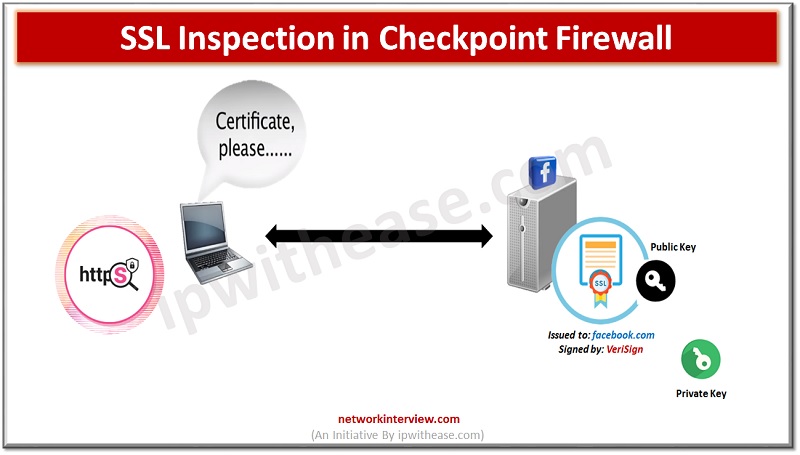
Encrypting SSL traffic is critical for user privacy and to securely conduct business across the net. Indeed we have seen a huge rise in websites shifting to SSL in recent years. This is a good thing however traffic can be …
Artificial Intelligence has become a revolutionary force in the quickly changing field of education, changing how teachers and students learn. Personalizing education to meet each student’s specific needs and learning style is a key component of this AI-driven transformation. We’ll …
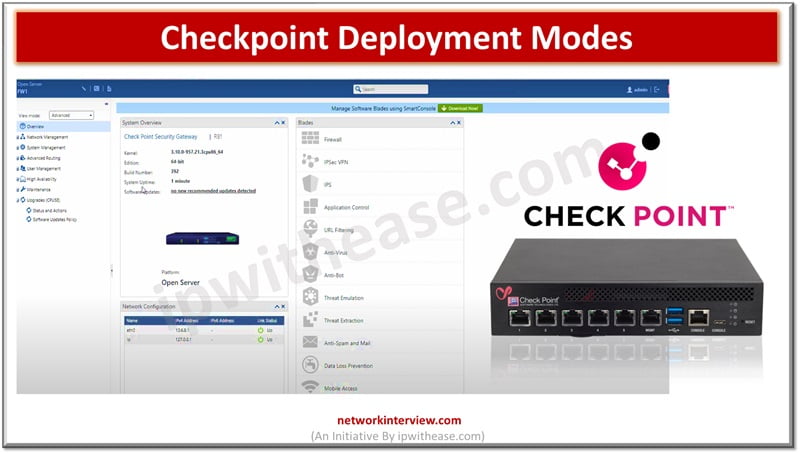
There are few ways to deploy Checkpoint Firewall in the network. Standalone Deployment Distributed Deployment Here, we will discuss Standalone and Distributed Modes of Checkpoint Deployment. Let’s start with Standalone Mode. Checkpoint Deployment Modes Standalone Deployment Mode Both Firewall and …
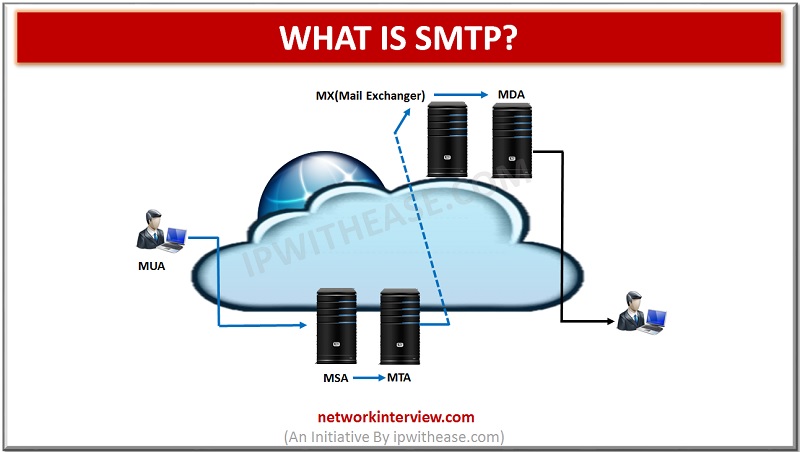
You might have heard of such things as SMTP ports and already know that it has something to do with setting up your email software. But what is it exactly, and how do you determine the proper one? This article …
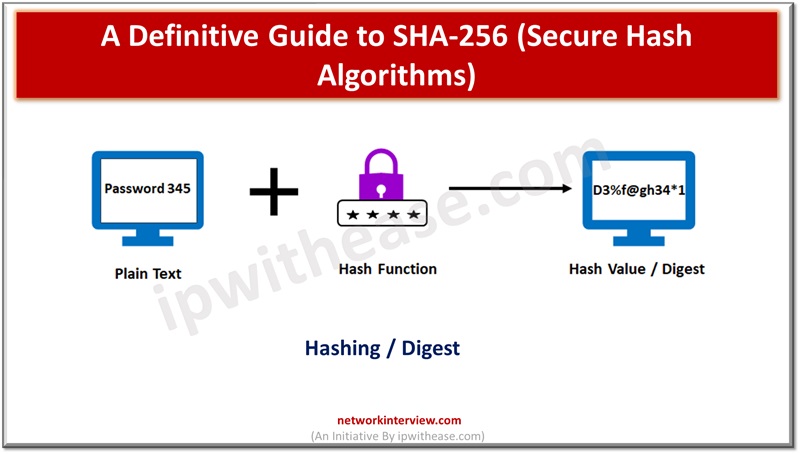
Hashing and encryption are one of the key mechanisms to secure data. A variety of algorithms exist in the cyber world to secure data with different key lengths – 64-bit, 128-bit, 256 bit and so on. However, the secure hash …
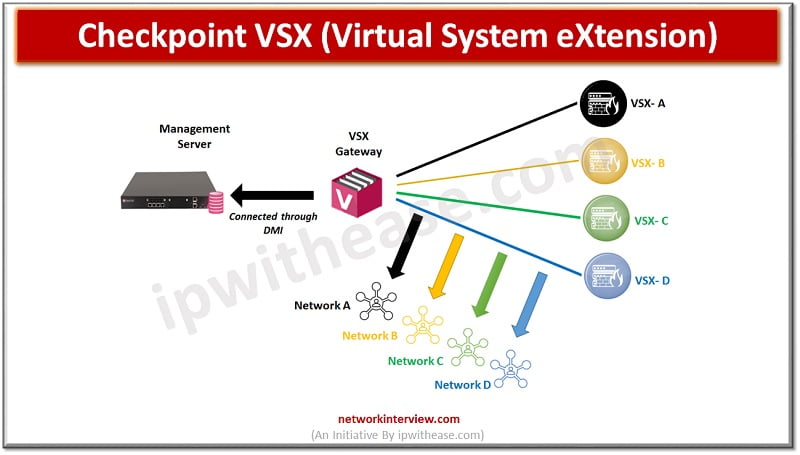
