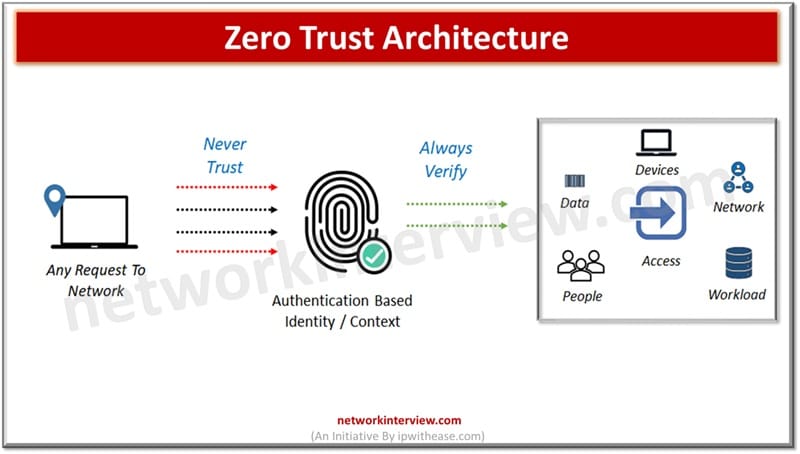
Since organizations are moving away from the traditional IT landscape to cloud computing, cloud-based assets, remote working models, the perimeter based old and traditional model of security is not sufficient enough for protection of data and sensitive systems. The modern …
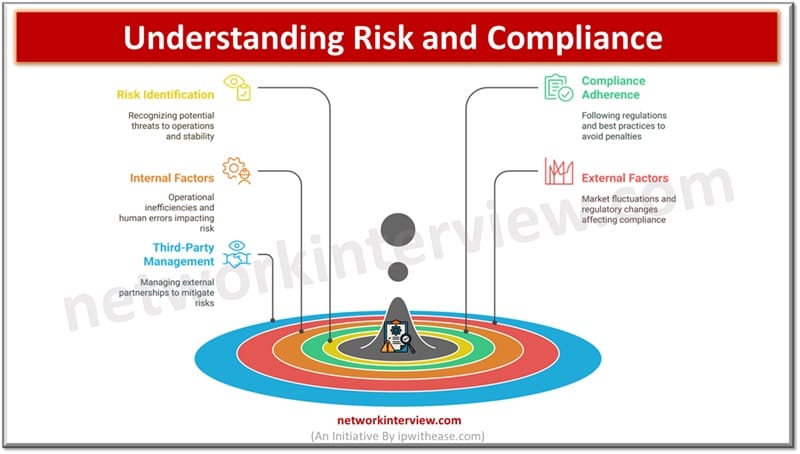
In today’s fast paced world, organizations are facing a lot of pressure to comply with regulatory standards, manage their risks effectively including third-party induced risks and protect organization’s sensitive data. With the constantly evolving cyber threat landscape and rising compliance …
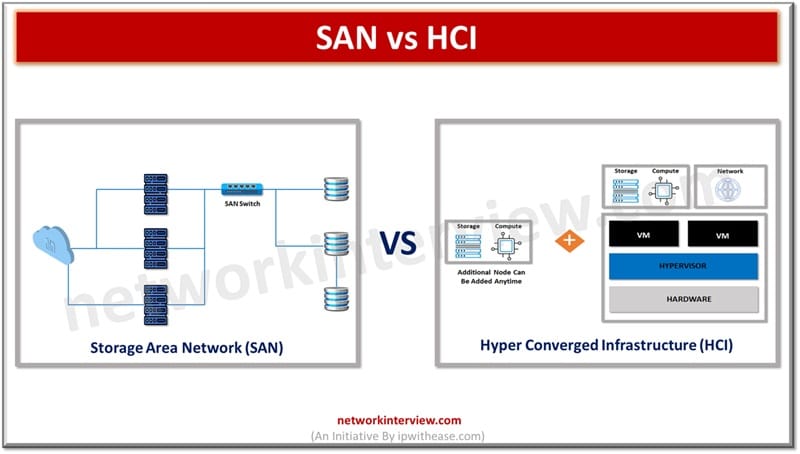
Today’s enterprises demand high speed data access with high volumes of data storage. Storage area network and Hyper Converged infrastructures provide solutions for compute, storage and networking and move past the hardware-based infrastructure limitations to more flexible software-based infrastructure. They …
With increased penetration of cloud computing, AI, machine learning cyber security incidents are on rise. Organizations are working towards reduction of risks associated with new upcoming technologies and trying to strike a balance between business growth and data security. Third …
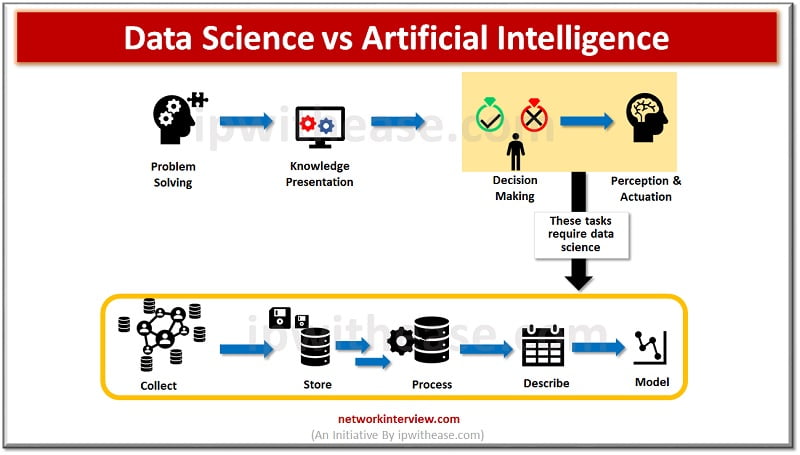
In the last couple of years there has been an explosion of workshops, conferences and symposia , books, reports and blogs which talk and cover the use of data in different fields and variations of words coming into existence such …
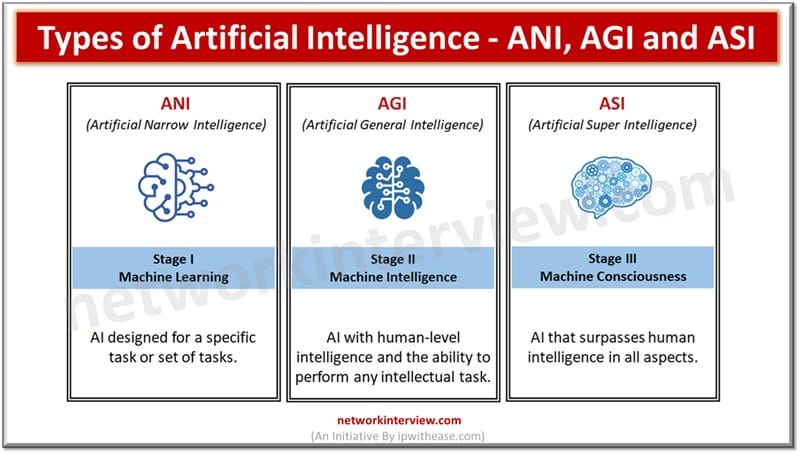
