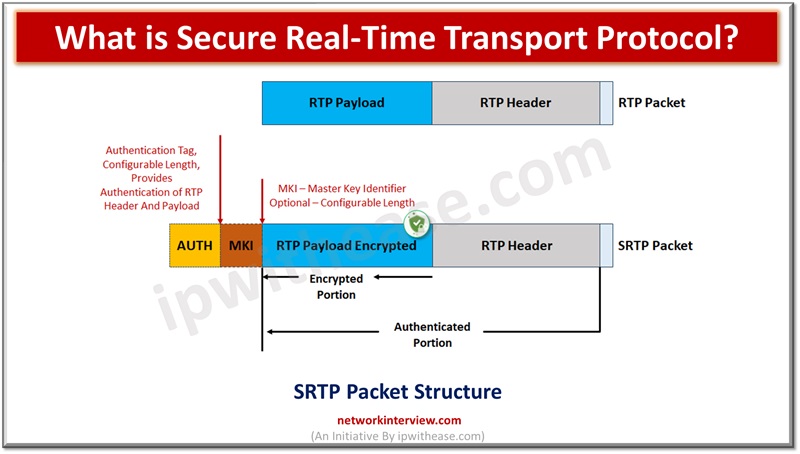
There are a set of protocols which define how real time traffic handling will be taken care of such as audio and video over the Internet. These protocols are known as Real Time Transport protocol (RTP). RTP protocol is used …
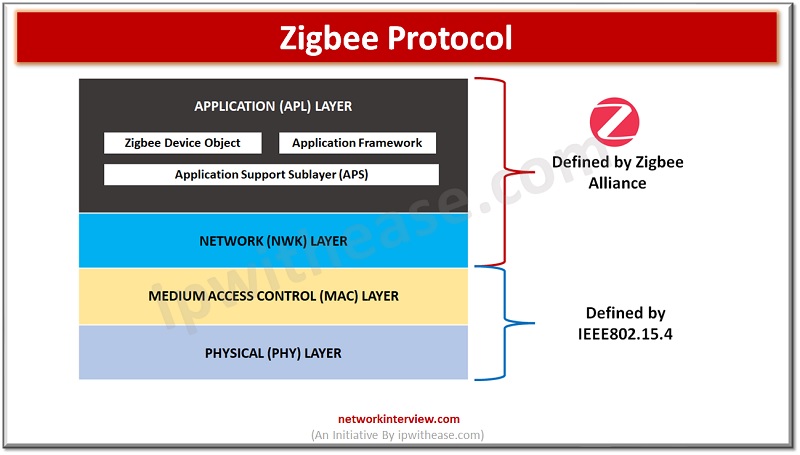
Zigbee is a wireless protocol that enables smart devices to communicate with each other over a Personal Area Network (PAN). It is widely used in home automation systems to control various devices such as light bulbs, sockets, locks, motion sensors, …
Wifi6 vs Wifi5 vs Wifi4 In the wireless world, Wi-Fi is the term that is similar in general to access of wireless. Although the fact is that this specific trademark is owned by Wi-Fi Alliance. This dedicated group takes care …
World is like a global digital village in the era of cloud computing. People need to communicate, participate in events , execute tasks irrespective of geo boundaries or locations. The internet , multimedia and wireless communication networks let people share …
Data breaches are costing organizations very expensive and every year exposing millions of people’s sensitive data resulting businesses to lose millions. Data breaches in year 2021 estimated to average cost of $4.24 million. Personally Identifiable and sensitive personal information is …
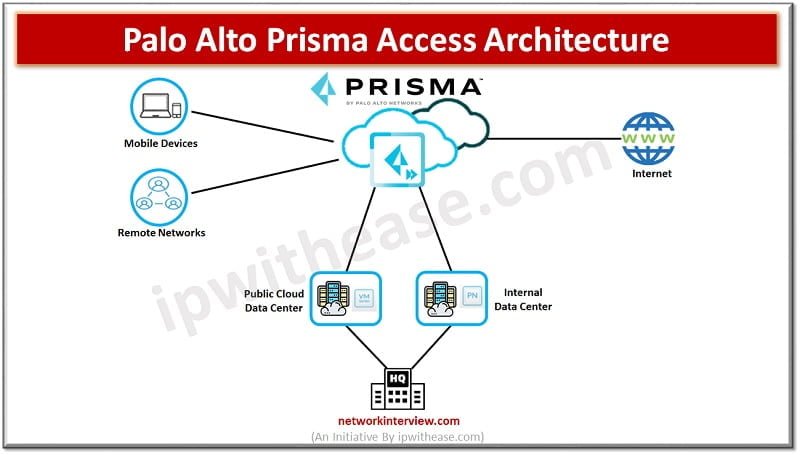
What is Palo Alto Prisma Access? Palo Alto Prisma Access is a Cloud service provided by Palo Alto Networks. This service provides secure access to Internet and business applications that may be hosted on SASE, a corporate headquarters, Data Centres, …
