Are you buying a new iphone? It’s always exciting to get a new smartphone. Isn’t it? But in all that thrill, we often forget to do the basics. So, if you are also looking for a seamless experience with your …
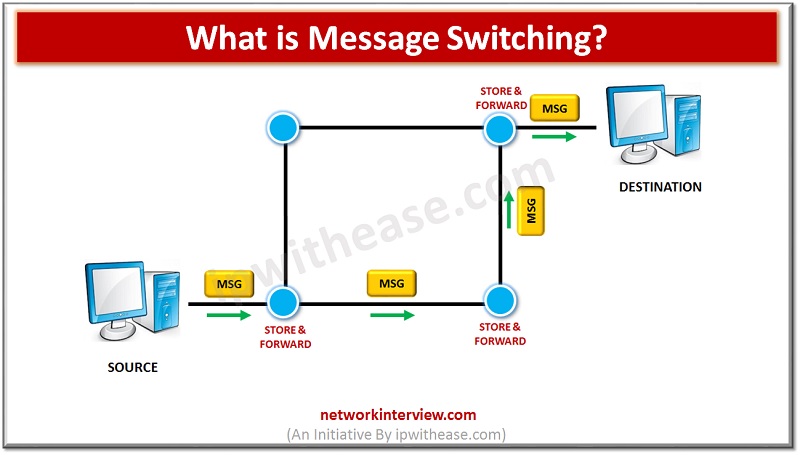
Introduction to Network Switching Before understanding Message Switching, let’s explore the basic types of switching. Switching is an important mechanism that provides communication between different networks or different computer(s) and manages the data flow between the two end points. There are …
LOOKING FOR A JOB IN CLOUD COMPUTING? Check out the Top Cloud Computing Certifications Today’s tremendous growth in Information Technology (IT) proves the importance of Cloud Computing. Industrialists say “the cloud computing is in the starting phase and expected to …
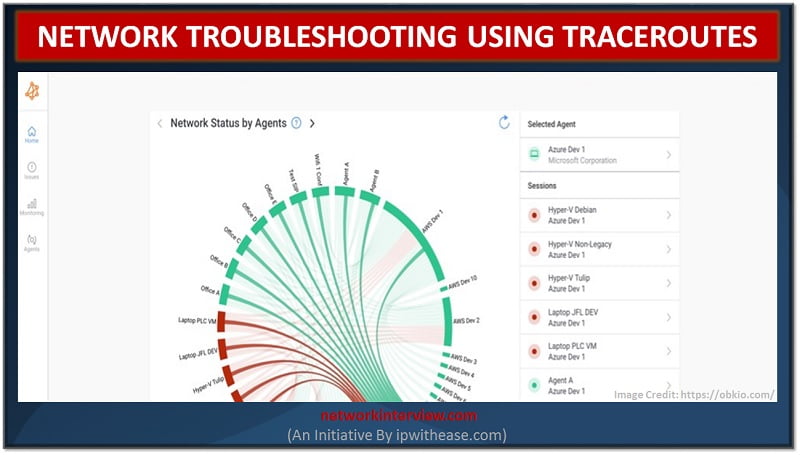
Any network engineer knows that when it comes to troubleshooting network problems and monitoring network performance, there are a variety of tools to help. Different tools play different parts in the troubleshooting process, so it’s important to understand what they …
Cloud Architect: Skills & Responsibilities With Cloud technologies showcasing a mushroom growth in the IT world and all the types of organizations (whether financial, manufacture or retail etc) moving the workloads to cloud, buffet of new roles and responsibilities have …
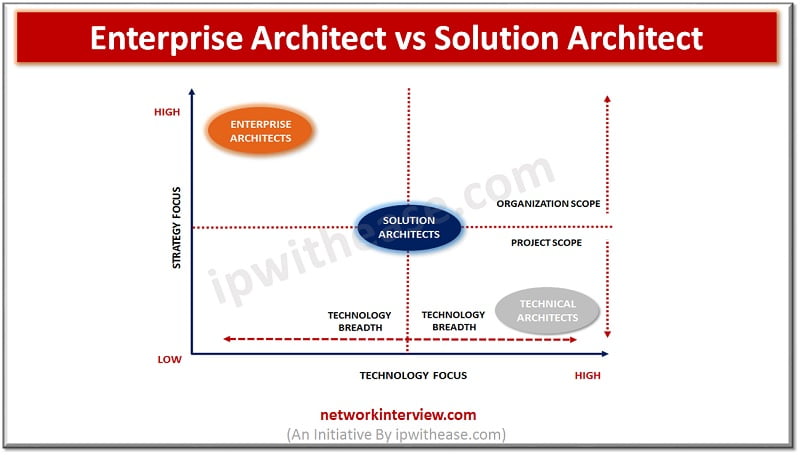
Enterprise Architect vs Solution Architect There are some key IT roles in organizations which focus on strategic and technology related aspects across their breadth and depth. Two such technical roles are of Enterprise Architect and Solutions Architect. While the former …
