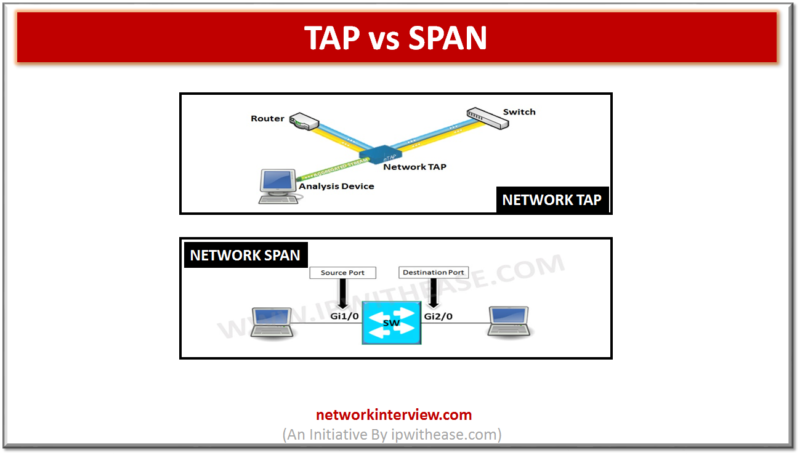
Difference between Network TAP and Network SPAN: SOURCE:https://ipwithease.com
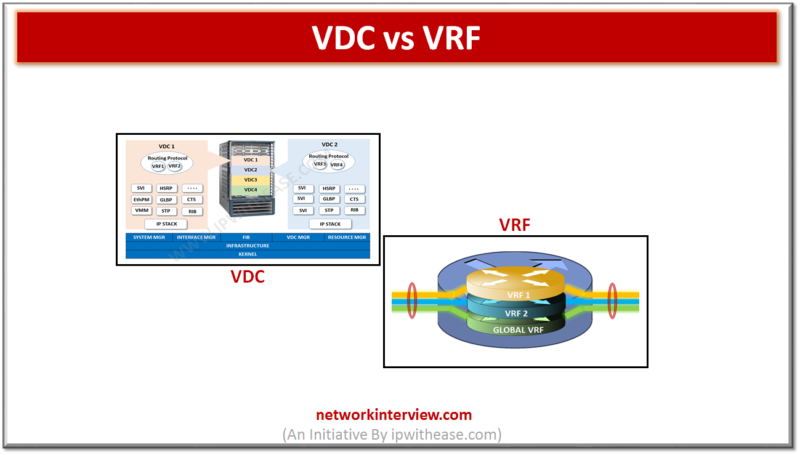
Difference between VDC and VRF: S No VDC VRF 1 A VDC virtualizes the device itself by presenting a single device as multiple logical devices. Feature which allows multiple instance of routing table to exist in a Layer 3 device …
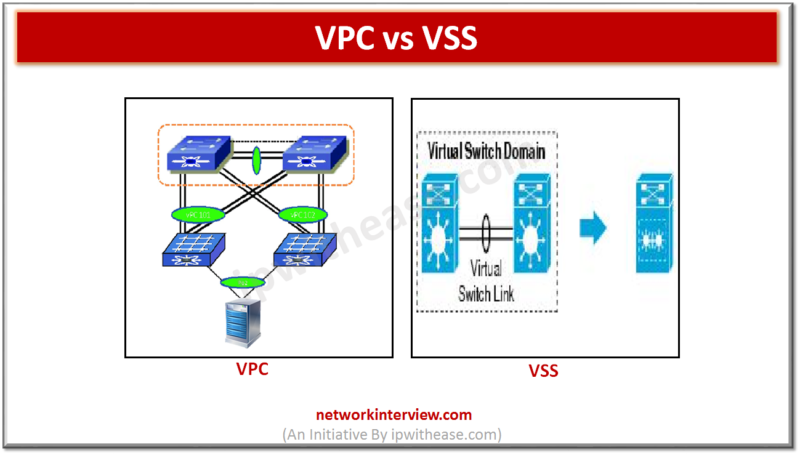
Comparison Table: VPC vs VSS SNo VPC VSS 1 Feature specific to Nexus Feature specific to catalyst 6500,4500 Series 2 Separate control plane for both switches. 2 Switches merge to form 1 logical Switch with a single control plane. 3 …
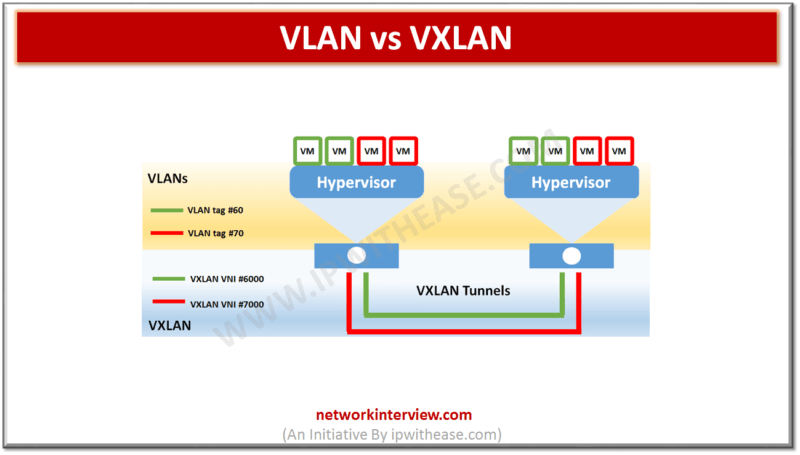
Difference between VLAN and VXLAN: Below table summarizes the differences between the two: PARAMETER VLAN VxLAN Full form Virtual Local Area Network Virtual Extensible LAN Definition Layer 2 partitioned & isolated broadcast domain in a network. Overlay tunnelling scheme where …
Difference between EIGRP and OSPF: EIGRP OSPF Advanced Distance Vector Routing protocol Link State Routing protocol Open standard(informational). EIGRP was converted to open standard in 2013. Open standard of IETF, supported by most vendors. Fast sub-second convergence Slower convergence than …
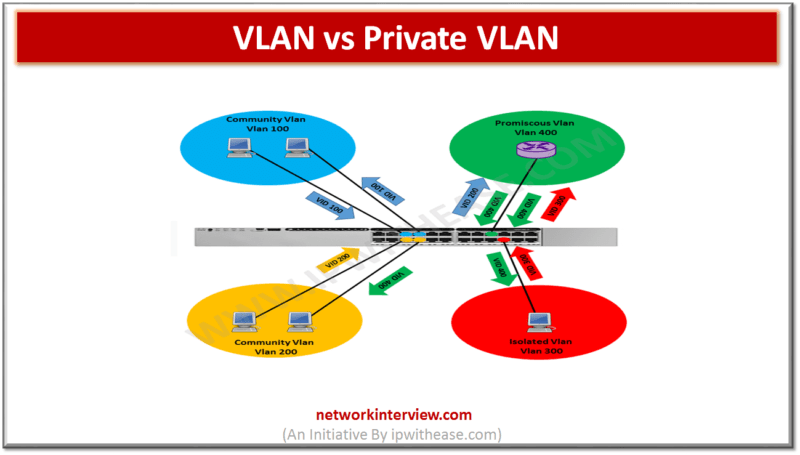
