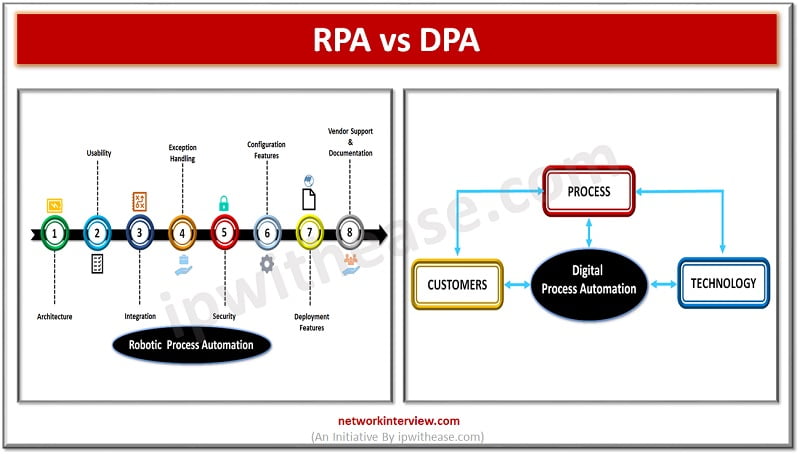
Process Automation As per Gartner prediction 72% of the enterprises will be working with Robotic process automation (RPA) in next two years and Digital process automation (DPA) is identified as major component for digital transformation with DPA market worth $6.76 …
Software quality assurance (QA) is evolving as technological advancements redefine industry practices. One breakthrough in this field is robotic process automation (RPA), which enhances testing efficiency and accuracy. According to Statista, the global RPA market is projected to exceed $13 …
Introduction to Software Testing When it comes to software testing, there are many different methods that you can use. Each of them has their own advantages and disadvantages, so it’s important to understand the pros and cons of each method …
Introduction to Penetration Testing Tools & Software Identifying weaker controls in systems via attack simulation help organizations to gather information about the different ways hackers can gain unauthorised access of systems and sensitive data and information or may get engaged …
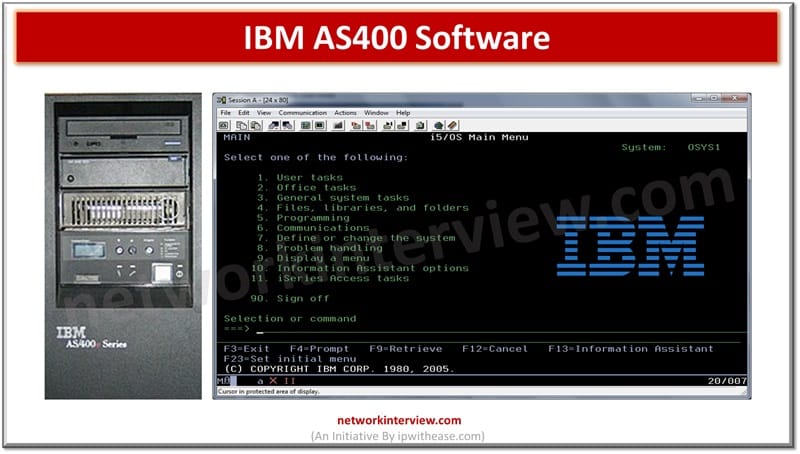
The Legacy of AS400 Software IBM developed the AS400 software, frequently referred to as IBM i, as an operating system and software framework for its midrange computers. It was first released in 1988. Before being renamed the iSeries, System i, …
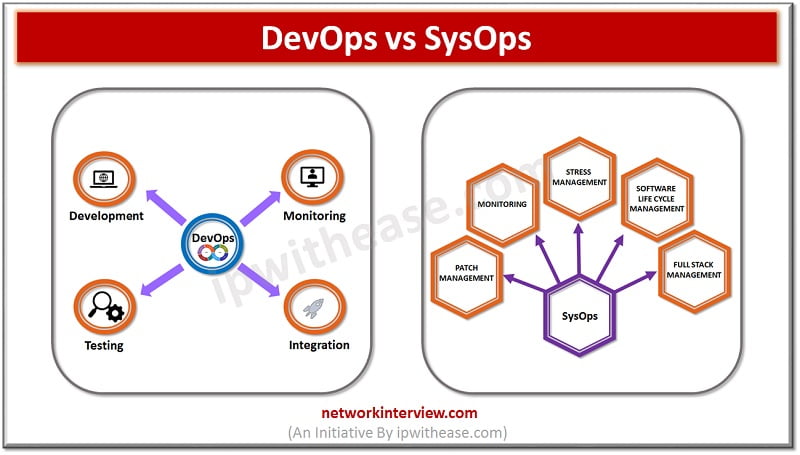
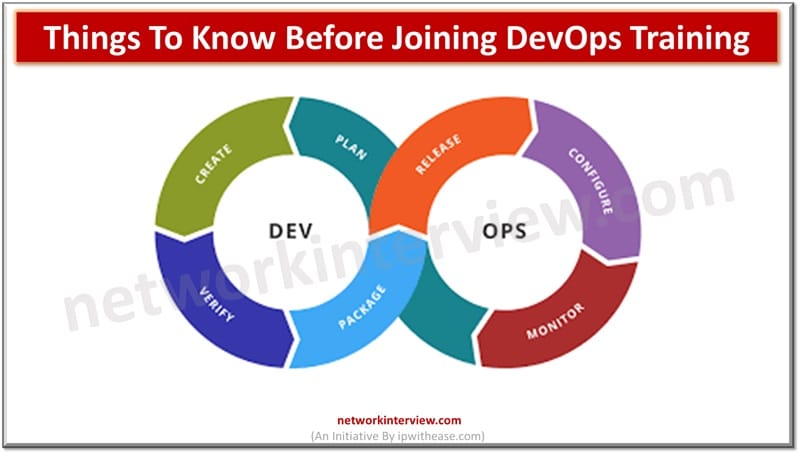
Introduction to DevOps & SysOps Technology advancements are crucial to the dynamic IT landscape in today’s times. Cloud computing has been crucial which presents excellent opportunities to business for the future. SysOps and DevOps are commonly used terminologies in cloud …