Difference Between MD5 and CRC MD5 and CRC are 2 of most commonly used hashing algorithms, infact while comparing files and including other use cases. In this article. We will understand both the concepts of hashing algorithm and how one …
Blockchain (Bitcoin Cryptocurrency) Technology Blockchain can be understood as “block of chains”, where the records or blocks are linked by cryptography. Each block (record) has a cryptographic hash of previous block (including a timestamp, and transaction data). Blockchain was introduced …
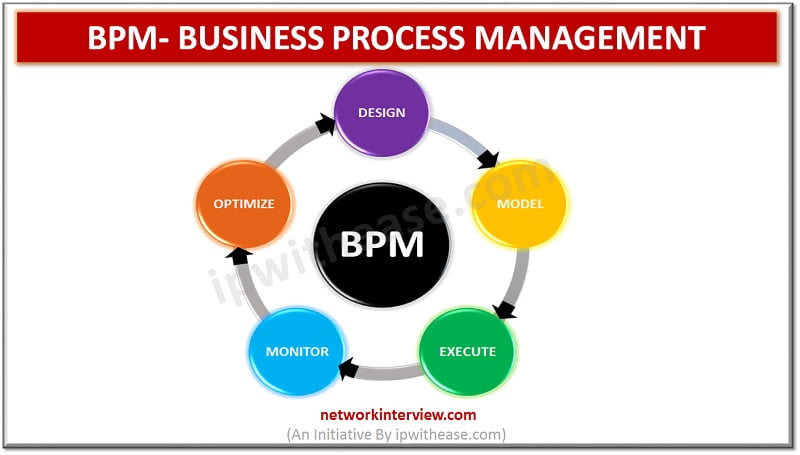
Business Process Management (BPM) Business process management (BPM) is a regulation that uses different tools and methods to design, model, execute, monitor, and enhance business processes. A business process correlates the behavior of people, systems, information, and things to bring …
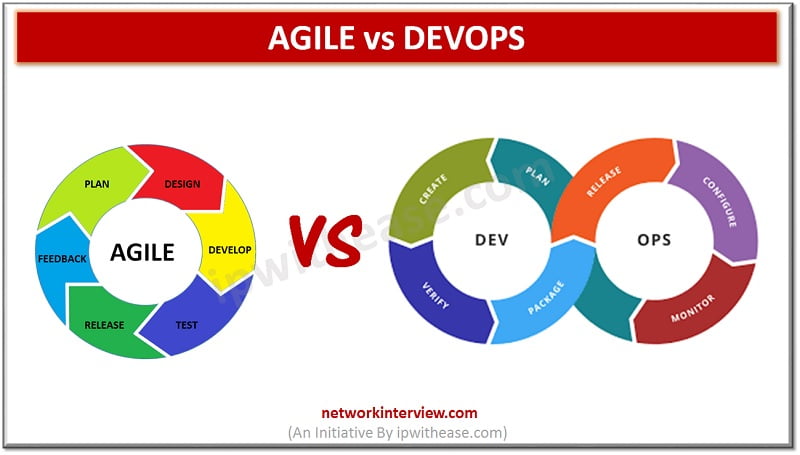
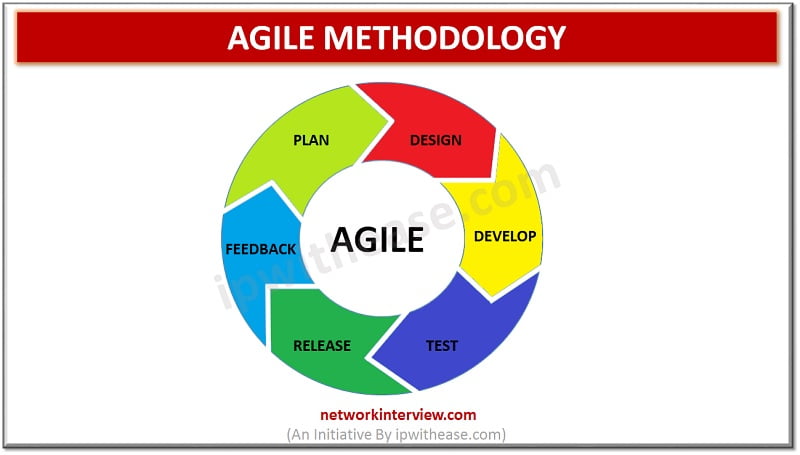
Difference between Agile and DevOps (Agile vs DevOps) What is Agile Methodology? Agile methodology points to a software development methodology consolidated to the idea of repetitive development, where requirements and solutions develop through fraternizing between self-organizing and cross-functional teams. The utmost …
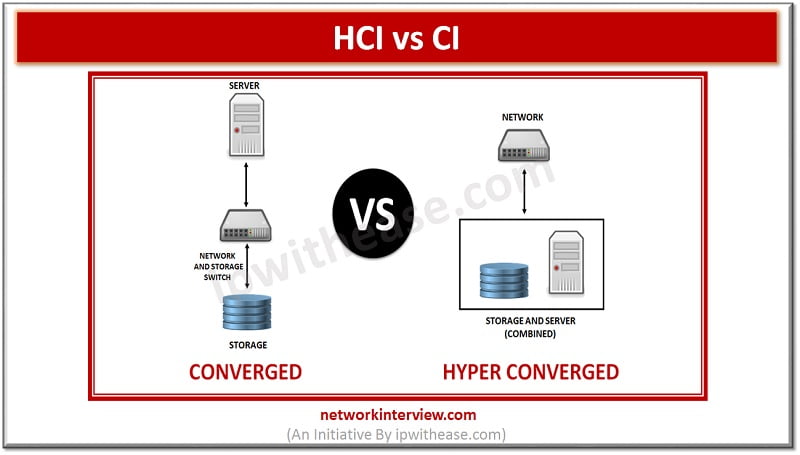
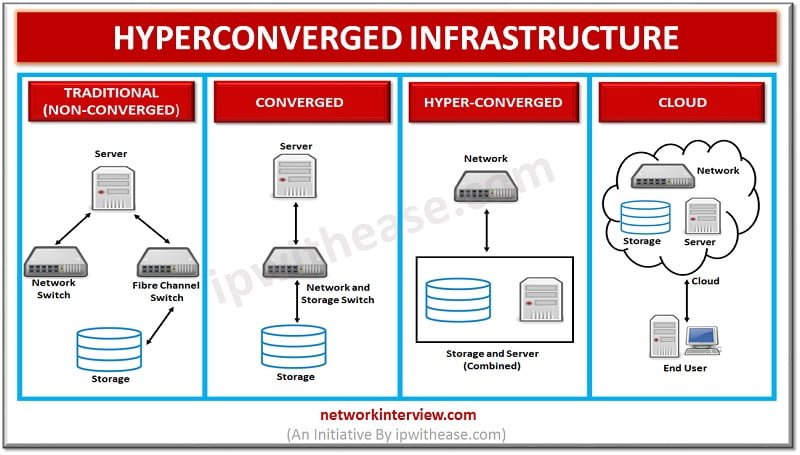
Hyper Converged Infrastructure (HCI) Vs Converged Infrastructure (CI) Hyperconvergence has been at the forefront of customer demand nowadays. Underpinned by virtualization technology, Hyperconvergence is gradually making strong hold in the IT world. In this article, we will talk through 2 …
