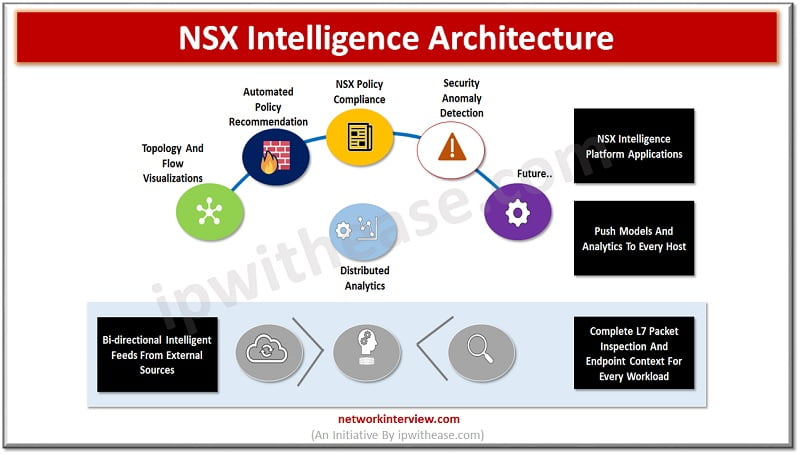
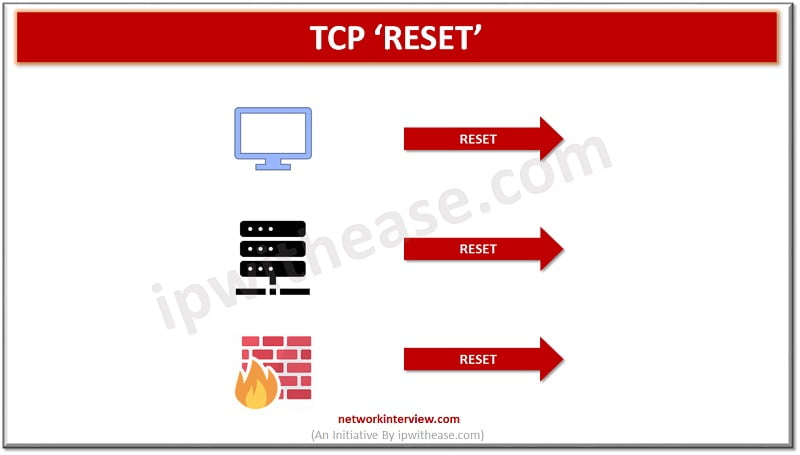
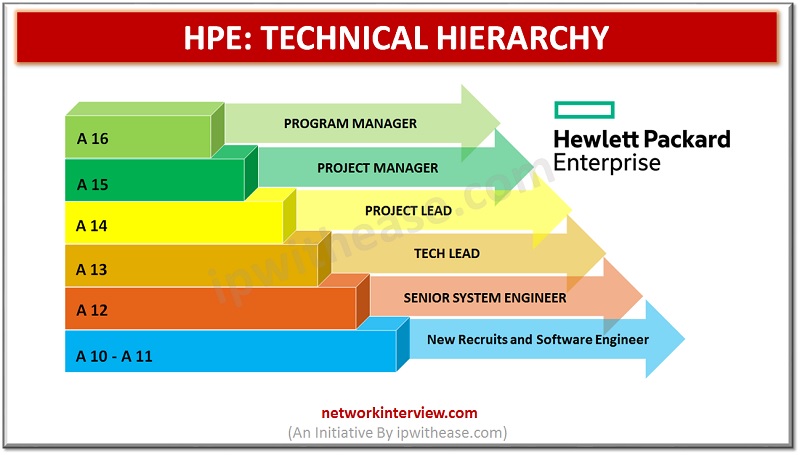
Introduction to IT Companies There is no doubt that Software Engineers and IT Consultants are one of the highest-earning personnel in the world. But not all of them are treated as the same. Their pay rate differs based on their …
Introduction to Pre-sale & Post-sale Specialization of sales engineers should be in technology and scientifically advanced products. With the help of technical skills, they explain the advantages of the products or services to the potential customers and also tell how …
Nowadays, software engineers have multiple career opportunities after their graduation. This is because of the massive Digitalisation and development of Information Technologies. And these increased opportunities create more confusion in selecting a perfect company for your future. However, over time, …
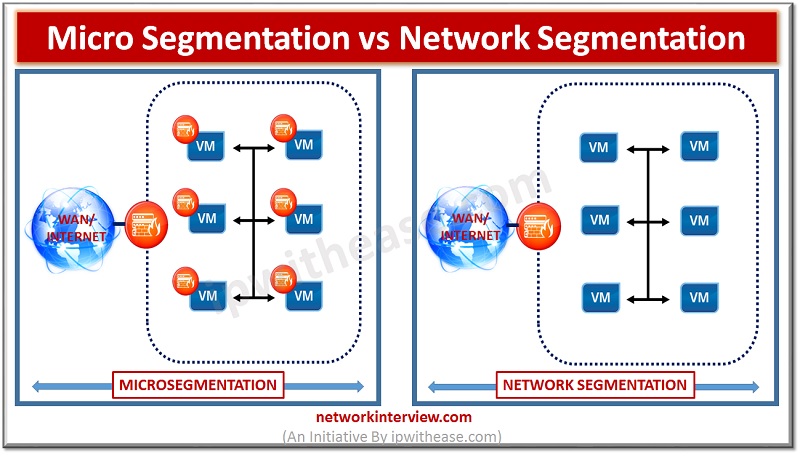
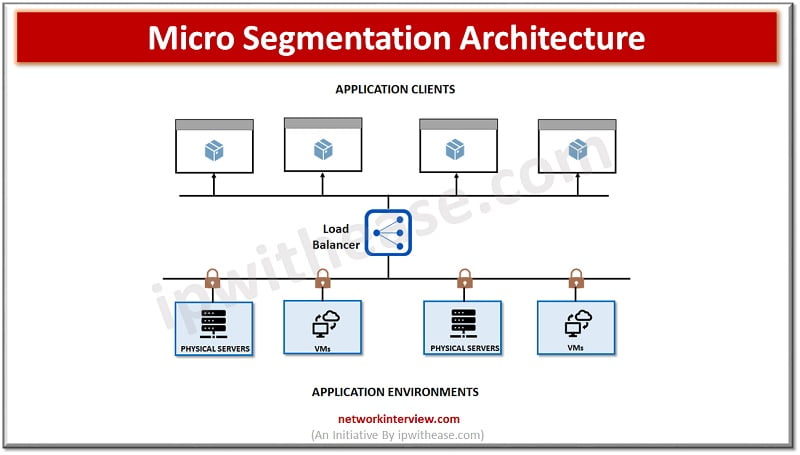
Micro segmentation vs Network Segmentation Over many years, Perimeter security has been considered the key to presenting a robust and secured network ecosystem . This was considered a suitable methodology when the network attacks were not so advanced and North-South …
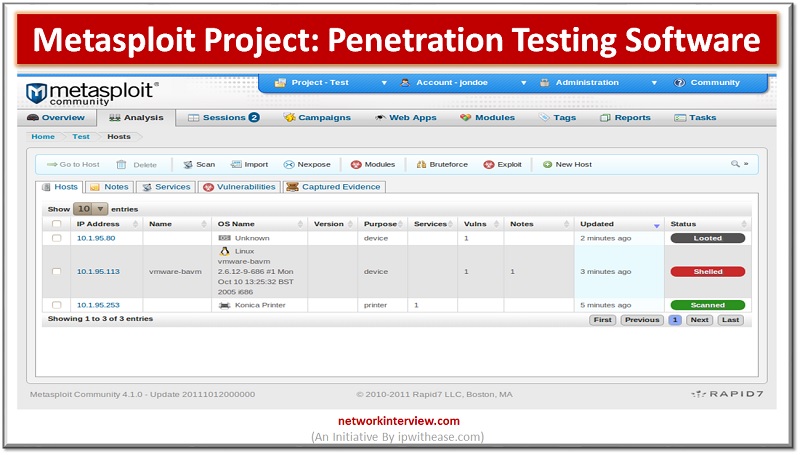
Introduction to Metasploit Project In the worldwide IT security community, we define the Metasploit Project as a computer security project that mainly provides information about security vulnerabilities and helps in penetration testing and development of the IDS Signatures. It is …
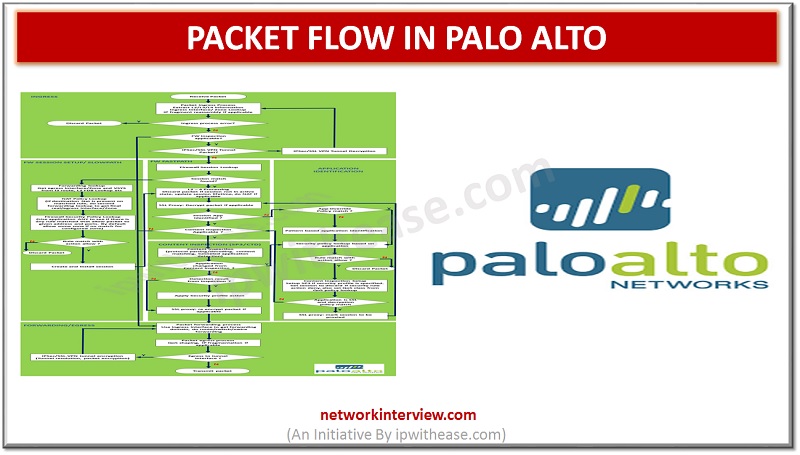