What is Checkpoint VSX? Checkpoint VSX full form is Virtual System eXtension (VSX), a product that runs multiple virtual firewalls in the same hardware firewall. You can purchase hardware appliances with Licence of Virtual firewall. Using one hardware you will …
Are you worried about losing important data due to a lost partition on your Mac? If you experience sudden deletion or loss of memorable photos, videos, or important documents, don’t freak out. There are several Mac data recovery methods available …
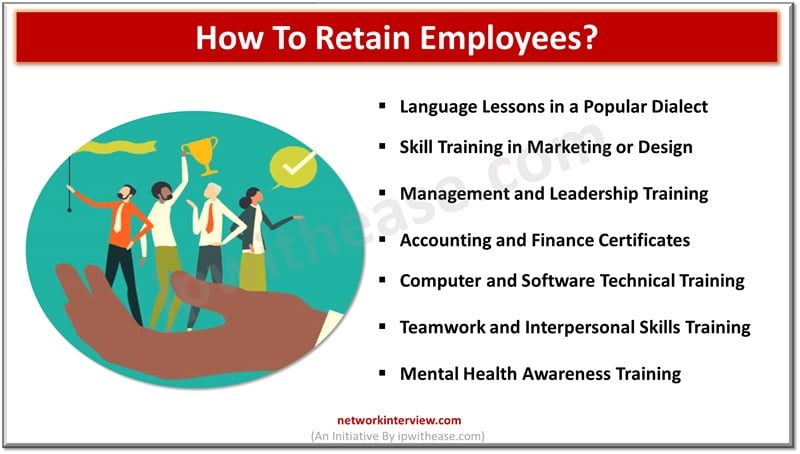
In a business landscape marked by rapidly evolving skill sets, how is your company attracting and retaining talent? One key strategy lies within the realm of training and development. Offering robust training not only ensures your team stays ahead of …
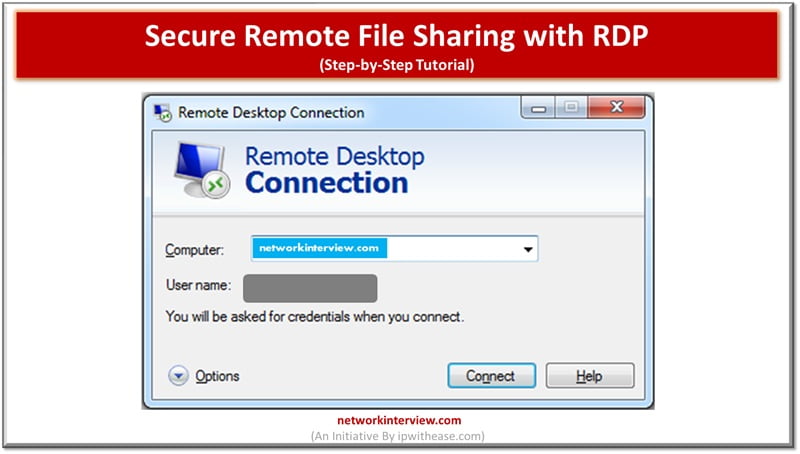
In today’s digital world, remote file sharing has become an essential aspect of business operations. Whether you need to transfer important documents, collaborate on projects, or access files from a remote location, having a secure and efficient method is crucial. …
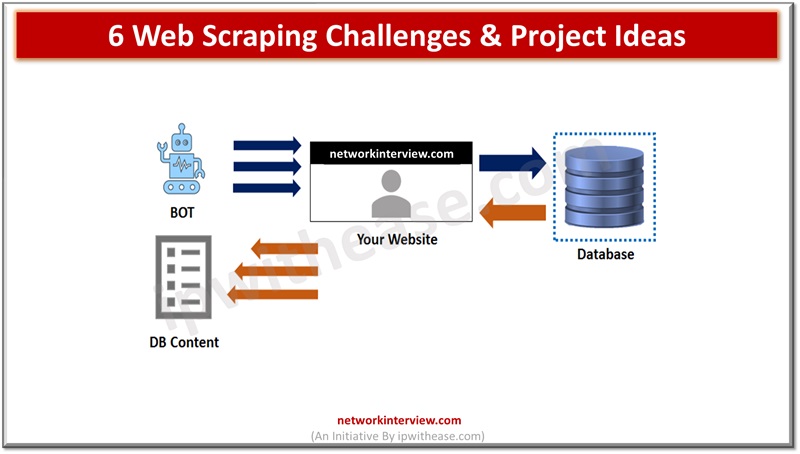
Web scraping is a wonderful way of drawing data down from sites and making it practically applicable for all sorts of purposes. Of course there are hurdles to leap over in this process, and you need an appropriate project to …
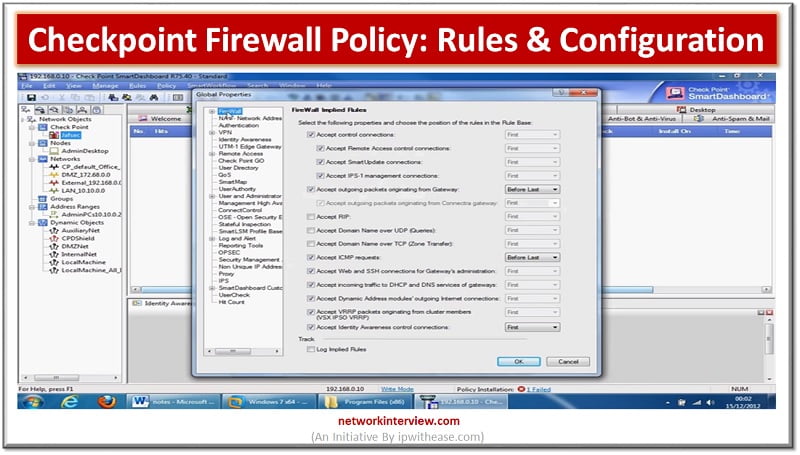
A firewall policy outlines the way an organization’s firewalls should handle the traffic that comes into and out of the specified IP addresses and address ranges, protocols, applications and content types governed by the organization’s security policies. Organizations should carry …
