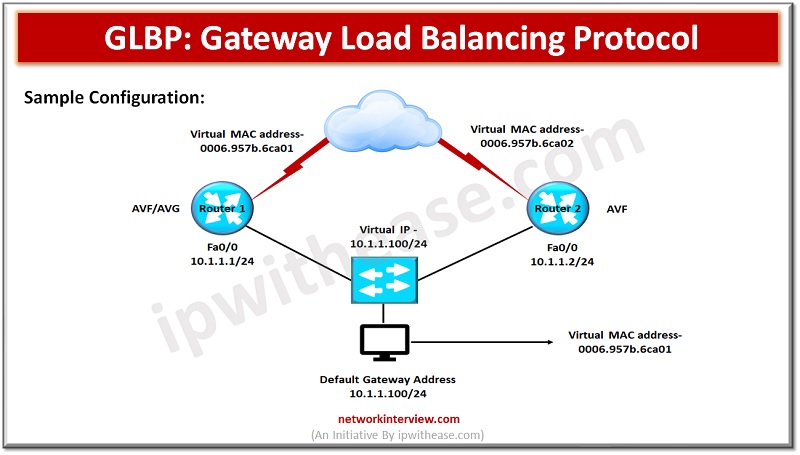
Introduction to Gateway Load Balancing Protocol Load balancing is one of the key requirements in networks and it can be achieved in several ways such as round robin, host dependent and weighted. Protocols supporting load balancing have the capability to …
Objectives Routing in Fortinet FortiGate Configuration Steps of Static Routing Configuration Steps of Dynamic Routing (BGP) Policy Base Routing Routing Monitor GUI Troubleshooting Commands for Routing in FortiGate Routing in Fortinet FortiGate Firewall Routing means how a packet can …
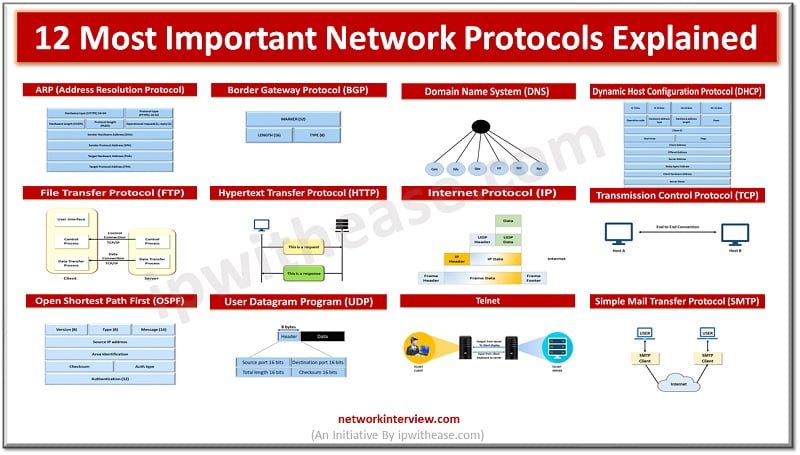
Network protocols establish rules of communication to control and govern exchange of information following secure, reliable methods. These are a set of rules designed to have a standard framework for interchange over networks. There are a variety of network protocols …
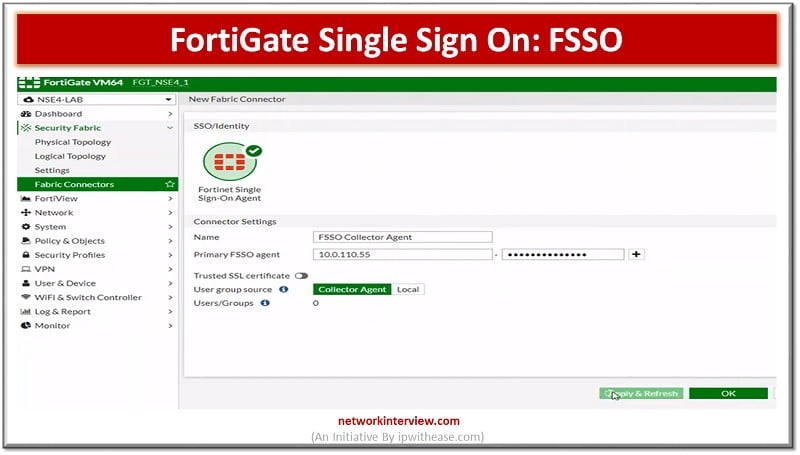
Single Sign On & FortiGate Single Sign On Single Sign On (SSO) is a process that allows users to automatically log into every application after being identified, regardless of platform, technology, and domain. FortiGate Single Sign On (FSSO) is a …
Hiring the right candidates for a vacant job position is crucial for any organization’s success. The process of finding the perfect fit can be daunting, as it requires a delicate balance of skill, experience, cultural fit, and potential for growth. …
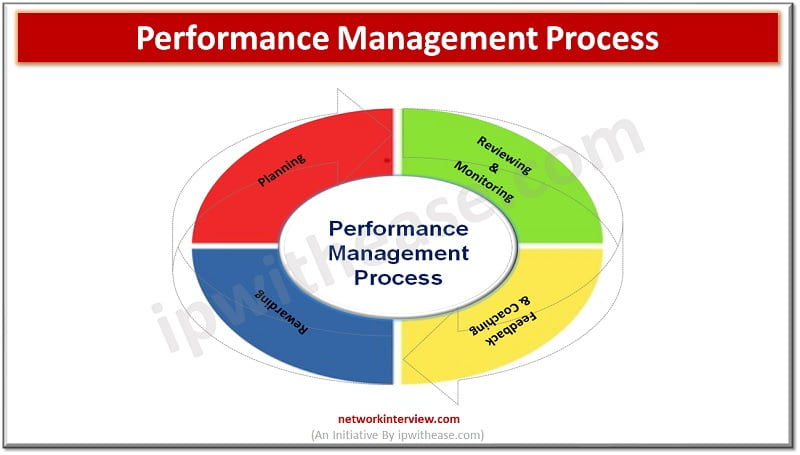
In the dynamic and ever-changing world of business today, companies continuously strive to outperform their competitors and attain long-term prosperity. A fundamental component in achieving organizational greatness is the implementation of a strong performance management process. This system encompasses multiple …