In this 21st century, humans rely more on machines than any other thing. So it is important to know about the important technologies that make the machines reliable. Yes, they are automation and artificial Intelligence. Automation has been among humans …
In today’s business space organizations are facing innumerable challenges which impact their financial stability, operations and reputation. Governance, risk and compliance is a methodology and structure which organizations are using to manage risks and address cyber security threats. It also …
Troubleshooting Palo Alto packet flow issues can be complex. In this blog, we will discuss some common Palo Alto Packet Flow Troubleshooting issues and troubleshooting steps. Palo Alto Packet Flow Troubleshooting Issues 1. Incorrect Security Policies Issue: Traffic is being …
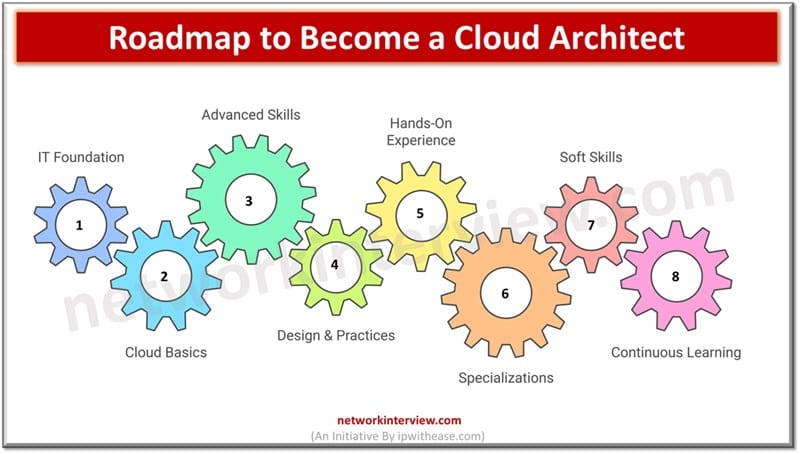
Becoming a Cloud Architect typically requires a mix of education, certifications, hands-on experience, and continuous learning. Step-by-Step Guide to Become a Cloud Architect Let’s go to the step by step roadmap to become a Cloud Architect along with the list …
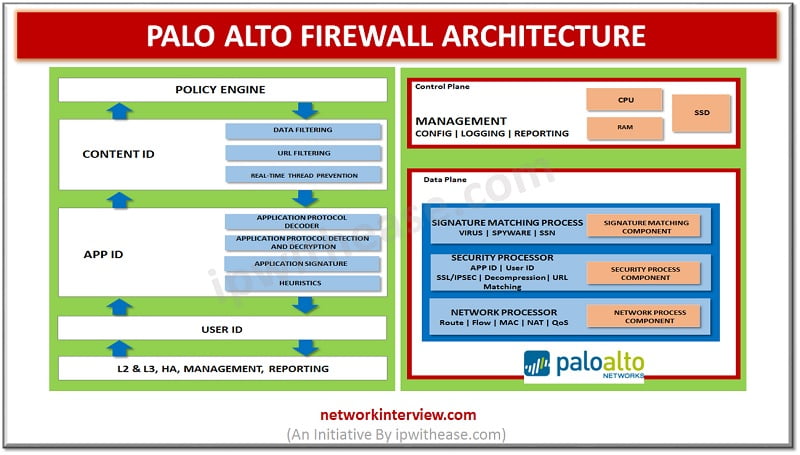
Network architecture refers to the structured approach of network, security devices and services structured to serve the connectivity needs of client devices, also considering controlled traffic flow and availability of services. Network devices typically include switches, routers and firewalls. Palo …
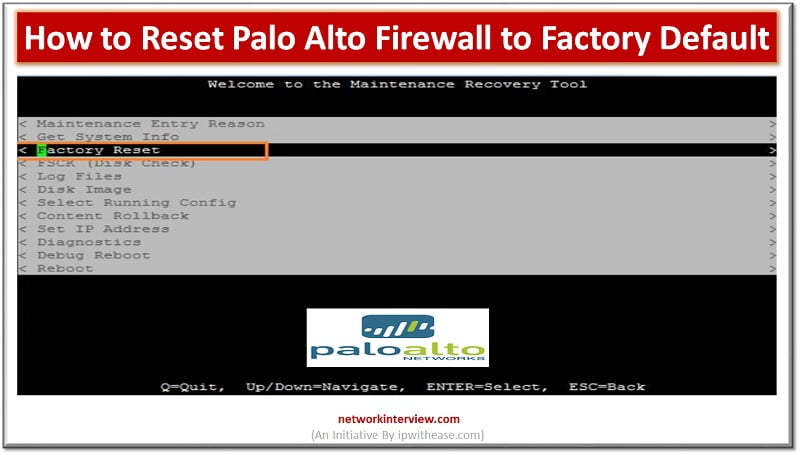
Introduction to Reset Palo Alto Firewall Firewall is a network security device which grants or rejects network access to traffic flowing between untrusted zone (External networks) to trusted (Internal networks) zone. Starting from initial days of Stateful inspection firewalls and …
