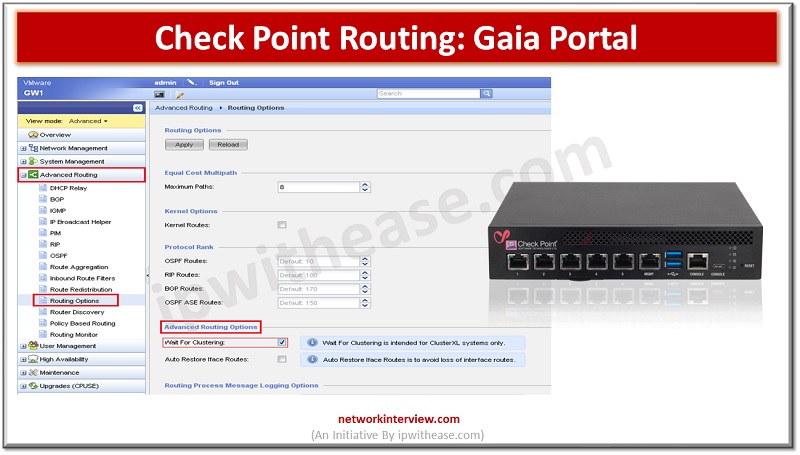
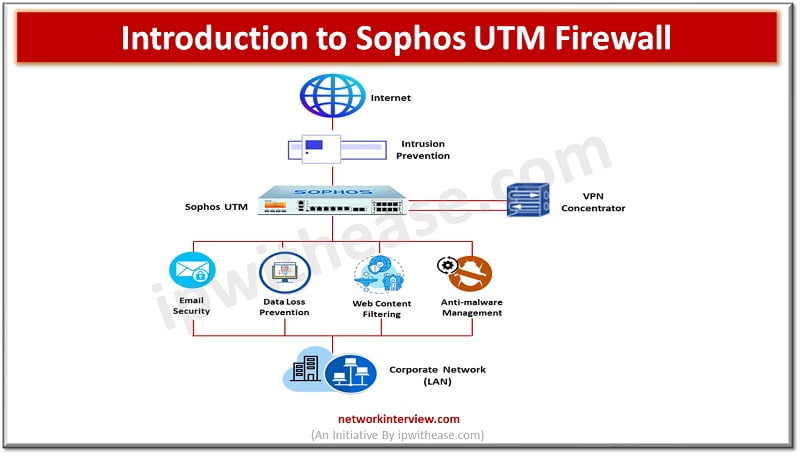
Gaia is the latest operating system for security applications developed by Check Point. It is named after Gaia, the mother of all in Greek mythology, symbolizing a well-integrated system comprising various components to ensure optimal performance. Gaia OS is designed …
Firewalls have come a long way and have been there for decades to provide protection against malicious attacks and intrusions. In their infancy days firewalls were a simple filtering mechanism based on ports and IP addresses. But over time, firewalls …
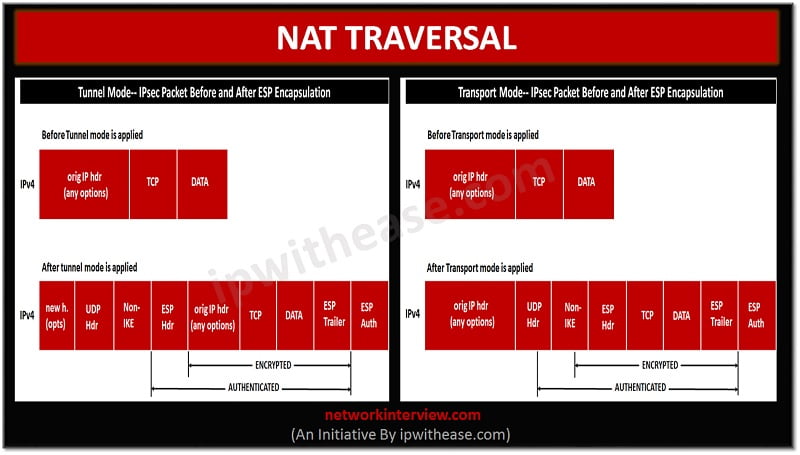
Overview The IPSEC NAT Traversal feature introduces IPSEC traffic to travel through Network Address Translation (NAT) or Port Address Translation (PAT) device in the network by addressing many incompatibilities between NAT and IPSEC. NAT Traversal is a UDP encapsulation which …
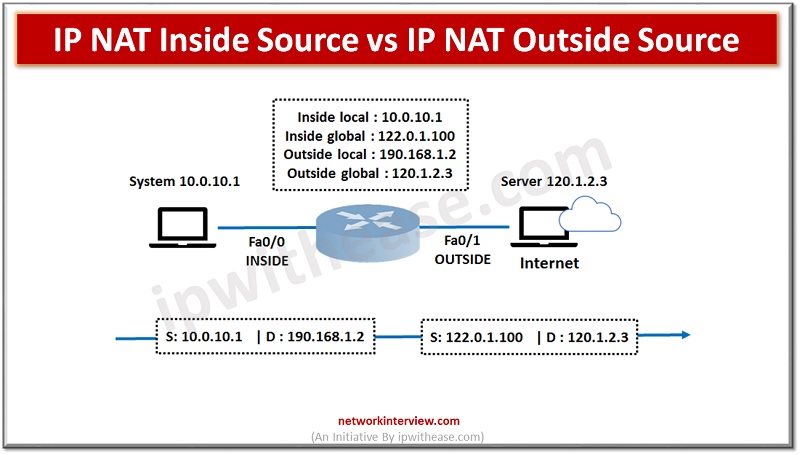
In order to access the Internet, we need one public IP address; however, we can use Private IP address in private networks. The Network address translation (NAT) allows multiple devices to access the Internet with a single public IP address. …
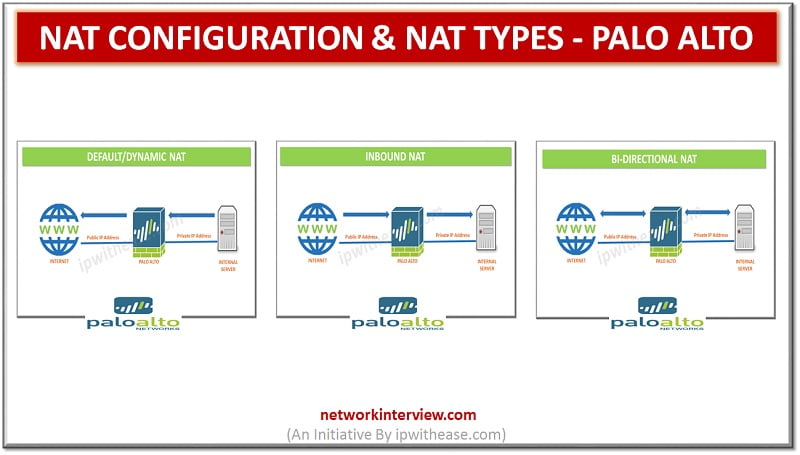
In the previous post we discussed the Architecture of Palo alto firewall. Now, we will discuss the NAT configuration and NAT types in Palo alto. Network Address Translation (NAT) allows to translate private, non-routable IP addresses to one or more …
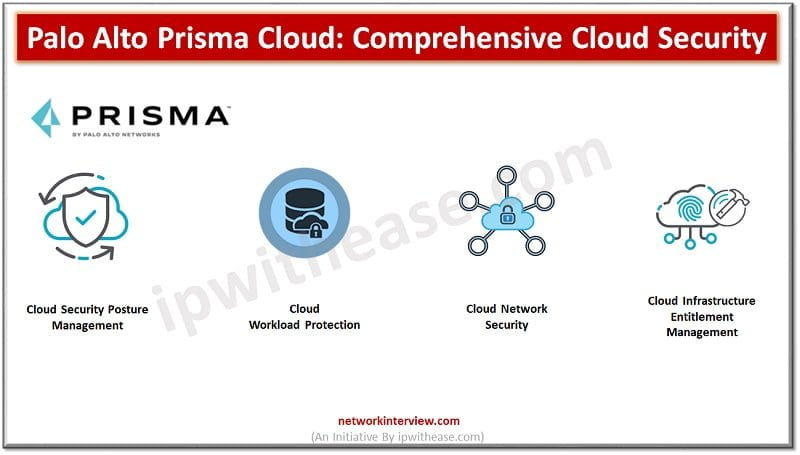
