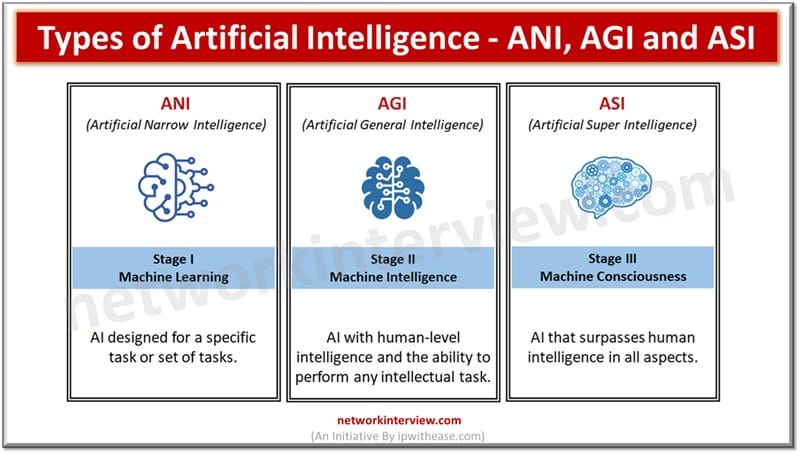
Generative AI refers to systems that create new content like text, images, or audio using machine learning models. Whereas, Responsible AI ensures AI systems are developed and used ethically, focusing on fairness, transparency, and safety. Artificial intelligence is reshaping organizations …
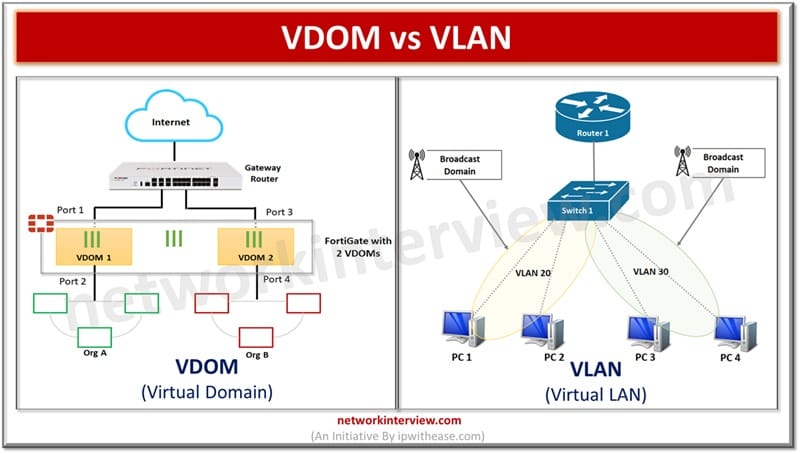
The majority of enterprises large, medium and small are moving to the cloud ecosystem to run their IT operations. Cloud service providers require a multi-tenancy strategy and products to support multi-tenant scenarios. Networking is one of the most crucial elements …
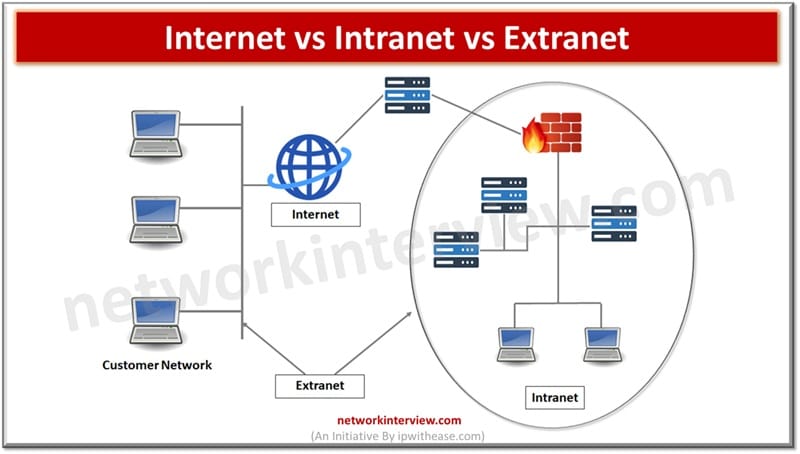
Networks are crucial in today’s digital world as they allow exchange, acquisitions and knowledge across organizations or within organizations. Every network meets a specific requirement as per its scope – connecting internal organizations, public ecosystem and secure connectivity with external …
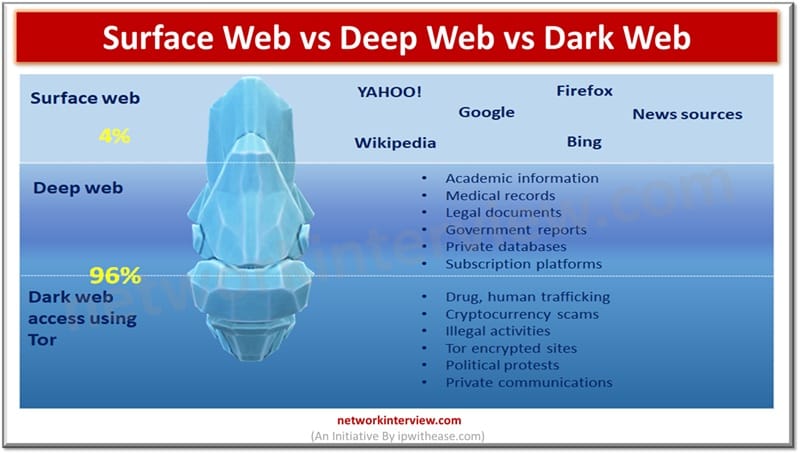
The Surface Web includes publicly accessible websites indexed by search engines. The Deep Web contains hidden content like databases and academic records, while the Dark Web is a small encrypted portion used for anonymity and often linked to illicit activities. …
Firewalls are the backbone of all networks and they have come a long way from traditional packet-based filtering firewalls to Next generation firewalls having convention firewall with network device filtering functions involving deep packet inspection, intrusion prevention system (IPS), TLS …
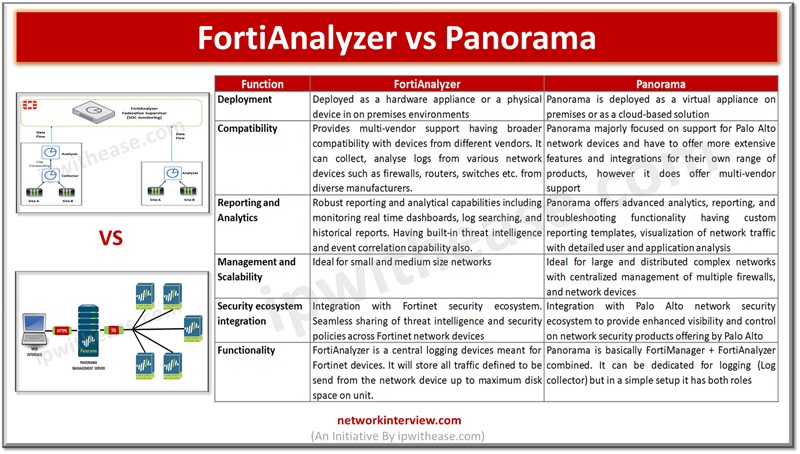
