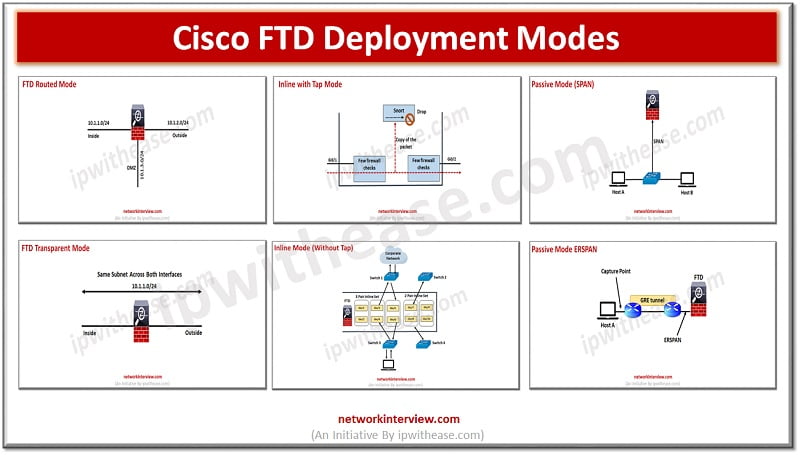
(FTD Deployment Modes: Routed, Transparent, Inline, Inline with tap, Passive SPAN, Passive ERSPAN) Cisco FTD design and deployment implementation involves setting up firewall, SSL inspection, NAT, IPS and active/standby HA. Deployment model determines placement of FirePower into the network as …
Digital marketing can be incredibly complex these days. Many different campaigns, tools, processes, and types of data are used in digital marketing, which can make it feel overwhelming and overly complex. You should know that there are a few steps …
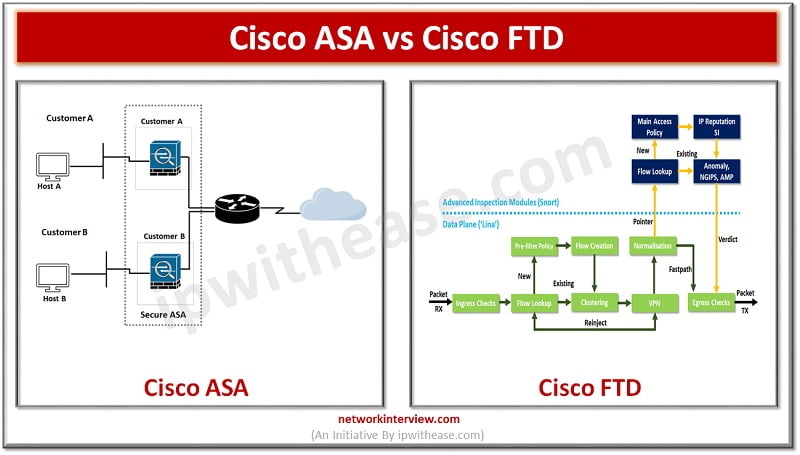
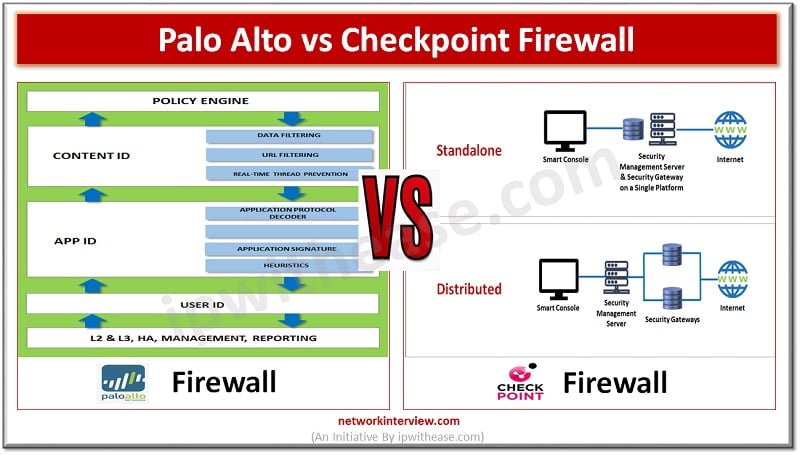
The Cisco Firepower Threat Defense (FTD) and Cisco Adaptive Security Appliance (ASA) are two types of security appliances that provide various features and capabilities to companies. These appliances were created with the intention of safeguarding businesses from cyber threats. Today …
Being connected with the network resources to get some work done is never easy, but luckily Active Directory (AD) exists! With the help of AD, the directory or database allows administrators to control access and manage permissions to different network …
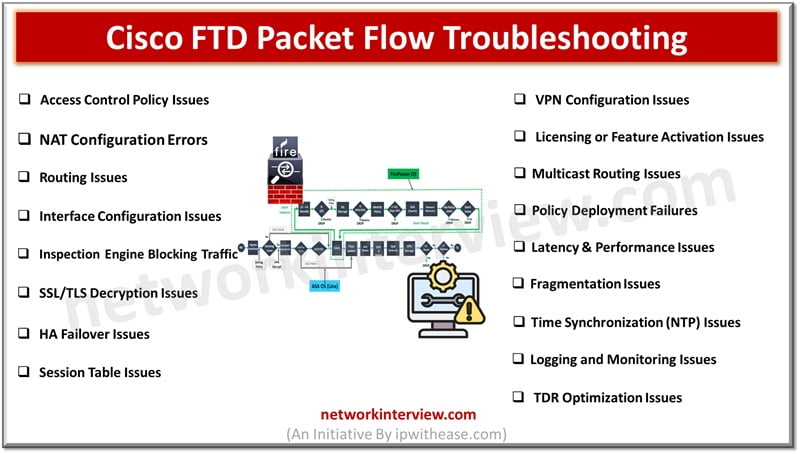
Troubleshooting Cisco FTD Packet Flow issues can be complex. Here is a summary of common Cisco FTD Packet Flow troubleshooting issues and the associated troubleshooting steps. Cisco FTD Packet Flow Troubleshooting Issues 1. Access Control Policy Issues Issue: Traffic is …
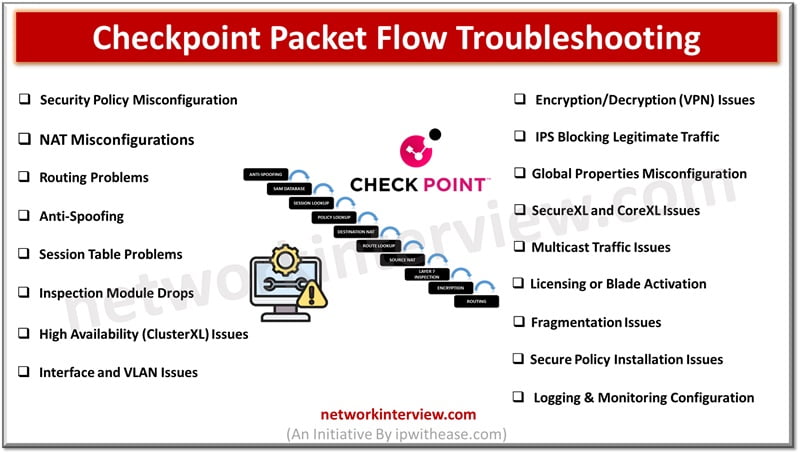
