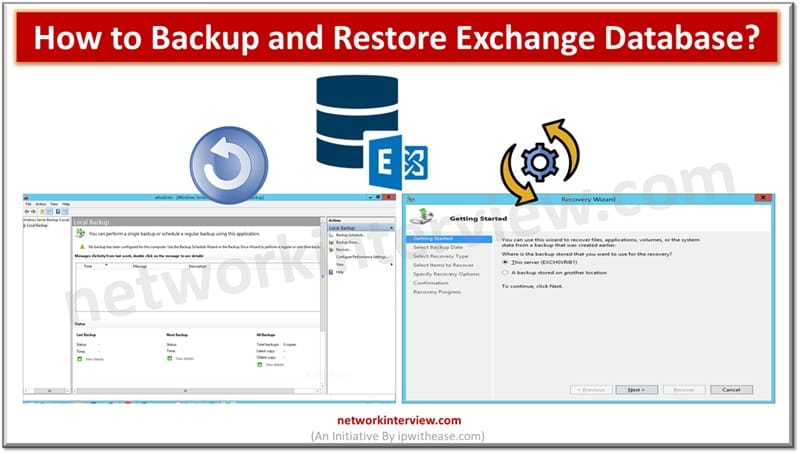
Unexpected power outage, Exchange Server failure, or any other disaster can happen anytime. Such incidents can cause corruption in the Exchange database, leading to downtime and data loss. This is why you will always take a backup of your database …
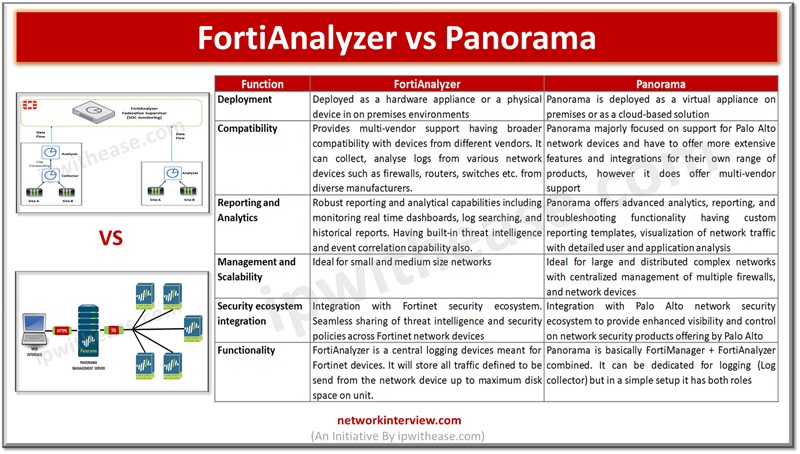
FortiManager is a centralized management platform made by Fortinet for administering lots of Fortinet devices (mainly FortiGate firewalls) from one place. Instead of logging into each firewall individually, FortiManager lets you manage them all through a single console. FortiManager comes …
Rapid changes in technology are creating a mass shift in the IT job market. It is expected that in the next five years 19 million jobs will be created, out of which 9% will be lost by 2050. 60% of …
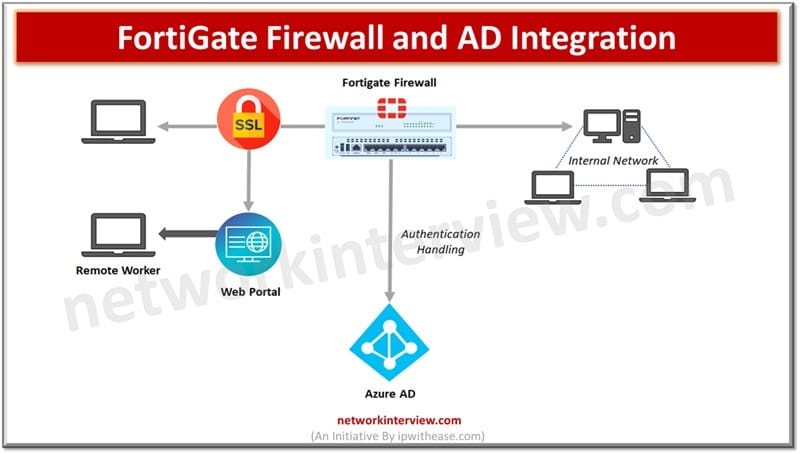
Integration of a FortiGate firewall with Active directory provides a strong defense on authentication and authorizations. In today’s digital IT landscape cyber threats are constantly evolving and getting more and more sophisticated which calls for ensuring a robust network security …
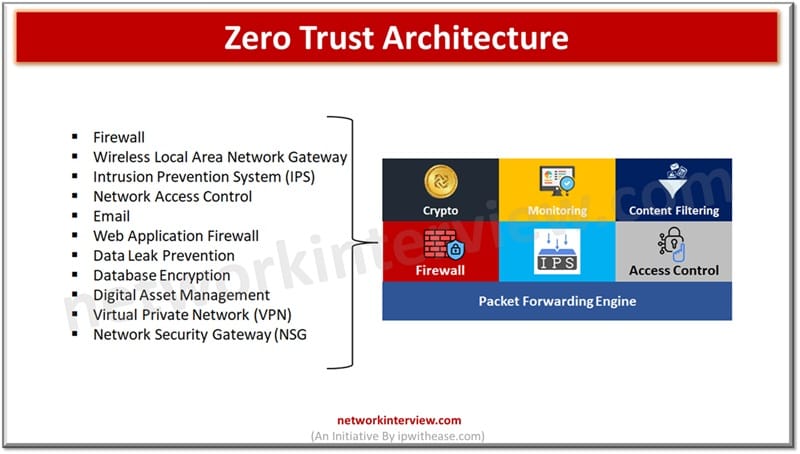
Traditional networks relied on authenticating once and getting inside and access to all resources. The modern networks operate on ‘Zero trust’ architecture which is a security framework working on the principle of no user, no device, no application is trusted …
Deepfake Technology is something about combining deep learning with something fake. It creates images or events that actually do not exist. Deepfake technology is used to mislead the public by spreading false or wrong information. Such as a Politian deep …