Centralized network management and analysis of network devices is one of the vital requirements of enterprise networks. Individual network component monitoring in larger networks brings a lot of overhead in terms of skills, resources, expertise and not a viable solution …
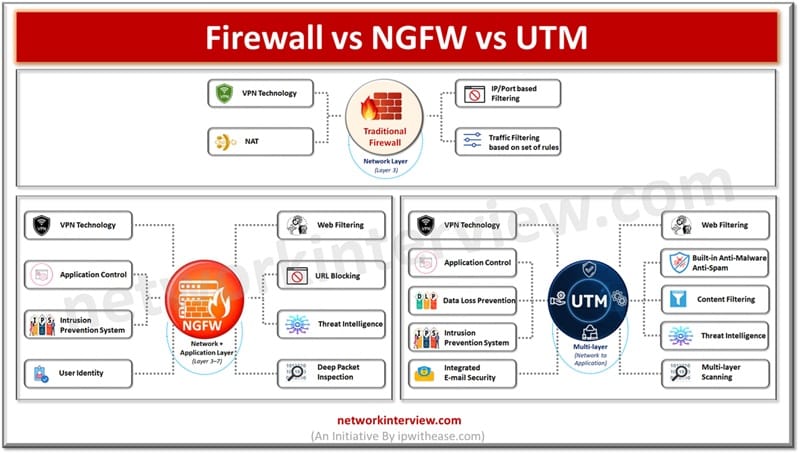
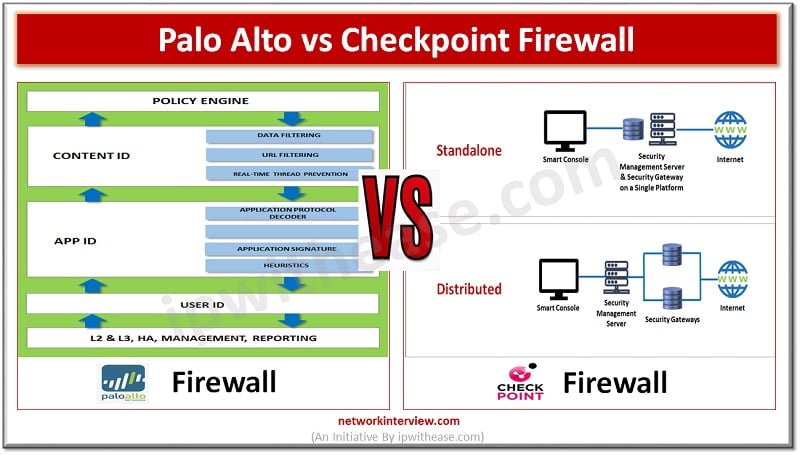
In today’s article we will understand the difference between traditional firewalls, Network generation firewalls (NGFW) and Unified threat management (UTM), their key features. Firewalls sit on the boundary of the network entry point and provide protection against malicious threats originating …
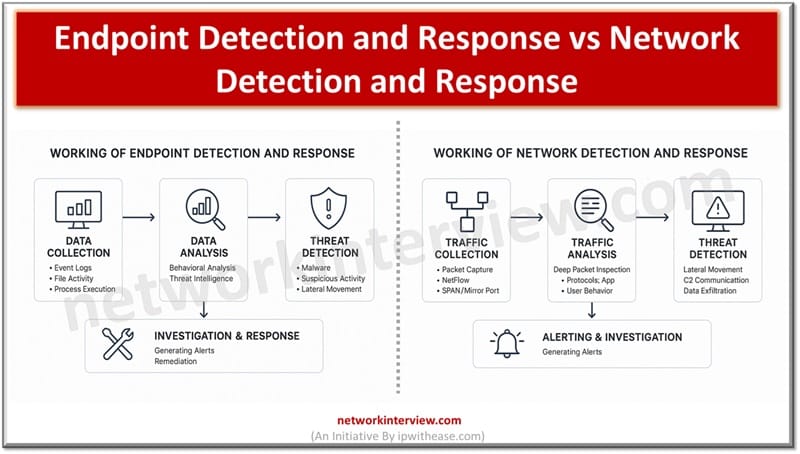
Endpoint Detection and Response focuses on monitoring and responding to threats on individual devices like laptops and servers. Whereas, Network Detection and Response monitors network traffic to detect and respond to threats across the entire network infrastructure. Constant threats and …
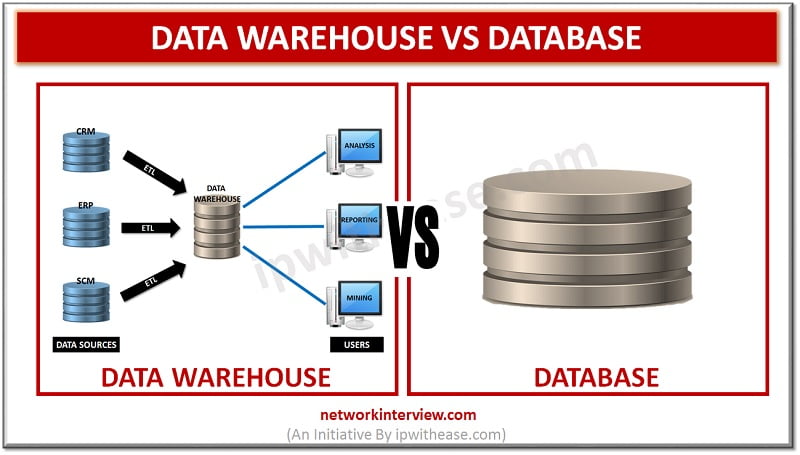
Before discussing difference between Database and Data Warehouse, let’s understand the two terms individually. Data Warehouse The data warehouse is devised to perform the reporting and analysis functions. The warehouse gathers data from varied databases of an organization to carry …
Database is a structured collection of data managed by a database management system (DBMS) that supports querying, transactions, and indexing. Whereas, a data storage is a more general term for any system used to store and retrieve data, including databases, …
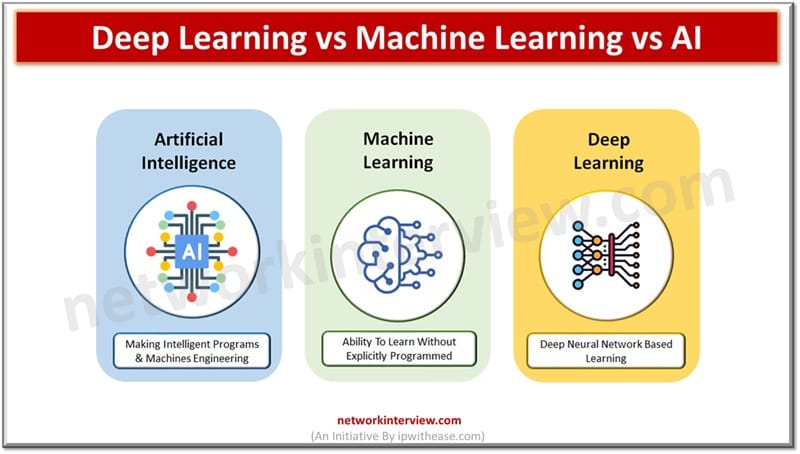