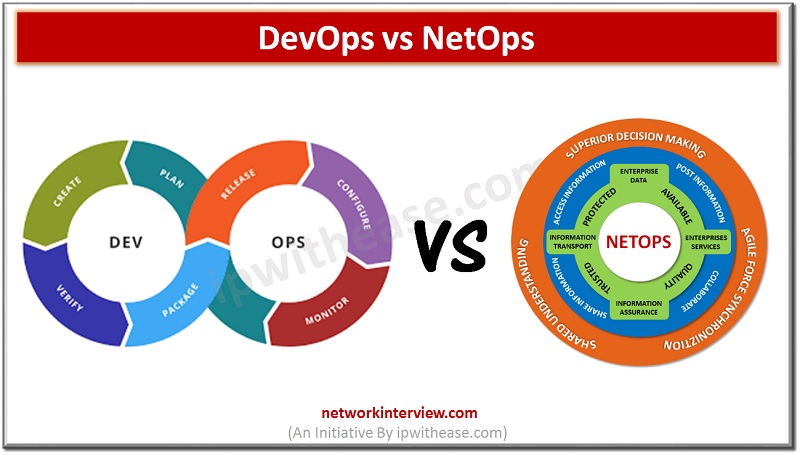
Introduction The tremendous technical development in the IT and other digital fields started the popular trend of creating acronyms with the Suffix Ops. And the word DevOps, NetOps, and SecOps are confusing IT and Tech communities further as they are …
Intoduction: Emerging Job Roles What is the difference between the Cloud Architect and DevOps Engineer? These new roles with growth of Cloud technologies has increased the confusion about roles? In this article, we will try to demystify some of concepts …
As companies seek to optimize their processes for development and operations, there is a consistent and growing demand for DevOps professionals. DevOps is both a mindset and a set of tools that facilitates interaction between the development and IT operations …
Everyone can use a little extra “simple” in their lives. Nowhere is that more apparent than in the arduous work of building network infrastructures to meet today’s demand for moving vast amounts of data across networks at gigabit speeds. Businesses …
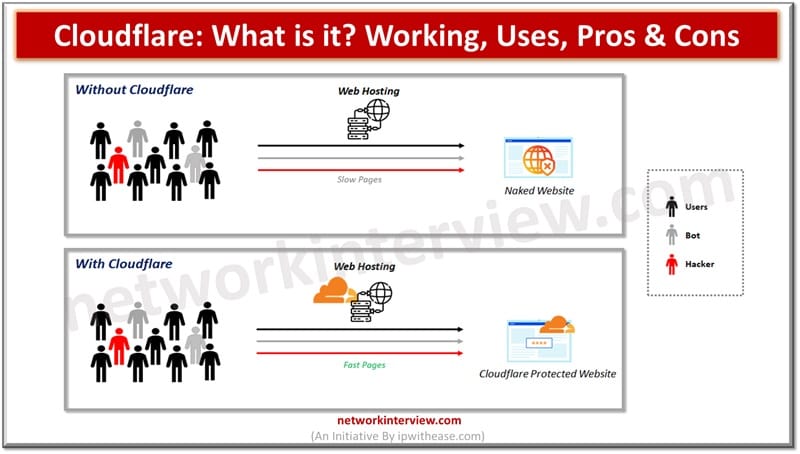
The Internet ecosystem is spanned across geographies and its users are spread around the globe. Millions of users of the Internet expect web content delivery in a speedy and efficient manner. Content delivery networks (CDNs) are called the lifeline of …
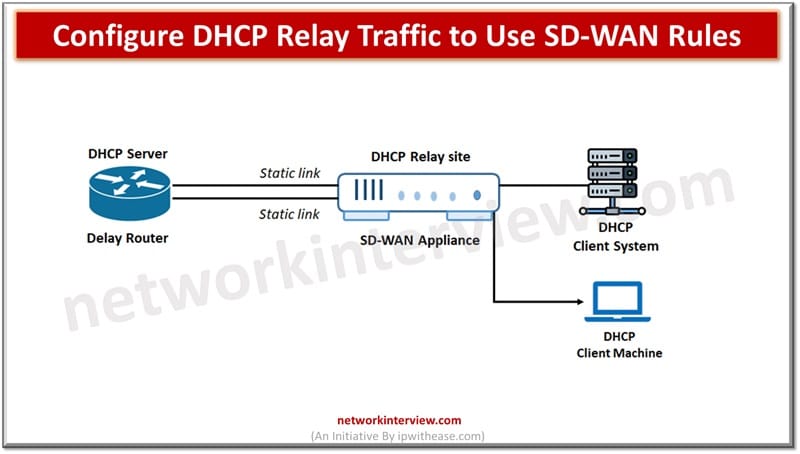
SD-WAN or software defined networking have SD-WAN rules also known as services rules. They are used for identification of traffic of interest and routing of traffic based on route condition and strategy between two devices in a network. SD-WAN rules …