Cyber security is an in-demand security measure that helps to protect enterprises, individuals, and their systems from online threats. It helps secure crucial data within computer devices and networks from unknown access. In this regard, Palo Alto Networks plays a …
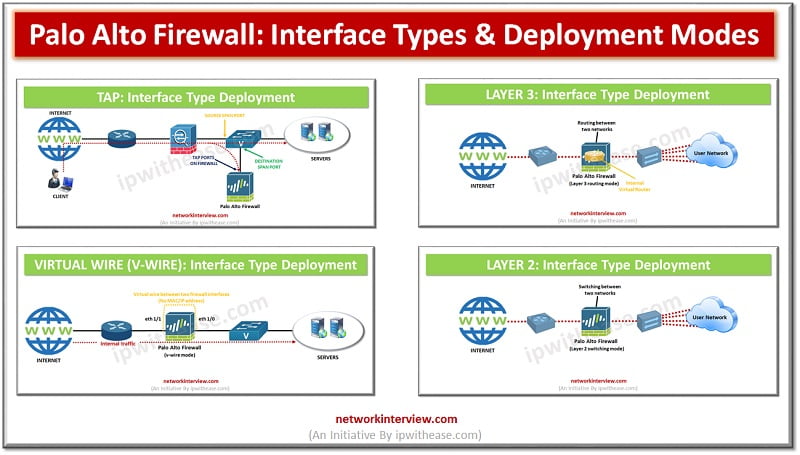
Introduction to Palo Alto Interface types/ Deployment Modes The entry and exit point of traffic in a firewall is enabled by the interface configurations of data ports. Palo Alto being a next-generation firewall, can operate in multiple deployments simultaneously as …
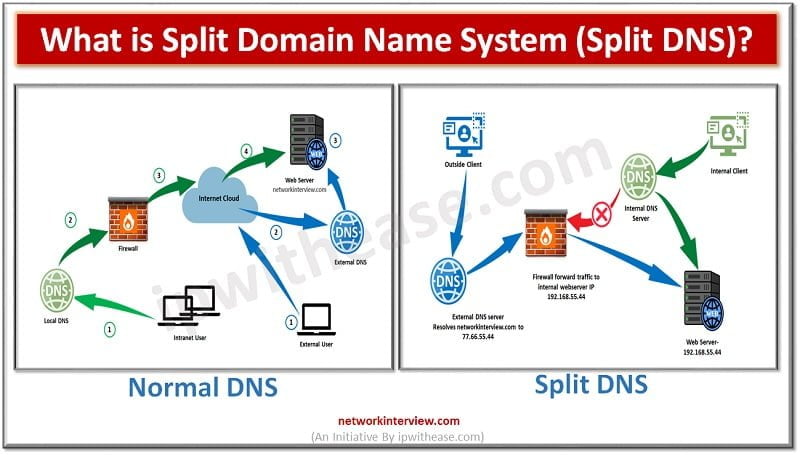
DNS Working Before understanding the Split Domain Name System, let’s discuss how normal DNS resolution works for Internet traffic. However, DNS works to resolve names to IPs. When an Internet client open a Web-browser and type www.networkinterview.com Internet Client will …
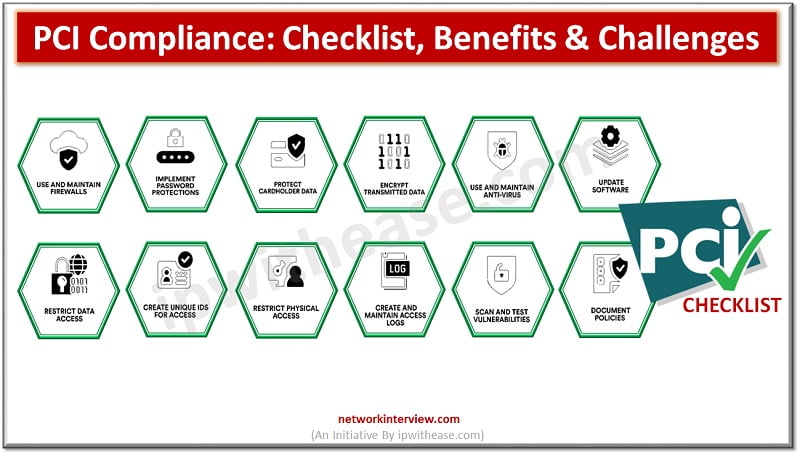
Whether you own a small business or manage a large enterprise, ensuring customer data security is a top priority. To that end, businesses must adhere to the Payment Card Industry Data Security Standard (PCI DSS), a set of security requirements …
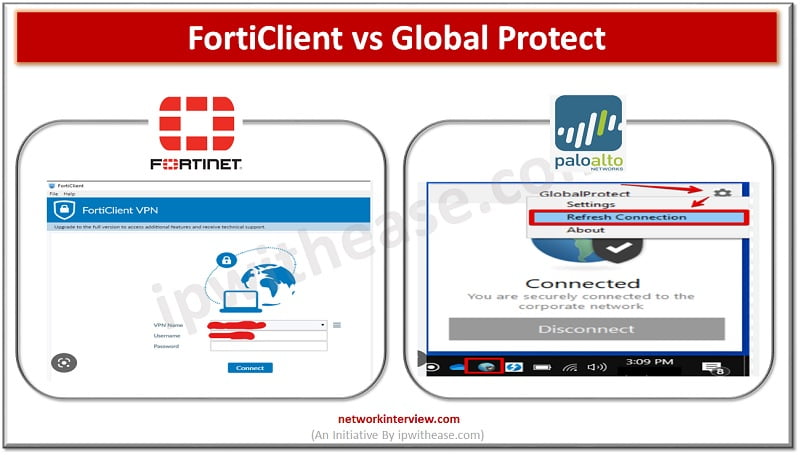
What is FortiClient? FortiClient is an app to provides UTM features like web filtering, giving web security and content-based filtering. FortiClient app is installed in the user’s system and tracks the traffic based on policy. The web application firewall offers malware …
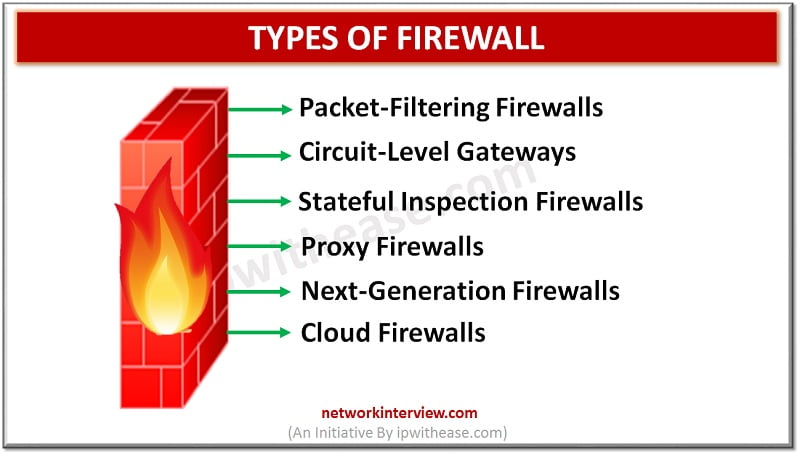
Introduction to Firewall In todays digital scenario, where businesses demand agility and information are hosted on cloud infrastructure security of data is one of the primary concerns of business and protection of data from unwanted sources is the prime objective. …