Today we look more in detail about these buzzwords which were estimated to replace 20% to 30% of the workforce in the next few years – Deep learning, Machine learning (ML) and Artificial intelligence (AI). What are the differences, their …
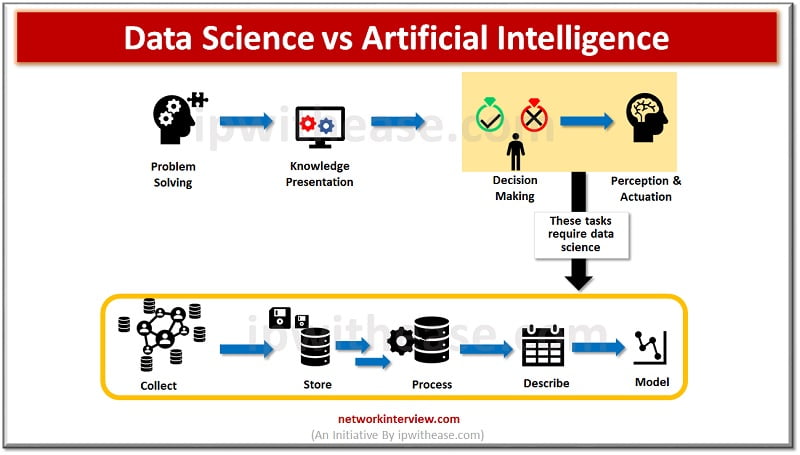
In the last couple of years there has been an explosion of workshops, conferences and symposia , books, reports and blogs which talk and cover the use of data in different fields and variations of words coming into existence such …
In this 21st century, humans rely more on machines than any other thing. So it is important to know about the important technologies that make the machines reliable. Yes, they are automation and artificial Intelligence. Automation has been among humans …
Rapid adoption of cloud technology across the globe has accelerated and drastically brought changes in the way enterprises are operating now. The introduction of Artificial intelligence or ‘cognitive technologies’ across enterprises to increase productivity, efficiency and accuracy of business operations …
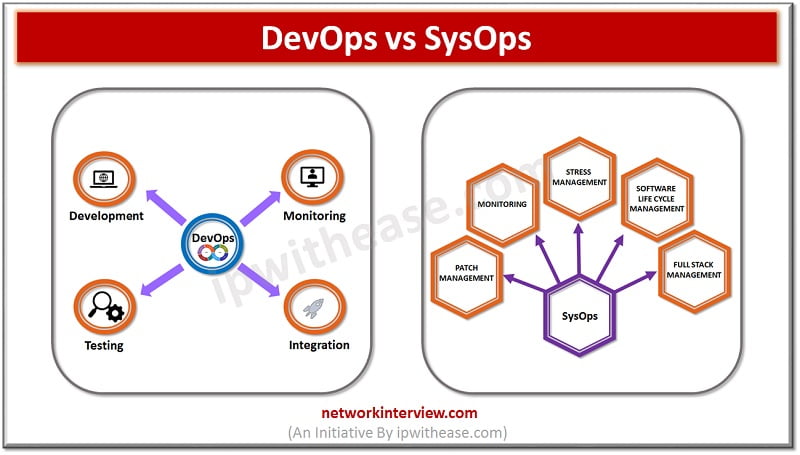
Introduction to DevOps & SysOps Technology advancements are crucial to the dynamic IT landscape in today’s times. Cloud computing has been crucial which presents excellent opportunities to business for the future. SysOps and DevOps are commonly used terminologies in cloud …
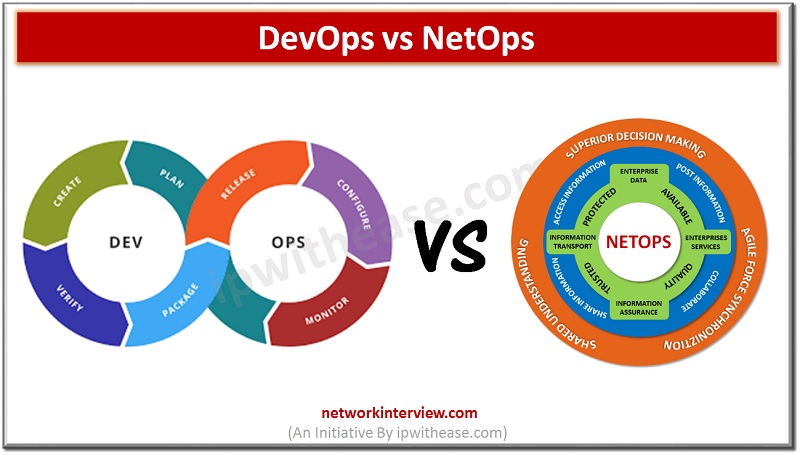
Introduction The tremendous technical development in the IT and other digital fields started the popular trend of creating acronyms with the Suffix Ops. And the word DevOps, NetOps, and SecOps are confusing IT and Tech communities further as they are …
