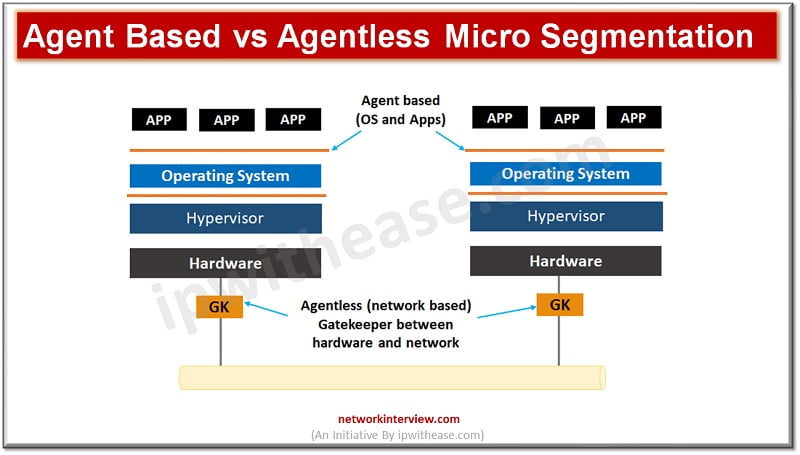
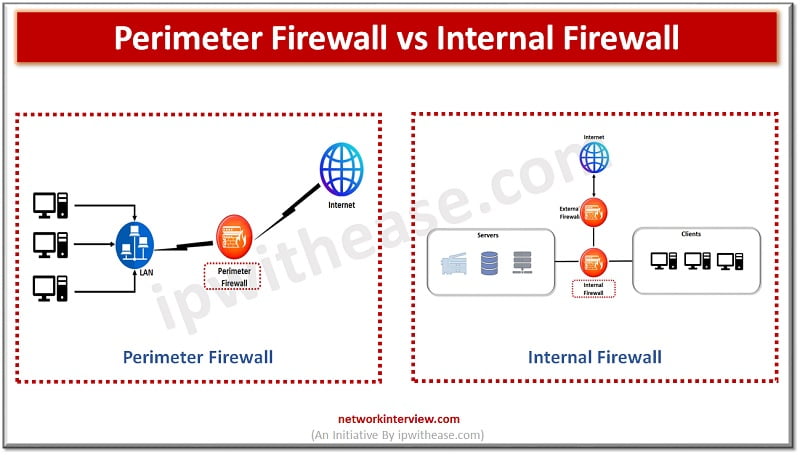
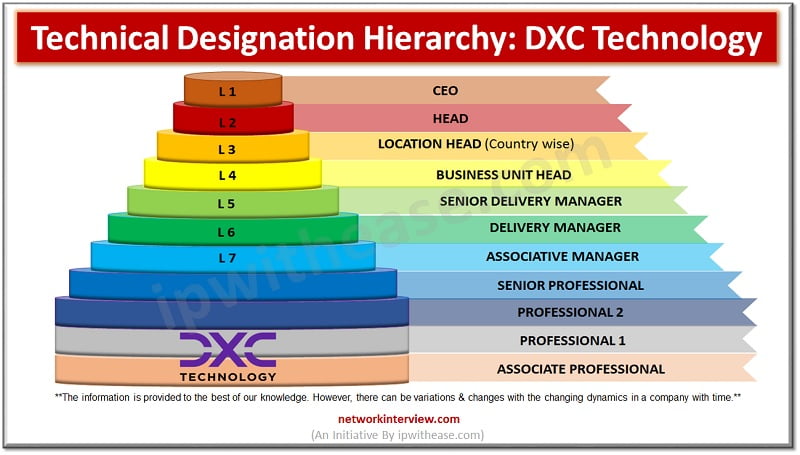
Granular level management of access and security controls is the focus of security techniques deployed nowadays as attacks have become more and more sophisticated so is the dynamics of protection also getting changed frequently. Virtually restricted access to any device …
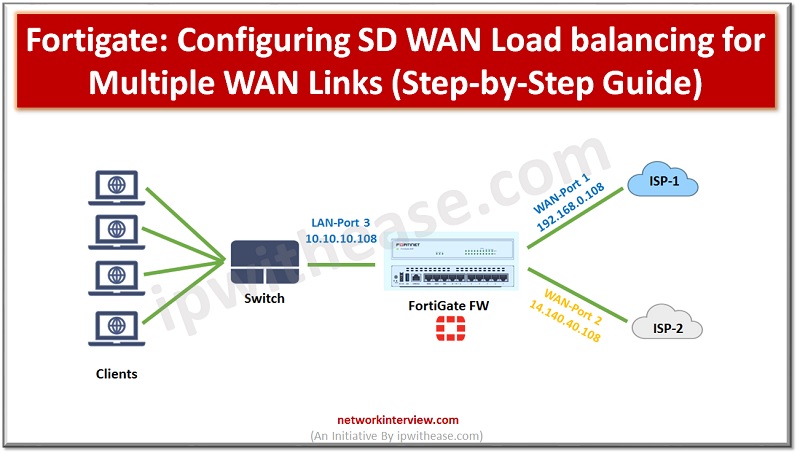
Configuring SD WAN Load balancing Below is the network setup on which we will configure FortiGate SD-WAN with load balancing for two different ISPs. Parameters which we have taken are LAN Port & Segment -> LAN Port 3 & 10.10.10.108 WAN …
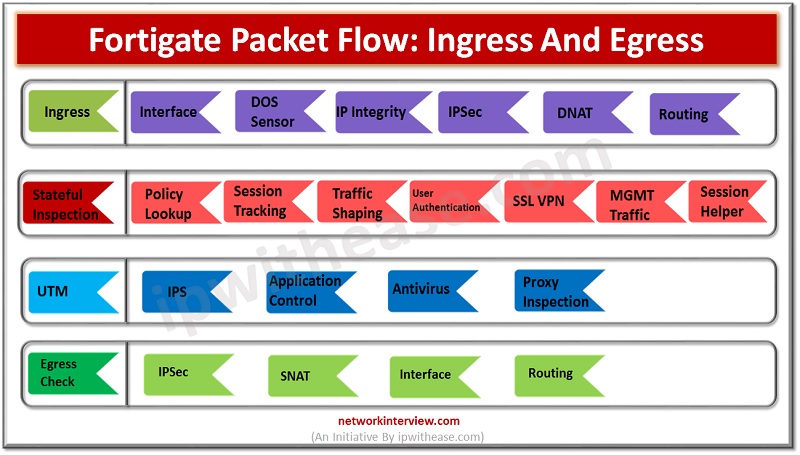
FortiGate packet flow is also known as Life of a Packet. This is the process when the packet enters the Ingress interface and exits from the Egress interface. Stages of FortiGate Packet Flow FortiGate packet flow consist of 4 stages …
Firewalls have come a long way since their inception in the year 1908s. The initial firewall was built by Digital Equipment Corporation (DEC) as a packet filtering firewall which simply inspected packet traffic and if it doesn’t match rules packet …
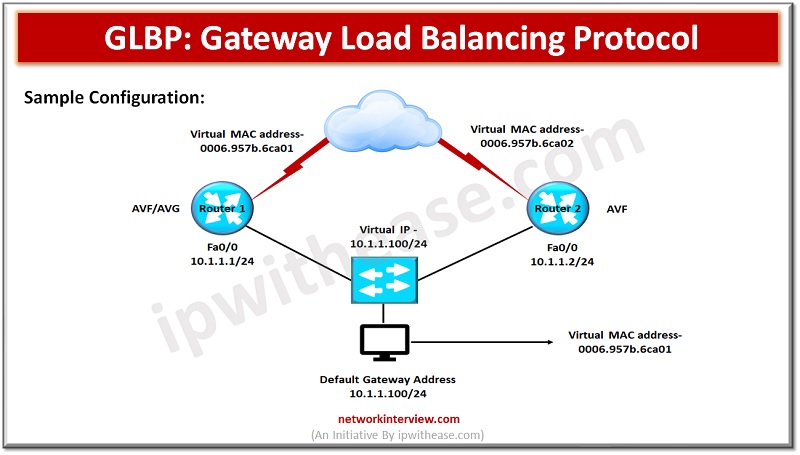
Introduction to Gateway Load Balancing Protocol Load balancing is one of the key requirements in networks and it can be achieved in several ways such as round robin, host dependent and weighted. Protocols supporting load balancing have the capability to …
Objectives Routing in Fortinet FortiGate Configuration Steps of Static Routing Configuration Steps of Dynamic Routing (BGP) Policy Base Routing Routing Monitor GUI Troubleshooting Commands for Routing in FortiGate Routing in Fortinet FortiGate Firewall Routing means how a packet can …