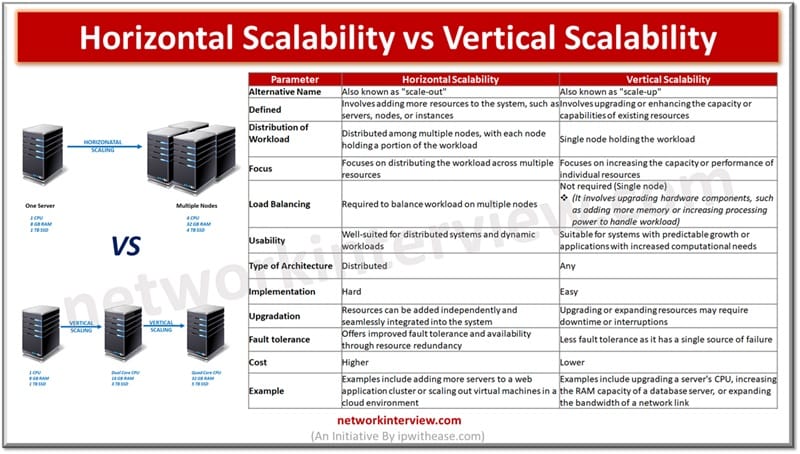
When your business starts to grow and your applications require more accessibility, power, and performance, you may need to consider either scaling up or scaling out. It’s a common question that arises, and the answer depends on your specific needs …
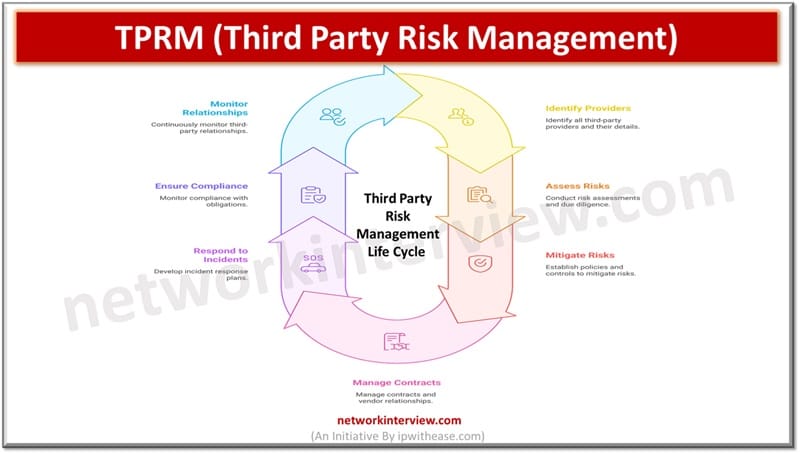
As business environments are changing rapidly third-party relationships are on boom creating a pivotal role in the business success. But it has a flip side too as a third-party introduction in your ecosystem brings a host of risks, cyber security …
Rapid adoption of cloud technology across the globe has accelerated and drastically brought changes in the way enterprises are operating now. The introduction of Artificial intelligence or ‘cognitive technologies’ across enterprises to increase productivity, efficiency and accuracy of business operations …
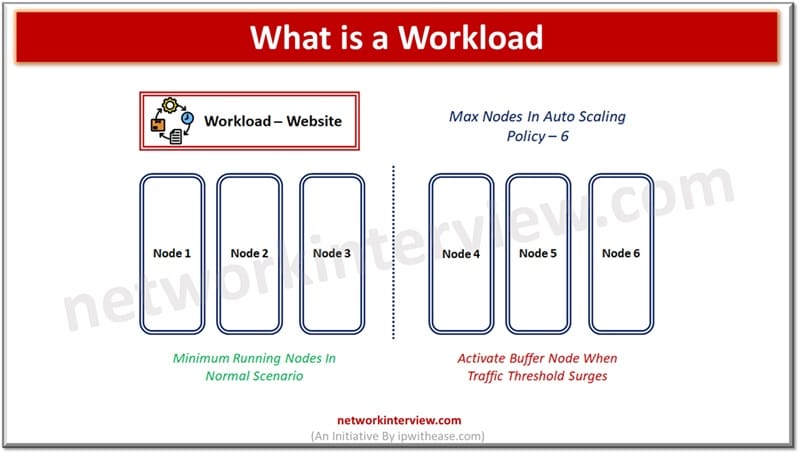
Workload terminology is generally associated with cloud computing. In cloud computing any application or service is deployed over the cloud referred to as workload which is consuming the computer (CPU, memory) and physical storage. Workload term is specifically associated with …
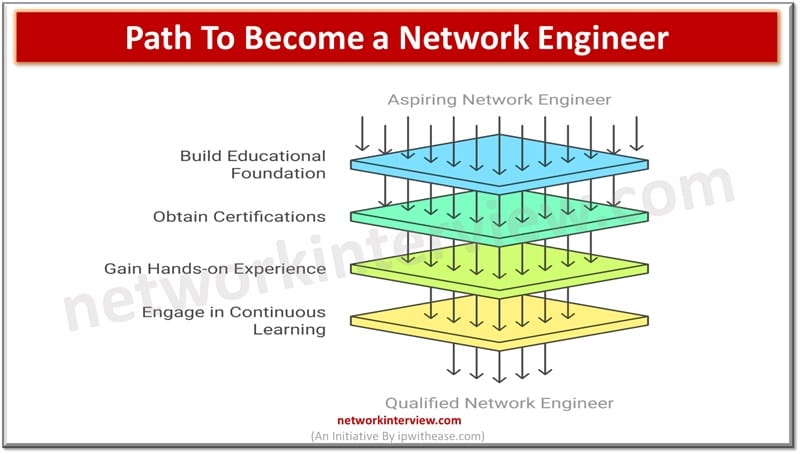
Becoming a network engineer typically requires a mix of education, certifications, hands-on experience, and continuous learning. Step-by-Step Path to become a Network Engineer Here’s a step-by-step guide to help you on the path: 1. Build a Strong Educational Foundation High …
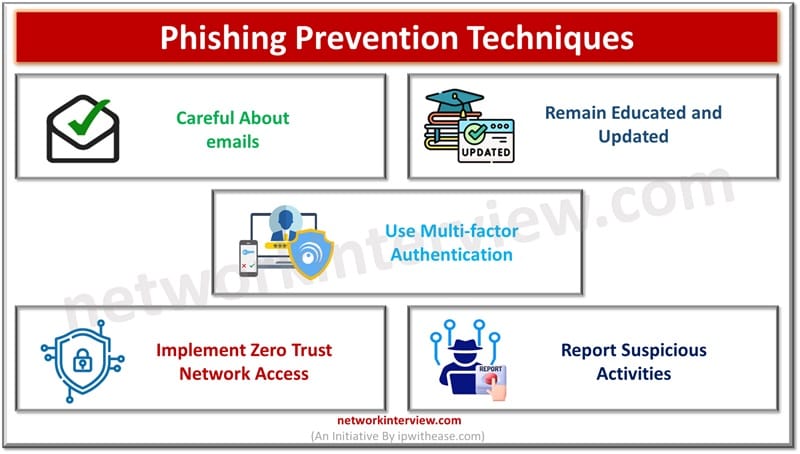