Intoduction: Emerging Job Roles What is the difference between the Cloud Architect and DevOps Engineer? These new roles with growth of Cloud technologies has increased the confusion about roles? In this article, we will try to demystify some of concepts …
Cyber Attack Technologies Various forms of cyber attacks are prevailing these days and method of attack sophistication has reached new levels where now attackers are not limited only to fake websites, messages or emails but also focus is on theft …
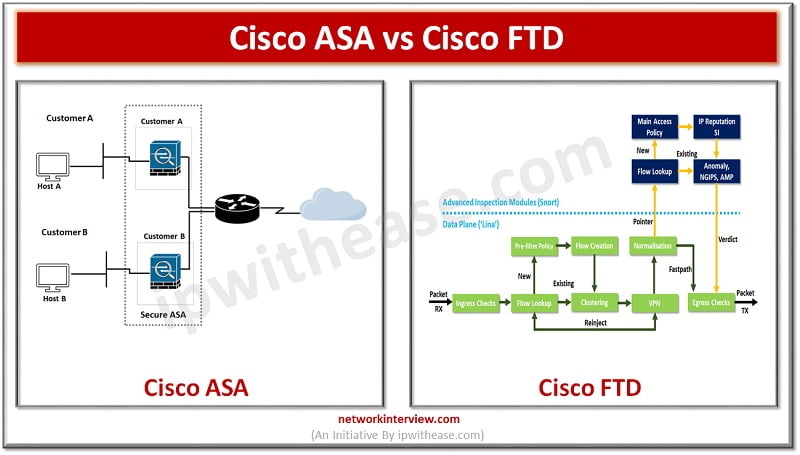
The Cisco Firepower Threat Defense (FTD) and Cisco Adaptive Security Appliance (ASA) are two types of security appliances that provide various features and capabilities to companies. These appliances were created with the intention of safeguarding businesses from cyber threats. Today …
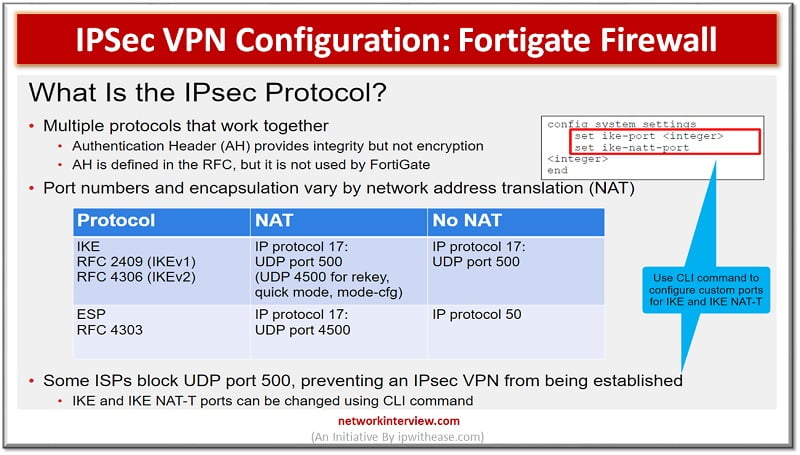
Objectives IPSec IKE Site to Site VPN between two FortiGate Sites Phase I and Phase II Parameters Tunnel Configuration Troubleshooting Commands IPSec VPN Configuration: Fortigate Firewall IPsec: It is a vendor neutral security protocol which is used to link …
Both the proxy and the firewall limit or block connections to and from a network but in a different way. While a firewall filters and blocks communication (ports or unauthorized programs that seek unauthorized access to our network), a proxy …
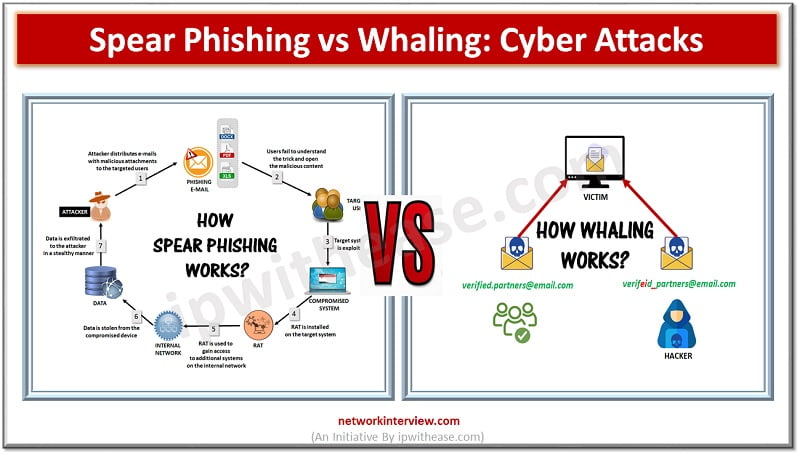
Cyber Attacks Cyber attacks are on rise since Covid 19 at a more rapid pace compared to before. Various forms of cyber attack techniques being used by hackers to gain access to organizations resulting in devastating effects such as unauthorized …