Difference between VLAN and Private VLAN: S No. VLAN PRIVATE VLAN 1 Different Vlans must belong to different IP subnets. PVLANs belong to the same IP subnet 2 Vlan works in Layer 2 and Layer 3 PVLAN is method to …
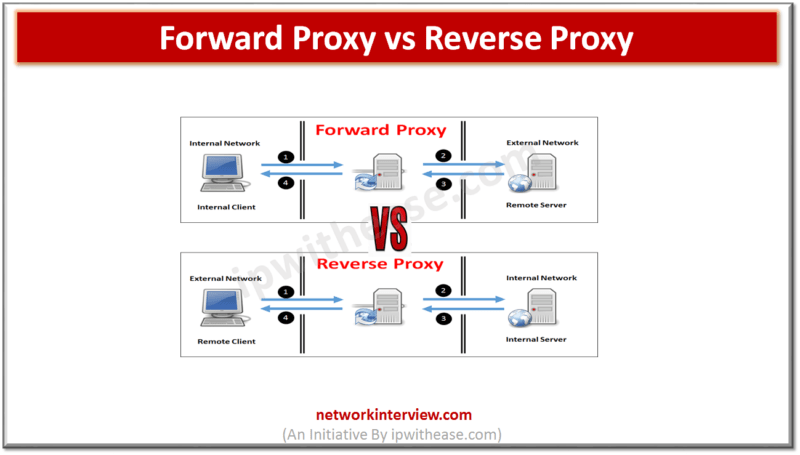
Difference between Forward Proxy and Reverse Proxy: SOURCE:https://ipwithease.com
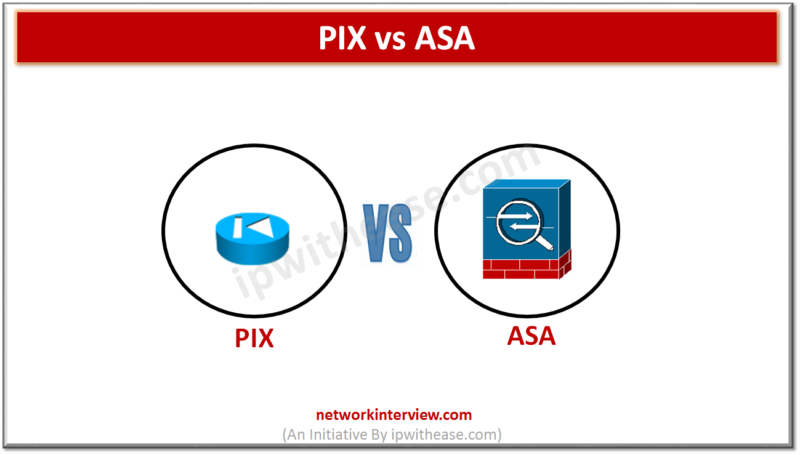
Comparison Table: Cisco PIX vs Cisco ASA Below table describes the difference between Cisco PIX and Cisco ASA firewalls: S No Cisco PIX Cisco ASA 1 Firewall appliance Is firewall and anti-malware security appliance 2 Physical Appliance Physical and Virtual …
Comparison Table: SNMP vs Syslog Below table summarizes the main differences between SNMP and Syslog: S.No. SNMP SYSLOG 1 SNMP allows for remote monitoring of SNMP-Allowable device on network. SYSLOG is a different protocol that can be used for exchanging …
Comparison Table: Li-Fi vs Wi-Fi Below table summarizes the difference between Li-Fi and Wi-Fi: FEATURE / PARAMETER LI-FI WI-FI Technology IrDA compliant devices WLAN 802.11a/b/g/n/ac/ad standard Operating Frequency 10,000 times frequency spectrum of radio 2.4 GHz , 4.9 GHz and …
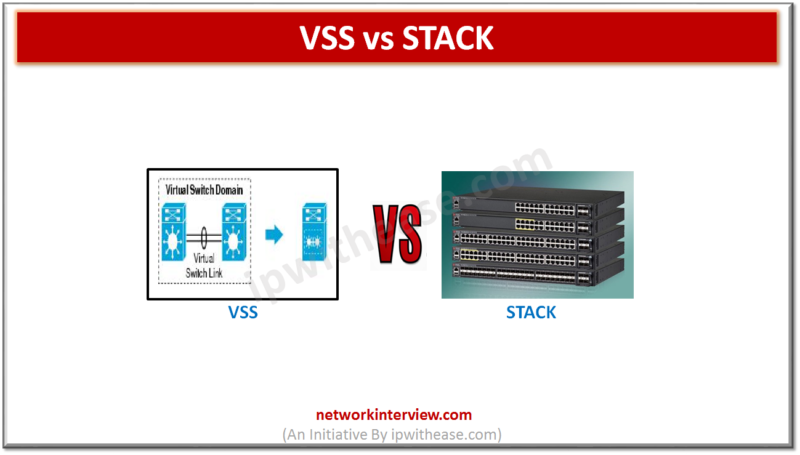
Comparison Table: Stack vs VSS Below table describes the difference between Stacking and VSS: FEATURE STACKING VSS Cabling Uses Proprietary Cabling Uses 10G Interfaces Distance Supported Limited by distance VSS members can be in geographically distant locations Chassis members Scalable …
