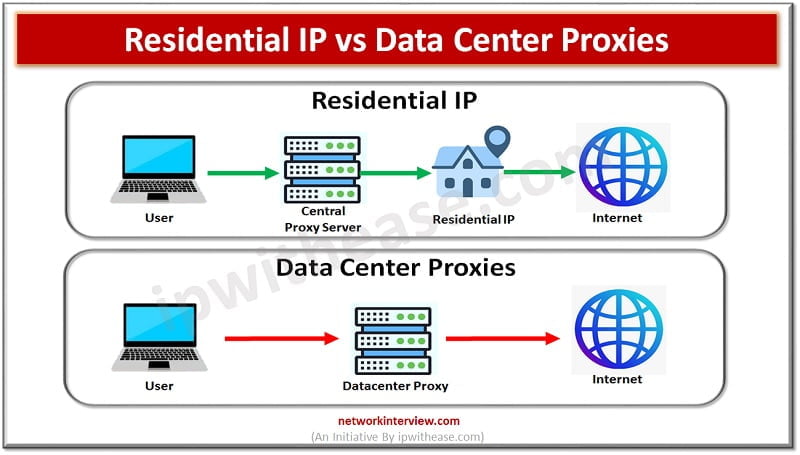
Today, a lot of people use proxy servers to access their accounts, so they may alter their IP addresses and stay out of trouble. The same cannot be said for all IP addresses. There are two types of IP proxies …
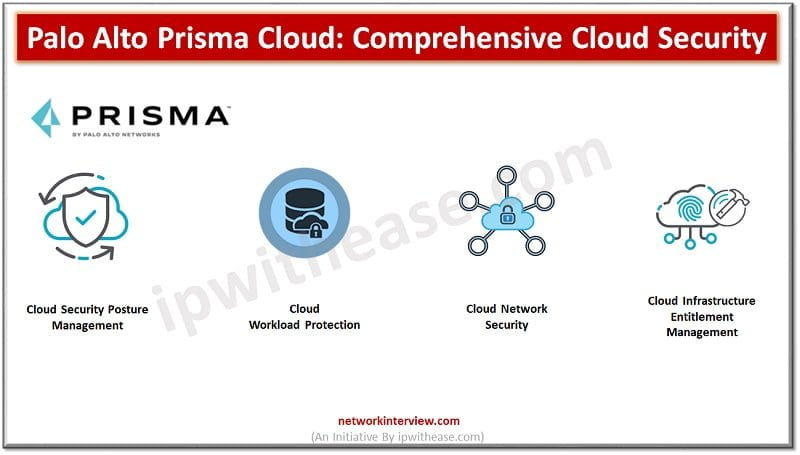
Cloud native technologies are helping Development teams to build and deploy applications faster than before. However, this open architecture increases challenges to Security teams. Cloud workloads are spread-out across Virtual Machine Containers Serverless and many points in between security devices …
To have faster time to market and bring in business agility organizations are more and more relying on technology. Technological advancements have one side facilitated business to grow faster and quickly adapt to changing needs of businesses and on other …
Though it’s been a while since cloud technology was introduced into our world still there is much confusion surrounding Network Security and Cloud Security. If you are one of those who can’t find the difference between these two terms: Network …
Every new technology or software invented goes under this question “Is it secure?” That’s how security is always considered an important feature in the digital era. But do we understand them clearly? Over time security is classified further into cloud …
