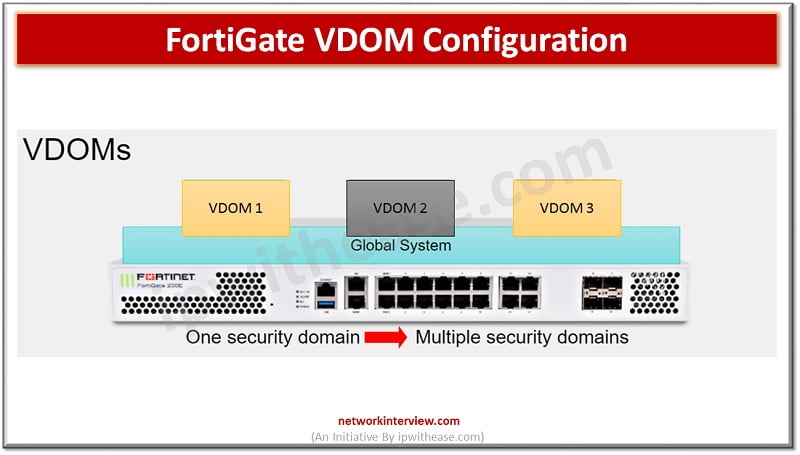
Understanding FortiGate VDOM FortiGate VDOM or Virtual Domain split FortiGate device into multiple virtual devices. Each VDOM has independent security policies, routing table and by-default traffic from VDOM can not move to different VDOM which means two interfaces of different …
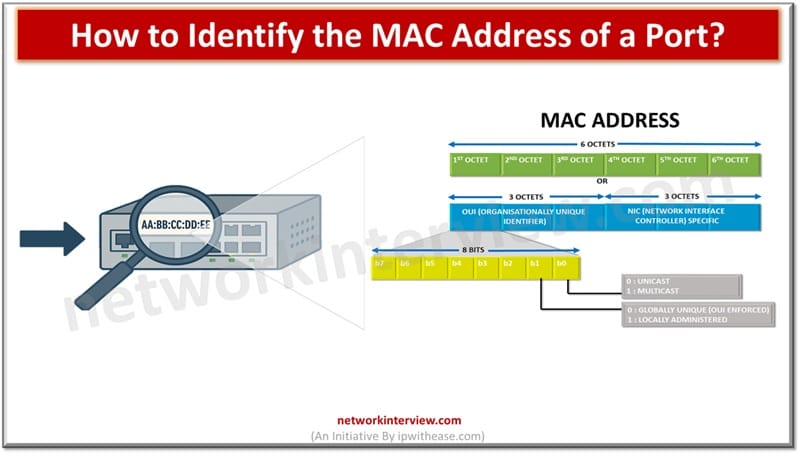
In the world of computer networks, communication between devices or systems happens using a unique identifier which facilitates data exchange and communication between interconnected systems. Unique identification of network interface controller (NIC) for network communication happens at the data link …
NAT-Network Address Translation NAT is a process that enables a single device such as a firewall or router to act as an agent between the internet or public network to LAN or private segment. NAT is usually use for below …
Troubleshooting Palo Alto packet flow issues can be complex. In this blog, we will discuss some common Palo Alto Packet Flow Troubleshooting issues and troubleshooting steps. Palo Alto Packet Flow Troubleshooting Issues 1. Incorrect Security Policies Issue: Traffic is being …
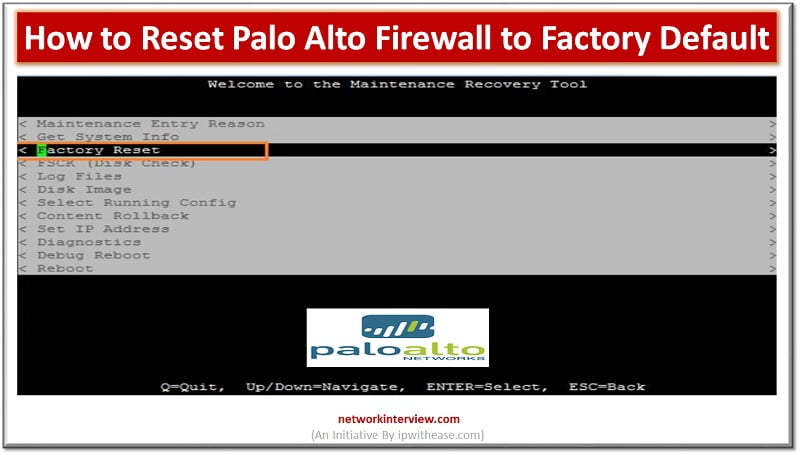