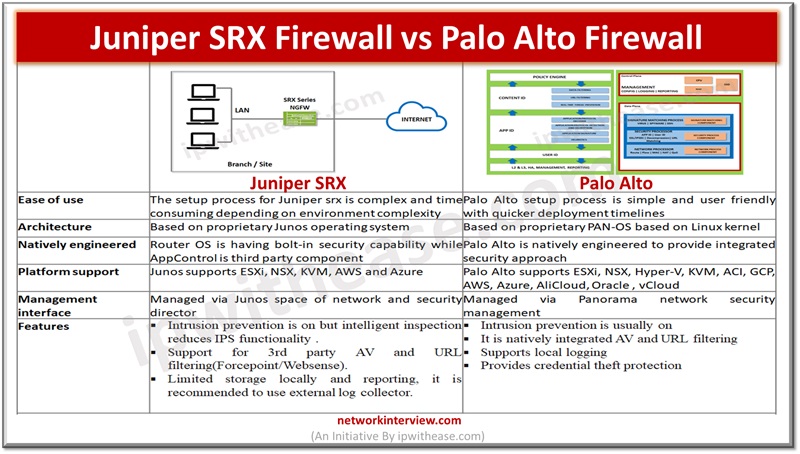
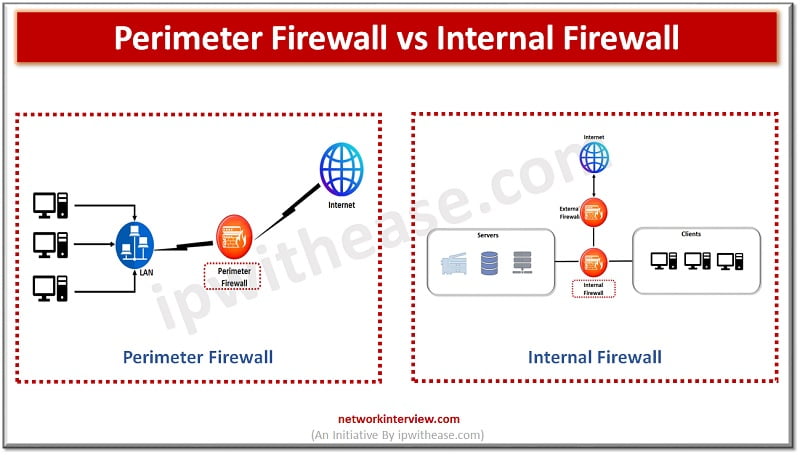
Attackers are constantly looking for vulnerabilities to penetrate your networks. Protection against direct, external threats require extensive network security functions deployed on the edge. Protections on the edge are provided by stateful and next generation firewalls (NGFWs) which offer features …
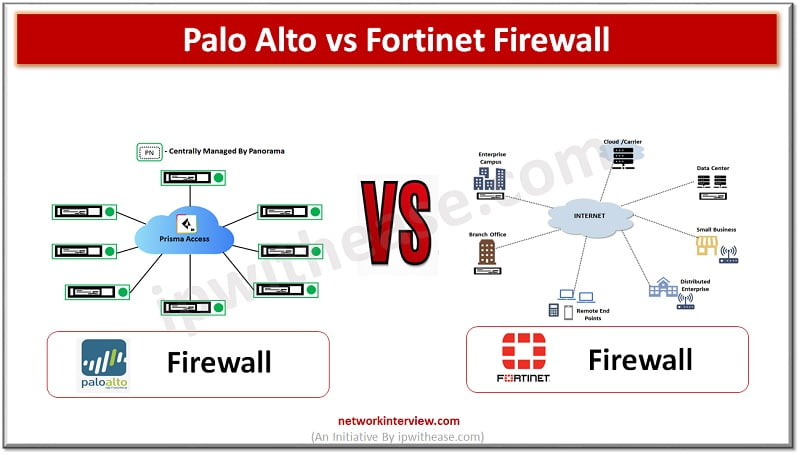
(Diagram depicting Palo Alto vs Fortinet Firewall) Organizations need to keep pace with rapid increase in technology demands such as remote working, anywhere connectivity, lower latency , increased availability along with protection of infrastructure from a never ending list of …
Application aware security is the need of the IT enterprises. Companies are replacing the old and outdated firewalls with Next generation firewalls which are application aware and this evolution can be attributed to web 2.0 where web-based applications and services …
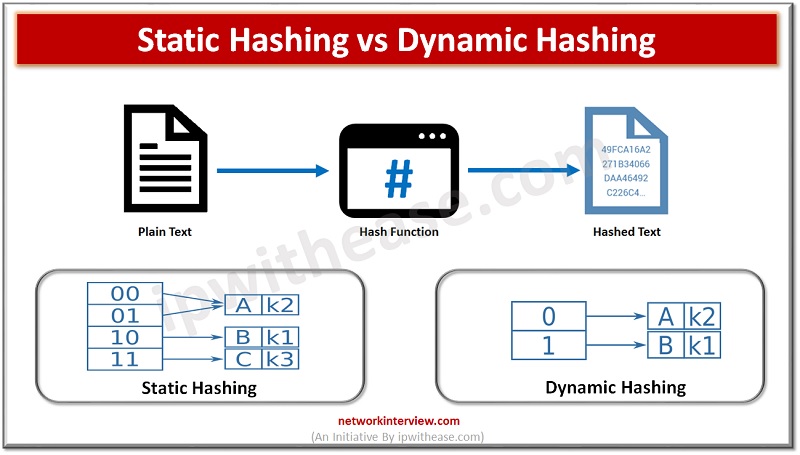
Introduction to Hashing Data structure often contains a lot of data that is difficult to search through. Hashing is an effective solution that can be used to map these large datasets to much smaller tables by utilizing a unique Hash …
All communication in Internet world is govern by OSI (Open Systems Interconnect) framework. There are seven layers in OSI model and each layer performs a set of functions to ensure data delivery to its intended recipient. The layer 3 or …