Cyber security software is a must for ensuring business and individuals security and privacy. It is a method to protect networks, systems and applications from cyber-attacks. It helps to avoid unauthorized data access, cyber attacks and identify stealing. Application, information …
Agility and innovation are key ingredients for digital transformation. However, agility requirements are hindered by telco-controlled SD WAN or MPLS networks. Slow moving ISPs and need to deploy expensive custom hardware, telco circuits, and VPNs create roadblocks and stop transformation …
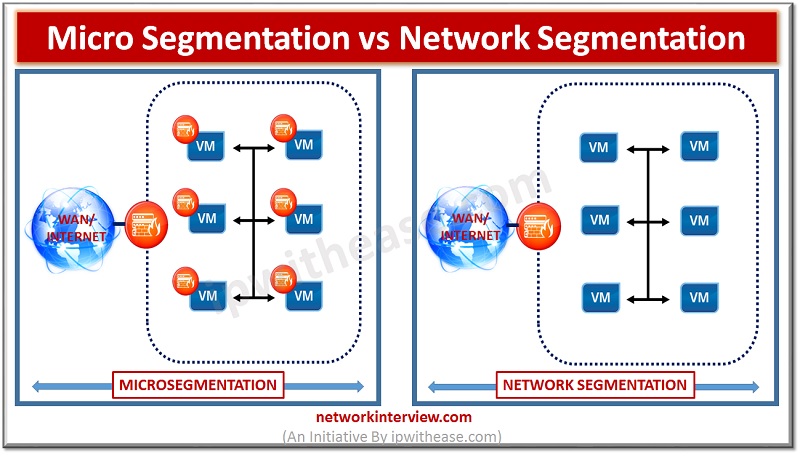
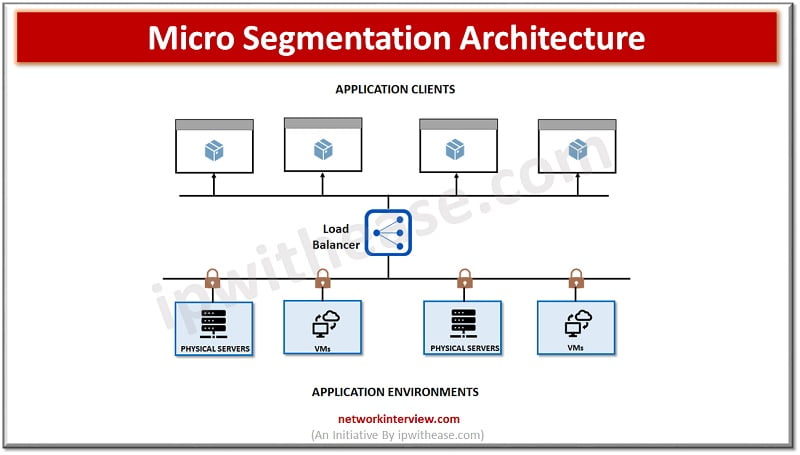
Micro segmentation vs Network Segmentation Over many years, Perimeter security has been considered the key to presenting a robust and secured network ecosystem . This was considered a suitable methodology when the network attacks were not so advanced and North-South …
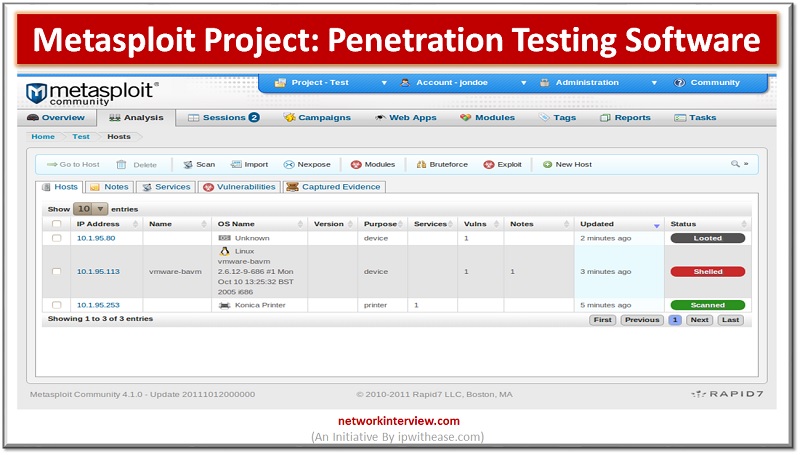
Introduction to Metasploit Project In the worldwide IT security community, we define the Metasploit Project as a computer security project that mainly provides information about security vulnerabilities and helps in penetration testing and development of the IDS Signatures. It is …
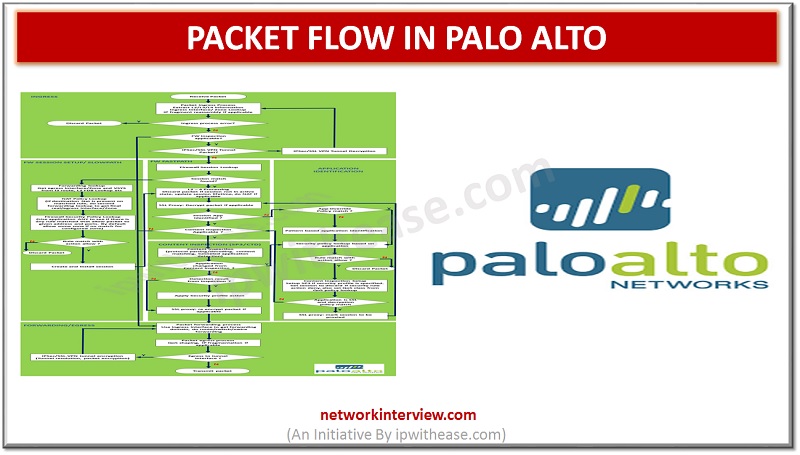
In this article, we will discuss on Packet handling process inside of PAN-OS of Palo Alto firewall. Introduction: Packet Flow in Palo Alto Packet passes through the multiple stages such as ingress and forwarding/egress stages that make packet forwarding decisions on …