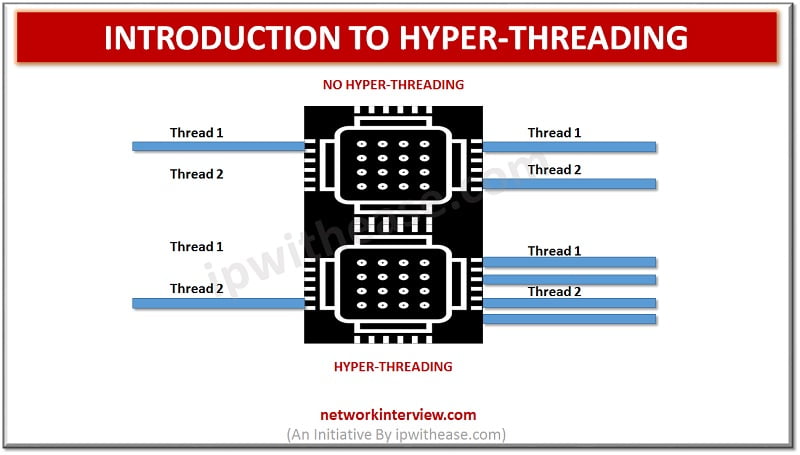
What is Hyper-Threading? Hyper-Threading (HT) concept was introduced by Intel on desktop CPUs with the Pentium 4 HT. Pentium 4 is a single CPU core and cannot perform multi-tasking and in order to address this situation, Hyper threading allows the …
What is Agile Methodology? Agile methodology points to a software development methodology consolidated to the idea of repetitive development, where requirements and solutions are developed through fraternizing between self-organizing and cross-functional teams. The utmost value in Agile development is that it …
Hyper Converged Infrastructure Vendors Multiple Vendors offers Hyper Converged Infrastructure (HCI). Before we discuss on vendors involved, a quick definition of HCI should provide a good understanding of the technology in discussion – Hyper Converged infrastructure integrates compute, storage and …
Colocation vs Carrier Neutral Data Center With introduction of new infrastructure services focused at providing smooth application access for customers, there have been new and improved cost effective solutions w.r.t Data Center Infrastructure services like power, space etc and Multi …
Introduction to Hyper Converged Infrastructure (HCI) Hyper Converged Infrastructure (Also called HCI in short) combines storage, computing and networking into a single system to reduce complexity and increase scalability. Hyper Converged platforms use a hypervisor for virtualized computing, software-defined storage …
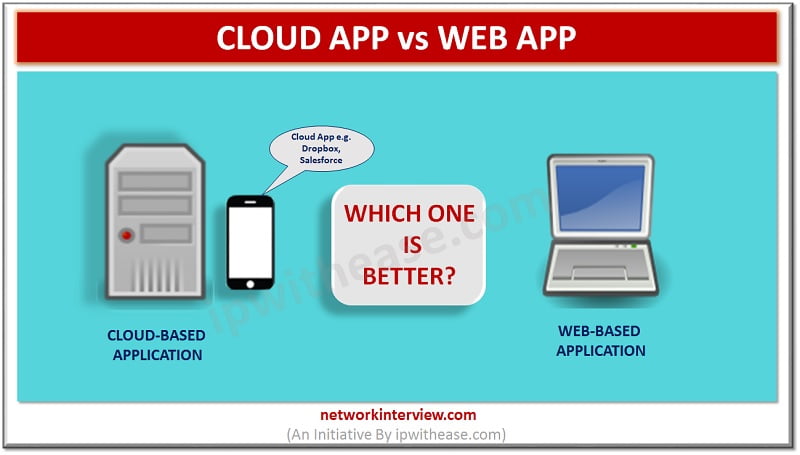