The amount and intensity of cybercrimes is growing exponentially based on social engineering techniques as humans are the weakest link in the chain of security and easy target of compromise. This is further fueled by remote operations. Most companies focus …
A resilient approach towards security and protection of digital assets is the need of the hour. The approach focuses on protection of hardware infrastructure and business applications to eliminate all vulnerabilities which could impact organizations, customers, and other stakeholders. Businesses …
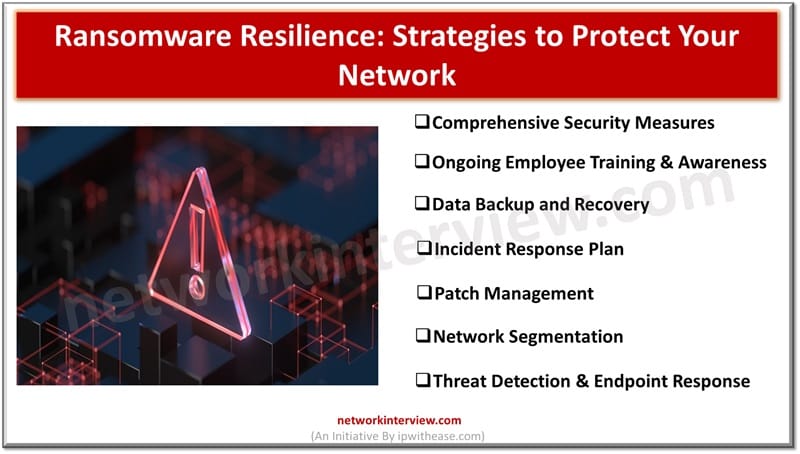
This is the era of digital dominance and ransomware threat looms largely on enterprises and individuals. It is a kind of digital arrest which has emerged as the most menacing threat in recent years. Cybercriminals have targeted businesses, hospitals, government …
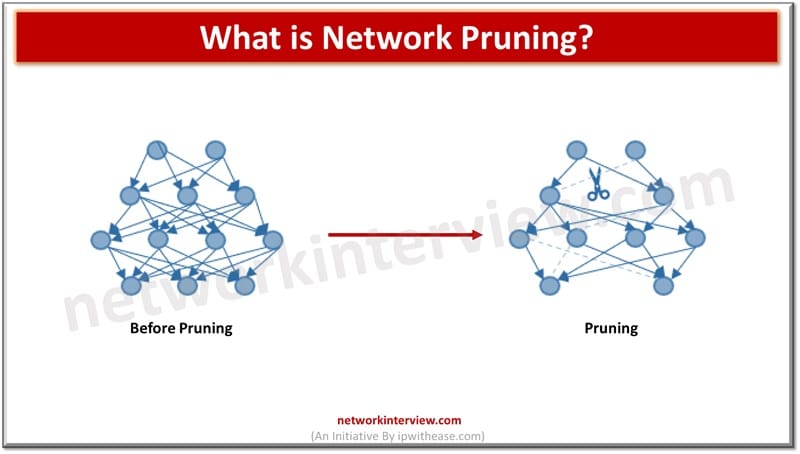
Network pruning is a process of optimizing or simplifying a network by removing unnecessary or redundant elements to improve performance, efficiency, and manageability. Here are some common network pruning techniques: Network Pruning Techniques 1. VTP Pruning VTP (VLAN Trunking Protocol) …
Robotic Process Automation Every company is dealing with increasing volumes of unstructured data and information, which makes it difficult to automate processes. There are plenty of Robotic Process Automation RPA tools that have made it easy for businesses to tackle …
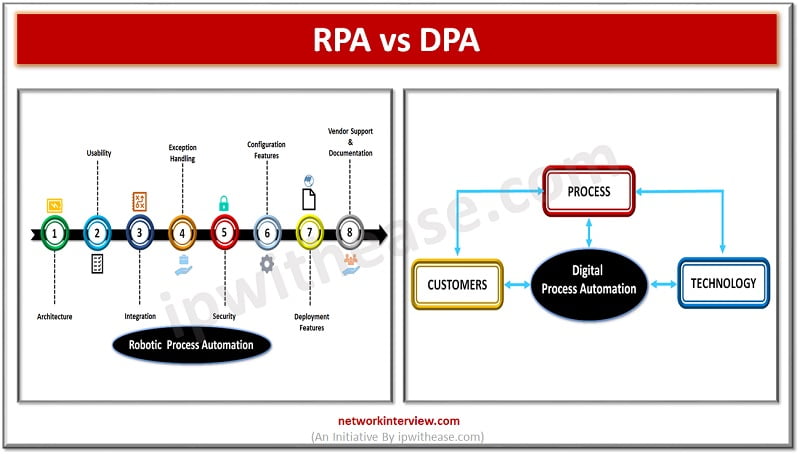
Process Automation As per Gartner prediction 72% of the enterprises will be working with Robotic process automation (RPA) in next two years and Digital process automation (DPA) is identified as major component for digital transformation with DPA market worth $6.76 …