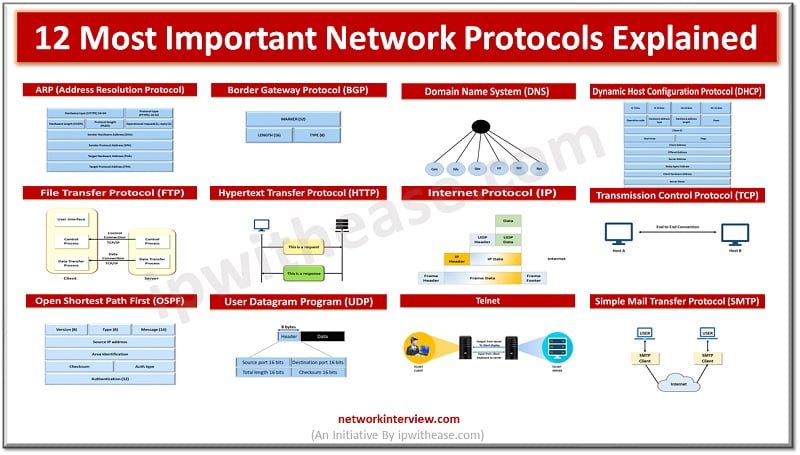
Network protocols establish rules of communication to control and govern exchange of information following secure, reliable methods. These are a set of rules designed to have a standard framework for interchange over networks. There are a variety of network protocols …
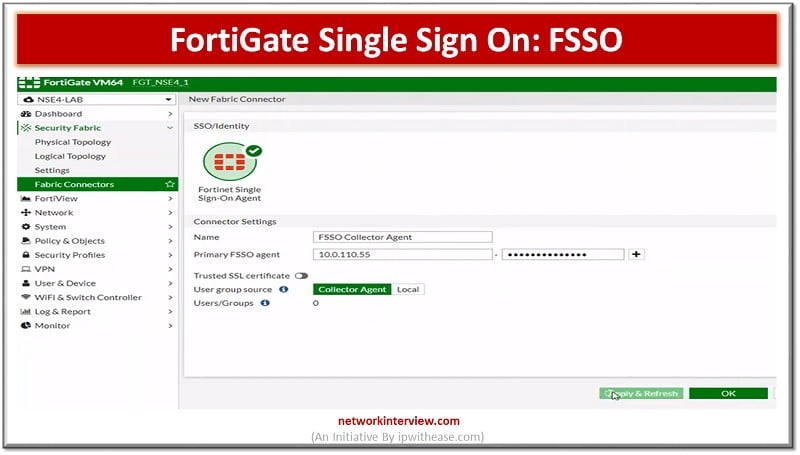
Single Sign On & FortiGate Single Sign On Single Sign On (SSO) is a process that allows users to automatically log into every application after being identified, regardless of platform, technology, and domain. FortiGate Single Sign On (FSSO) is a …
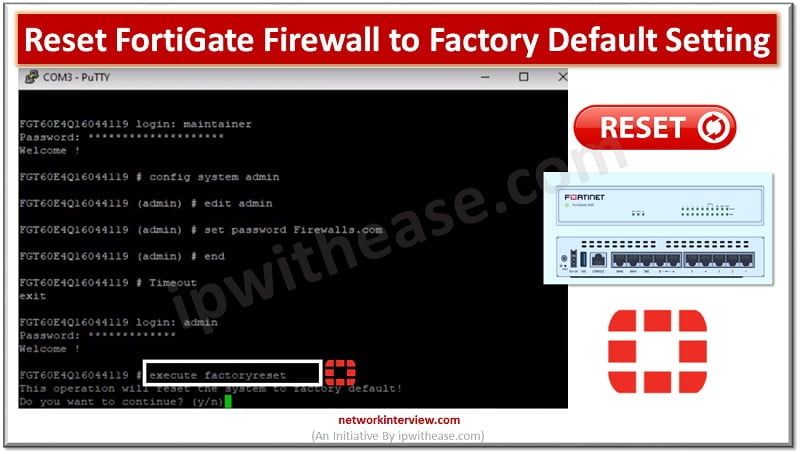
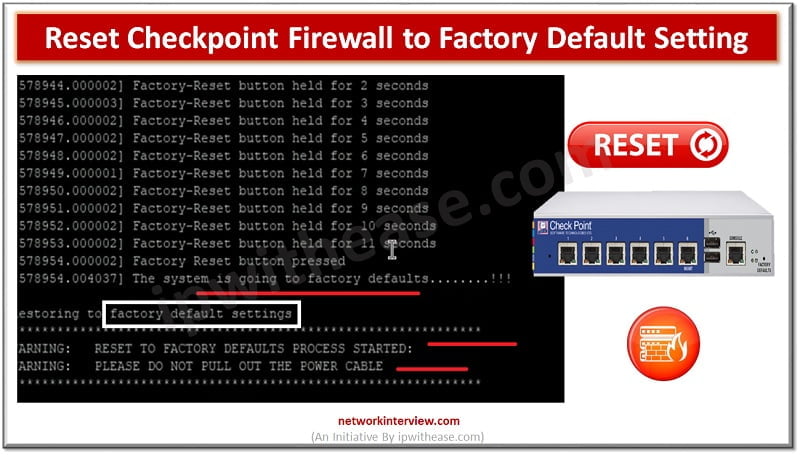
Factory default means resetting the device to the original default configuration and deleting all customized configuration from the firewall/device. Why do we need to reset the firewall to factory default? Device is crashed and need to remove from network Remove …
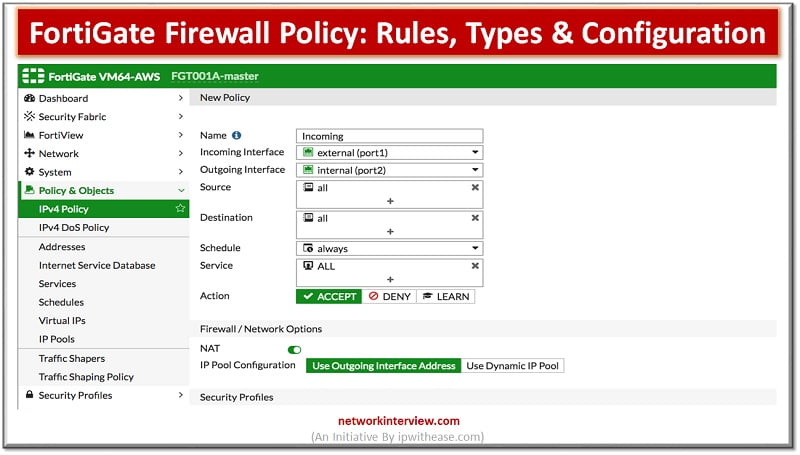
What Are Firewall Policies? Firewall policies define which traffic matches them and what FortiGate does when traffic does match, should the traffic be allowed? Initially FortiGate basis this decision on simple criteria, such as the source of the traffic then …
The CSPO (Certified Scrum Product Owner) certification is considered prestigious for individuals aiming to succeed in Agile product management. With the increasing popularity of Agile methodologies in various industries, obtaining a CSPO certification can unlock various career prospects and showcase …