Cloud App vs Web App What is a Cloud App? Cloud App is an application that operates through the cloud and has some characteristics of both desktop apps and web apps. Cloud App is a more advanced web app. It’s …
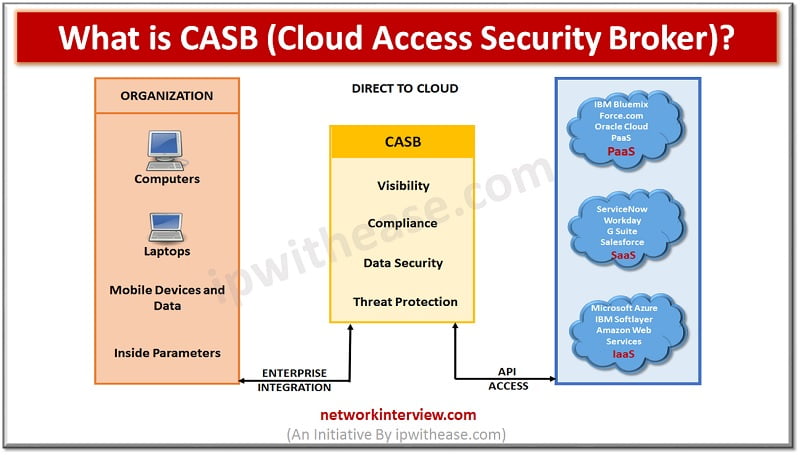
What is CASB? Cloud access security brokers (CASBs) is a cloud hosted solution placed between cloud service consumers and cloud service providers to implement security, compliance and governance security policies for cloud applications. CASBs help organizations to extend the security …
NSLookup Command NSLookup Overview NSLookup (Name Server Lookup). NSlookup is a simple but very practical command-line tool which is used to find DNS records, or in other words, IP address that corresponds to a host or the domain name that …
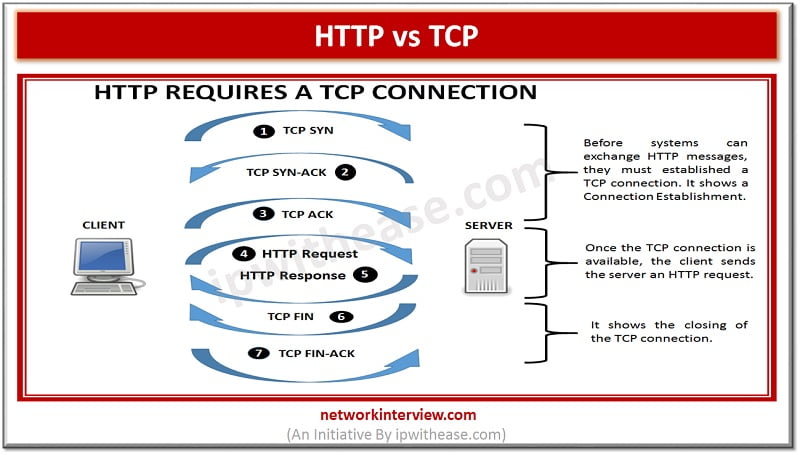
Before discussing the difference, let’s understand the two terms first What is HTTP? HTTP is a Hypertext Transfer Protocol. HTTP works similar to other application services like SMTP and FTP. Like the performance of FTP, it transfers a document using …
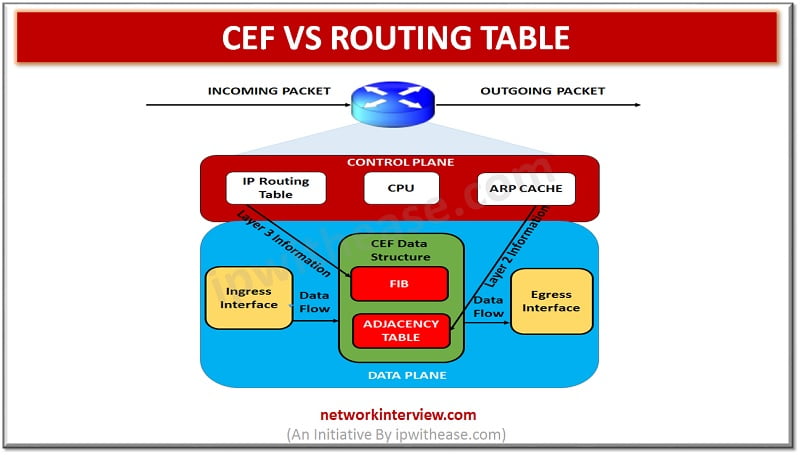
CEF vs Routing Table RIB (or routing table) and CEF (Cisco Express Forwarding) are two different tables which are used in routing across IP networking platform. Both have common information but perform two distinctly different purposes. CEF technology is new in …
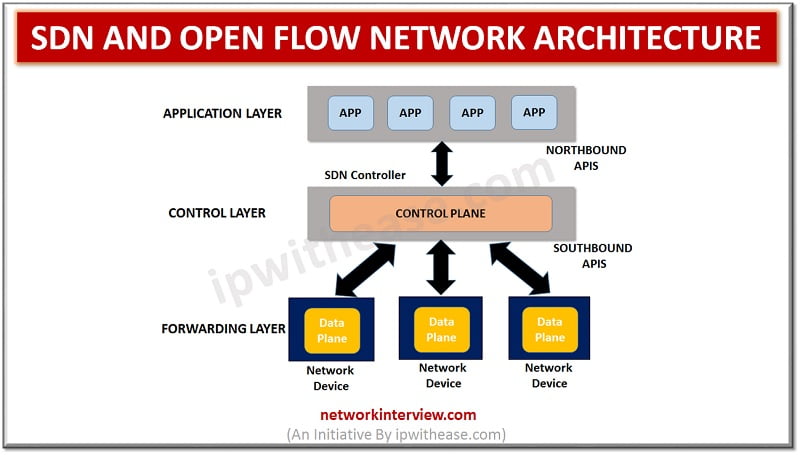
SDN and Open Flow Network Architecture With colossal growth in Cloud computing and Intent based networking, SDN technology has clearly lead the race. Infact SDN has also catered to needs of overgrowing demand on IT for faster response to requests …
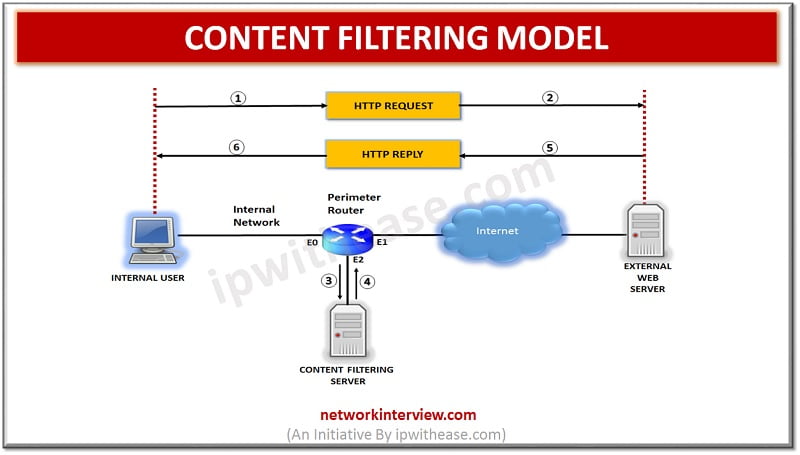