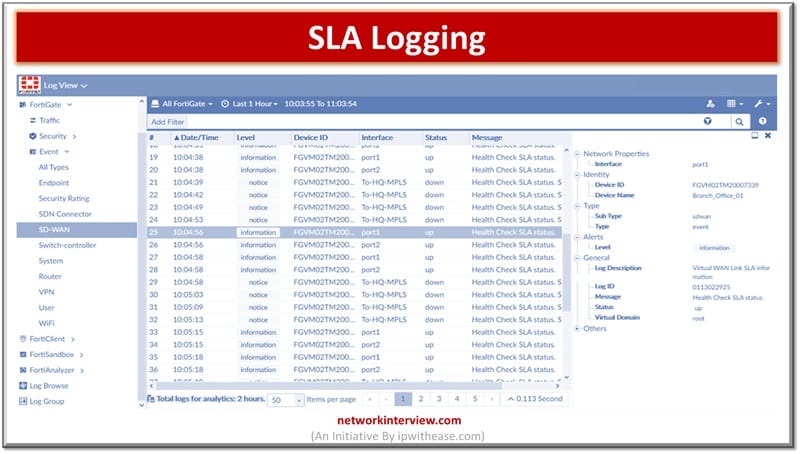
Logs are an important aspect of monitoring and management. Logs enablement of devices is crucial to perform fault isolation, resolution of issues and also help in locating the root cause of problem for permanent fix. All modern devices have the …
Cyber Attack Technologies Various forms of cyber attacks are prevailing these days and method of attack sophistication has reached new levels where now attackers are not limited only to fake websites, messages or emails but also focus is on theft …
The arena of business is ever-evolving, and in the current digital age, information is as crucial as currency. With the burgeoning amount of data that businesses generate and acquire, managing this knowledge effectively becomes imperative. Knowledge management systems can help …
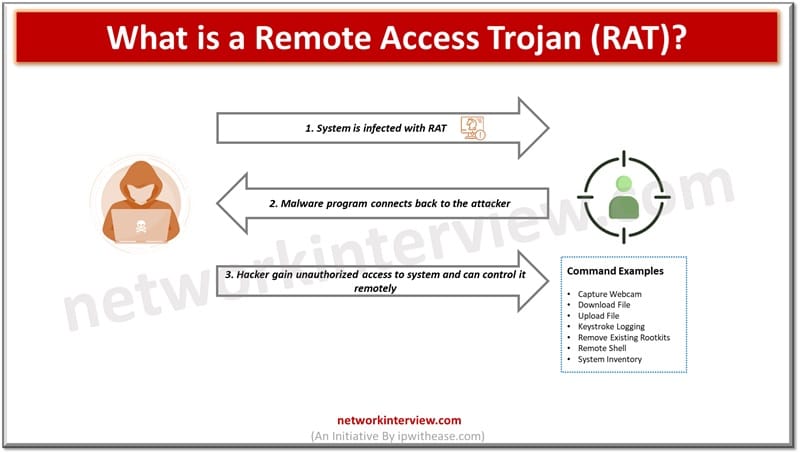
Remote access and control over systems remotely is widely used to provide technical support to users or work outside the boundaries of offices. With the rise of remote working however, especially during Covid-19 pandemic had allowed attackers to use remote …
The information access is made uninterrupted over wired and wireless networks from anywhere, anytime, any device using modern technology. Today end users are mobile and often equipped with digital portable devices and they expect services availability as and when it …
Domain name system (DNS) is widely used terminology in Internet or public networks. DNS maps host name to IP addresses in a similar fashion as phone books or telephone directory maps a name to a phone number. This is an …
