It is a fact that small businesses form the majority of all types of commerce in America, with over 99% of all industries being classed as operated by small firms. Put simply, small businesses account for the largest part of …
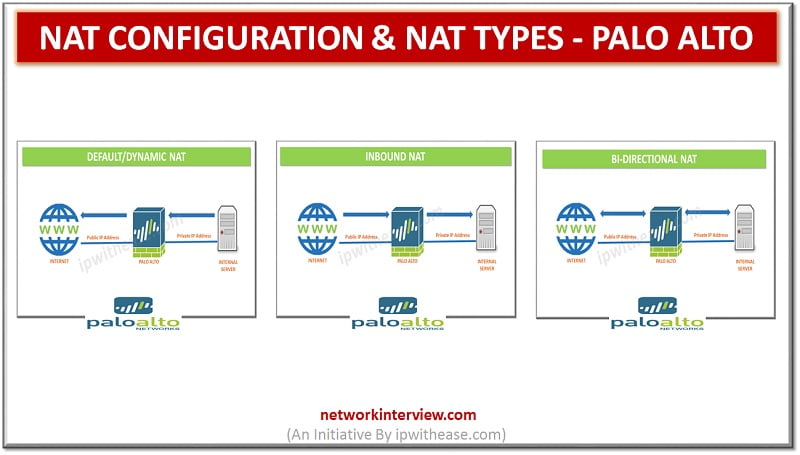
In the previous post we discussed the Architecture of Palo alto firewall. Now, we will discuss the NAT configuration and NAT types in Palo alto. Network Address Translation (NAT) allows to translate private, non-routable IP addresses to one or more …
Cyber security is an in-demand security measure that helps to protect enterprises, individuals, and their systems from online threats. It helps secure crucial data within computer devices and networks from unknown access. In this regard, Palo Alto Networks plays a …
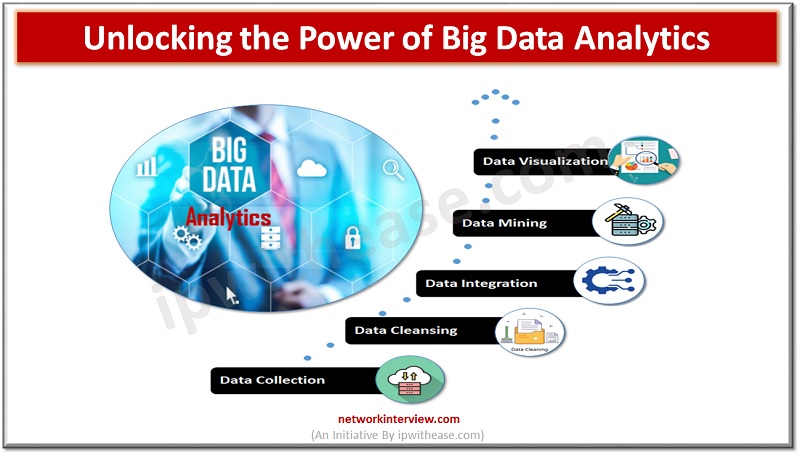
Big data analytics is the process of analyzing large and complex sets of data to uncover patterns and trends. As the amount of data continues to grow at an exponential rate, the need for big data analytics is becoming increasingly …
Nothing lasts forever, especially high-tech products like a laptop or computer. However, if you know how to care for it, your computer can survive for a very long time. This applies to both PCs and laptops. If your equipment malfunctions …
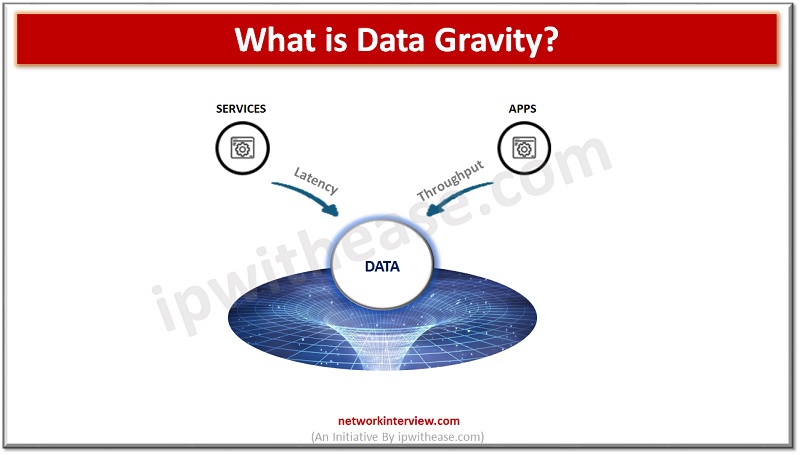
Data gravity is an increasingly important concept in the age of digital transformation, and understanding how it works, its benefits, and challenges is essential for all businesses. In this article, we’ll unpack the concept of data gravity and provide a …