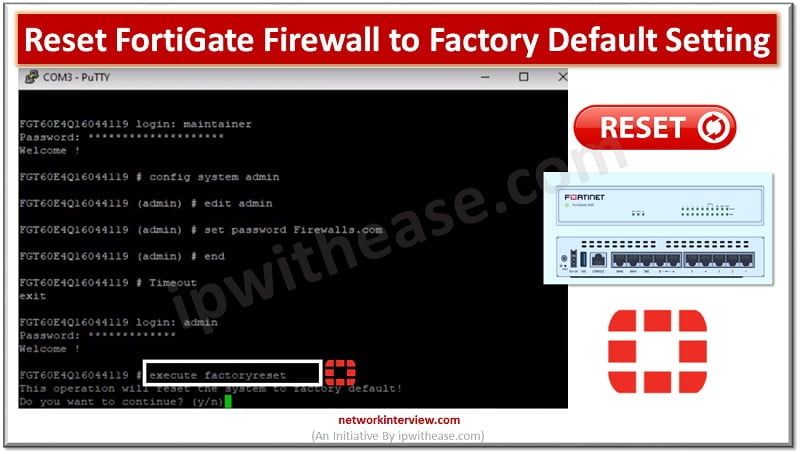
Factory default means resetting the device to the original default configuration and deleting all customized configuration from the firewall/device. Why do we need to reset the firewall to factory default? Device is crashed and need to remove from network Remove …
As we move into an increasingly digital world, businesses must collect and manage up-to-date data easily. Manual storage processes are often inadequate and unreliable, especially with large customer datasets, putting organizations at a disadvantage. Fortunately, Master Data Management (MDM) tools …
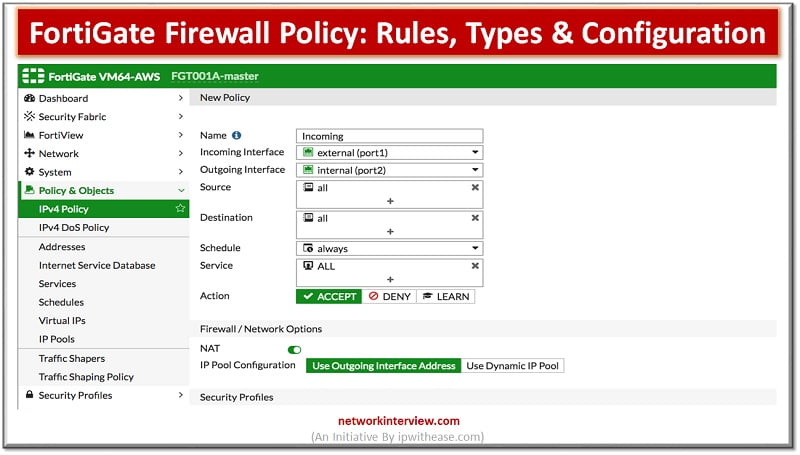
What Are Firewall Policies? Firewall policies define which traffic matches them and what FortiGate does when traffic does match, should the traffic be allowed? Initially FortiGate basis this decision on simple criteria, such as the source of the traffic then …
The CSPO (Certified Scrum Product Owner) certification is considered prestigious for individuals aiming to succeed in Agile product management. With the increasing popularity of Agile methodologies in various industries, obtaining a CSPO certification can unlock various career prospects and showcase …
In today’s digital age, the security of user access rights has become more important than ever before. Managing user access rights is a crucial task in any organization that deals with sensitive data. The rise of distributed systems has made …