The days are gone where people acquired a skill or earned success in a job competitive exam, got a job and held it till eternity. To secure a job and continue it would mean a stable career – learn during …
With the AI boom, professionals are looking to acquire new AI certifications to take a leap in the job market. AI certification will give them an edge in the job market but the question is are these certifications necessary? And …
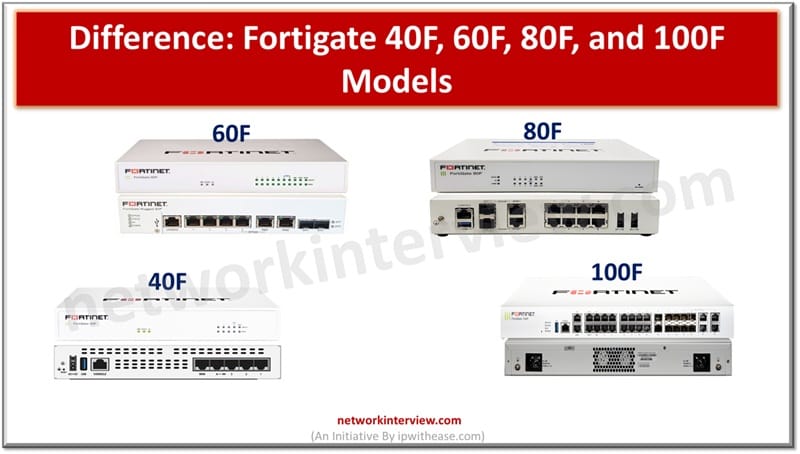
Fortigate 40F, 60F, 80F and 100F models differ in performance and scalability and are meant to address all types of businesses. While choosing a firewall one has to have a balanced approach and consider functionality and fit. Fortigate Next generation …
Artificial intelligence (AI) is leveraged to enhance threat detection and prevention by applying machine learning techniques and using intelligent algorithms. AI is empowering cybersecurity and helping in analysis of vast amounts of data, identification of threat patterns at a scale …
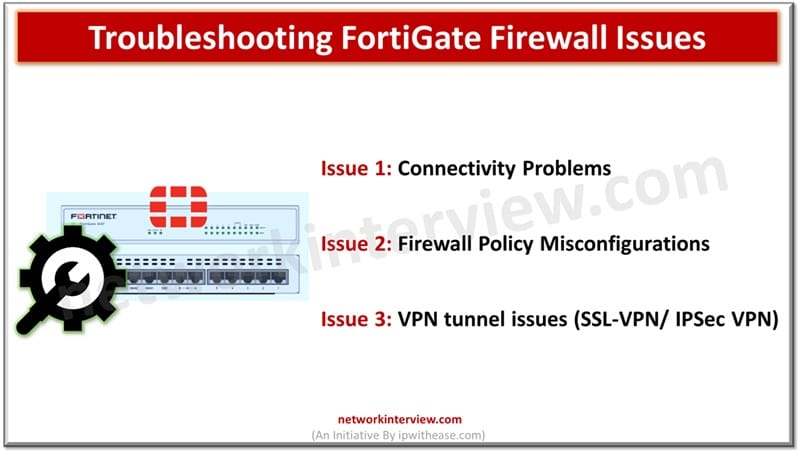
Like any other devices, firewalls do face disruptions and issues. For network administrators network disruptions due to firewall issues is critical as suddenly users cannot access critical resources, application failures occur, and expectation is to restore services to As-IS state …
Generative AI refers to systems that create new content like text, images, or audio using machine learning models. Whereas, Responsible AI ensures AI systems are developed and used ethically, focusing on fairness, transparency, and safety. Artificial intelligence is reshaping organizations …