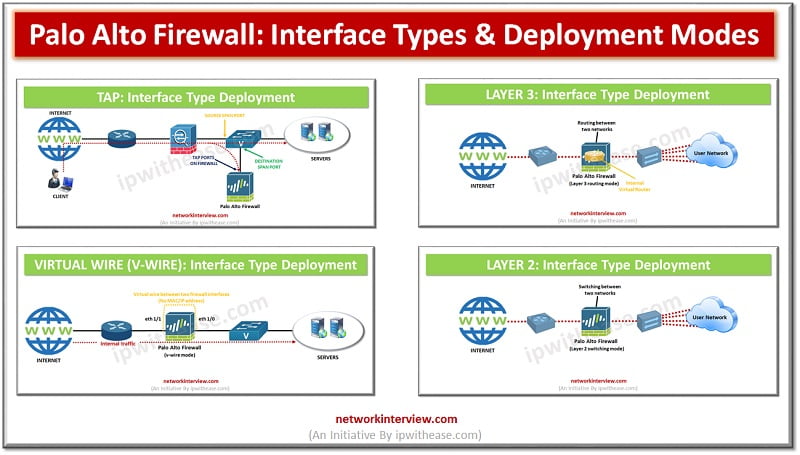
Introduction to Palo Alto Interface types/ Deployment Modes The entry and exit point of traffic in a firewall is enabled by the interface configurations of data ports. Palo Alto being a next-generation firewall, can operate in multiple deployments simultaneously as …
When it comes to software testing, there are two main approaches – manual testing and automated testing. Each one has its own advantages and disadvantages, and it can be difficult to decide which approach is best for your needs. In …
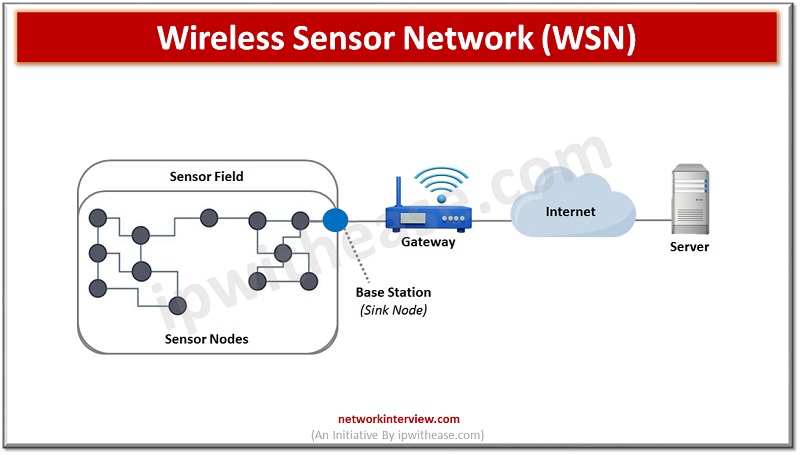
Wireless sensor networks (WSNs) have been around for decades, and their importance has only grown over time. WSNs are used for monitoring, gathering and transmitting data from various sources, such as temperature, humidity, air quality and more. They are also …
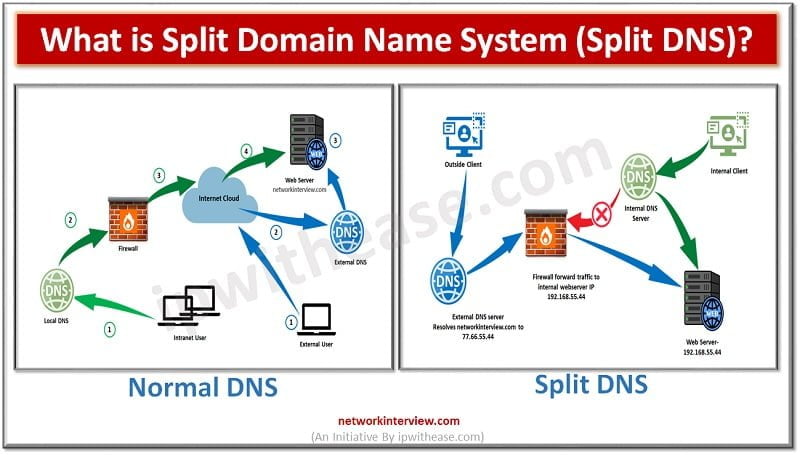
DNS Working Before understanding the Split Domain Name System, let’s discuss how normal DNS resolution works for Internet traffic. However, DNS works to resolve names to IPs. When an Internet client open a Web-browser and type www.networkinterview.com Internet Client will …
Smart contracts are computer programs that run on blockchain technology and execute automatically when certain conditions are met. They have revolutionized the way we think about contracts and are becoming increasingly popular in various industries. However, finding smart contract developers …
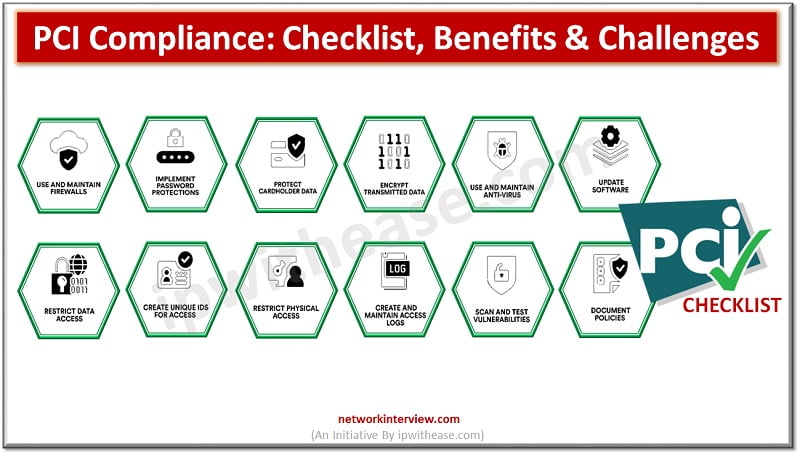