In this article, we will discuss on Packet handling process inside of PAN-OS of Palo Alto firewall. Introduction: Packet Flow in Palo Alto Packet passes through the multiple stages such as ingress and forwarding/egress stages that make packet forwarding decisions on …
Cloud Engineer vs DevOps Engineer Cloud has changed the way how we do Business. Cost savings have led the IT assets, especially compute Infrastructure migration to Cloud. Accompanied by this move, there have been buffet of new roles which have …
Introduction to Cloud Technology Cloud Technologies has dramatically changed the world in the last decade, the data center has become a private cloud and Container technology has become mainstream, Artificial Intelligence and Cloud Computing are now interlinked industries. Looking back …
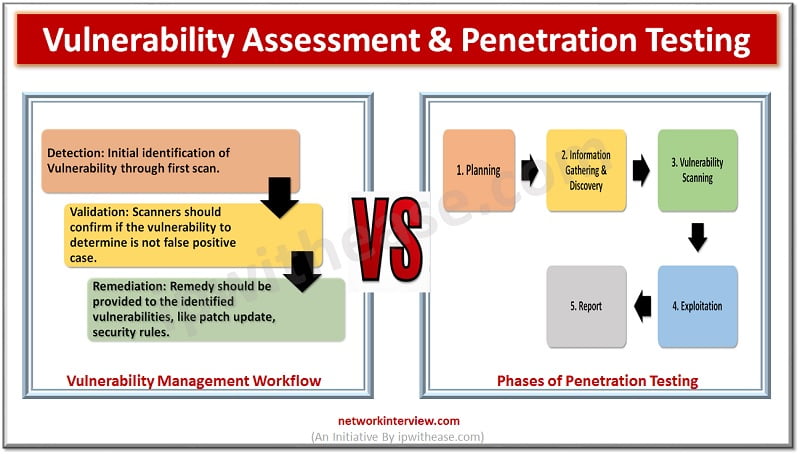
Introduction Vulnerability assessment is the way to identify weakness in the system. Vulnerability itself means “Weakness” and Vulnerability assessment means how to find weakness in a system and create a report accordingly. On the other hand, Penetration testing is used …
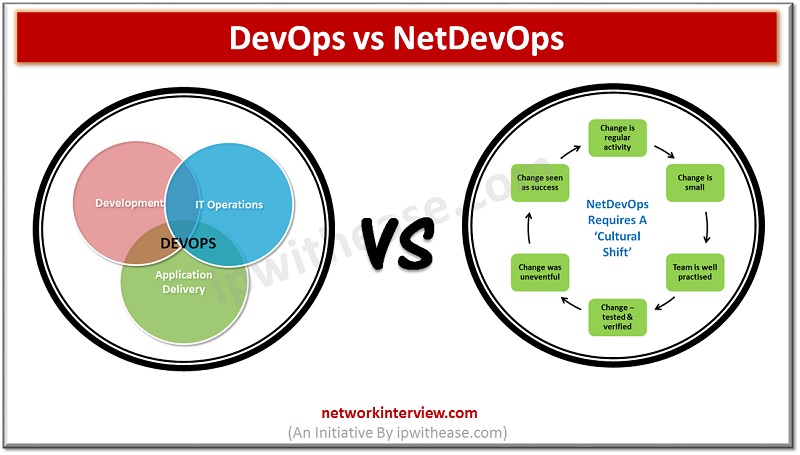
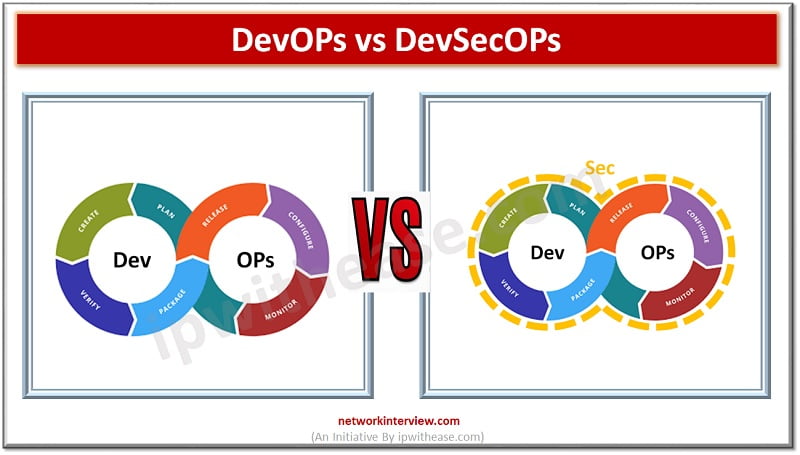
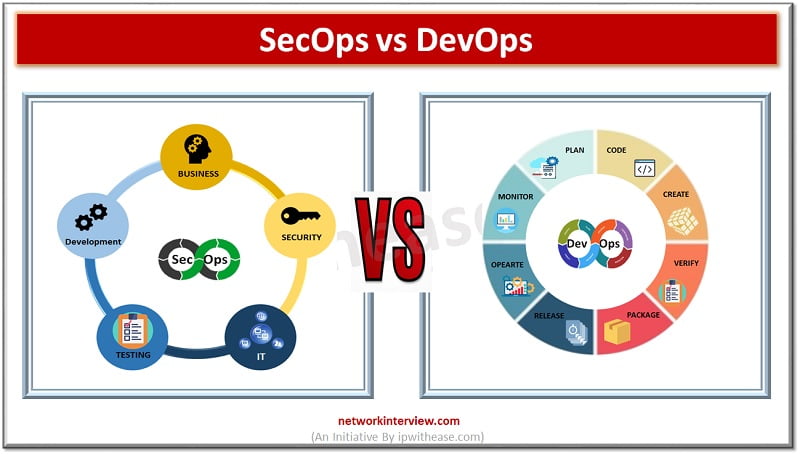
Introduction With the growing advancement in technology there is an increasing need for collaboration and Agility. Software developments require a constant collaboration between programmers and system administrators in the software development process to develop apps which are efficient, secure and …
Software development and operations teams are always striving to establish a consistent environment for development globally. The products are brought from hands of developers to customers however the existence of silos between development, QA and operations teams always create conflicting …