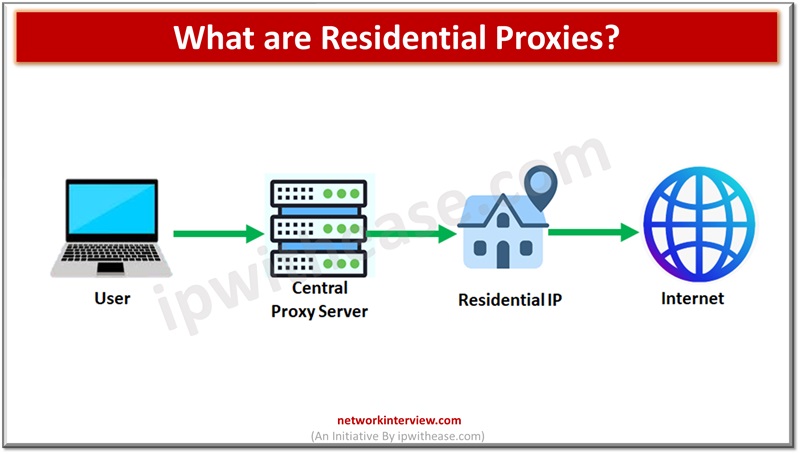
Many active Internet users know about proxies and VPNs, but there is an easier and more flexible way of staying anonymous. Find more information about it right now! What are Residential Proxies? A resident proxy is an intermediate server through …
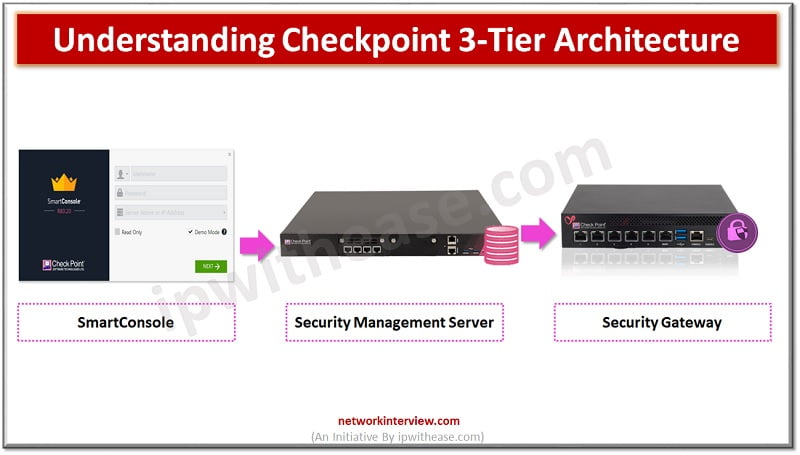
Before starting to explore Checkpoint NGX Firewall technologies, it is critical to comprehend Checkpoint 3-Tier architecture. This architecture describes the relationships between the components of Checkpoint, as well as how they work together as a harmonious unit. Each element has …
In the ever-evolving landscape of project management and product development, agility has become the name of the game. Agile methodologies have gained widespread recognition for their ability to enhance flexibility, improve collaboration, and drive product success. One key role in …
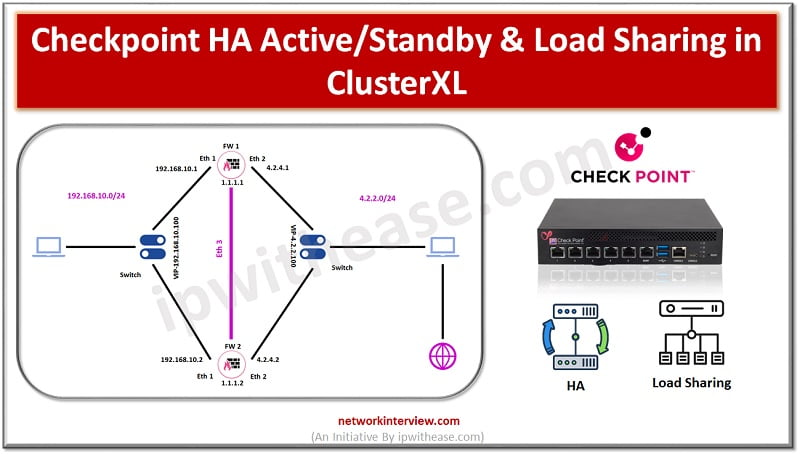
Checkpoint HA High Availability is the feature of firewall in which it eliminates the single point of failure in the network. Two firewalls make a cluster and act as an active passive mode. Active firewall handles the network traffic while …
AI tools were mostly limited to larger enterprises during the early stages of their introduction. However, today, even small businesses have access to a variety of advanced AI resources at an affordable price. As a result, adoption of artificial intelligence …
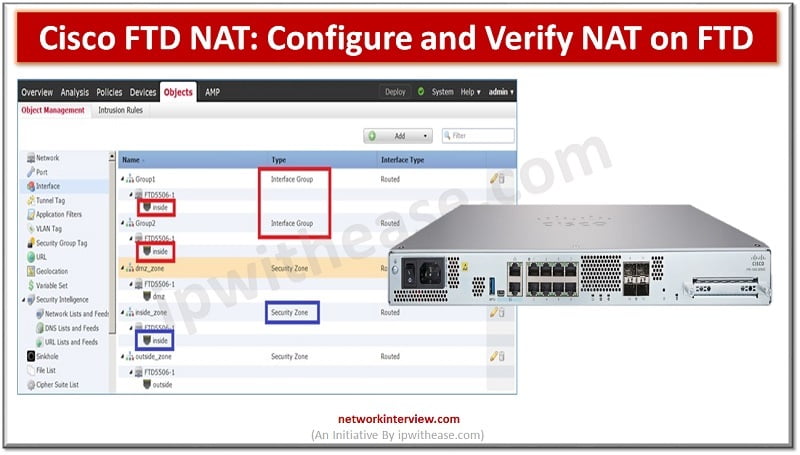