Troubleshooting Checkpoint Packet Flow issues can be complex. Here are common Checkpoint Packet Flow troubleshooting issues and steps to address them. Checkpoint Packet Flow Troubleshooting Issues 1. Security Policy Misconfiguration Issue: Traffic is dropped due to incorrect or missing security …
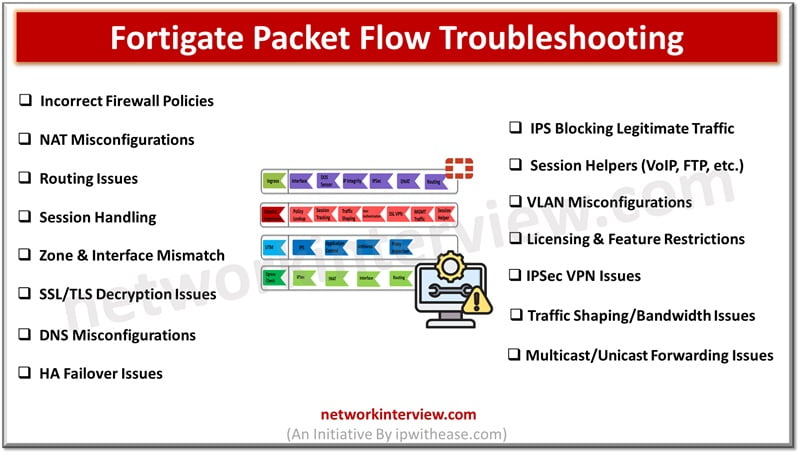
Troubleshooting Fortigate Packet Flow issues can be complex. Here’s an overview of common Fortigate Packet Flow troubleshooting issues and steps to resolve them. Fortigate Packet Flow Troubleshooting Issues 1. Incorrect Firewall Policies Issue: Traffic is dropped due to misconfigured firewall …
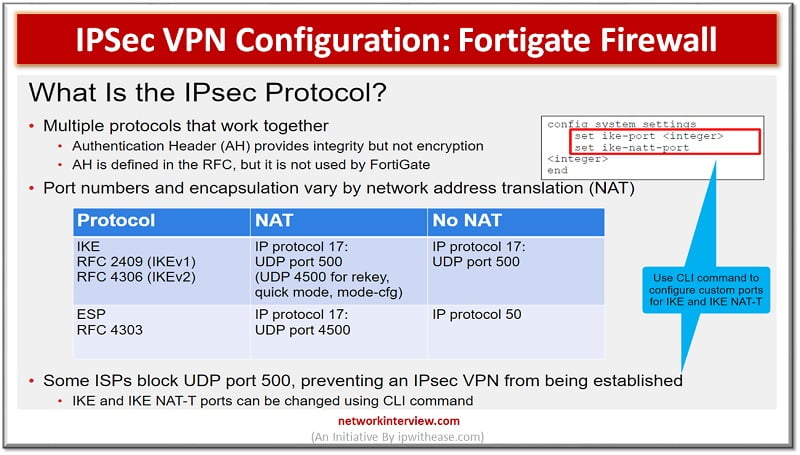
Objectives IPSec IKE Site to Site VPN between two FortiGate Sites Phase I and Phase II Parameters Tunnel Configuration Troubleshooting Commands IPSec VPN Configuration: Fortigate Firewall IPsec: It is a vendor neutral security protocol which is used to link …
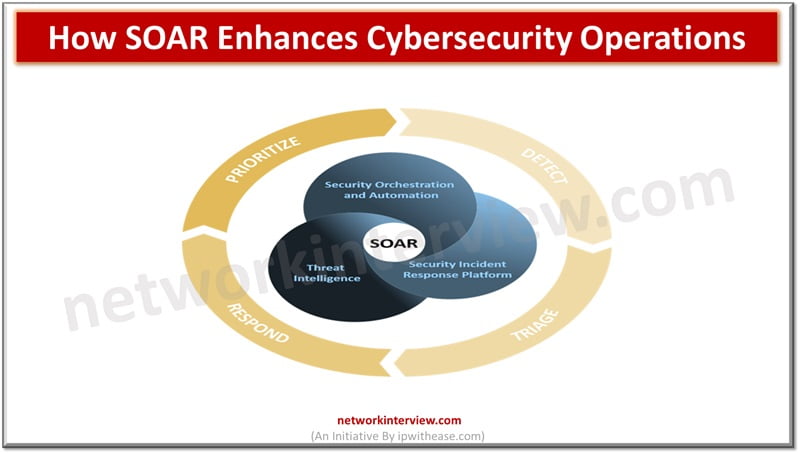
In today’s rapidly evolving digital landscape, cybersecurity has become more critical than ever. With the increasing frequency and sophistication of cyberattacks, organizations must find efficient ways to protect their data and systems. One of the most effective solutions is the …
How can your talent sourcing strategy improve your hiring process? Finding the right people is crucial for any organization. With the right plan, you can attract top candidates quickly and efficiently. Understanding key elements can make all the difference. Ready …
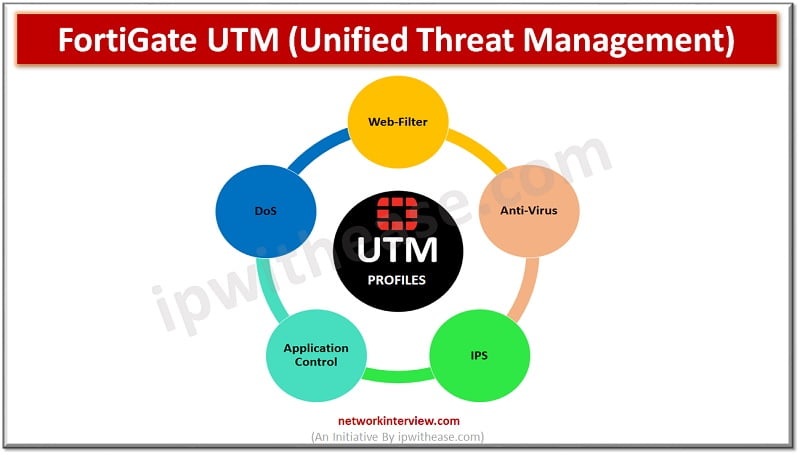
UTM-Unified Threat Management UTM (Unified Threat Management) is a feature of a firewall in which multiple security profiles combine and provide protection from threats and attacks. These features are antivirus, web filtering, IPS, anti-spam etc. UTM is the consolidated solution …