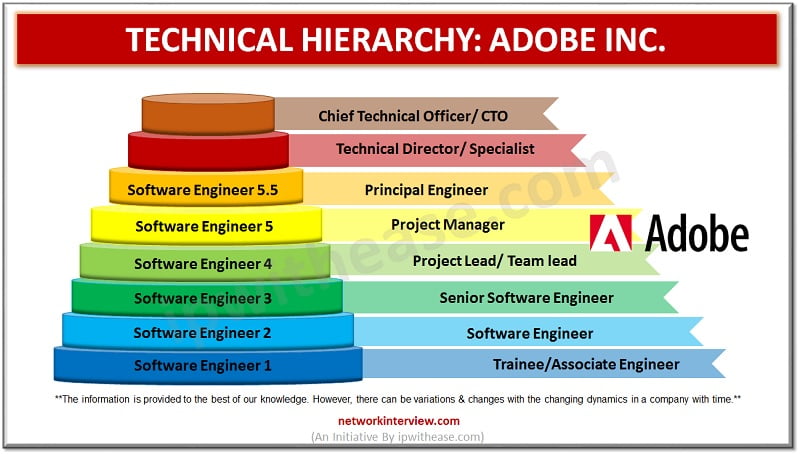
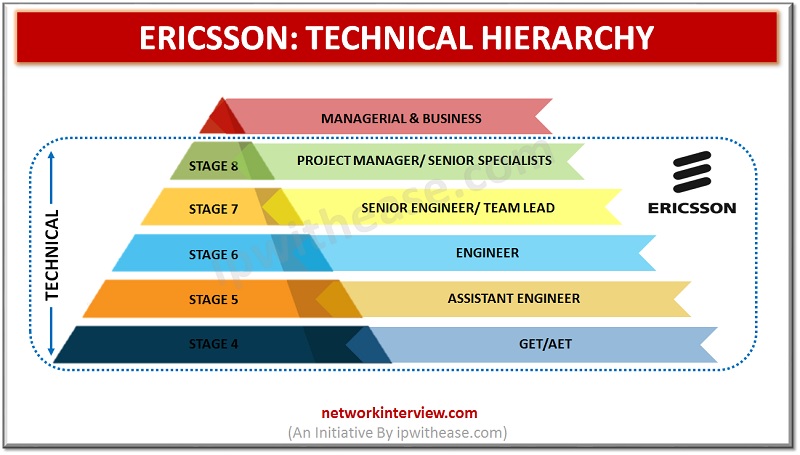
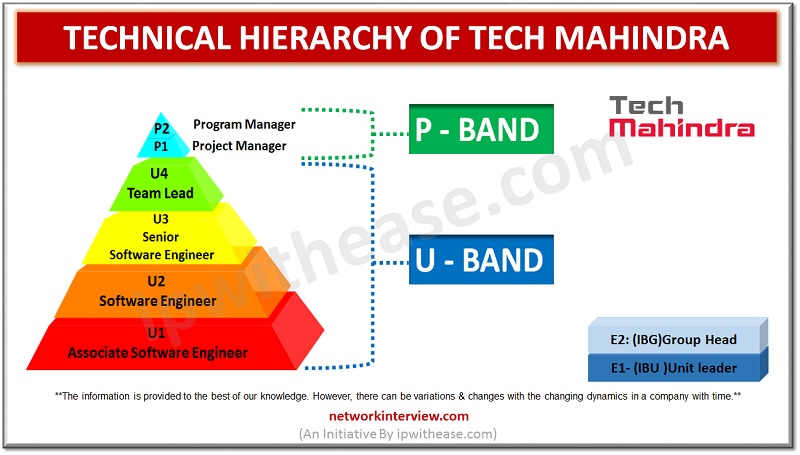
It is important to know about the Hierarchy of the organization. Because the hierarchy level gives you the idea about your future chances and the person who you need to report. It reduces the unwanted hesitation and nervousness within you. …
Infrastructure as a code is one of the greatest changes brought by DevOps in recent times. Complicated provisioning, deployment and release of cloud infrastructure processes which required following complicated steps where cloud resources were created manually is a thing of …
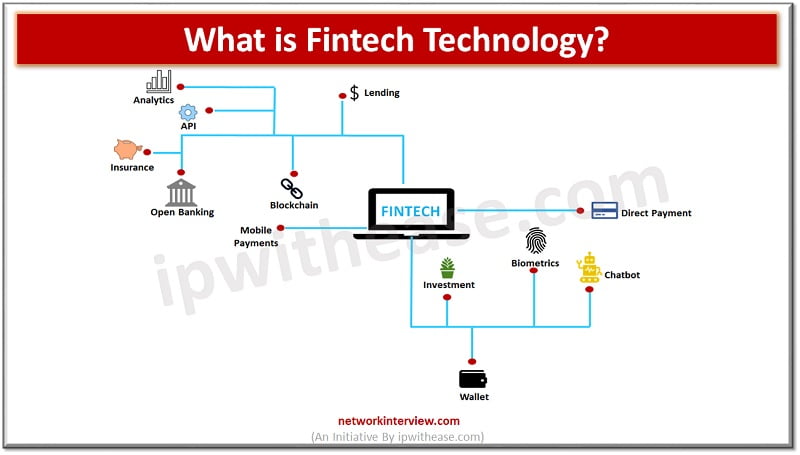
The field of finance is rapidly changing , financial firms, insurance agencies and investment banks are involved at the intersection of data and technology. Big data, machine learning, harnessing algorithms, blockchain technologies are widely spreading to conduct businesses. Financial technology …
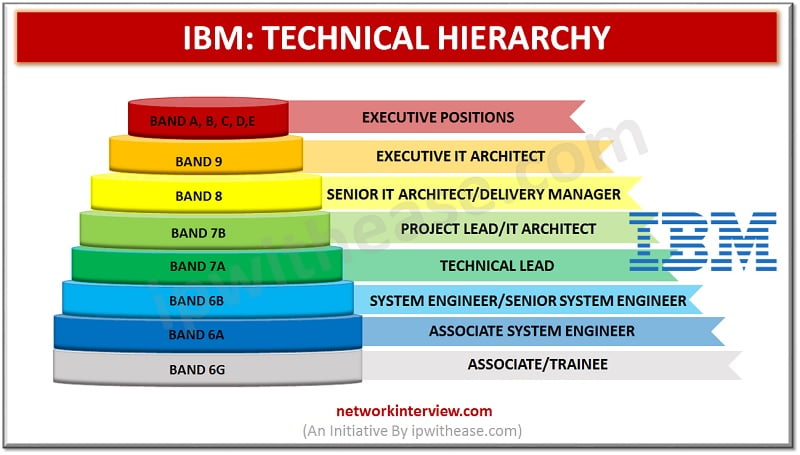
Have you got a job in Tech Mahindra? Are confused about your responsibility and roles? Then you are in the right place. In this article you will have a clear understanding of the Technical Hierarchy of Tech Mahindra and the …
Increased development and spread of information technology and the internet had led to creation of distinct ways to communicate in virtual environments. The cognitive interfaces provide a new form of interaction between humans and systems. The graphical user interface is …
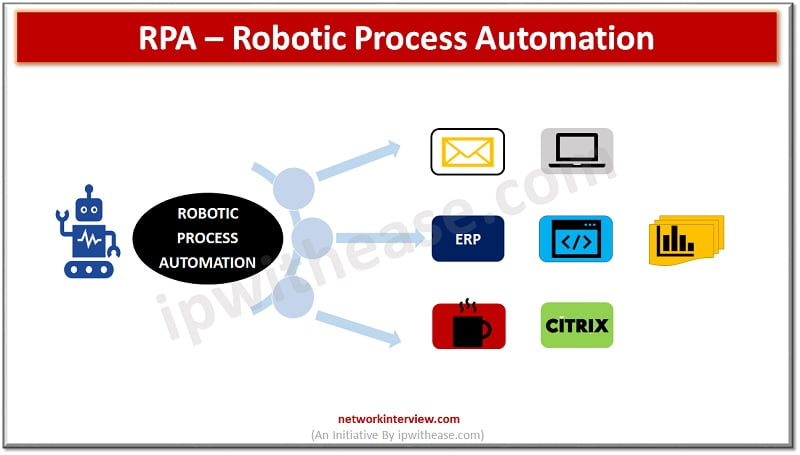