Cisco FTD NAT: Introduction An IP address is the basis of every communication over the network and Internet. Each computer device is assigned an IP address within an IP network which identifies the host as a unique entity. But due …
Online interviews for coding speak a lot about building a successful team from scratch. In any case, it isn’t simple. Why? Because the recruitment process must be really advanced to make sure you’re not enlisting candidates who sparkle within the …
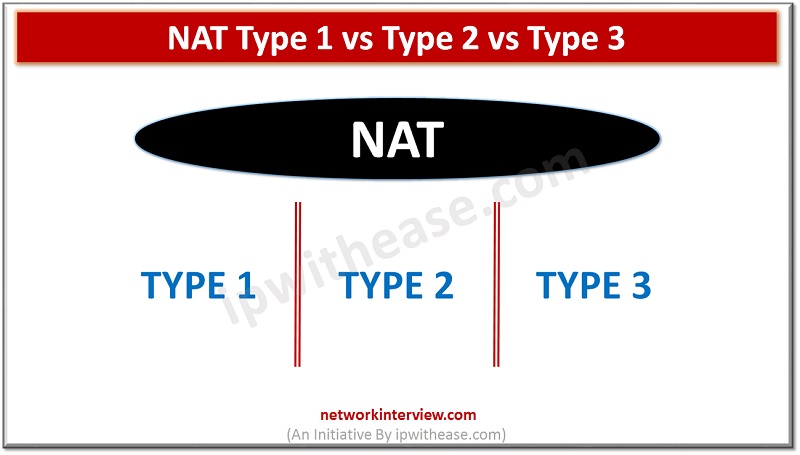
NAT Type 1 vs 2 vs 3 Nowadays, the 2 major gaming console types used extensively around the globe are Sony PlayStation Microsoft Xbox NAT stands for Network Address Translation, which represents the ability to translate a public IP address …
In the dynamic world of data analytics, professionals who hold a Master’s in Data Analytics are in high demand. The USA, renowned for its top-notch education and thriving job market, is an ideal destination for pursuing this advanced degree. In …
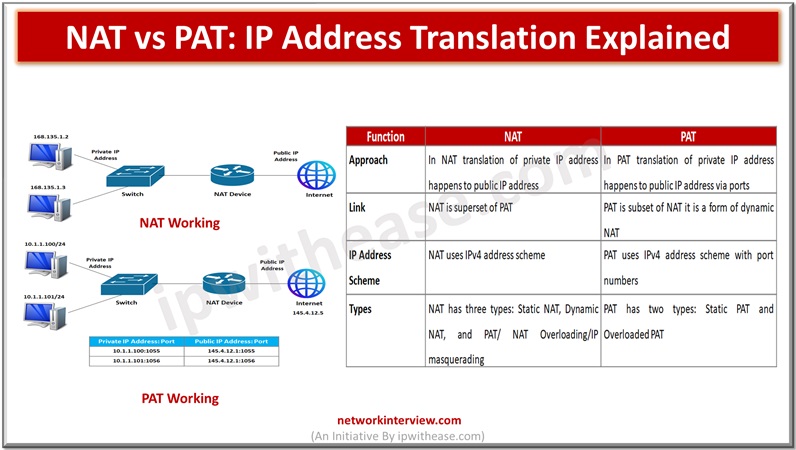
In the networking world IP address translation is required so that internal systems could have access to the external world or Internet. The IPv4 scheme can have a maximum of four billion IPv4 addresses in theory but the actual number …
Security is of paramount concern while using the Internet and its services. Have you ever thought about how secure your data is over the Internet while working? When I am connecting to the Internet, we are taking ISP services so …
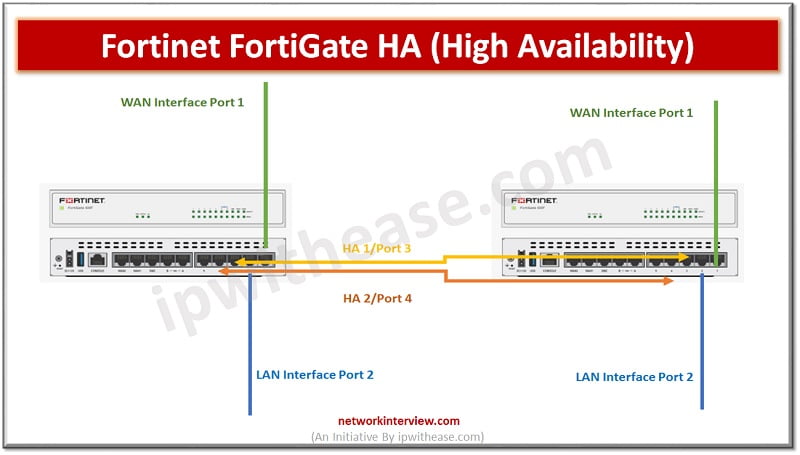