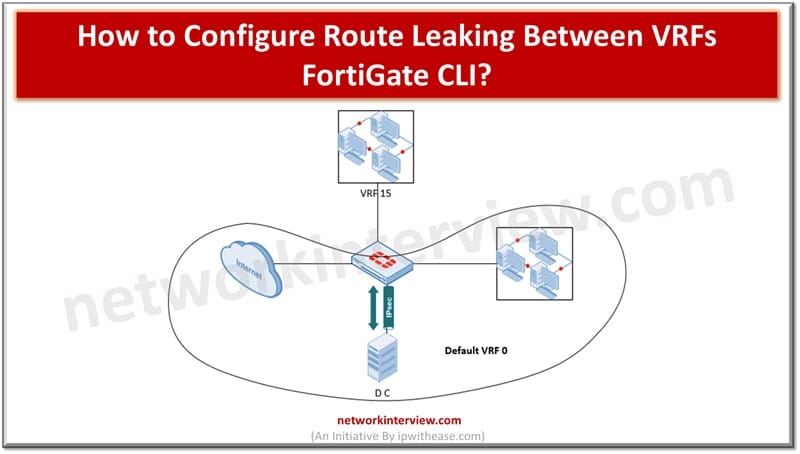
Cloud hosted workloads require customer traffic isolation and separate routing at logical level but through common hardware. Using virtual route forwarding (VRF) technique multiple routing tables can be created within the same router. VRF is used to divide routing functionality …
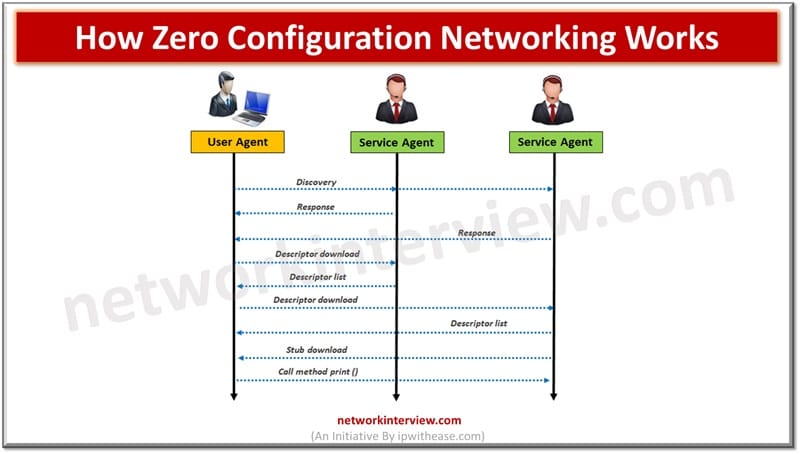
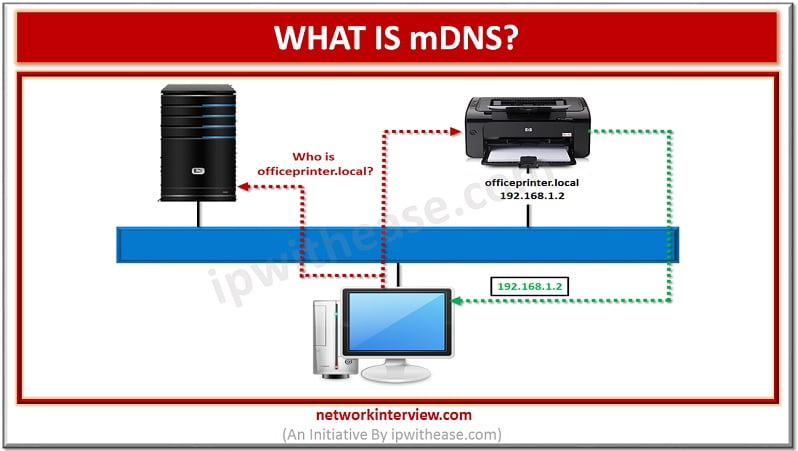
What is mDNS? The method of using familiar semantics of operating, packet formats and interfaces of DNS programming in small network without a DNS server is termed as Multicast DNS or mDNS. Every network node with mDNS reserved multicast address …
Traditional networks use DNS and DHCP protocols which require servers and complex configurations to operate. Multicast DNS or mDNS is a set of protocols and technologies which provide automatic services of discovery, name resolution without manual configuration. It is a …
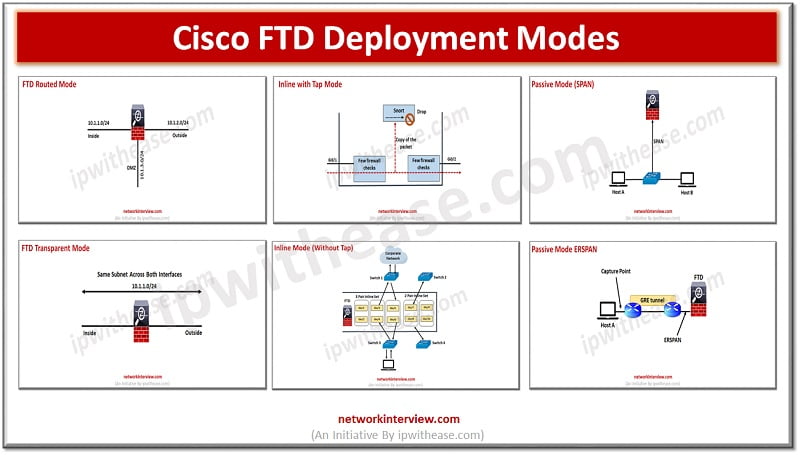
(FTD Deployment Modes: Routed, Transparent, Inline, Inline with tap, Passive SPAN, Passive ERSPAN) Cisco FTD design and deployment implementation involves setting up firewall, SSL inspection, NAT, IPS and active/standby HA. Deployment model determines placement of FirePower into the network as …
Digital marketing can be incredibly complex these days. Many different campaigns, tools, processes, and types of data are used in digital marketing, which can make it feel overwhelming and overly complex. You should know that there are a few steps …
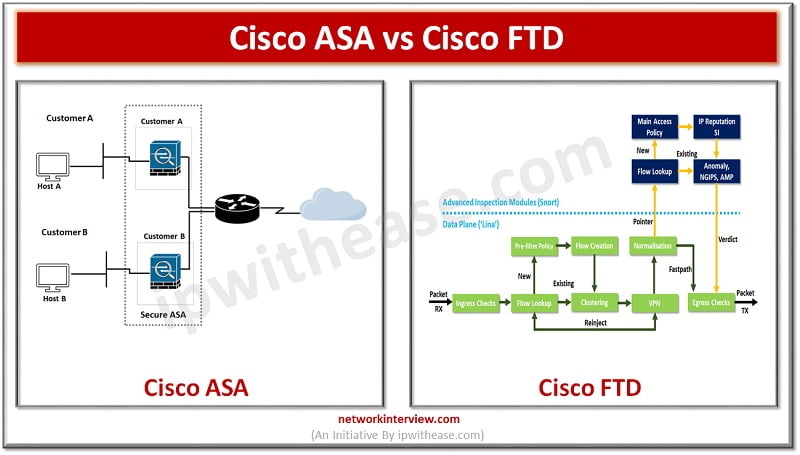