Advancements in technology have revolutionized our lives, simplifying the achievement of various goals and tasks. Among these technological advancements, ai voice generator tools play a significant role in enhancing convenience and understanding. TTS ( Text to Speech) enables influencers to …
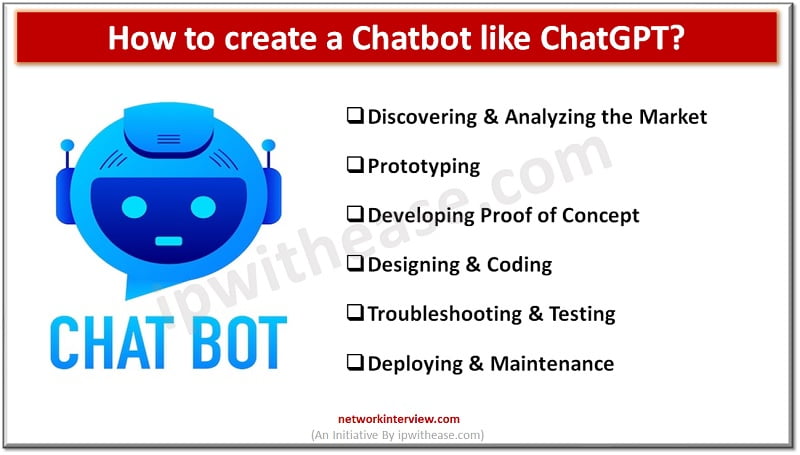
What was once restricted to academic discourses and testing facilities has evolved into things that are more accessible to the general public. This surge of Artificial Intelligence has penetrated the human realm. Artificial intelligence (AI) chatbots are at the forefront …
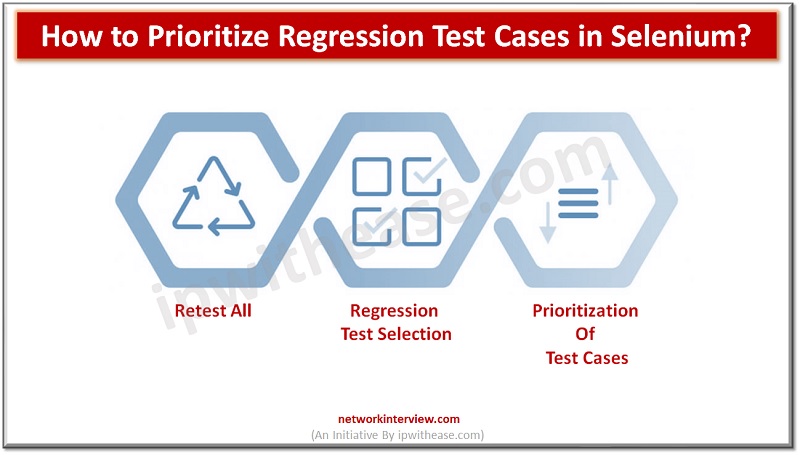
Regression testing plays a critical part in software development by verifying that modifications or upgrades to a program do not generate new faults or disrupt current functionality. However, since regression test suites may frequently be extensive and time-consuming, selecting test …
Selenium Real Device Testing A hugely well-liked open-source framework called Selenium enables programmers and testers to automate web browsers and produce automated tests that perfectly mimic user interactions with web applications. The use of strong error handling and reporting techniques …
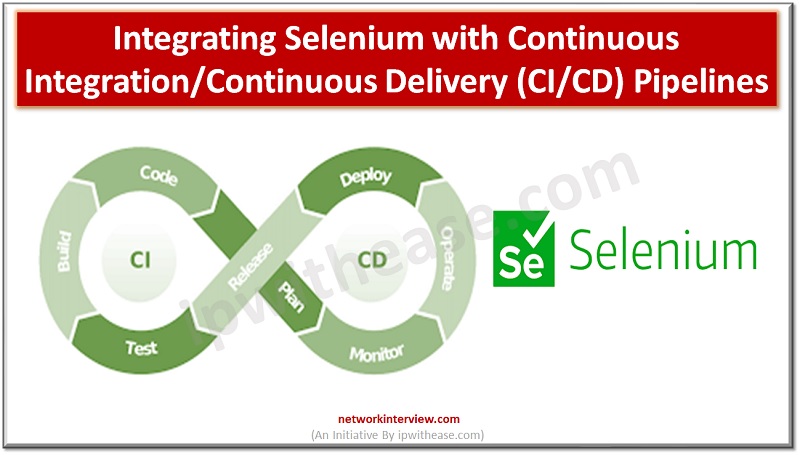
Introduction to Continuous Integration/Continuous Delivery The contemporary practice for application development included separating the development process into three separate stages. These included the development, testing, and the production phase. The application developers separated these phases, which means that the next …