Artificial Intelligence and Machine Learning are two emerging concepts which are playing a very crucial role since the Covid pandemic hit us. Both technologies are being used to study the new virus, test potential medical treatments, analyse impact on public …
Firewalls are the primary line of defense for organizations; they are there for more than three decades but evolved and came a long way with drastic features and also sold now as separate appliances and make smarter decisions about what …
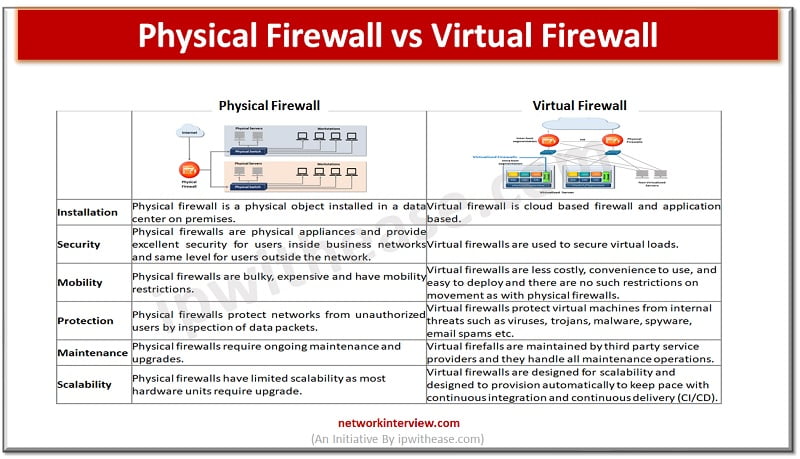
Firewalls are the first line of defense for an organization’s networks. Firewalls come in different categories – they can be a hardware appliance, software based or virtual. The increasing penetration of cloud computing infrastructures has given rise to virtual firewalls. …
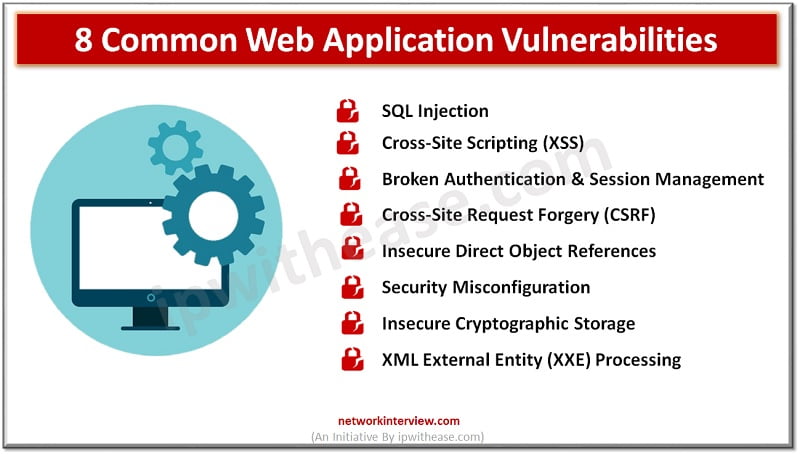
Introduction to Web Application Vulnerabilities Web application vulnerabilities are glitches or imperfections found in the system. These can lead to security risks, such as cyber-attacks or data breaches. Sadly, these risks occur more often than network or asset dangers. According …
Understanding each Encryption Technique When we dive in-depth to explore more about wireless key management and encryption technologies, then we would find that network protocols play an imperative part in it. As we are dealing with the technologies that are …
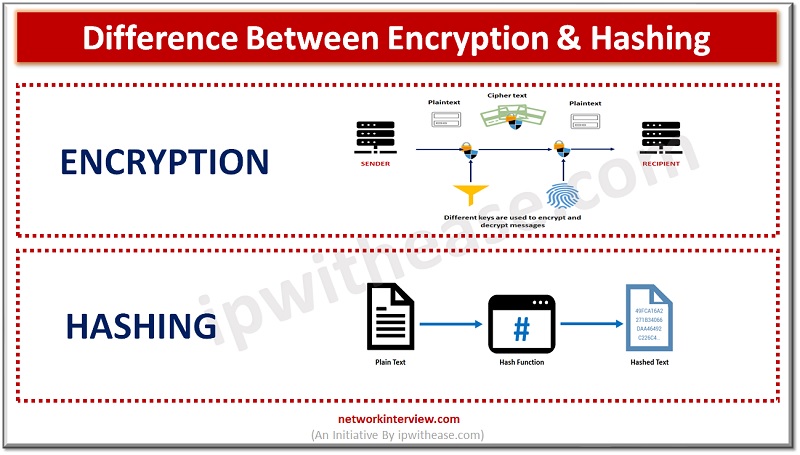
In the realm of data security, hashing and encryption are commonly employed to protect information from unauthorized access. While both methods have distinct processes and advantages, they are occasionally mistakenly used interchangeably. This blog will delve into the definitions of …
