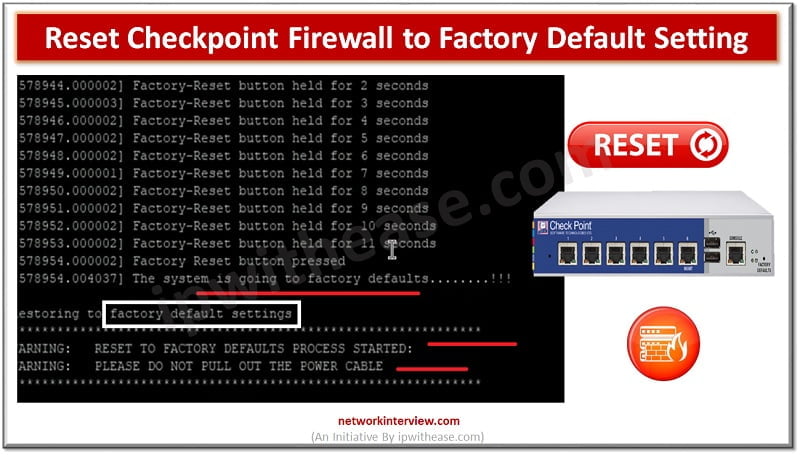
Let’s understand the difference between “Reset” and “Factory-Reset”. Reset – Admin can only wipe-out the configuration Factory-Reset/Default – Admin can wipe out the configuration of device and put the device in default operation/firmware. For Example, when you buy a Firewall, …
If you’ve worked hard to earn a promotion, it’s important to showcase your accomplishments and career growth on your resume. Not only does this demonstrate your ability to take on new responsibilities and succeed in a higher position, but it …
Local Internet Service Providers face many challenges in today’s market. They must compete with large telcos while operating with limited resources and budgets. One of the challenges is managing their network and devices efficiently. This is where Splynx TR-069 ACS …
These days, most businesses rely heavily on software for their daily operation. This is likely to include industry-specific software as well as a range of general business software programs. It is not hard to imagine how difficult it would be …
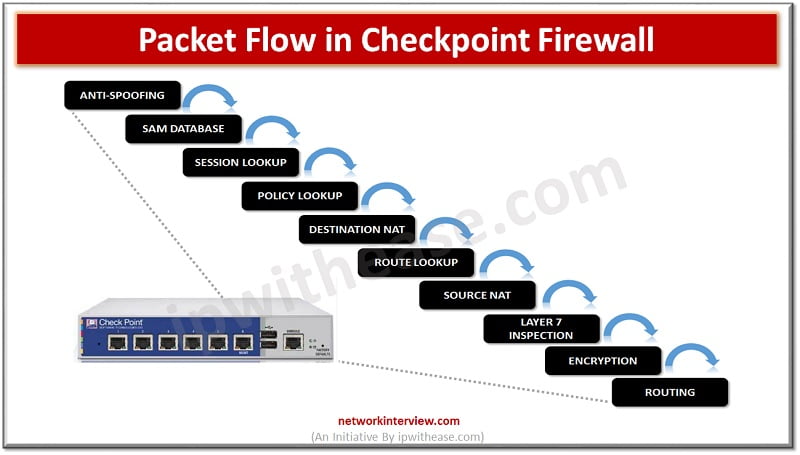
Checkpoint Firewall Packet Flow In the above image Checkpoint Firewall packet flow is shown. Let’s start with Anti-spoofing. Anti-Spoofing Anti-spoofing is a technique which can identify the packet and drop it if the packet has a FAKE/False source address. Let’s …
You might not know, but every domain name (website) has a unique IP address which makes it accessible to the network and users. If you are thinking about why a website has an IP address, then take into account that …