The tech world is changing fast and greatly affects the IT industry. This quick growth means there’s a huge need for IT support technicians who are good at their jobs and can fulfill clients’ needs. In such a fast-growing domain, …
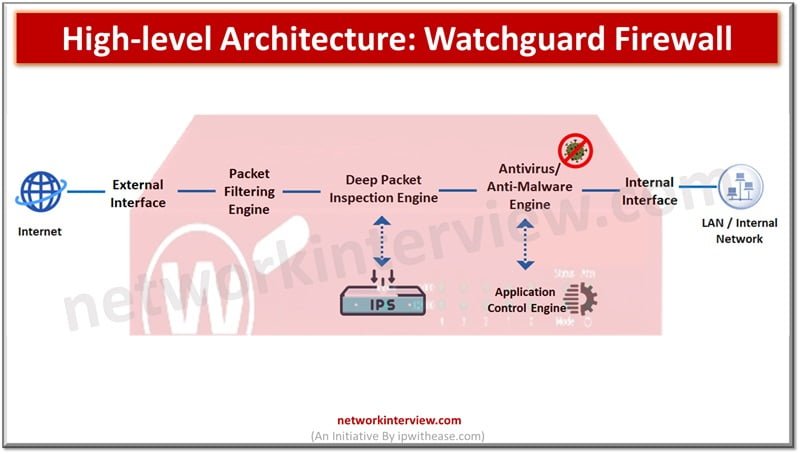
FortiGate firewalls are the primary line of defence against security threats coming from open Internet. The increasing sophistication in cyberattacks make it difficult to solely rely on firewalls for network protection. The NGFW firewall like FortiGate provides unified threat management …
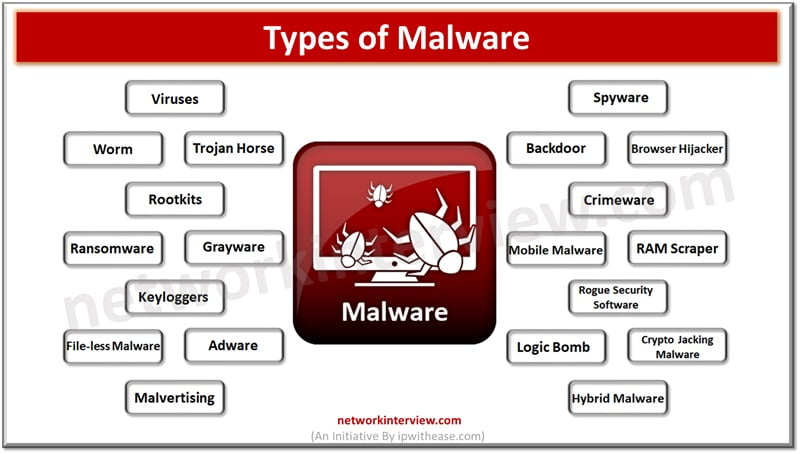
Malware software is a constant concern in the digital age. Cyber criminals continuously come up with innovative ways to break into computer systems and steal personal data, cause disruption to businesses, ask for ransomware, cause data destruction. Malware software is …
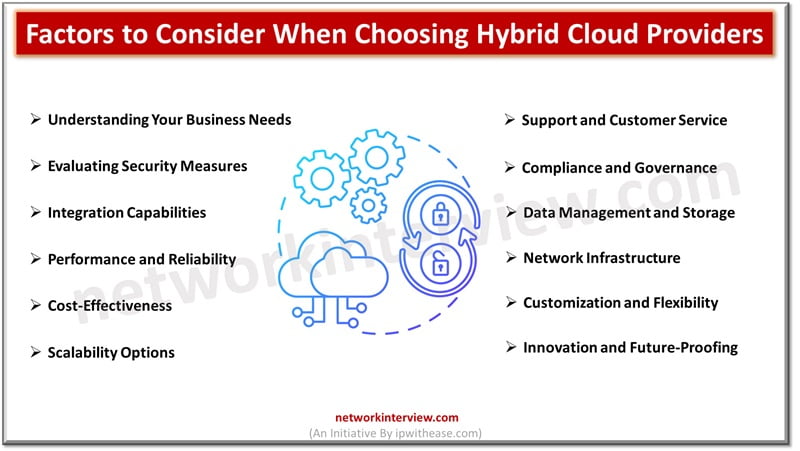
Are you overwhelmed by the myriad of hybrid cloud computing providers available? Choosing the right one can significantly affect your business’s scalability and efficiency. This blog will guide you through key factors to consider when selecting a hybrid cloud provider. …
Data security is a major concern for enterprises especially dealing with sensitive data. Creating a safe and secure environment becomes top most priority for them. In 2023 cyber attacks worldwide increased by 7%. Each company experiencing on an average 1200+ …
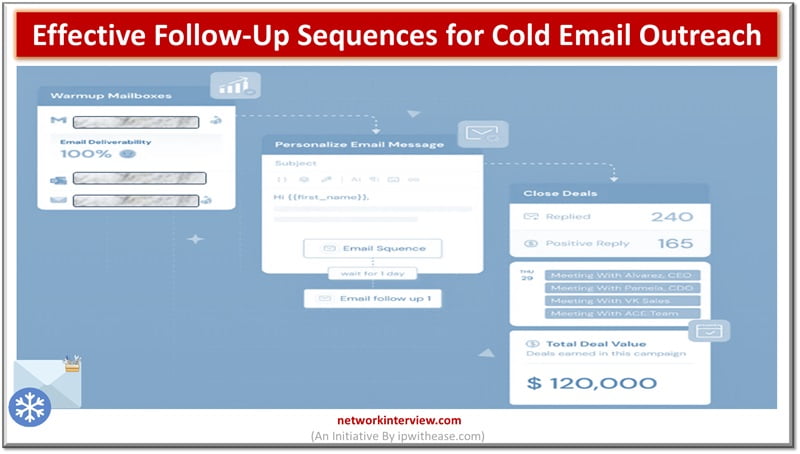