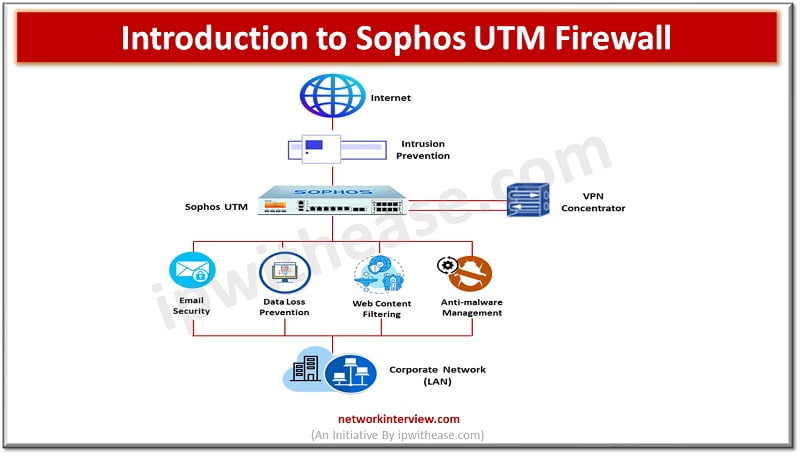
UTM (Unified Threat Management) solution deployed at the gateway level and scans all the malicious and suspicious traffic which passes through the network. UTM has multiple parameters such as URL Filtering Application Control Intrusion Prevention System Antivirus & Anti-Bot Data …
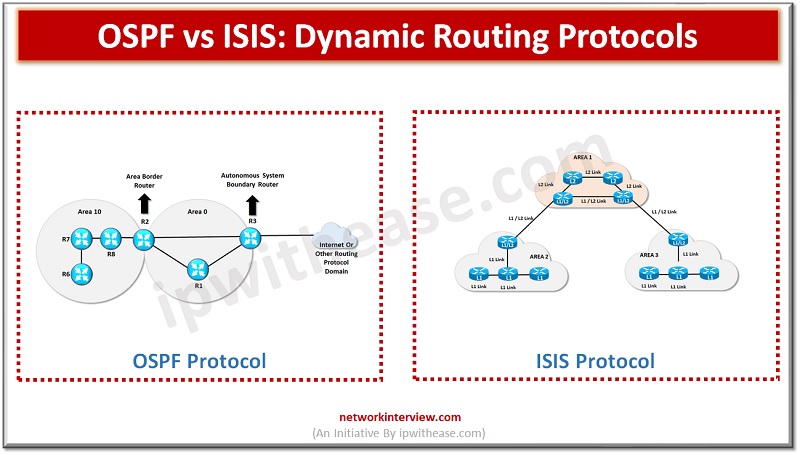
Computer communication networks are growing at a rapid pace, they are based on technology which provides the technical infrastructure, whereas routing protocols are used for transmission of data packets across the Internet. Routing protocols specify how routers communicate with each …
In recent times, the worldwide cyber security scenario has witnessed a surge in potential risks. With the onset of the pandemic, cyber offenders exploited the vulnerability of poorly aligned networks when companies transitioned to remote working setups. The cyber attack …
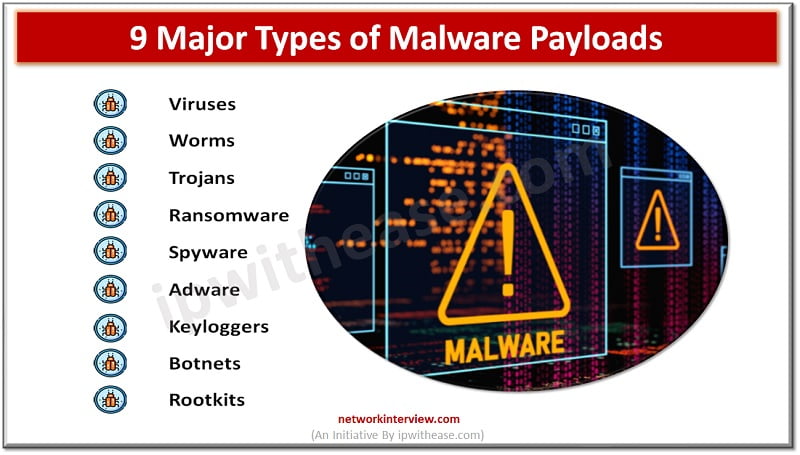
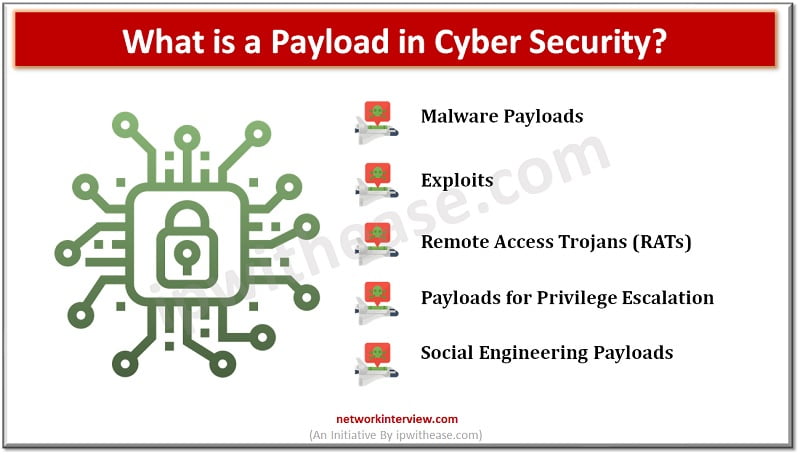
As a cybersecurity professional, you will come across many technical terms and jargon in the field. One of the terms that we often hear in cybersecurity is “payload.” In simple terms, a payload refers to the part of a malicious …
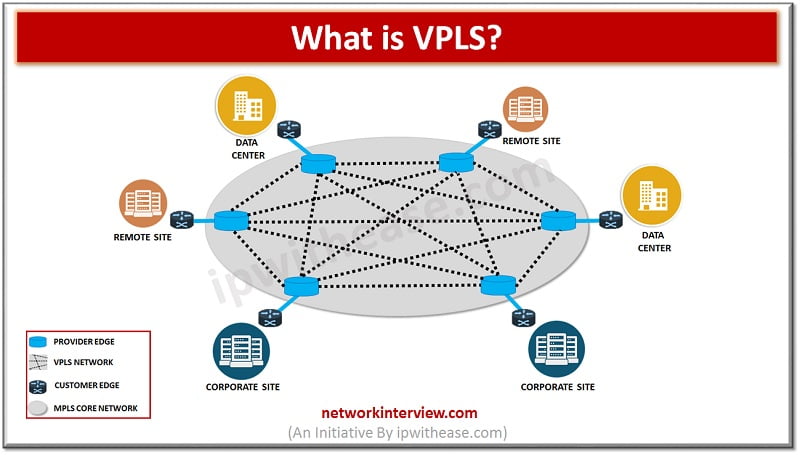
Introduction to VPLS As we have already discussed MPLS in detail in our previous article, so here I will focus on VPLS first and then the differences between the two. VPLS i.e. Virtual Private LAN Service. It is a service that …
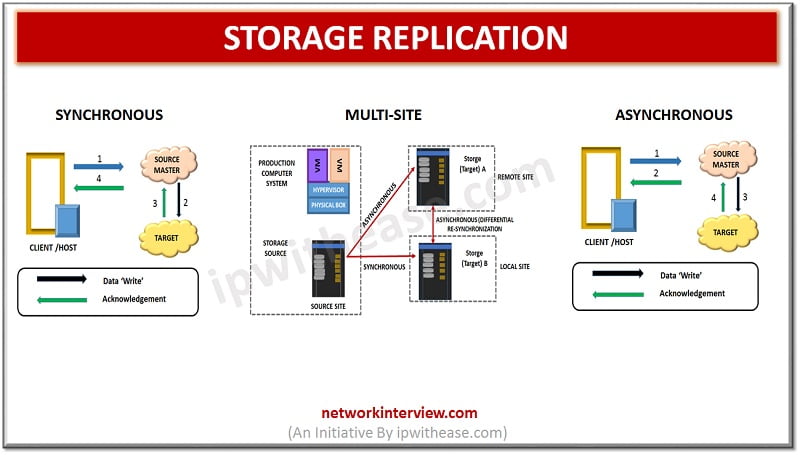