Overview Content filtering is essential to exclude access to web pages or email deemed objectionable. Content filtering is used by corporations as part of their security framework setup. Content filtering service boosts network security by blocking entry to suspicious websites …
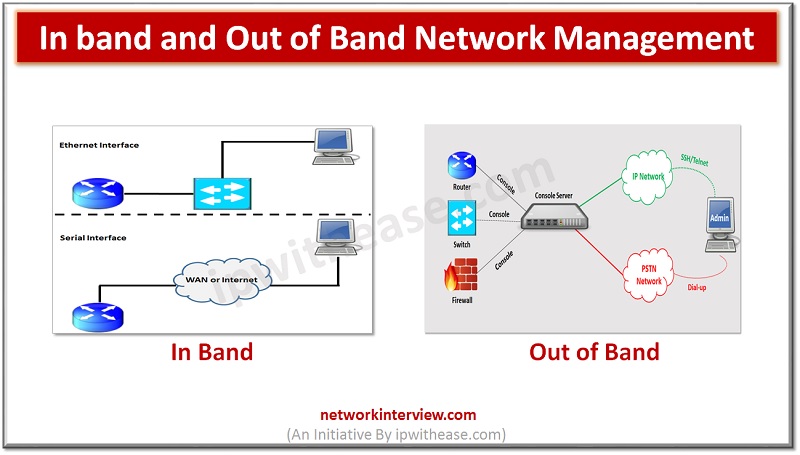
In this post, we will discuss about In band and Out of Band Network Management. The sequential order of subtopics is enlisted as below – Topics Understanding of Network Management In-band management Out-of-Band Management Comparison of In-band and Out-of-Band Management …
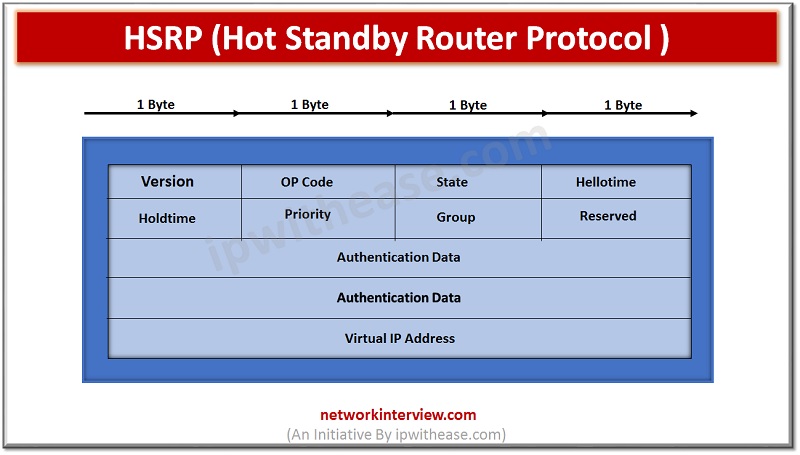
Hot Standby Router Protocol (HSRP) In this article, we will discuss on HSRP protocol, related terminologies, its operation and configuration. We will cover following points:- Topic Content Understanding FHRP Definition of HSRP HSRP Packet Key Points Operation and Configuration of …
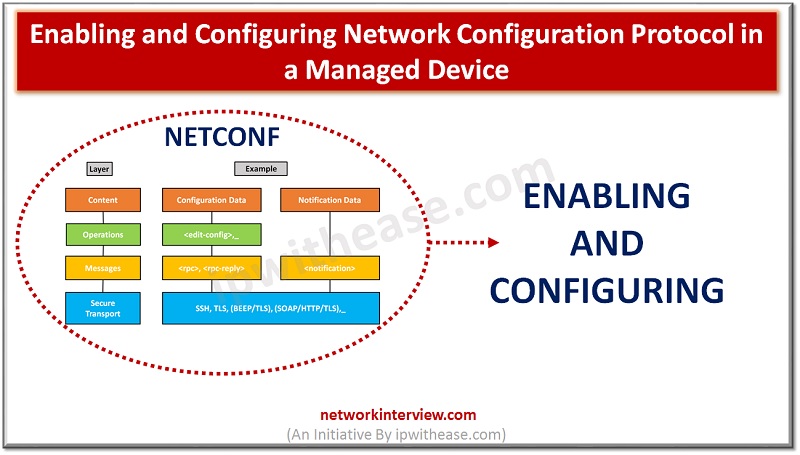
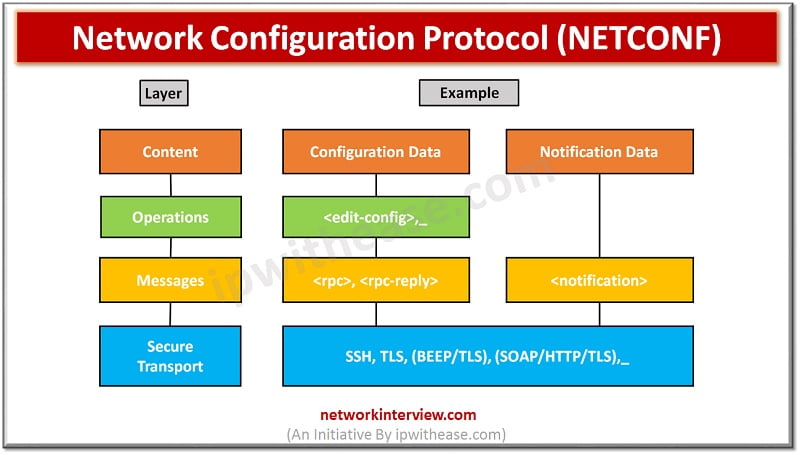
Enabling and Configuring Network Configuration Protocol NETCONF is a protocol that can manage, configure and install new configuration to network device. Its operations are realized on top of an easy Remote Procedure Call (RPC) layer. NETCONF uses Extensible Markup Language …
NETCONF Protocol – Network Configuration Protocol Network monitoring systems are tasked with ensuring the availability and performance of computers and network services and can detect and report on failures of devices or connections by deploying NETCONF/SNMP in device. Content of …
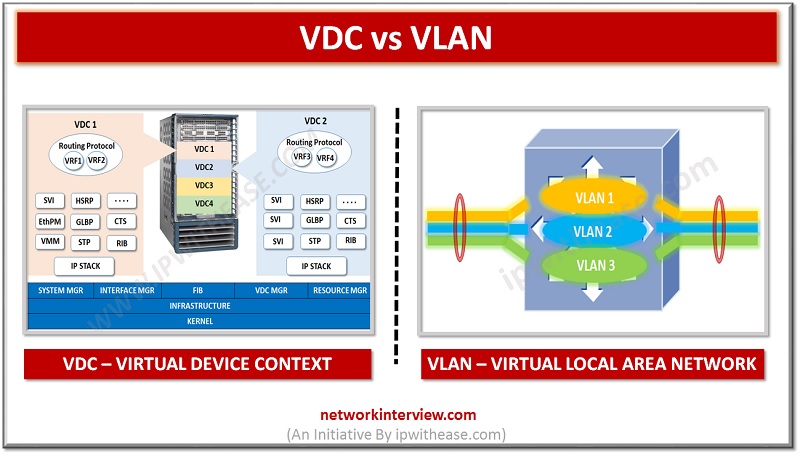