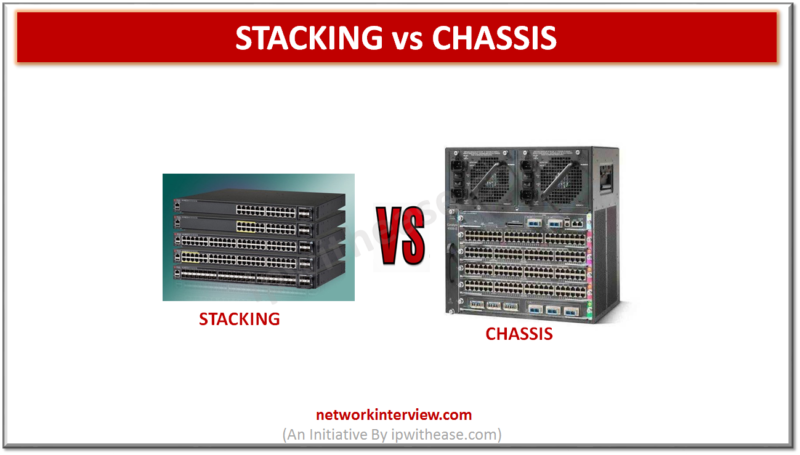
Comparison Table: Stacking vs Chassis Below table describes the difference between Stacking and Chassis: PARAMETER STACKING CHASSIS Cost Less Expensive More Expensive Ease of Redeployment Easier to resize or redeploy Not easy to resize or redeploy Placement Preferably at Access …
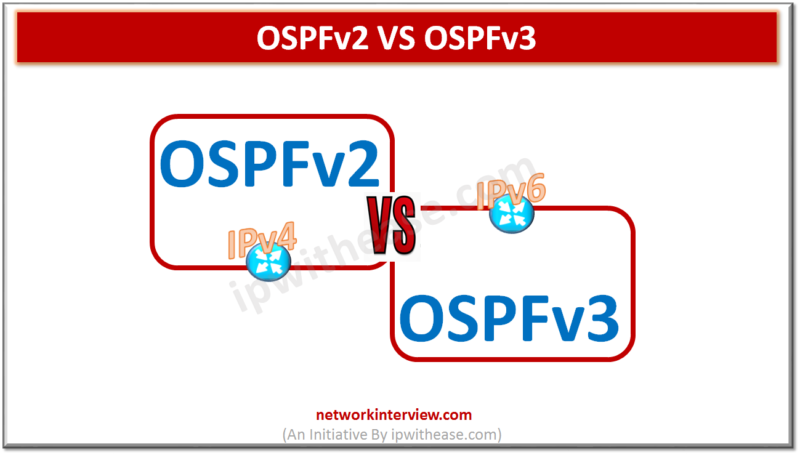
Difference between OSPFv2 and OSPFv3 Below table summarizes the differences between OSPFv2 and OSPFv3: PARAMETER OSPFv2 OSPFv3 Routed Protocol Support IPV4 IPV6 OSPF multicast all routers IP address 224.0.0.5 FF02::5 OSPF DR and BDR multicast IP address 224.0.0.6 FF02::6 Support …
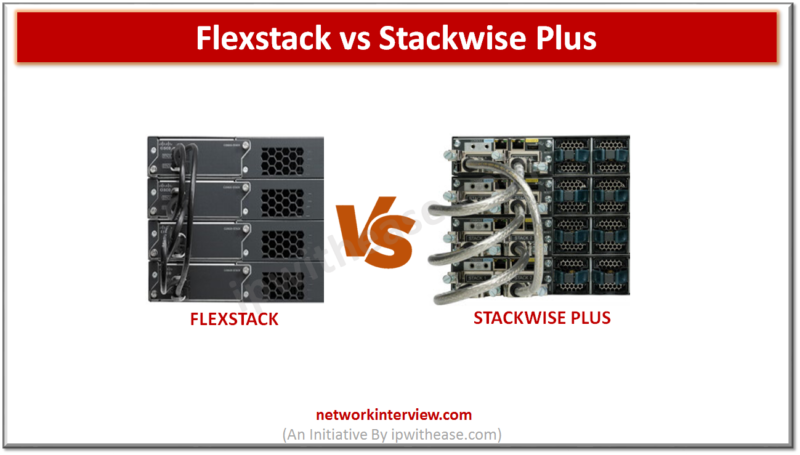
Difference between FlexStack and Stackwise Plus : SOURCE:https://ipwithease.com
Difference between BGP Hard Reset and Soft Reset: PARAMETER HARD RESET SOFT RESET Philosophy This will tear down the TCP connection between the peers and re-establish the connection with a BGP Open message and proceed with the regular message exchanges …
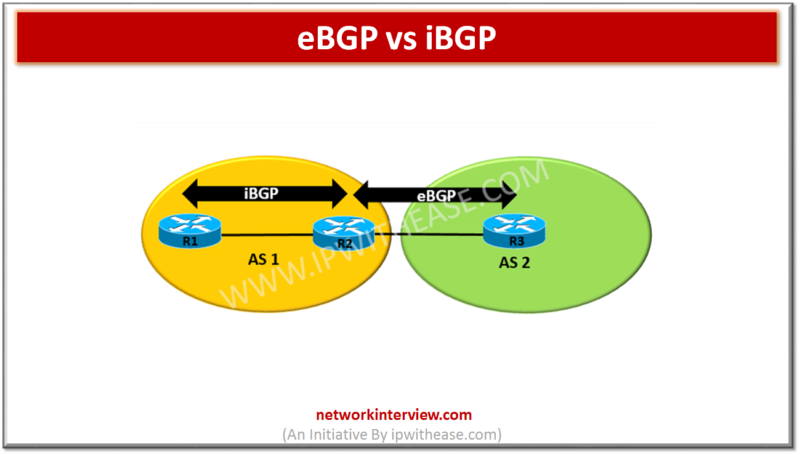
Before discussing eBGP vs iBGP, let’s understand the two protocols briefly. eBGP It is abbreviation for External Border Gateway Protocol and is one of the flavors of BGP protocol. eBGP Routing protocol is used between BGP speaking neighbors which belong …
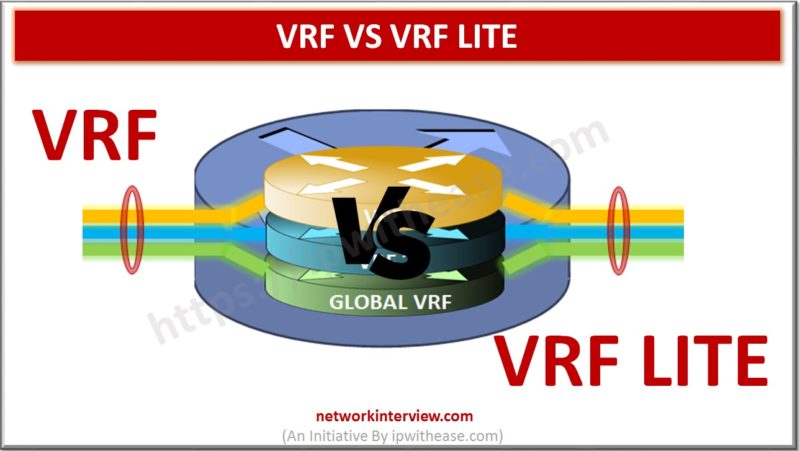