Whether you own a small business or manage a large enterprise, ensuring customer data security is a top priority. To that end, businesses must adhere to the Payment Card Industry Data Security Standard (PCI DSS), a set of security requirements …
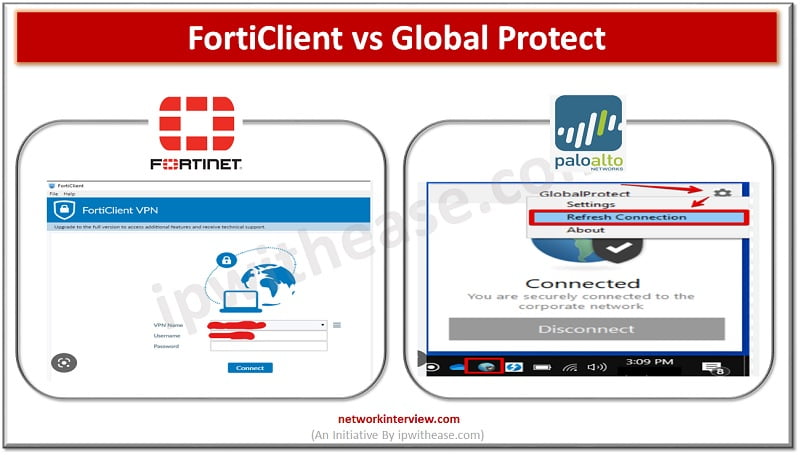
What is FortiClient? FortiClient is an app to provides UTM features like web filtering, giving web security and content-based filtering. FortiClient app is installed in the user’s system and tracks the traffic based on policy. The web application firewall offers malware …
You can keep tabs on your friends and family with the tap of a button using mobile phone tracking software. Yet, do you understand how these applications function? Or the many different methods that they can assist you in locating …
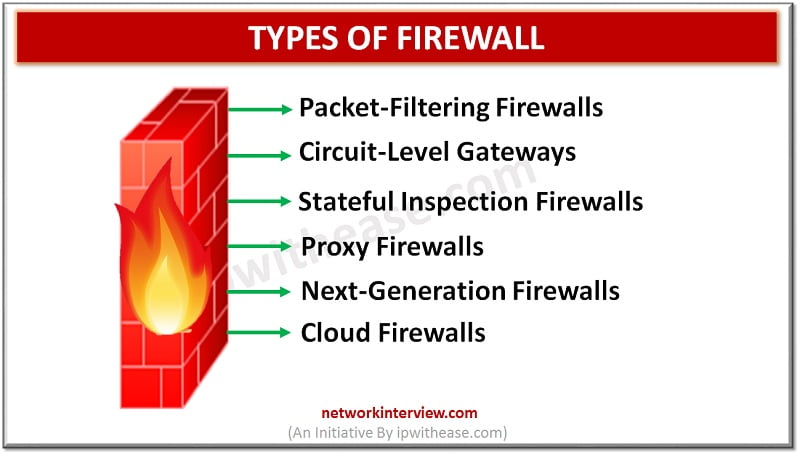
Introduction to Firewall In todays digital scenario, where businesses demand agility and information are hosted on cloud infrastructure security of data is one of the primary concerns of business and protection of data from unwanted sources is the prime objective. …
A decade after data scientists were labeled “the sexiest job of the 21st century” by Harvard Business Review in 2012, data scientists continue to be among the greatest and most sought-after job roles in the IT sector, making their way …
In 1996, Congress passed the HIPAA law to protect individuals’ health information. This federal act established national standards for how sensitive patient data should be stored and handled, requiring healthcare providers to meet these regulations. To make sure their practice …
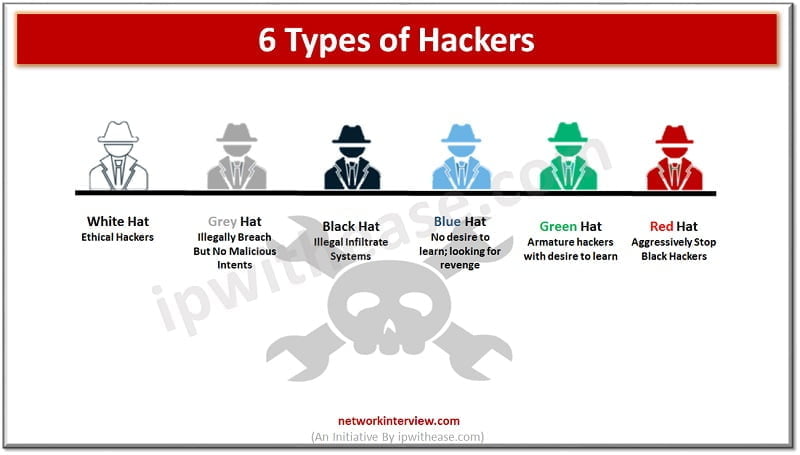
