Guest OS vs Host OS When it comes to virtualization, several strategies are there that are popular. Your selection among these depends on several factors including imports, its development, software interface, virtual machines alters and other characteristics as well. Hosted …
Ripple and RippleNet The technology that serves both like a network for digital payment and a cryptocurrency for the financial transactions is termed as Ripple. The operation of Ripple takes place on a peer-to-peer and open source decentralized platform on …
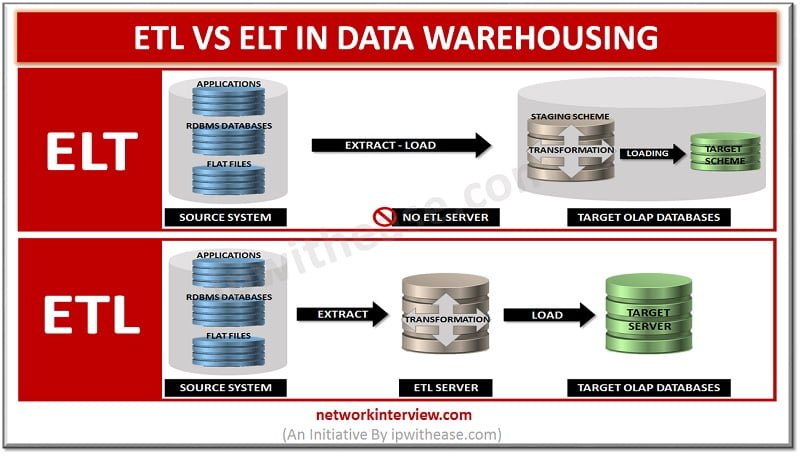
ETL vs ELT in Data Warehousing ETL: When the data is extracted from disparate sources and then it is transformed, the process is termed as ETL (extract, transform, and load). For data transformation, the actions performed include applying calculations and …
In the information technology (IT) industry, including the network engineers is in demand for the employment purpose but the supply of candidates is decreasing. In accordance with this, in 2015, job posting had increased with 74% from the past years …
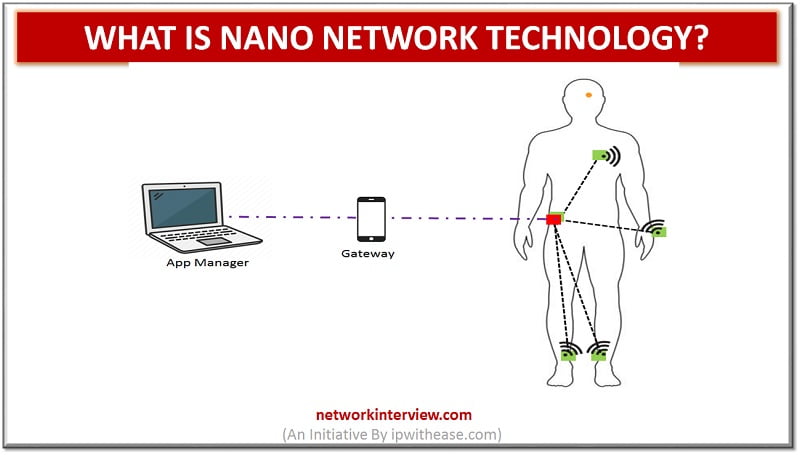
Nano Network Technology A set of interconnected nanomachines (devices a few hundred nanometres or a few micrometres all things considered in size) is known as nanonetwork. This technology is also called by the name nanoscale network. They are able to perform simple …
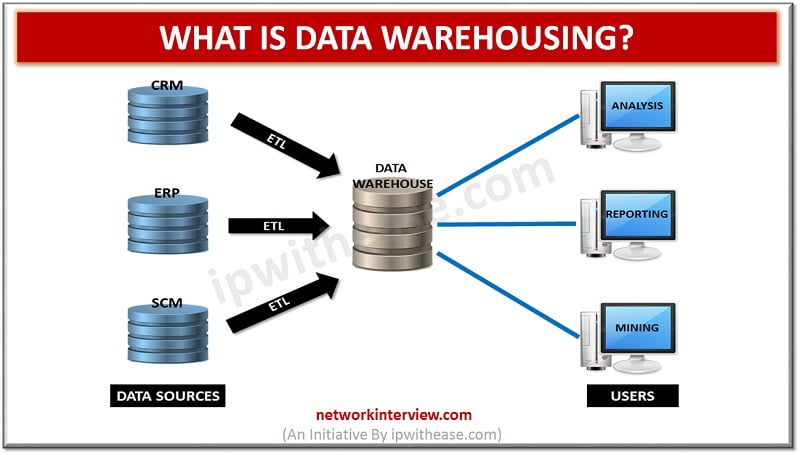