Below table describes the difference between VRF and VRF Lite: VRF VRF Lite MBGP VPNv4 or MPLS required for running full VRF. VRF-lite is a subset of the MPLS VPN functionality. It supports only the VRF related functionality (no MBGP …
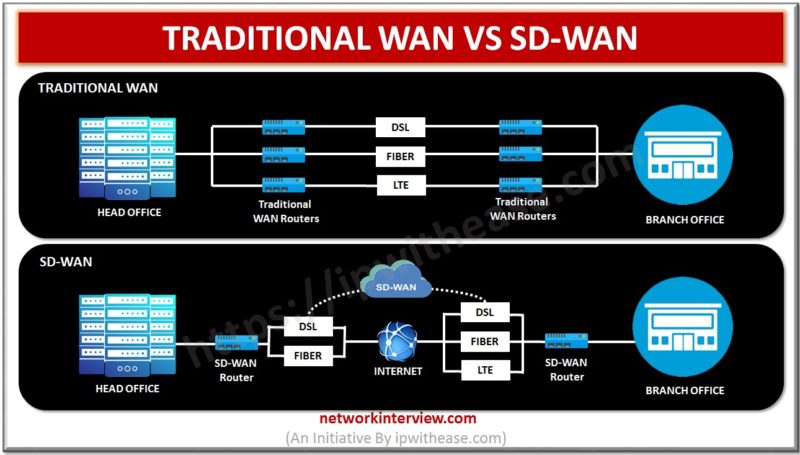
Difference between Traditional WAN & SD WAN Below table summarizes the difference between Traditional WAN and SD WAN technologies: PARAMETER TRADITIONAL WAN SD WAN Bandwidth Crunch When Bandwidth chokes due to high utilization by users or applications , following is …
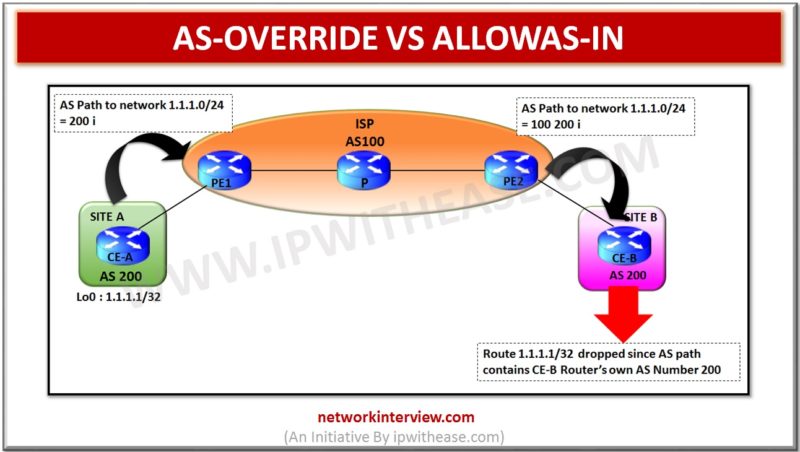
Below table describes the difference between AS-OVERRIDE and ALLOWAS-IN; PARAMETER AS-OVERRIDE ALLOWAS-IN Overview Used by PE to modify the AS Path so that prefix is not dropped based on BGP default behaviour to disallow its own AS number in the …
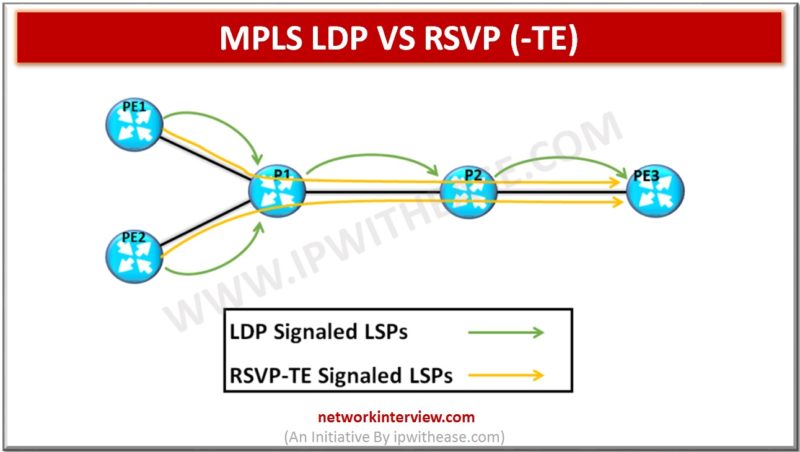
Comparison Table : LDP vs RSVP Below table describes the difference between LDP and RSVP: PARAMETERS LDP RSVP Abbreviation for Label Distribution protocol Resource Reservation Protocol Provisioning Easy to configure. We just need to enable on interfaces. Label bindings automatically …
Comparison Table : RD vs RT in MPLS Below table describes the difference between RD vs RT in MPLS: PARAMETER RD RT Abbreviation for Route Distinguisher Route Target Definition 64-bit identifier prepended to IPv4 route used to identify VPN the …