Introduction : VDC vs VLAN Virtualization in IT systems has helped Network estate immensely. 2 technologies which have helped networking across various segments are VLAN and VDC. While VLAN is short for Virtual Local Area Network, VDC means Virtual device …
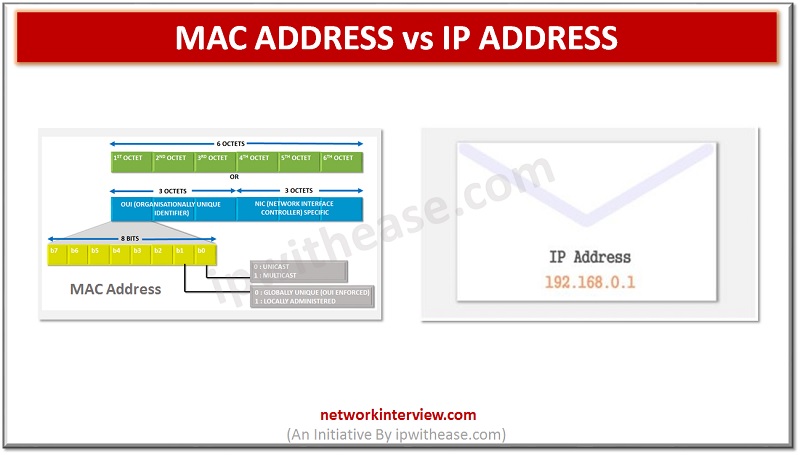
Introduction: MAC Address vs IP Address All devices part of a network can connect and communicate with each other. However, when we try to put logic around the communication between these devices, the key query that always arises in our …
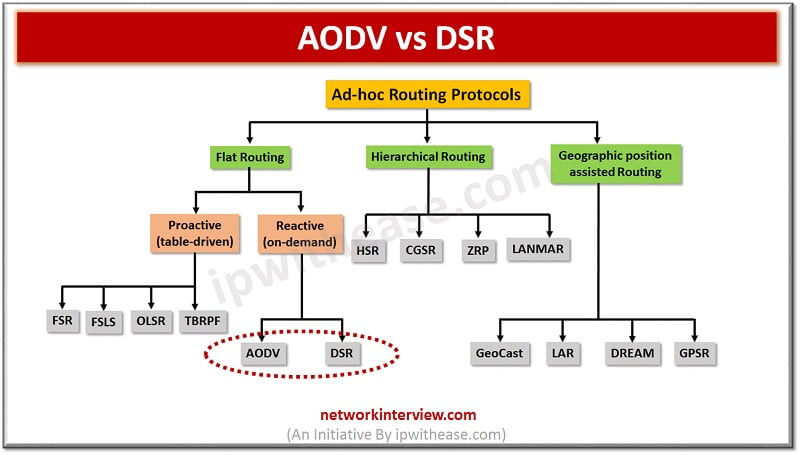
Difference between AODV Routing Protocol and DSR Protocol An ad hoc network or Mobile ad hoc network refers to a network connection established for a single session and does not require a router or a wireless base station. It does …
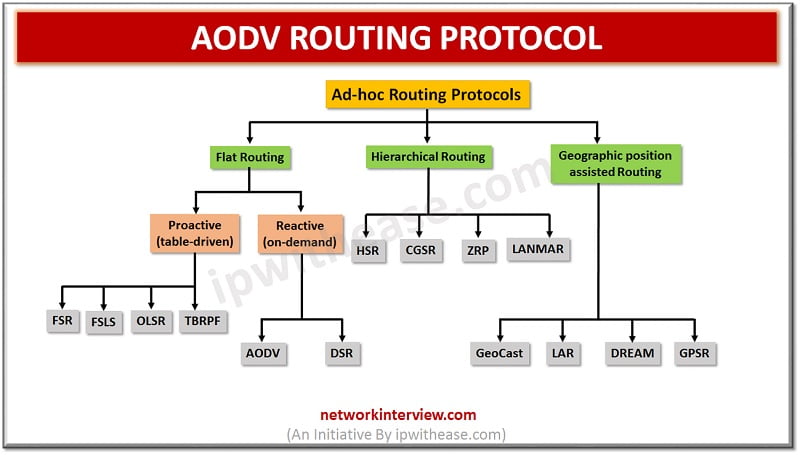
Hierarchy of Ad-hoc routing protocols In this article, we will understand the concept of AODV Routing protocol, which is type of Reactive (On-Demand) protocol. So, before beginning let’s understand what is a reactive protocol. Reactive Protocol Reactive Routing Protocol is …
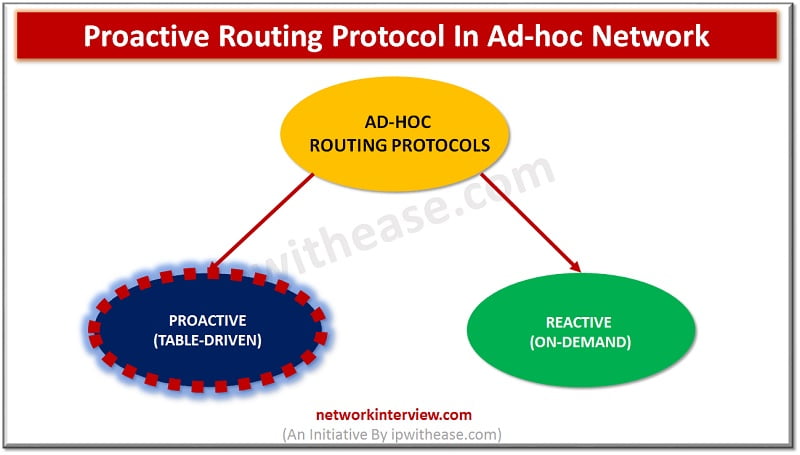
Proactive Routing Protocol Introduction Ad-hoc network is a collection of mobile nodes forming an instant network without a fixed topology. In such a network each node acts as both router and host simultaneously and can join or move out in …
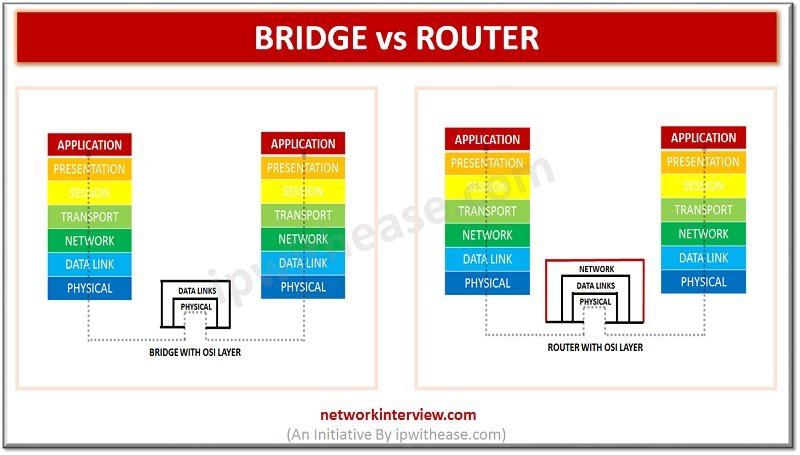
Network Bridge and Router are 2 key networking devices used in connecting segments or networks. While Bridge has been taken by switch, Router still remains the cornerstone of any WAN Network and has been expanding its role with introduction of …