Introduction to Reset Palo Alto Firewall Firewall is a network security device which grants or rejects network access to traffic flowing between untrusted zone (External networks) to trusted (Internal networks) zone. Starting from initial days of Stateful inspection firewalls and …
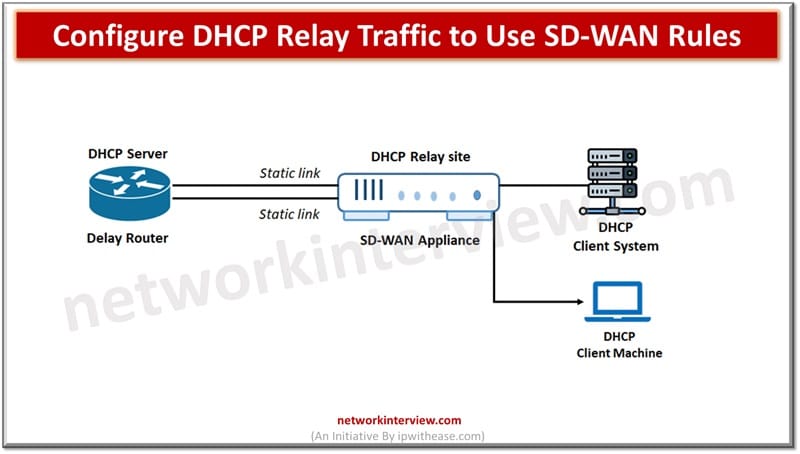
SD-WAN or software defined networking have SD-WAN rules also known as services rules. They are used for identification of traffic of interest and routing of traffic based on route condition and strategy between two devices in a network. SD-WAN rules …
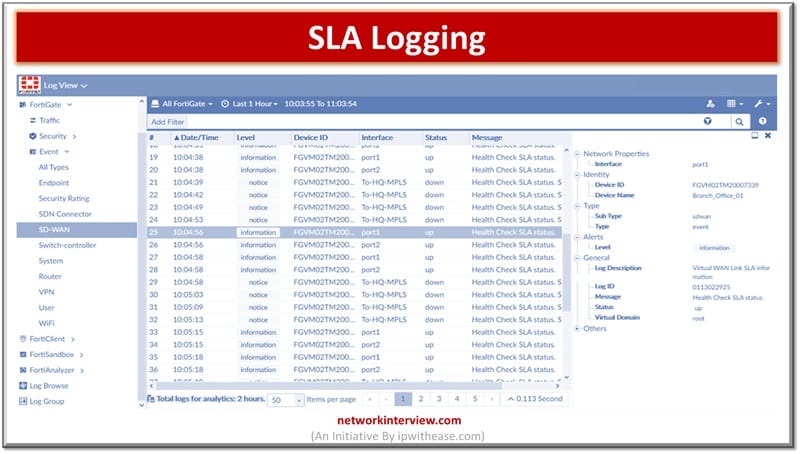
Logs are an important aspect of monitoring and management. Logs enablement of devices is crucial to perform fault isolation, resolution of issues and also help in locating the root cause of problem for permanent fix. All modern devices have the …
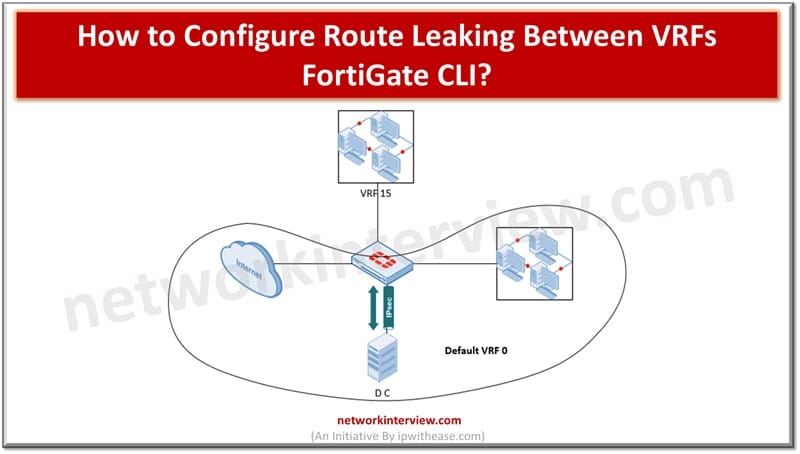
Cloud hosted workloads require customer traffic isolation and separate routing at logical level but through common hardware. Using virtual route forwarding (VRF) technique multiple routing tables can be created within the same router. VRF is used to divide routing functionality …
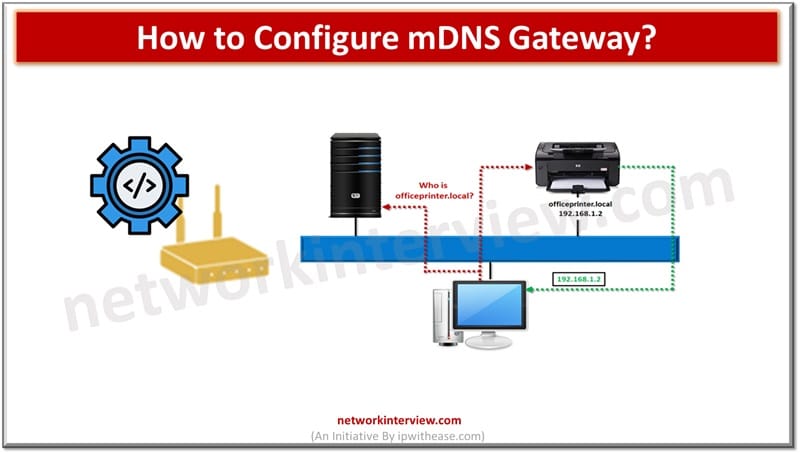