You must have heard the word ‘hacker’ multiple times in cybersecurity. The organizations have trained security staff to take care of cybersecurity threats. Hacking is generally referred to as someone gaining access to your network and systems by unauthorized means. …
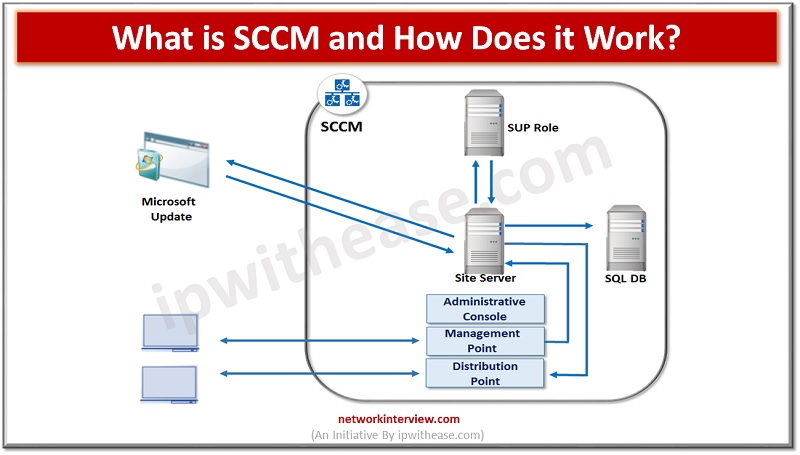
Configuration Manager, commonly known as SCCM, is a powerful and versatile tool created by Microsoft. It provides IT professionals with an integrated platform to manage and deploy software, hardware, and other resources across their networks. In this blog, we’ll take …
With the rise of technology and the internet, the world has become more connected than ever before. From online shopping to social media, we rely heavily on technology in our daily lives. While technology has made our lives easier, it …
In today’s digital world, the need for brand protection is more important than ever. With the rise of online marketplaces and e-commerce websites, counterfeiters have found a way to exploit brands and make money off of fake products. To combat …
Maintaining the security of your personal or business network and Internet connection is essential in today’s digital world. With the rise of sophisticated cyber threats, identity theft, and data breaches, protecting yourself from potential risks is becoming more critical than …
It is not possible to safeguard your DVDs data always, because there are chances and possibilities for the DVD to get damaged. After getting damaged it is not an easier task for you to recover the file and data that …
