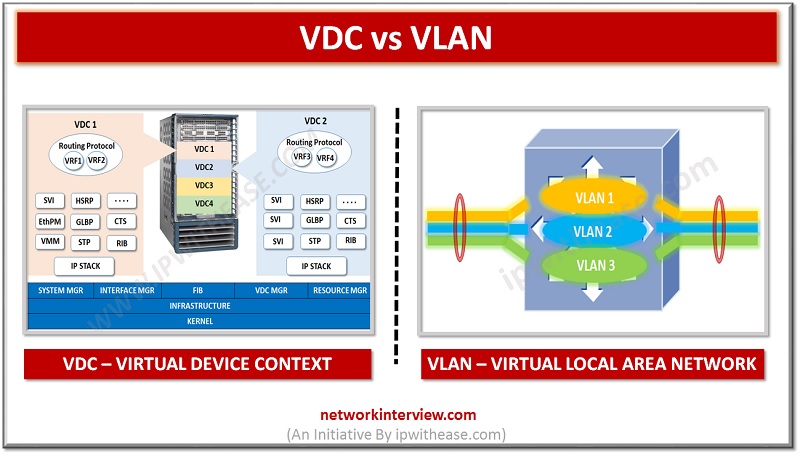
Introduction : VDC vs VLAN Virtualization in IT systems has helped Network estate immensely. 2 technologies which have helped networking across various segments are VLAN and VDC. While VLAN is short for Virtual Local Area Network, VDC means Virtual device …
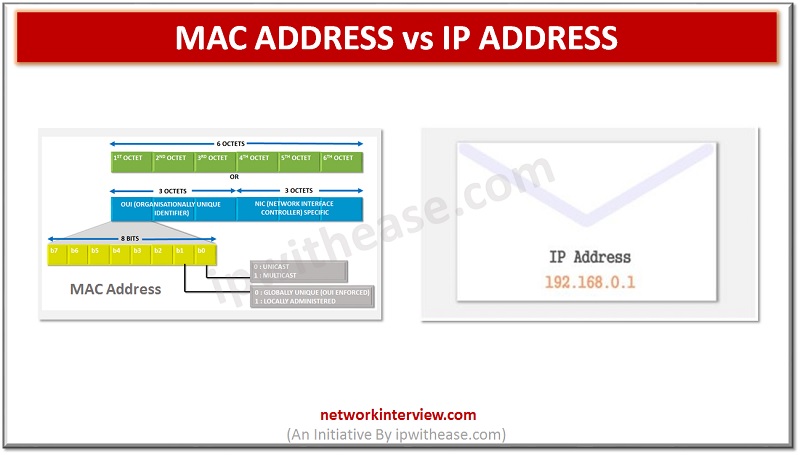
Introduction: MAC Address vs IP Address All devices part of a network can connect and communicate with each other. However, when we try to put logic around the communication between these devices, the key query that always arises in our …
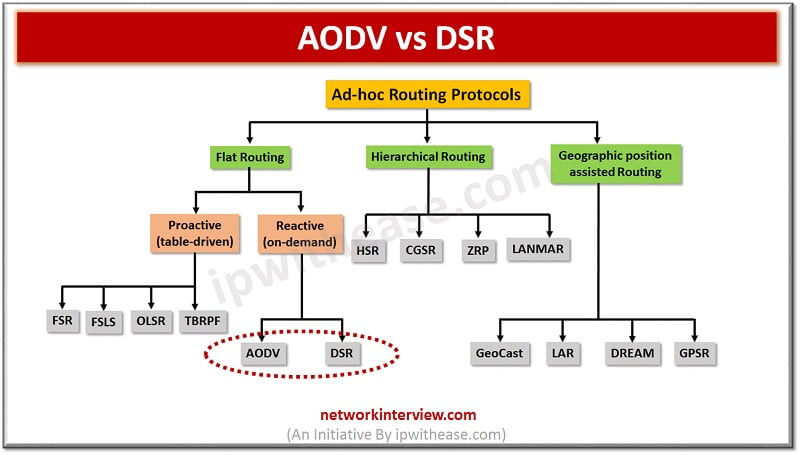
Difference between AODV Routing Protocol and DSR Protocol An ad hoc network or Mobile ad hoc network refers to a network connection established for a single session and does not require a router or a wireless base station. It does …
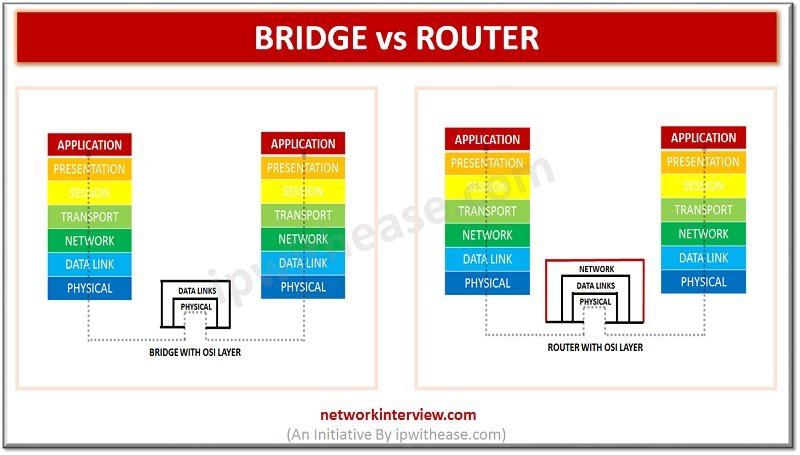
Network Bridge and Router are 2 key networking devices used in connecting segments or networks. While Bridge has been taken by switch, Router still remains the cornerstone of any WAN Network and has been expanding its role with introduction of …
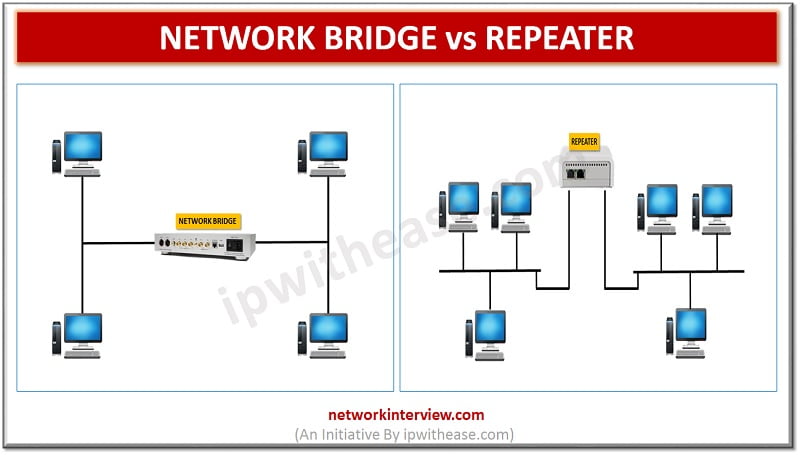
