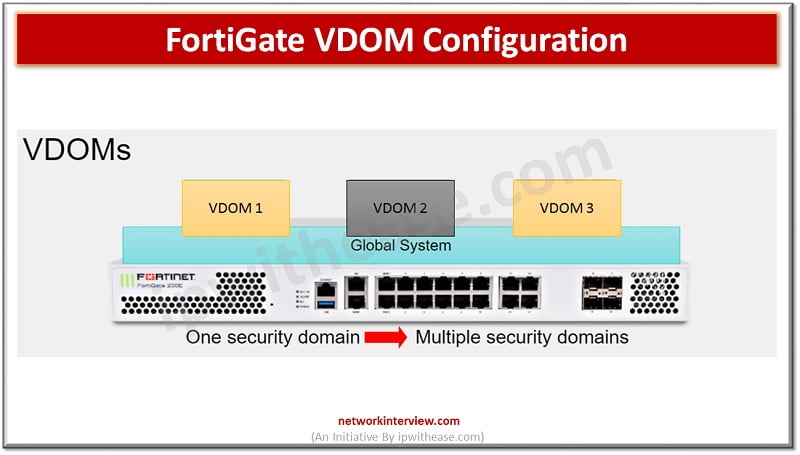
Understanding FortiGate VDOM FortiGate VDOM or Virtual Domain split FortiGate device into multiple virtual devices. Each VDOM has independent security policies, routing table and by-default traffic from VDOM can not move to different VDOM which means two interfaces of different …
NAT-Network Address Translation NAT is a process that enables a single device such as a firewall or router to act as an agent between the internet or public network to LAN or private segment. NAT is usually use for below …
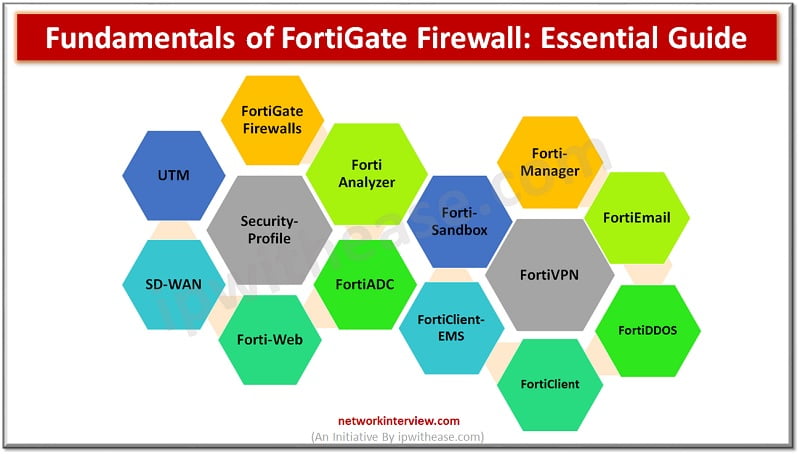
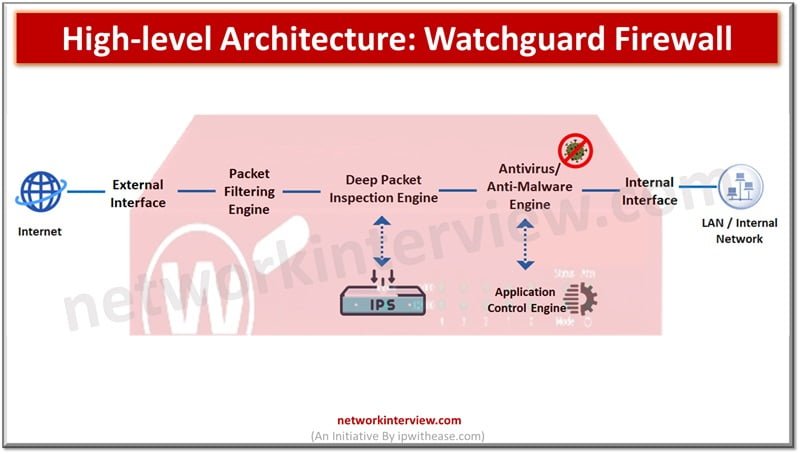
FortiGate fundamentals and principles involve high security infrastructure and provide a secure set up to the client. FortiGate Firewall is the most respected and highly used security product in the market. It uses artificial intelligence and machine learning to achieve …
Firewalls have evolved a lot since their inception. The gatekeeper or epitome of perimeter security used to enhance network security. Initial days firewalls were simple packet filters which examined packets of information passing through them and blocked which did not …
Network architecture refers to the structured approach of network, security devices and services structured to serve the connectivity needs of client devices, also considering controlled traffic flow and availability of services. Network devices typically include switches, routers and firewalls. Palo …