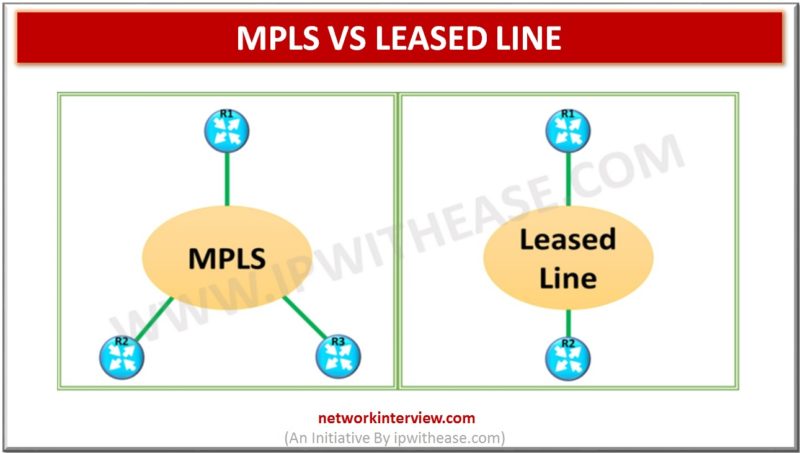
Comparison Table: MPS vs LEASED LINE Below table describes the difference between MPLS and Leased Line: PARAMETER MPLS LEASED LINE Segregation of customer traffic Logical separation of customer traffic. Physical separation of customer traffic Connectivity Type Multipoint or point-to-Point Point-to-Point …
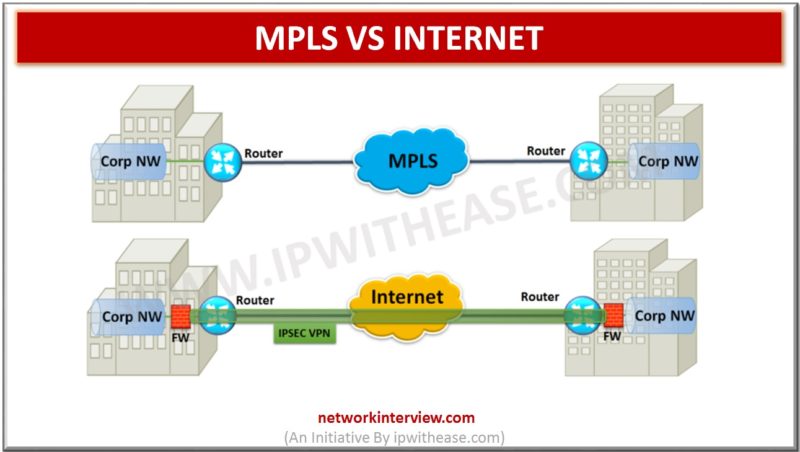
Comparison Table : MPLS vs INTERNET Below table describes the difference between MPLS and Internet: PARAMETERS MPLS INTERNET Carriers Single carrier provides MPLS connectivity for all the locations Not limited to single carrier. Different locations can be connected through various …
Comparison Table: MPLS vs VPN Below table describes the difference between MPLS and VPN: PARAMETER MPLS VPN Scope of Operation Operates on carrier provided Network (Logically segregated to support multiple customers) that will further connect to all customer sites. Operates …
Comparison Table: MPLS vs SD-WAN Below table describes the difference between MPLS and SD-WAN: PARAMETER MPLS SD-WAN Abbreviation for Multiprotocol Label Switching Software Defined – Wide Area Network Provisioning time High Very low Configuration Manual Configuration “Zero Touch provisioning” allows …
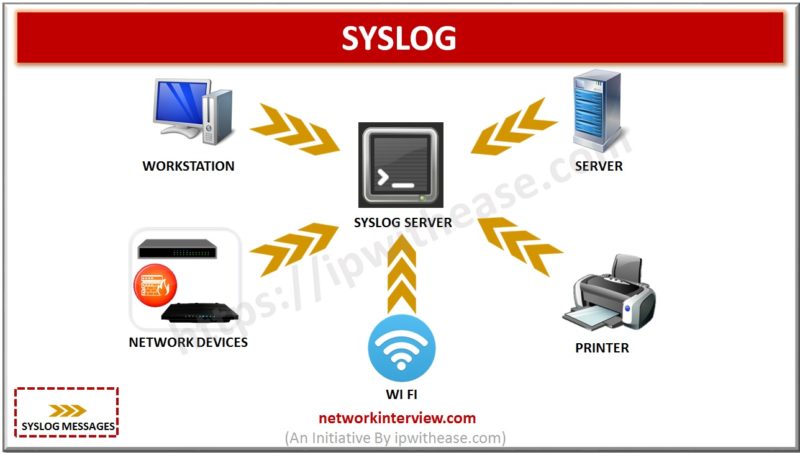