NETWORK BRIDGE vs REPEATER While working on networking concepts, network engineers may face challenge in understanding how Network Bridge and repeater are different and their working principles. In this article, we will touchbase on both the devices and compare their …
SSL Certificate types : Intermediate Certificate and Root Certificate When we look at the function of the SSL certificates at the first glance, then we would find that they are pretty straightforward. You would simply install it to your concerned …
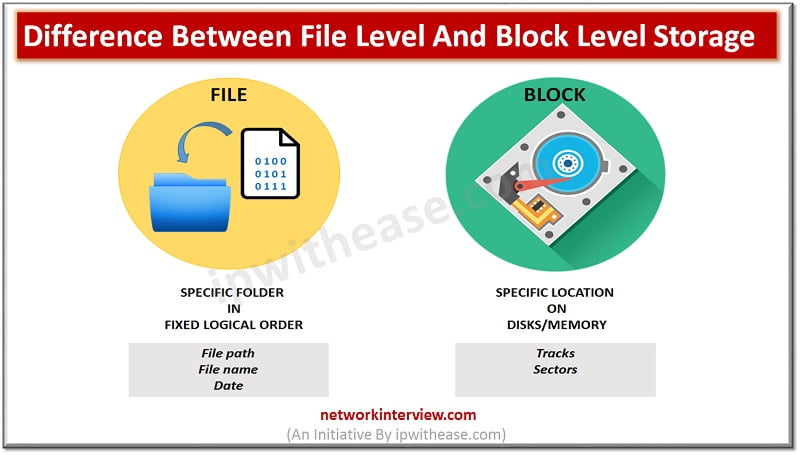
In this post, we will discuss the difference between File Level Storage and Block Level Storage. File Level Storage: The storage system of Network Attached Storage and hard drives is a file level storage. Here in this storage system, the …
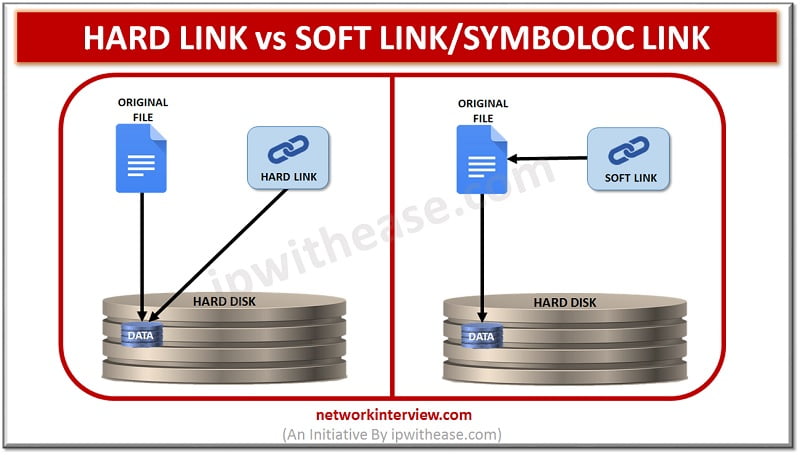
Hard link and Symbolic link Similar to the pointers in the programming languages, there are links in UNIX/LINUX which are just like pointers which point towards a directory or a file. To generate these links is like creating shortcuts for …
Guest OS vs Host OS When it comes to virtualization, several strategies are there that are popular. Your selection among these depends on several factors including imports, its development, software interface, virtual machines alters and other characteristics as well. Hosted …