Introduction to Software Testing When it comes to software testing, there are many different methods that you can use. Each of them has their own advantages and disadvantages, so it’s important to understand the pros and cons of each method …
Introduction to Penetration Testing Tools & Software Identifying weaker controls in systems via attack simulation help organizations to gather information about the different ways hackers can gain unauthorised access of systems and sensitive data and information or may get engaged …
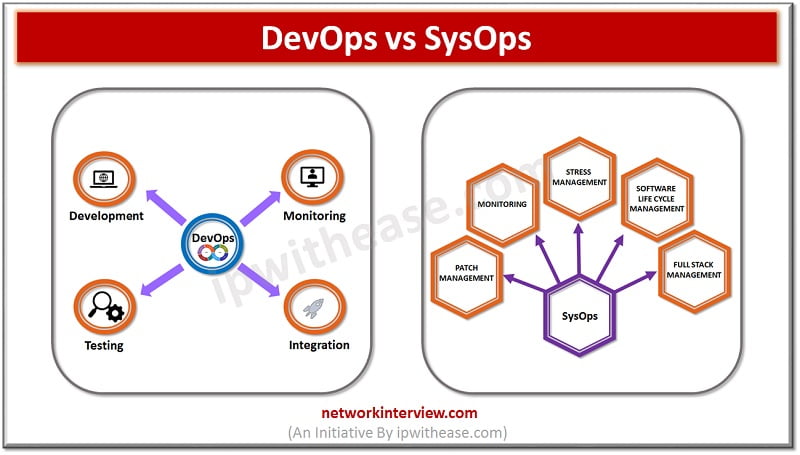
Introduction to DevOps & SysOps Technology advancements are crucial to the dynamic IT landscape in today’s times. Cloud computing has been crucial which presents excellent opportunities to business for the future. SysOps and DevOps are commonly used terminologies in cloud …
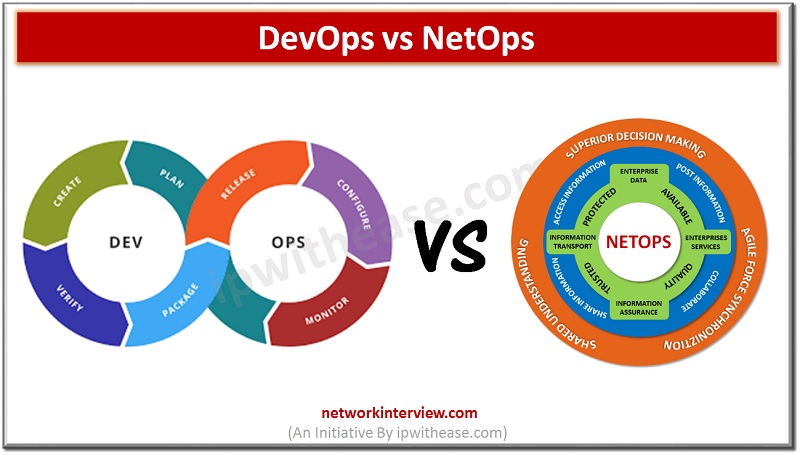
Introduction The tremendous technical development in the IT and other digital fields started the popular trend of creating acronyms with the Suffix Ops. And the word DevOps, NetOps, and SecOps are confusing IT and Tech communities further as they are …
Intoduction: Emerging Job Roles What is the difference between the Cloud Architect and DevOps Engineer? These new roles with growth of Cloud technologies has increased the confusion about roles? In this article, we will try to demystify some of concepts …
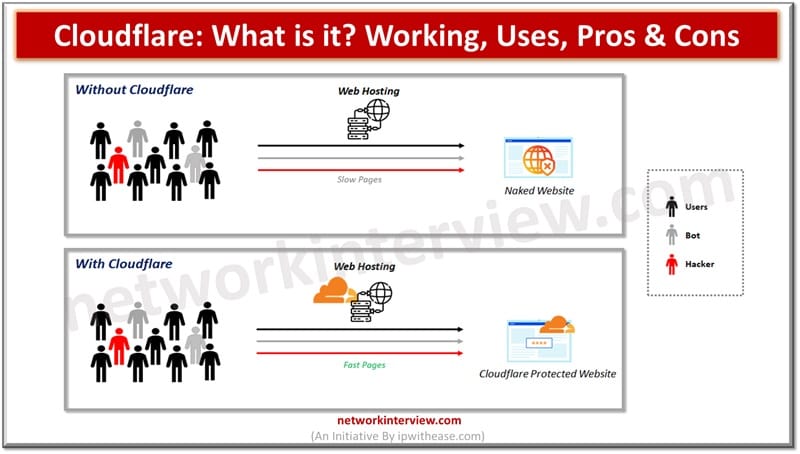
The Internet ecosystem is spanned across geographies and its users are spread around the globe. Millions of users of the Internet expect web content delivery in a speedy and efficient manner. Content delivery networks (CDNs) are called the lifeline of …
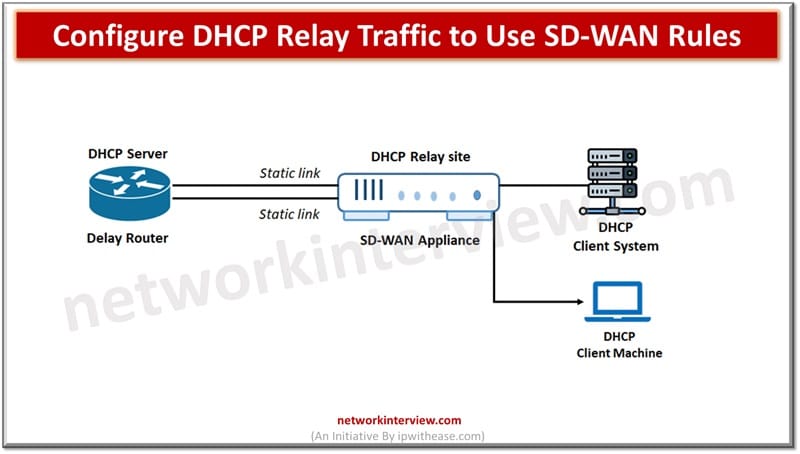