The Cisco Firepower Threat Defense (FTD) and Cisco Adaptive Security Appliance (ASA) are two types of security appliances that provide various features and capabilities to companies. These appliances were created with the intention of safeguarding businesses from cyber threats. Today …
Being connected with the network resources to get some work done is never easy, but luckily Active Directory (AD) exists! With the help of AD, the directory or database allows administrators to control access and manage permissions to different network …
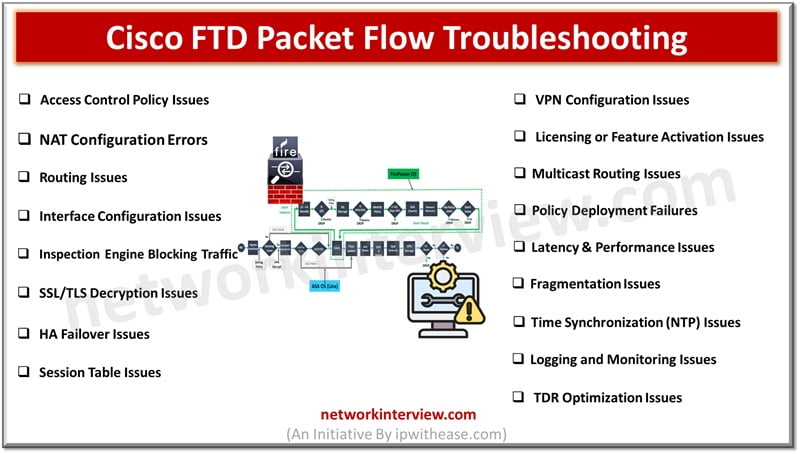
Troubleshooting Cisco FTD Packet Flow issues can be complex. Here is a summary of common Cisco FTD Packet Flow troubleshooting issues and the associated troubleshooting steps. Cisco FTD Packet Flow Troubleshooting Issues 1. Access Control Policy Issues Issue: Traffic is …
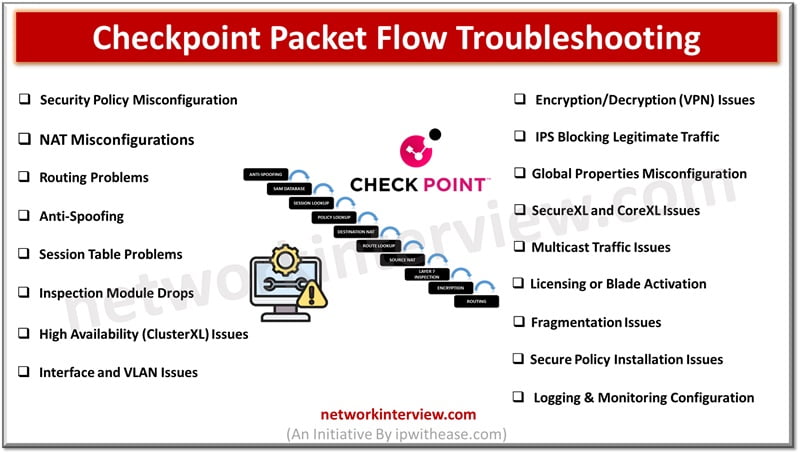
Troubleshooting Checkpoint Packet Flow issues can be complex. Here are common Checkpoint Packet Flow troubleshooting issues and steps to address them. Checkpoint Packet Flow Troubleshooting Issues 1. Security Policy Misconfiguration Issue: Traffic is dropped due to incorrect or missing security …
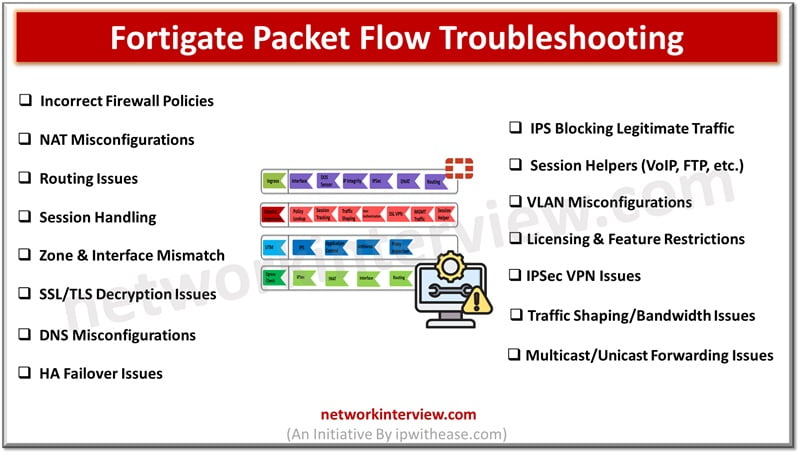
Troubleshooting Fortigate Packet Flow issues can be complex. Here’s an overview of common Fortigate Packet Flow troubleshooting issues and steps to resolve them. Fortigate Packet Flow Troubleshooting Issues 1. Incorrect Firewall Policies Issue: Traffic is dropped due to misconfigured firewall …
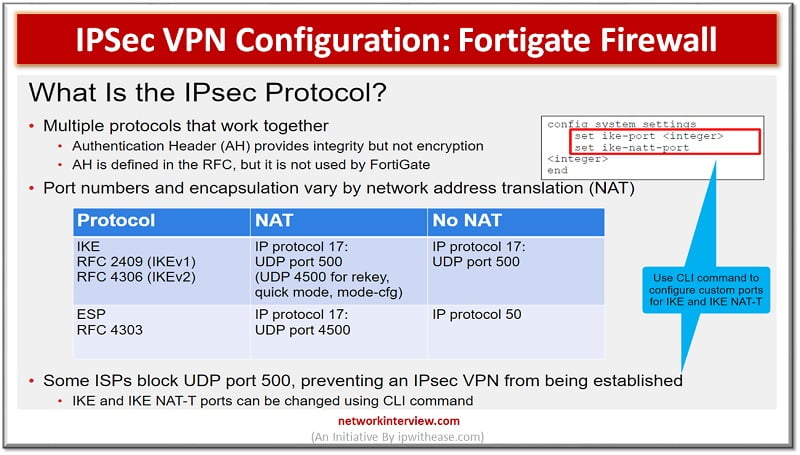