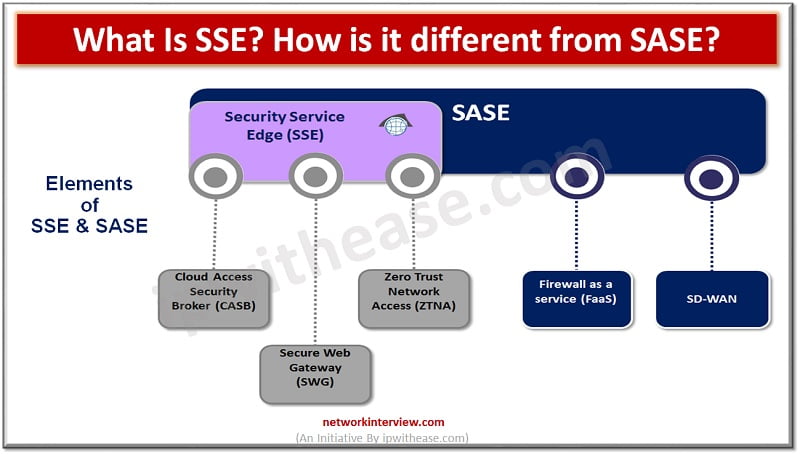
Introduction to SSE & SASE Security and network architecture have taken a front seat since cloud adoption is all time high and constantly growing. The demand for remote workforce is increasing and per Gartner research demand for remote working is …
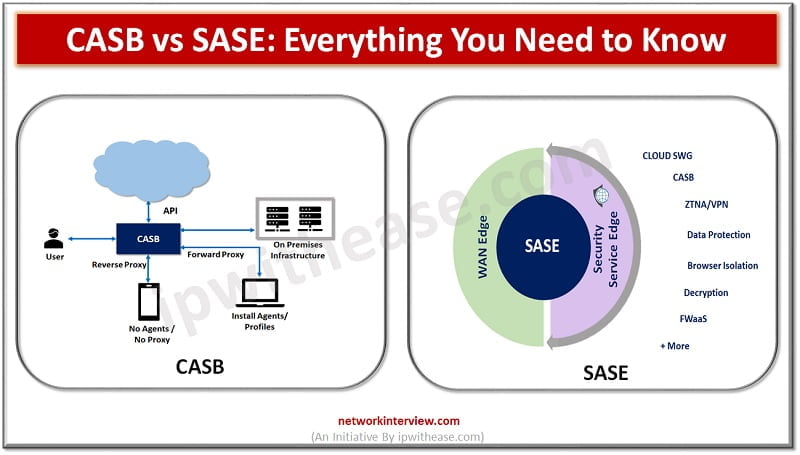
CASB vs SASE: Introduction As more and more data moves onto the cloud new tools and methods are evolving to control data and adhere to security regulations. Coronavirus pandemic is becoming an acceleration factor as all around the world companies …
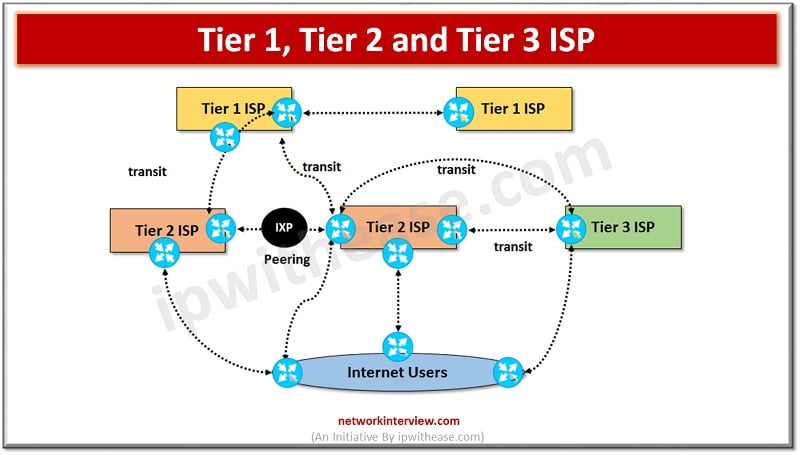
Internet Service Providers Internet service providers are organizations which provide internet connection to end users and other organizations which can be customer businesses, individuals. ISPs have made it easier and affordable to connect to the internet. ISP acts like a …
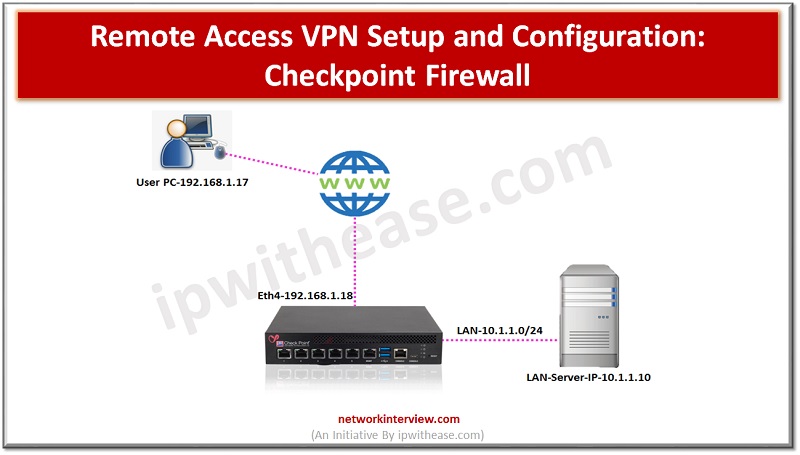
A remote access VPN (virtual private network) allows clients who are working remotely to firmly access and utilize applications and servers that deploys in the office Data Centre and head office, encrypting all VPN traffic the users send and receive …
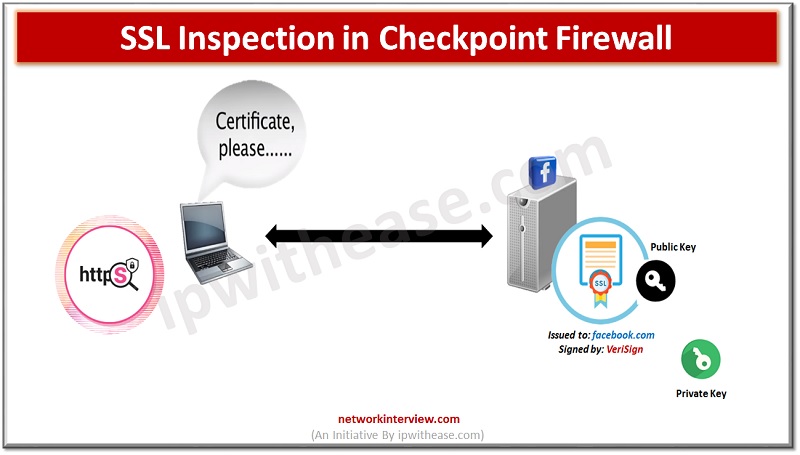
Encrypting SSL traffic is critical for user privacy and to securely conduct business across the net. Indeed we have seen a huge rise in websites shifting to SSL in recent years. This is a good thing however traffic can be …
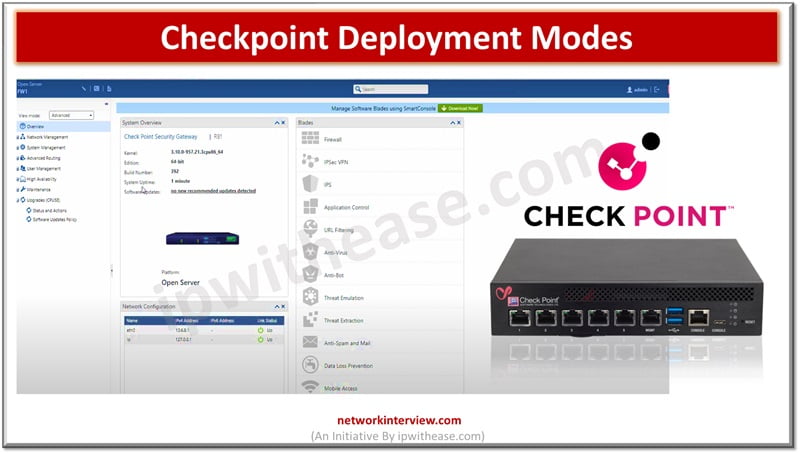