Traditional networks use DNS and DHCP protocols which require servers and complex configurations to operate. Multicast DNS or mDNS is a set of protocols and technologies which provide automatic services of discovery, name resolution without manual configuration. It is a …
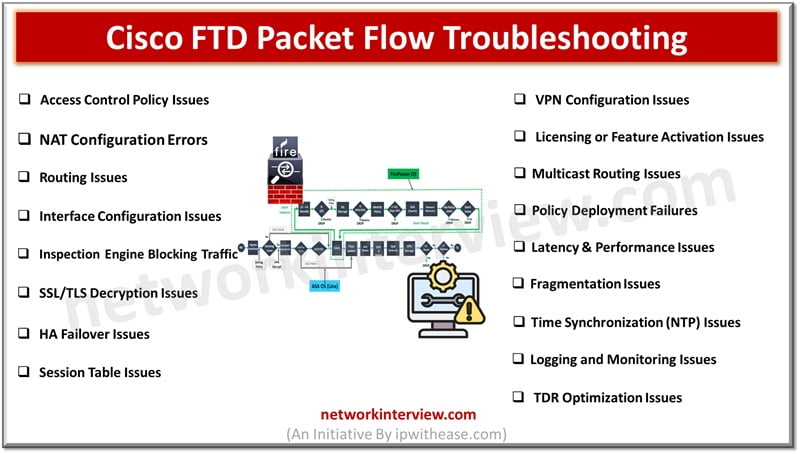
Troubleshooting Cisco FTD Packet Flow issues can be complex. Here is a summary of common Cisco FTD Packet Flow troubleshooting issues and the associated troubleshooting steps. Cisco FTD Packet Flow Troubleshooting Issues 1. Access Control Policy Issues Issue: Traffic is …
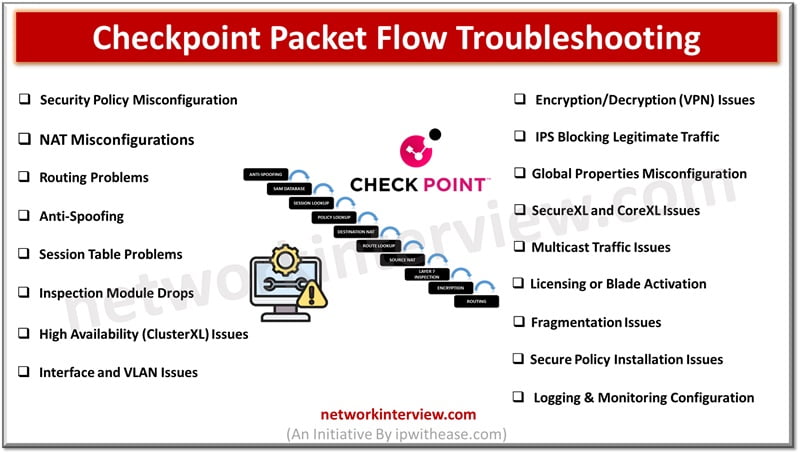
Troubleshooting Checkpoint Packet Flow issues can be complex. Here are common Checkpoint Packet Flow troubleshooting issues and steps to address them. Checkpoint Packet Flow Troubleshooting Issues 1. Security Policy Misconfiguration Issue: Traffic is dropped due to incorrect or missing security …
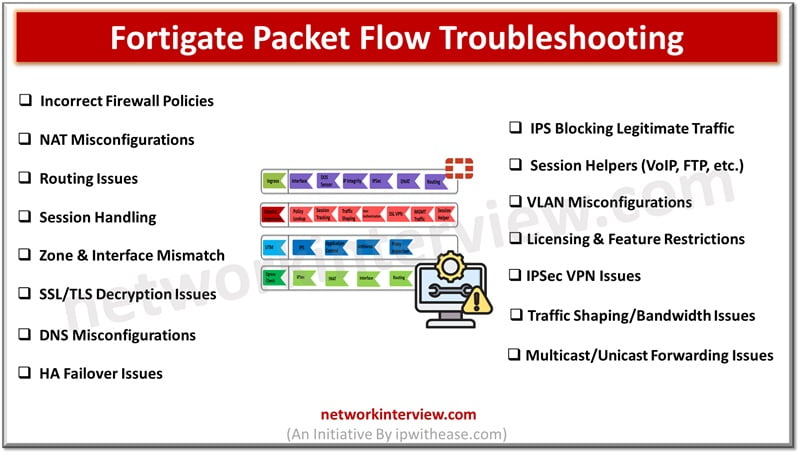
Troubleshooting Fortigate Packet Flow issues can be complex. Here’s an overview of common Fortigate Packet Flow troubleshooting issues and steps to resolve them. Fortigate Packet Flow Troubleshooting Issues 1. Incorrect Firewall Policies Issue: Traffic is dropped due to misconfigured firewall …
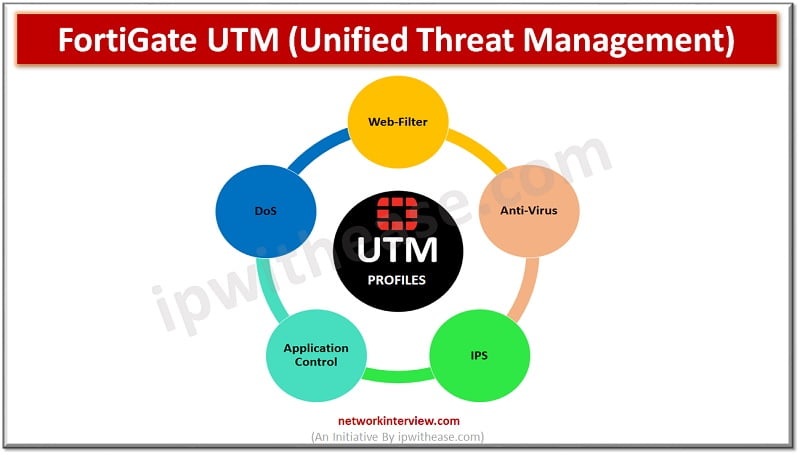