Without CPUs and GPUs, computers couldn’t function. The CPU’s control unit organizes several tasks and executes memory instructions as the computer’s “brain”. The graphics processing unit (GPU) has expanded to do many computational processes despite its origins in visual rendering. …
Wifi6 vs Wifi5 vs Wifi4 In the wireless world, Wi-Fi is the term that is similar in general to access of wireless. Although the fact is that this specific trademark is owned by Wi-Fi Alliance. This dedicated group takes care …
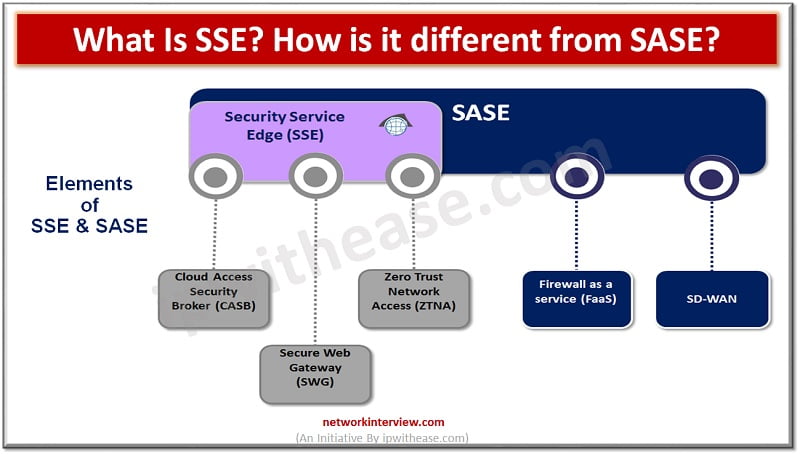
Introduction to SSE & SASE Security and network architecture have taken a front seat since cloud adoption is all time high and constantly growing. The demand for remote workforce is increasing and per Gartner research demand for remote working is …
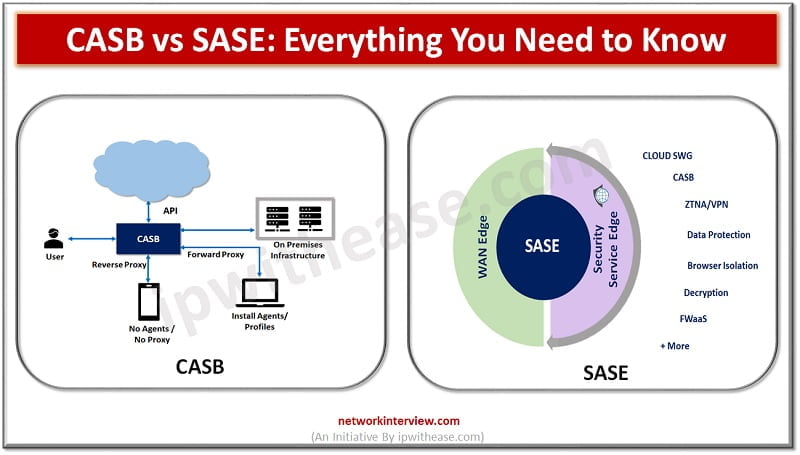
CASB vs SASE: Introduction As more and more data moves onto the cloud new tools and methods are evolving to control data and adhere to security regulations. Coronavirus pandemic is becoming an acceleration factor as all around the world companies …
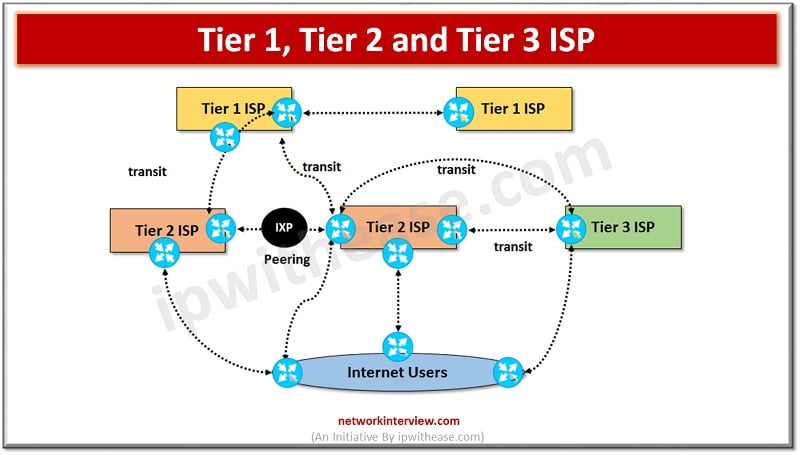
Internet Service Providers Internet service providers are organizations which provide internet connection to end users and other organizations which can be customer businesses, individuals. ISPs have made it easier and affordable to connect to the internet. ISP acts like a …
NAT Type 1 vs 2 vs 3 Nowadays, the 2 major gaming console types used extensively around the globe are Sony PlayStation Microsoft Xbox NAT stands for Network Address Translation, which represents the ability to translate a public IP address …
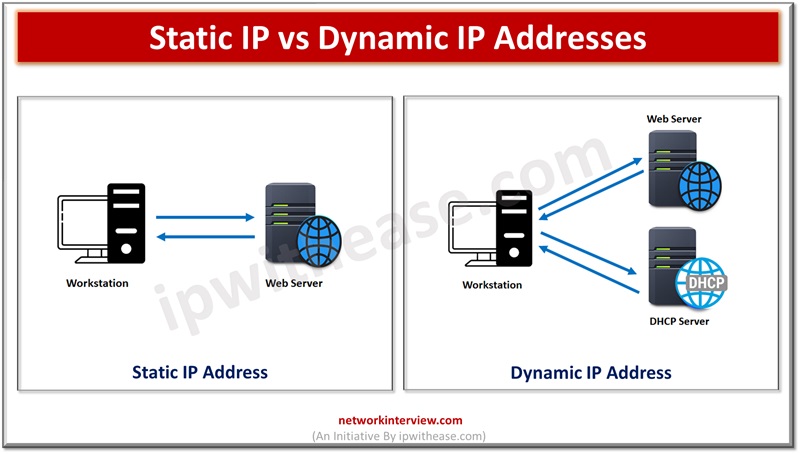