Storage replication – Sneak Preview Continuous data protection with zero downtime, higher availability and speed requirements govern the business requirements in the current arena. The purpose of replication is protection from disaster which may occur at one location and operations …
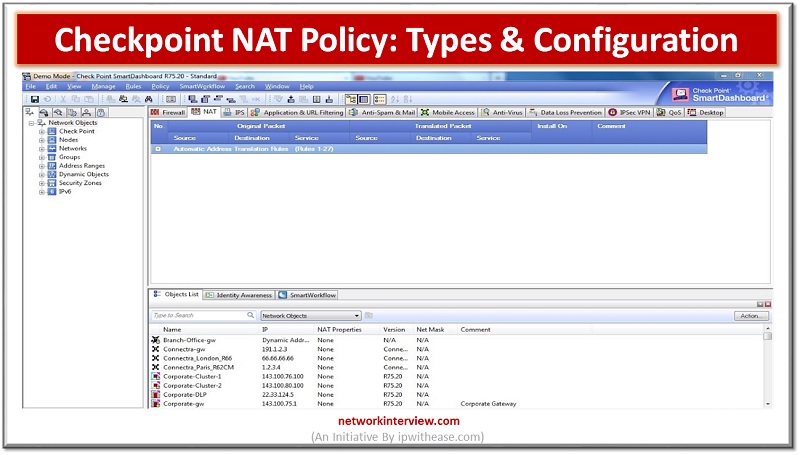
What is NAT (Network Address Translation)? Many firewalls include network address translation, a procedure that translates between internal and external IP addresses. NAT enables a private network to use non-routable internal IP addresses that are mapped to one or more …
Are you in your final year of pursuing a Software Engineering Degree? Do you want to join a new company from your present? Then there are many things you should consider before making the decision. One of them is the …
Let’s understand the difference between “Reset” and “Factory-Reset”. Reset – Admin can only wipe-out the configuration Factory-Reset/Default – Admin can wipe out the configuration of device and put the device in default operation/firmware. For Example, when you buy a Firewall, …
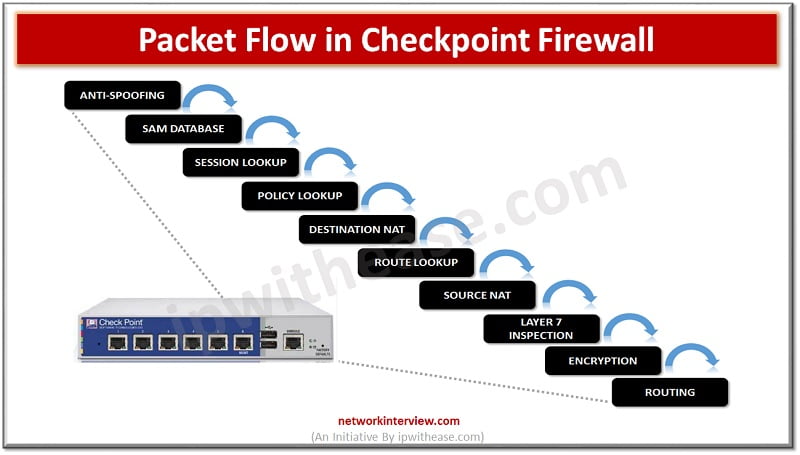
Checkpoint Firewall Packet Flow In the above image Checkpoint Firewall packet flow is shown. Let’s start with Anti-spoofing. Anti-Spoofing Anti-spoofing is a technique which can identify the packet and drop it if the packet has a FAKE/False source address. Let’s …
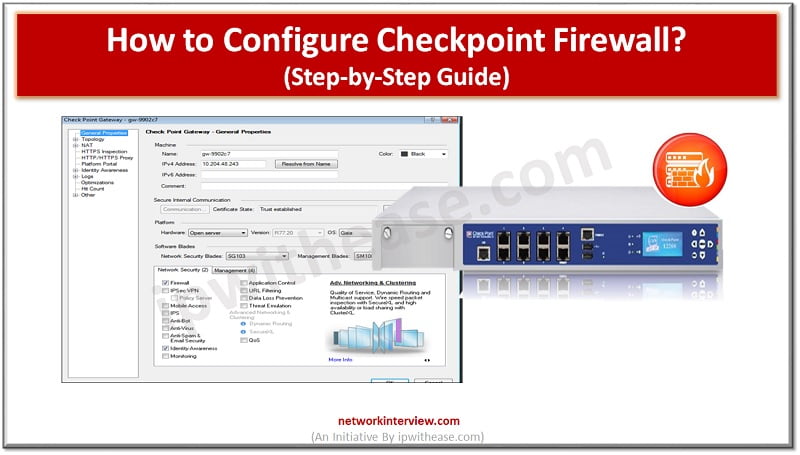
Prerequisites to Configure Checkpoint Firewall Sometimes in the network we need to install a new Checkpoint Firewall from scratch which requires a few prerequisite as follows: Console Cable Physical access to device (arrange any local site Engineer) Bootable USB Stick …