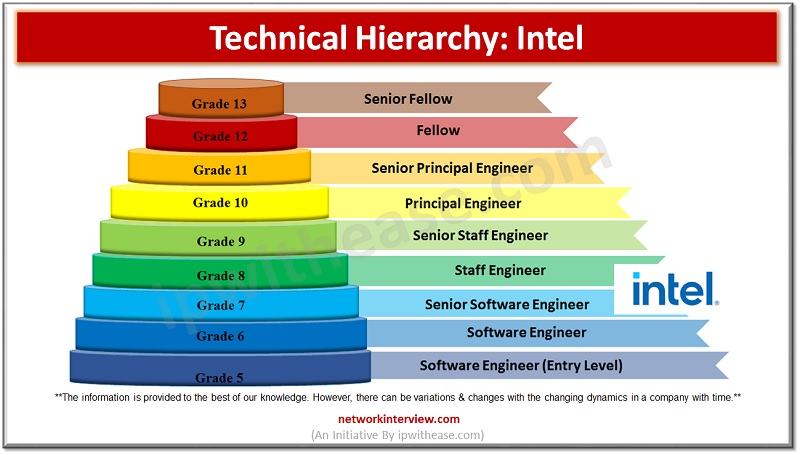
Getting a job in an MNC is always the dream of aspiring new Engineers and developers. But oftentimes, the hierarchy and job positions mentioned in the Interview make them confused and they land on a position lower or higher to …
Screening and interviewing tech candidates in Latin America requires a specific set of skills and considerations. One of the first steps is to understand the concept of nearshore development, which refers to outsourcing software development to neighboring countries with similar time …
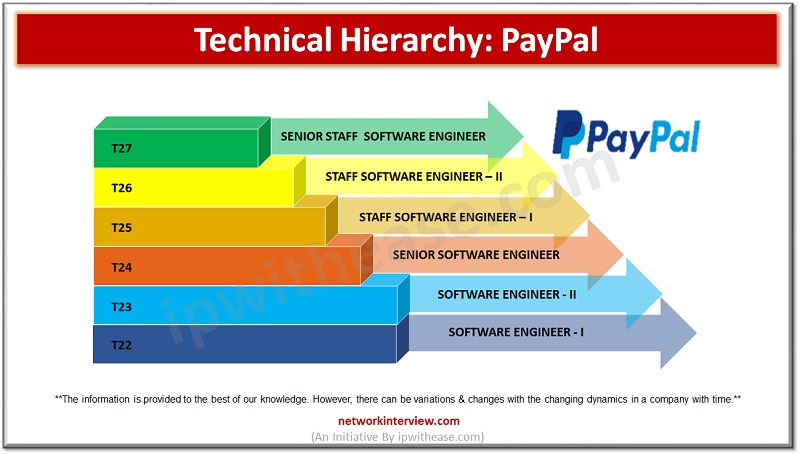
It is a dream for many graduating Software engineers to land a job at PayPal. The main reason is its global availability and promising salary and other benefits. Are you one of them? Then you should consider certain things first. …
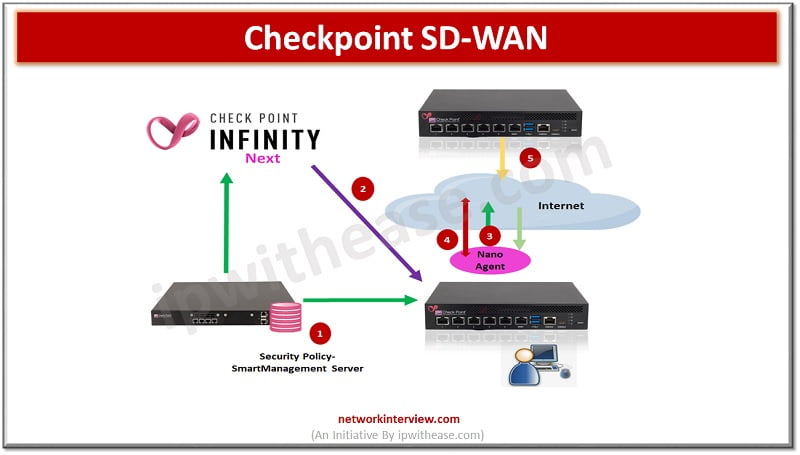
Note: This document is for those seekers who have prior knowledge of SD WAN and want to enhance SD WAN concept in Checkpoint perspective. This blog covers below topics of Checkpoint SD WAN: Quantum CheckpointSD-WAN concept Architecture Application basic traffic …
Fans of podcasts are always on the lookout for an incredible platform on which they can listen to their favorite shows without running into any problems. They all want hassle-free apps with appealing features. Inarguably, the number of fans of …
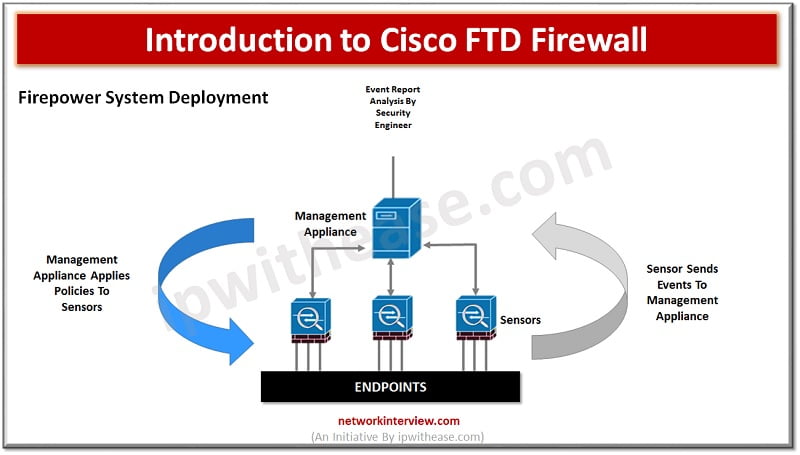
figure:1 As more and more systems are Internet facing due to high penetration of cloud and associates’ applications and services, the need for a very strong security system at perimeter or gateway to enterprises is becoming more and more crucial. …