There are few ways to deploy Checkpoint Firewall in the network. Standalone Deployment Distributed Deployment Here, we will discuss Standalone and Distributed Modes of Checkpoint Deployment. Let’s start with Standalone Mode. Checkpoint Deployment Modes Standalone Deployment Mode Both Firewall and …
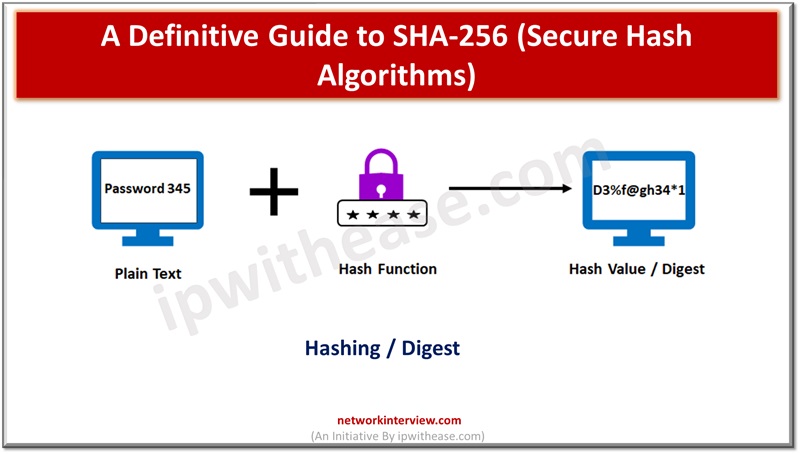
Hashing and encryption are one of the key mechanisms to secure data. A variety of algorithms exist in the cyber world to secure data with different key lengths – 64-bit, 128-bit, 256 bit and so on. However, the secure hash …
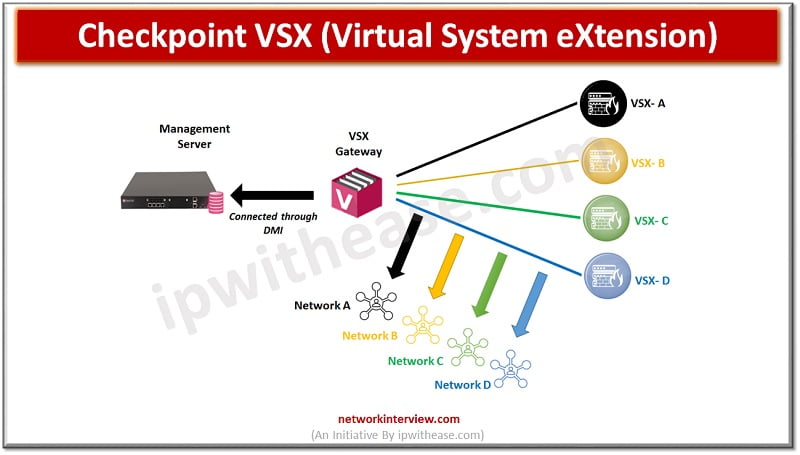
What is Checkpoint VSX? Checkpoint VSX full form is Virtual System eXtension (VSX), a product that runs multiple virtual firewalls in the same hardware firewall. You can purchase hardware appliances with Licence of Virtual firewall. Using one hardware you will …
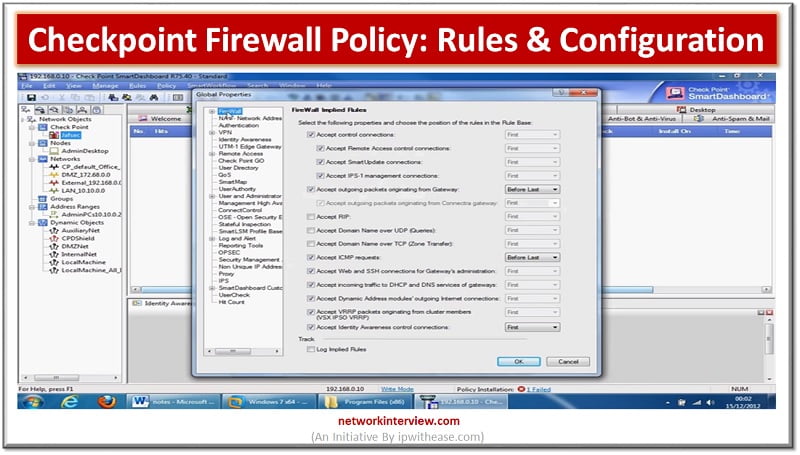
A firewall policy outlines the way an organization’s firewalls should handle the traffic that comes into and out of the specified IP addresses and address ranges, protocols, applications and content types governed by the organization’s security policies. Organizations should carry …
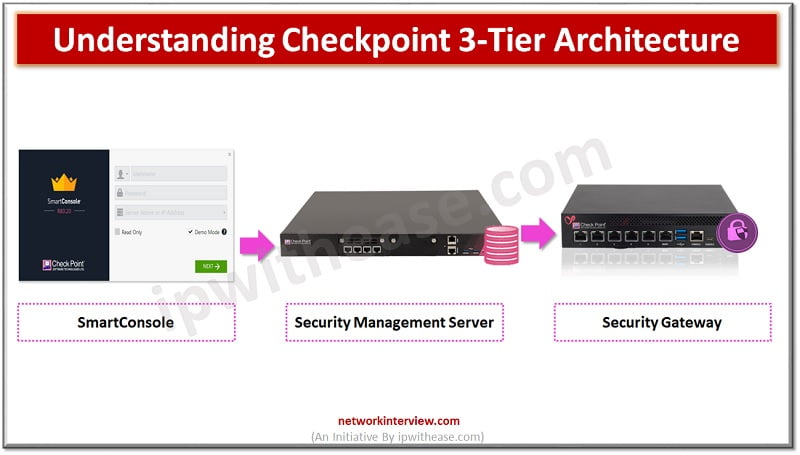
Before starting to explore Checkpoint NGX Firewall technologies, it is critical to comprehend Checkpoint 3-Tier architecture. This architecture describes the relationships between the components of Checkpoint, as well as how they work together as a harmonious unit. Each element has …
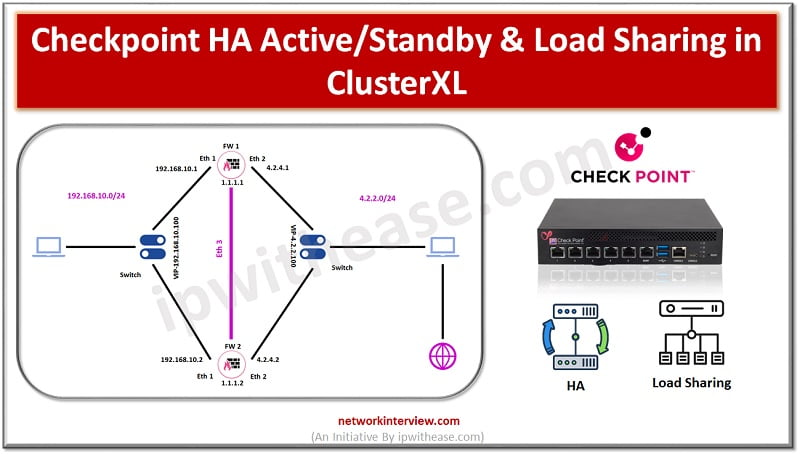
Checkpoint HA High Availability is the feature of firewall in which it eliminates the single point of failure in the network. Two firewalls make a cluster and act as an active passive mode. Active firewall handles the network traffic while …