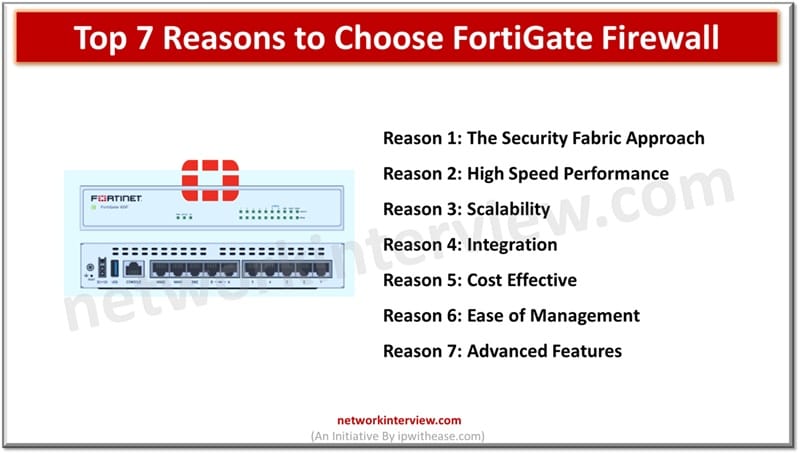
Firewalls are the network’s first line of defense and provide protection from threats coming from the outside world. A strong, well built and secure firewalls provides an effective means to neutralize cyber threats. The cyber threats have increased multi-fold with …
To understand the AI impact on job market, lets go back to pre-covid era, when the focus of the recruiters was on hiring candidates with high skills, good qualifications from reputed educational institutions; and off course the majority of IT …
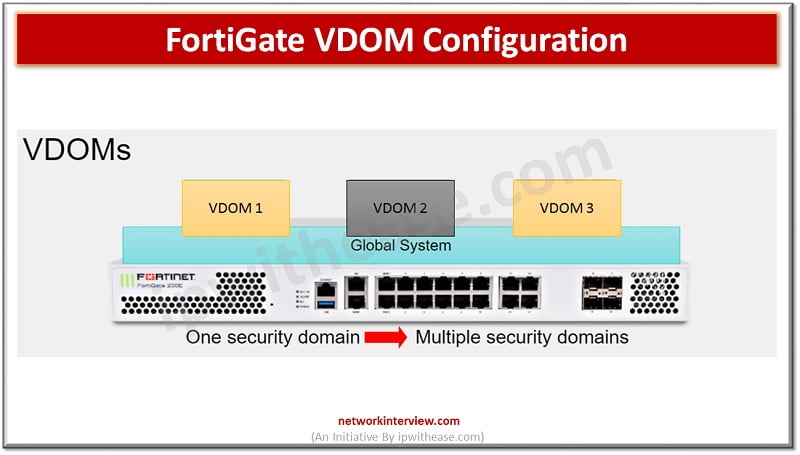
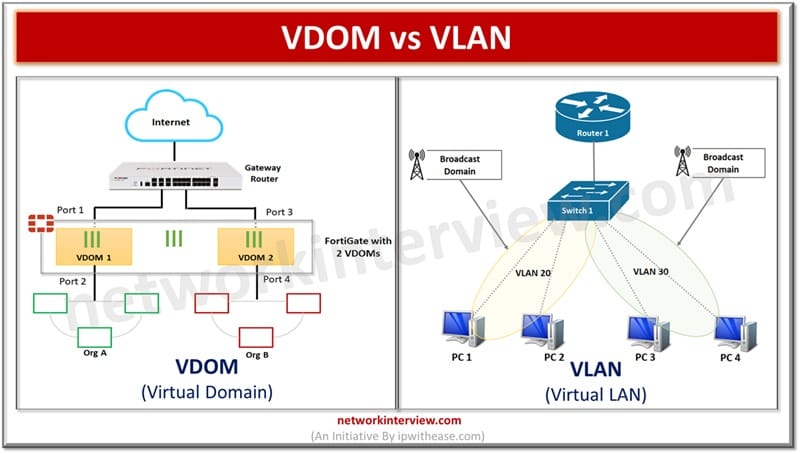
Understanding FortiGate VDOM FortiGate VDOM or Virtual Domain split FortiGate device into multiple virtual devices. Each VDOM has independent security policies, routing table and by-default traffic from VDOM can not move to different VDOM which means two interfaces of different …
The Evolving Cyber Threat Landscape Attack surfaces multiply faster than most organizations can patch. Last year, global ransomware incidents spiked over 37%, according to multiple threat intelligence reports, and IoT devices are still shipping with laughably weak security controls. Supply …
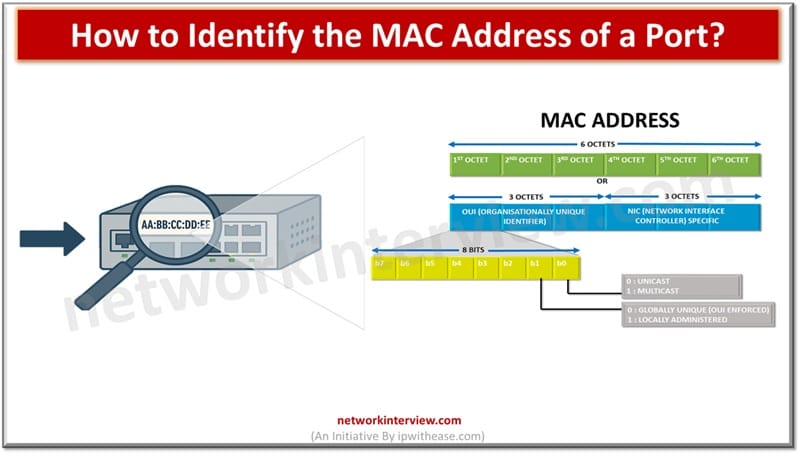
All computer systems and programs use human readable and understandable IP addresses for communication across the network; however, actual communication between systems takes over the MAC or physical address of the device derived at layer 2 data-link layer of OSI …
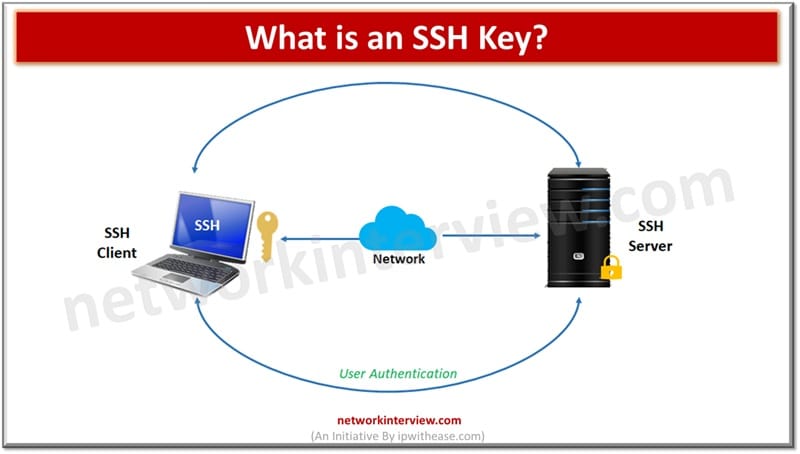