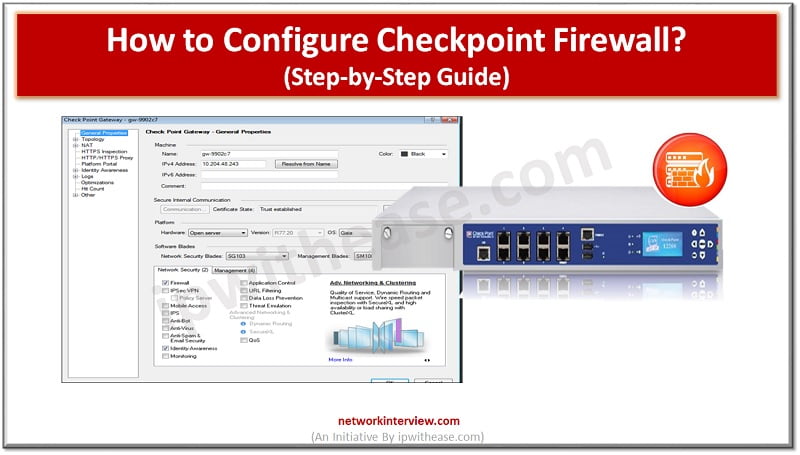
Prerequisites to Configure Checkpoint Firewall Sometimes in the network we need to install a new Checkpoint Firewall from scratch which requires a few prerequisite as follows: Console Cable Physical access to device (arrange any local site Engineer) Bootable USB Stick …
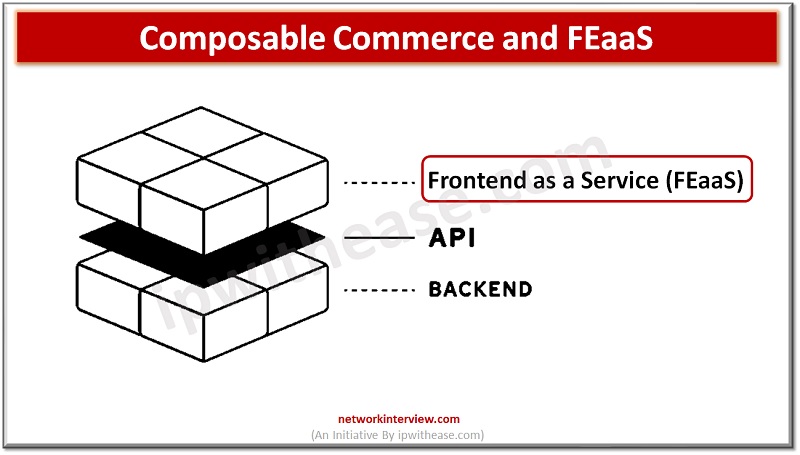
Today’s digital world has opened up a new realm of possibilities for retail businesses. With the introduction of composable commerce and FEaaS (Frontend as a Service), online retailers now have access to tools that can help them drive growth in …
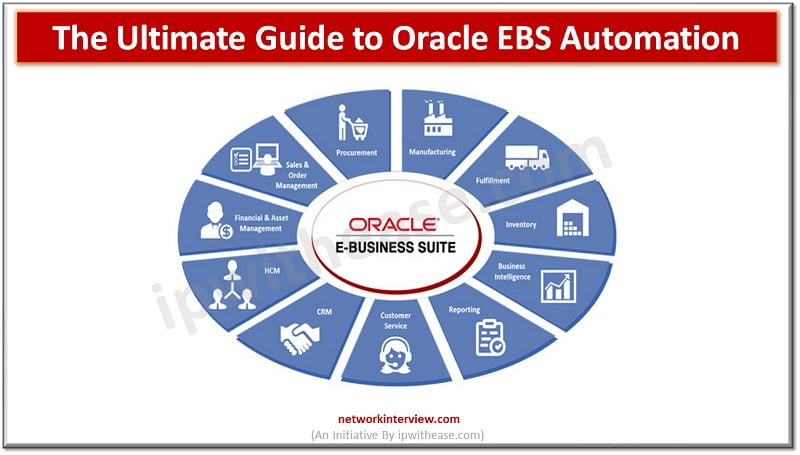
The popular business application known as Oracle E-Business Suite (EBS) is utilized by numerous organizations worldwide. Financial management, human resources management, supply chain management, and customer relationship management are just a few of the departments it aids in the day-to-day …
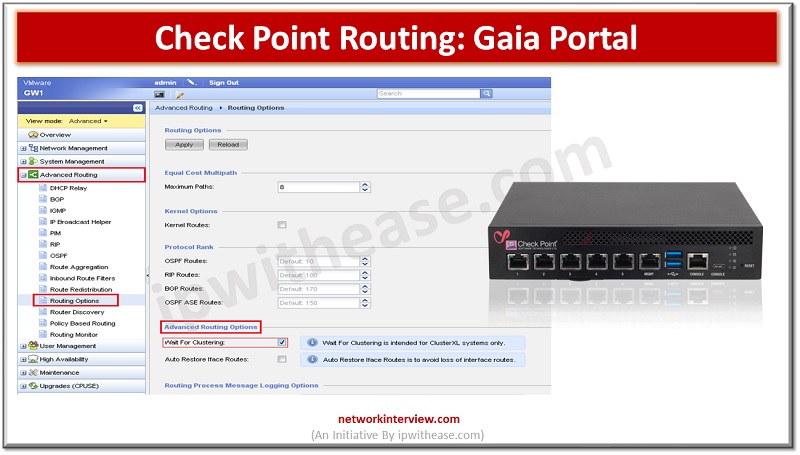
Gaia is the latest operating system for security applications developed by Check Point. It is named after Gaia, the mother of all in Greek mythology, symbolizing a well-integrated system comprising various components to ensure optimal performance. Gaia OS is designed …
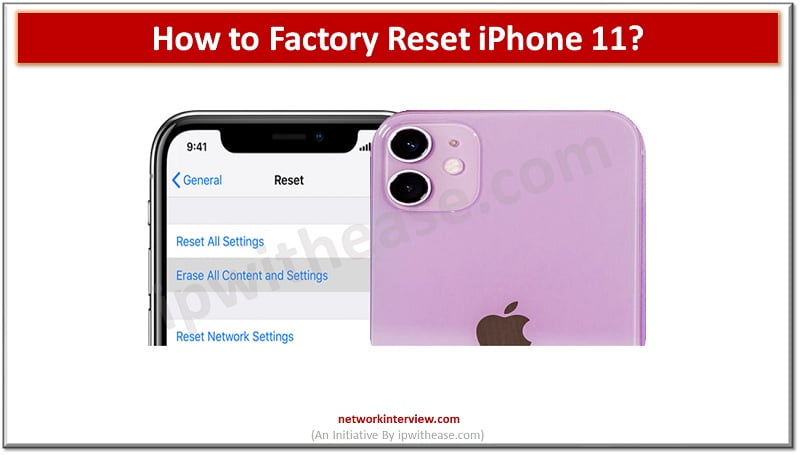
When it comes to selling your iPhone 11, taking the necessary steps to ensure your personal data is securely wiped from the device is crucial. This is where a factory reset comes into play. A factory reset restores your iPhone …
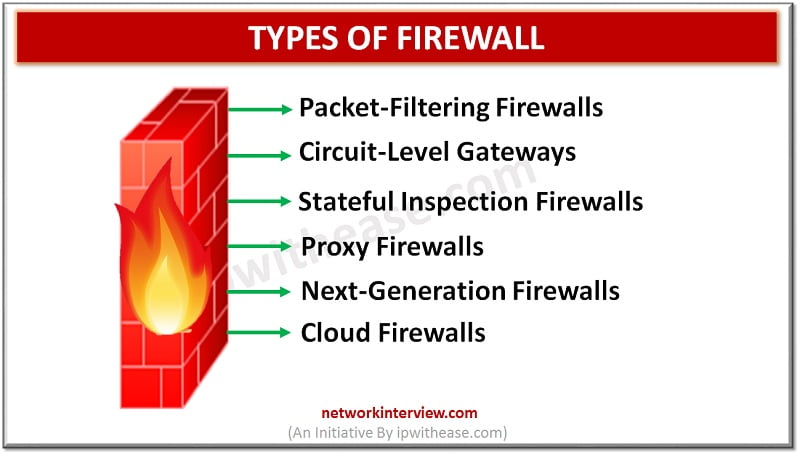