Objectives High Availability HA Modes FGCP (FortiGate Clustering Protocol) Heartbeat Interfaces and Virtual IP Interfaces HA Requirement Configure Primary FortiGate Firewall Configure Secondary FortiGate Firewall HA-Troubleshooting What is High Availability? High Availability (HA) is a feature of Firewalls in which …
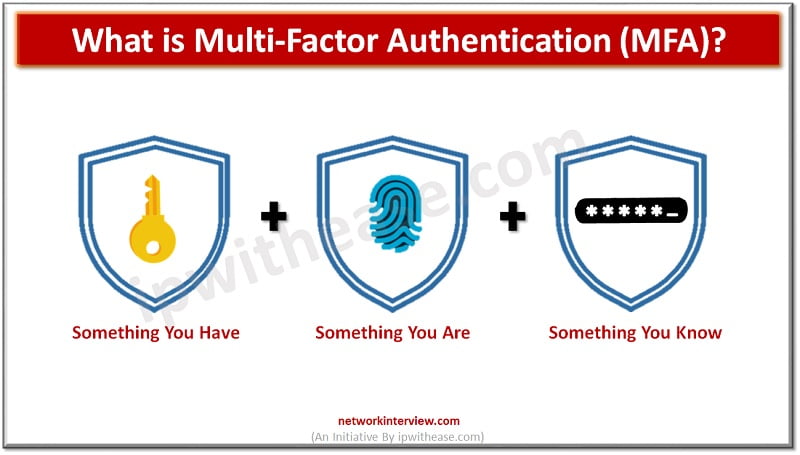
Companies of all sizes are becoming increasingly aware of the need for stronger user authentication to reduce the risk of cyber attacks. This is particularly true in light of recent high-profile attacks on accounts from Internet users such as celebrities, …
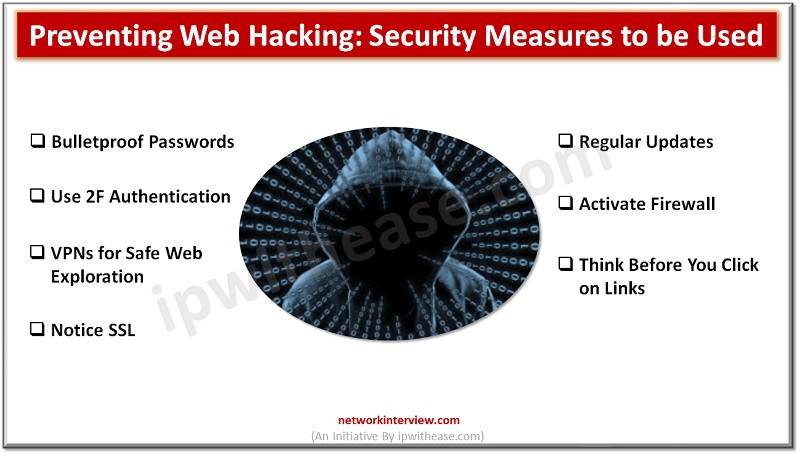
Web hacking is scary. We all know that! Yet, we need to talk about web hacking. The 2021 Cyber Threat Report by SonicWall reveals an alarming 62% increase in ransomware worldwide. Frightening, isn’t it? In this blog post, we’re going …
Network security is of paramount importance for IT administrators. Various ways and means and a variety of tools are used to protect organization networks from internal and external attacks. All communications in a network happens via IP addresses as per …
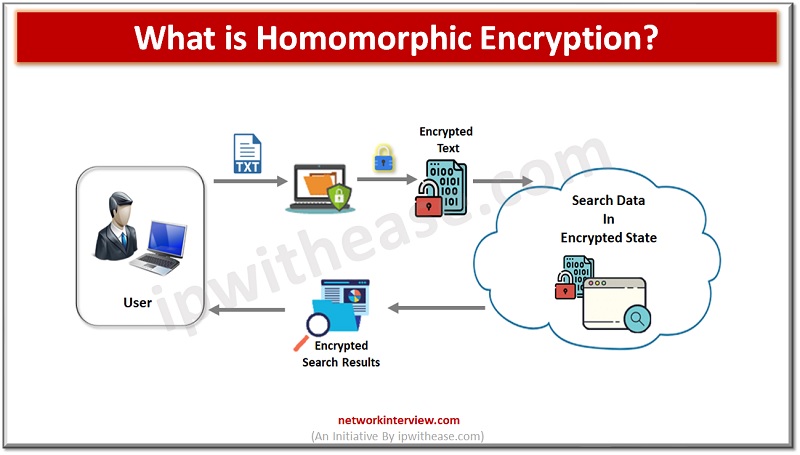
Homomorphic encryption is a powerful and innovative type of encryption that promises to revolutionize the way that data is secured and shared. HE is a relatively new technology and is still in the early stages of research and development. However, …
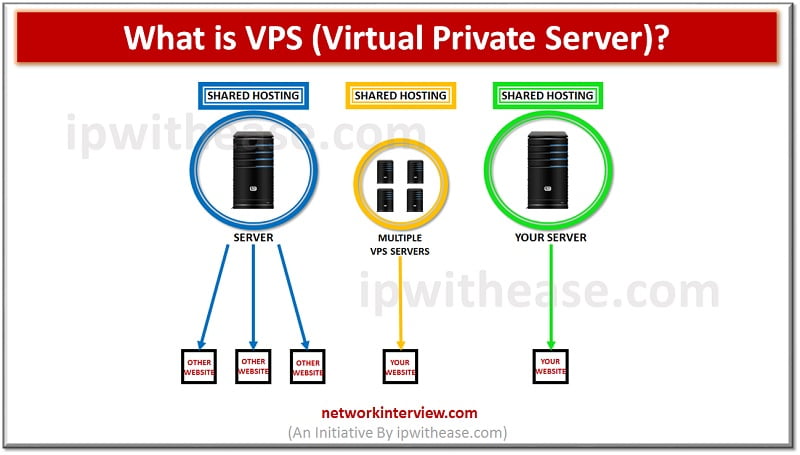
Introduction to VPS (Virtual Private Server) In the IT community, we define with the term VPS (Virtual Private Server), any virtual machine that is sold as a service by an Internet Hosting Service. In normal conditions, a virtual private server …