The process of data management and collection from different sources is termed as data warehousing for the purpose of offering useful insights of business. Analysis and connection of business data from diverse sources serves as the major purpose of data …
After the invention of Android 9 Pie, Google has announced that they will introduce a numerical order for their future OS versions. So, here we will give you an insight on the upcoming OS version that is Android 11. As …
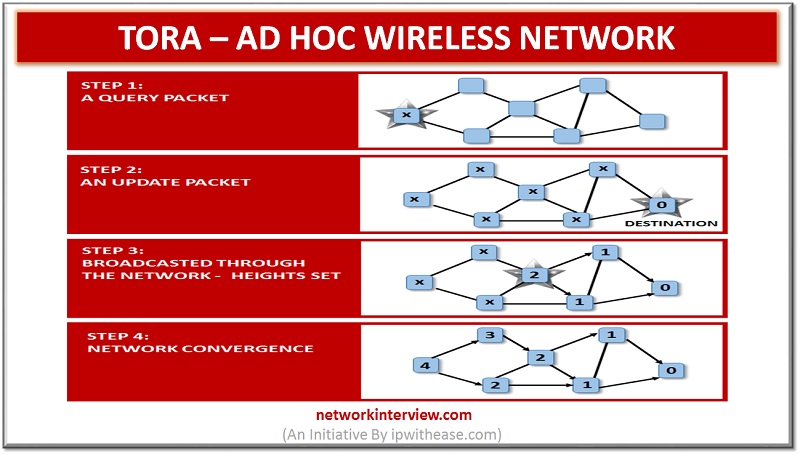
Temporally Ordered Routing Algorithm is abbreviated as TORA which is a source that is initiated on demand routing protocol. The invention of this protocol was done in 1997 by Vincent Park and M. Scott Corson who belongs from the university …
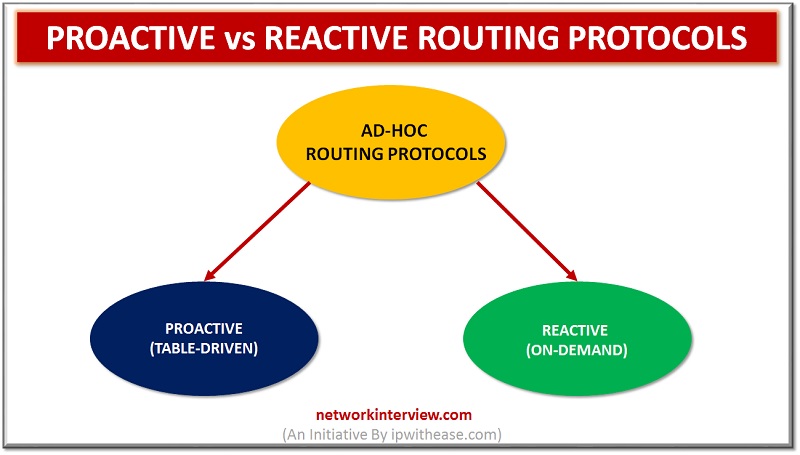
Proactive vs Reactive Routing Protocols Routing protocols are the routes that help to learn dynamic routes. These protocols are organized on routers in regards with exchanging the information related with routing. Using the routing protocols in your network has many …
There are several certifications that are offered by Cisco Systems Inc. for the products. Many credentials of Cisco match with IT practitioner credentials of specialist, intermediate, entry level and expert-level. The managers or Network professionals are definitely valuable for the …
TOGAF and ITIL What is TOGAF? The methodology of enterprise architecture by which development of enterprise software receives high level framework is termed as TOGAF (The Open Group Architecture Framework). A systematic approach is used in TOGAF by which it …
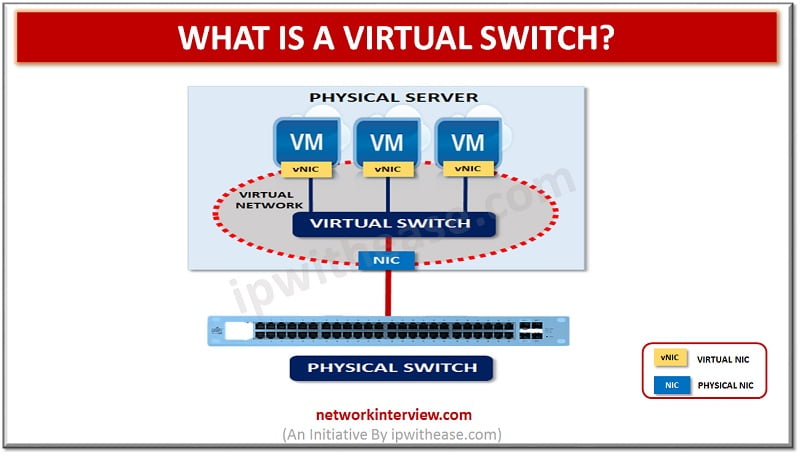