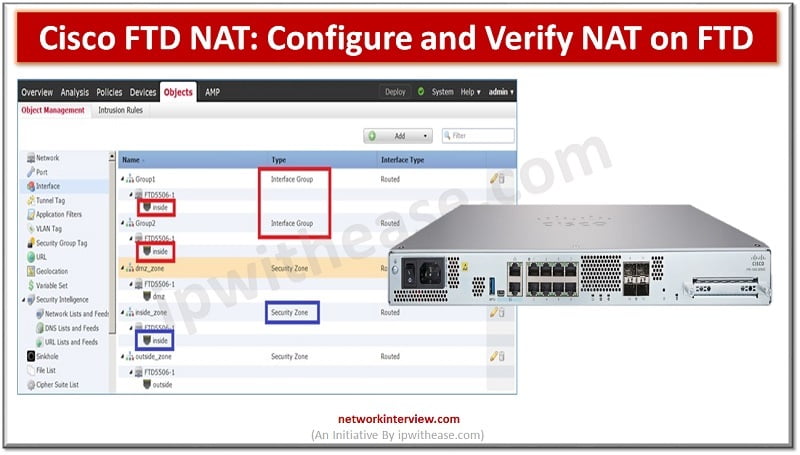
Cisco FTD NAT: Introduction An IP address is the basis of every communication over the network and Internet. Each computer device is assigned an IP address within an IP network which identifies the host as a unique entity. But due …
NAT Type 1 vs 2 vs 3 Nowadays, the 2 major gaming console types used extensively around the globe are Sony PlayStation Microsoft Xbox NAT stands for Network Address Translation, which represents the ability to translate a public IP address …
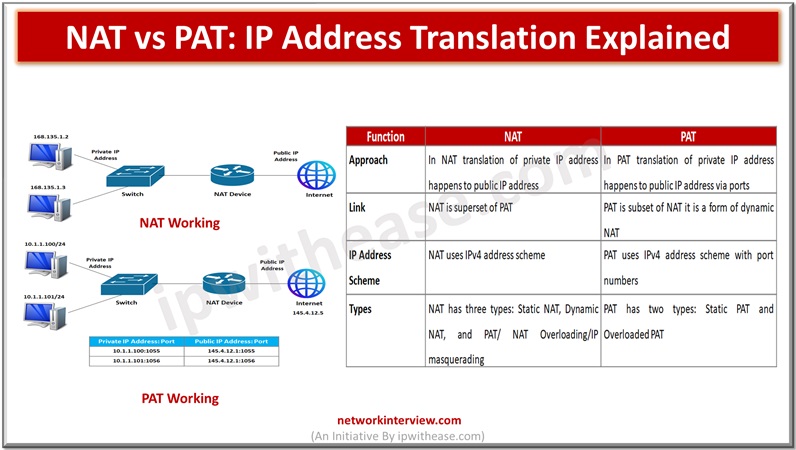
In the networking world IP address translation is required so that internal systems could have access to the external world or Internet. The IPv4 scheme can have a maximum of four billion IPv4 addresses in theory but the actual number …
Security is of paramount concern while using the Internet and its services. Have you ever thought about how secure your data is over the Internet while working? When I am connecting to the Internet, we are taking ISP services so …
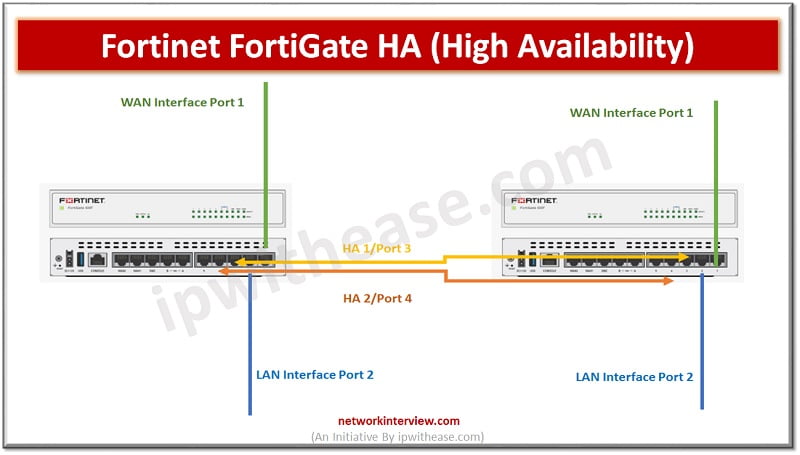
Objectives High Availability HA Modes FGCP (FortiGate Clustering Protocol) Heartbeat Interfaces and Virtual IP Interfaces HA Requirement Configure Primary FortiGate Firewall Configure Secondary FortiGate Firewall HA-Troubleshooting What is High Availability? High Availability (HA) is a feature of Firewalls in which …
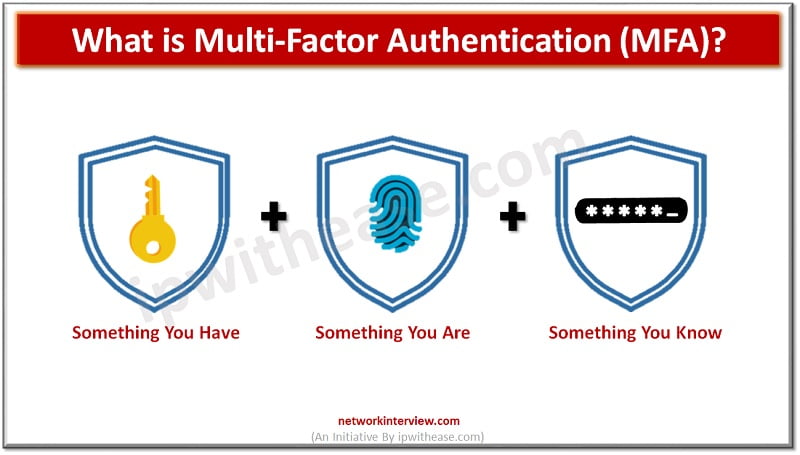
Companies of all sizes are becoming increasingly aware of the need for stronger user authentication to reduce the risk of cyber attacks. This is particularly true in light of recent high-profile attacks on accounts from Internet users such as celebrities, …