In 1996, Congress passed the HIPAA law to protect individuals’ health information. This federal act established national standards for how sensitive patient data should be stored and handled, requiring healthcare providers to meet these regulations. To make sure their practice …
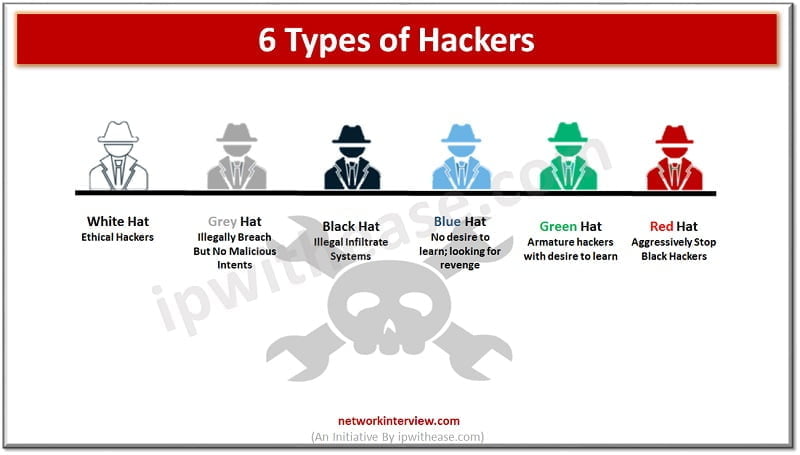
You must have heard the word ‘hacker’ multiple times in cybersecurity. The organizations have trained security staff to take care of cybersecurity threats. Hacking is generally referred to as someone gaining access to your network and systems by unauthorized means. …
With the rise of technology and the internet, the world has become more connected than ever before. From online shopping to social media, we rely heavily on technology in our daily lives. While technology has made our lives easier, it …
Maintaining the security of your personal or business network and Internet connection is essential in today’s digital world. With the rise of sophisticated cyber threats, identity theft, and data breaches, protecting yourself from potential risks is becoming more critical than …
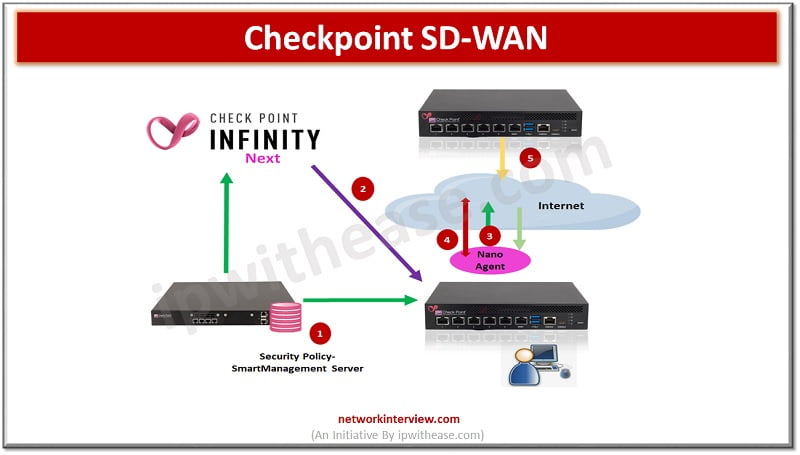
Note: This document is for those seekers who have prior knowledge of SD WAN and want to enhance SD WAN concept in Checkpoint perspective. This blog covers below topics of Checkpoint SD WAN: Quantum CheckpointSD-WAN concept Architecture Application basic traffic …
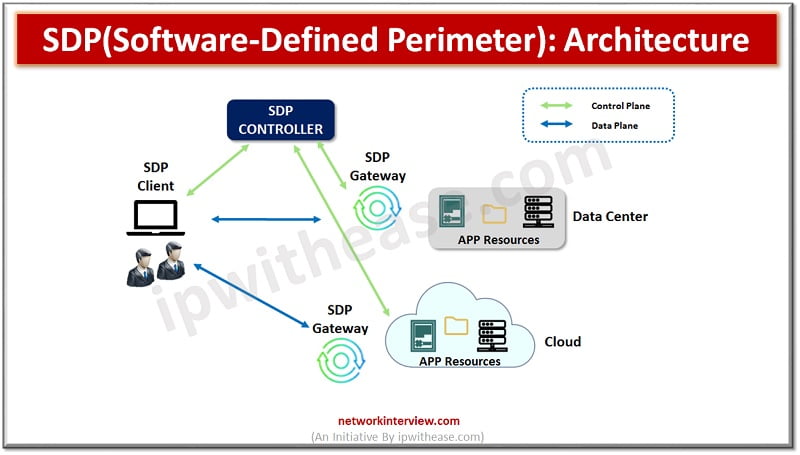