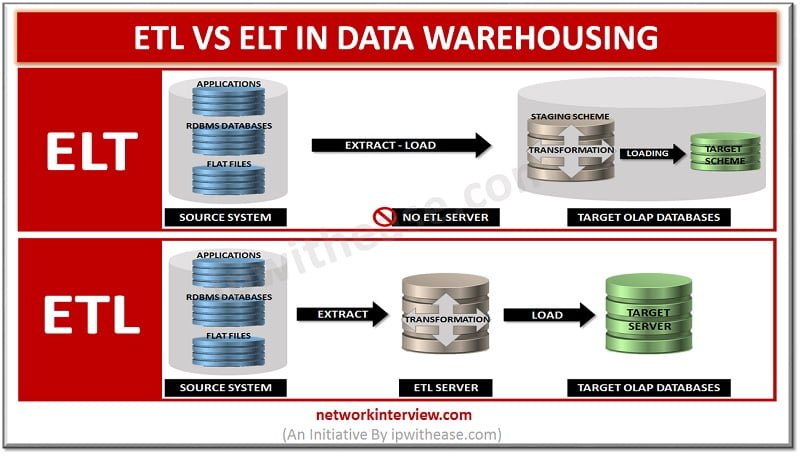
ETL vs ELT in Data Warehousing ETL: When the data is extracted from disparate sources and then it is transformed, the process is termed as ETL (extract, transform, and load). For data transformation, the actions performed include applying calculations and …
Proactive vs Reactive Routing Protocols Routing protocols are the routes that help to learn dynamic routes. These protocols are organized on routers in regards with exchanging the information related with routing. Using the routing protocols in your network has many …
TOGAF and ITIL What is TOGAF? The methodology of enterprise architecture by which development of enterprise software receives high level framework is termed as TOGAF (The Open Group Architecture Framework). A systematic approach is used in TOGAF by which it …
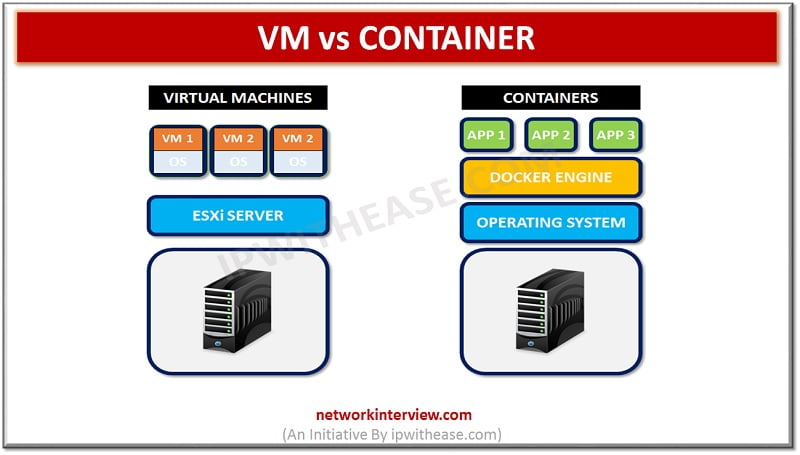
VM VS CONTAINER Virtual Machines VM or Virtual machine enables you to create and operate a discrete virtual environment- an operating system, acting like an individual computer. Through VMs, softwares that cannot work on your main OS, can easily work …