Artificial Intelligence and Machine Learning are two emerging concepts which are playing a very crucial role since the Covid pandemic hit us. Both technologies are being used to study the new virus, test potential medical treatments, analyse impact on public …
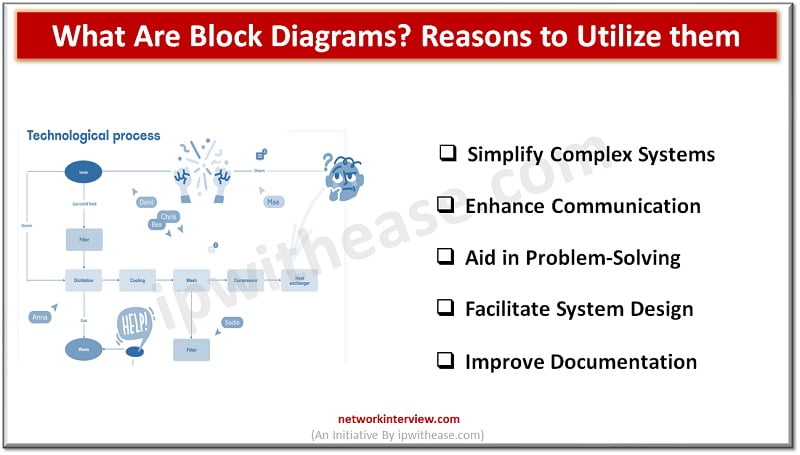
Block diagrams are powerful visual tools that help simplify complex systems and processes by breaking them down into interconnected blocks or functional units. They provide a high-level overview of the components and relationships within a system, enabling teams to better …
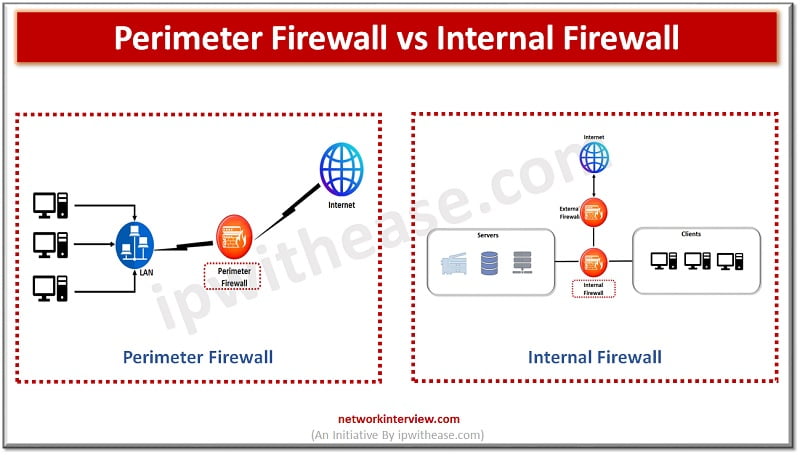
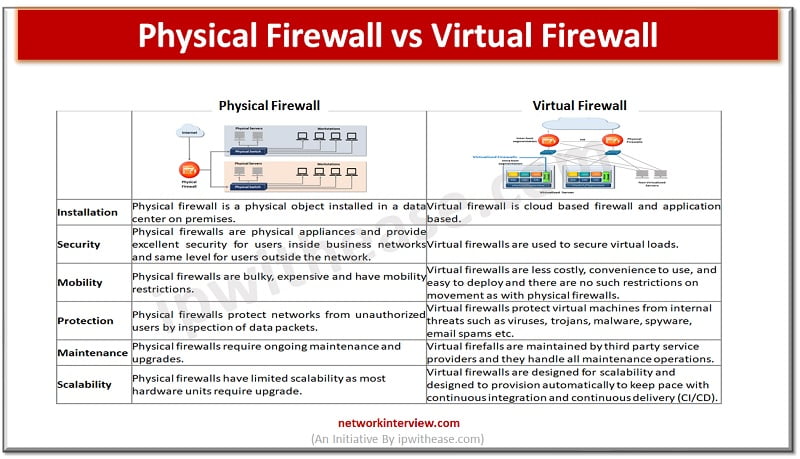
Firewalls are the primary line of defense for organizations; they are there for more than three decades but evolved and came a long way with drastic features and also sold now as separate appliances and make smarter decisions about what …
Firewalls are the first line of defense for an organization’s networks. Firewalls come in different categories – they can be a hardware appliance, software based or virtual. The increasing penetration of cloud computing infrastructures has given rise to virtual firewalls. …
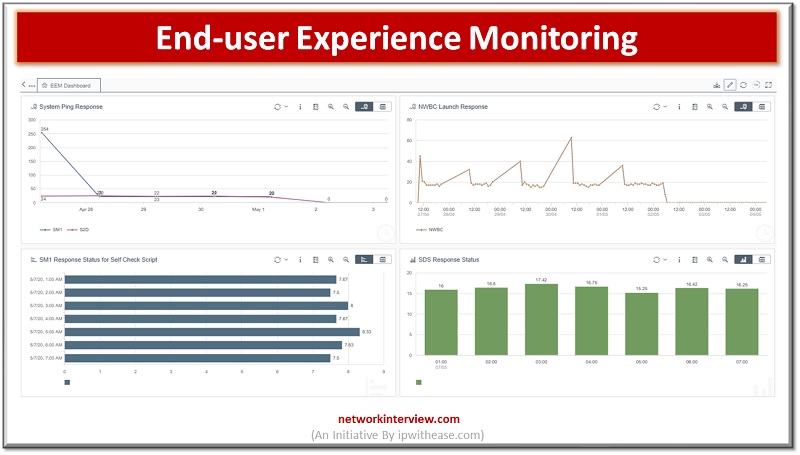
The Importance of End-User Experience Monitoring End-user experience monitoring is a critical aspect of ensuring a high-quality digital experience. The need for businesses to provide an optimal digital experience to their customers is at its peak, and digital experience monitoring …
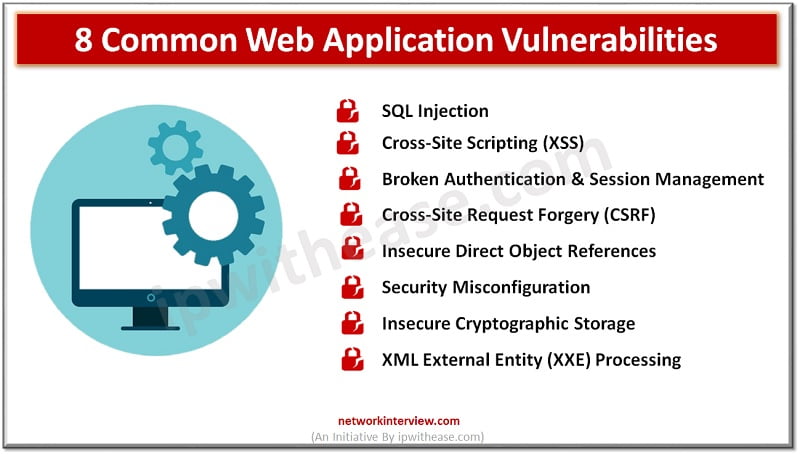
Introduction to Web Application Vulnerabilities Web application vulnerabilities are glitches or imperfections found in the system. These can lead to security risks, such as cyber-attacks or data breaches. Sadly, these risks occur more often than network or asset dangers. According …