Introduction to RPA Convergence of the physical world and digital world has changed how businesses are interacting with customers nowadays. Robotic Process Automation can be tracked back in early 2000 , it has progressed and developed over a number of years. …
Introduction to Agile Methodologies Most organizations are adopting agile methodology to enable better collaboration between customer and the IT. With Agile the power of teamwork is unleashed. Agile is an iterative approach which concentrates on a continuous delivery framework. The …
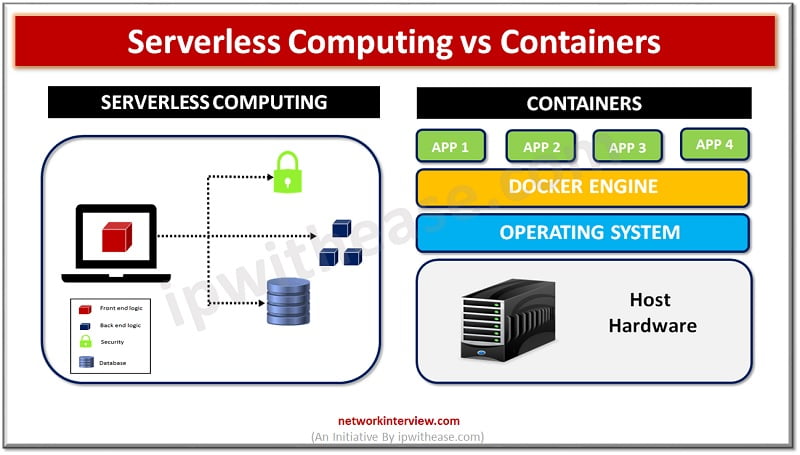
Introduction In the era of enterprise computing organizations are seeking ways to develop, deploy and manage applications in a more efficient , fast and scalable manner. Traditionally applications are tightly linked to servers and the operating systems which executed their …
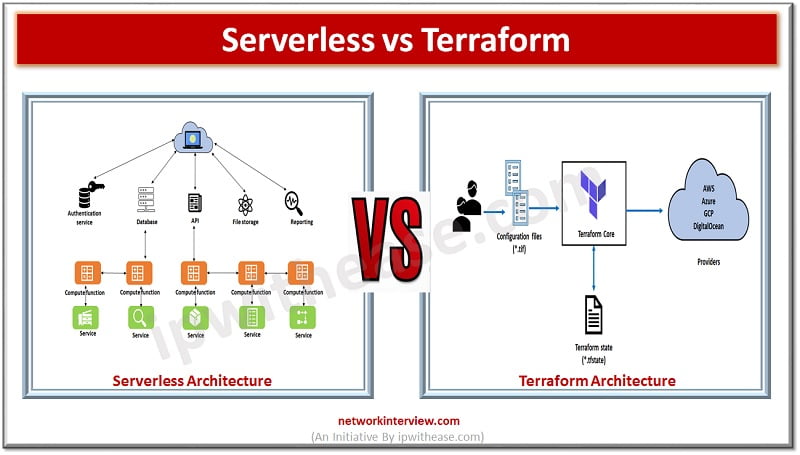
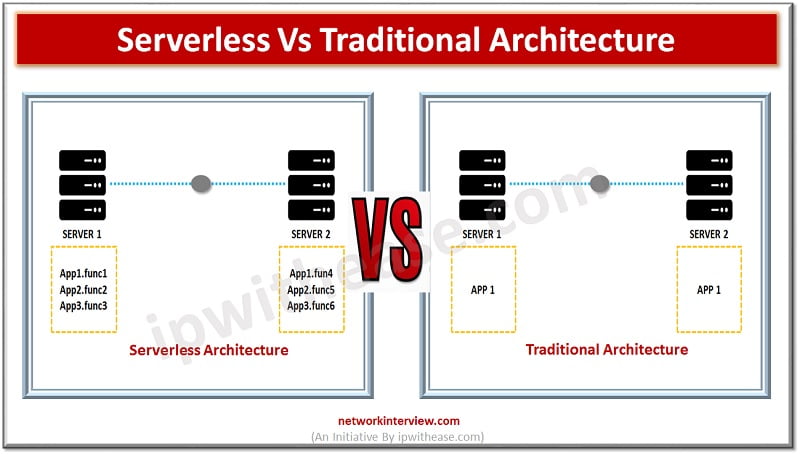
Introduction to Serverless Architecture Over the years organizations have invested money in buying costly servers. The traditional architecture requires large IT staff for maintaining data centres, training and hiring skilled personnel, tracking obsolete hardware and replacing it which would bring …
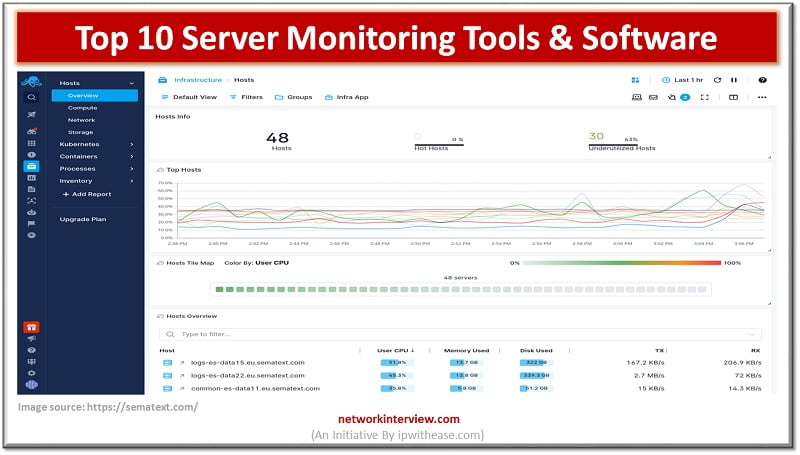
Importance of Server Monitoring Server performance monitoring is an important function that every organization that uses cloud technology should be aware of. The server monitoring makes sure your server resources are being utilized fully and it runs smoothly. In this …
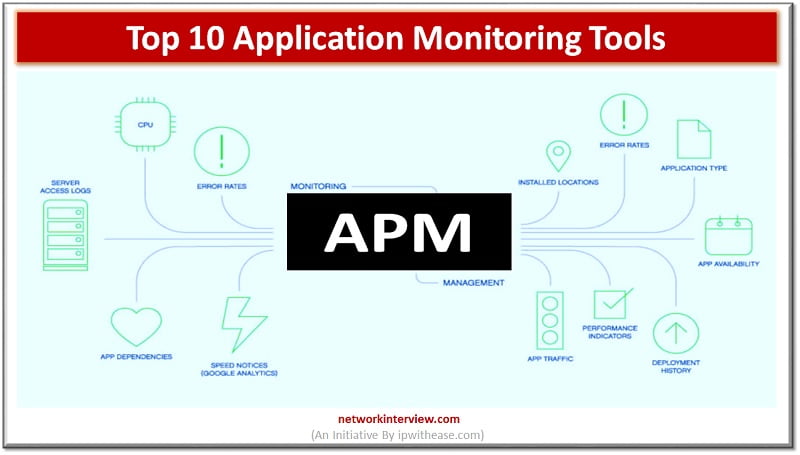