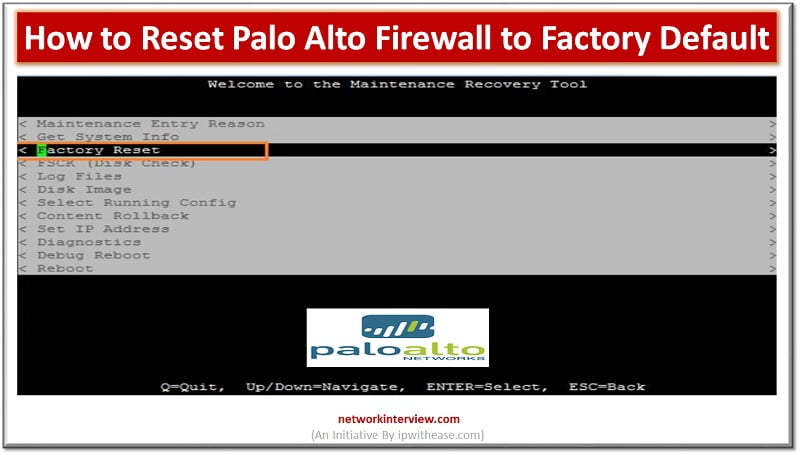
Introduction to Reset Palo Alto Firewall Firewall is a network security device which grants or rejects network access to traffic flowing between untrusted zone (External networks) to trusted (Internal networks) zone. Starting from initial days of Stateful inspection firewalls and …
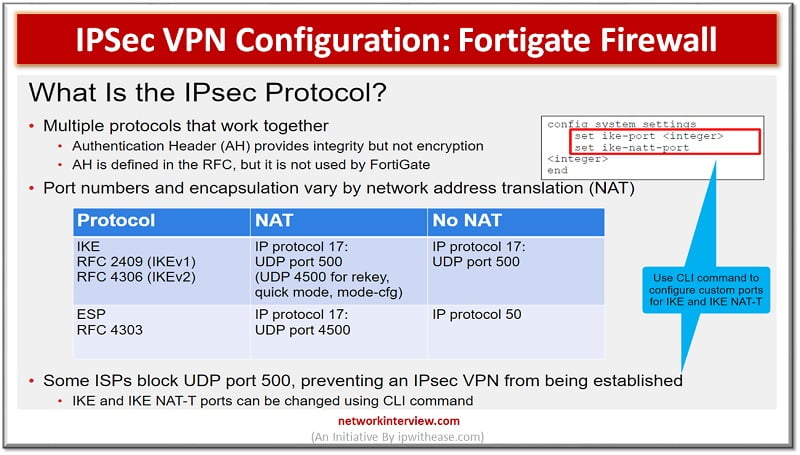
Objectives IPSec IKE Site to Site VPN between two FortiGate Sites Phase I and Phase II Parameters Tunnel Configuration Troubleshooting Commands IPSec VPN Configuration: Fortigate Firewall IPsec: It is a vendor neutral security protocol which is used to link …
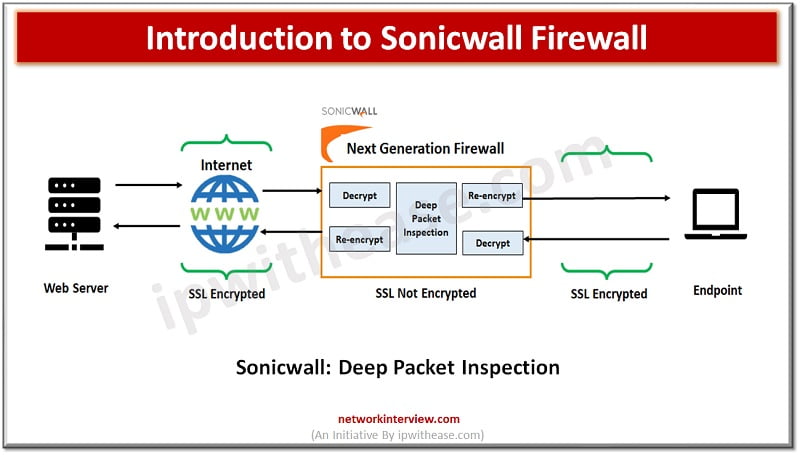
Evolution of Firewalls: Sonicwall Firewall Firewall technologies have evolved at a very rapid pace since its inception and from initial packet filtering firewalls which use to inspect packet traffic and took decision to allow or reject packets, which is then …
Both the proxy and the firewall limit or block connections to and from a network but in a different way. While a firewall filters and blocks communication (ports or unauthorized programs that seek unauthorized access to our network), a proxy …
Firewalls are network perimeter security devices which separate internal networks from external public networks such as the Internet to reduce the risk of external attacks. Firewalls use access policies and identify types of information, in addition they also control ports …
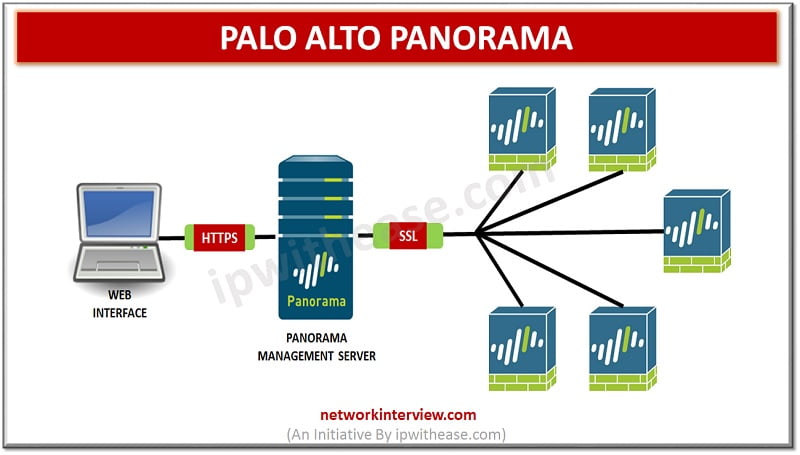