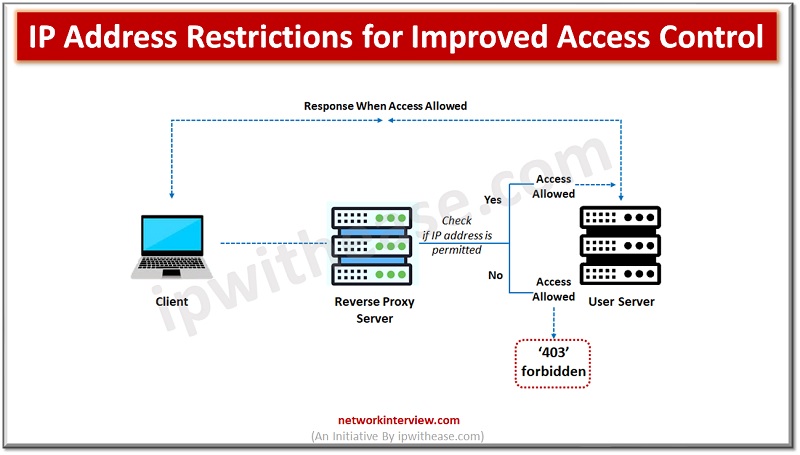
Network security is of paramount importance for IT administrators. Various ways and means and a variety of tools are used to protect organization networks from internal and external attacks. All communications in a network happens via IP addresses as per …
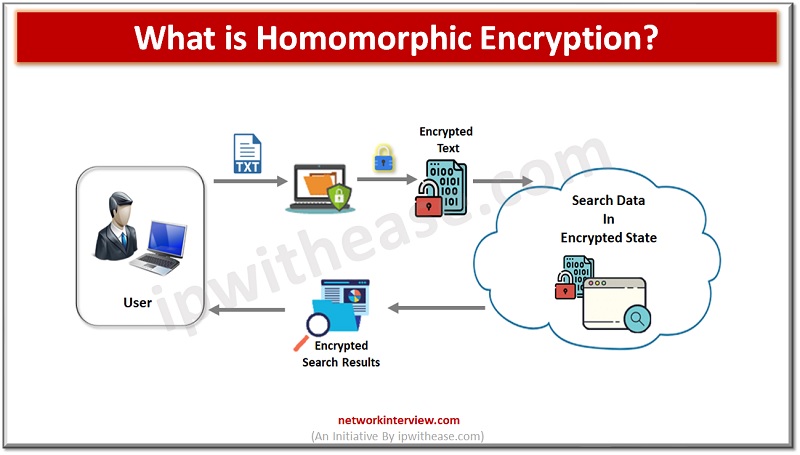
Homomorphic encryption is a powerful and innovative type of encryption that promises to revolutionize the way that data is secured and shared. HE is a relatively new technology and is still in the early stages of research and development. However, …
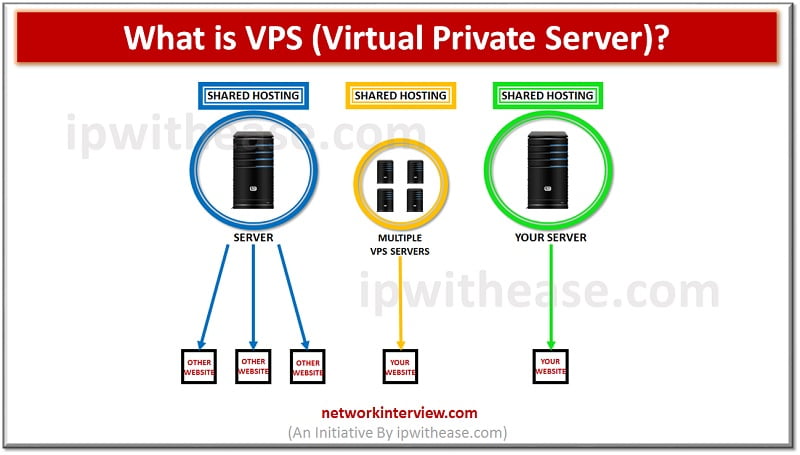
Introduction to VPS (Virtual Private Server) In the IT community, we define with the term VPS (Virtual Private Server), any virtual machine that is sold as a service by an Internet Hosting Service. In normal conditions, a virtual private server …
Well, not always. As VPN is a new concept , so the rules are murky and open to multiple interpretations. Though all good VPN companies will do their best to protect your data, privacy, and overall security on the web, …
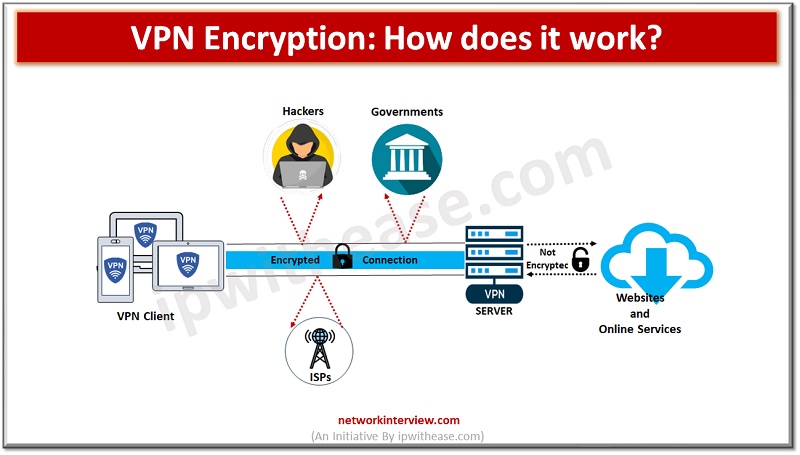
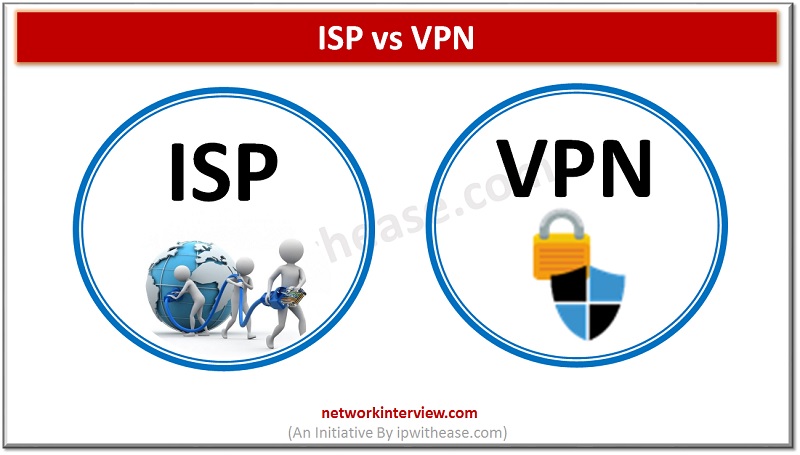
Introduction to ISP & VPN Internet service providers (ISP) facilitates internet navigation and helps in transmitting all your Internet packets however VPN creates a secure tunnel where data is encrypted during transmission. Often people get confused between the two terms …
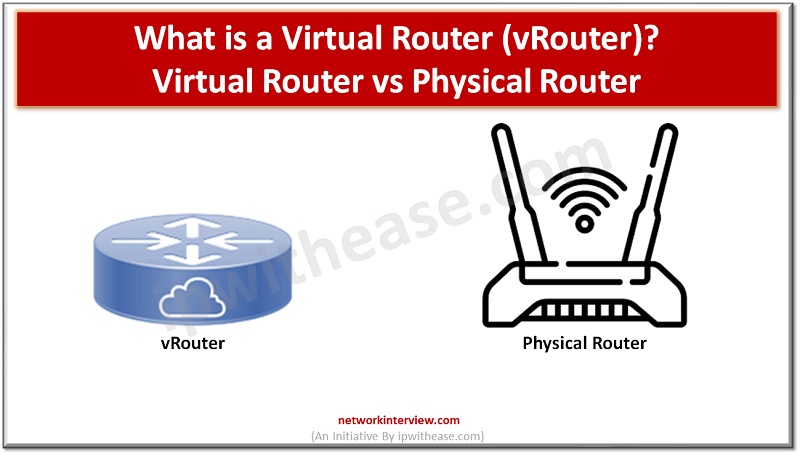