A key component of successful lead era is cold email outreach, which gives companies a simple and affordable way to contact potential clients. This effective tactic allows businesses to connect with potential clients who might not be mindful of their …
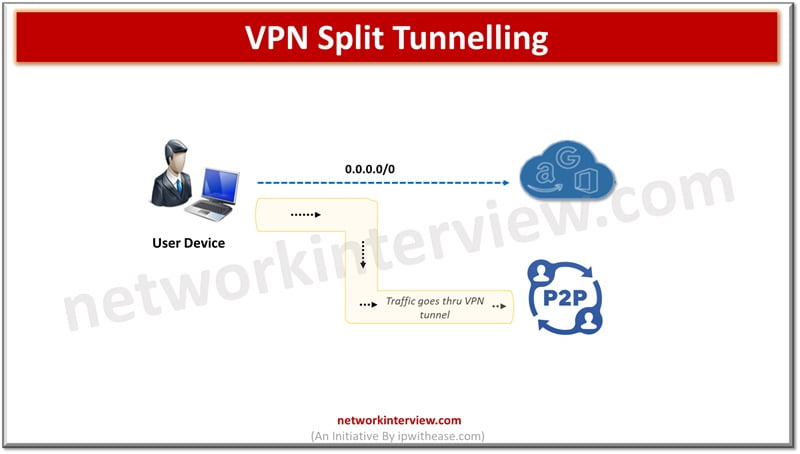
VPN or virtual private networks functions on tunnelling and connection encryption to keep internal activity, location, identity, and IP address hidden from public eyes. VPNs can unblock geo locked and censored content, can bypass statewide firewalls and torrents safely to …
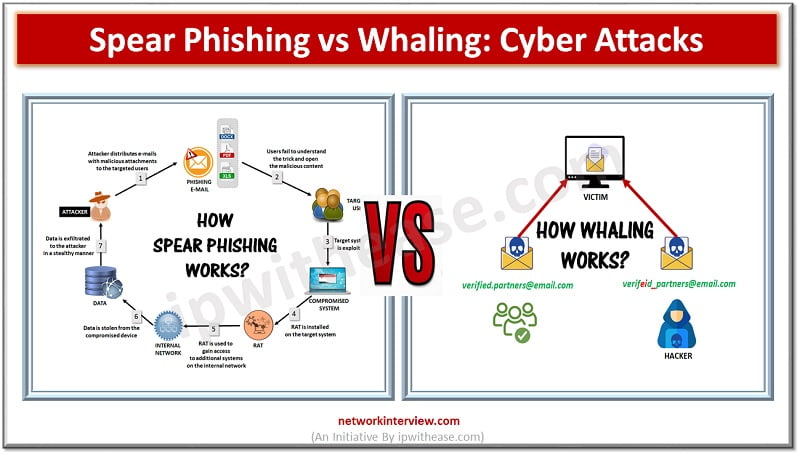
There are various types of Cyber Attacks on rise. As physical boundaries are diminishing rapidly and majority of enterprises rely on Internet and other emerging technologies such as cloud computing, GenAI etc. to run their businesses bad vectors are taking …
Traditional firewalls have come a long way by providing a clear overview of network traffic jams. Allows or blocks traffic according to port, state and protocols and filters traffic as per rules specified by firewall administrators. NGFWs have eventually changed …
Firewalls have always been the first line of defence, traditional firewalls have a set of rules to keep bad traffic and requests from malicious hackers away from organization networks. The role of traditional firewalls is however changing and getting replaced …
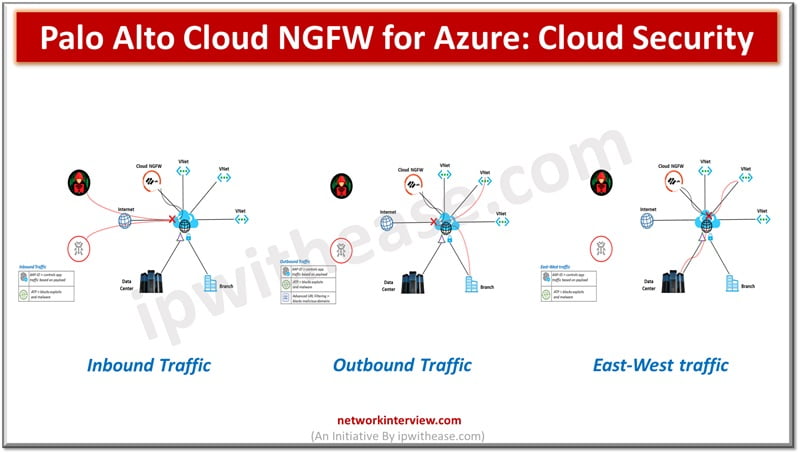
In today’s digital age, the protection of sensitive data and critical assets is paramount, particularly for large enterprises. With sprawling networks, diverse endpoints, and a plethora of applications to manage, the challenges of securing operations at scale are immense. However, …