Firewalls have come a long way and have been there for decades to provide protection against malicious attacks and intrusions. In their infancy days firewalls were a simple filtering mechanism based on ports and IP addresses. But over time, firewalls …
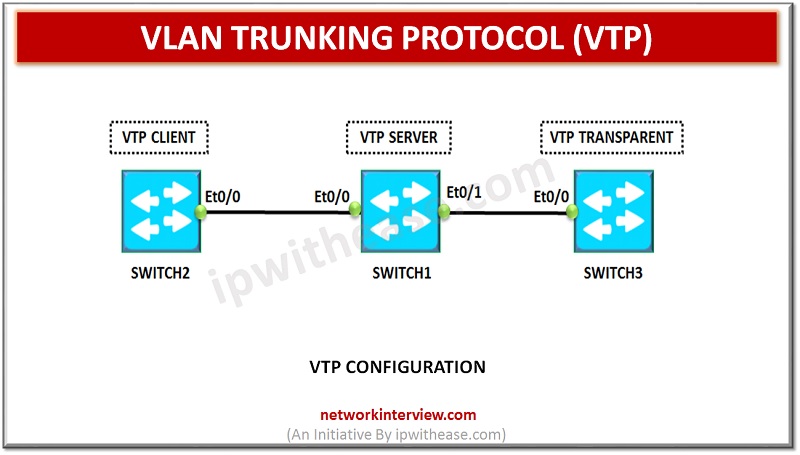
VLAN Trunking Protocol VLAN Trunking Protocol is used by Cisco switches to exchange VLAN information. In VTP, synchronization of VLAN information, such as VLAN ID or VLAN name can be done with switches inside the same VTP domain. VTP domain is …
Let’s talk about something that’s probably an essential part of your everyday life: Windows 10. This fantastic operating system from Microsoft has been around for a while now, and it’s packed with features to help you be more productive and …
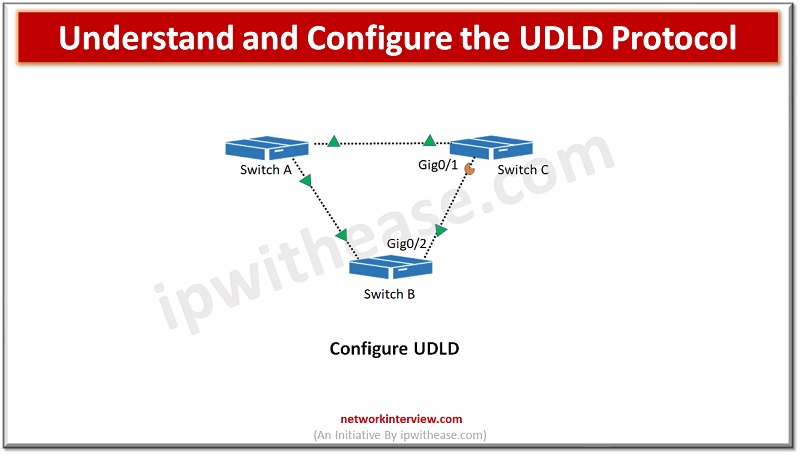
Switches are used to connect hosts on networks. Switch forwards data packets between devices using packet switching technique. Any mis-wiring or hardware faults could lead to disruption in network communication path and create serious network issues such as spanning tree …
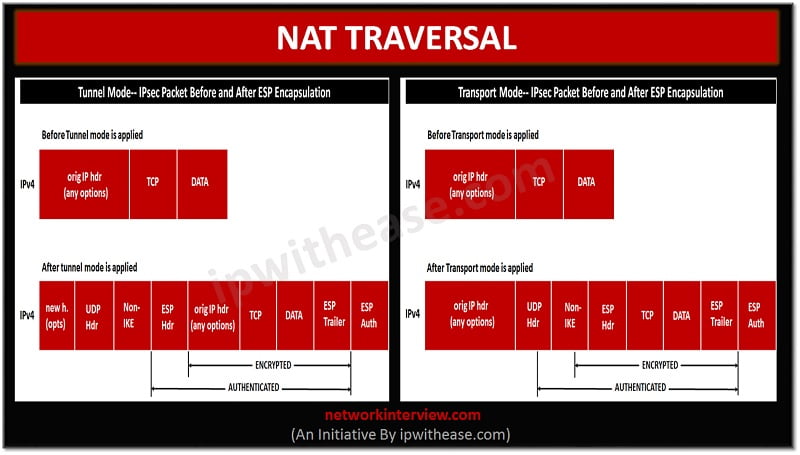
Overview The IPSEC NAT Traversal feature introduces IPSEC traffic to travel through Network Address Translation (NAT) or Port Address Translation (PAT) device in the network by addressing many incompatibilities between NAT and IPSEC. NAT Traversal is a UDP encapsulation which …
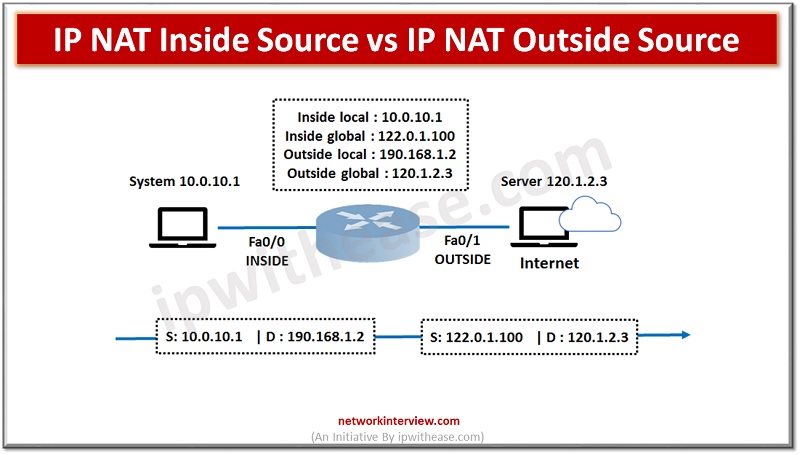