As the world becomes increasingly digital, the need for efficient, reliable, and cost-effective networking solutions is more critical than ever. One such solution that has gained popularity in recent years is the Virtual Router. In this article, we will learn …
The cybersecurity industry has become increasingly competitive, making it essential for professionals to validate their skills through certifications. Cisco offers a range of CyberOps certifications that are highly sought after by employers. In this article, we will guide you through …
In today’s internet world a good NAC solution partner is needed for every company involved in the digital or e-commerce industries. In this article, you will get to know the top 10 NAC solutions for your business. Let’s start the …
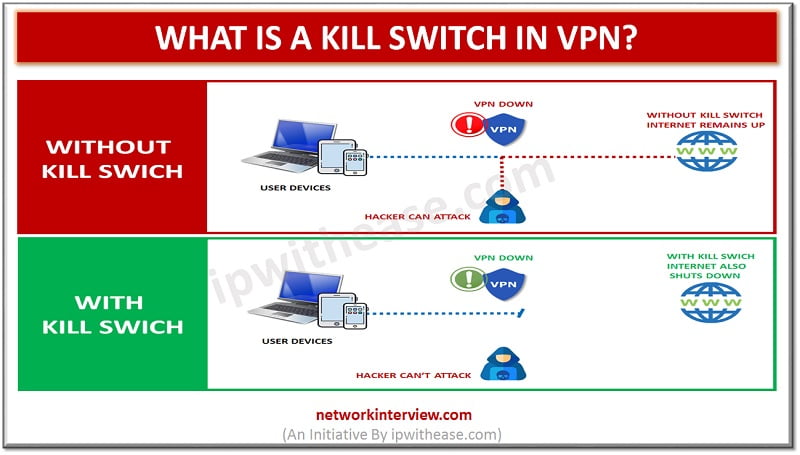
Kill switch in VPN A VPN kill switch is also known as an internet kill switch. For the VPN security solution, a VPN kill switch is a critical piece. It is considered to be the top feature for the best …
VPN (Virtual private Network) has become an essential part of network and security suite when it comes to secured communication over Internet. VPN forms secured tunnels between a local client and a remote server. Remote and mobile workers use VPN …
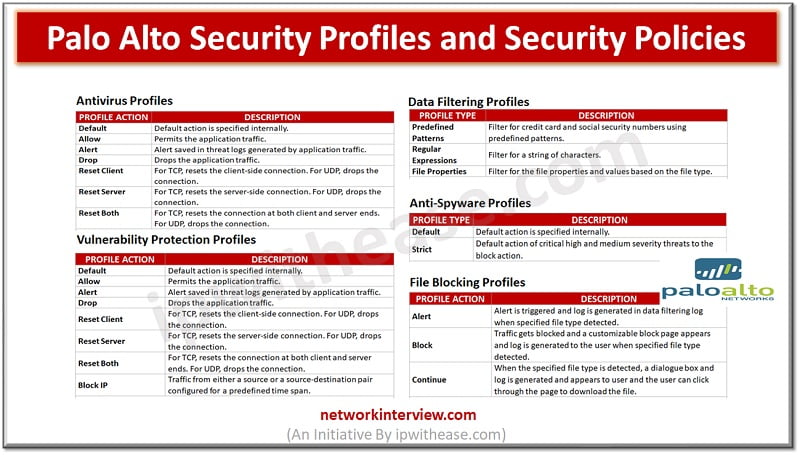
Below are the key profile types provisioned in Palo Alto Firewall. Lets discus all the profile types one by one – Palo Alto Security Profiles & Security Policies While security policy rules enable to allow or block traffic in network, …
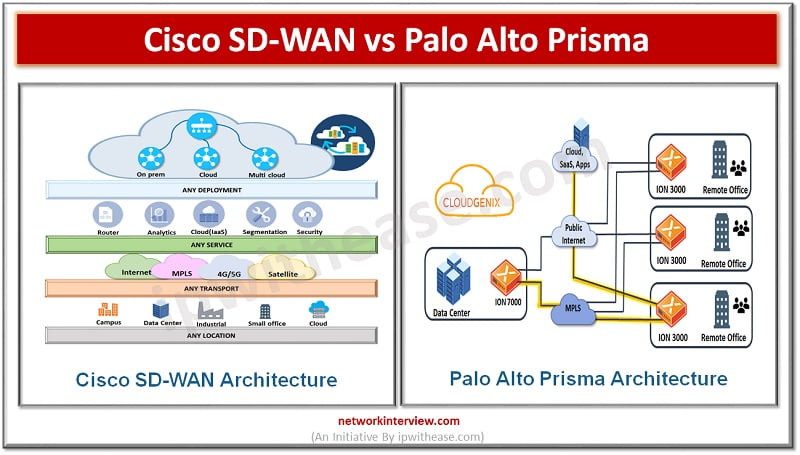