Objectives IPSec IKE Site to Site VPN between two FortiGate Sites Phase I and Phase II Parameters Tunnel Configuration Troubleshooting Commands IPSec VPN Configuration: Fortigate Firewall IPsec: It is a vendor neutral security protocol which is used to link …
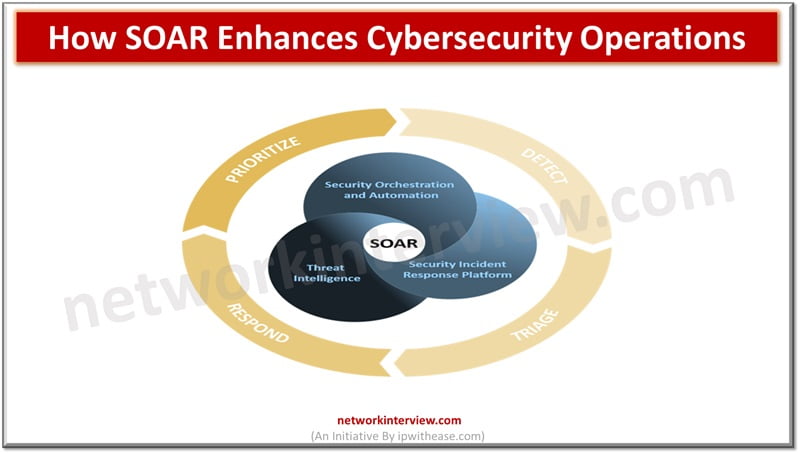
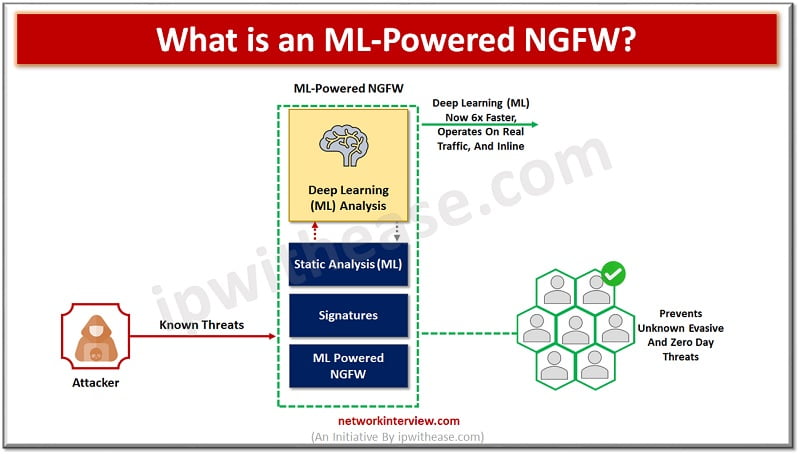
In today’s rapidly evolving digital landscape, cybersecurity has become more critical than ever. With the increasing frequency and sophistication of cyberattacks, organizations must find efficient ways to protect their data and systems. One of the most effective solutions is the …
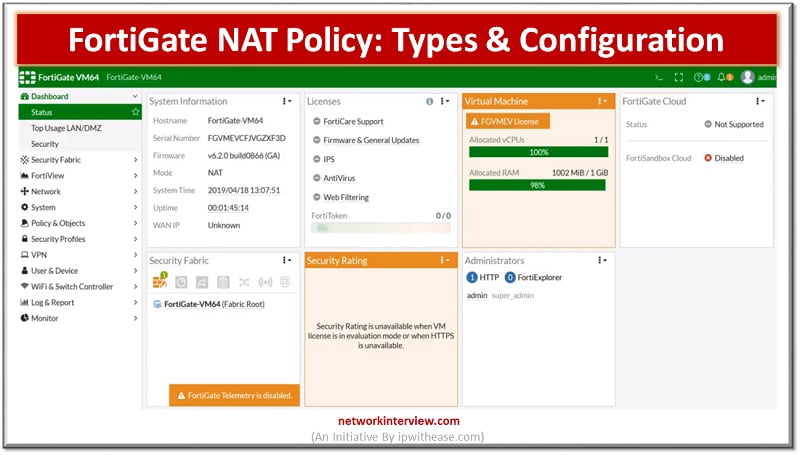
NAT-Network Address Translation NAT is a process that enables a single device such as a firewall or router to act as an agent between the internet or public network to LAN or private segment. NAT is usually use for below …
How can your talent sourcing strategy improve your hiring process? Finding the right people is crucial for any organization. With the right plan, you can attract top candidates quickly and efficiently. Understanding key elements can make all the difference. Ready …
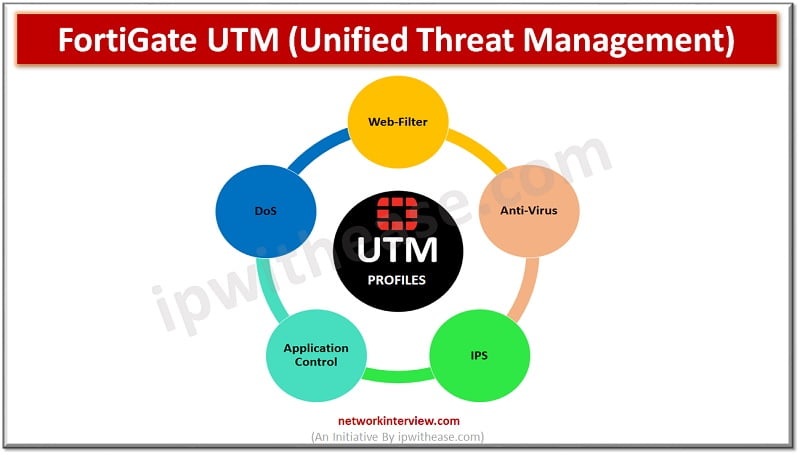
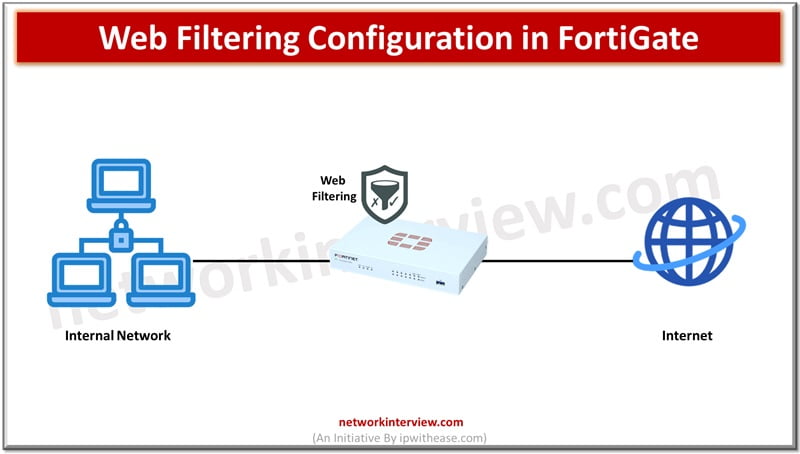
UTM-Unified Threat Management UTM (Unified Threat Management) is a feature of a firewall in which multiple security profiles combine and provide protection from threats and attacks. These features are antivirus, web filtering, IPS, anti-spam etc. UTM is the consolidated solution …
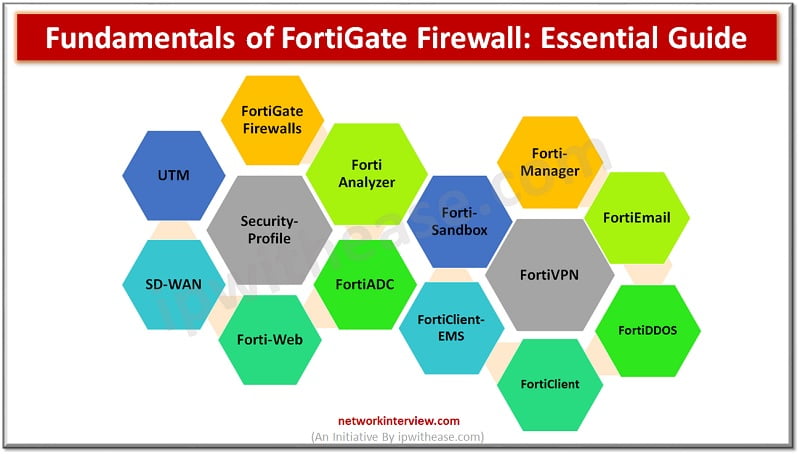
FortiGate fundamentals and principles involve high security infrastructure and provide a secure set up to the client. FortiGate Firewall is the most respected and highly used security product in the market. It uses artificial intelligence and machine learning to achieve …