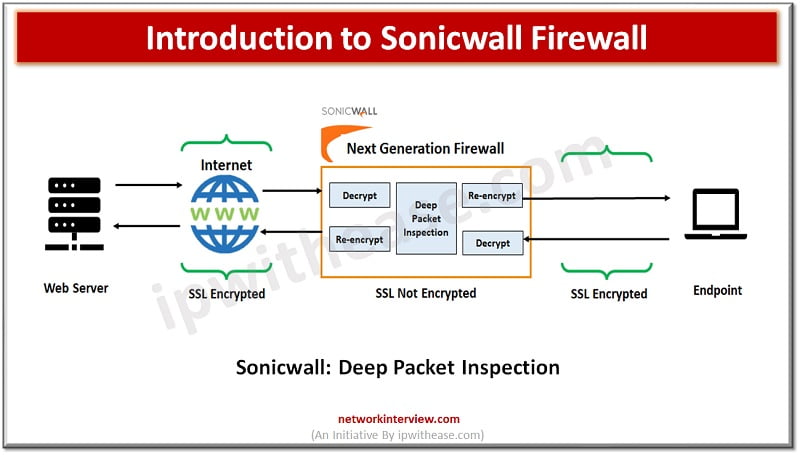
Evolution of Firewalls: Sonicwall Firewall Firewall technologies have evolved at a very rapid pace since its inception and from initial packet filtering firewalls which use to inspect packet traffic and took decision to allow or reject packets, which is then …
Both the proxy and the firewall limit or block connections to and from a network but in a different way. While a firewall filters and blocks communication (ports or unauthorized programs that seek unauthorized access to our network), a proxy …
Artificial intelligence is the new buzz world in the digitized world. Organizations are building AI capabilities in their products using generative AI and machine learning to enhance productivity. Elimination of repetitive tasks by using AI assistant to handle those tasks …
Choosing the right WiFi standard can significantly impact your internet experience. In this article, we’ll explore the differences between WiFi5 vs WiFi6 to help you determine which network device support is right for you. Understanding these differences will help you …
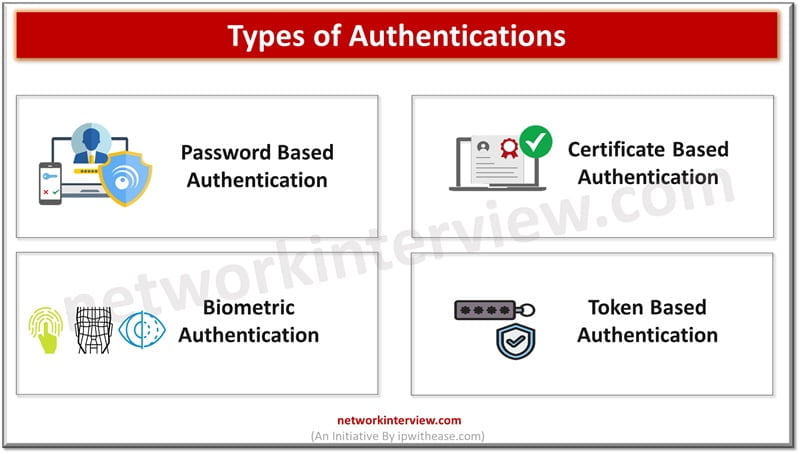
Authentication is the first step at entry level for ensuring security and it is required for managing user identification and providing access control for seamless operational experience in a secure manner. Individual authentications are not only restricted to passwords and …
Firewalls are network perimeter security devices which separate internal networks from external public networks such as the Internet to reduce the risk of external attacks. Firewalls use access policies and identify types of information, in addition they also control ports …