SD-WAN Solutions Penetration of cloud all around the enterprises also brought the need for hybrid networking solutions supporting private WANs and commodity Internet connections to support adoption of cloud applications, remote connectivity, scalability with application performance and including visibility. Major …
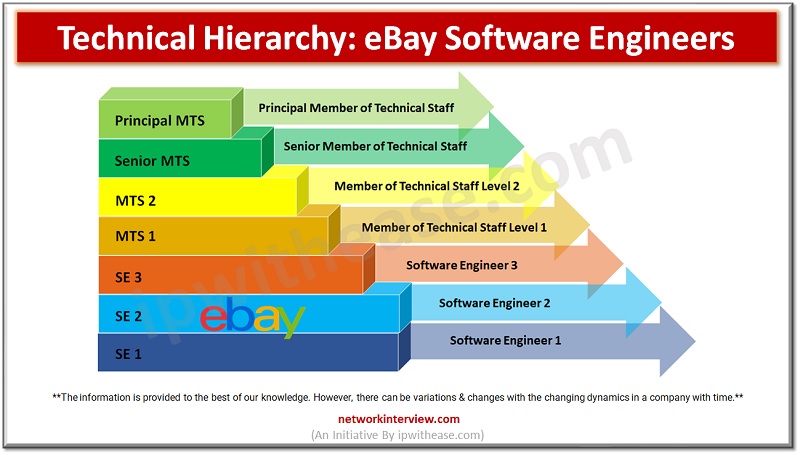
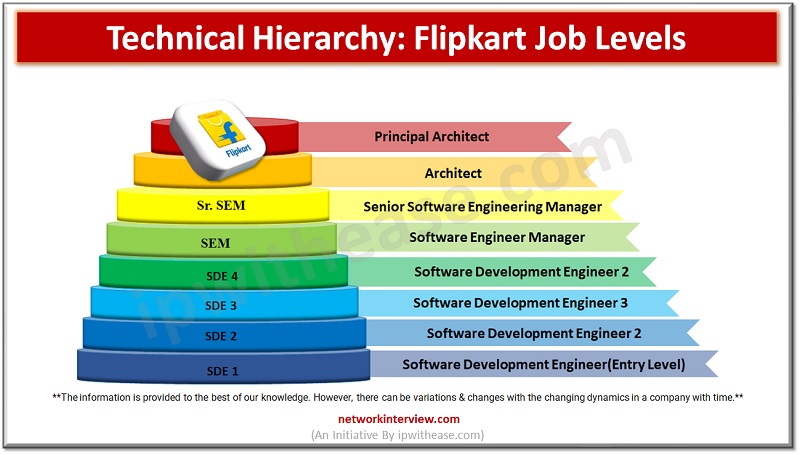
As the E-commerce industry has boomed very fast in the past years, many new engineering and other IT graduates are willing to get a job at E-commerce companies like Amazon, Flipkart, eBay, etc… But it’s important to know about the …
In today’s remote world E-commerce and logistics have been achieved as a successful industry. So it is a common interest for many of the new graduates to get a job at E-commerce giants like Amazon, Flipkart, and eBay. Are you …
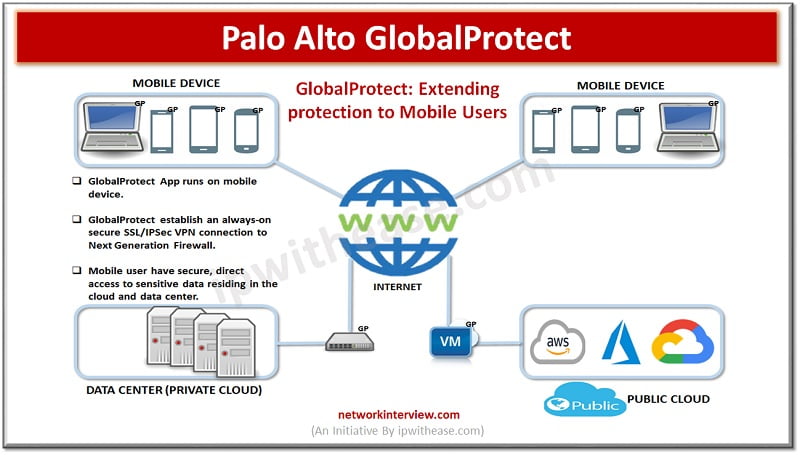
Introduction Palo Alto GlobalProtect is a network security for endpoints that protects mobile workforce by extending the Next-Generation Security Platform to all users geographically anywhere. GlobalProtect secures traffic by applying security policies with Palo Alto next-generation to the application. GlobalProtect …
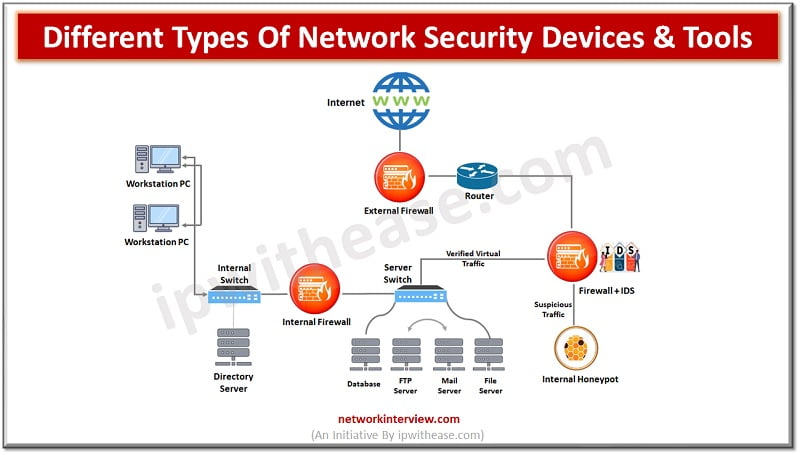
There are several aspects to security and Network Security is one of the key components in this. Network security protects networks from unauthorized access and threats. Organizations deploy or adapt measures to protect networks from malicious attackers. Network security devices …
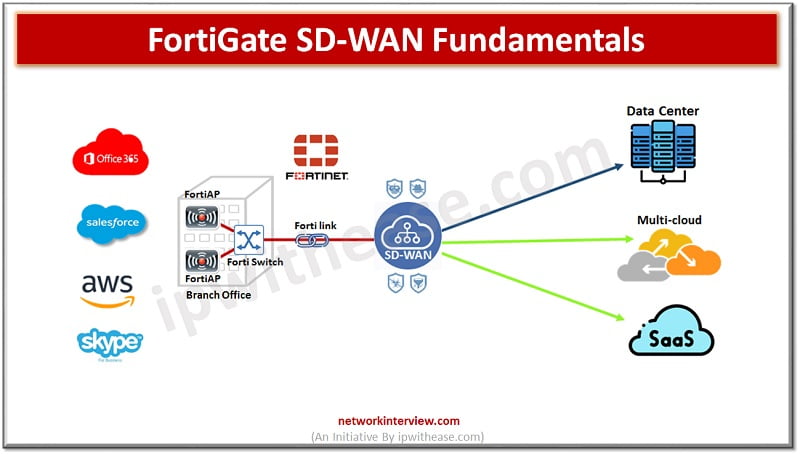