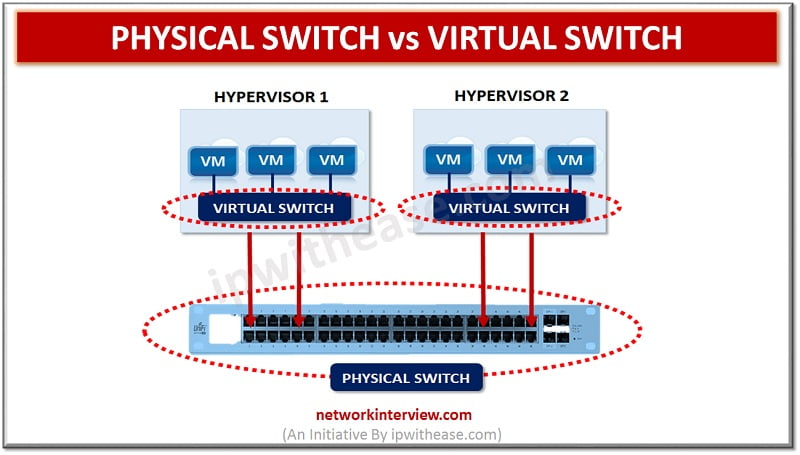
The logical entity termed as virtual switch is the fabric of logical switching by which the switch is followed as device of layer-2 network. Functions similar to the regular network switch are ensured by virtual switch with certain functionalities of …
Wi-Fi 6 Technology With the advent of wireless technology, faster Internet is something that is non-negotiable for most of the users. It is especially demanding for most of the users as there are more bandwidth-consuming apps, videos and games becoming …
Over the Top technology The communication and transmission of data have become more secured, fast and convenient with the passage of time. With the advent of high speed Internet connection in most of the parts of the globe, it is …
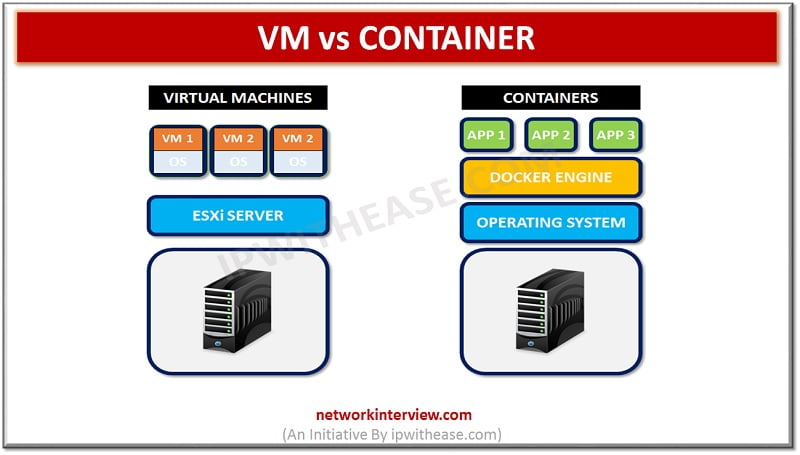
VM VS CONTAINER Virtual Machines VM or Virtual machine enables you to create and operate a discrete virtual environment- an operating system, acting like an individual computer. Through VMs, softwares that cannot work on your main OS, can easily work …
Physical Switch vs Virtual Switch A good and reliable network can help you in running a business operation seamlessly. That is the reason why a professionally reliable network always come with certain vital features that ensure unflinching results as per …
OpenFlow vs Netconf There are several data programming and configuration protocols that make the flow of information seamless across the networks. Among these protocols, OpenFlow and Netconf are considered to be popular and widely used ones when it comes to …