Modern cloud infrastructure highly relies on SSH keys and they are the foundation of secure access management in the cloud ecosystem. The SSH keys establish secure communication between servers and clients and provide faster access as compared to traditional password-based …
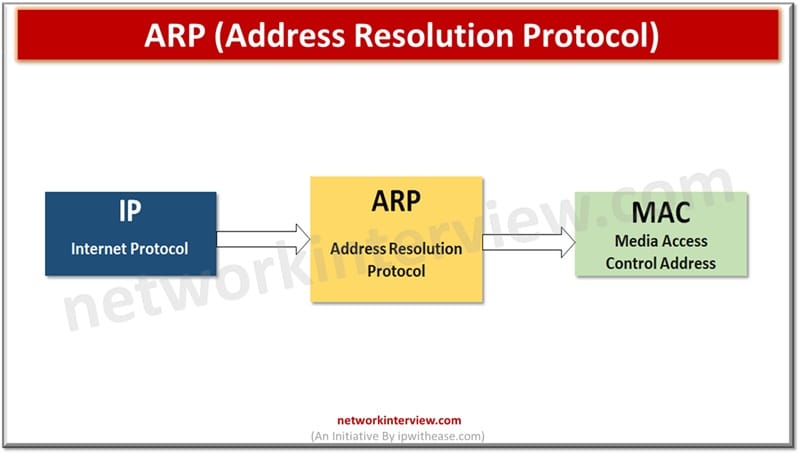
In the world of computer networks, communication between devices or systems happens using a unique identifier which facilitates data exchange and communication between interconnected systems. Unique identification of network interface controller (NIC) for network communication happens at the data link …
The majority of enterprises large, medium and small are moving to the cloud ecosystem to run their IT operations. Cloud service providers require a multi-tenancy strategy and products to support multi-tenant scenarios. Networking is one of the most crucial elements …
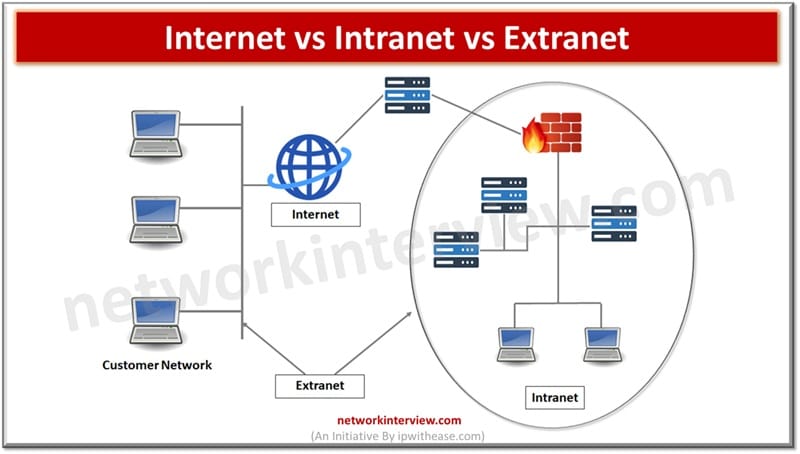
Networks are crucial in today’s digital world as they allow exchange, acquisitions and knowledge across organizations or within organizations. Every network meets a specific requirement as per its scope – connecting internal organizations, public ecosystem and secure connectivity with external …
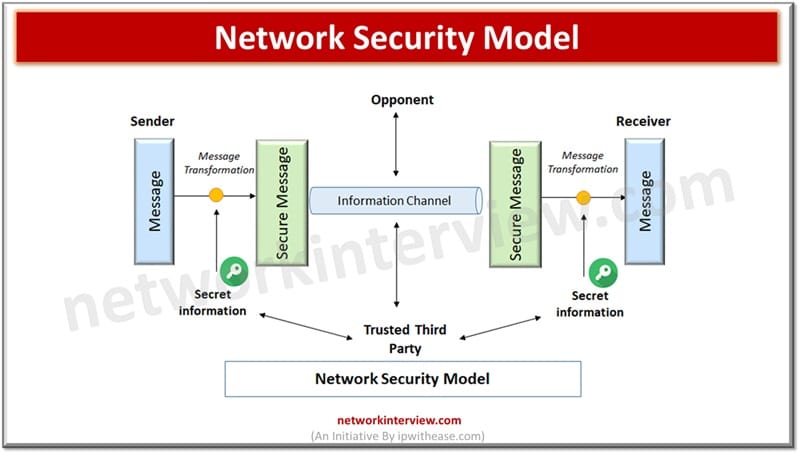
The moment we think about the power of the public Internet as the most viable and cheap medium of fastest communication, network security comes to mind as a matter of concern. Though fast, cheap and reliable but if not properly …
NAT-Network Address Translation NAT is a process that enables a single device such as a firewall or router to act as an agent between the internet or public network to LAN or private segment. NAT is usually use for below …