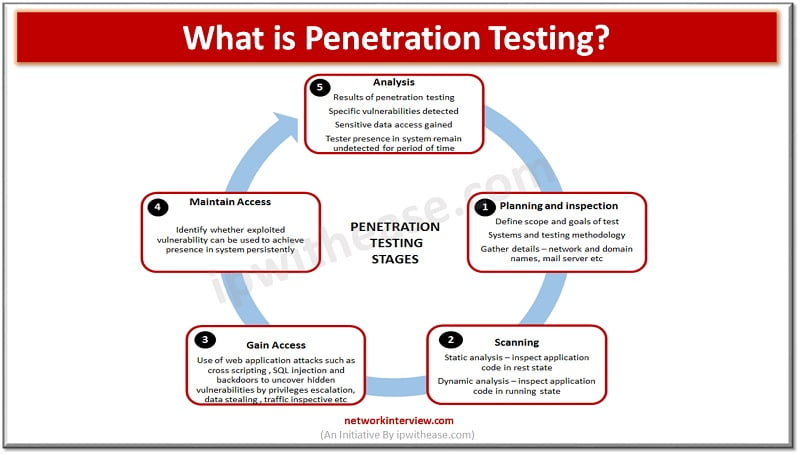
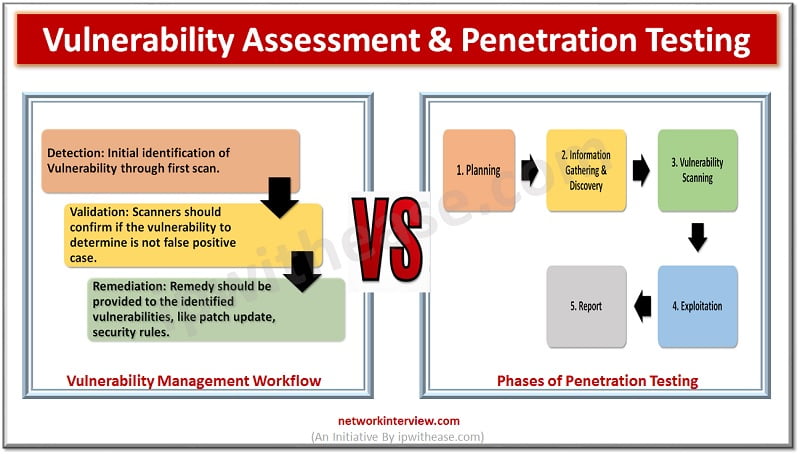
Introduction Vulnerability assessment is the way to identify weakness in the system. Vulnerability itself means “Weakness” and Vulnerability assessment means how to find weakness in a system and create a report accordingly. On the other hand, Penetration testing is used …
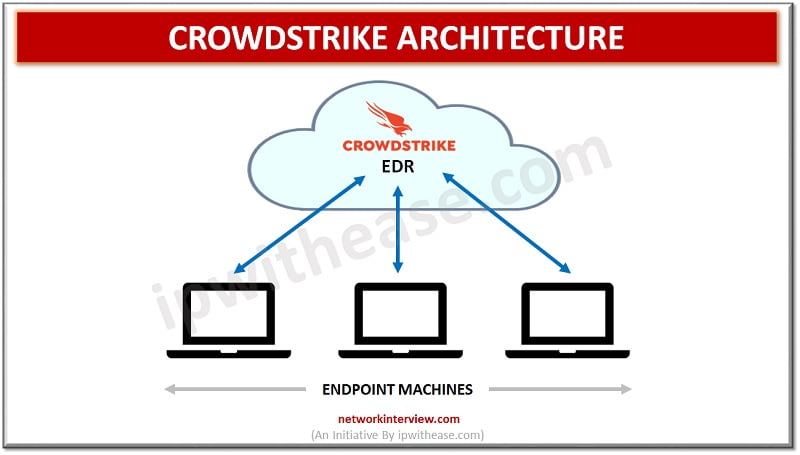
Introduction to Crowdstrike Threat Intelligence and Endpoint Protection is of paramount importance for organizations especially in the scenario where organizations have moved their IT infrastructure over cloud and sophisticated hackers are moving beyond malware to breach organizations. Increasingly relying on …
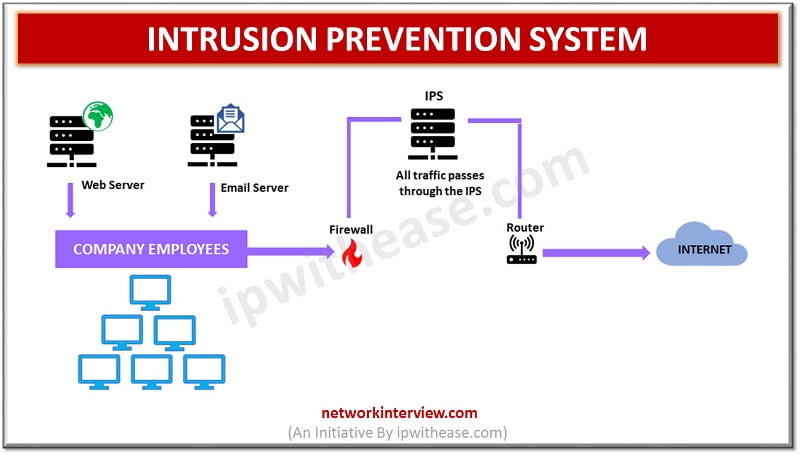
Network security is of paramount importance. Organizations invest the majority of their resources in security of their networks from external attacks using firewalls and intrusion prevention systems; however if a breach occurs in this system, intruders will have access to …
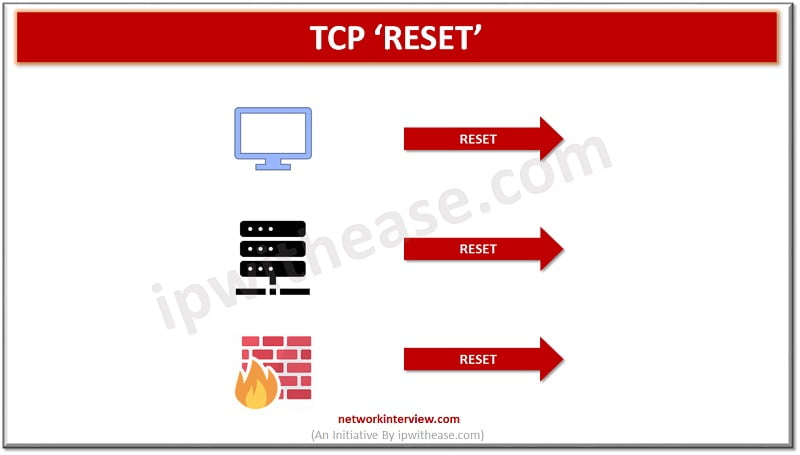
Introduction to TCP RST Protection of sensitive data is major challenge from unwanted and unauthorized sources. The next generation firewalls introduced by Palo Alto during year 2010 come up with variety of built in functions and capabilities such as hybrid …