SD-WAN or software defined networking have SD-WAN rules also known as services rules. They are used for identification of traffic of interest and routing of traffic based on route condition and strategy between two devices in a network. SD-WAN rules …
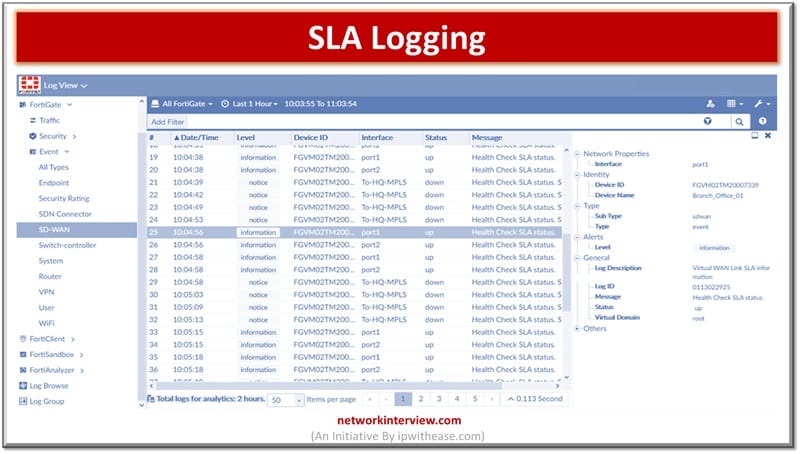
Logs are an important aspect of monitoring and management. Logs enablement of devices is crucial to perform fault isolation, resolution of issues and also help in locating the root cause of problem for permanent fix. All modern devices have the …
Cyber Attack Technologies Various forms of cyber attacks are prevailing these days and method of attack sophistication has reached new levels where now attackers are not limited only to fake websites, messages or emails but also focus is on theft …
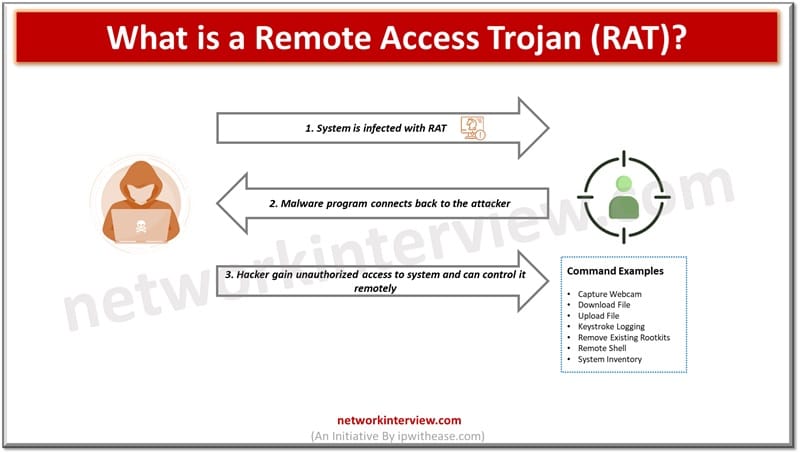
Remote access and control over systems remotely is widely used to provide technical support to users or work outside the boundaries of offices. With the rise of remote working however, especially during Covid-19 pandemic had allowed attackers to use remote …
The information access is made uninterrupted over wired and wireless networks from anywhere, anytime, any device using modern technology. Today end users are mobile and often equipped with digital portable devices and they expect services availability as and when it …
Domain name system (DNS) is widely used terminology in Internet or public networks. DNS maps host name to IP addresses in a similar fashion as phone books or telephone directory maps a name to a phone number. This is an …
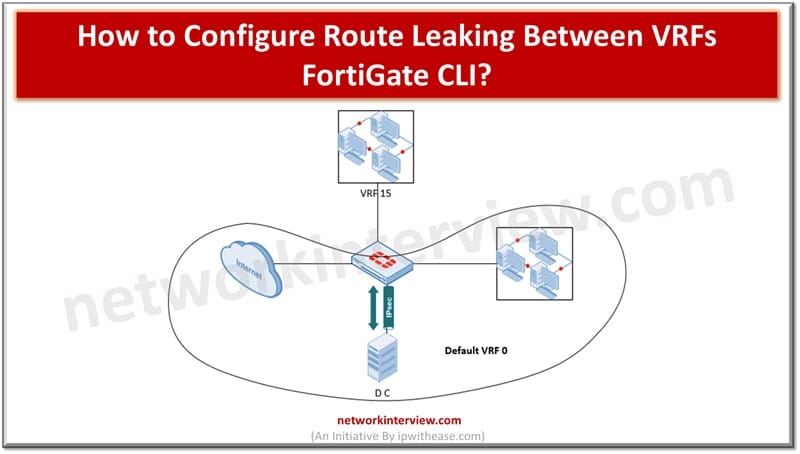