Introduction to ISP & VPN Internet service providers (ISP) facilitates internet navigation and helps in transmitting all your Internet packets however VPN creates a secure tunnel where data is encrypted during transmission. Often people get confused between the two terms …
Ethical Hacking and cyber security are two concepts we often remain confused about. To get a basic idea of the difference between ethical hacking and cyber security, remember that both terms have the same goal: to keep data safe. The …
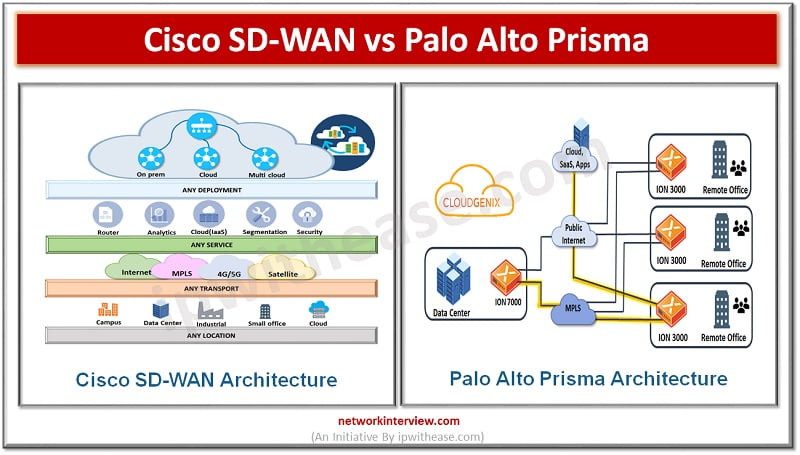
SD-WAN Solutions Penetration of cloud all around the enterprises also brought the need for hybrid networking solutions supporting private WANs and commodity Internet connections to support adoption of cloud applications, remote connectivity, scalability with application performance and including visibility. Major …
What is URL Filtering? Sometimes you browse your favorite social networking site on any of the web browser and that web browser displays the message “You are not allowed to browse following website”. This is because of the URL filtering. …
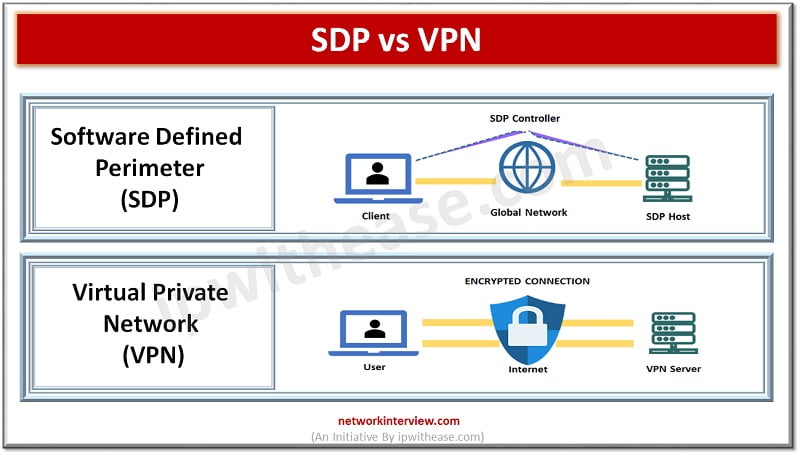
Traditional model of working from the office is quickly diminishing and becoming a thing of the past. As we transition to a hybrid model of working, network security becomes more and more complex. At the same time organizations resources are …
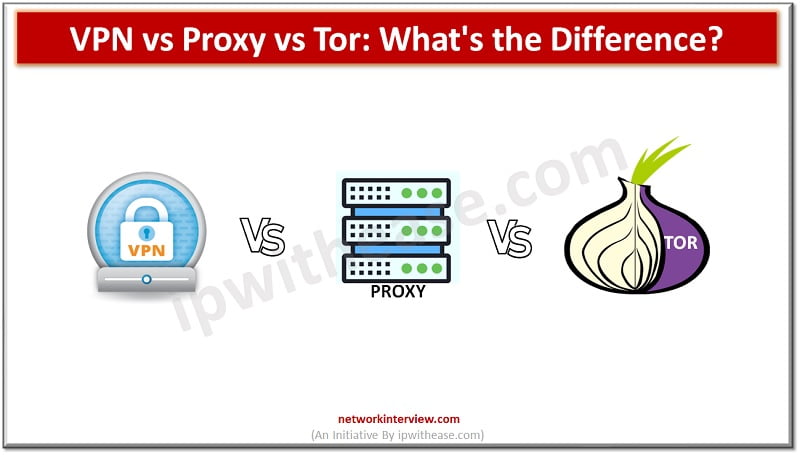
In today’s digital age, protecting our privacy and security online has become increasingly important. With the rise of cyber threats and the constant tracking of our online activities, it’s crucial to find effective ways to safeguard our personal information. Three …