Syslog is a method to collect messages from devices to a server running a syslog daemon. Logging to a central syslog server helps in aggregation of logs and alerts. Cisco devices can send their log messages to a Unix-style SYSLOG …
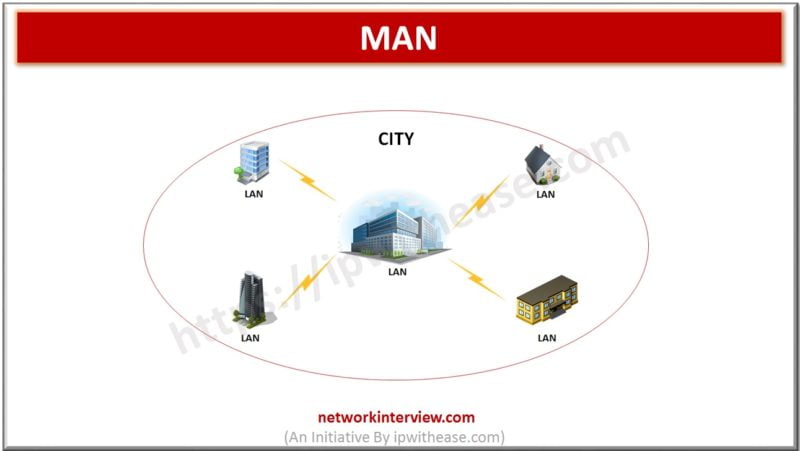
Introduction Computer Networks can be divided into various types depending upon their size and usability. The size of a network can be assessed by its geographical distribution. It can be as small as a room with a few devices/computers or …
Introduction Computer Networks can be divided into various types depending upon their size and usability. The size of a network can be assessed by its geographical distribution. It can be as small as a room with a few devices/computers or …
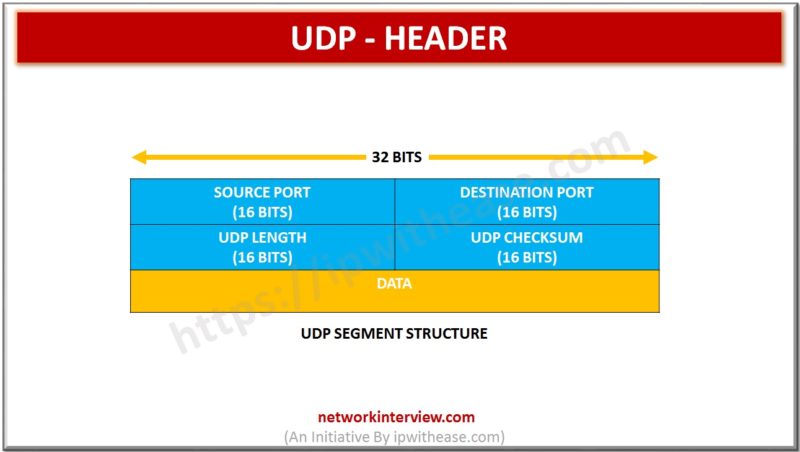
UDP HEADER It consists of four fields each of 2 bytes in length – Source Port(16 bits) – This field identifies the sender’s port. Cleared to zero if not used. Destination Port(16 bits) – This field identifies the receiver’s port. …
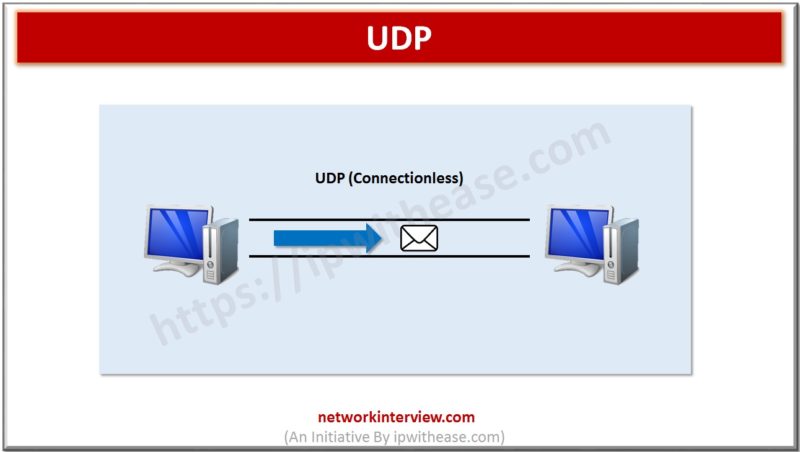
UDP (User Datagram Protocol) is a transport layer protocol used primarily for low-latency and loss tolerating connections. Outlined by RFC 768 it provides a best-effort datagram service to an end host.In distinction to TCP, UDP just sends the packets with no packet acknowledgements that ends up into much lower bandwidth overhead and latency. However …
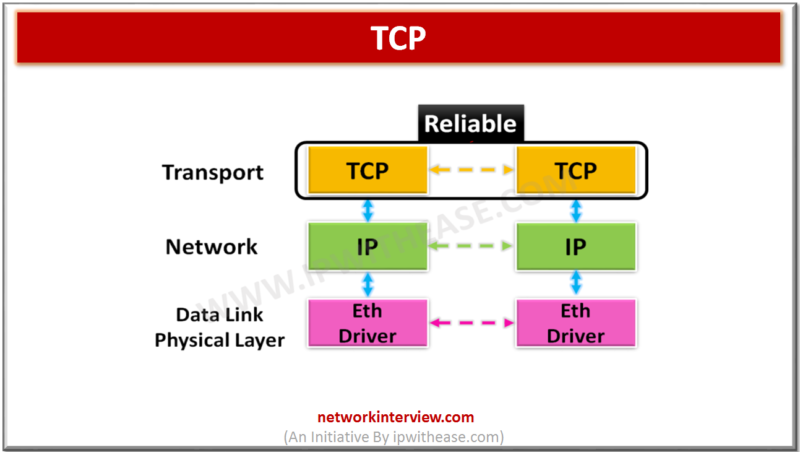