Cloud hosted workloads require customer traffic isolation and separate routing at logical level but through common hardware. Using virtual route forwarding (VRF) technique multiple routing tables can be created within the same router. VRF is used to divide routing functionality …
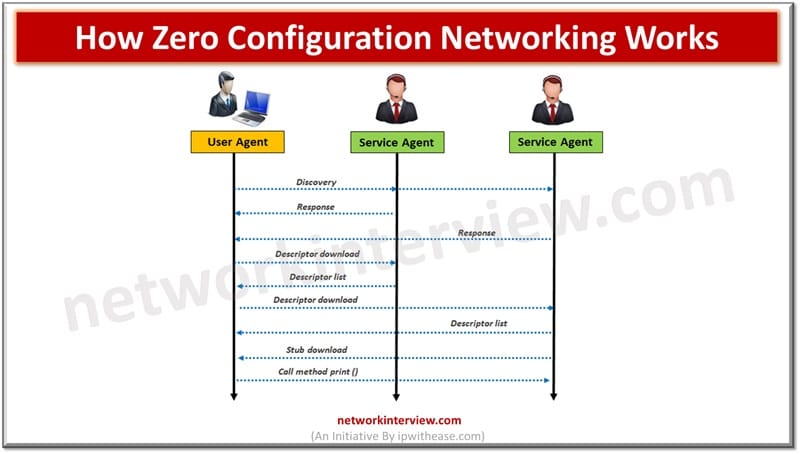
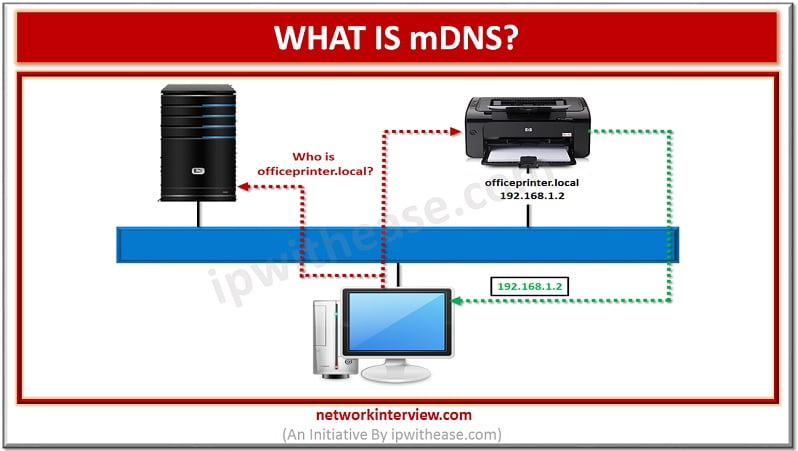
What is mDNS? The method of using familiar semantics of operating, packet formats and interfaces of DNS programming in small network without a DNS server is termed as Multicast DNS or mDNS. Every network node with mDNS reserved multicast address …
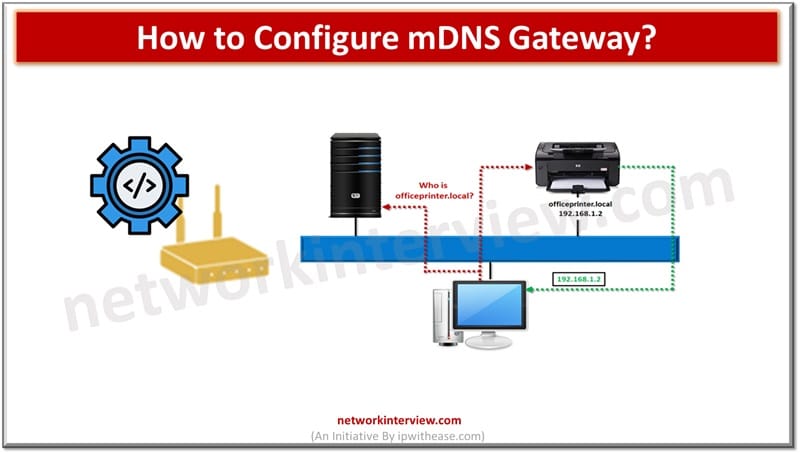
Traditional networks use DNS and DHCP protocols which require servers and complex configurations to operate. Multicast DNS or mDNS is a set of protocols and technologies which provide automatic services of discovery, name resolution without manual configuration. It is a …
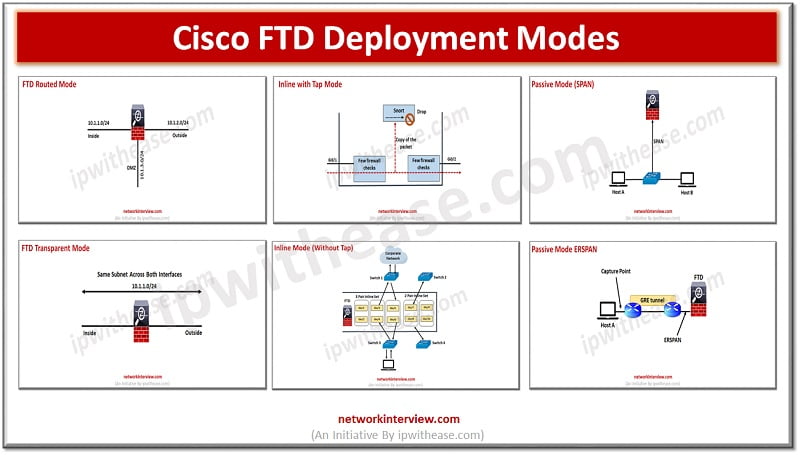
(FTD Deployment Modes: Routed, Transparent, Inline, Inline with tap, Passive SPAN, Passive ERSPAN) Cisco FTD design and deployment implementation involves setting up firewall, SSL inspection, NAT, IPS and active/standby HA. Deployment model determines placement of FirePower into the network as …
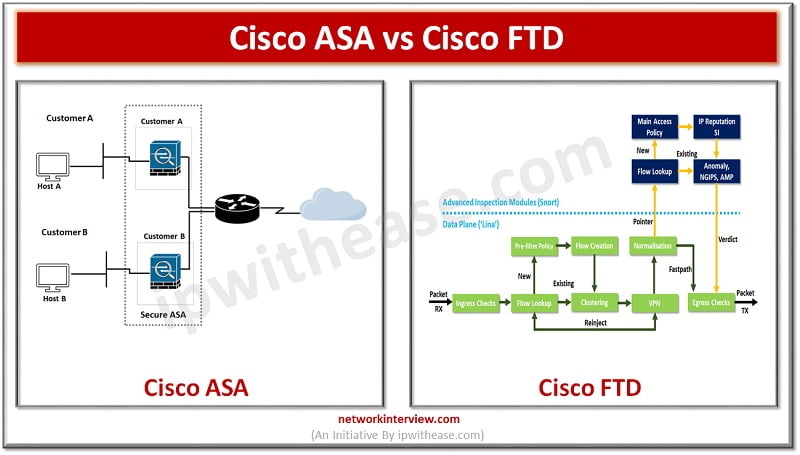
The Cisco Firepower Threat Defense (FTD) and Cisco Adaptive Security Appliance (ASA) are two types of security appliances that provide various features and capabilities to companies. These appliances were created with the intention of safeguarding businesses from cyber threats. Today …
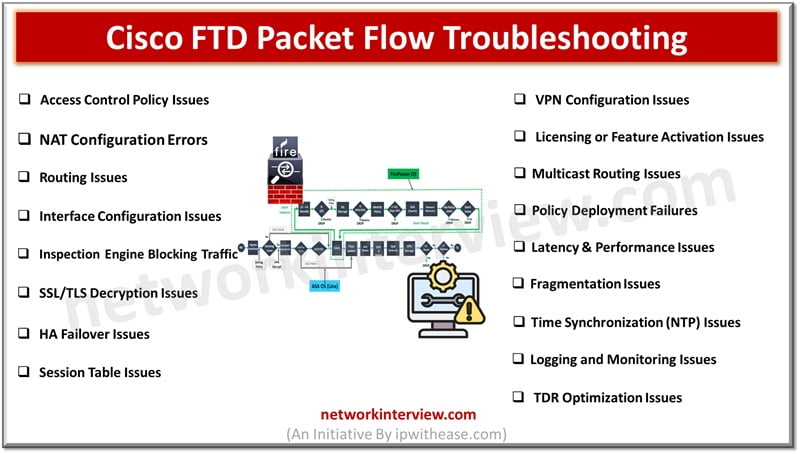