The tech world is changing fast and greatly affects the IT industry. This quick growth means there’s a huge need for IT support technicians who are good at their jobs and can fulfill clients’ needs. In such a fast-growing domain, …
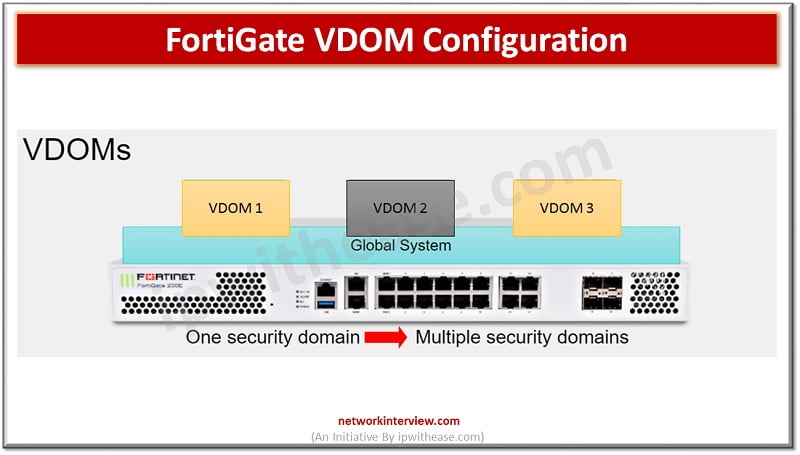
Understanding FortiGate VDOM FortiGate VDOM or Virtual Domain split FortiGate device into multiple virtual devices. Each VDOM has independent security policies, routing table and by-default traffic from VDOM can not move to different VDOM which means two interfaces of different …
FortiGate firewalls are the primary line of defence against security threats coming from open Internet. The increasing sophistication in cyberattacks make it difficult to solely rely on firewalls for network protection. The NGFW firewall like FortiGate provides unified threat management …
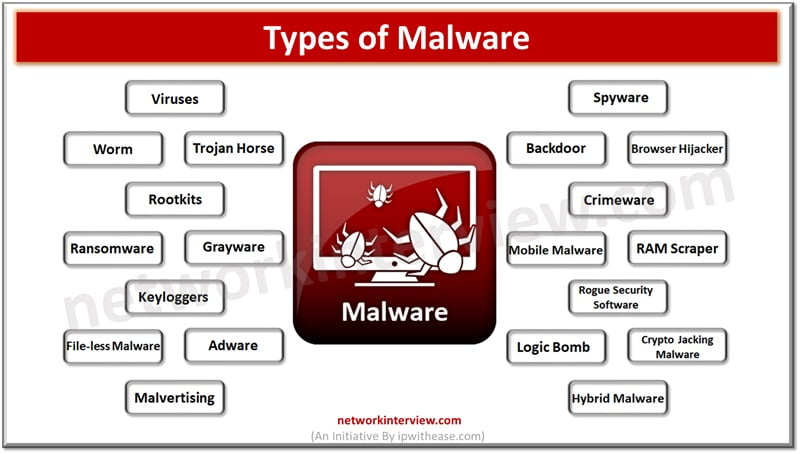
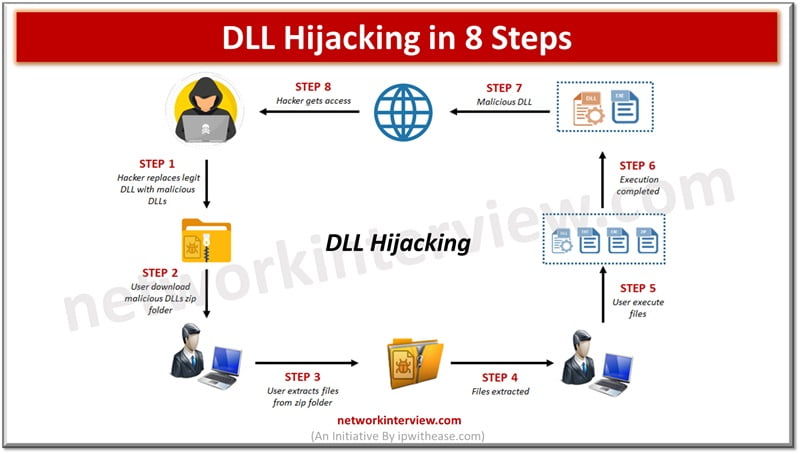
Malware software is a constant concern in the digital age. Cyber criminals continuously come up with innovative ways to break into computer systems and steal personal data, cause disruption to businesses, ask for ransomware, cause data destruction. Malware software is …
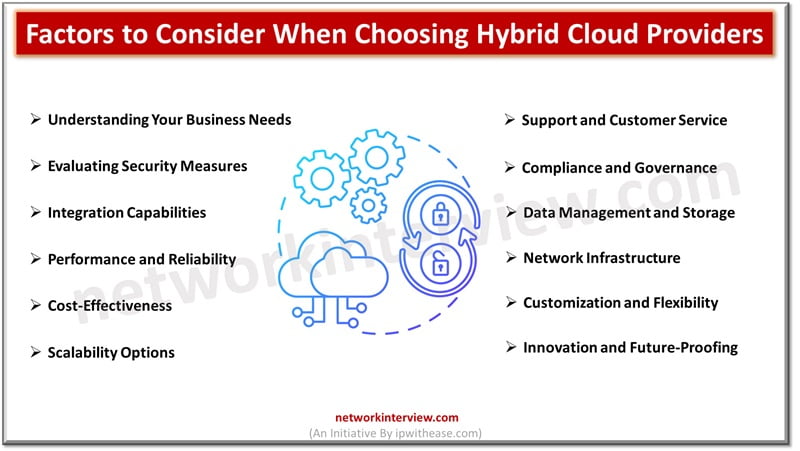
Are you overwhelmed by the myriad of hybrid cloud computing providers available? Choosing the right one can significantly affect your business’s scalability and efficiency. This blog will guide you through key factors to consider when selecting a hybrid cloud provider. …