Introduction to Cryptography Cryptography is crypto + graphy, where “crypto” means “hidden” or “secret” and “graphy” means “to write”. Cryptography is a technique through which the information/data is communicated securely/secretly. This technique is irreplaceably essential in the present world of …
Introduction to Packet Capturing Before discussing Palo alto packet capture, let’s first understand the term packet capture. Packet capture is network interception of data packet which can be analysed , downloaded, archived or discarded. The reason for packet capturing is …
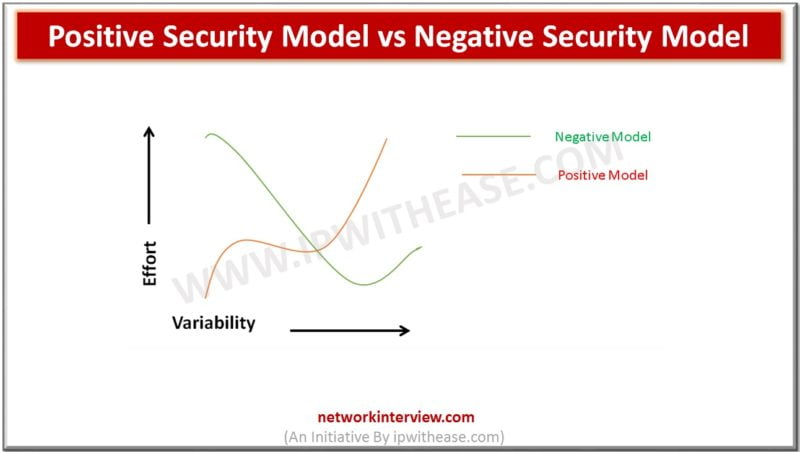
Introduction : Positive Security Model & Negative Security Model Achieving highest level of security and being one step ahead from the hackers has always been a significant challenge for any IT company. Security is always a hot discussion topic whenever …
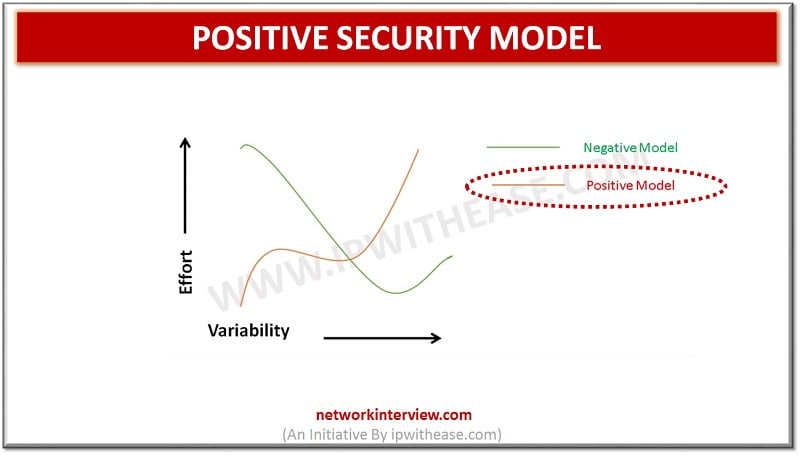
Network Security Models: There are two types of Network Security Model: Positive Security Model Negative Security Model In this post, we will discuss Positive Security Model in detail. Positive Security Model While setting up Web facing applications, a lot of …
Cybersecurity Trends With more and more digital advancement and penetration of cloud organizations are very much concerned about the cybersecurity threats which are on high rise and have an upward trend. Emerging technologies such as cloud computing, Artificial intelligence (AI), …