Troubleshooting Cisco FTD Packet Flow issues can be complex. Here is a summary of common Cisco FTD Packet Flow troubleshooting issues and the associated troubleshooting steps. Cisco FTD Packet Flow Troubleshooting Issues 1. Access Control Policy Issues Issue: Traffic is …
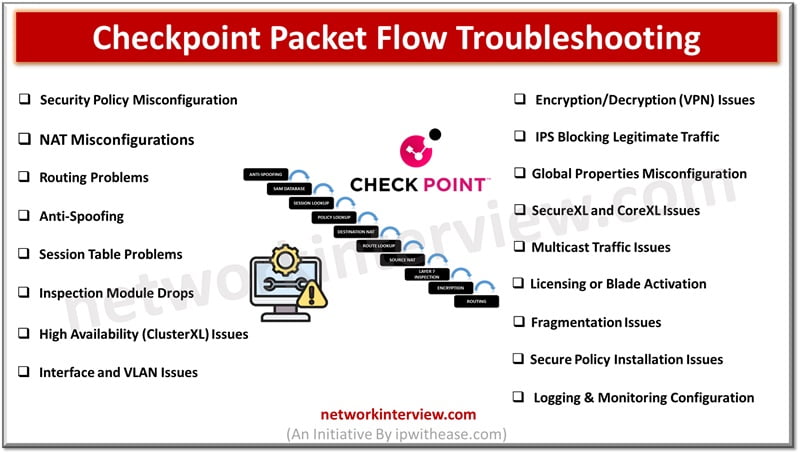
Troubleshooting Checkpoint Packet Flow issues can be complex. Here are common Checkpoint Packet Flow troubleshooting issues and steps to address them. Checkpoint Packet Flow Troubleshooting Issues 1. Security Policy Misconfiguration Issue: Traffic is dropped due to incorrect or missing security …
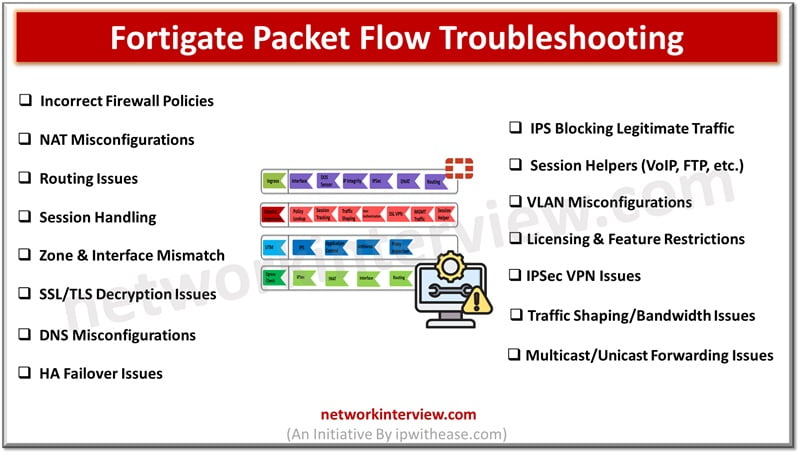
Troubleshooting Fortigate Packet Flow issues can be complex. Here’s an overview of common Fortigate Packet Flow troubleshooting issues and steps to resolve them. Fortigate Packet Flow Troubleshooting Issues 1. Incorrect Firewall Policies Issue: Traffic is dropped due to misconfigured firewall …
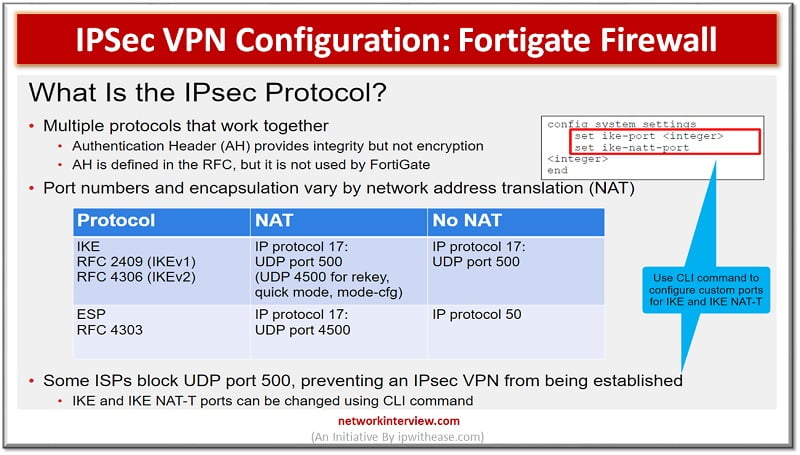
Objectives IPSec IKE Site to Site VPN between two FortiGate Sites Phase I and Phase II Parameters Tunnel Configuration Troubleshooting Commands IPSec VPN Configuration: Fortigate Firewall IPsec: It is a vendor neutral security protocol which is used to link …
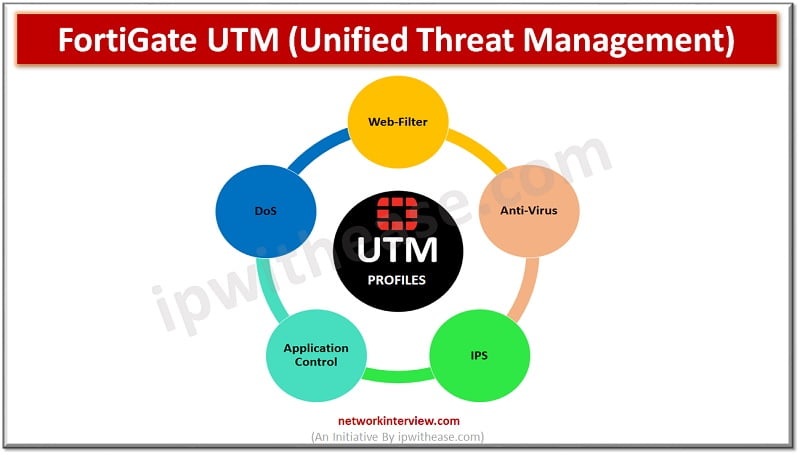
UTM-Unified Threat Management UTM (Unified Threat Management) is a feature of a firewall in which multiple security profiles combine and provide protection from threats and attacks. These features are antivirus, web filtering, IPS, anti-spam etc. UTM is the consolidated solution …
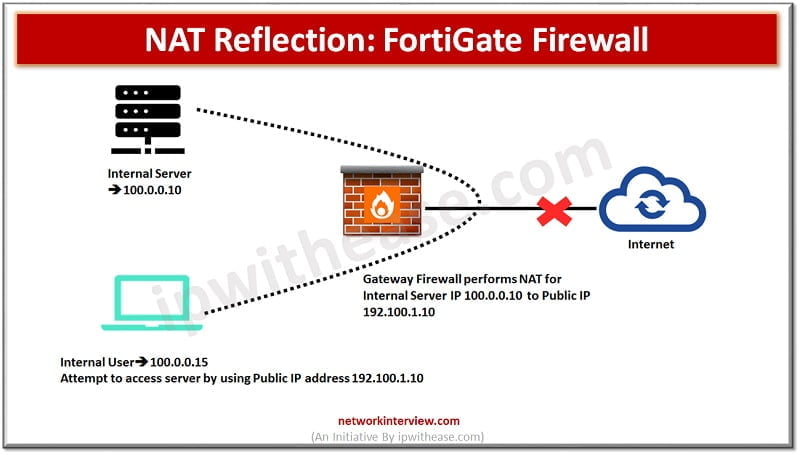
What is NAT Reflection? We use Hairpin NAT or NAT reflection when our aim is to access an internal server from an internal workstation of a client by being able to access the Public IP that would be bound to …