Importance of Application Monitoring The day-to-day life of every person in this world depends on more than one application. This need led to the creation of different types of apps and thus creating the demand for Application Monitoring Tools. Every …
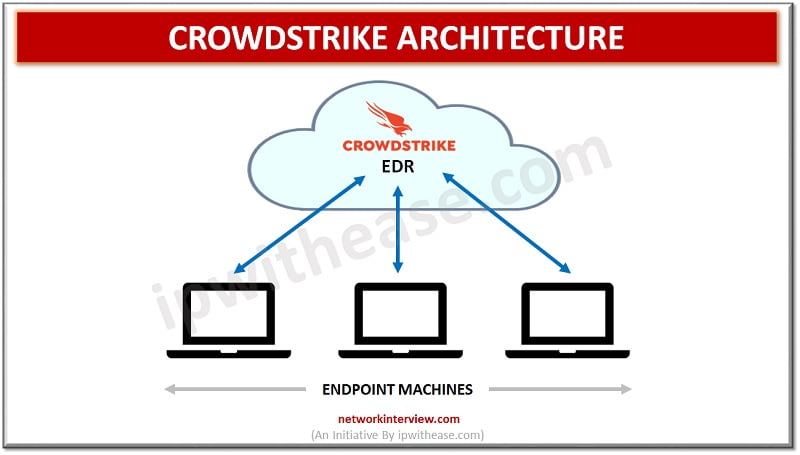
Introduction to Crowdstrike Threat Intelligence and Endpoint Protection is of paramount importance for organizations especially in the scenario where organizations have moved their IT infrastructure over cloud and sophisticated hackers are moving beyond malware to breach organizations. Increasingly relying on …
It is a common interest to know about the position you are going to be hired and its hierarchy in the chain of command. But it is not easy to know the internal workings of organizations. Do you want to …
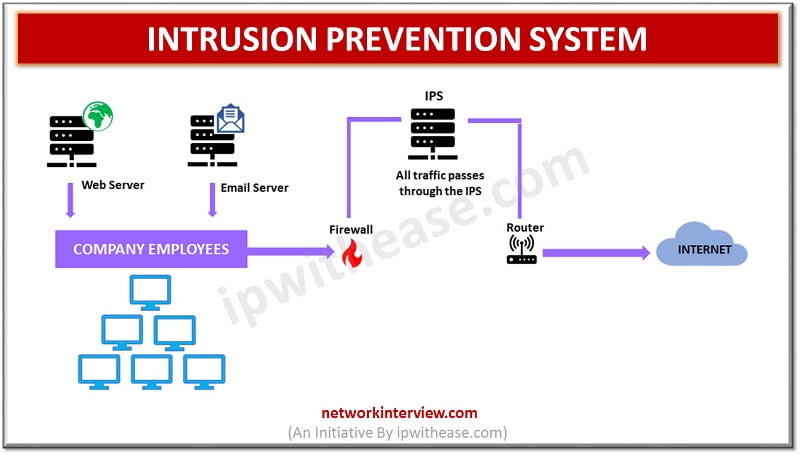
Network security is of paramount importance. Organizations invest the majority of their resources in security of their networks from external attacks using firewalls and intrusion prevention systems; however if a breach occurs in this system, intruders will have access to …
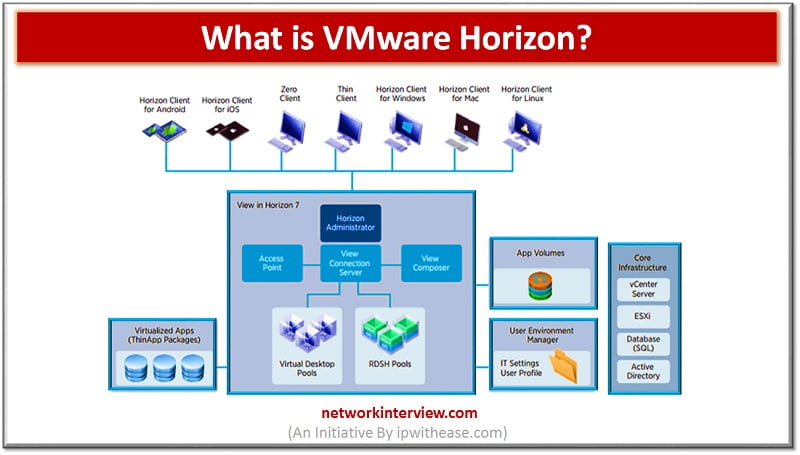
Introduction to VMware Horizon In the IT industry, VMware Horizon is defined as a commercial desktop and app virtualization product developed by VMware Inc for Microsoft Windows, Linux and macOS operating systems. It was initially introduced in the market with …
Data centres operations be it from cloud or on premises network is the backbone of these infrastructures which supports businesses starting from application delivery to security. As workloads are changed, migrate, evolve networking technologies too need to match the pace. …