In order to access the Internet, we need one public IP address; however, we can use Private IP address in private networks. The Network address translation (NAT) allows multiple devices to access the Internet with a single public IP address. …
The blockchain ecosystem is growing at a stupendous pace with the ability to register a dominant impact across different industries. As a matter of fact, blockchain has transformed the banking and financial services industry with cryptocurrencies and decentralized finance use …
It is a fact that small businesses form the majority of all types of commerce in America, with over 99% of all industries being classed as operated by small firms. Put simply, small businesses account for the largest part of …
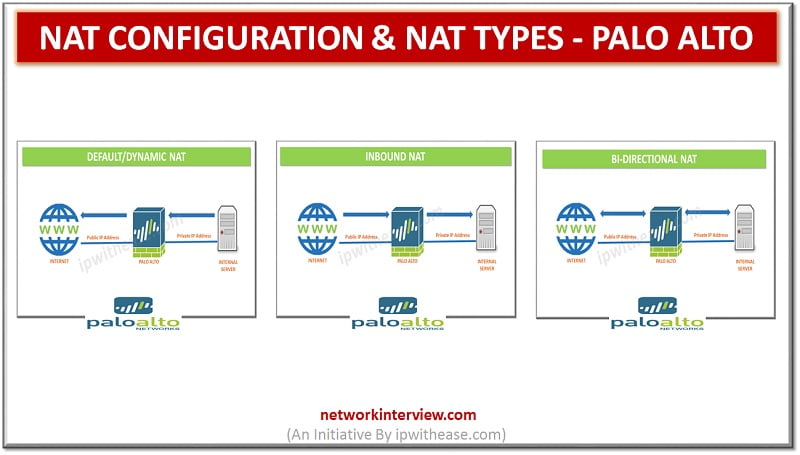
In the previous post we discussed the Architecture of Palo alto firewall. Now, we will discuss the NAT configuration and NAT types in Palo alto. Network Address Translation (NAT) allows to translate private, non-routable IP addresses to one or more …
Cyber security is an in-demand security measure that helps to protect enterprises, individuals, and their systems from online threats. It helps secure crucial data within computer devices and networks from unknown access. In this regard, Palo Alto Networks plays a …
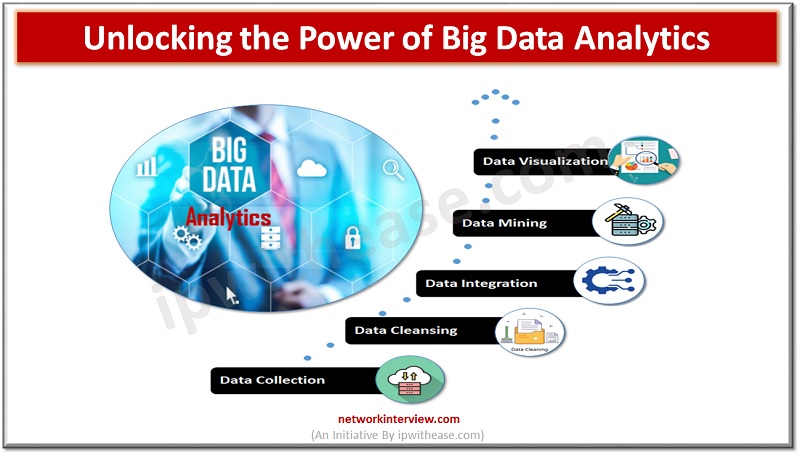
Big data analytics is the process of analyzing large and complex sets of data to uncover patterns and trends. As the amount of data continues to grow at an exponential rate, the need for big data analytics is becoming increasingly …