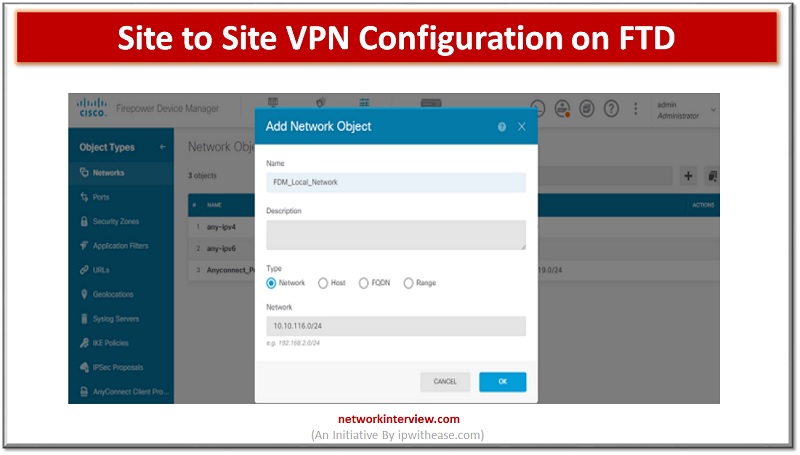
VPNs allow access to restricted sites with secure connection. In FirePower devices we can configure site to site VPN on FTD devices. The site to site VPN is configured for FTD devices using the FirePower Defence management console. In today’s …
Site-to-Site VPN Overview A VPN connection that allows you to connect two Local Area Networks (LANs) securely is called a site-to-site VPN. Route based VPN can be configuring to connect Palo Alto Networks firewalls located at two sites or to …
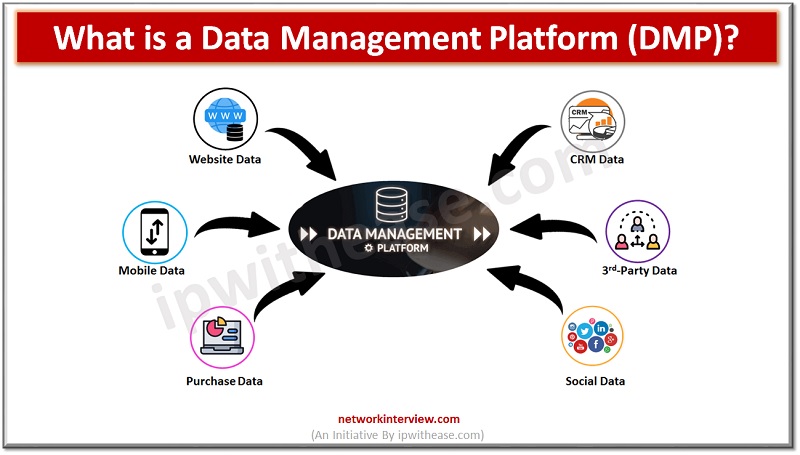
In today’s digital age, data is everything. From businesses to individuals, having access to the right data can make all the difference in making decisions and optimizing processes. Data Management Platforms (DMPs) are powerful systems that enable organizations to manage, …
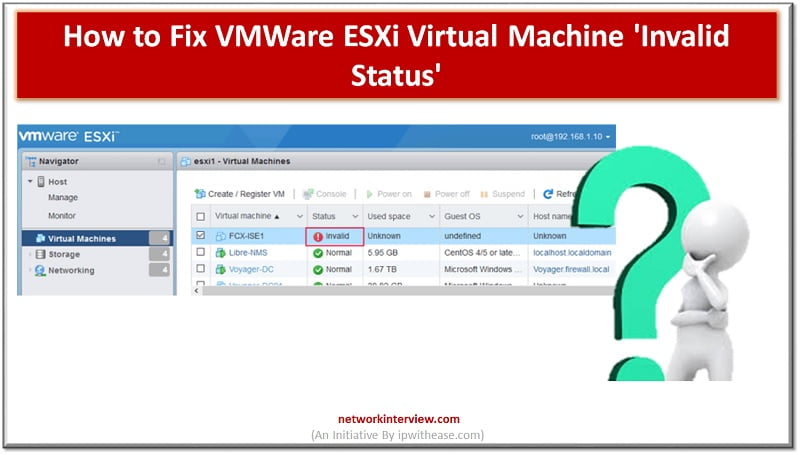
Troubleshooting VMWare ESXi Virtual Machine ‘Invalid Status’ Let’s troubleshoot VM Invalid status You can see multiple “invalid” VM machines in the image below. Here status is showing invalid. Reason of Invalid VM Machine status could be related to the storage …
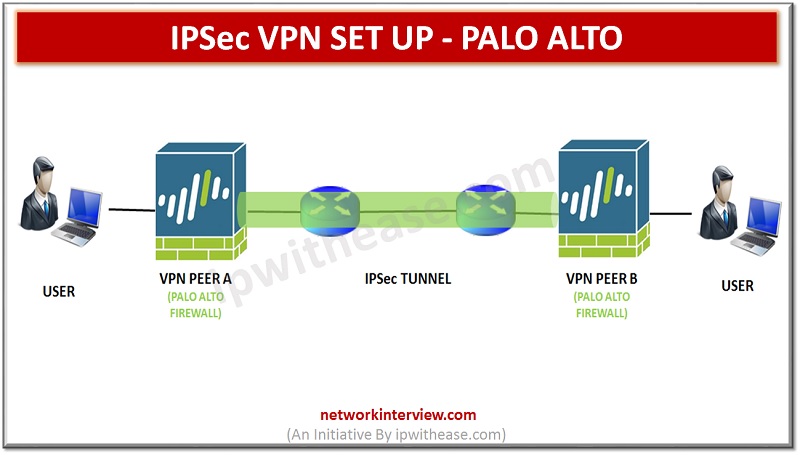
Overview In our previous article, we studied IPSec VPN Set Up. In this article we will run through CLI commands and GUI steps to configure an IPSec VPN, including the tunnel and route configuration on a Palo Alto Networks firewall. …
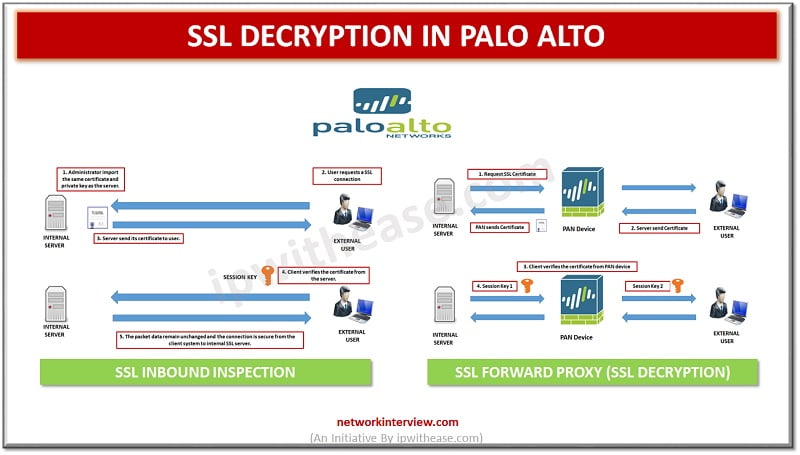
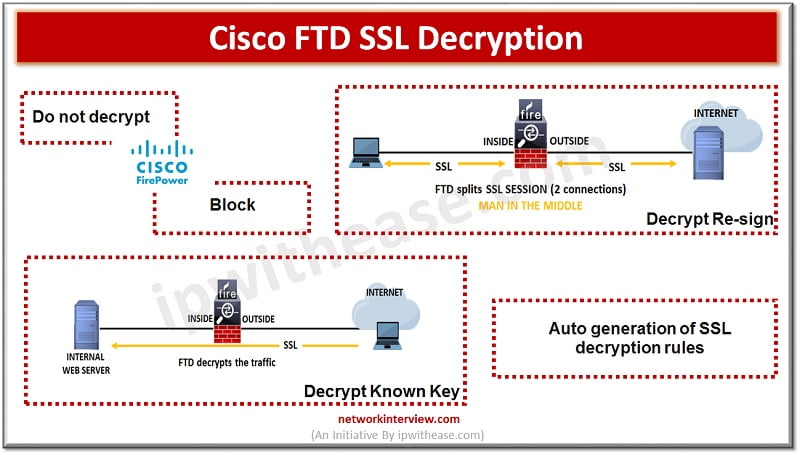