Introduction to TCP RST Protection of sensitive data is major challenge from unwanted and unauthorized sources. The next generation firewalls introduced by Palo Alto during year 2010 come up with variety of built in functions and capabilities such as hybrid …
Have you cleared an interview with HP Enterprise? Congrats! By the way, do you know about the technical Hierarchy or your designation in HPE’s Chain of Command? Don’t worry, here in this article you will get the basic information about …
Introduction to Cryptography Cryptography is crypto + graphy, where “crypto” means “hidden” or “secret” and “graphy” means “to write”. Cryptography is a technique through which the information/data is communicated securely/secretly. This technique is irreplaceably essential in the present world of …
Introduction to Packet Capturing Before discussing Palo alto packet capture, let’s first understand the term packet capture. Packet capture is network interception of data packet which can be analysed , downloaded, archived or discarded. The reason for packet capturing is …
Introduction to Top Internet Providers in US In the US Telecommunications market , we observe an evolution to the services provided by ISP companies that changes almost every month. Therefore, in the list that follows, please consider that all …
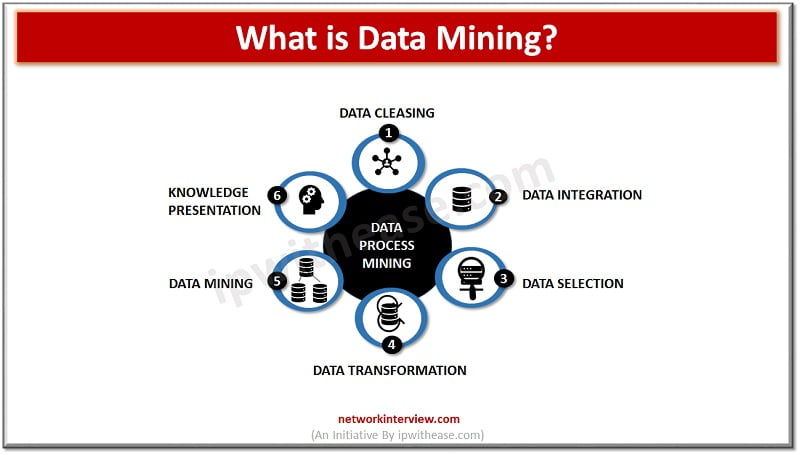
The volume of data which is being produced every year is very …very huge and doubling almost every two years. The digital universe is 90% of unstructured data but that does not mean more volume of data means more information. …
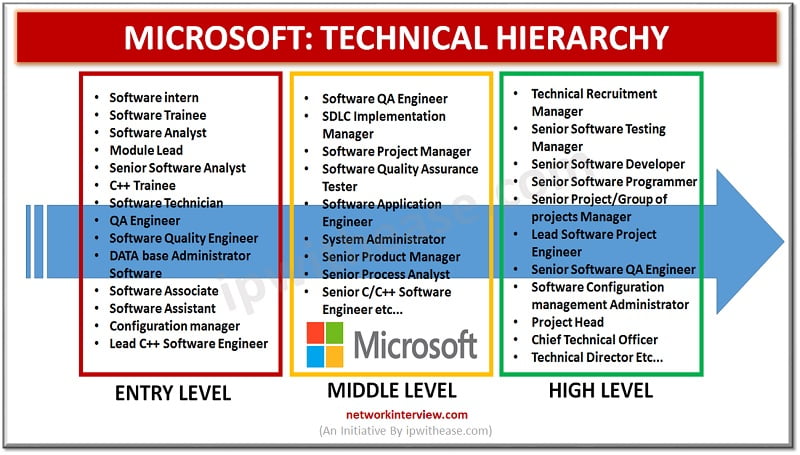