Network security is designed to protect organization information by protecting the integrity of the network from unauthorized access and threats. The system networks are linked to daily transactions and communication within the organizations private or government which need security. The …
Introduction to Spoofing Today, in the cyber security community “spoofing” is called as any fraudulent or malicious practice in which communication is established from an unknown source, usually disguised as a known source to the receiver. In order to understand …
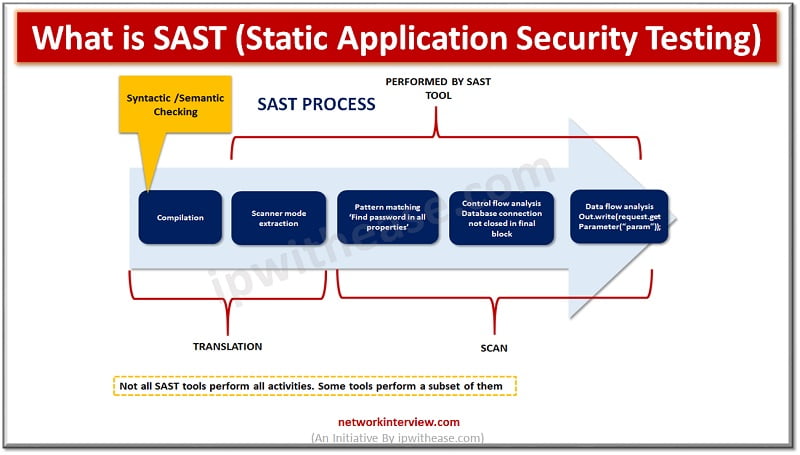
Introduction to SAST Application security testing makes applications more resilient to security threats and identifies weaknesses and vulnerabilities in application source code. Initial days software code testing was done manually however as organizations matured and software’s became modular in nature …
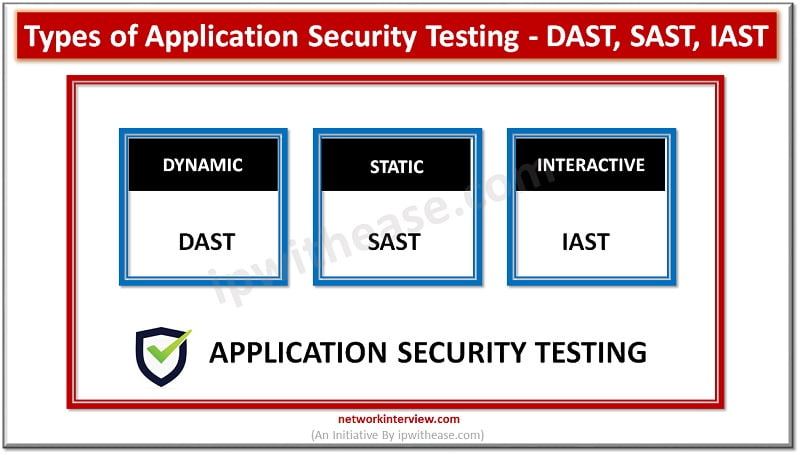
Introduction to Application Security Testing Application Security testing is an integral part of SDLC (Software development lifecycle) and used to discover the weaknesses, risks or threats in software applications and help to detect vulnerabilities hidden in applications which can be …
Introduction to Palo Alto Firewall is a network security device that permit or denies network access to traffic flows between an untrusted zone and a trusted zone. Palo Alto Firewall is one of the globally coveted and widely preferred Security …