Before digging deep into Palo alto SSL Decryption, let’s first understand what is Decryption? What is Decryption? Palo Alto firewalls can be decrypt and inspect traffic to gain visibility of threats and to control protocols, certificate verification and failure handling. …
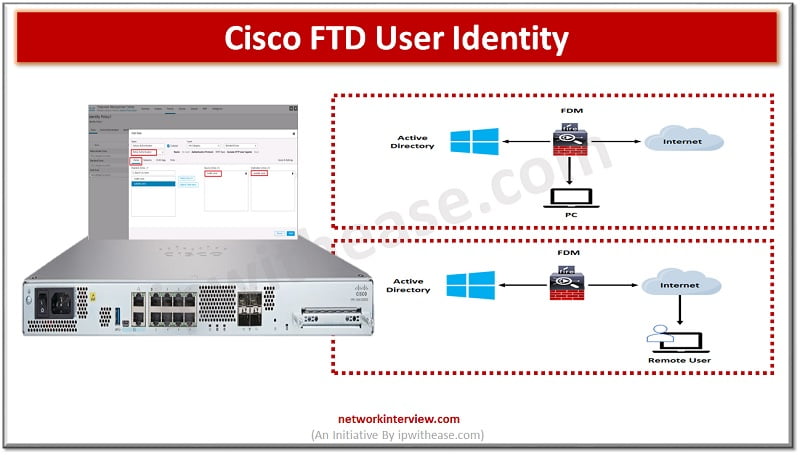
User identity information helps to identify the source of policy breaches, attacks or network vulnerabilities and trace them to specific users. Majority of traffic inspection products support filtering based on IP address. However, Cisco FTD identity policy feature gives the …
Web development is an area in which companies have taken a serious turn in the past few years. With the help of the Internet and modern techniques, enterprises have become extremely successful and popular among online customers. The world has …
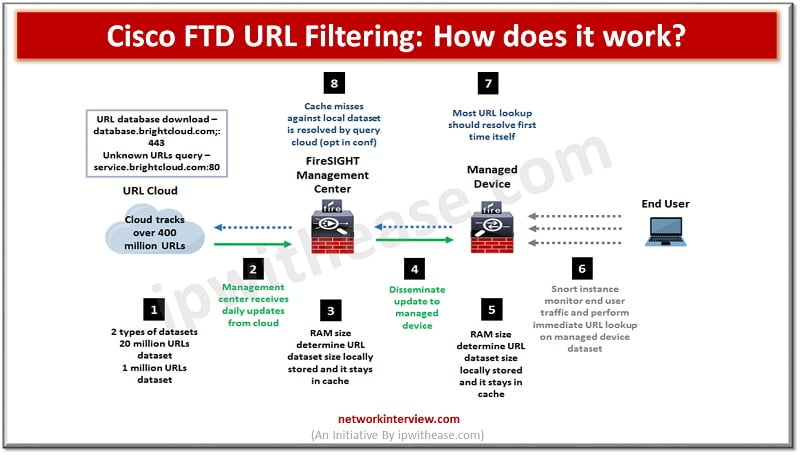
Pic: Showing How Cisco FTD URL Filtering works URL filtering or content filtering is one of the key features of firewalls. It helps to prevent access to harmful and malicious content which could cause data loss, system crash, virus or …
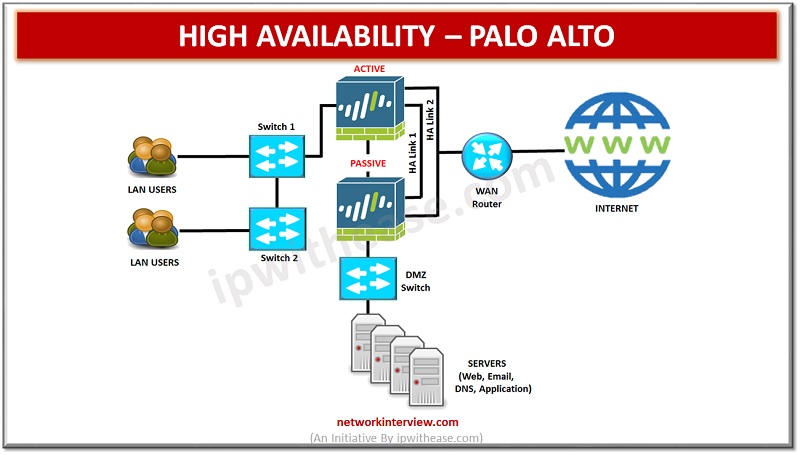
High availability (HA) refers to a system or component that is operational without interruption for long periods of time. High availability (HA) is measured as a percentage, with a 100% percent system indicating a service that experiences zero downtime. High …
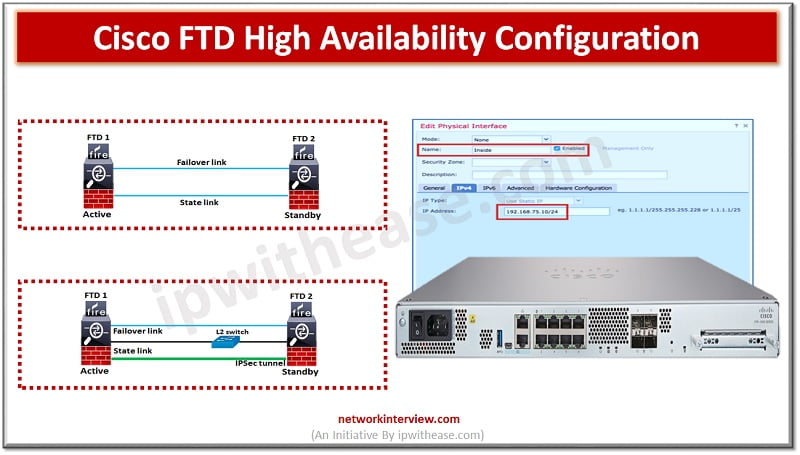