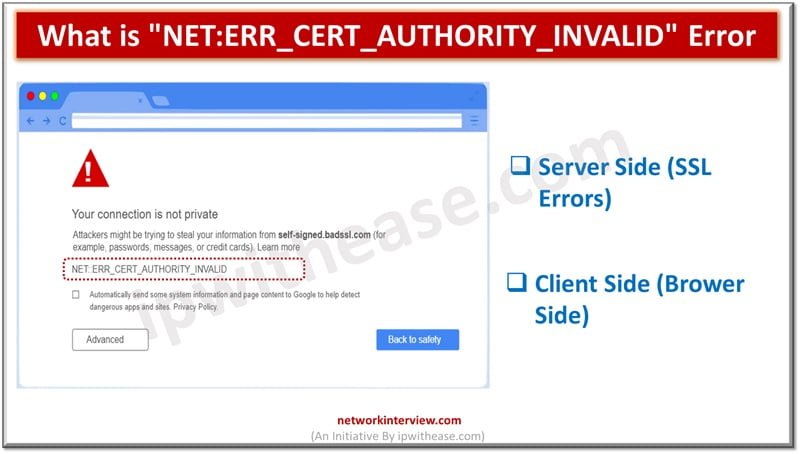
Secure Socket layer (SSL) certificates is one of the most widely used and popular mechanisms for public website security. SSL certificates keep data of users secure, verify ownership for the website, prevent attack vectors from creation of a fake version …
Firewalls are a key component in perimeter security. Firewalls have come a long way starting from stateful inspection technique to Next Generation firewalls (NGFW) and now a firewall which is machine learning (ML) aware and delivered as cloud native service …
Being proficient with the resources available is essential for success in the ever changing field of project management. Even though many project managers use Microsoft Project for planning and execution, using Microsoft Project Viewer might help you become even more …
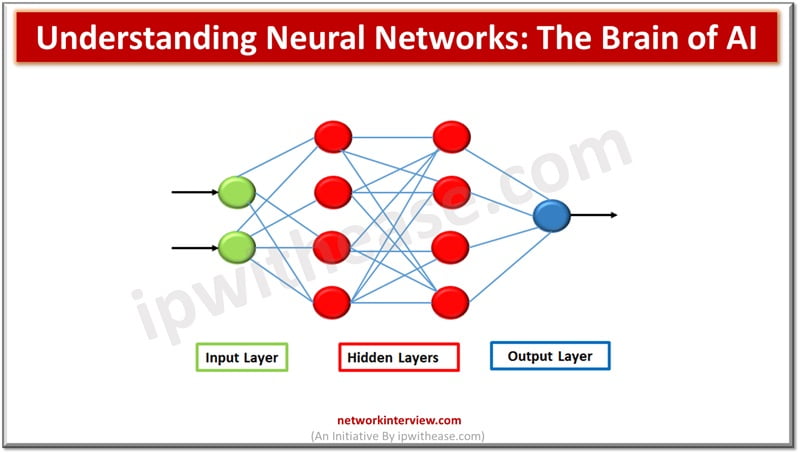
Artificial intelligence, machine learning, neural networks are the latest buzz words in the field of technology. Neural networks are the cornerstone for artificial intelligence (AI) to function. The idea is to mimic the capabilities of the human brain and create …
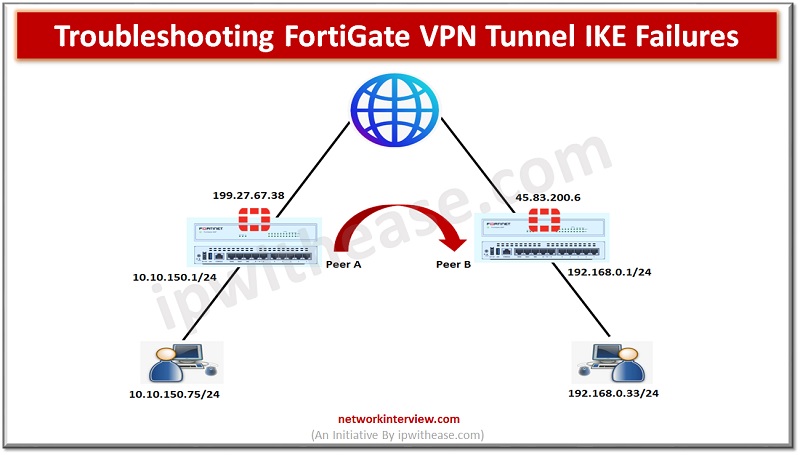
In our previous post, we have already discussed the IPSec VPN Configuration in Fortigate Firewall. Here in this post we will understand how to trouble shoot the FortiGate VPN tunnel IKE failures. We are using below topology to troubleshoot the …
The landscape of website creation is evolving rapidly, thanks to the integration of AI technologies. AI website builders for WordPress are particularly transformative, offering users intuitive design experiences, automated functionalities, and smart customization options. This article explores the top 10 …