FortiGate fundamentals and principles involve high security infrastructure and provide a secure set up to the client. FortiGate Firewall is the most respected and highly used security product in the market. It uses artificial intelligence and machine learning to achieve …
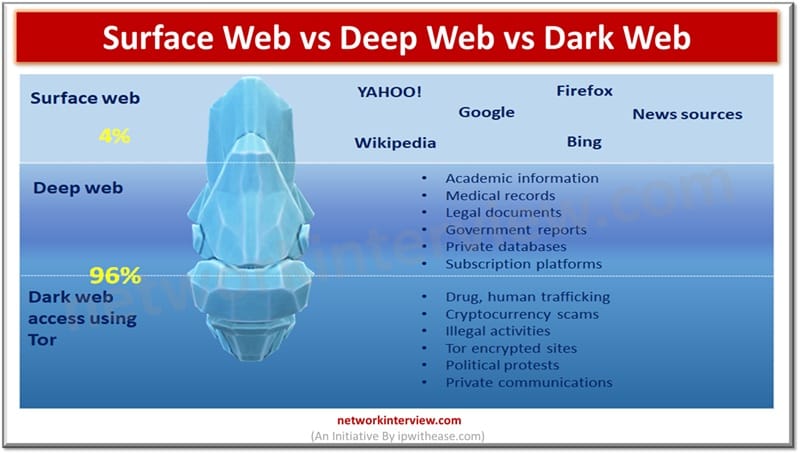
The Surface Web includes publicly accessible websites indexed by search engines. The Deep Web contains hidden content like databases and academic records, while the Dark Web is a small encrypted portion used for anonymity and often linked to illicit activities. …
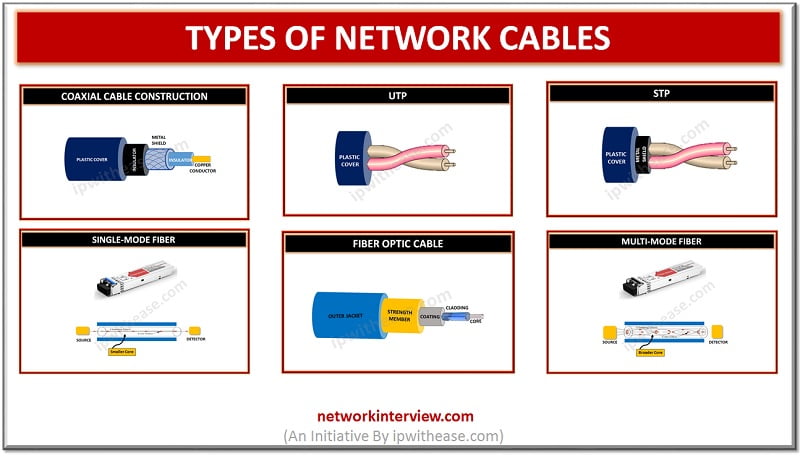
The medium that allows traveling of information through it from one device of network to other is termed as network cable. Selection of the cable type for the network is dependent on factors such as topology, size and procedure of …
In an era dominated by cloud platforms, Wi‑Fi 6E and software‑defined everything, it is tempting to forget that every byte of corporate data still travels across a physical medium for most of its journey. Data cabling is that hidden infrastructure …
With the widespread use of Internet and cloud computing, social networking, e-commerce applications, a large amount of data gets generated daily. Data security is a very crucial aspect of network security as more and more people are using the Internet …
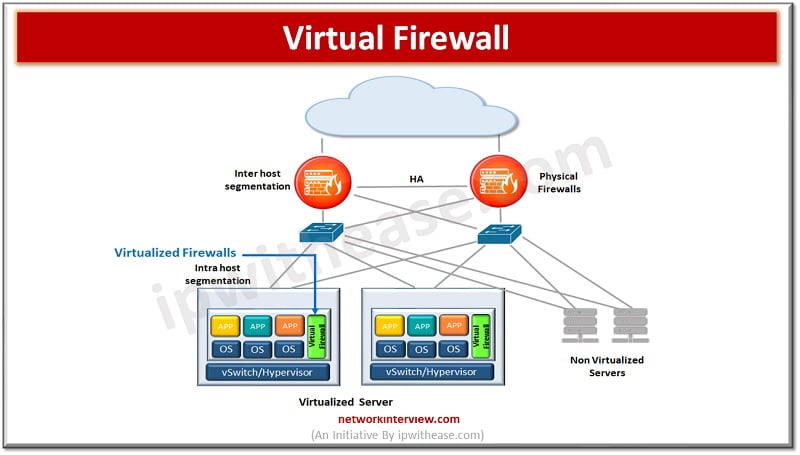
Firewalls have evolved a lot since their inception. The gatekeeper or epitome of perimeter security used to enhance network security. Initial days firewalls were simple packet filters which examined packets of information passing through them and blocked which did not …