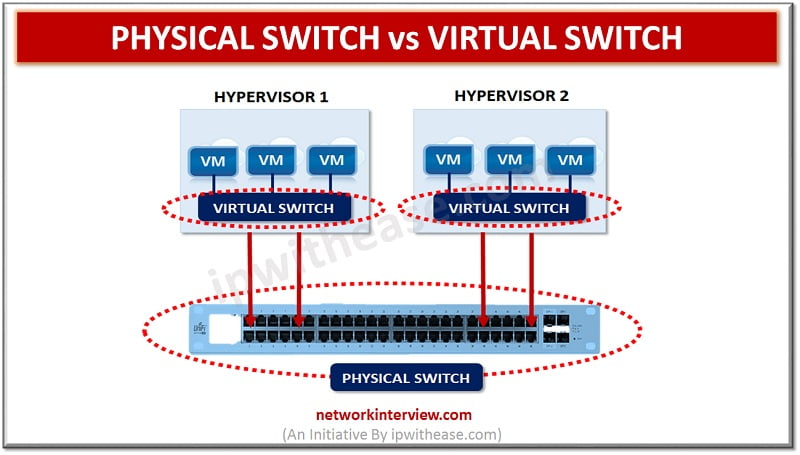
Physical Switch vs Virtual Switch A good and reliable network can help you in running a business operation seamlessly. That is the reason why a professionally reliable network always come with certain vital features that ensure unflinching results as per …
OpenFlow vs Netconf There are several data programming and configuration protocols that make the flow of information seamless across the networks. Among these protocols, OpenFlow and Netconf are considered to be popular and widely used ones when it comes to …
Network Administrator Vs System Administrator Network Administrator and System Administrator are the two terms that overlap each other but in reality, they are very different from each other. In this blog, we will discuss what the roles of network administrators …
CMD vs BAT The importance of the batch file can be easily understood by the power users and system administrators. But, generally most of the regular computer users are unaware of these files. This indicates that people are not utilizing …
Difference between LDAP and AD The framework of IT infrastructure of most of the organizations has Active Directory as a significant part. This significance is the reason why attackers have the Active Directory at the top of their target. In …