Nothing lasts forever, especially high-tech products like a laptop or computer. However, if you know how to care for it, your computer can survive for a very long time. This applies to both PCs and laptops. If your equipment malfunctions …
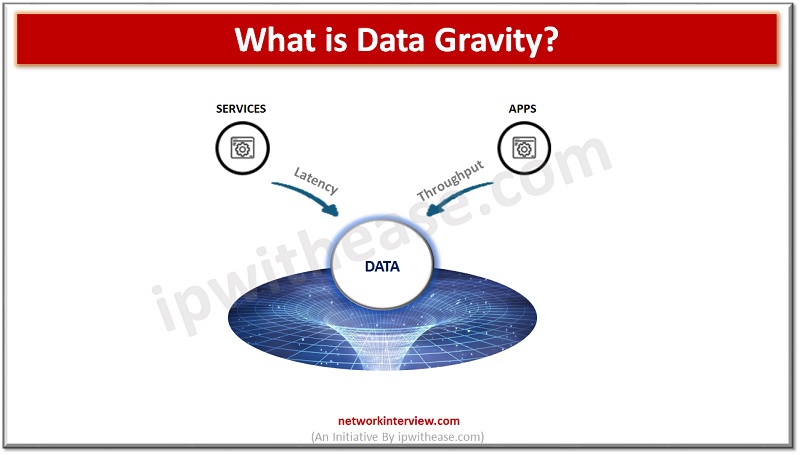
Data gravity is an increasingly important concept in the age of digital transformation, and understanding how it works, its benefits, and challenges is essential for all businesses. In this article, we’ll unpack the concept of data gravity and provide a …
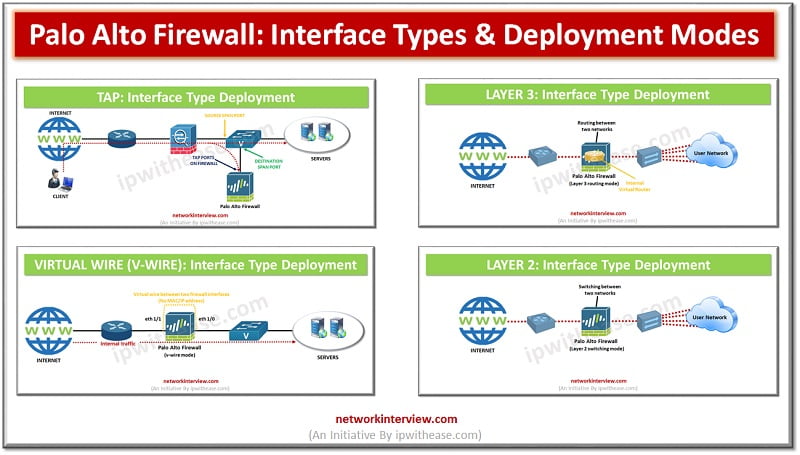
Introduction to Palo Alto Interface types/ Deployment Modes The entry and exit point of traffic in a firewall is enabled by the interface configurations of data ports. Palo Alto being a next-generation firewall, can operate in multiple deployments simultaneously as …
When it comes to software testing, there are two main approaches – manual testing and automated testing. Each one has its own advantages and disadvantages, and it can be difficult to decide which approach is best for your needs. In …
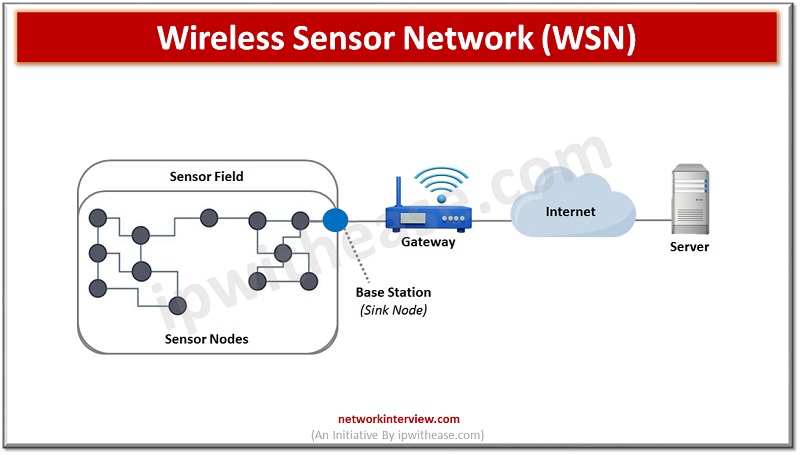
Wireless sensor networks (WSNs) have been around for decades, and their importance has only grown over time. WSNs are used for monitoring, gathering and transmitting data from various sources, such as temperature, humidity, air quality and more. They are also …
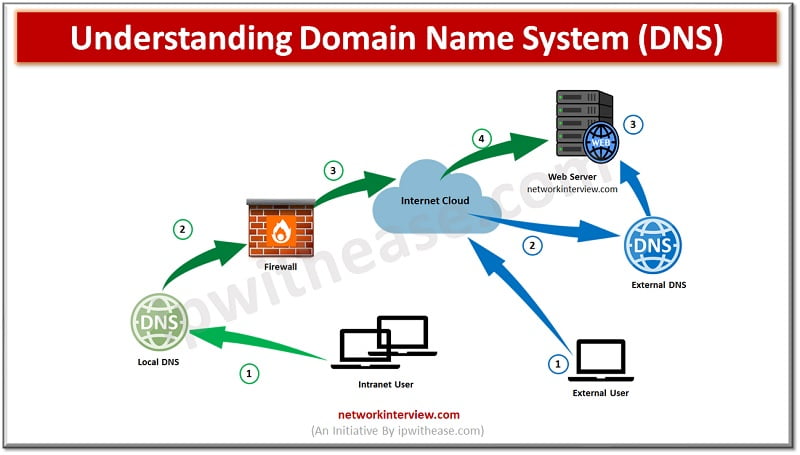
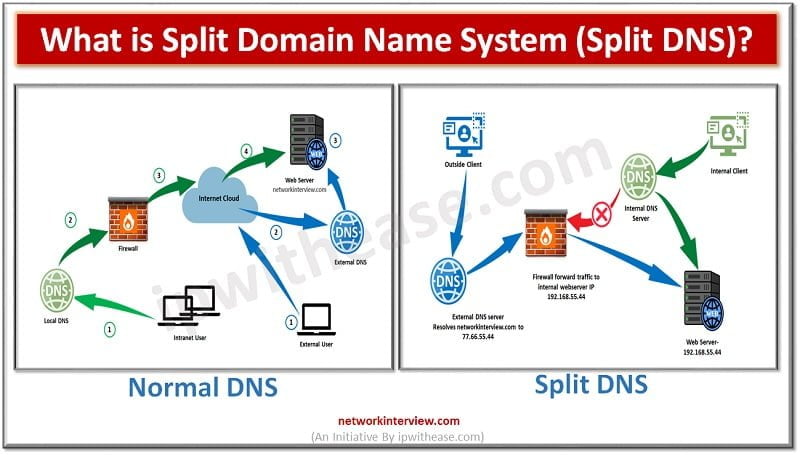
DNS Working Before understanding the Split Domain Name System, let’s discuss how normal DNS resolution works for Internet traffic. However, DNS works to resolve names to IPs. When an Internet client open a Web-browser and type www.networkinterview.com Internet Client will …