Network Administrator Vs System Administrator Network Administrator and System Administrator are the two terms that overlap each other but in reality, they are very different from each other. In this blog, we will discuss what the roles of network administrators …
Why Cisco certification? The present day job market is highly competitive and in this scenario, it is not simple to enter the tech industry. There is no doubt that career in this industry offer high rewards but for getting the …
CMD vs BAT The importance of the batch file can be easily understood by the power users and system administrators. But, generally most of the regular computer users are unaware of these files. This indicates that people are not utilizing …
Windows Management Instrumentation (WMI) is Microsoft’s technological invention intended for taking care of Windows’ varied operational environments. Microsoft has offered set of specifications in the form of WMI for strengthening applications and devices management in the network. The information regarding …
Difference between LDAP and AD The framework of IT infrastructure of most of the organizations has Active Directory as a significant part. This significance is the reason why attackers have the Active Directory at the top of their target. In …
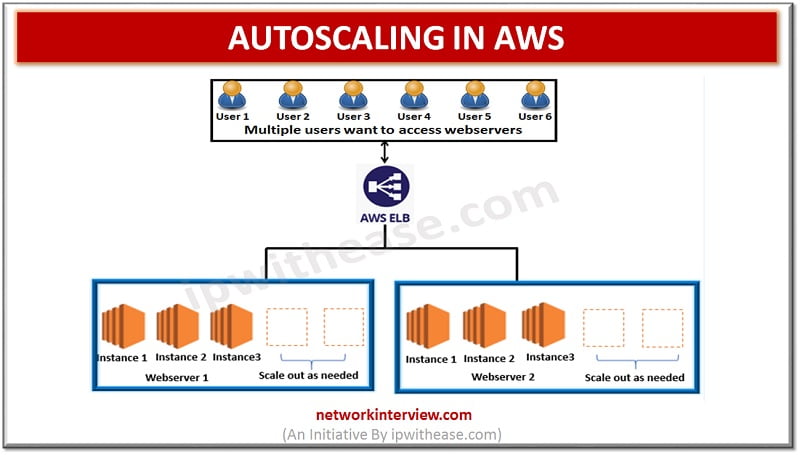
Autoscaling in AWS Better Fault tolerance/ better availability/ better cost management/ better scalability – These must be considered while hosting a website/ App on the server to allow smooth functioning of the website/ App. Website owners have a key requirement …