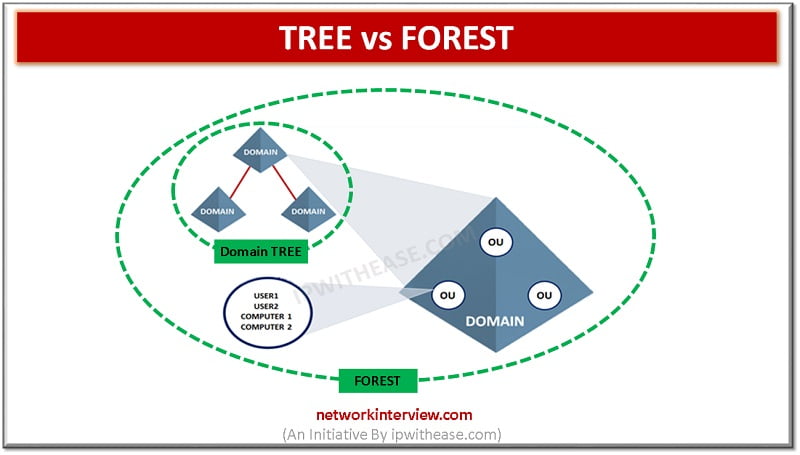
Introduction to Tree and Forest An Activity Directory is a product of Microsoft that runs on Server of Windows. It allows managing, accessing, and permissions for the network resources. The data is stored as an object in this directory and …
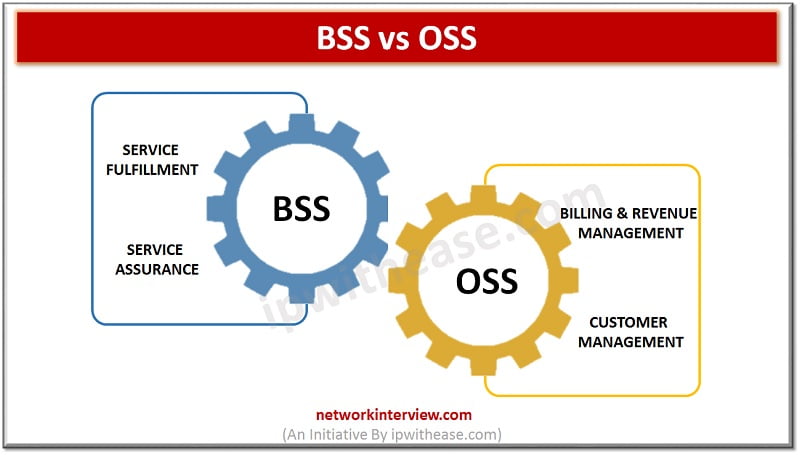
BSS vs OSS Two terms which in limelight especially in Telecom Operation world are BSS and OSS. BSS stands for Business Support Systems while OSS refers to Operations Support Systems. By their names, both the terms may seem complementary, however …
High Level Language vs Low Level Language Computer programming languages are broadly categorized into 2 types namely – High Level Language and Low Level Language. Abbreviation for High Level Language is HLL and Low Level Language is LLL. The former …
Linux vs Windows Windows has been quite a popular choice for home and office users. It’s been the widely used Operating system used in desktops, laptops and personal computers. Linux is an open-source operating system which is based on UNIX …