UTM-Unified Threat Management UTM (Unified Threat Management) is a feature of a firewall in which multiple security profiles combine and provide protection from threats and attacks. These features are antivirus, web filtering, IPS, anti-spam etc. UTM is the consolidated solution …
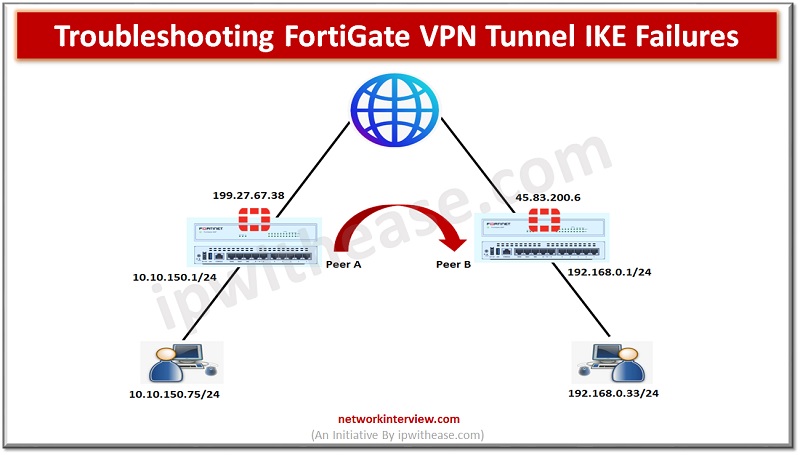
In our previous post, we have already discussed the IPSec VPN Configuration in Fortigate Firewall. Here in this post we will understand how to trouble shoot the FortiGate VPN tunnel IKE failures. We are using below topology to troubleshoot the …
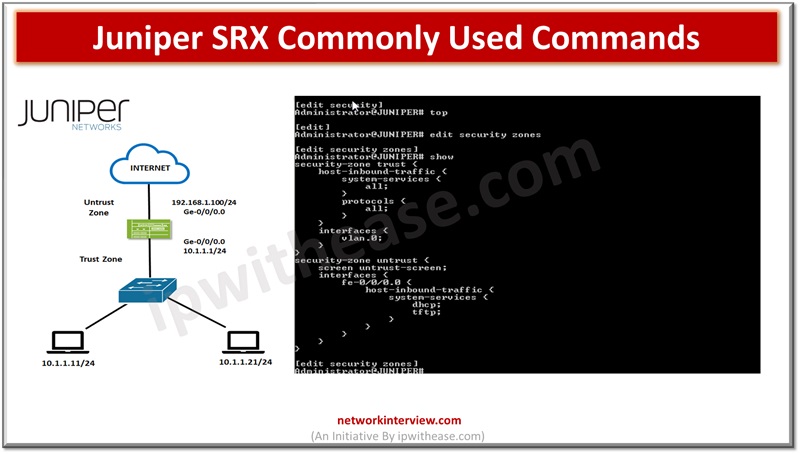
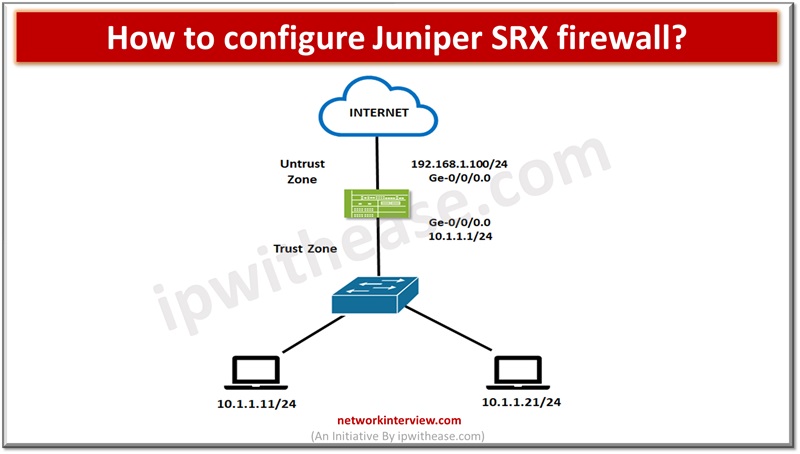
In the previous articles, we have studied the basics of Juniper SRX firewall, its architecture, installation, modes, security policies etc. Today, we will discuss the command line interface of Juniper SRX. Commonly Used Commands: Juniper SRX Here are some commonly …
We can’t imagine a network without a firewall, they are the staple of almost every network in the IT landscape. The firewalls provide protection to nearly every network-based transaction. Over a decade the underlying technology has changed rapidly as the …
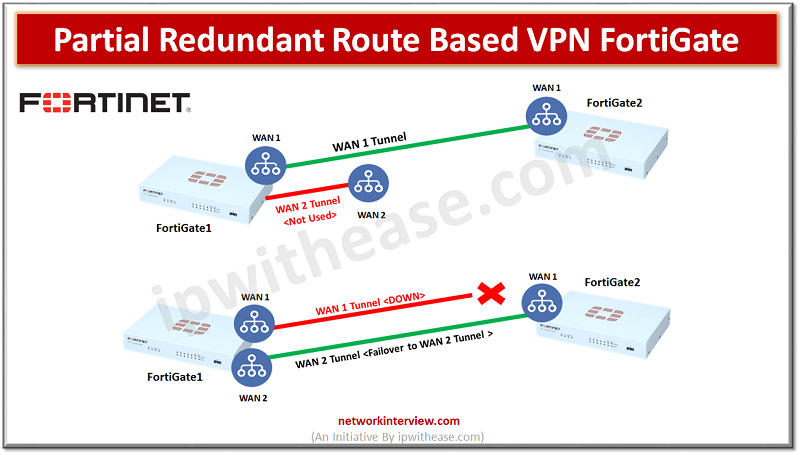