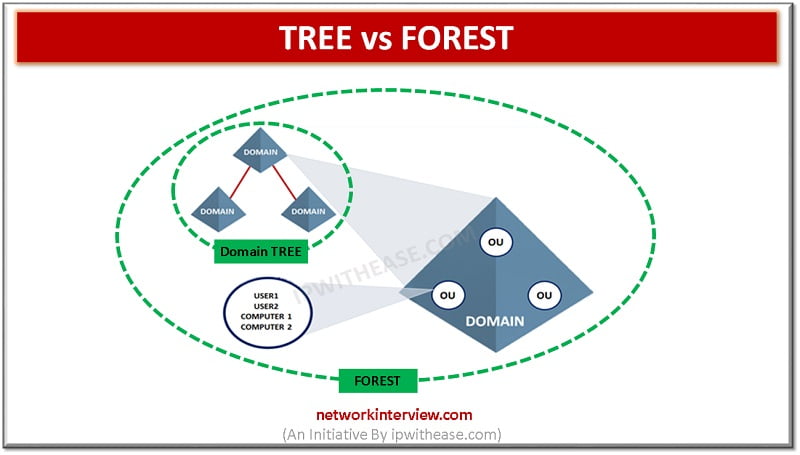
Introduction to Tree and Forest An Activity Directory is a product of Microsoft that runs on Server of Windows. It allows managing, accessing, and permissions for the network resources. The data is stored as an object in this directory and …
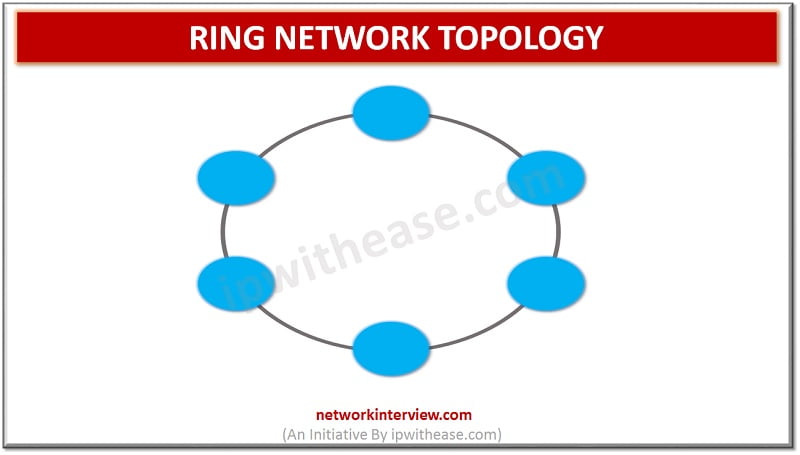
Network Topology refers to the physical or logical layout of a network. Ring topology is a type of network topology in which each network device is connected to two other devices, forward and backward forming a single continuous path for signal transmission. …
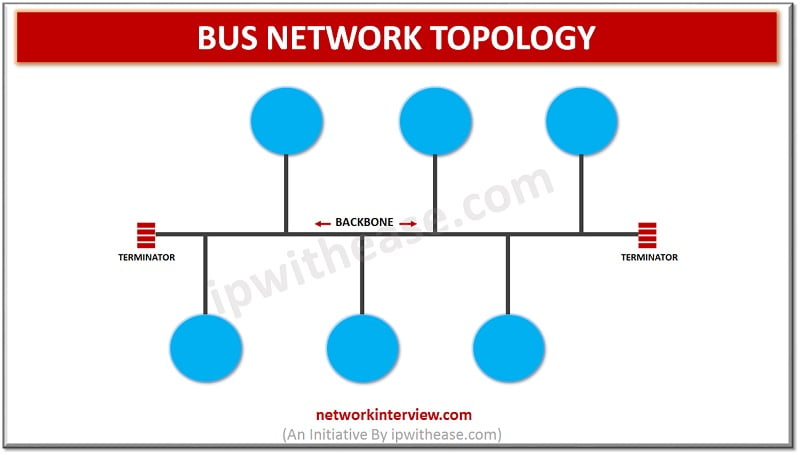
Network Topology refers to the physical or logical layout of a network. BUS Network Topology Bus topology is a type of network topology where each node is connected to a single cable known as the backbone. Though there is no limit …
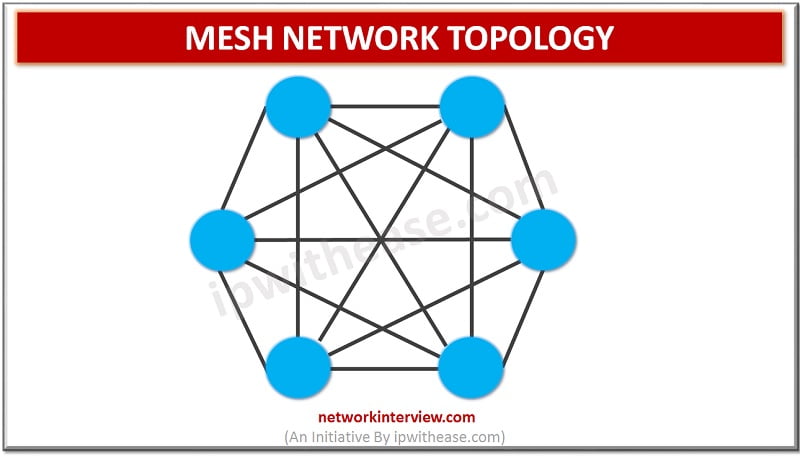
MESH NETWORK TOPOLOGY Network Topology refers to the physical or logical layout of a network. Mesh network topology is a type of site-to-site WAN topology in which each network device is connected to every other device through a dedicated link …
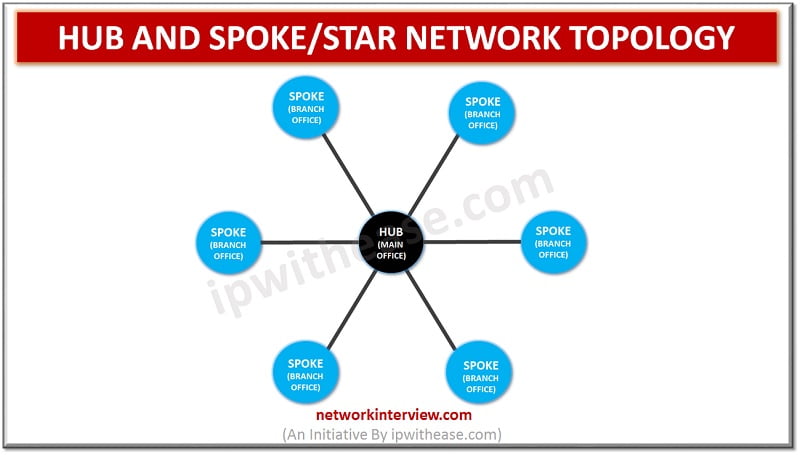
HUB AND SPOKE/ STAR NETWORK TOPOLOGY Network Topology refers to the physical or logical layout of a network. Hub and spoke or star topology is a site-to-site Wide Area Network (WAN) topology. In this type of topology, we have a central device, called …