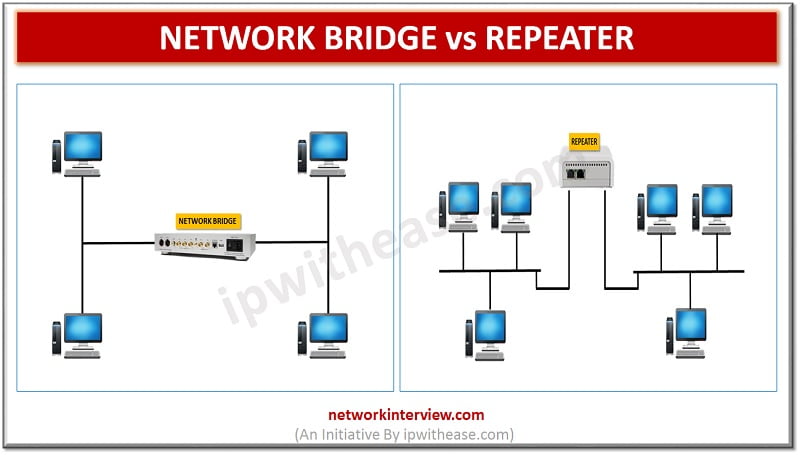
NETWORK BRIDGE vs REPEATER While working on networking concepts, network engineers may face challenge in understanding how Network Bridge and repeater are different and their working principles. In this article, we will touchbase on both the devices and compare their …
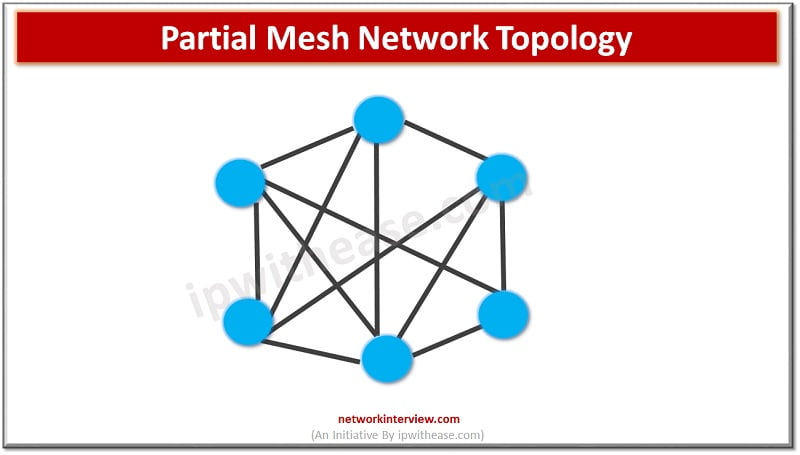
Different types of network topologies exist and based on multiple factors organizations can choose the best topology to suit them. Performance, Fault tolerance , redundancy, ease of error detection and correction, installation and configuration , scalability requirements, management and costs …
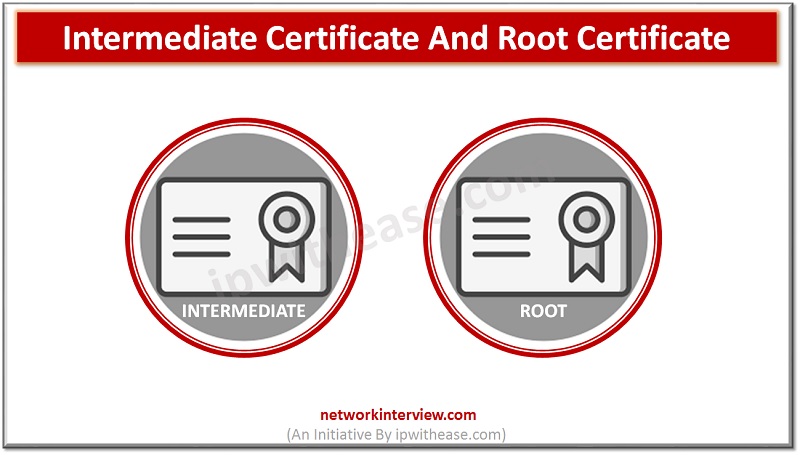
SSL Certificate types : Intermediate Certificate and Root Certificate When we look at the function of the SSL certificates at the first glance, then we would find that they are pretty straightforward. You would simply install it to your concerned …
Self Hosting simply denotes the fact that you own your website. It will provide you with unlimited capabilities to execute operations at your own level. In certain cases, where you are considering voluntary site operation as well as revenue generation …
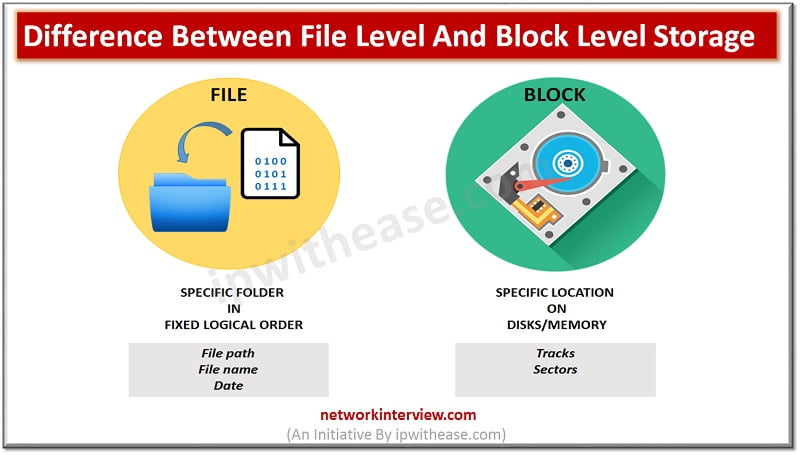
In this post, we will discuss the difference between File Level Storage and Block Level Storage. File Level Storage: The storage system of Network Attached Storage and hard drives is a file level storage. Here in this storage system, the …
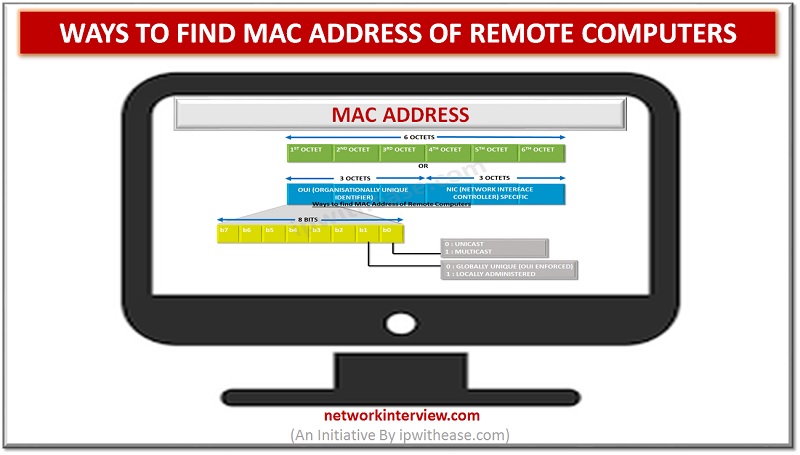
Ways to find MAC Address Network and System administrators are many times caught is issue of finding MAC address of some remote device in network. Physical validation of each device may be time consuming and very tedious activity. In this …