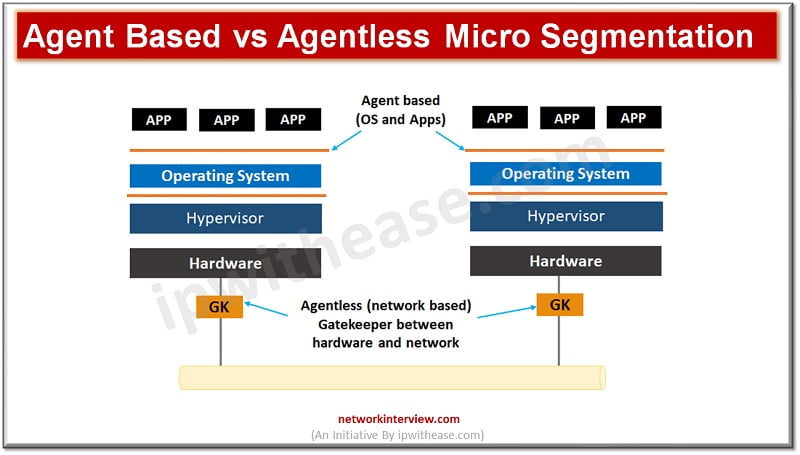
Granular level management of access and security controls is the focus of security techniques deployed nowadays as attacks have become more and more sophisticated so is the dynamics of protection also getting changed frequently. Virtually restricted access to any device …
Firewalls have come a long way since their inception in the year 1908s. The initial firewall was built by Digital Equipment Corporation (DEC) as a packet filtering firewall which simply inspected packet traffic and if it doesn’t match rules packet …
Artificial Intelligence and Machine Learning are two emerging concepts which are playing a very crucial role since the Covid pandemic hit us. Both technologies are being used to study the new virus, test potential medical treatments, analyse impact on public …
Firewalls are the primary line of defense for organizations; they are there for more than three decades but evolved and came a long way with drastic features and also sold now as separate appliances and make smarter decisions about what …
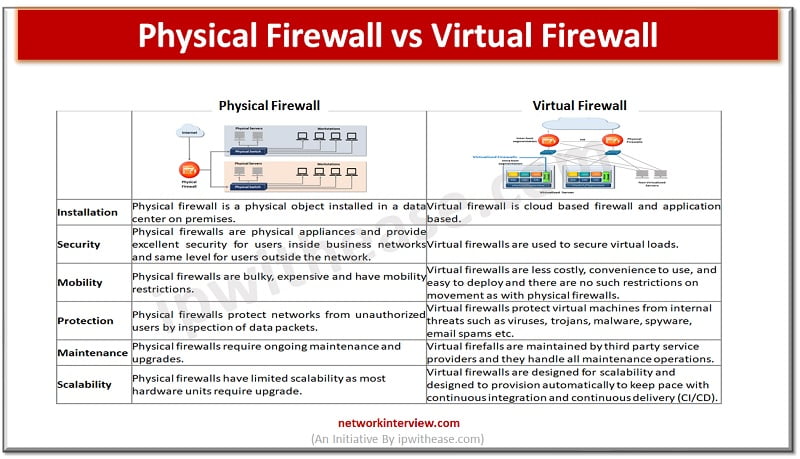
Firewalls are the first line of defense for an organization’s networks. Firewalls come in different categories – they can be a hardware appliance, software based or virtual. The increasing penetration of cloud computing infrastructures has given rise to virtual firewalls. …
Understanding each Encryption Technique When we dive in-depth to explore more about wireless key management and encryption technologies, then we would find that network protocols play an imperative part in it. As we are dealing with the technologies that are …