Smart contracts are computer programs that run on blockchain technology and execute automatically when certain conditions are met. They have revolutionized the way we think about contracts and are becoming increasingly popular in various industries. However, finding smart contract developers …
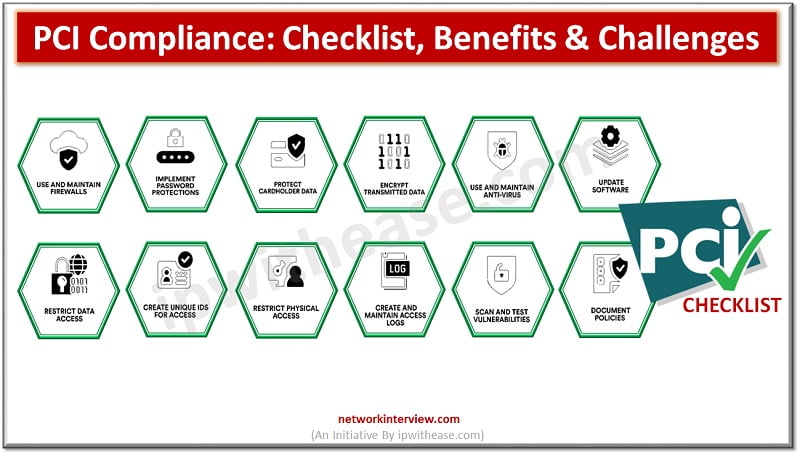
Whether you own a small business or manage a large enterprise, ensuring customer data security is a top priority. To that end, businesses must adhere to the Payment Card Industry Data Security Standard (PCI DSS), a set of security requirements …
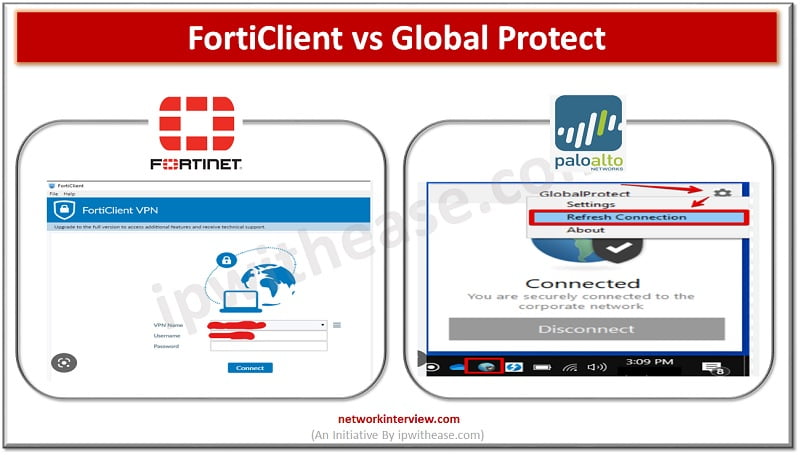
What is FortiClient? FortiClient is an app to provides UTM features like web filtering, giving web security and content-based filtering. FortiClient app is installed in the user’s system and tracks the traffic based on policy. The web application firewall offers malware …
You can keep tabs on your friends and family with the tap of a button using mobile phone tracking software. Yet, do you understand how these applications function? Or the many different methods that they can assist you in locating …
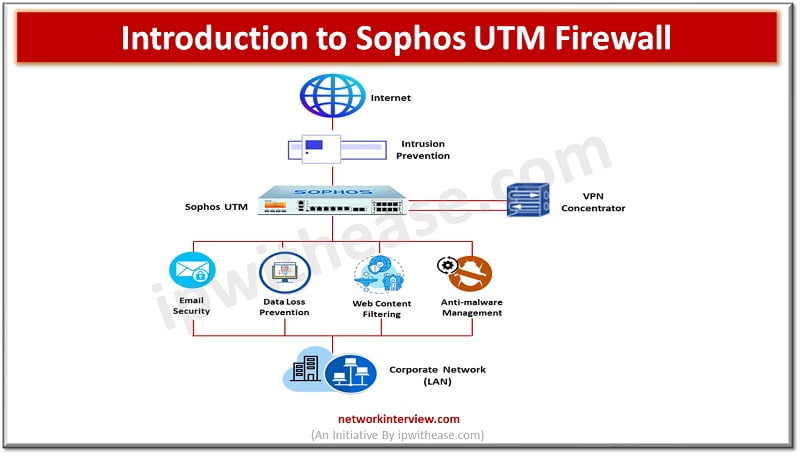
Introduction to Firewall In todays digital scenario, where businesses demand agility and information are hosted on cloud infrastructure security of data is one of the primary concerns of business and protection of data from unwanted sources is the prime objective. …