Introduction Palo Alto has been considered one of the most coveted and preferred Next generation Firewall considering its robust performance, deep level of packet inspection and myriad of features required in enterprise and service provider domain. When troubleshooting network and …
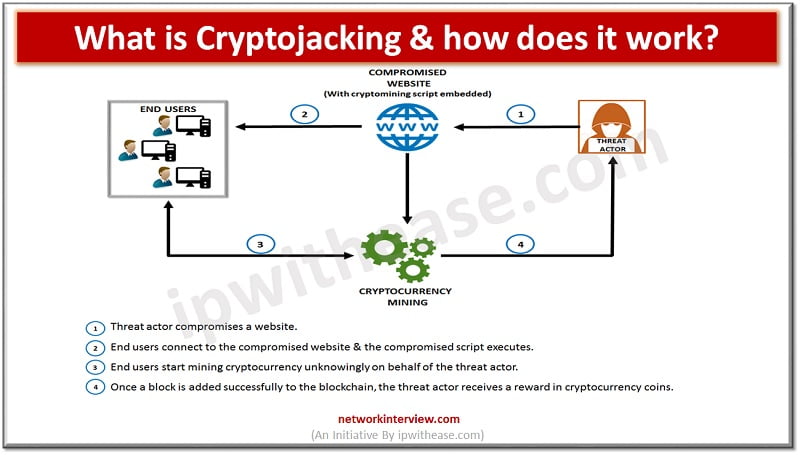
The modern technologically advanced world not only opens the gate for new opportunities but also for new threats. One of them is Cryptojacking, a cybercrime that became more active in the past two decades. Is this your first time hearing …
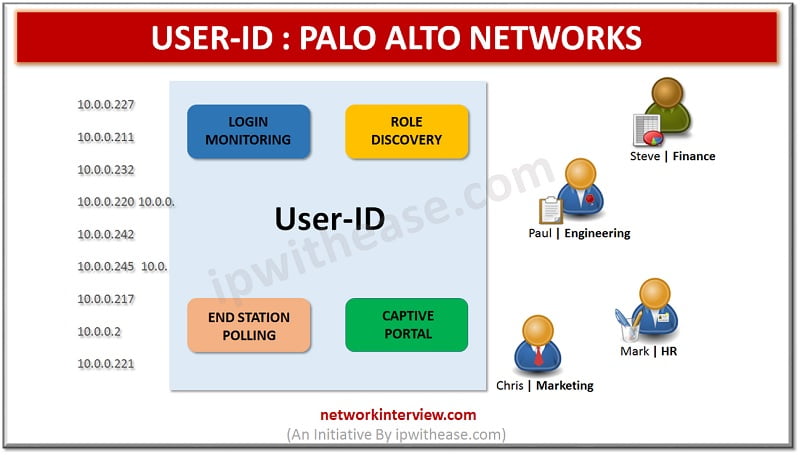
In this article, we will understand the terminologies related to USER ID and their role w.r.t login monitoring, role discovery and related nuances. USER ID : PALO ALTO NETWORKS User Identification is a very unique feature of Palo Alto firewall …
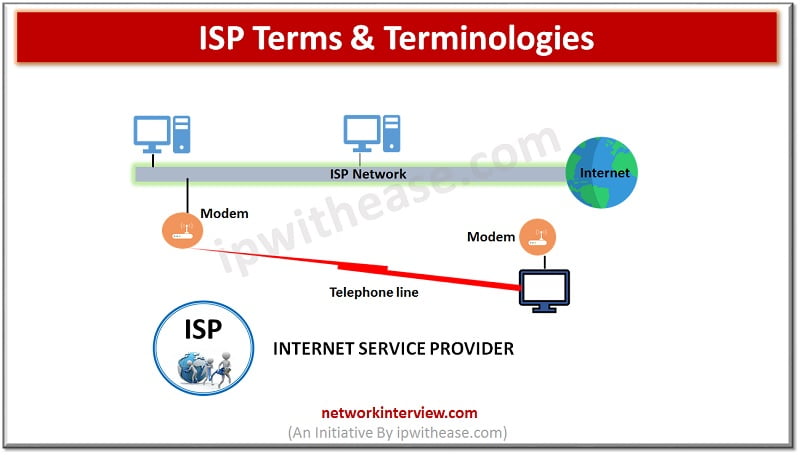
ISP stands for Internet service provider they offer a wide variety of Internet services related to browsing, Email services, faxing capability, audio and video communications and hosting services etc. Let’s look more in detail about Internet service provider (ISP) and …
Introduction to CASB Solutions CASB (Cloud Access Security Broker) is an intermediary between cloud users and cloud applications. CASB solution is a software/hardware application that is located inside the network or works as a cloud-native application. Cloud access security broker …