The DVD technology was emerged in 1997. It revolutionized the movie industry and brought digital sound and video into homes all over the world. The Blu-ray Discs (BD) were introduced in 2006. With their high storage capacity, these discs can hold and …
In this post, we shall discuss about comparison of URL filtering and Content filtering. Both the terms are interrelated, however differ in flavor of how they protect and assets they protect. SO, lets understand them in more detail – URL …
RAM (Random Access Memory) is a key memory component of computers, PCs, PDAs, smartphones and laptops. RAM is the main memory in a computer or PC and is much faster to read and write from than other kinds of storage. …
The differences between GLC-T and GLC-TE are as follows – SOURCE:https://ipwithease.com
Virtual Private Networks (VPNs) and Proxy servers are both useful tools for improving your online privacy and security, but they serve different purposes. A VPN works by transferring your internet connection to a private server, thus making it much harder …
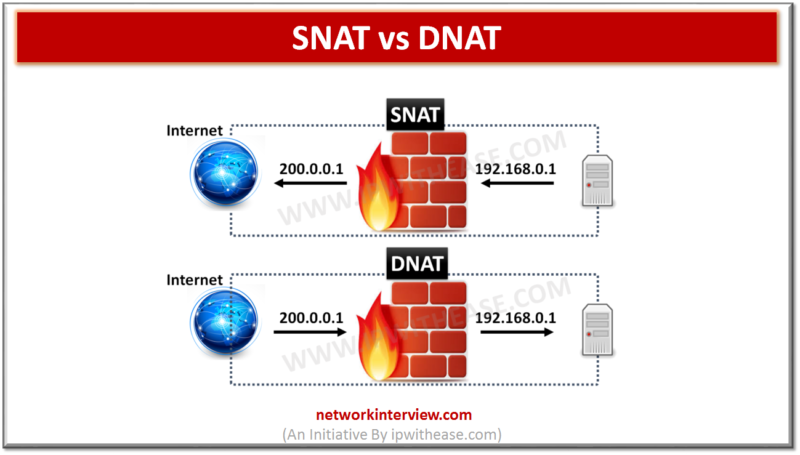
Introduction : SNAT vs DNAT In our previous post, we discussed about the NAT in detail. NAT is abbreviated for Network Address Translation, so the key word here is translation, as it is the process that is responsible for translation …