figure:1 As more and more systems are Internet facing due to high penetration of cloud and associates’ applications and services, the need for a very strong security system at perimeter or gateway to enterprises is becoming more and more crucial. …
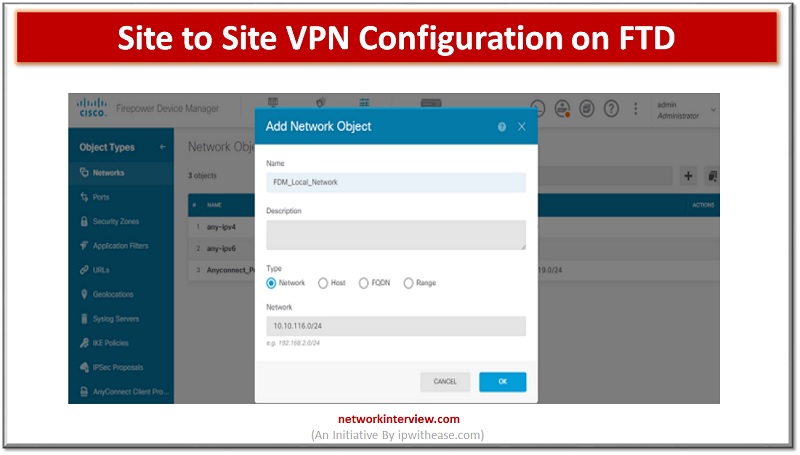
VPNs allow access to restricted sites with secure connection. In FirePower devices we can configure site to site VPN on FTD devices. The site to site VPN is configured for FTD devices using the FirePower Defence management console. In today’s …
Site-to-Site VPN Overview A VPN connection that allows you to connect two Local Area Networks (LANs) securely is called a site-to-site VPN. Route based VPN can be configuring to connect Palo Alto Networks firewalls located at two sites or to …
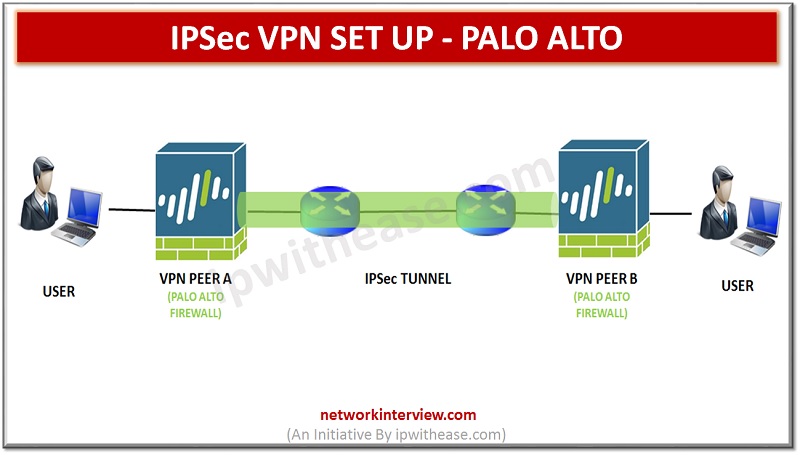
Overview In our previous article, we studied IPSec VPN Set Up. In this article we will run through CLI commands and GUI steps to configure an IPSec VPN, including the tunnel and route configuration on a Palo Alto Networks firewall. …
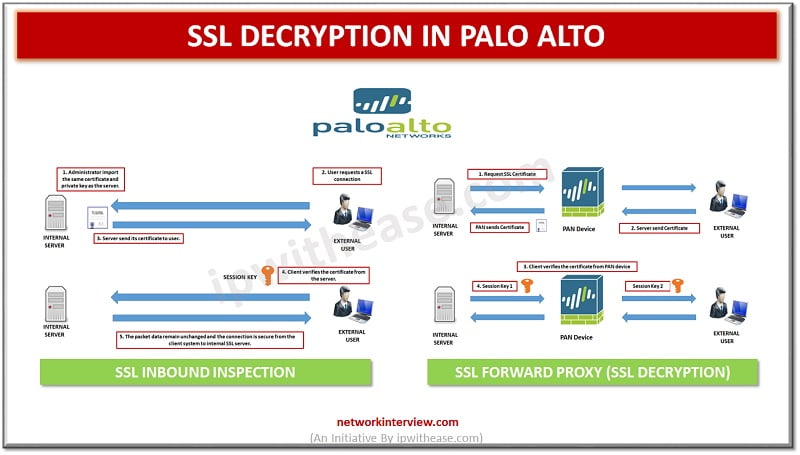
Before digging deep into Palo alto SSL Decryption, let’s first understand what is Decryption? What is Decryption? Palo Alto firewalls can be decrypt and inspect traffic to gain visibility of threats and to control protocols, certificate verification and failure handling. …
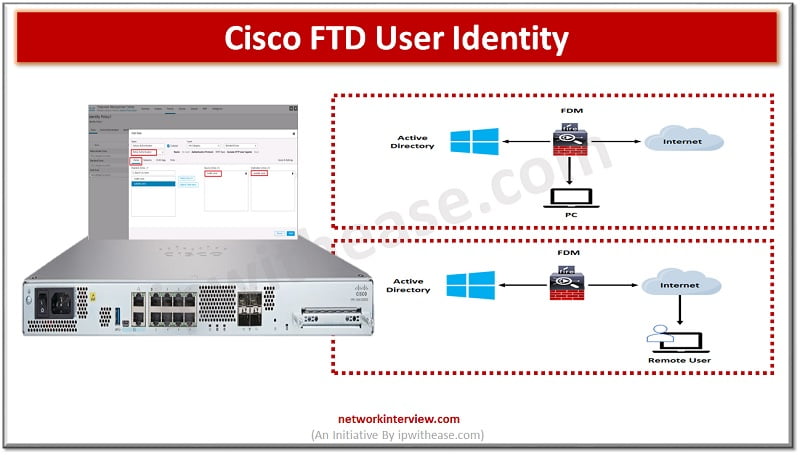
User identity information helps to identify the source of policy breaches, attacks or network vulnerabilities and trace them to specific users. Majority of traffic inspection products support filtering based on IP address. However, Cisco FTD identity policy feature gives the …