The technology sector continues to evolve rapidly, leading to the prominence of several high-paying tech skills. In this blog, we will discuss the top 10 high-income tech skills to be considered as a career option. List of top High-Income Tech …
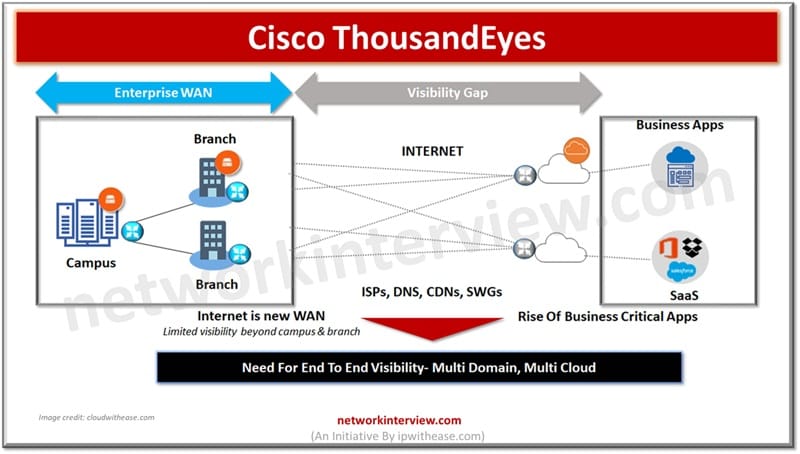
Cisco ThousandEyes is a comprehensive platform for measuring, monitoring, and troubleshooting network performance. It is a cloud-hosted platform that helps organizations ensure reliable and secure user experience and network performance across the globe. ThousandEyes provides insights into the performance and …
Firewalls are the backbone of all networks and they have come a long way from traditional packet-based filtering firewalls to Next generation firewalls having convention firewall with network device filtering functions involving deep packet inspection, intrusion prevention system (IPS), TLS …
Centralized network management and analysis of network devices is one of the vital requirements of enterprise networks. Individual network component monitoring in larger networks brings a lot of overhead in terms of skills, resources, expertise and not a viable solution …
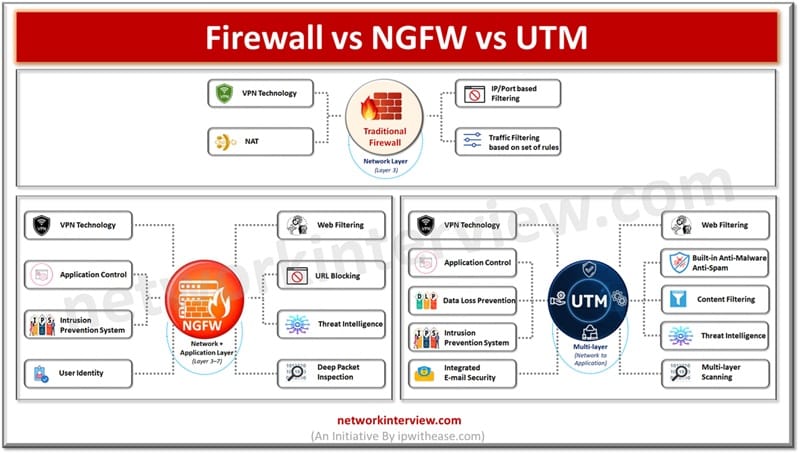
In today’s article we will understand the difference between traditional firewalls, Network generation firewalls (NGFW) and Unified threat management (UTM), their key features. Firewalls sit on the boundary of the network entry point and provide protection against malicious threats originating …