Are you ready to take your networking career to the next level? The Cisco Certified Network Associate (CCNA) exam is a crucial stepping stone towards achieving that goal. Whether you’re just starting or looking to enhance your skills, passing the …
Well, not always. As VPN is a new concept , so the rules are murky and open to multiple interpretations. Though all good VPN companies will do their best to protect your data, privacy, and overall security on the web, …
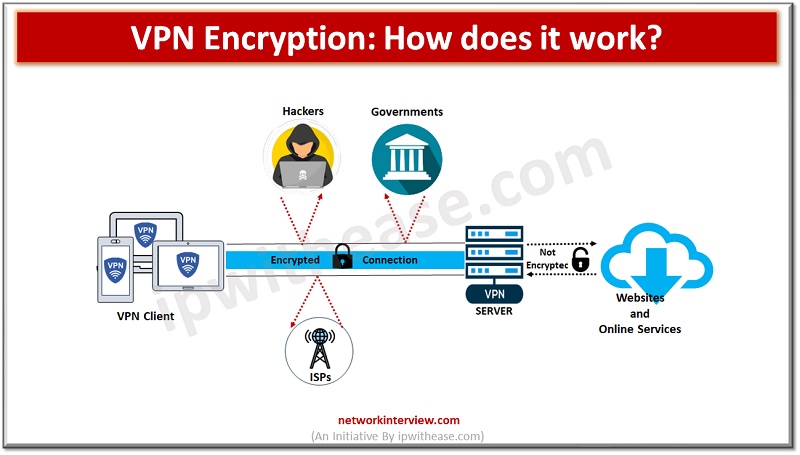
Introduction to ISP & VPN Internet service providers (ISP) facilitates internet navigation and helps in transmitting all your Internet packets however VPN creates a secure tunnel where data is encrypted during transmission. Often people get confused between the two terms …
As the world becomes increasingly digital, the need for efficient, reliable, and cost-effective networking solutions is more critical than ever. One such solution that has gained popularity in recent years is the Virtual Router. In this article, we will learn …
The cybersecurity industry has become increasingly competitive, making it essential for professionals to validate their skills through certifications. Cisco offers a range of CyberOps certifications that are highly sought after by employers. In this article, we will guide you through …
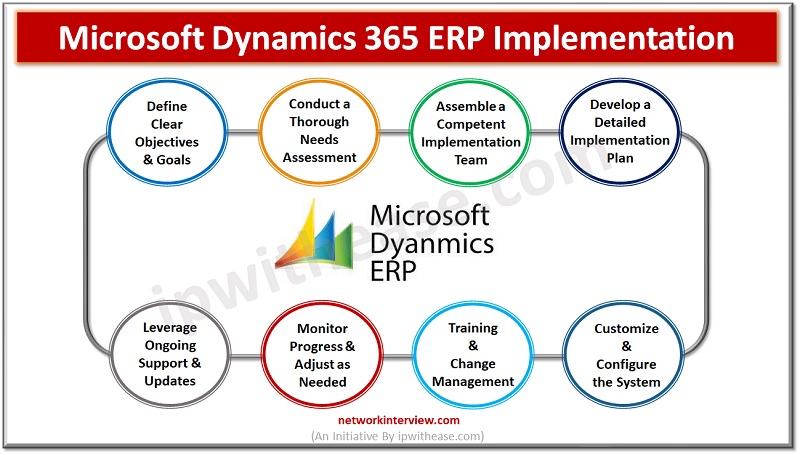
Organizations are continually looking for methods to improve efficiency, simplify processes, and boost profitability in today’s dynamic business world. Microsoft Dynamics 365 ERP, an integrated enterprise resource planning system created to improve many parts of corporate management, is one of …