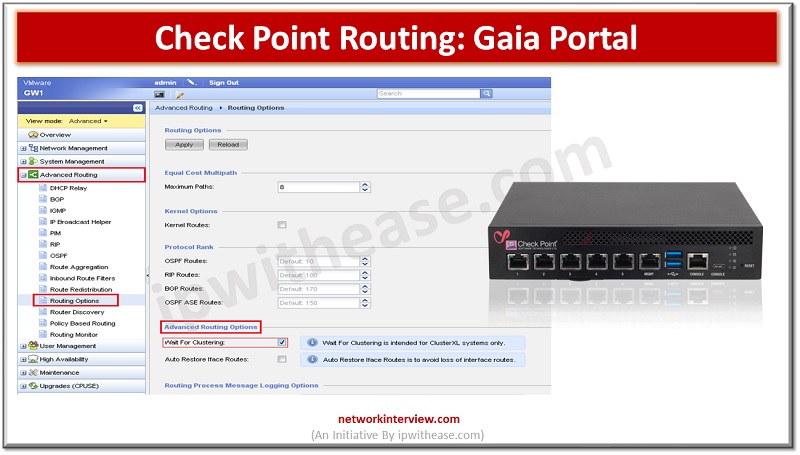
Gaia is the latest operating system for security applications developed by Check Point. It is named after Gaia, the mother of all in Greek mythology, symbolizing a well-integrated system comprising various components to ensure optimal performance. Gaia OS is designed …
Firewalls have come a long way and have been there for decades to provide protection against malicious attacks and intrusions. In their infancy days firewalls were a simple filtering mechanism based on ports and IP addresses. But over time, firewalls …
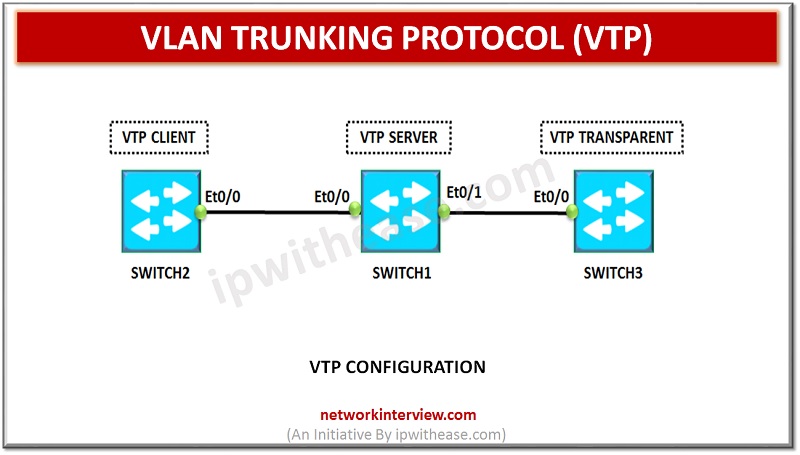
VLAN Trunking Protocol VLAN Trunking Protocol is used by Cisco switches to exchange VLAN information. In VTP, synchronization of VLAN information, such as VLAN ID or VLAN name can be done with switches inside the same VTP domain. VTP domain is …
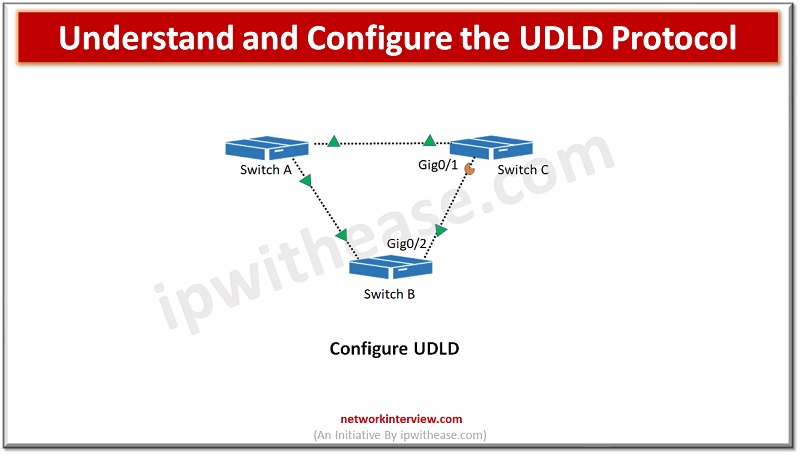
Switches are used to connect hosts on networks. Switch forwards data packets between devices using packet switching technique. Any mis-wiring or hardware faults could lead to disruption in network communication path and create serious network issues such as spanning tree …
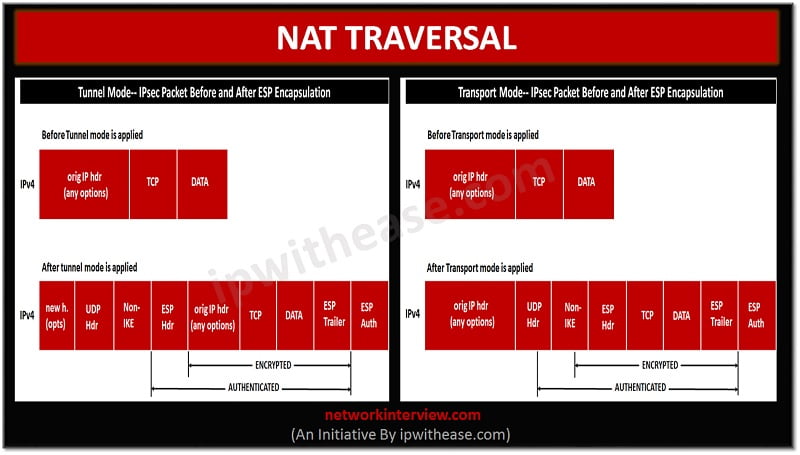
Overview The IPSEC NAT Traversal feature introduces IPSEC traffic to travel through Network Address Translation (NAT) or Port Address Translation (PAT) device in the network by addressing many incompatibilities between NAT and IPSEC. NAT Traversal is a UDP encapsulation which …
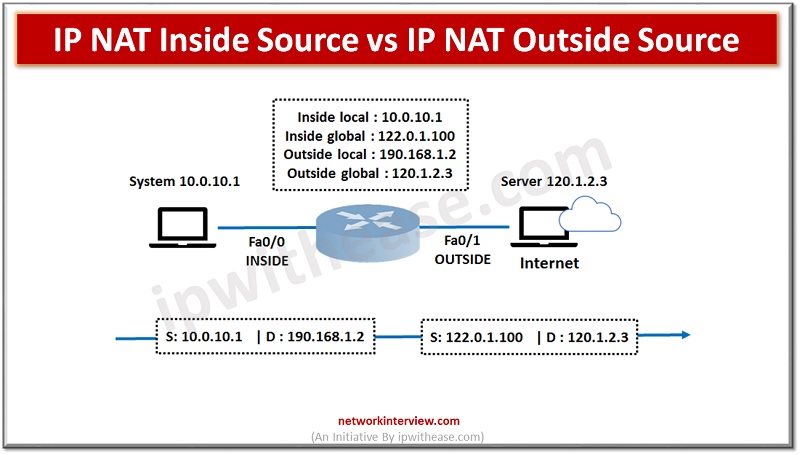
In order to access the Internet, we need one public IP address; however, we can use Private IP address in private networks. The Network address translation (NAT) allows multiple devices to access the Internet with a single public IP address. …