A decade after data scientists were labeled “the sexiest job of the 21st century” by Harvard Business Review in 2012, data scientists continue to be among the greatest and most sought-after job roles in the IT sector, making their way …
In 1996, Congress passed the HIPAA law to protect individuals’ health information. This federal act established national standards for how sensitive patient data should be stored and handled, requiring healthcare providers to meet these regulations. To make sure their practice …
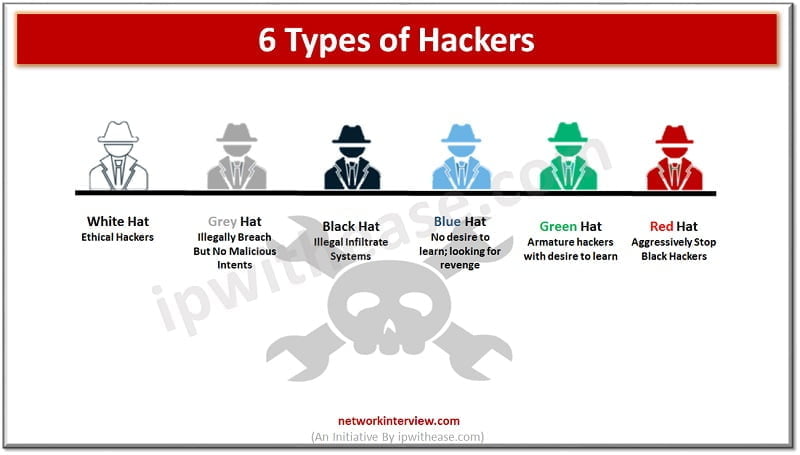
You must have heard the word ‘hacker’ multiple times in cybersecurity. The organizations have trained security staff to take care of cybersecurity threats. Hacking is generally referred to as someone gaining access to your network and systems by unauthorized means. …
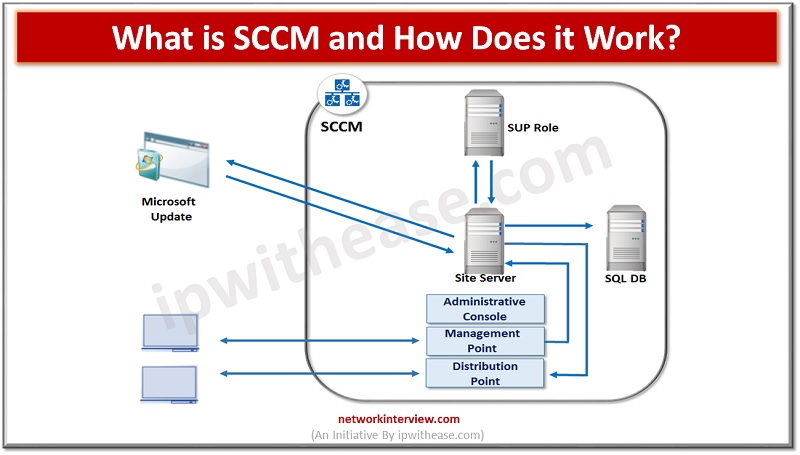
Configuration Manager, commonly known as SCCM, is a powerful and versatile tool created by Microsoft. It provides IT professionals with an integrated platform to manage and deploy software, hardware, and other resources across their networks. In this blog, we’ll take …
With the rise of technology and the internet, the world has become more connected than ever before. From online shopping to social media, we rely heavily on technology in our daily lives. While technology has made our lives easier, it …
In today’s digital world, the need for brand protection is more important than ever. With the rise of online marketplaces and e-commerce websites, counterfeiters have found a way to exploit brands and make money off of fake products. To combat …