Difference Between MD5 and CRC MD5 and CRC are 2 of most commonly used hashing algorithms, infact while comparing files and including other use cases. In this article. We will understand both the concepts of hashing algorithm and how one …
SSL Certificate types : Intermediate Certificate and Root Certificate When we look at the function of the SSL certificates at the first glance, then we would find that they are pretty straightforward. You would simply install it to your concerned …
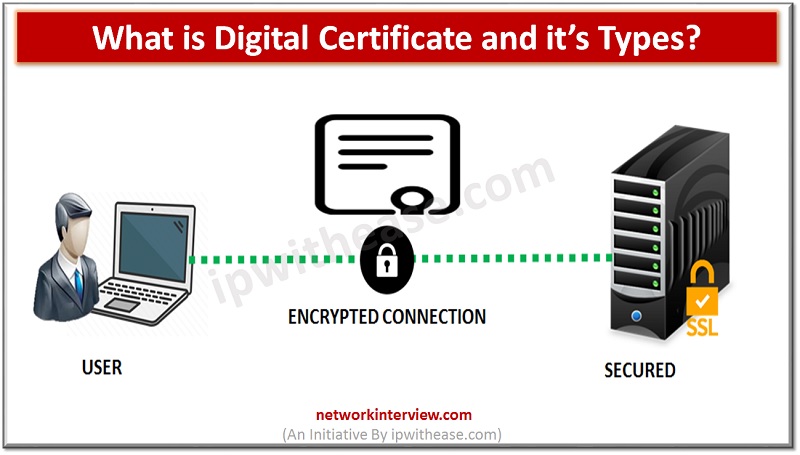
A digital certificate, which is also termed as public key certificate is applied to cryptographically link up the ownership of public key to the entity owning the same. Here, we are going to get a better insight of what is …
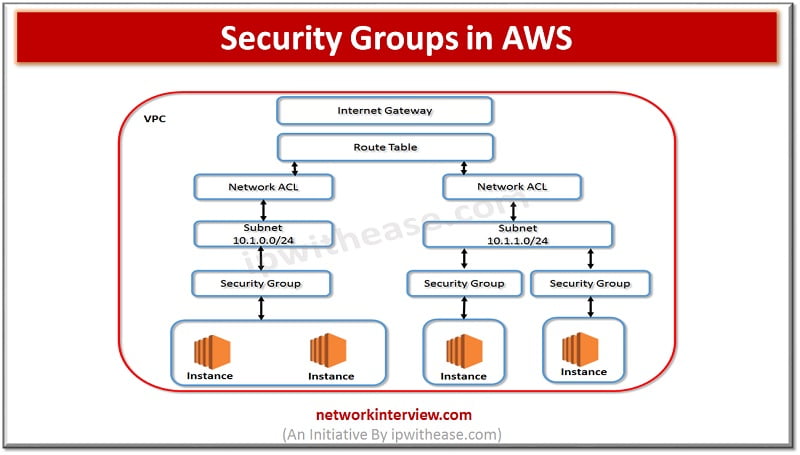
Security Groups in AWS I am sure that while working on Security groups, we do ponder about Firewalls and Rules i.e. allowing or denying traffic based on hardware or software firewalls. In case of AWS security groups are very similar …
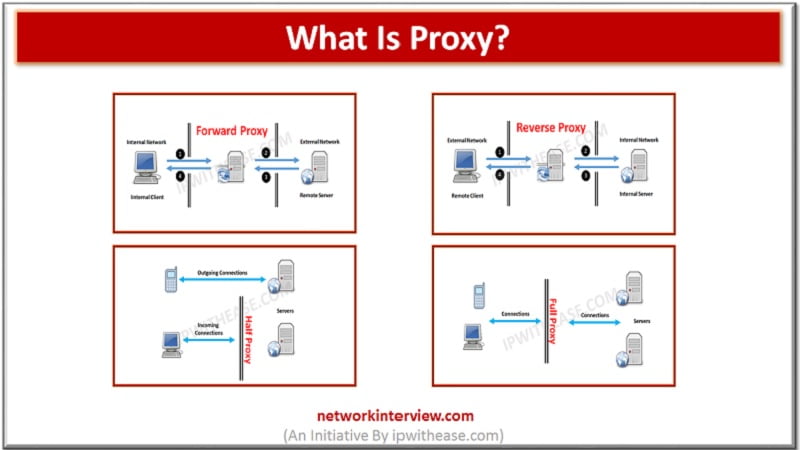
Proxies (often called intermediaries in the SOA world) are hardware or software solutions that sit between the client and the server and do something to requests and sometimes responses. The most often heard use of the term proxy is in …
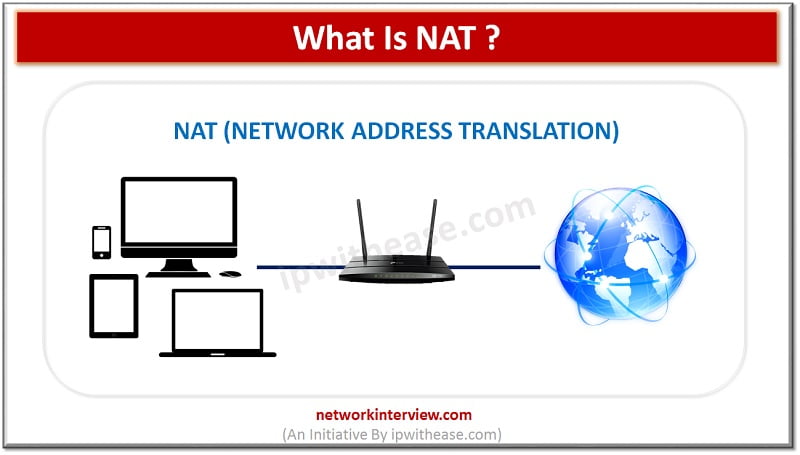