Objectives FortiGate1 has two WAN links and FortiGate2 has single WAN link Create site-to-site route based VPN with Redundant Connection Configure Dead-Peer-Detection failover Configure Link-Health Partial Redundancy is where we don’t have primary and secondary WAN connections on both peer1 …
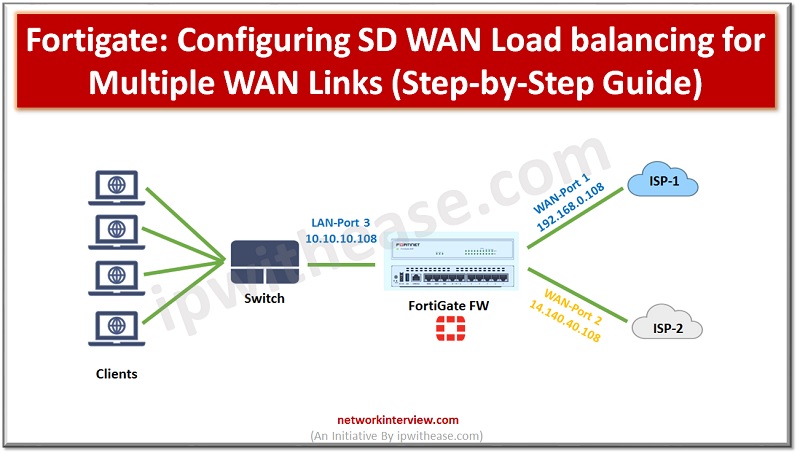
Configuring SD WAN Load balancing Below is the network setup on which we will configure FortiGate SD-WAN with load balancing for two different ISPs. Parameters which we have taken are LAN Port & Segment -> LAN Port 3 & 10.10.10.108 WAN …
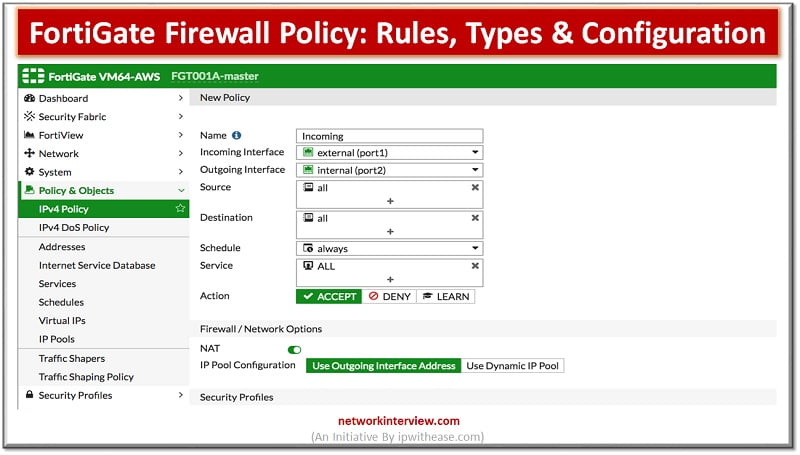
What Are Firewall Policies? Firewall policies define which traffic matches them and what FortiGate does when traffic does match, should the traffic be allowed? Initially FortiGate basis this decision on simple criteria, such as the source of the traffic then …
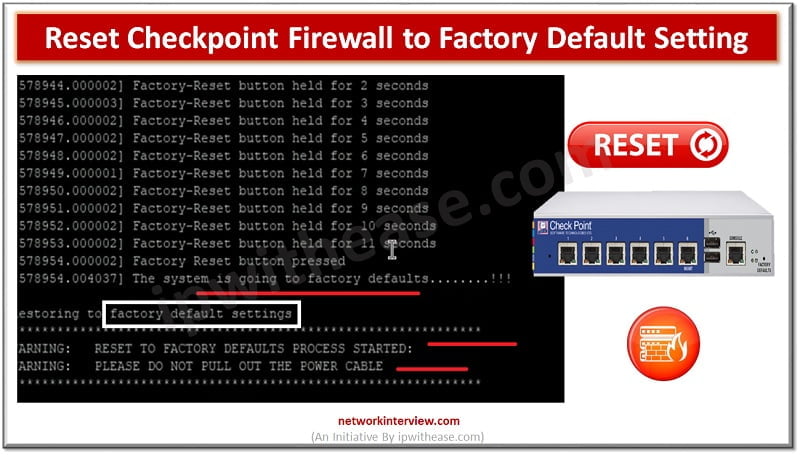
Let’s understand the difference between “Reset” and “Factory-Reset”. Reset – Admin can only wipe-out the configuration Factory-Reset/Default – Admin can wipe out the configuration of device and put the device in default operation/firmware. For Example, when you buy a Firewall, …
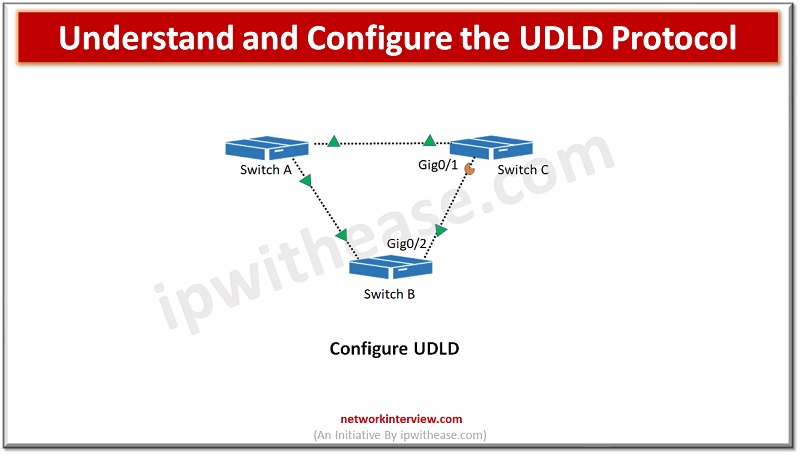
