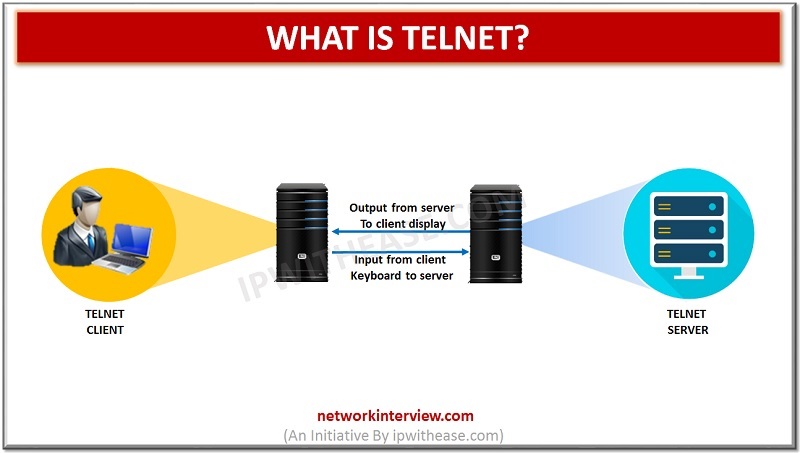
Telnet is one of the protocols that is used both on the internet and LAN (Local Area Network). In other words, Telnet is a protocol that is used in order to get access to the remote computer or the terminals. …
URL Stands for Uniform Resource Locator. It is a web address that is used to locate any of the data stored on the cloud using the internet. URL is a type of Uniform Resource Identifier (URI). Use Cases of URL …
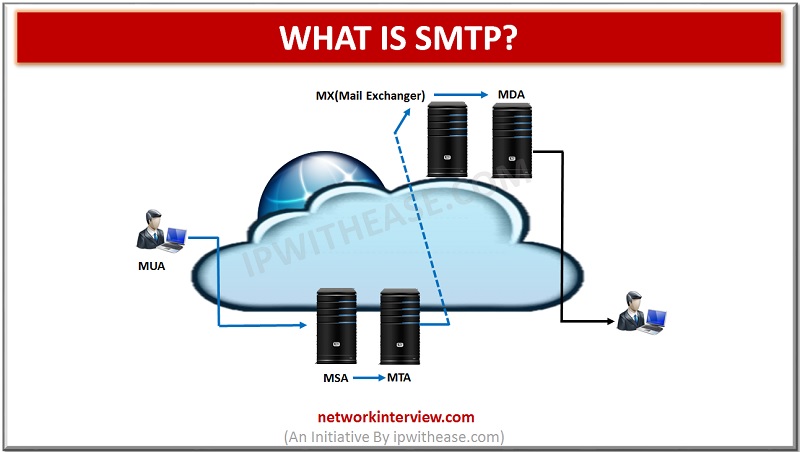
SMTP stands for Simple Mail Transfer Protocol. It is the protocol used for the email service that is used on the internet. It works on the TCP/IP protocol. Using the SMTP, we can either send or receive email messages from …
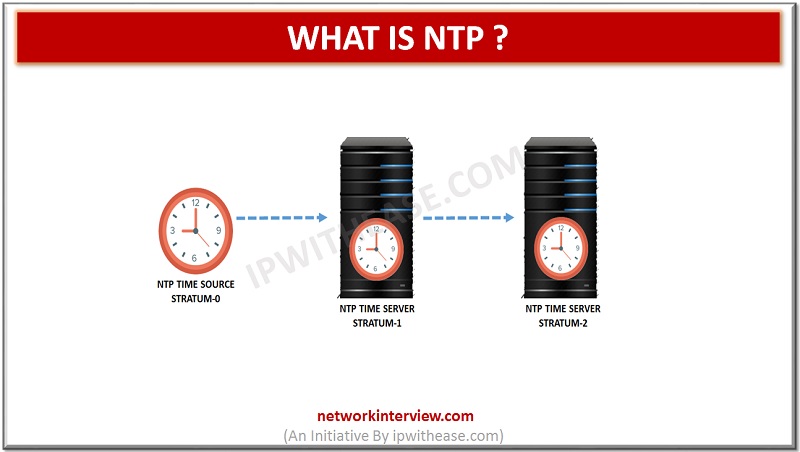
Introduction to NTP NTP is the protocol used in reference to time. NTP is responsible for synchronizing the time of the computer with the time of the network. NTP stands for Network Time Protocol. It is one of the oldest …
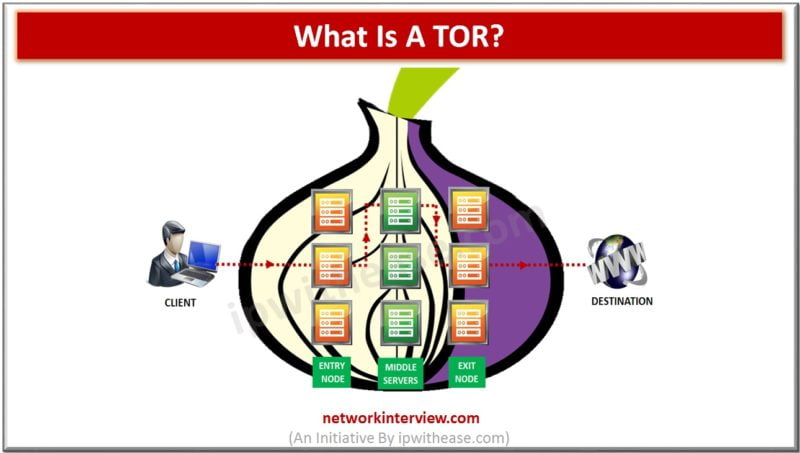