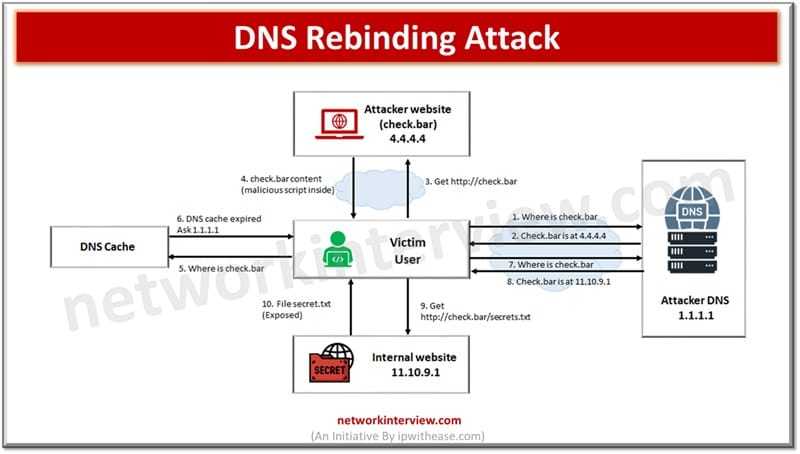
A DNS rebinding attack tricks a browser into bypassing same-origin policy, thereby allowing attackers to access internal networks or devices through malicious DNS responses. In networking systems are addressed with a unique numerical value which is known as IP address. …
RAID is an acronym for Redundant Array of Independent Disks. It is a standard data storage technology that associates multiple physical disks into a single logical unit to provide three fundamental benefits – Data redundancy (protection against disk failures) Throughput/Performance …
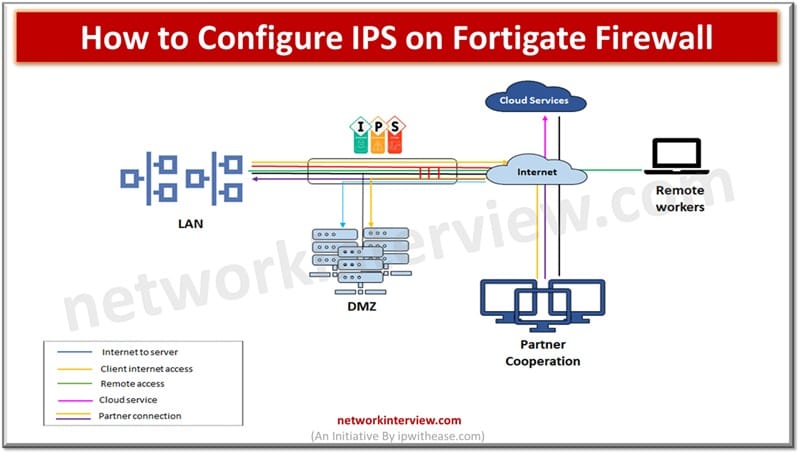
To configure IPS on a FortiGate firewall, enable an IPS sensor in the relevant security policy. Then, apply or customize the sensor under Security Profiles > Intrusion Prevention. Intrusion prevention systems or IPS provide security for the networks and hosts …
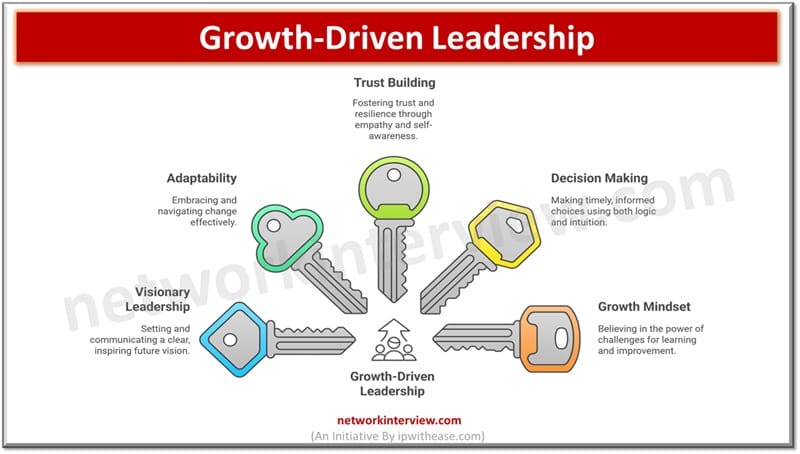
Because businesses change so quickly today, leaders are presented with unique obstacles. Since globalization, technology changes, changing customer expectations, and economic swings exist, leaders need to look past old management tactics. An approach based on agility and vision helps organizations …
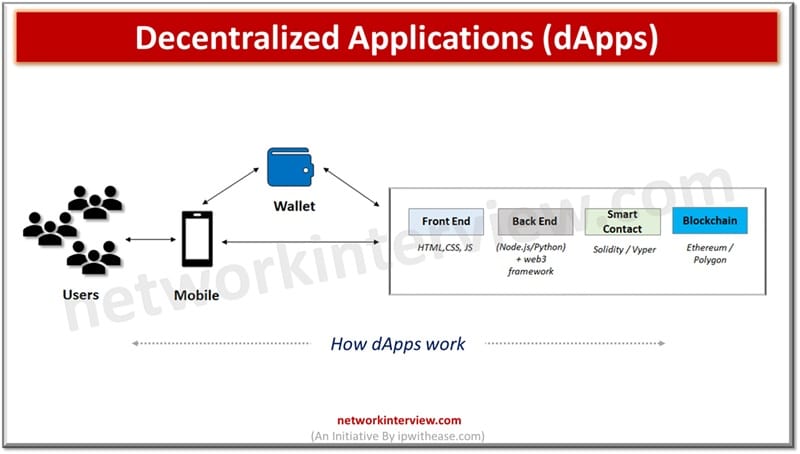
Decentralized Applications are software programs that run on a blockchain or peer-to-peer network, enabling trustless and transparent operations without central control. Web 3.0’s ultimate aim is to move the Internet from centralized model to decentralized model. Currently all big giants …
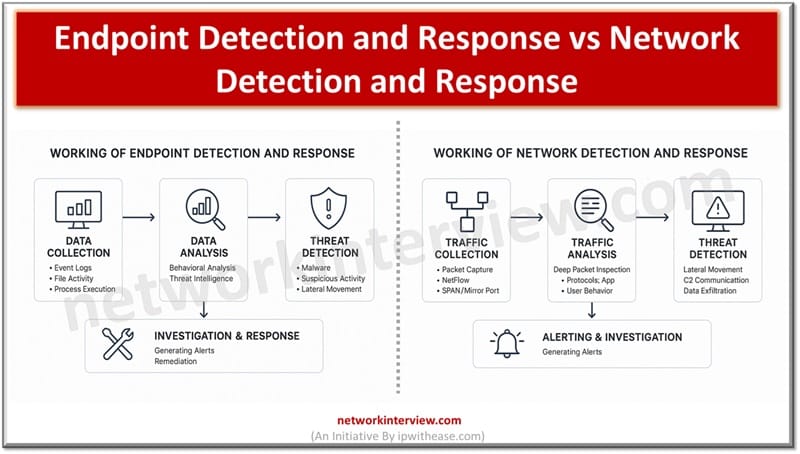