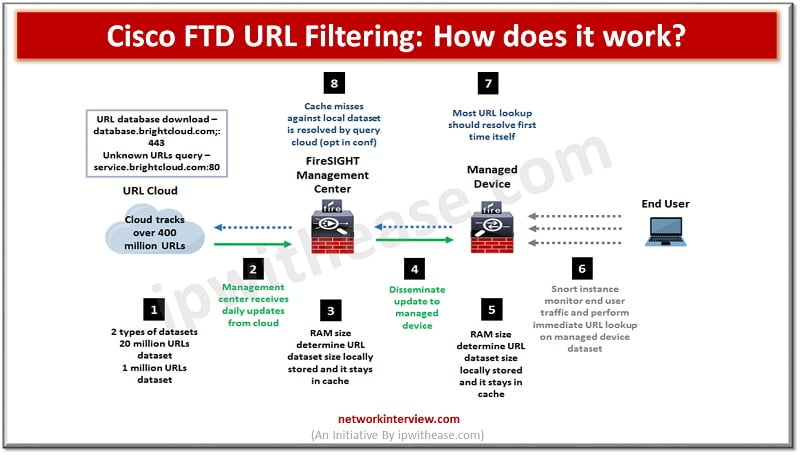
Pic: Showing How Cisco FTD URL Filtering works URL filtering or content filtering is one of the key features of firewalls. It helps to prevent access to harmful and malicious content which could cause data loss, system crash, virus or …
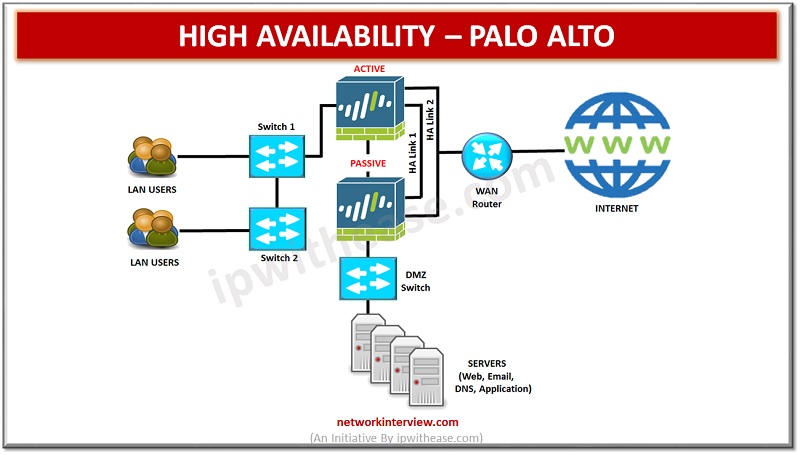
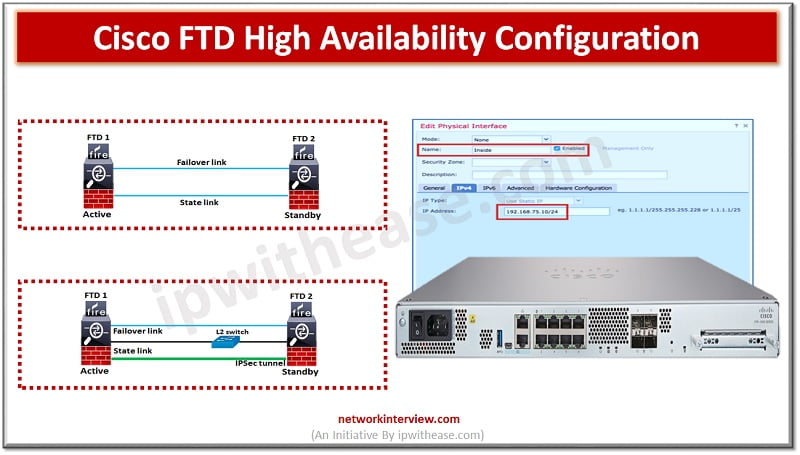
High availability (HA) refers to a system or component that is operational without interruption for long periods of time. High availability (HA) is measured as a percentage, with a 100% percent system indicating a service that experiences zero downtime. High …
To ensure uptime and continuous availability in the event of disaster is a required key feature for any production environments be it servers, networks and other computing equipment. All Cisco devices majority support high availability (HA) also known as failover. …
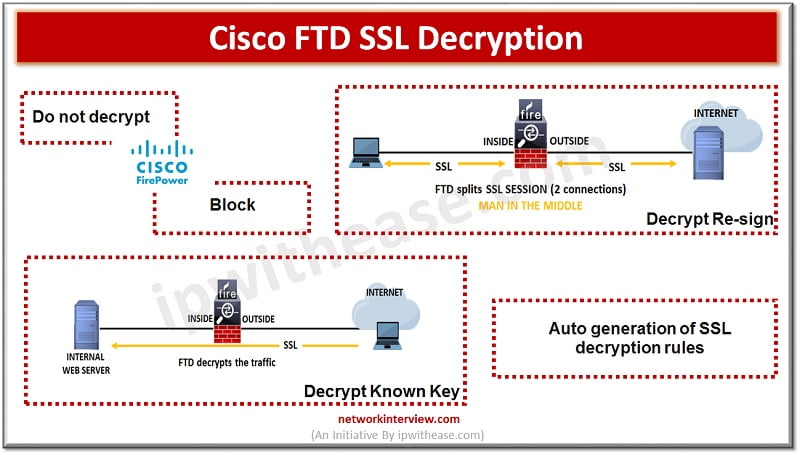
Some protocols like HTTPS use Secure socket layer (SSL), transport layer protocol (TLS) to encrypt traffic for secure transmissions. As the system cant inspect encrypted connections we first must decrypt to apply access roles which consider higher layer traffic characteristics …
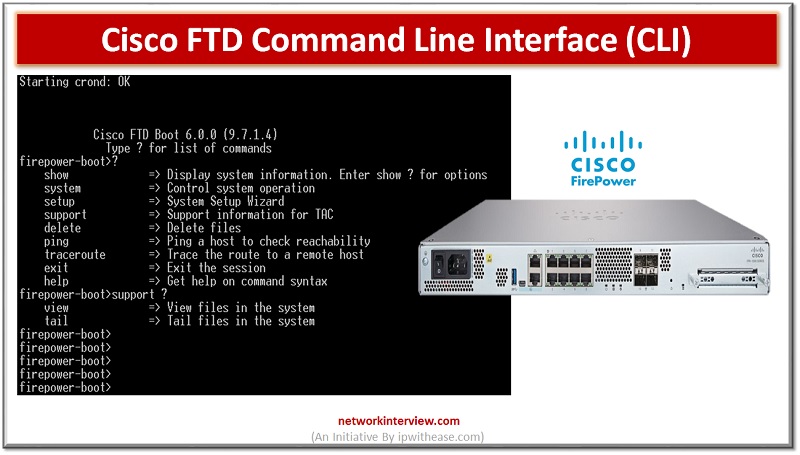
Majority of Cisco devices provide command line interface (CLI) as we call it to configure, manage and troubleshoot devices. Use of CLI allows users to execute Cisco IOS commands directly and simply as well as via remote access. In today’s …
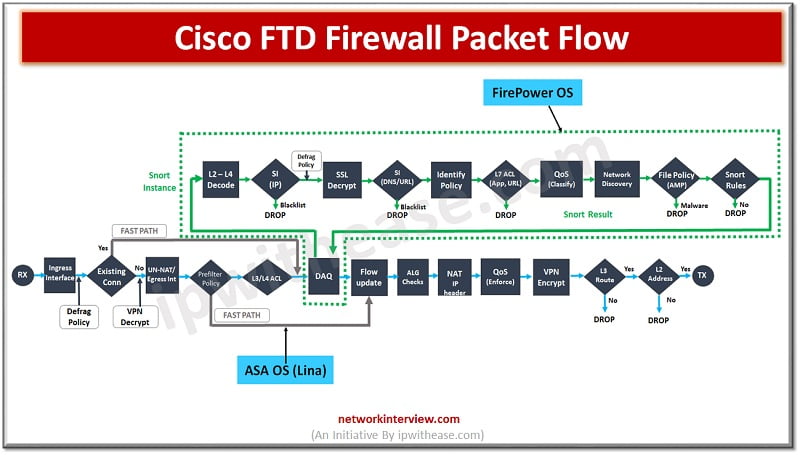
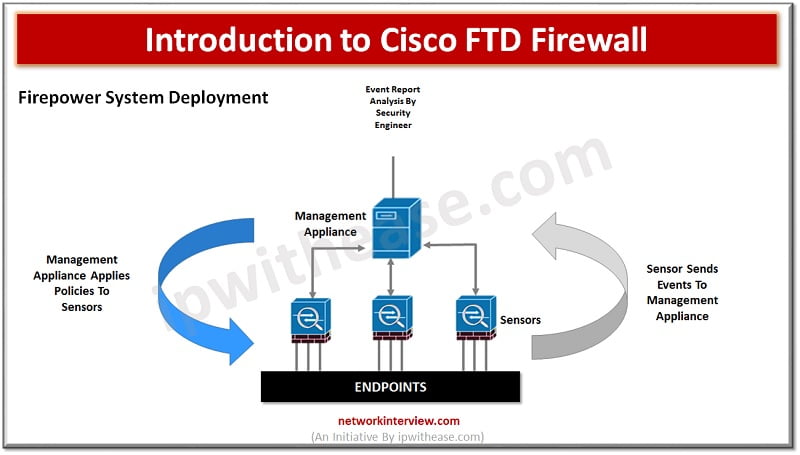