SSL SAN and its purpose The Subject Alternative Name or SAN is a form of extension to X.509 specification permitting users to stipulate additional host names for single kind SSL certificate. Basically, the SAN extension is a form of standard …
The invention of computer encouraged the mankind to take the giant leaps of aspiration with every passing decade. Right from putting first step on the Moon to measuring the nadir of the Earth at Mariana Trench, the contribution of computers …
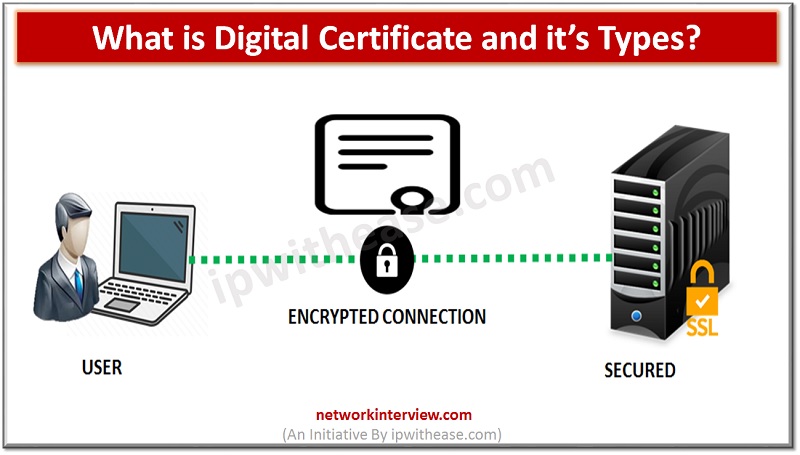
A digital certificate, which is also termed as public key certificate is applied to cryptographically link up the ownership of public key to the entity owning the same. Here, we are going to get a better insight of what is …
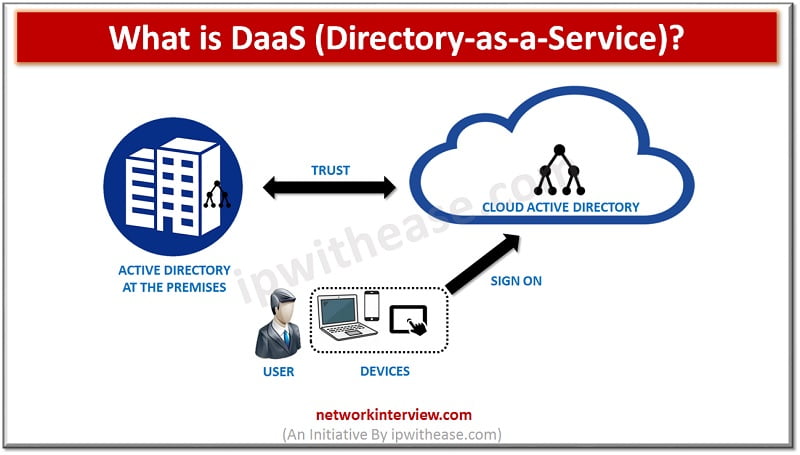
DaaS is one of the latest terms in the field of cloud computing that is going to be more prevalent in future. It stands for directory-as-a-service and here we will try to understand what is DaaS (Directory-as-a-Service) and how it …
IMPACT OF CORONAVIRUS ON IT SERVICE The coronavirus pandemic has brought the modern world on the verge of a catastrophe that it has witnessed never before. The pandemic has affected manufacturing, operational and services sector equally. It is true that …
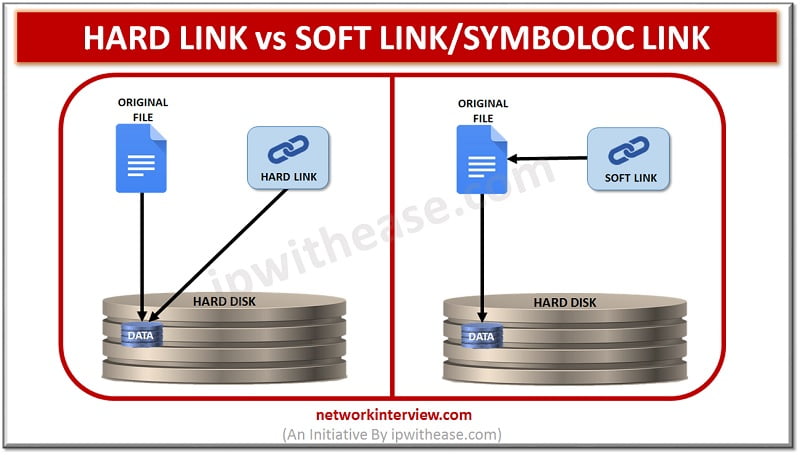
Hard link and Symbolic link Similar to the pointers in the programming languages, there are links in UNIX/LINUX which are just like pointers which point towards a directory or a file. To generate these links is like creating shortcuts for …