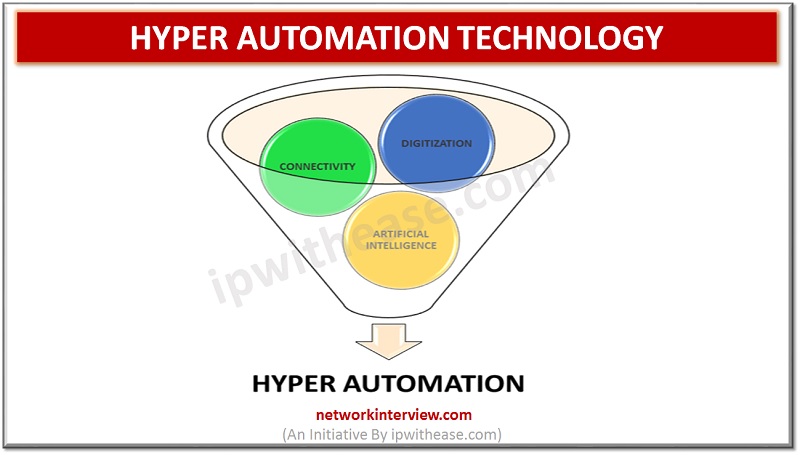
If we were speaking a decade back and one of us comes up with an idea of amalgamating machine learning and artificial intelligence to attain perfection in conventional automation industry, then most of us would have laughed at it as …
Skills required for Network Engineer In any IT setup, Network Engineer is the key and fundamental resource responsible for setup of network infrastructure on which all the services like Security, voice, wireless, messaging and Internet are made accessible. A network …
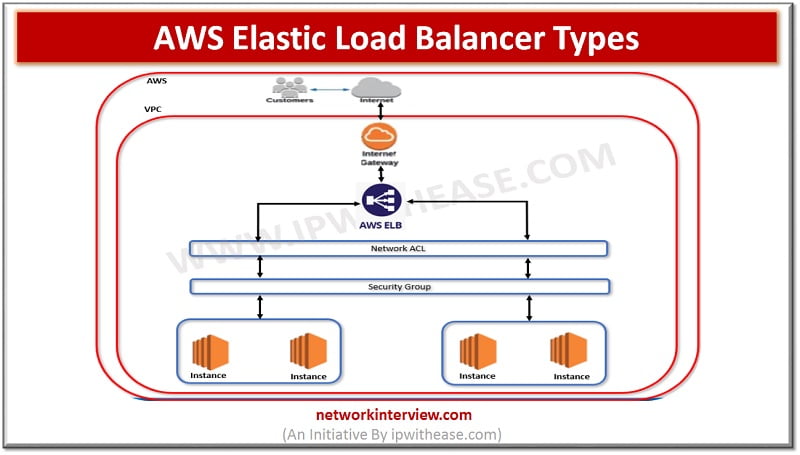
Elastic Load balancer types in AWS Application availability, continuity of service, greater performance of the application – These are the things we would always require from a platform owner while designing the network and answer to this in AWS is …
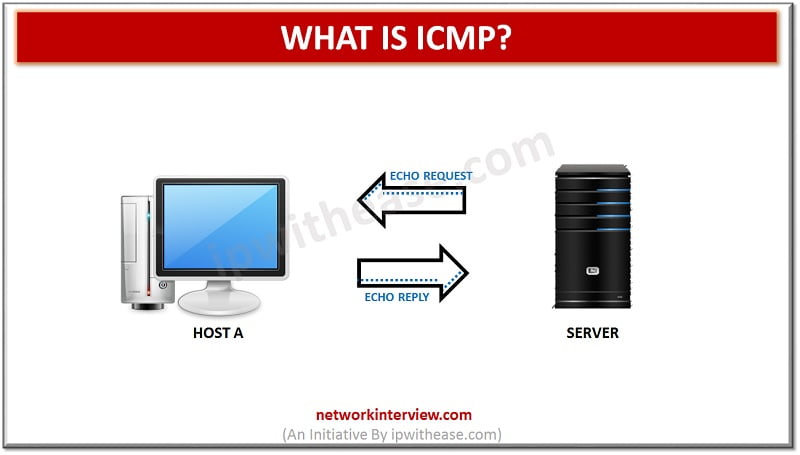
ICMP stands for the Internet Control Message Protocol. It is a primary protocol in the Internet Protocol Suite. It is used by network devices to relay an error message and management queries. It helps to reroute the message to its …
Cloud Migration Cloud computing is a technology that involves delivering different hosting services over the Internet using various hardware and software. Cloud computing allows we can access any files from anywhere in the world. It creates files remotely accessible. It …
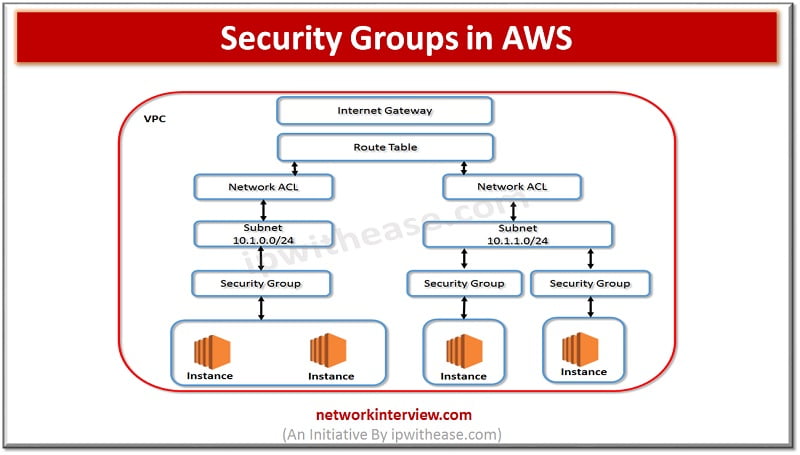
Security Groups in AWS I am sure that while working on Security groups, we do ponder about Firewalls and Rules i.e. allowing or denying traffic based on hardware or software firewalls. In case of AWS security groups are very similar …