To ensure uptime and continuous availability in the event of disaster is a required key feature for any production environments be it servers, networks and other computing equipment. All Cisco devices majority support high availability (HA) also known as failover. …
Some protocols like HTTPS use Secure socket layer (SSL), transport layer protocol (TLS) to encrypt traffic for secure transmissions. As the system cant inspect encrypted connections we first must decrypt to apply access roles which consider higher layer traffic characteristics …
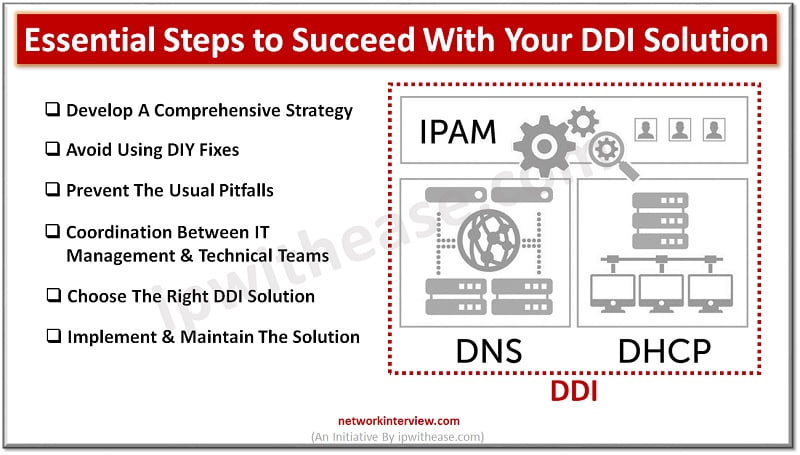
The acronym DDI stands for DNS, DHCP, and IP address management (IPAM). The combination of these three crucial networking elements into a single management solution is referred to by this widely used acronym. A DDI solution offers a centralised platform …
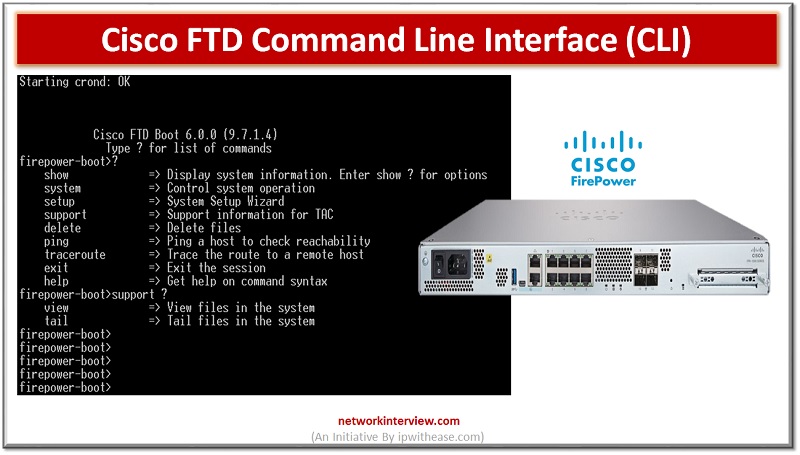
Majority of Cisco devices provide command line interface (CLI) as we call it to configure, manage and troubleshoot devices. Use of CLI allows users to execute Cisco IOS commands directly and simply as well as via remote access. In today’s …
“Cloud is Everywhere.” Yes, if you are reading this article, you are using cloud services directly or indirectly. In other words, cloud computing services are crucial to everyone’s daily lives. In fact, a number of titans of the digital industry …
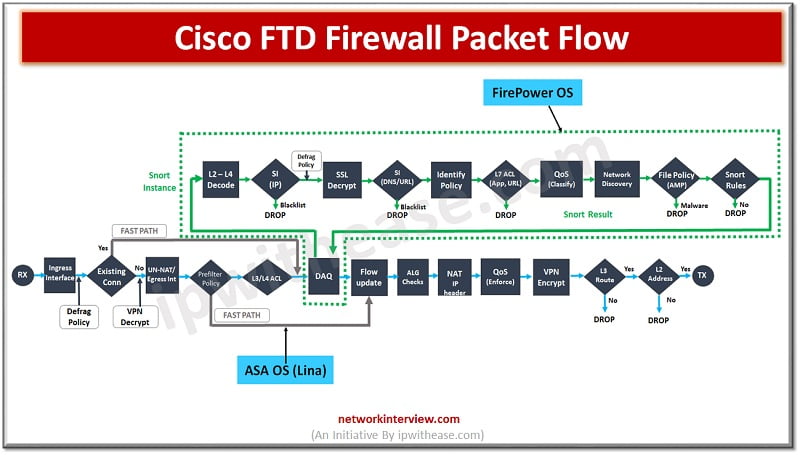
In the evaluation of next generation firewalls (NGFW), the next leap made by Cisco FTD is (Unified Firepower threat defence) software which includes not just NGFW but also Next generation Intrusion prevention systems (NGIP), Advanced Malware protection (AMP) and many …