TCP i.e.Transmission Control Protocol is one of main Transport Layer protocol which provides reliable, connection-oriented communication over IP networks between two end stations. When data is provided to the IP protocol, it encapsulates them in IP datagrams. TCP is defined by the …
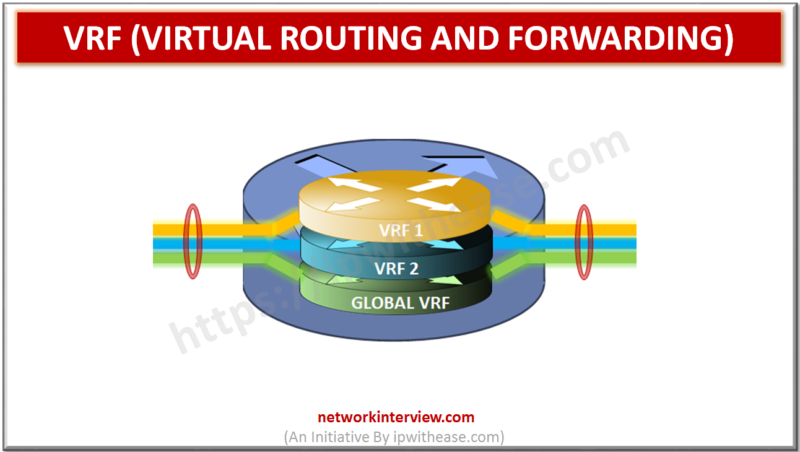
VRF (Virtual routing and forwarding) is a technology that allows multiple instances of a routing table to co-exist within the same router at the same time. Overlapping IP addresses can be used without conflicting with each other as the routing …
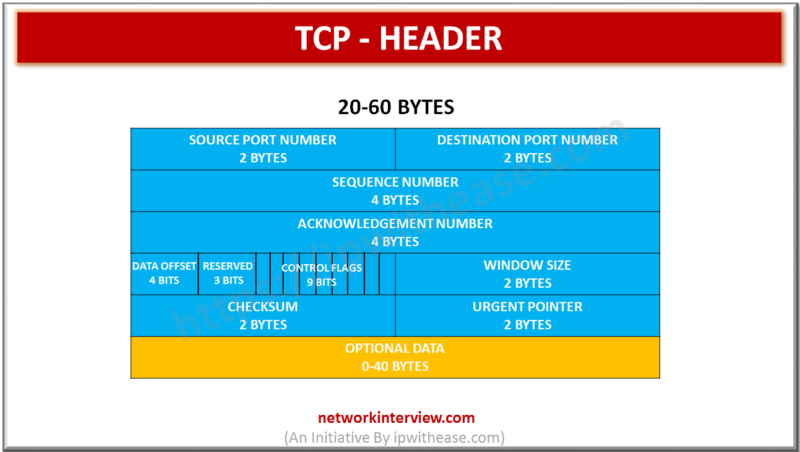
TCP HEADER (Transmission Control Protocol ) Source port (16 bits): Port related to the application in progress on the source machine Destination port (16 bits): Port related to the application in progress on the destination machine Sequence number (32 bits): When the …
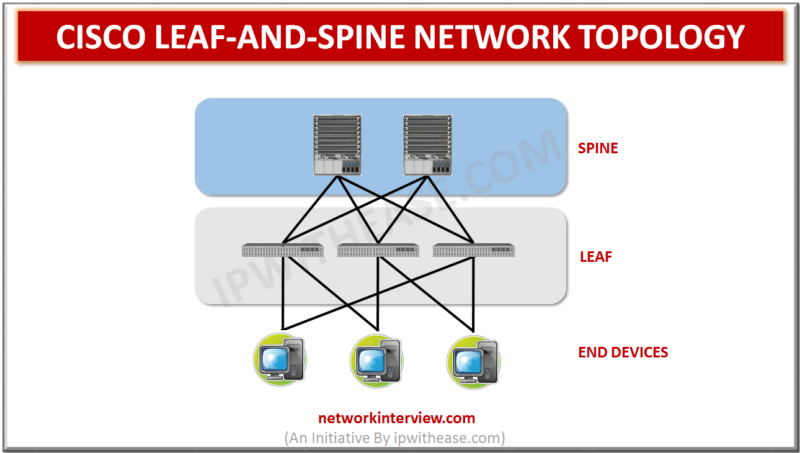
Network Topology Leaf-and-spine is a two-layer network topology composed of leaf switches and spine switches. We are all aware of the Cisco’s 3-tier network topology with the following 3 layers – 1)Access Layer 2)Aggregation/Distribution Layer 3)Core layer The Access Layer …
Introduction to WAN Computer Networks can be divided into various types depending upon their size and usability. The size of a network can be assessed by its geographical distribution. It can be as small as a room with a few …