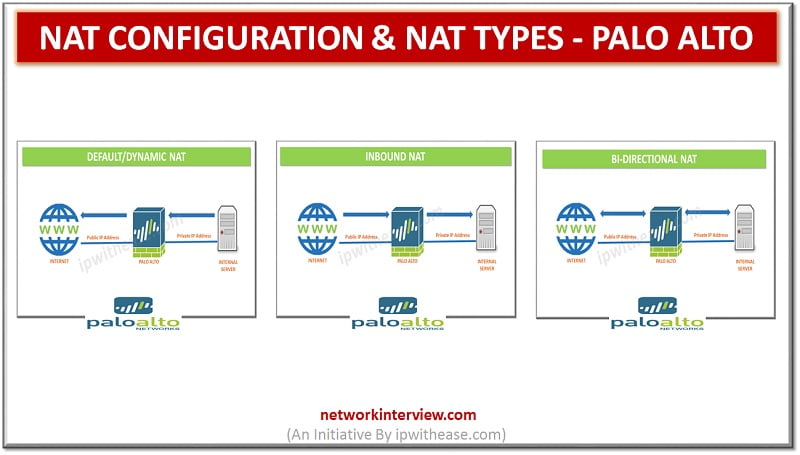
In the previous post we discussed the Architecture of Palo alto firewall. Now, we will discuss the NAT configuration and NAT types in Palo alto. Network Address Translation (NAT) allows to translate private, non-routable IP addresses to one or more …
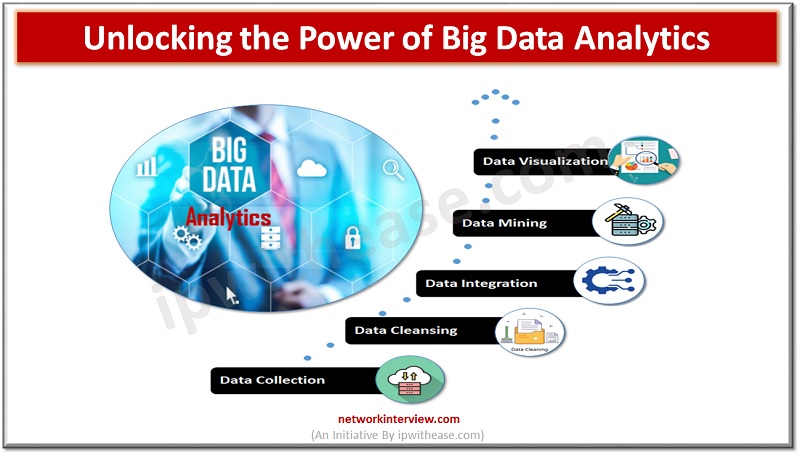
Big data analytics is the process of analyzing large and complex sets of data to uncover patterns and trends. As the amount of data continues to grow at an exponential rate, the need for big data analytics is becoming increasingly …
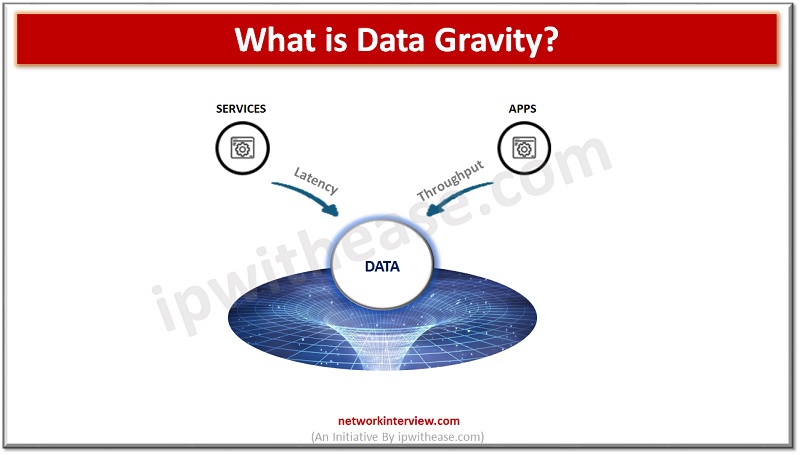
Data gravity is an increasingly important concept in the age of digital transformation, and understanding how it works, its benefits, and challenges is essential for all businesses. In this article, we’ll unpack the concept of data gravity and provide a …
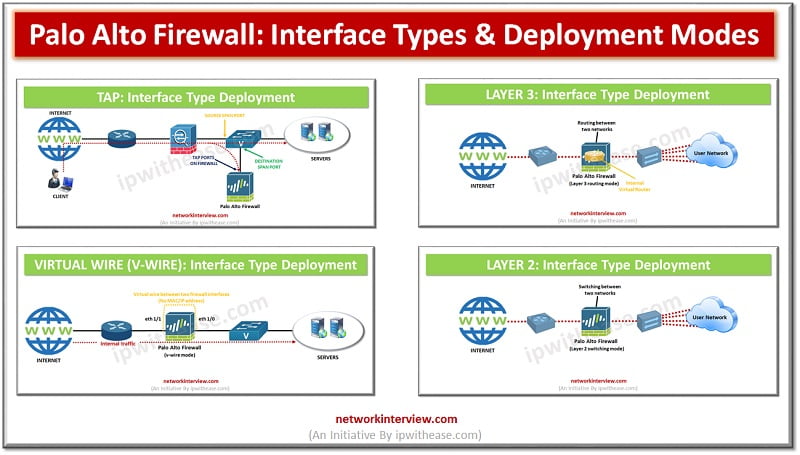
Introduction to Palo Alto Interface types/ Deployment Modes The entry and exit point of traffic in a firewall is enabled by the interface configurations of data ports. Palo Alto being a next-generation firewall, can operate in multiple deployments simultaneously as …
When it comes to software testing, there are two main approaches – manual testing and automated testing. Each one has its own advantages and disadvantages, and it can be difficult to decide which approach is best for your needs. In …
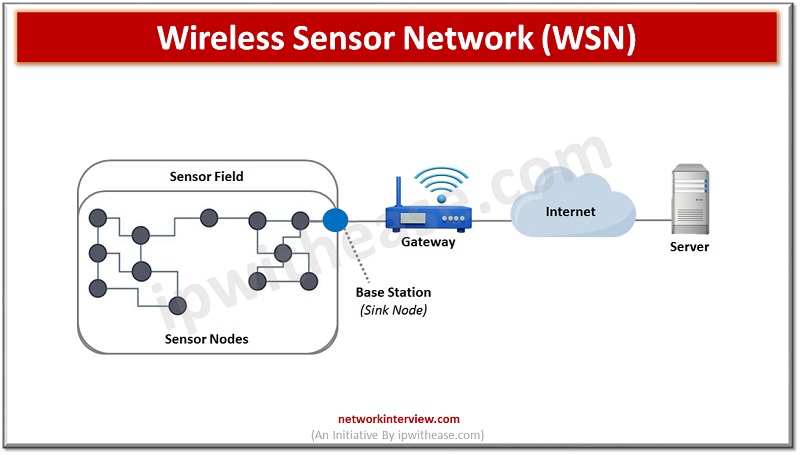