Today’s environments demand a hybrid working environment and setups. 74% of organizations world wide use a hybrid working model especially post pandemic this phenomenon was prevalent and 59% of workers were working remotely. This working model during pandemic paved the …
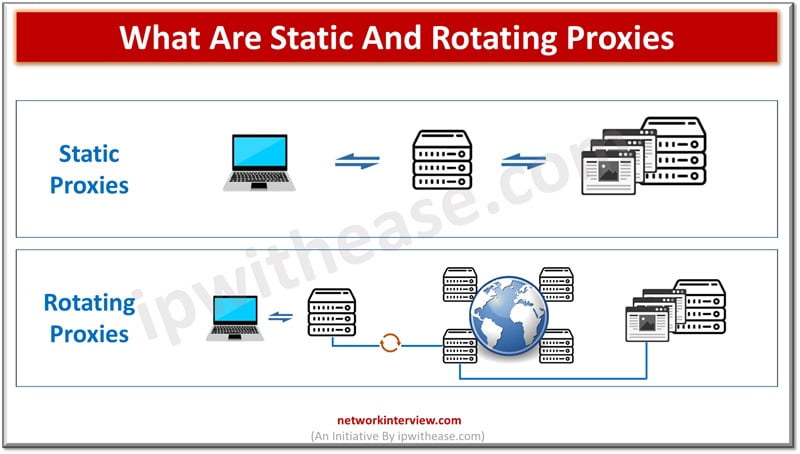
Basically, a proxy anonymizes your connection to the internet by masking or hiding your IP (Internet Protocol) address. How does it hide your IP? When you route a request through a proxy server, it substitutes your IP address with its …
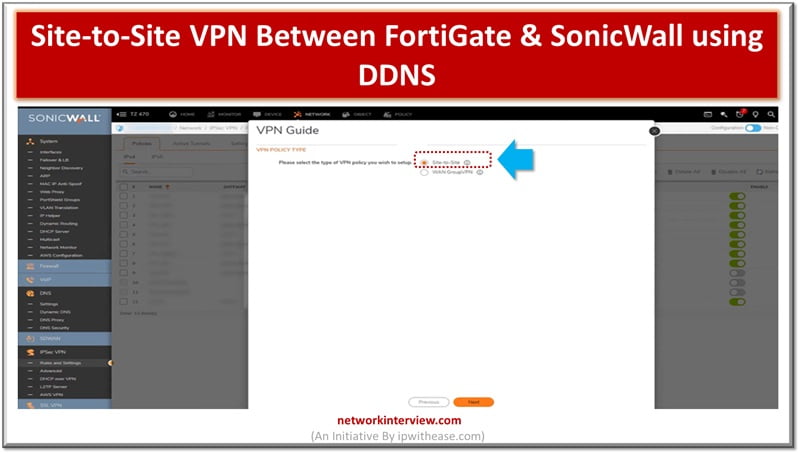
Site to Site VPN is connection between two or more networks used widely by enterprises to leverage Internet connection between private traffic in lieu of using private MPLS circuits. Site to site VPNs used by enterprises offices dispersed across geo …
Cyber Attacks Cyber attacks are on rise since Covid 19 at a more rapid pace compared to before. Various forms of cyber attack techniques being used by hackers to gain access to organizations resulting in devastating effects such as unauthorized …
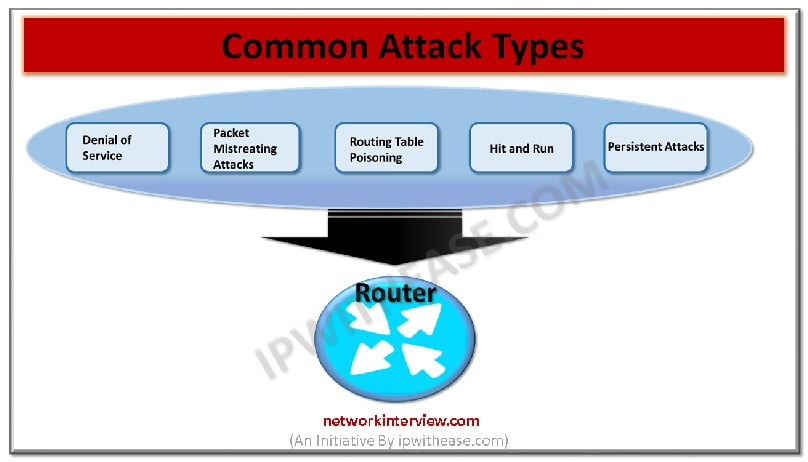
It is not possible to 100% prevent the router attacks. However, there are possibilities of few things that could be done for preventing the occurrence of most common attacks of routers on the network and the system. Widespread attacks are …
Email marketing remains a significant tool in the digital age, with a well-curated email list being a vital asset for any business. Effective email capture strategies are essential for fostering relationships with potential and current customers, driving sales, and reinforcing …