Switches are used to connect hosts on networks. Switch forwards data packets between devices using packet switching technique. Any mis-wiring or hardware faults could lead to disruption in network communication path and create serious network issues such as spanning tree …
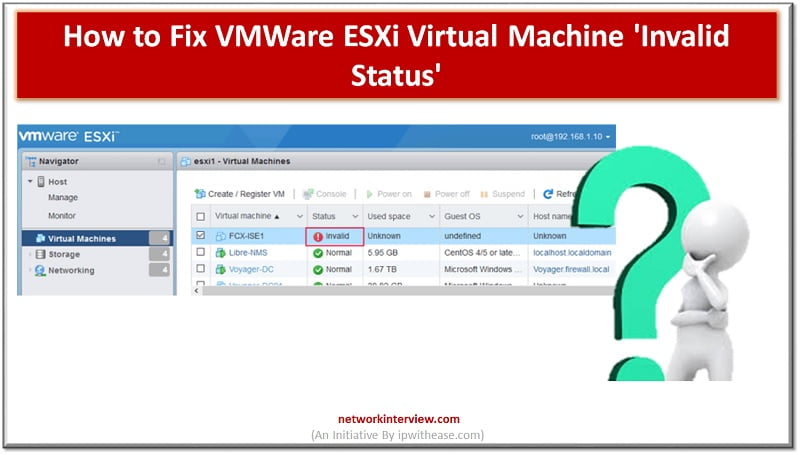
Troubleshooting VMWare ESXi Virtual Machine ‘Invalid Status’ Let’s troubleshoot VM Invalid status You can see multiple “invalid” VM machines in the image below. Here status is showing invalid. Reason of Invalid VM Machine status could be related to the storage …
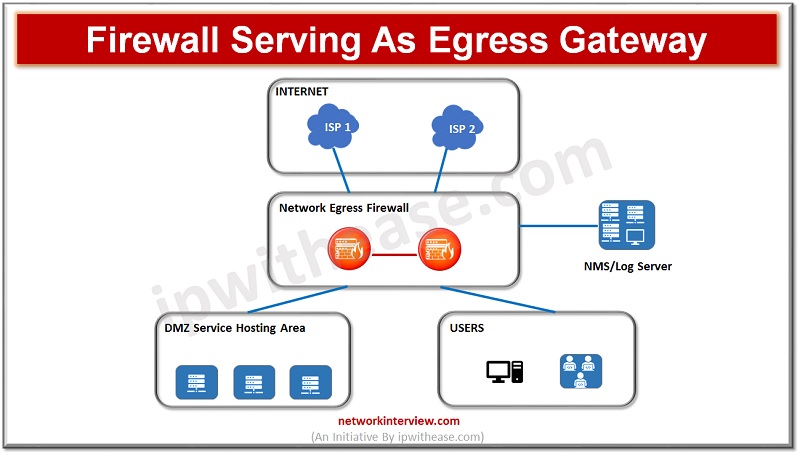
(Diagram depicting firewall acting as Egress Gateway) As enterprises are moving onto cloud their critical business applications, infrastructure services and use of hybrid clouds have evolved, secure networking is the demand of time along with performance and scalability of networks …
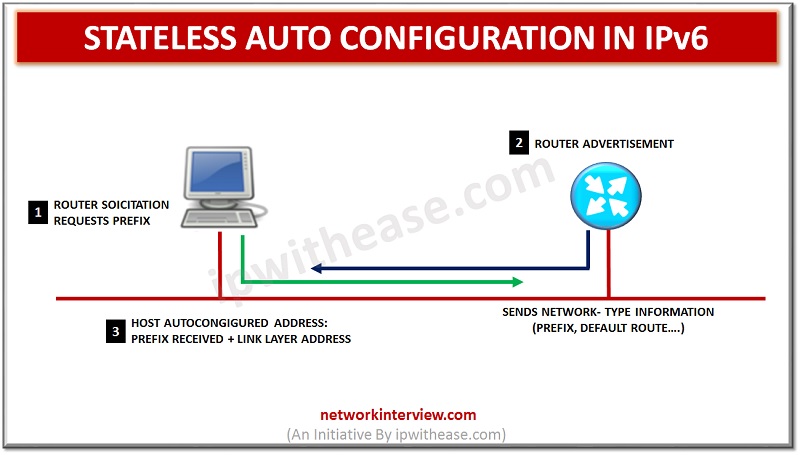
IPv6 Stateless Autoconfiguration enables a local link address which allows the user to access the internet from anywhere. No intermediary IP address or support is needed to be created as the DHCP server. All the devices that are connected with …
Introduction to Packet Capturing Before discussing Palo alto packet capture, let’s first understand the term packet capture. Packet capture is network interception of data packet which can be analysed , downloaded, archived or discarded. The reason for packet capturing is …