TOR (The Onion Router) is a software and open network which allows the users to browse the Web anonymously. TOR makes it difficult, if not impossible, for any snoops to see our web mail, search history, social media posts or …
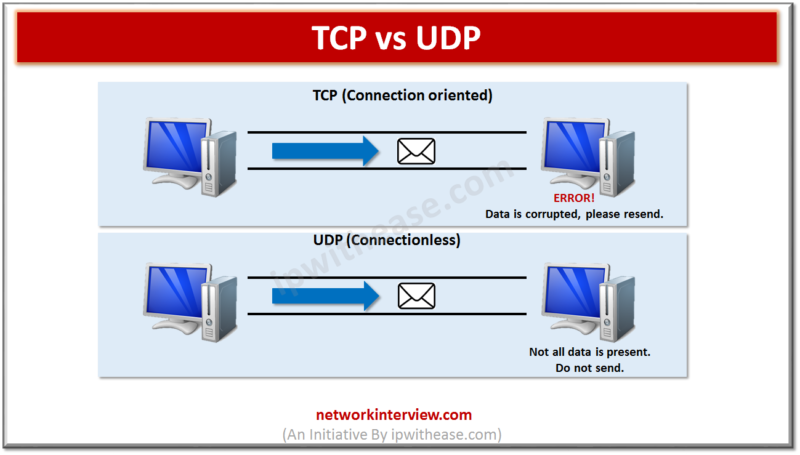
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two core protocols of the Internet Protocol (IP) suite. They differ significantly in their features, use cases, and reliability. TCP vs UDP Here’s a detailed comparison: 1. Connection Handling TCP: …
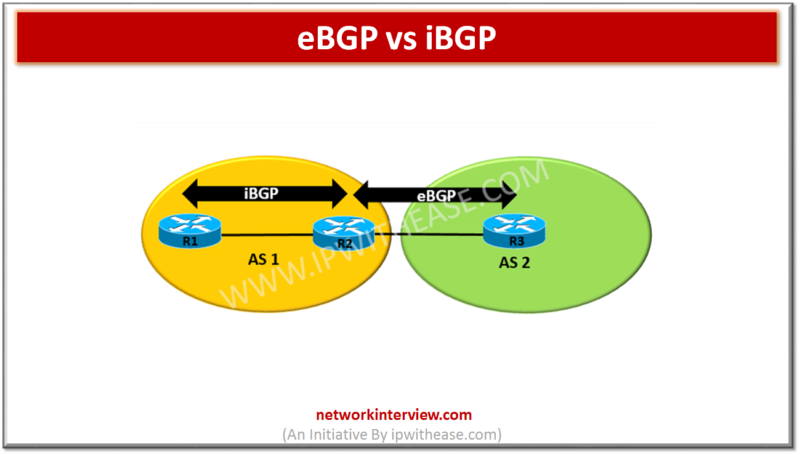
Before discussing eBGP vs iBGP, let’s understand the two protocols briefly. What is eBGP It is abbreviation for External Border Gateway Protocol and is one of the flavors of BGP protocol. eBGP Routing protocol is used between BGP speaking neighbors …
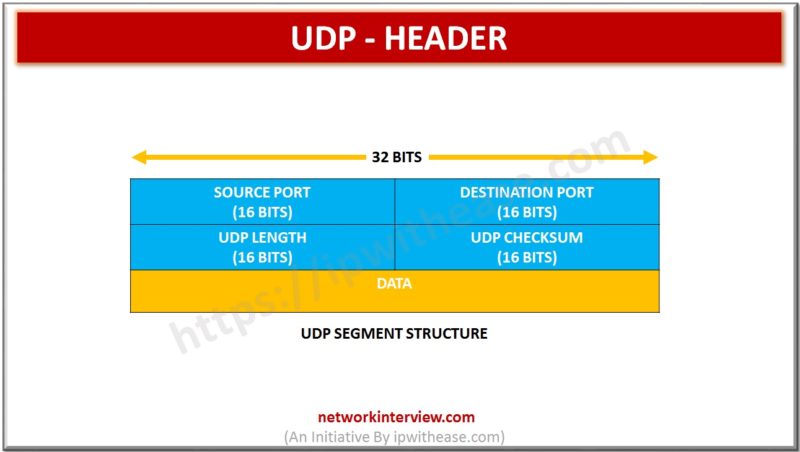
UDP HEADER It consists of four fields each of 2 bytes in length – Source Port(16 bits) – This field identifies the sender’s port. Cleared to zero if not used. Destination Port(16 bits) – This field identifies the receiver’s port. …