Understanding each Encryption Technique When we dive in-depth to explore more about wireless key management and encryption technologies, then we would find that network protocols play an imperative part in it. As we are dealing with the technologies that are …
In today’s fast-paced and competitive business landscape, small businesses face numerous challenges that can hinder growth and productivity. Limited resources, time constraints, and the need to juggle multiple tasks often leave small business owners overwhelmed and struggling to keep up. …
One of the most popular programs for signing PDFs is Adobe Acrobat Reader DC, which allows you to electronically sign documents on your computer or mobile device. Here’s how to do it: Open the PDF you want to sign in …
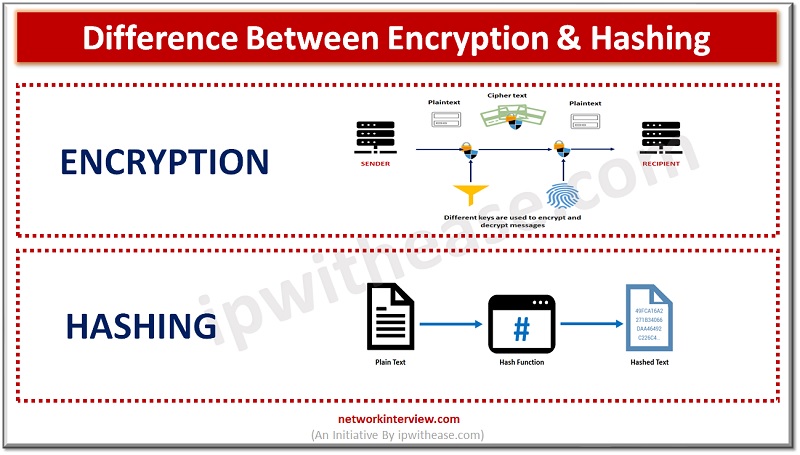
In the realm of data security, hashing and encryption are commonly employed to protect information from unauthorized access. While both methods have distinct processes and advantages, they are occasionally mistakenly used interchangeably. This blog will delve into the definitions of …
The digital marketplace is growing at an unprecedented rate, with e-commerce businesses serving as the cornerstone of this rapid expansion. As these businesses evolve and flourish, they face a pivotal challenge: securing their customers’ financial information. One of the most …
Discussing the implications of VPN providers logging user activity and the importance of privacy policy The usage of VPNs has become increasingly popular among internet users who place great importance on privacy policy and security. VPNs are known for their …