SD-WAN Local Breakout SD-WAN is a virtual interface which connects different link types using a group of member interfaces. Using SD-WAN simplifies configuration for administrators who can configure a single set of routes and firewall policies and deploy them to …
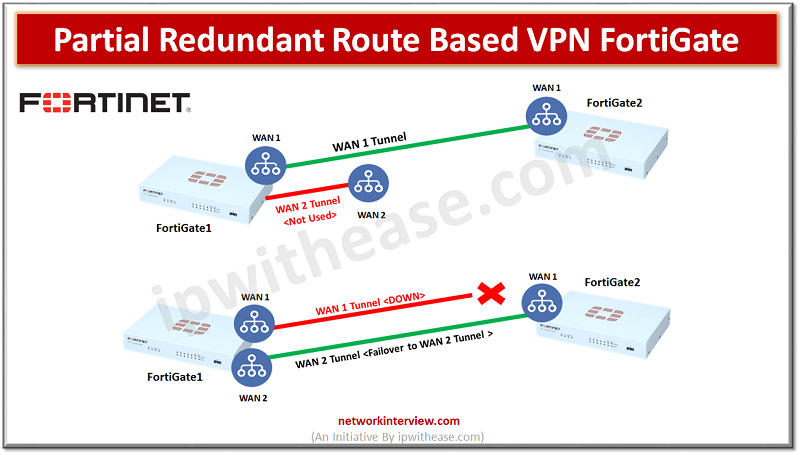
Objectives FortiGate1 has two WAN links and FortiGate2 has single WAN link Create site-to-site route based VPN with Redundant Connection Configure Dead-Peer-Detection failover Configure Link-Health Partial Redundancy is where we don’t have primary and secondary WAN connections on both peer1 …
What is URL Filtering? Sometimes you browse your favorite social networking site on any of the web browser and that web browser displays the message “You are not allowed to browse following website”. This is because of the URL filtering. …
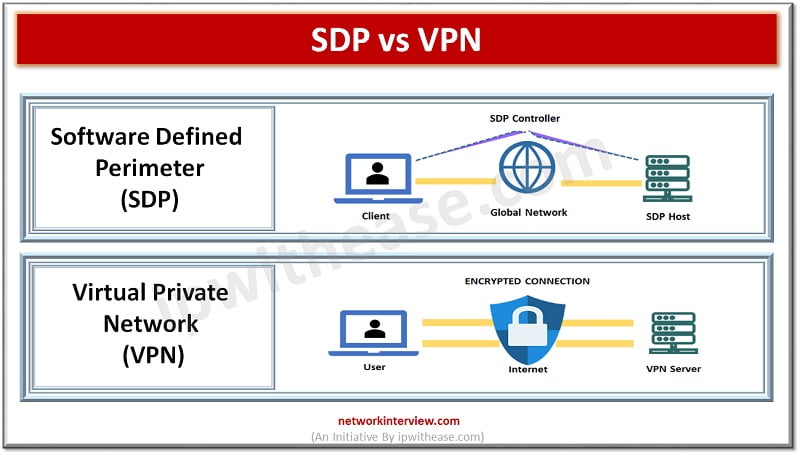
Traditional model of working from the office is quickly diminishing and becoming a thing of the past. As we transition to a hybrid model of working, network security becomes more and more complex. At the same time organizations resources are …
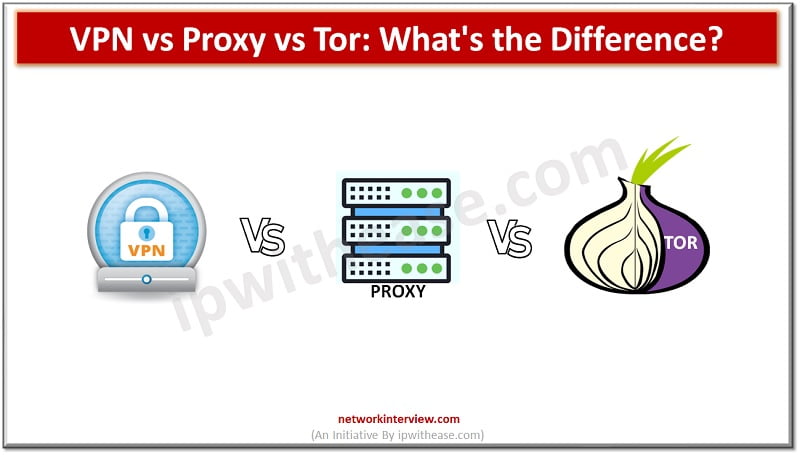
In today’s digital age, protecting our privacy and security online has become increasingly important. With the rise of cyber threats and the constant tracking of our online activities, it’s crucial to find effective ways to safeguard our personal information. Three …
SEO, or Search Engine Optimization, is the process of optimizing online content and websites to enhance their visibility in search engine results. The main objective of SEO is to attract relevant organic traffic to websites, increasing the likelihood of converting …