Dynamic changes have happened in the financial area over ongoing years. IT (Information Technology) services are indispensable to this change’s prosperity. IT services envelop assorted advancements and arrangements and oblige numerous requirements across different businesses. For this situation, monetary establishments …
In today’s internet world a good NAC solution partner is needed for every company involved in the digital or e-commerce industries. In this article, you will get to know the top 10 NAC solutions for your business. Let’s start the …
In today’s world, securing online businesses and safeguarding sensitive data is a top priority for web-based businesses. Network access control (NAC) solutions have become highly useful in achieving this crucial goal. NAC systems act as gatekeepers, controlling who can access …
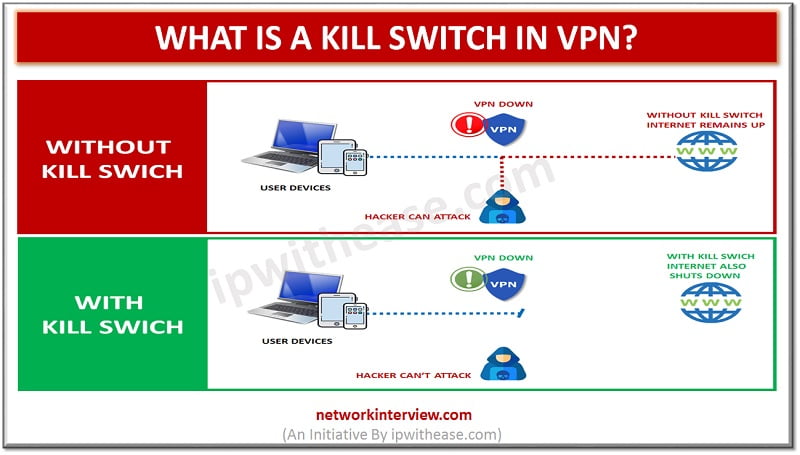
Kill switch in VPN A VPN kill switch is also known as an internet kill switch. For the VPN security solution, a VPN kill switch is a critical piece. It is considered to be the top feature for the best …
VPN (Virtual private Network) has become an essential part of network and security suite when it comes to secured communication over Internet. VPN forms secured tunnels between a local client and a remote server. Remote and mobile workers use VPN …
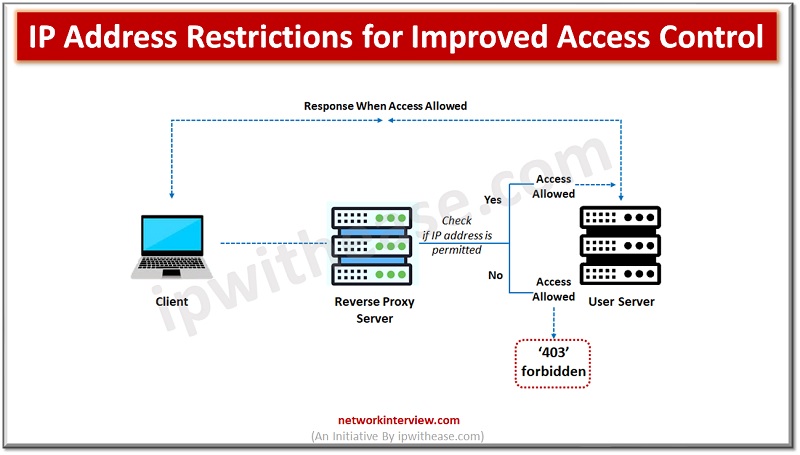
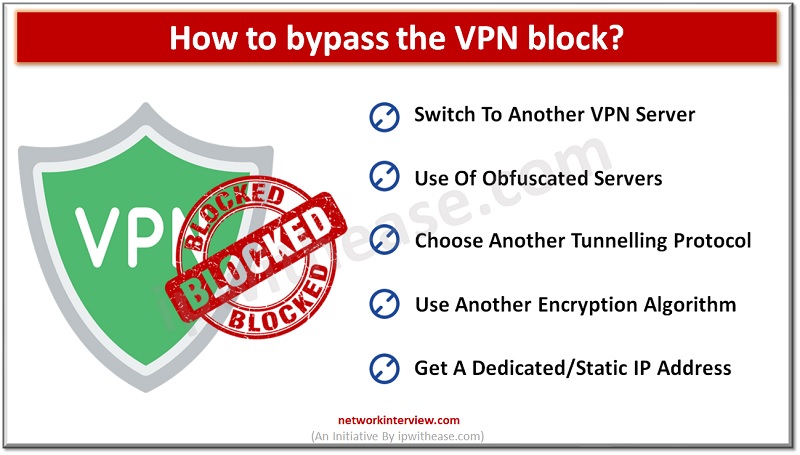