In the evaluation of next generation firewalls (NGFW), the next leap made by Cisco FTD is (Unified Firepower threat defence) software which includes not just NGFW but also Next generation Intrusion prevention systems (NGIP), Advanced Malware protection (AMP) and many …
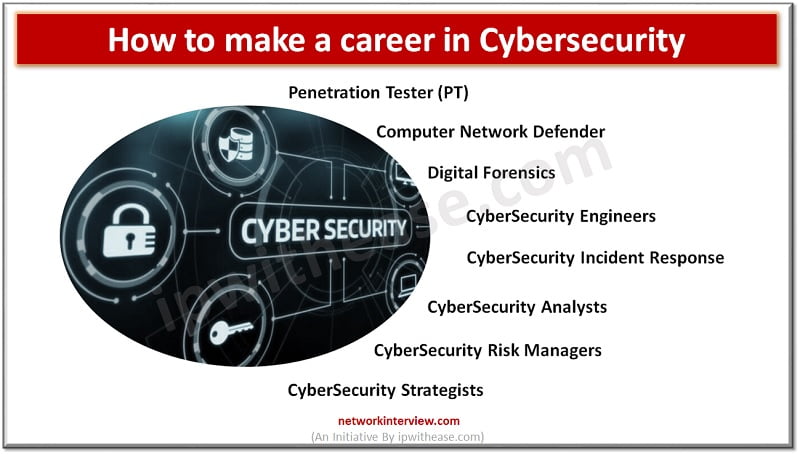
Career in Cybersecurity In this digital world, data is everywhere. This ensures that there are ample opportunities for people who have a passion for ethical hacking, known as “ethical hackers” to find jobs with companies that need their services. A …
If you want to earn a certificate in cloud computing, there’s no doubt that Microsoft is the most popular organisation among others. Azure AZ 500 is one such certified exam that perfectly fits those looking for a career in this …
Enterprises are moving their workloads on cloud infrastructure. Gartner forecasts that globally public cloud spending will increase by 18.4% in 2021 to a total of $304.9 billion. As organizations shift IT spend more and more on cloud services, they are …
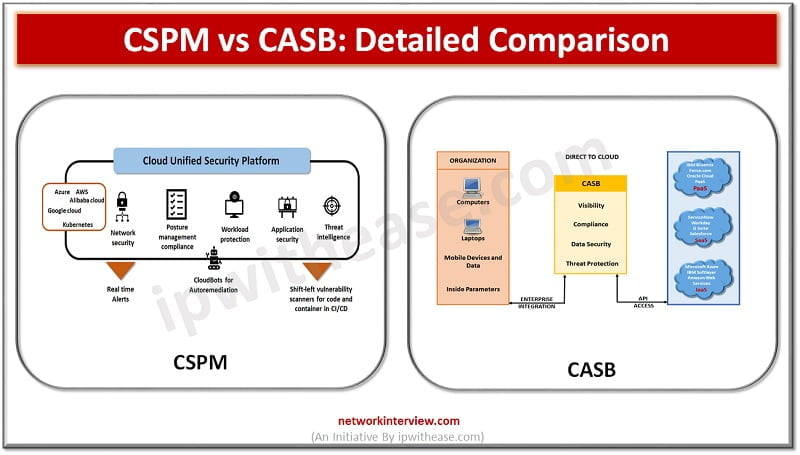
A common question arises in the mind of IT focals related to Cloud access security broker (CASB) service products such as we already have a web proxy firewall then how is this different? Is CASB a replacement for web proxy/ …
Virtual Private Network is referred to as VPN. Your internet traffic is encrypted by VPN software, which also uses a secure connection to deliver your data to a remote server. The info then makes its way to the internet from …
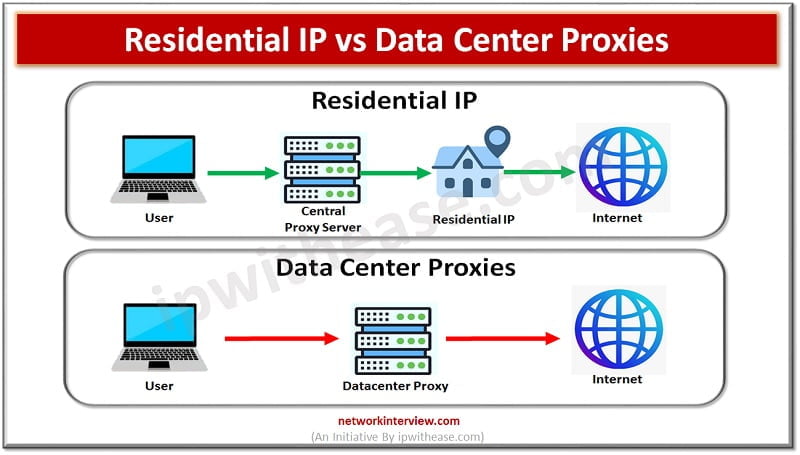
Today, a lot of people use proxy servers to access their accounts, so they may alter their IP addresses and stay out of trouble. The same cannot be said for all IP addresses. There are two types of IP proxies …