Getting a job in MICROSOFT is a dream come true. But are you worried about the hierarchy and chain of command of your work environment? You are in the right place. It’s normal to think about the hierarchy in your …
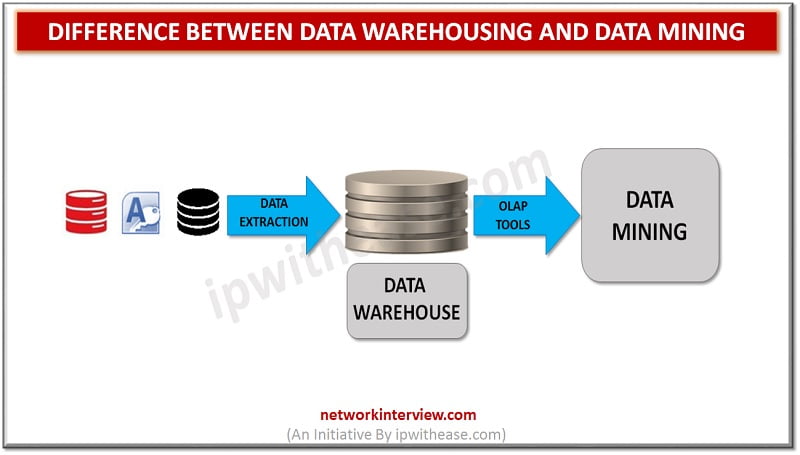
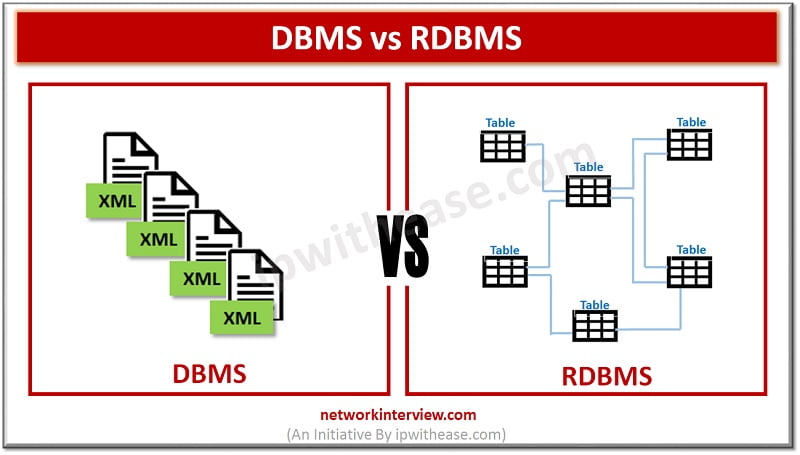
Before discussing difference between Data Warehousing and Data Mining, let’s understand the two terms first. Data Warehousing Data Warehousing refers to a collective place for holding or storing data which is gathered from a range of different sources to derive …
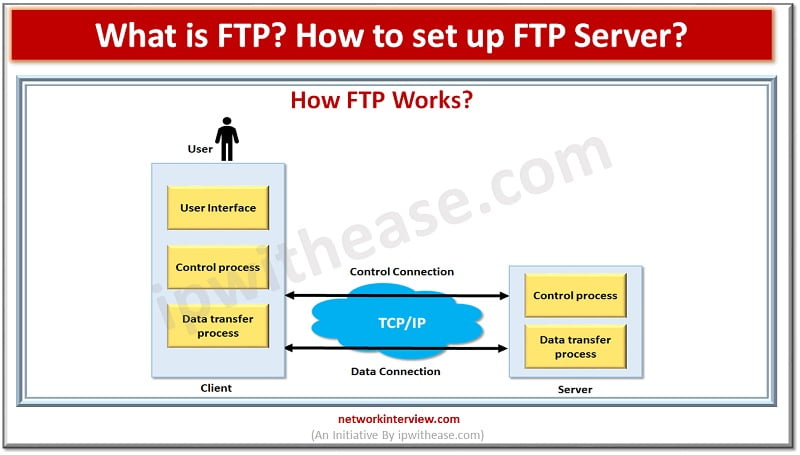
File transfer protocol (FTP) has been around for more time than HTTP and TCP/IP protocol and has more than 40+ years of existence in the industry. Its original specification was written way back in 1971 and initial FTP clients were …
The data world is constantly evolving and changing, this in turn has created a necessity to have a solution, software or technology in place to handle the data in the proper manner. The need to create and manage properly is …
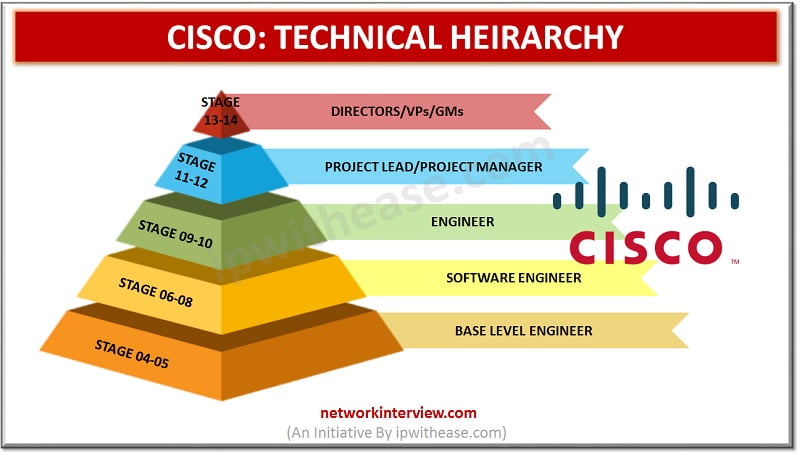
If you are thinking of the networking and IT field, then you must have heard about the CISCO. Cisco is highly ranked at 63rd spot in Fortune 500 (2020) companies. Are you planning to get a job in CISCO? Then …
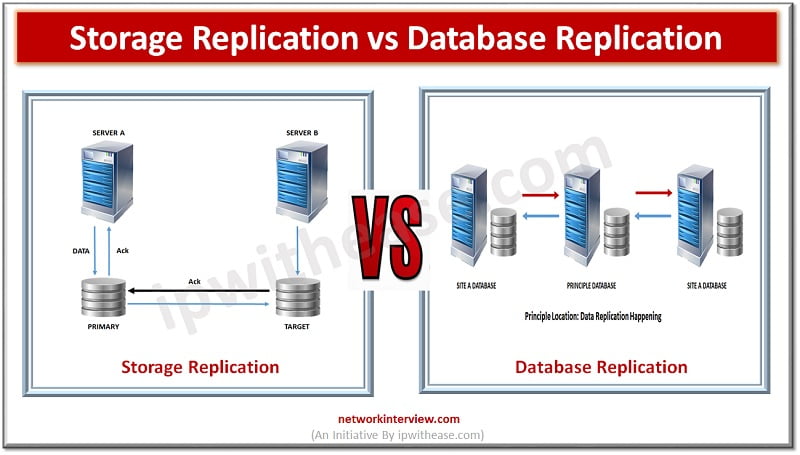
Mission critical Business applications require uninterrupted availability of systems. Use of ‘Replication’ technologies let IT environments deliver robust data protection for the enterprises. Today we look at some replication technologies ! Storage Replication Storage replication technology enables replication of volumes …
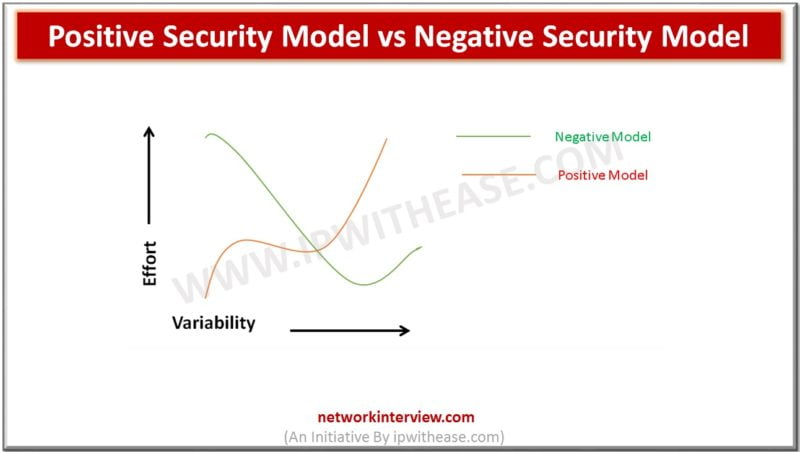
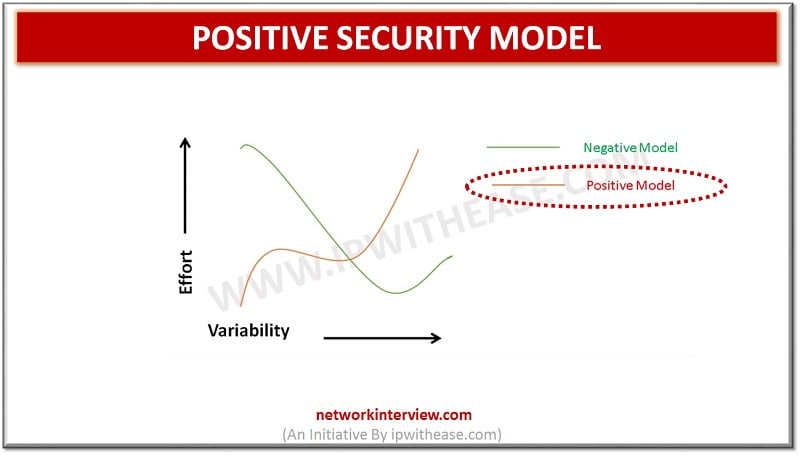