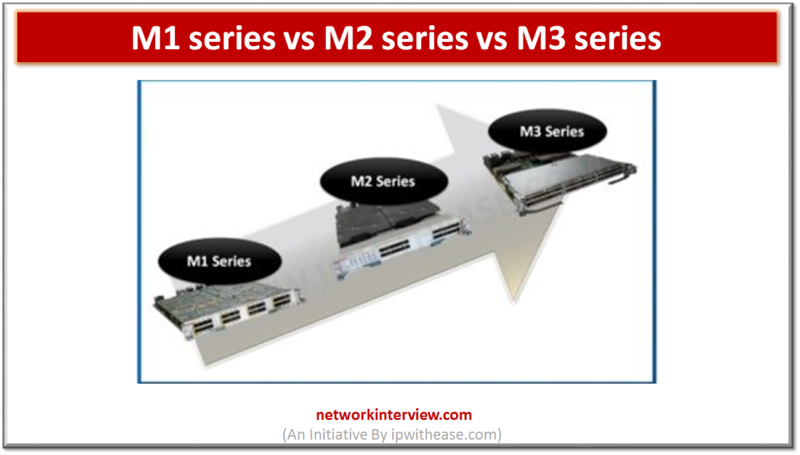
The differences between M1 Series, M2 Series and M3 Series are as follows – SOURCE:https://ipwithease.com
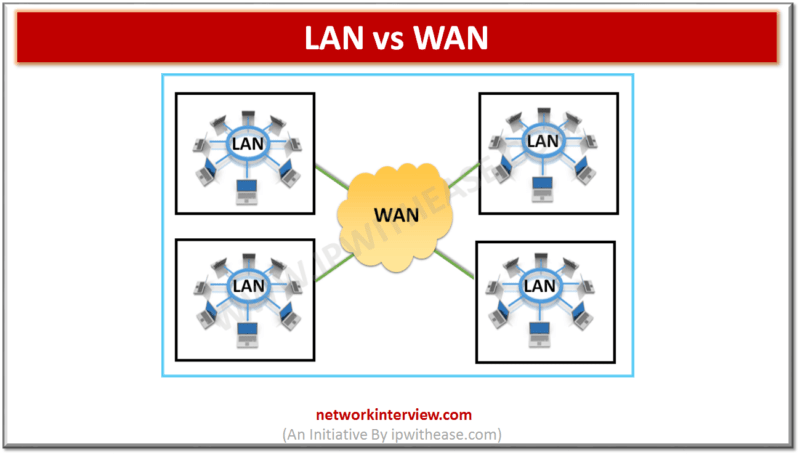
Before understanding LAN vs WAN, let’s know the two terms. LAN is abbreviation for Local Area Network. LAN is a network covering a small geographic area and connecting various end devices like computers and printers. LAN may be limited to a home, office, …
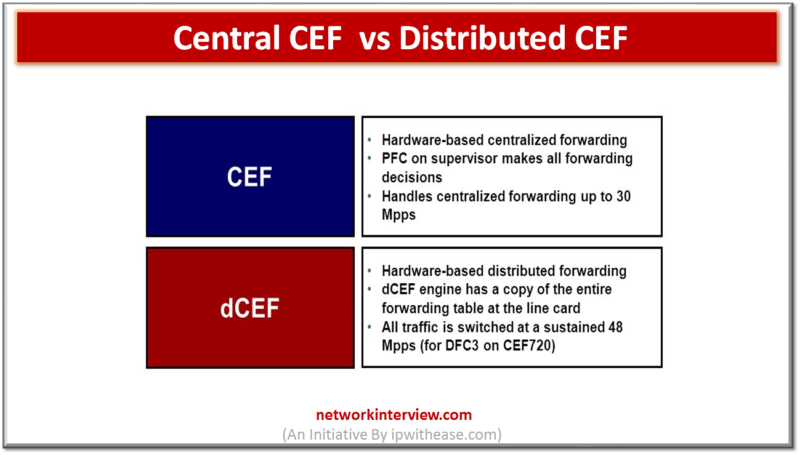
Difference between Central CEF and Distributed CEF SOURCE:https://ipwithease.com
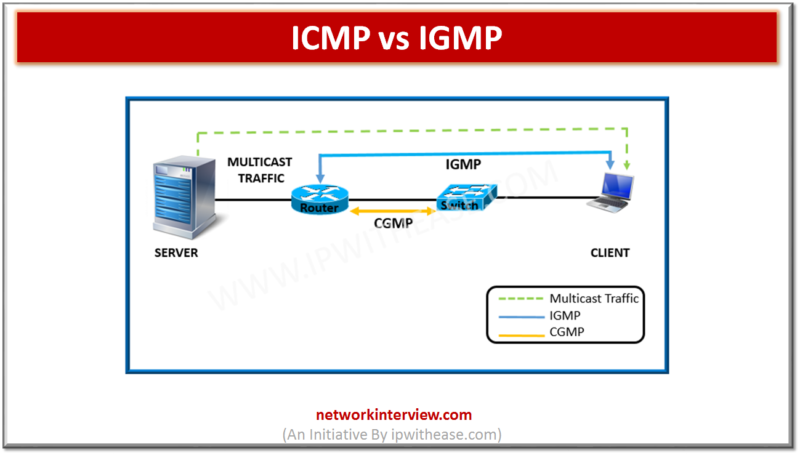
Difference between IGMP and CGMP SOURCE:https://ipwithease.com
In today’s world, a stable internet connection is essential for work, entertainment, and staying connected. But when setting up your home network, you might wonder: What’s the difference between a modem and a router? Many people confuse these two devices, …
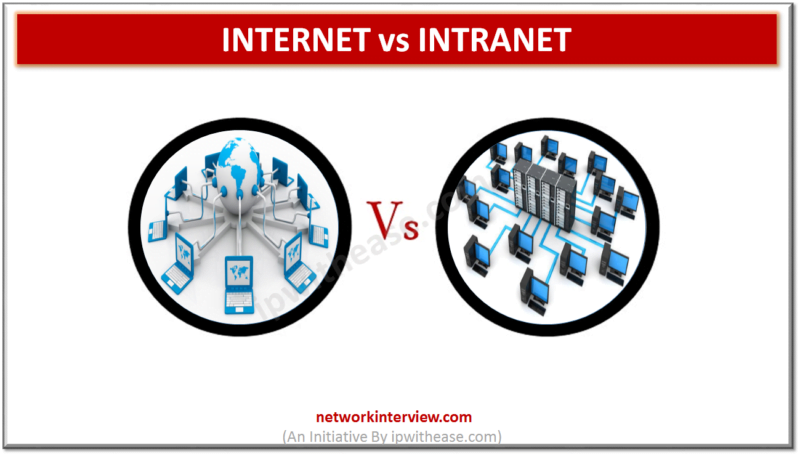
Difference between Internet and Intranet SOURCE:https://ipwithease.com
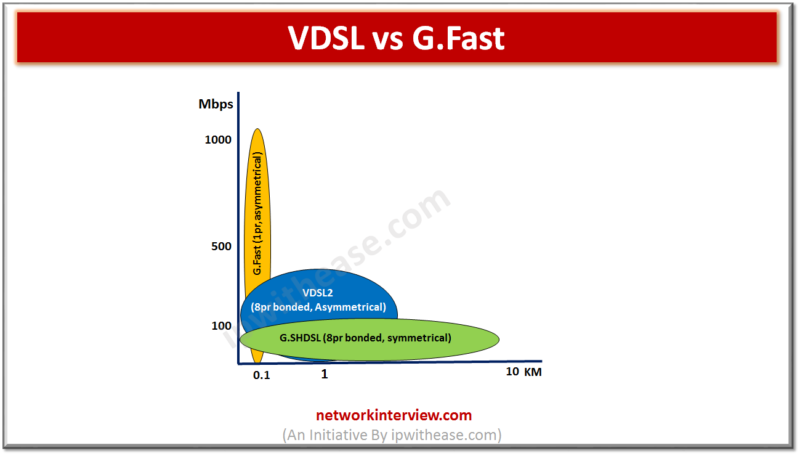
Difference between VDSL and G.Fast SOURCE:https://ipwithease.com