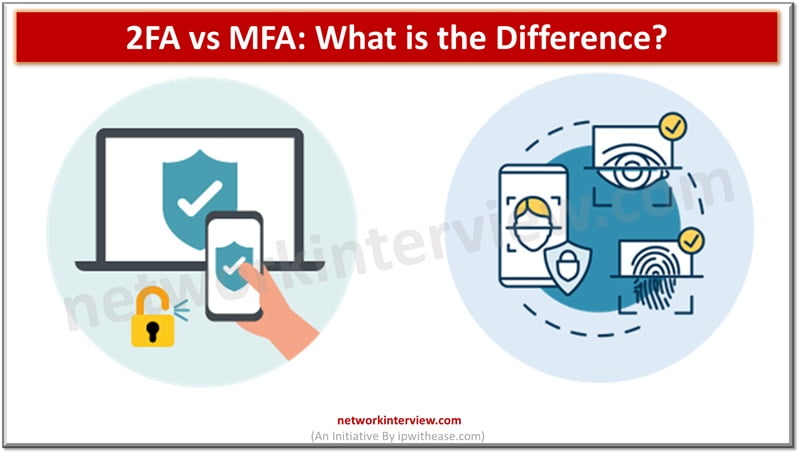
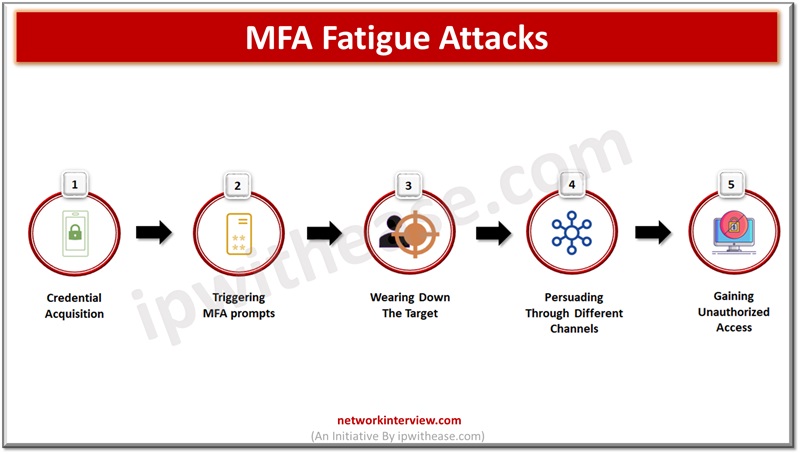
Leaked or stolen credentials are primary sources being used by cybercriminals in breach networks and steel company confidential and sensitive data. Normal authentication involving a username and password is an old technique and no longer provides protection against sophisticated attacks …
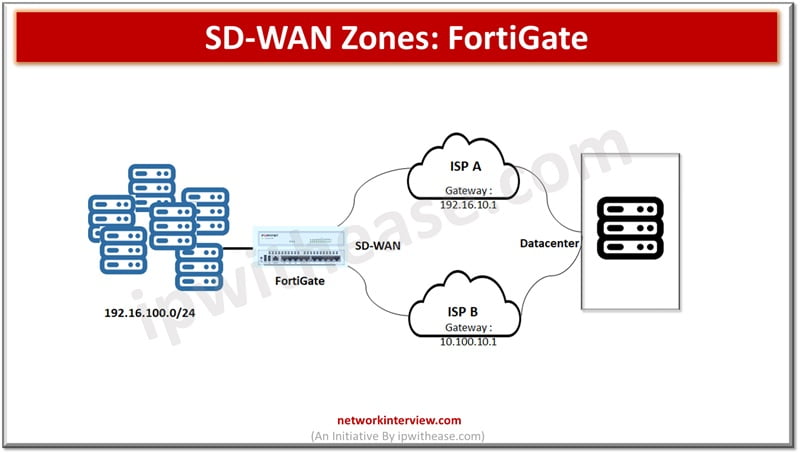
SD-WAN is a software defined networking approach wherein hardware is separated from the control plane. SD-WAN is an ideal technology for cloud and on prem deployments. It is a consolidation of transport connections, underlays, monitor and load balancing traffic across …
Attackers are constantly looking for vulnerabilities to penetrate your networks. Protection against direct, external threats require extensive network security functions deployed on the edge. Protections on the edge are provided by stateful and next generation firewalls (NGFWs) which offer features …
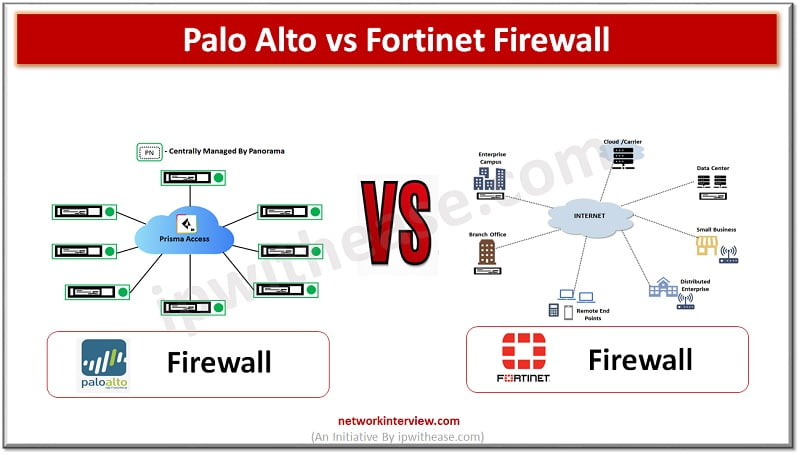
(Diagram depicting Palo Alto vs Fortinet Firewall) Organizations need to keep pace with rapid increase in technology demands such as remote working, anywhere connectivity, lower latency , increased availability along with protection of infrastructure from a never ending list of …
Application aware security is the need of the IT enterprises. Companies are replacing the old and outdated firewalls with Next generation firewalls which are application aware and this evolution can be attributed to web 2.0 where web-based applications and services …