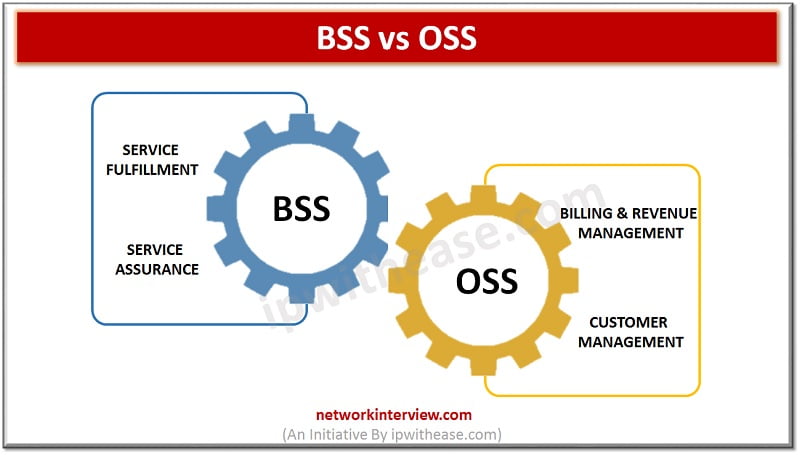
BSS vs OSS Two terms which in limelight especially in Telecom Operation world are BSS and OSS. BSS stands for Business Support Systems while OSS refers to Operations Support Systems. By their names, both the terms may seem complementary, however …
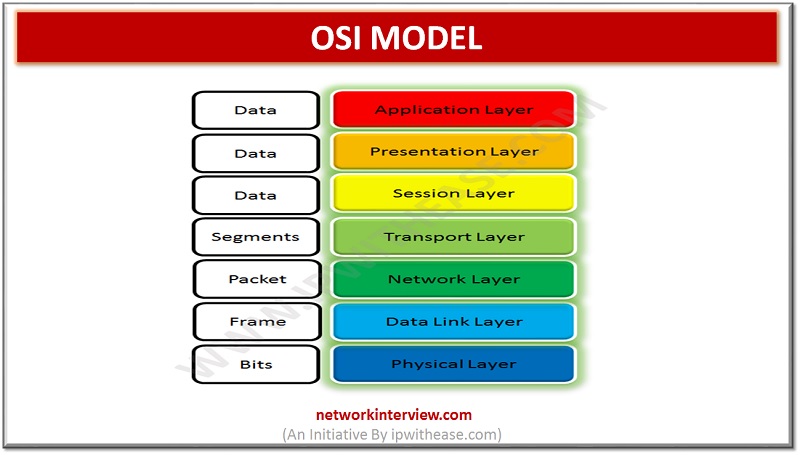
Open Systems Interconnection (OSI) Model It refers to a logical and conceptual network model that defines the network communication protocol that is used by open systems to communicates and connect with other network systems. This network model has seven subcomponents. …
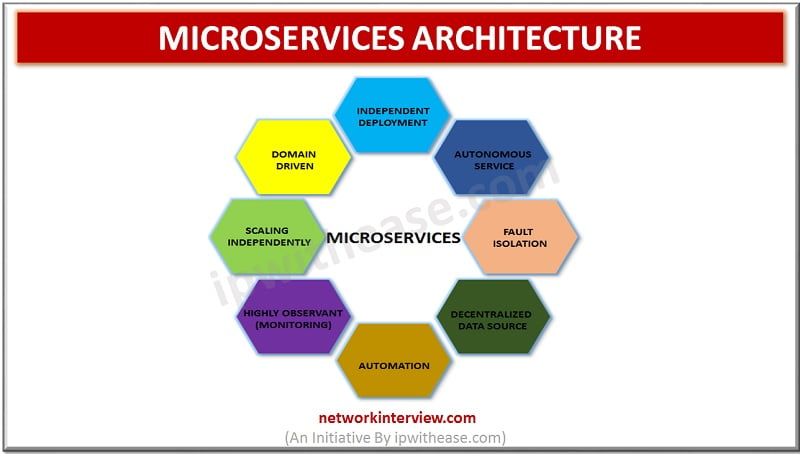
Microservices is the current hot topic being discussed in the software development circles. People are using microservices architecture for their businesses instead of using monolithic approach. The traditional methods of building enterprise application i.e. monolithic approach creates many problems when …
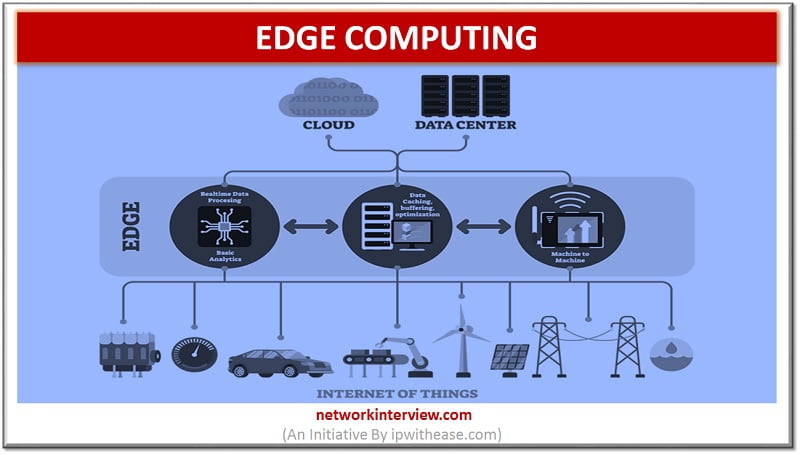
What is Edge computing? The networking philosophy known as Edge computing is aimed at taking computing close to data source so as to reduce the bandwidth and latency use. In other words, running fewer procedures in cloud is termed as …
High Level Language vs Low Level Language Computer programming languages are broadly categorized into 2 types namely – High Level Language and Low Level Language. Abbreviation for High Level Language is HLL and Low Level Language is LLL. The former …