Maintaining the security of your personal or business network and Internet connection is essential in today’s digital world. With the rise of sophisticated cyber threats, identity theft, and data breaches, protecting yourself from potential risks is becoming more critical than …
It is not possible to safeguard your DVDs data always, because there are chances and possibilities for the DVD to get damaged. After getting damaged it is not an easier task for you to recover the file and data that …
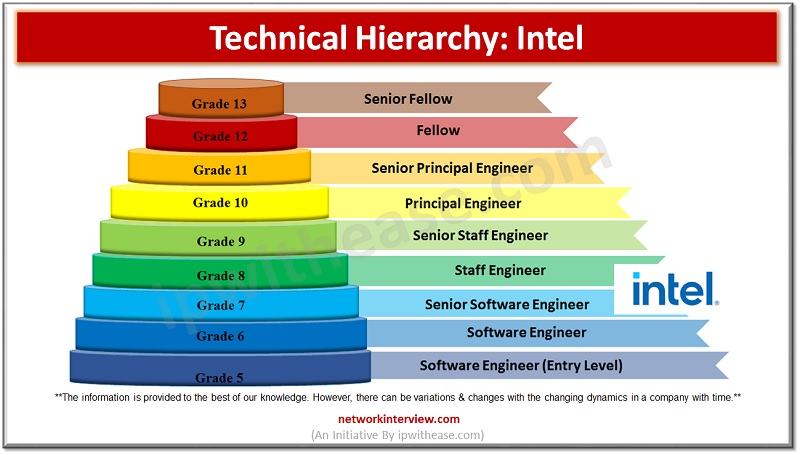
Getting a job in an MNC is always the dream of aspiring new Engineers and developers. But oftentimes, the hierarchy and job positions mentioned in the Interview make them confused and they land on a position lower or higher to …
Screening and interviewing tech candidates in Latin America requires a specific set of skills and considerations. One of the first steps is to understand the concept of nearshore development, which refers to outsourcing software development to neighboring countries with similar time …
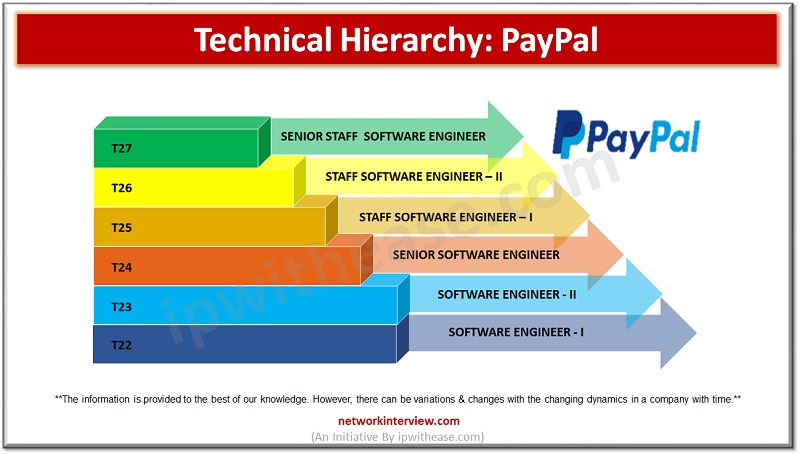
It is a dream for many graduating Software engineers to land a job at PayPal. The main reason is its global availability and promising salary and other benefits. Are you one of them? Then you should consider certain things first. …
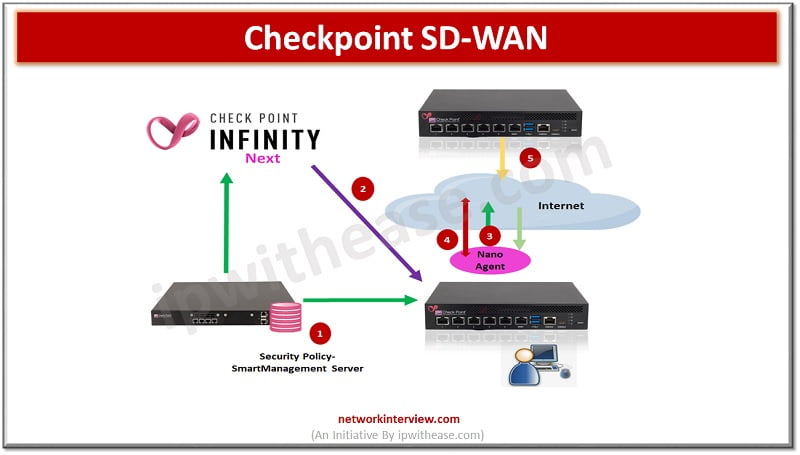
Note: This document is for those seekers who have prior knowledge of SD WAN and want to enhance SD WAN concept in Checkpoint perspective. This blog covers below topics of Checkpoint SD WAN: Quantum CheckpointSD-WAN concept Architecture Application basic traffic …