Cloud native technologies are helping Development teams to build and deploy applications faster than before. However, this open architecture increases challenges to Security teams. Cloud workloads are spread-out across Virtual Machine Containers Serverless and many points in between security devices …
Every person will stand at the cross-road where they need to decide between two career paths. So are you one of them, standing at the crossroads at choosing between a career in Cyber Security or Cloud Computing? Most computer major …
To have faster time to market and bring in business agility organizations are more and more relying on technology. Technological advancements have one side facilitated business to grow faster and quickly adapt to changing needs of businesses and on other …
Though it’s been a while since cloud technology was introduced into our world still there is much confusion surrounding Network Security and Cloud Security. If you are one of those who can’t find the difference between these two terms: Network …
Every new technology or software invented goes under this question “Is it secure?” That’s how security is always considered an important feature in the digital era. But do we understand them clearly? Over time security is classified further into cloud …
Cyber security software is a must for ensuring business and individuals security and privacy. It is a method to protect networks, systems and applications from cyber-attacks. It helps to avoid unauthorized data access, cyber attacks and identify stealing. Application, information …
Technological advances have changed the dynamics of the healthcare industry. Today, hospitals and clinics prefer using electronic health records (EHR), practice management, billing and patient engagement software to make business processes a breeze. But this technological era has given birth …
Agility and innovation are key ingredients for digital transformation. However, agility requirements are hindered by telco-controlled SD WAN or MPLS networks. Slow moving ISPs and need to deploy expensive custom hardware, telco circuits, and VPNs create roadblocks and stop transformation …
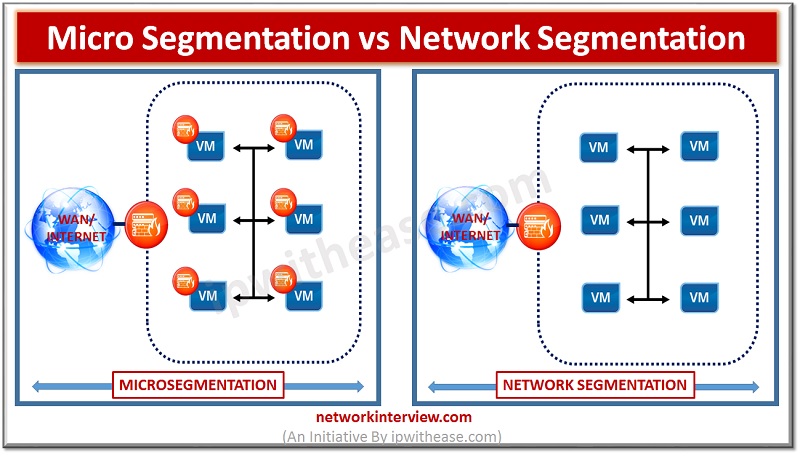
Micro segmentation vs Network Segmentation Over many years, Perimeter security has been considered the key to presenting a robust and secured network ecosystem . This was considered a suitable methodology when the network attacks were not so advanced and North-South …
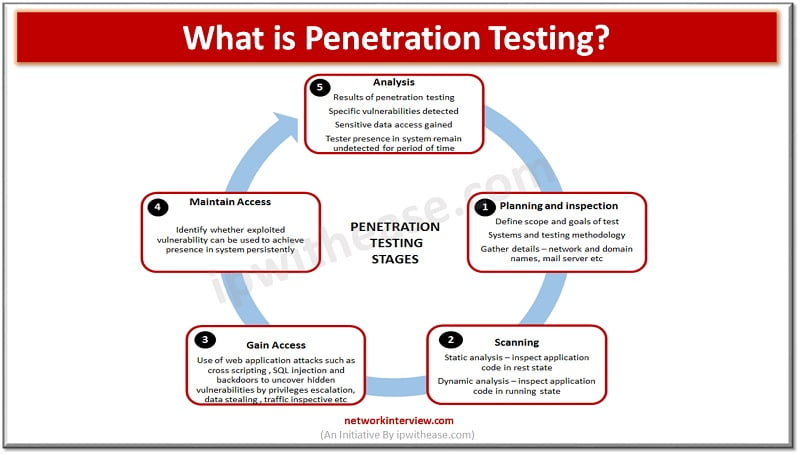
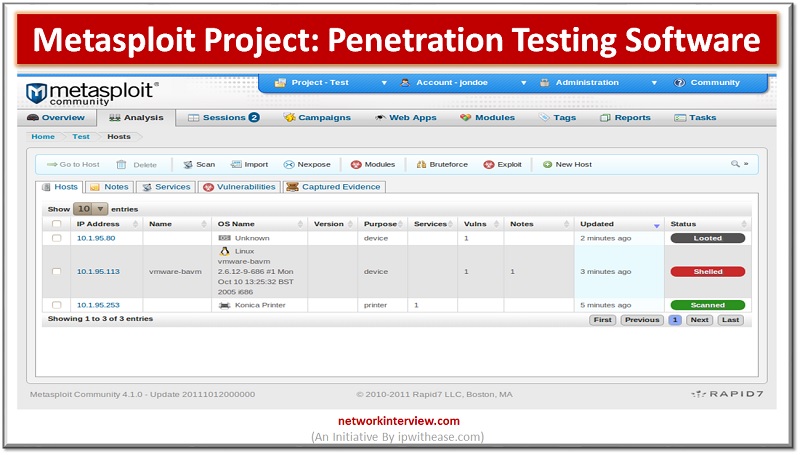
Introduction to Metasploit Project In the worldwide IT security community, we define the Metasploit Project as a computer security project that mainly provides information about security vulnerabilities and helps in penetration testing and development of the IDS Signatures. It is …
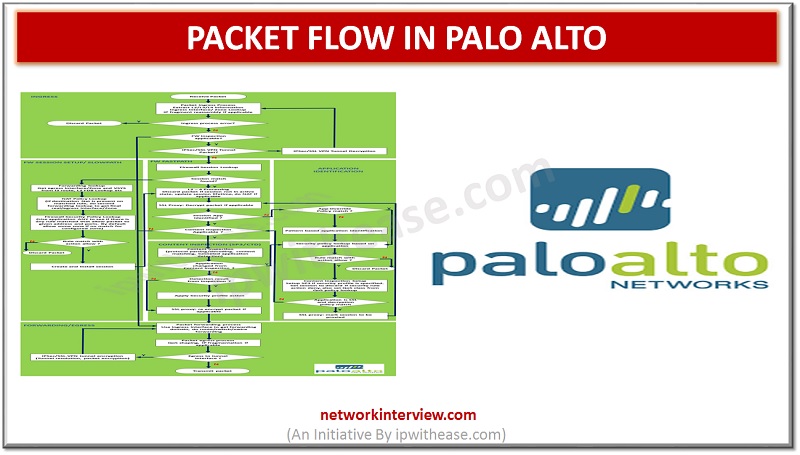
In this article, we will discuss on Packet handling process inside of PAN-OS of Palo Alto firewall. Introduction: Packet Flow in Palo Alto Packet passes through the multiple stages such as ingress and forwarding/egress stages that make packet forwarding decisions on …