Introduction Palo Alto has been considered one of the most coveted and preferred Next generation Firewall considering its robust performance, deep level of packet inspection and myriad of features required in enterprise and service provider domain. When troubleshooting network and …
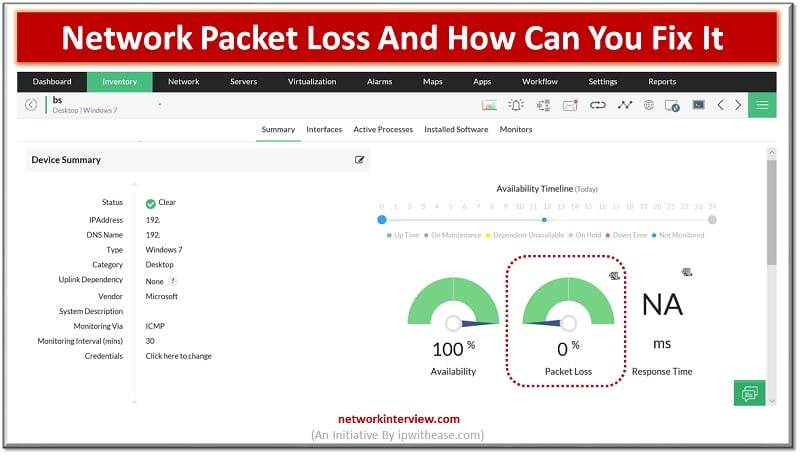
Packet loss causes a multitude of network performance issues, including slow performance, disruption, and in some cases, even loss of connectivity. These issues inevitably affect productivity and have a noticeable effect on business, which is why they need to be …
As a Website owner or website developer, you must be used to HTTP or any other types of errors. Infact, its basic nature that you will be startled on selling an error code for the first time. Are you the …
Google Account Recovery Today nearly 1.5 billion people use Google Accounts and its services. Google has become a part of our life and most of us are depending on it for work and personal use. Whoever you are, you can …
Introduction to Packet Capture “Packet Capture” is defined as network interception of a data packet that is traversing a specific point through a data network. These kind of packets are captured using appropriate tools in real time which are stored …