Introduction to LAN Computer Networks can be divided into various types depending upon their size and usability. The size of a network can be assessed by its geographical distribution. It can be as small as a room with a few …
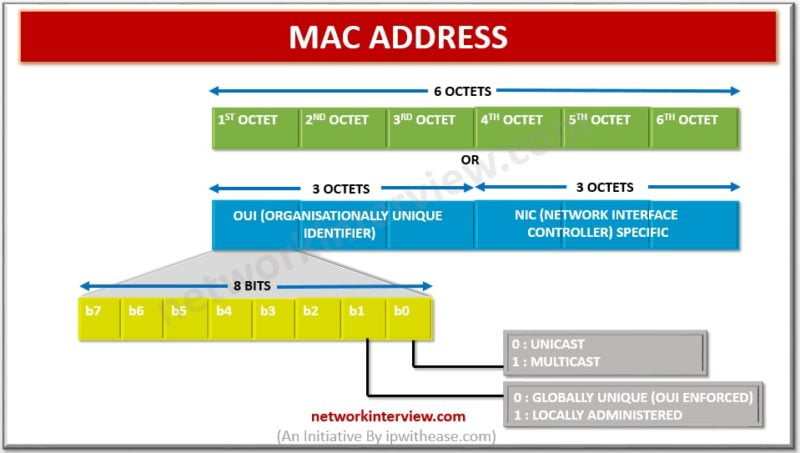
MAC (Media Access Control) Address The MAC address is used by the Media Access Control sublayer of the Data-Link Layer (DLC) of telecommunication protocols. Every NIC (also called LAN card) has a hardware address that’s known as a MAC, for Media Access Control. …
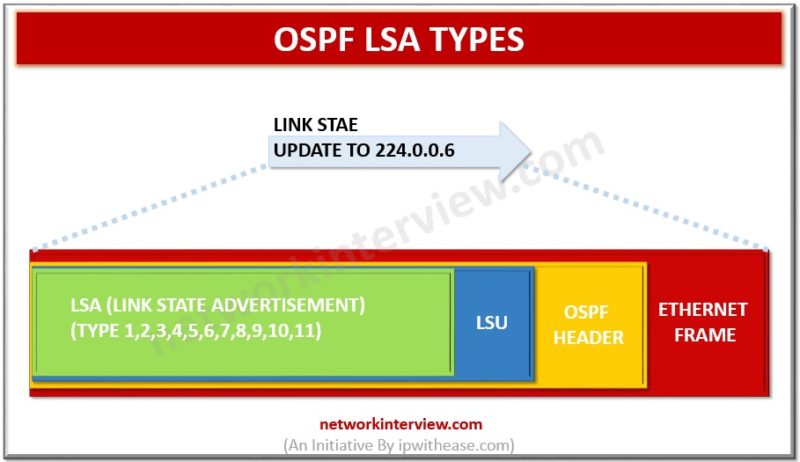
OSPF uses LSAs or Link state Advertisements to share information of each network and populate the LSDB (Link State Database). The main LSA types are : LSA Type 1 (Router LSA):generated by each router for each area it is located. …
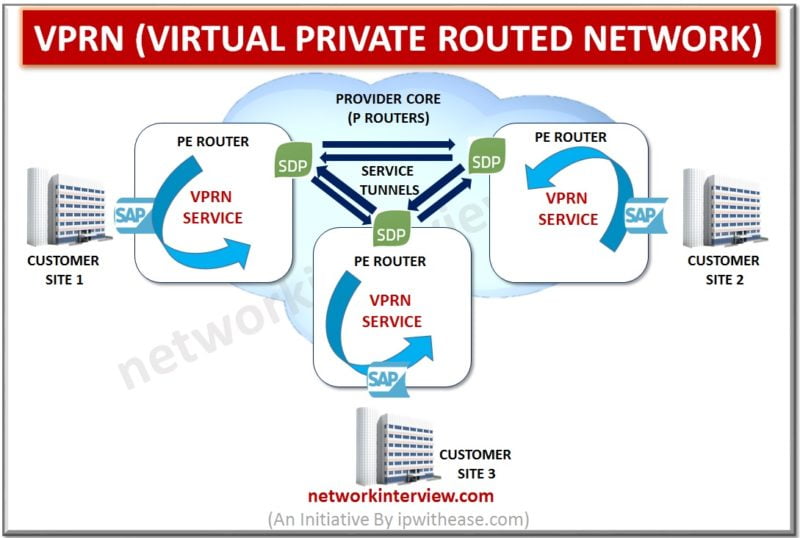
VPRN (Virtual Private Routed Network) is a Multipoint-to-Multiponit Layer 3 VPN Service that connects multiple branches in a single logical routed architecture over IP/MPLS network of a Service Provider. This is called Layer 3 VPN generally, but Alcatel-Lucent define this Layer 3 VPN as VPRN(Virtual Private Routed …
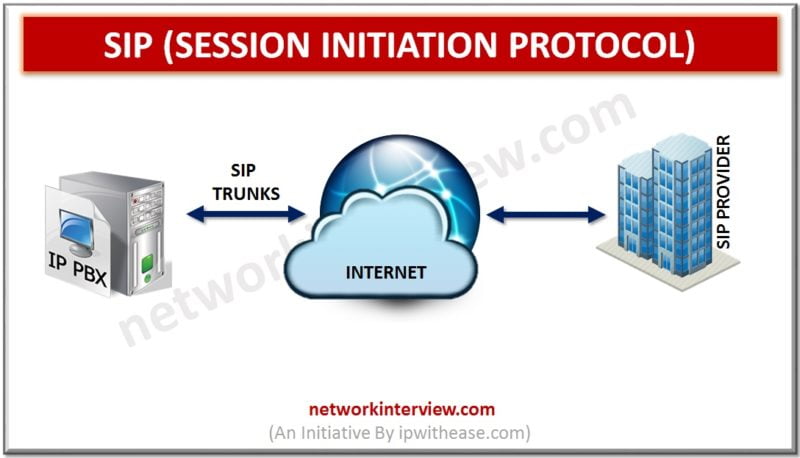
SIP i.e. Session Initiation protocol is an open source protocol. It communicates on TCP or UDP on port numbers 5060 or 5061. SIP has got a range of different messages with each having lot of additional data, thus making it …