Each iPhone and iPad has a set storage capacity, but even the largest storage devices can eventually become filled with the content you acquire through music, apps, photos, and messages. Unfortunately, you cannot increase your device’s storage capacity, but there …
In today’s rapidly evolving digital landscape, the importance of cloud computing is inescapable. As a cornerstone of modern technology, cloud computing has transformed how businesses operate by offering flexible, cost-effective, and scalable solutions to data storage and management. But what …
What are infographics and how can they be useful for IT professionals? We’re explaining the answers along with tips on how to make infographics that resonate. Have you heard of infographics? You know about other formats that are great for …
In today’s digital age, cybersecurity is a critical concern for businesses of all sizes. With cyber threats becoming more sophisticated and prevalent, it is essential for employees to be well informed and proactive in protecting sensitive company and customer data. …
Every business is more than just a person or a team working on a task. If you’re a business owner or manager, you know how many aspects and issues a company has to deal with throughout the day. It’s incredibly …
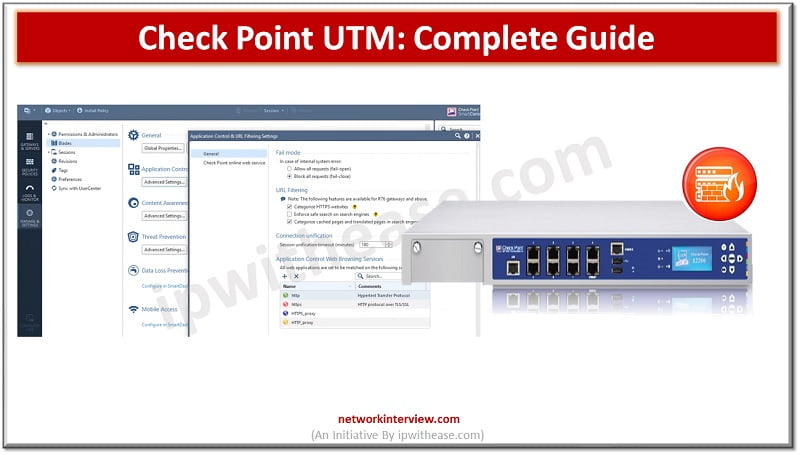
UTM (Unified Threat Management) solution deployed at the gateway level and scans all the malicious and suspicious traffic which passes through the network. UTM has multiple parameters such as URL Filtering Application Control Intrusion Prevention System Antivirus & Anti-Bot Data …