Linux vs Windows Windows has been quite a popular choice for home and office users. It’s been the widely used Operating system used in desktops, laptops and personal computers. Linux is an open-source operating system which is based on UNIX …
The DVD technology was emerged in 1997. It revolutionized the movie industry and brought digital sound and video into homes all over the world. The Blu-ray Discs (BD) were introduced in 2006. With their high storage capacity, these discs can hold and …
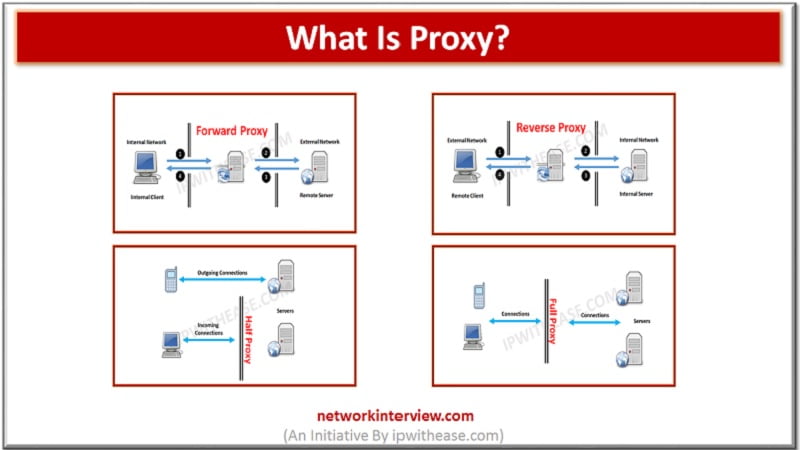
Proxies (often called intermediaries in the SOA world) are hardware or software solutions that sit between the client and the server and do something to requests and sometimes responses. The most often heard use of the term proxy is in …
Introduction to URL Filtering Make sure that you type the name of your favorite social networking site in the web browser and it displays a message “The policy of your organization does not allow navigation to this website” and does …
Botnet(BOT) Users began to know this malicious program from the year 2000 when a teenager from Canada launched a series of denial of service attacks against very popular websites. The young man, whose nickname was Mafiaboy, attacked Yahoo, ETrade, Dell, …
For some years now, the word cyber security has become a standard among companies. Information Technology is already a common tool in business and to keep systems safe, security measures are lacking to help us avoid being exposed to large …