We occasionally run into issues online browsing that prevent us from visiting a website. Our connection, the software we employ, or the device itself may occasionally be at fault. However, the website may be preventing us due to a fault. …
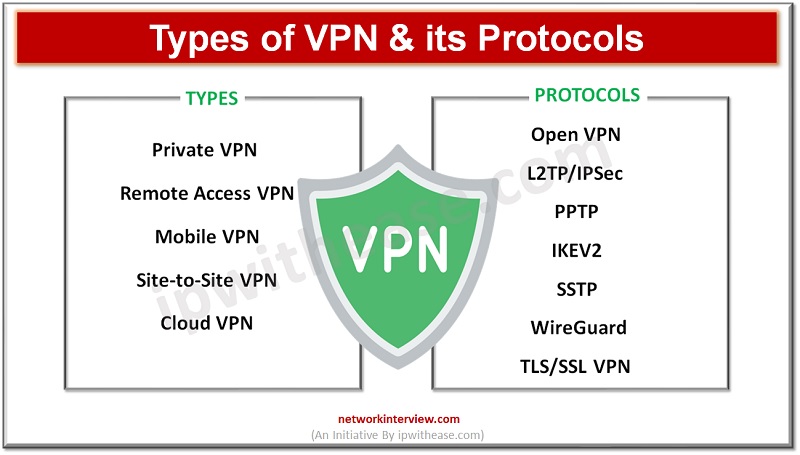
A Virtual Private Network (VPN) is a technology that creates a secure and encrypted connection over the internet, allowing users to access the internet as if they were connected to a private network. VPNs are used for several purposes, primarily …
Adapting to the evolving digital landscape is essential for businesses of all sizes. Today, every business is striving to establish a strong online presence. And as today’s customers demand more, businesses can no longer ignore the significance of digitalization. This …
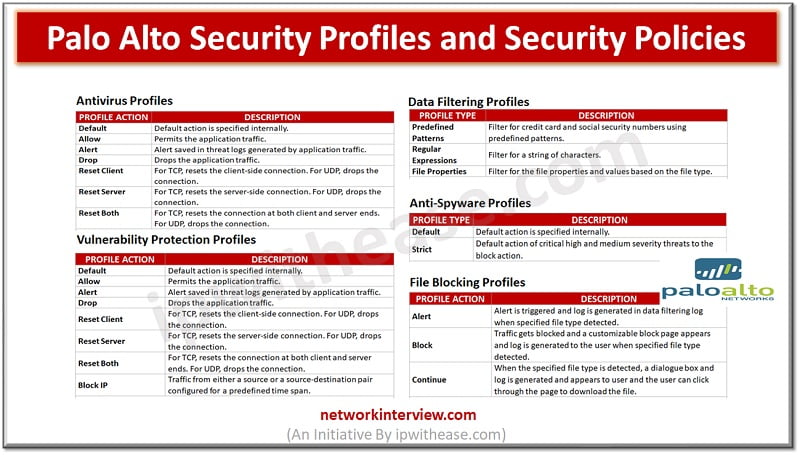
Below are the key profile types provisioned in Palo Alto Firewall. Lets discus all the profile types one by one – Palo Alto Security Profiles & Security Policies While security policy rules enable to allow or block traffic in network, …
In the digital age, email remains a cornerstone of communication. However, the traditional email experience is undergoing a metamorphosis, thanks to the infusion of Artificial Intelligence (AI). Let’s explore this transformative journey. The Email of Yesteryears Historically, email platforms were …
In today’s digital age, online learning has become an integral part of education at all levels. It’s no surprise that businesses are also embracing this technology to enhance their training and professional development programs. One tool that has gained popularity …