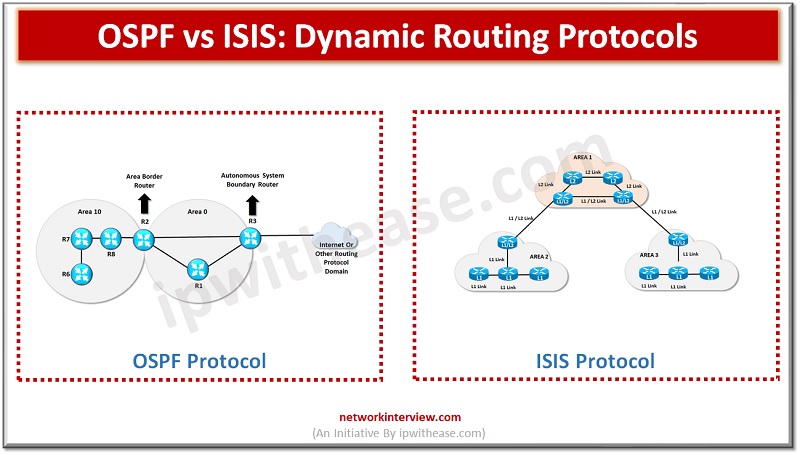
Computer communication networks are growing at a rapid pace, they are based on technology which provides the technical infrastructure, whereas routing protocols are used for transmission of data packets across the Internet. Routing protocols specify how routers communicate with each …
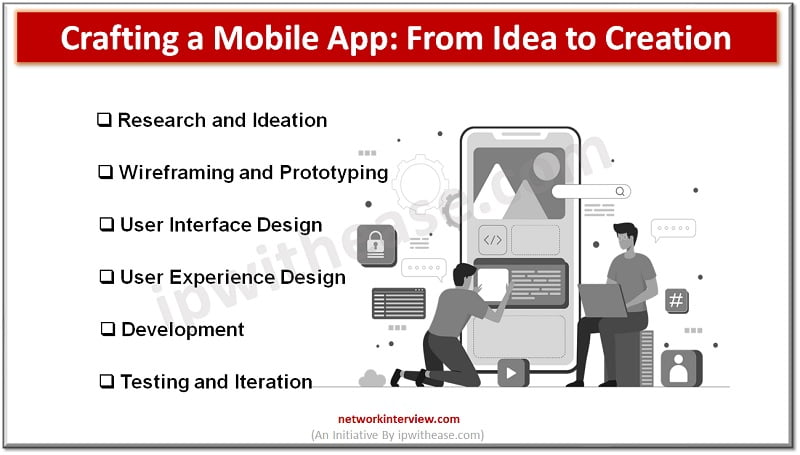
In today’s digital era, mobile apps have become an integral part of our lives. From ordering grub, booking rides, to keeping up with friends, these apps have completely transformed our tech interactions. But have you ever pondered over the process …
In recent times, the worldwide cyber security scenario has witnessed a surge in potential risks. With the onset of the pandemic, cyber offenders exploited the vulnerability of poorly aligned networks when companies transitioned to remote working setups. The cyber attack …
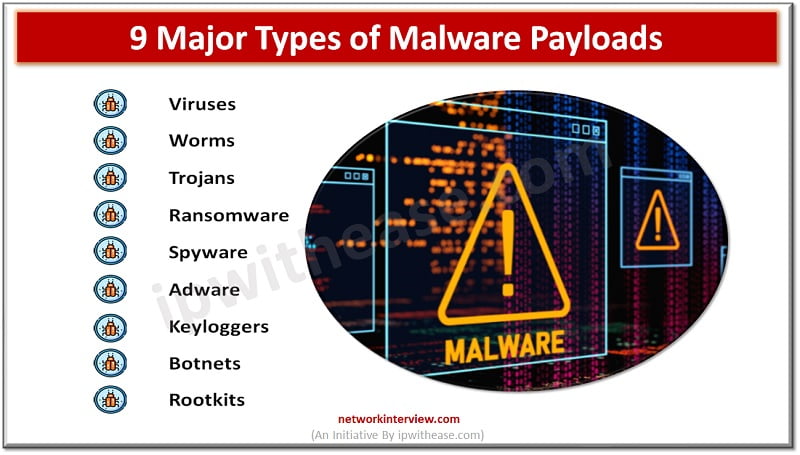
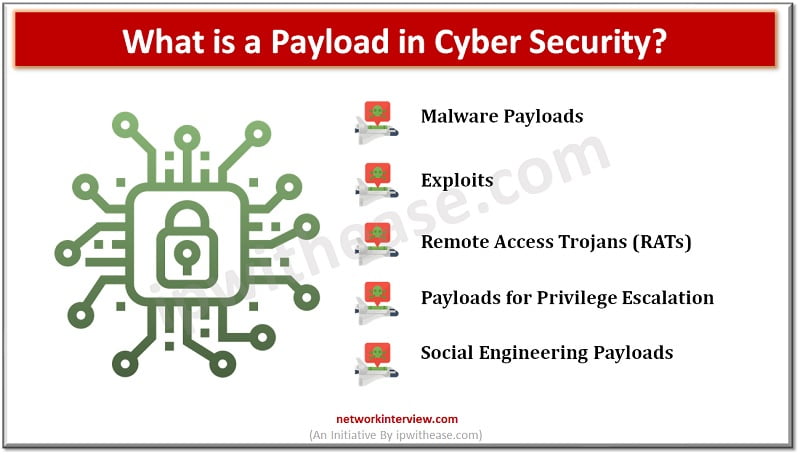
As a cybersecurity professional, you will come across many technical terms and jargon in the field. One of the terms that we often hear in cybersecurity is “payload.” In simple terms, a payload refers to the part of a malicious …
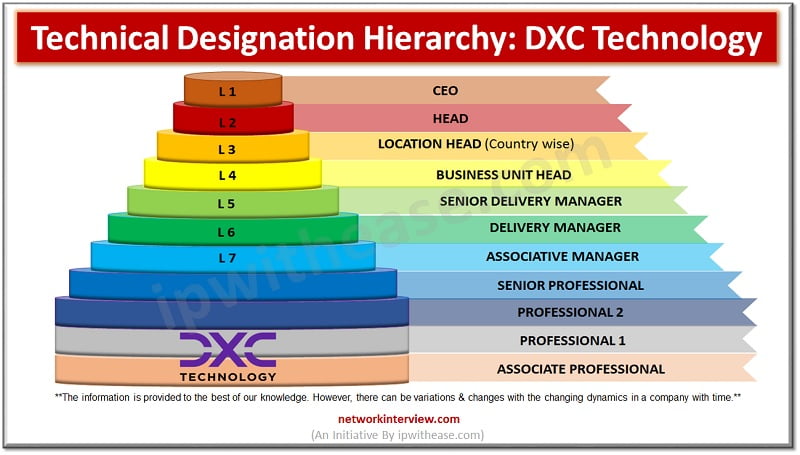
In today’s competitive job market, finding an employer who values their staff is crucial. Luckily, the IT industry has some great options for employee friendly companies. IT Companies are also focused on providing an employee friendly environment. There are global …
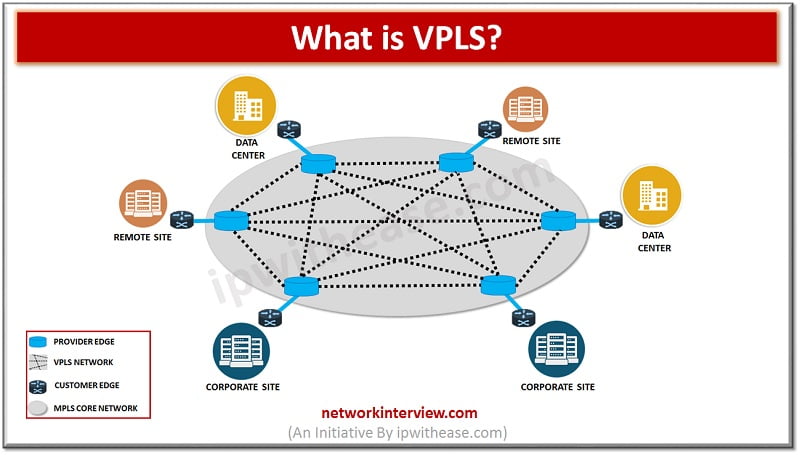