Wireless sensor networks (WSNs) have been around for decades, and their importance has only grown over time. WSNs are used for monitoring, gathering and transmitting data from various sources, such as temperature, humidity, air quality and more. They are also …
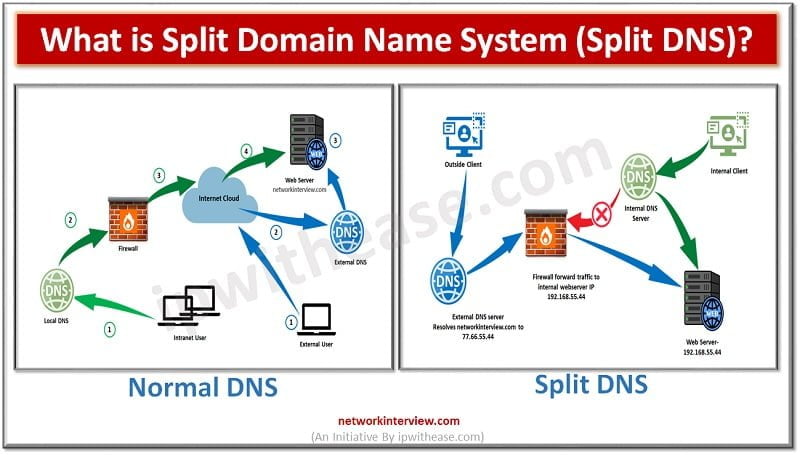
DNS Working Before understanding the Split Domain Name System, let’s discuss how normal DNS resolution works for Internet traffic. However, DNS works to resolve names to IPs. When an Internet client open a Web-browser and type www.networkinterview.com Internet Client will …
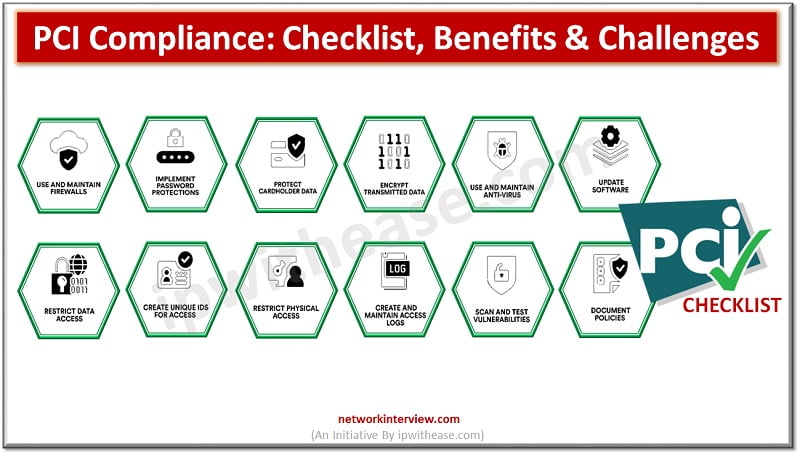
Whether you own a small business or manage a large enterprise, ensuring customer data security is a top priority. To that end, businesses must adhere to the Payment Card Industry Data Security Standard (PCI DSS), a set of security requirements …
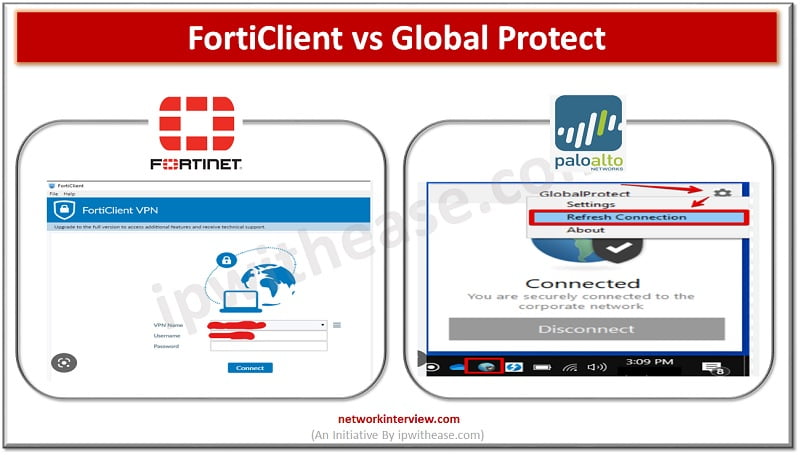
What is FortiClient? FortiClient is an app to provides UTM features like web filtering, giving web security and content-based filtering. FortiClient app is installed in the user’s system and tracks the traffic based on policy. The web application firewall offers malware …
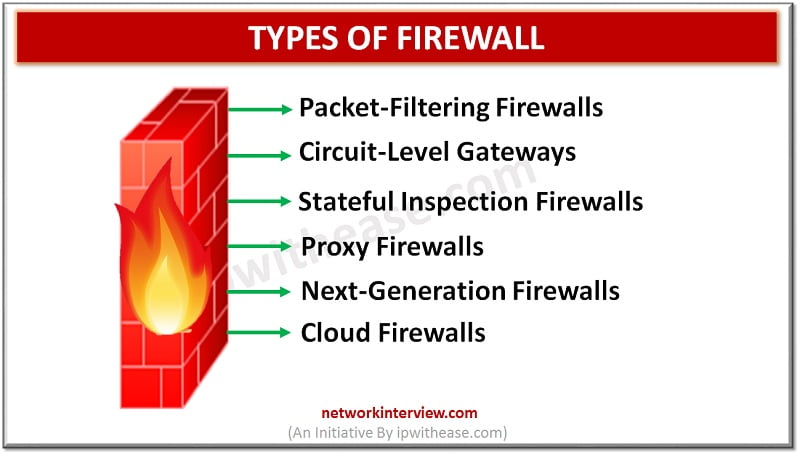
Introduction to Firewall In todays digital scenario, where businesses demand agility and information are hosted on cloud infrastructure security of data is one of the primary concerns of business and protection of data from unwanted sources is the prime objective. …
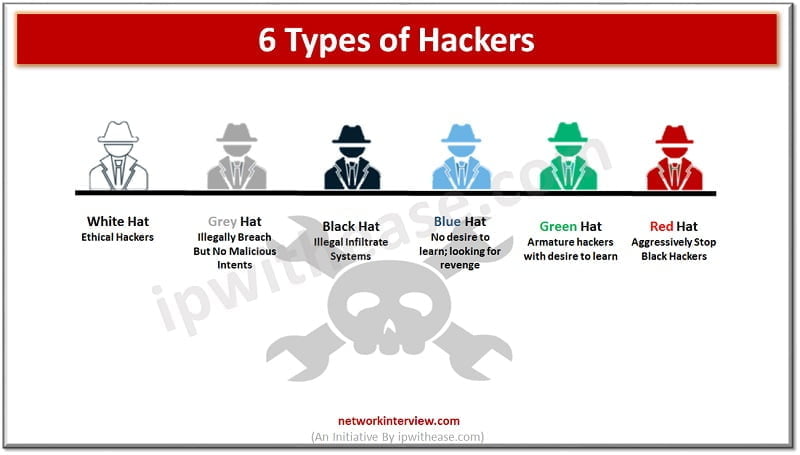
You must have heard the word ‘hacker’ multiple times in cybersecurity. The organizations have trained security staff to take care of cybersecurity threats. Hacking is generally referred to as someone gaining access to your network and systems by unauthorized means. …