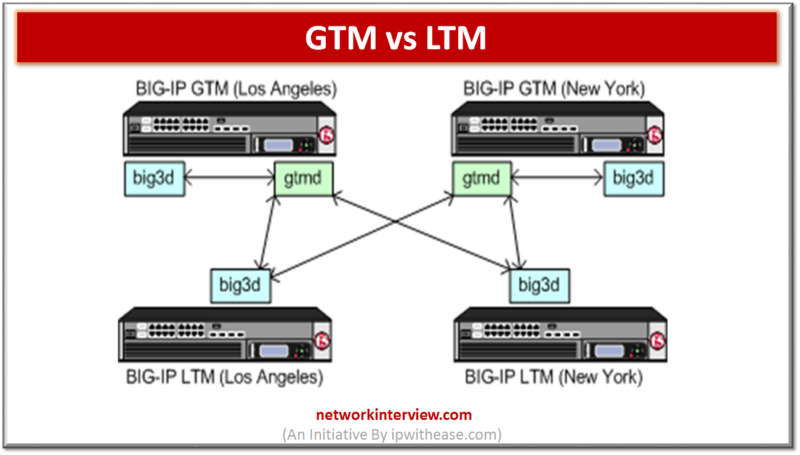
Difference between GTM and LTM FUNCTION GTM LTM Full Form Global Traffic Balancer Local Traffic Manager Industry Standard name Global Load Balancer Server Load balancer Name resolution GTM performs name to IP resolution Does not perform name to IP resolution …
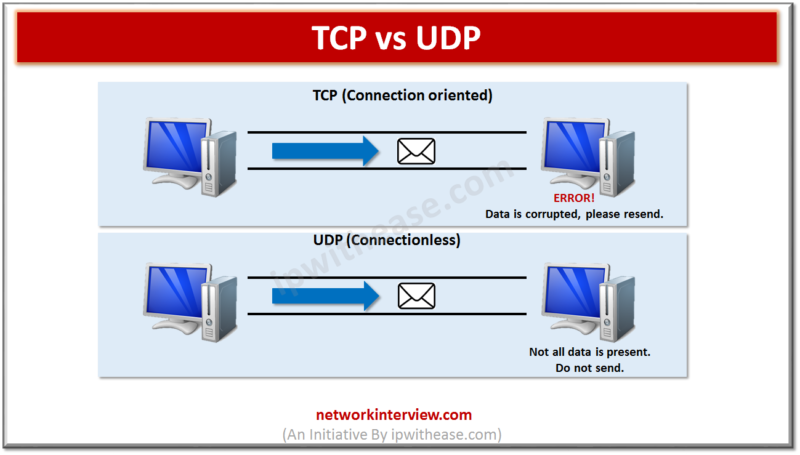
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two core protocols of the Internet Protocol (IP) suite. They differ significantly in their features, use cases, and reliability. TCP vs UDP Here’s a detailed comparison: 1. Connection Handling TCP: …
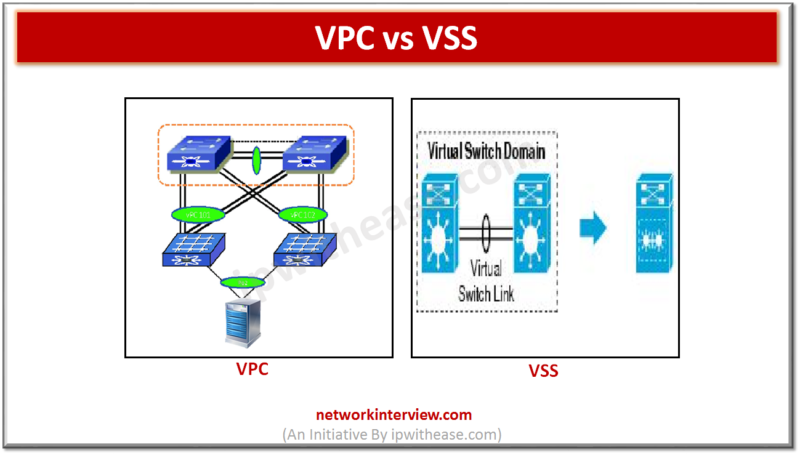
Both Virtual PortChannel (vPC) and Virtual Switching System (VSS) are Cisco technologies designed to improve network redundancy and bandwidth utilization by eliminating Spanning Tree Protocol (STP) blockages. However, they operate differently and are used in different scenarios. Lets explore the …
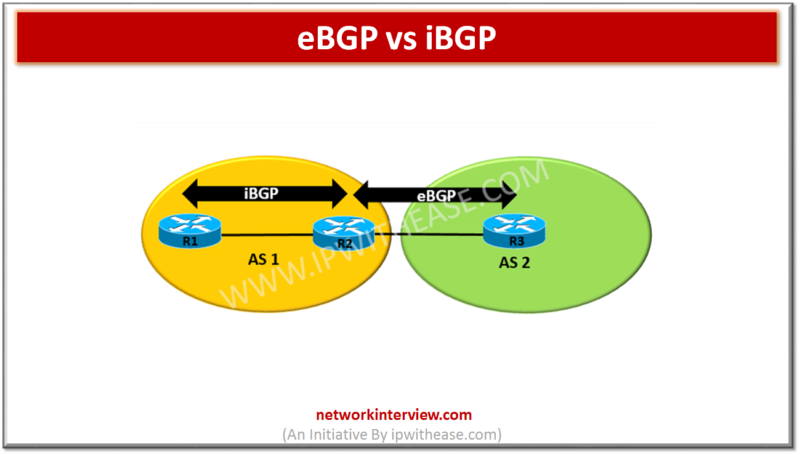
Before discussing eBGP vs iBGP, let’s understand the two protocols briefly. What is eBGP It is abbreviation for External Border Gateway Protocol and is one of the flavors of BGP protocol. eBGP Routing protocol is used between BGP speaking neighbors …