Introduction to VPLS As we have already discussed MPLS in detail in our previous article, so here I will focus on VPLS first and then the differences between the two. VPLS i.e. Virtual Private LAN Service. It is a service that …
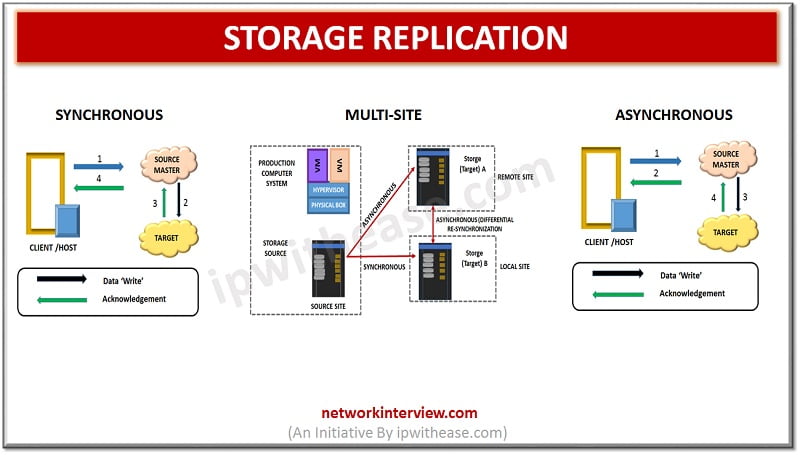
Storage replication – Sneak Preview Continuous data protection with zero downtime, higher availability and speed requirements govern the business requirements in the current arena. The purpose of replication is protection from disaster which may occur at one location and operations …
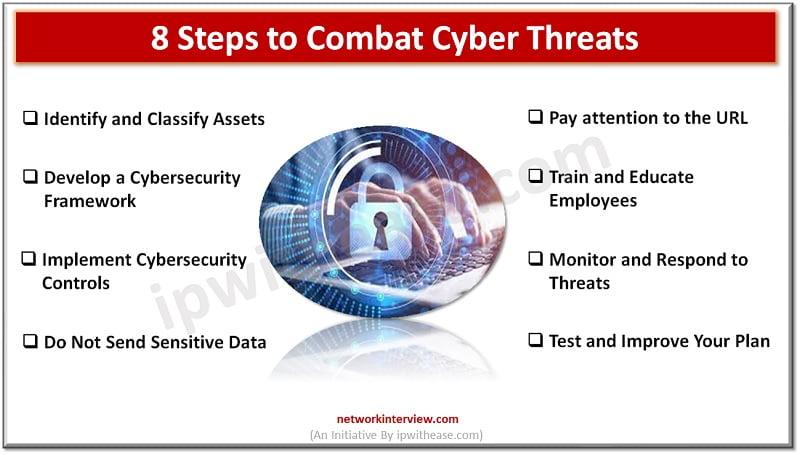
Cyber attacks are becoming more common and sophisticated, which means businesses need to be more prepared than ever before. The COVID-19 pandemic has brought with it a rise in remote work, leading to an increased reliance on technology for business …
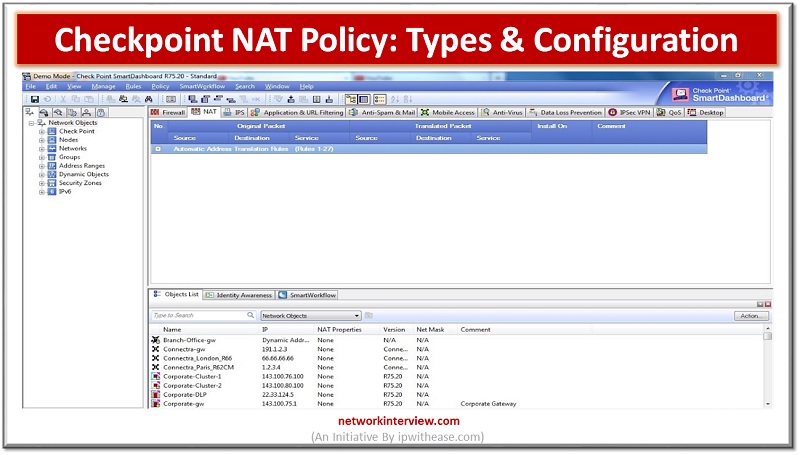
What is NAT (Network Address Translation)? Many firewalls include network address translation, a procedure that translates between internal and external IP addresses. NAT enables a private network to use non-routable internal IP addresses that are mapped to one or more …
Workday is a Financial Management and Human Capital Management Software that is hosted in the cloud. It’s a Software-as-a-Service (SaaS) model. Workday recognizes the importance of a company’s key operations working together and being integrated. Workday Studio is a fantastic …
Are you in your final year of pursuing a Software Engineering Degree? Do you want to join a new company from your present? Then there are many things you should consider before making the decision. One of them is the …