Endpoint Detection and Response focuses on monitoring and responding to threats on individual devices like laptops and servers. Whereas, Network Detection and Response monitors network traffic to detect and respond to threats across the entire network infrastructure. Constant threats and …
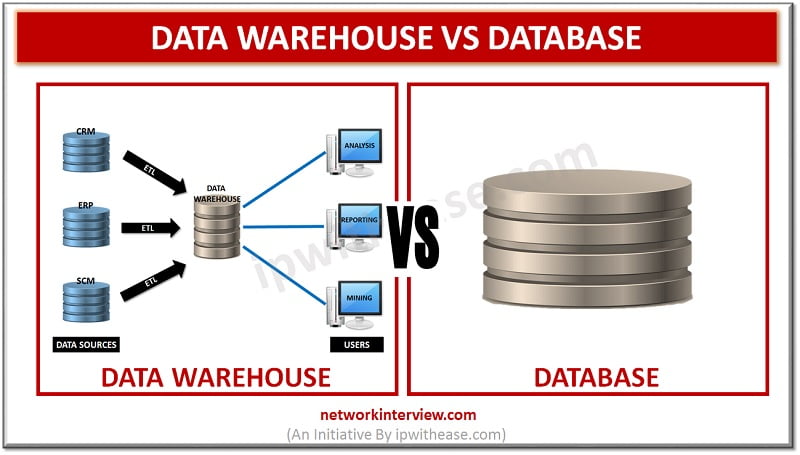
Before discussing difference between Database and Data Warehouse, let’s understand the two terms individually. Data Warehouse The data warehouse is devised to perform the reporting and analysis functions. The warehouse gathers data from varied databases of an organization to carry …
Importance of Database Monitoring In today’s digital world, Data is wealth, Data is Power and Data is everything. Thus a business should give large importance to Users and their data. The Database monitoring tools can help us to a wide …
Database is a structured collection of data managed by a database management system (DBMS) that supports querying, transactions, and indexing. Whereas, a data storage is a more general term for any system used to store and retrieve data, including databases, …
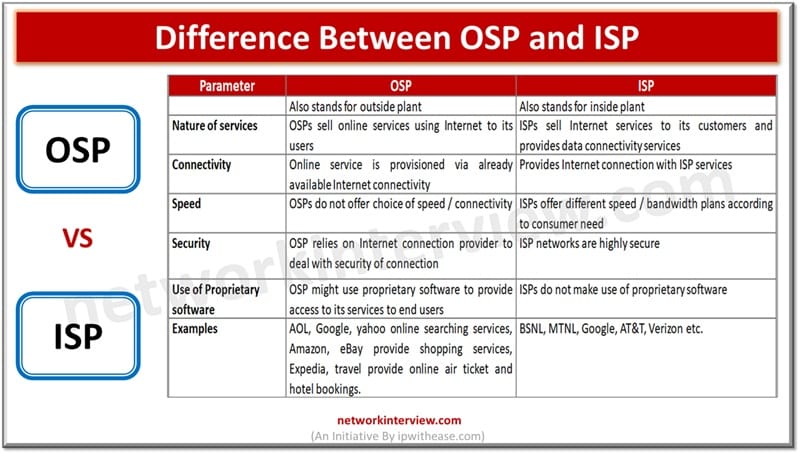
An ISP provides the physical and network access needed to connect users to the internet. Whereas, an OSP offers internet-based services like email, cloud storage, or social media platforms. Service providers play a major role in providing different kinds of IT …
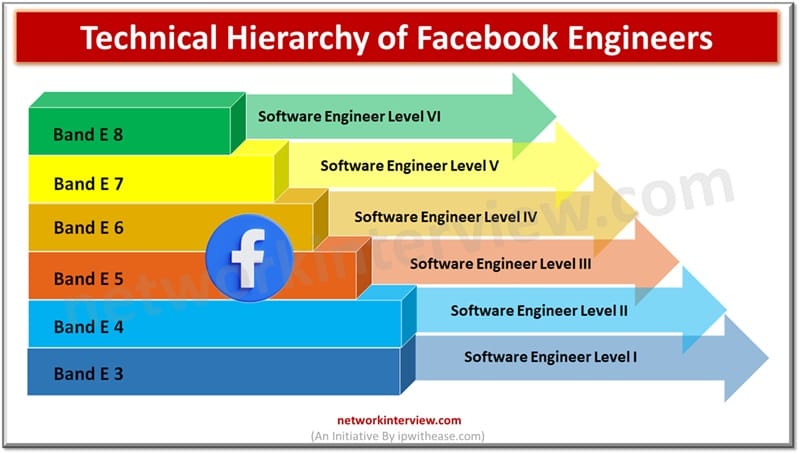
It is a dream goal of the new engineering graduates to get hired in one of the Big 5 Tech companies of the World. And Facebook has a great chance as it is already embedded with our lives. However one …