NSLookup Command NSLookup Overview NSLookup (Name Server Lookup). NSlookup is a simple but very practical command-line tool which is used to find DNS records, or in other words, IP address that corresponds to a host or the domain name that …
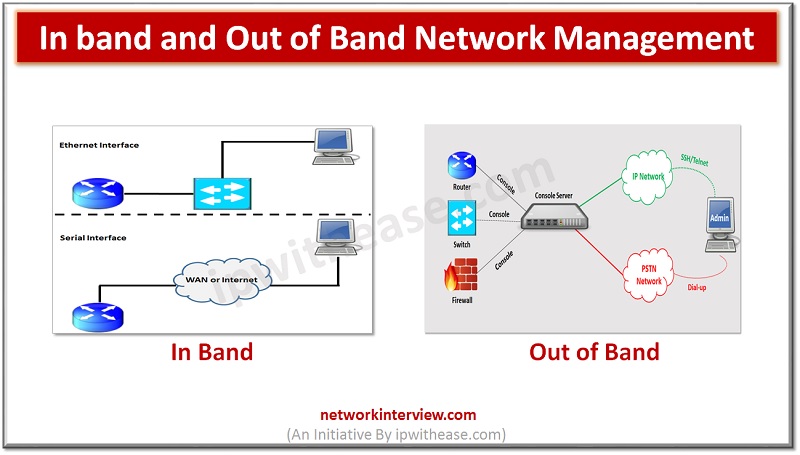
In this post, we will discuss about In band and Out of Band Network Management. The sequential order of subtopics is enlisted as below – Topics Understanding of Network Management In-band management Out-of-Band Management Comparison of In-band and Out-of-Band Management …
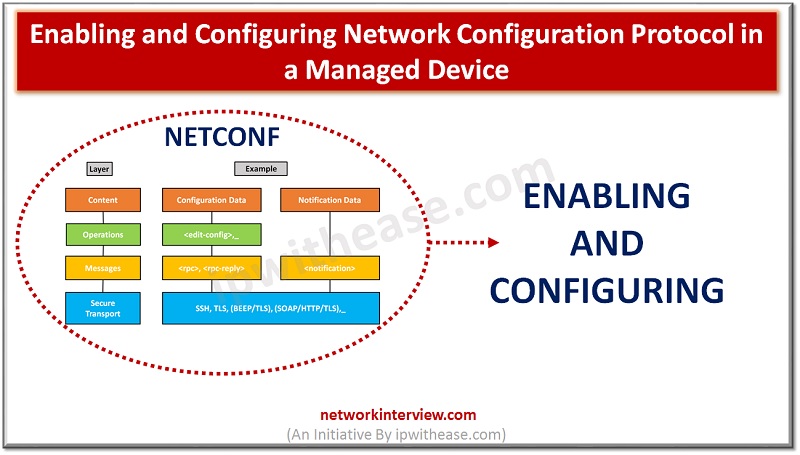
Enabling and Configuring Network Configuration Protocol NETCONF is a protocol that can manage, configure and install new configuration to network device. Its operations are realized on top of an easy Remote Procedure Call (RPC) layer. NETCONF uses Extensible Markup Language …
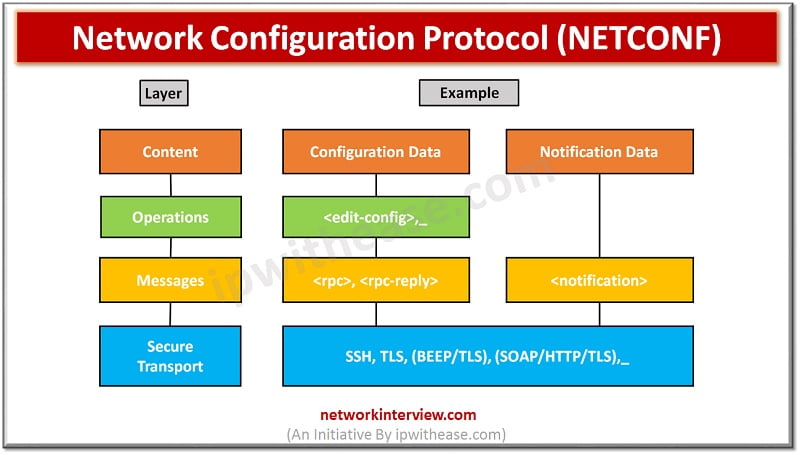
NETCONF Protocol – Network Configuration Protocol Network monitoring systems are tasked with ensuring the availability and performance of computers and network services and can detect and report on failures of devices or connections by deploying NETCONF/SNMP in device. Content of …