Introduction : Positive Security Model & Negative Security Model Achieving highest level of security and being one step ahead from the hackers has always been a significant challenge for any IT company. Security is always a hot discussion topic whenever …
Network Security Models: There are two types of Network Security Model: Positive Security Model Negative Security Model In this post, we will discuss Positive Security Model in detail. Positive Security Model While setting up Web facing applications, a lot of …
Cybersecurity Trends With more and more digital advancement and penetration of cloud organizations are very much concerned about the cybersecurity threats which are on high rise and have an upward trend. Emerging technologies such as cloud computing, Artificial intelligence (AI), …
Network security is designed to protect organization information by protecting the integrity of the network from unauthorized access and threats. The system networks are linked to daily transactions and communication within the organizations private or government which need security. The …
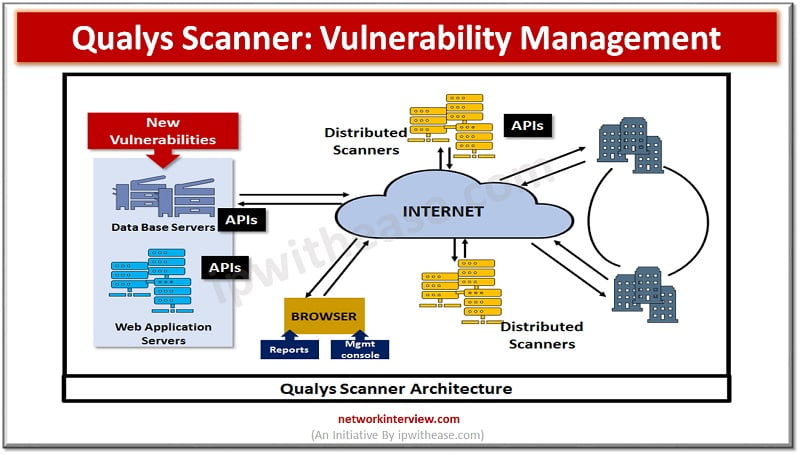
Vulnerability management is a critical component of risk management as attackers are always looking for new vulnerabilities to exploit and take advantage of them which may have gone unnoticed. Several Vulnerability management tools are available in the market which help …
Introduction to Spoofing Today, in the cyber security community “spoofing” is called as any fraudulent or malicious practice in which communication is established from an unknown source, usually disguised as a known source to the receiver. In order to understand …