NAT (NETWORK ADDRESS TRANSLATION) In computer networking, Network Address Translation (NAT) is the process of modifying IP address information in IP packet headers while in transit across a traffic routing device. Network Address Translation (NAT) allows security administrators to overcome …
Firewalls are computer software programs that hinder illegitimate access to or from a personal network. They are used to improve security in a system of computers connected to a similar interface, including the Internet and LAN. Thus, they are a …
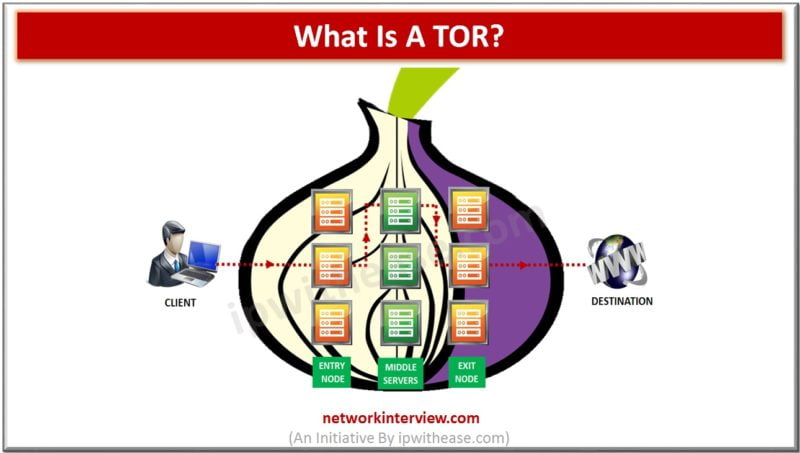
TOR (The Onion Router) is a software and open network which allows the users to browse the Web anonymously. TOR makes it difficult, if not impossible, for any snoops to see our web mail, search history, social media posts or …
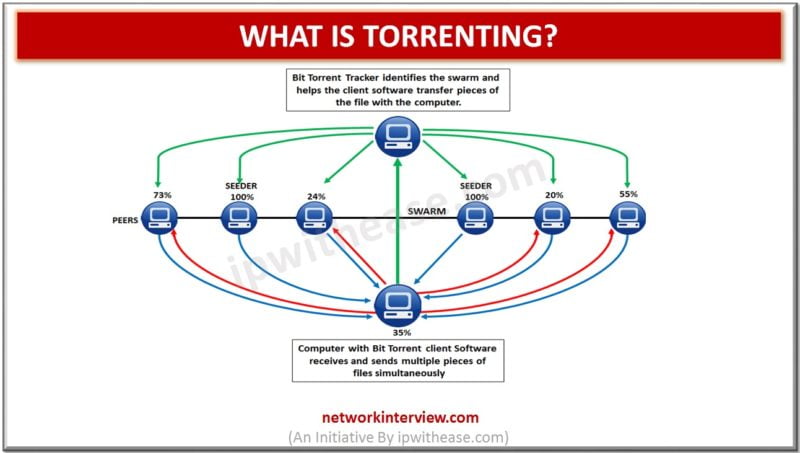
Introduction to Torrenting Torrenting is a P2P (peer-to-peer) file sharing technology used to share files efficiently. This technology relies on a community of decentralized users for file sharing rather than being dependent on traditional single website or source for downloading. …
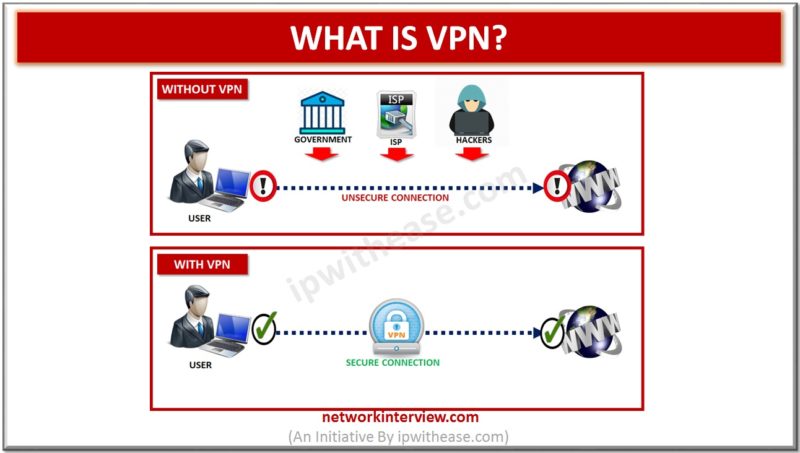
VPN (Virtual Private Network) is a technology that lets you access the web safely and privately. It acts like a secure tunnel between your device and the internet. The information traveling between a connected device (computer, smartphone, tablet) and a …