Data security is a major concern for enterprises especially dealing with sensitive data. Creating a safe and secure environment becomes top most priority for them. In 2023 cyber attacks worldwide increased by 7%. Each company experiencing on an average 1200+ …
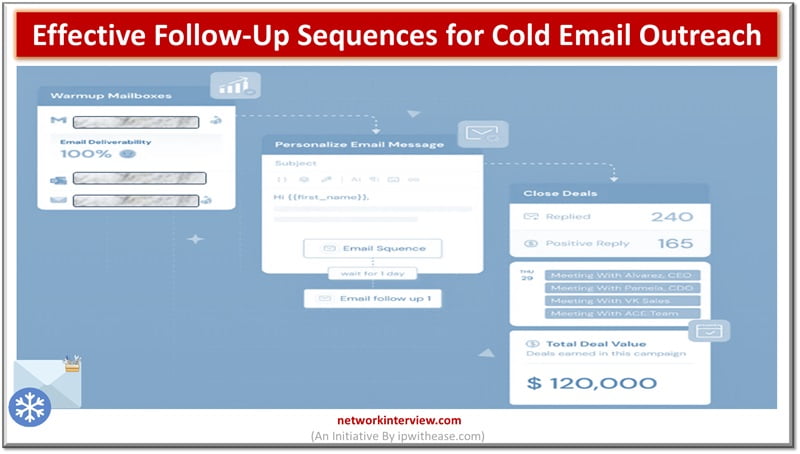
A key component of successful lead era is cold email outreach, which gives companies a simple and affordable way to contact potential clients. This effective tactic allows businesses to connect with potential clients who might not be mindful of their …
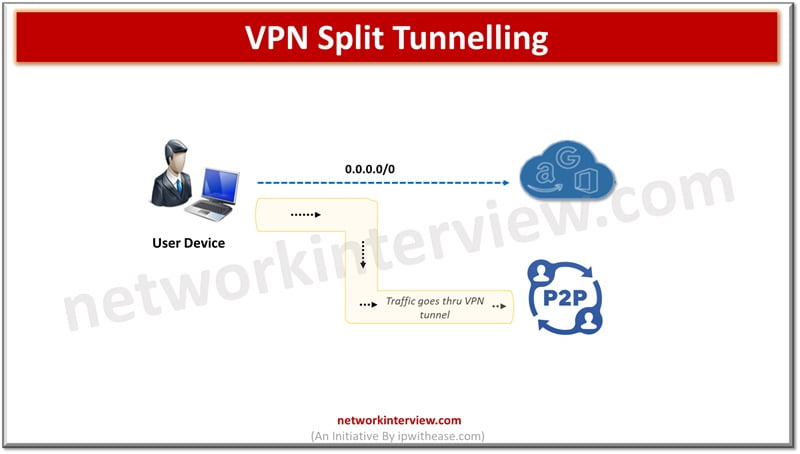
VPN or virtual private networks functions on tunnelling and connection encryption to keep internal activity, location, identity, and IP address hidden from public eyes. VPNs can unblock geo locked and censored content, can bypass statewide firewalls and torrents safely to …
There are various types of Cyber Attacks on rise. As physical boundaries are diminishing rapidly and majority of enterprises rely on Internet and other emerging technologies such as cloud computing, GenAI etc. to run their businesses bad vectors are taking …
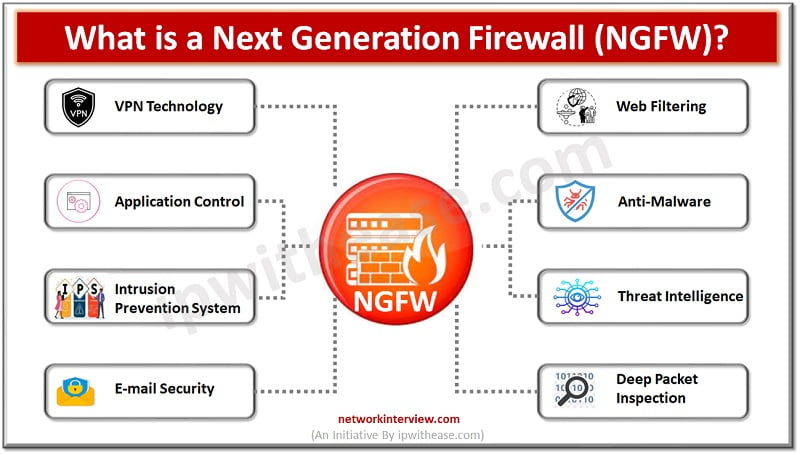
Traditional firewalls have come a long way by providing a clear overview of network traffic jams. Allows or blocks traffic according to port, state and protocols and filters traffic as per rules specified by firewall administrators. NGFWs have eventually changed …
Firewalls have always been the first line of defence, traditional firewalls have a set of rules to keep bad traffic and requests from malicious hackers away from organization networks. The role of traditional firewalls is however changing and getting replaced …