Introduction to Palo Alto Panorama Palo Alto Panorama is the centralized management server that offers a global visibility and control over the multiple Palo Alto Networks next generation firewalls from web interface console. Panorama manage multiple Palo Alto Networks firewalls …
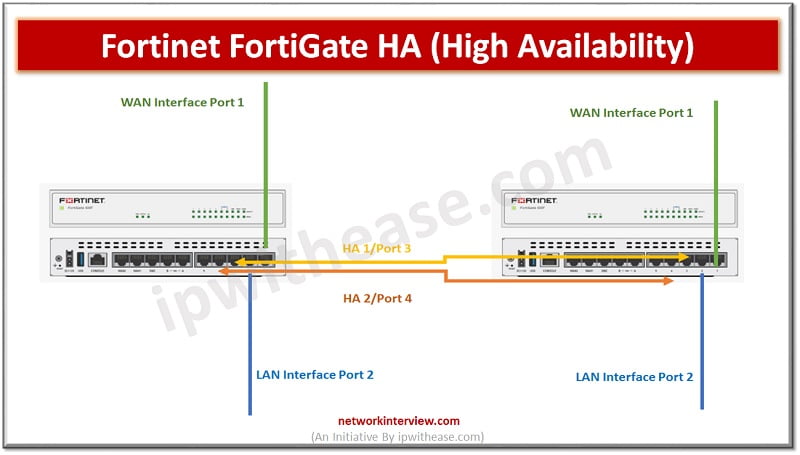
Objectives High Availability HA Modes FGCP (FortiGate Clustering Protocol) Heartbeat Interfaces and Virtual IP Interfaces HA Requirement Configure Primary FortiGate Firewall Configure Secondary FortiGate Firewall HA-Troubleshooting What is High Availability? High Availability (HA) is a feature of Firewalls in which …
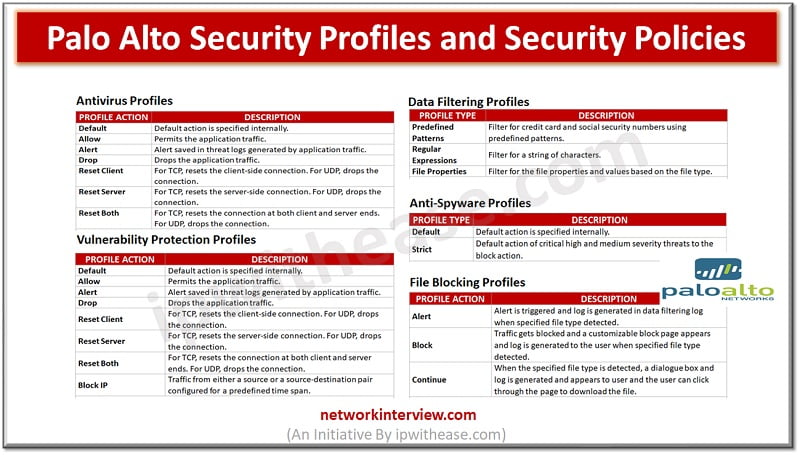
Below are the key profile types provisioned in Palo Alto Firewall. Lets discus all the profile types one by one – Palo Alto Security Profiles & Security Policies While security policy rules enable to allow or block traffic in network, …
Firewalls have come a long way since their inception in the year 1908s. The initial firewall was built by Digital Equipment Corporation (DEC) as a packet filtering firewall which simply inspected packet traffic and if it doesn’t match rules packet …
Objectives Routing in Fortinet FortiGate Configuration Steps of Static Routing Configuration Steps of Dynamic Routing (BGP) Policy Base Routing Routing Monitor GUI Troubleshooting Commands for Routing in FortiGate Routing in Fortinet FortiGate Firewall Routing means how a packet can …
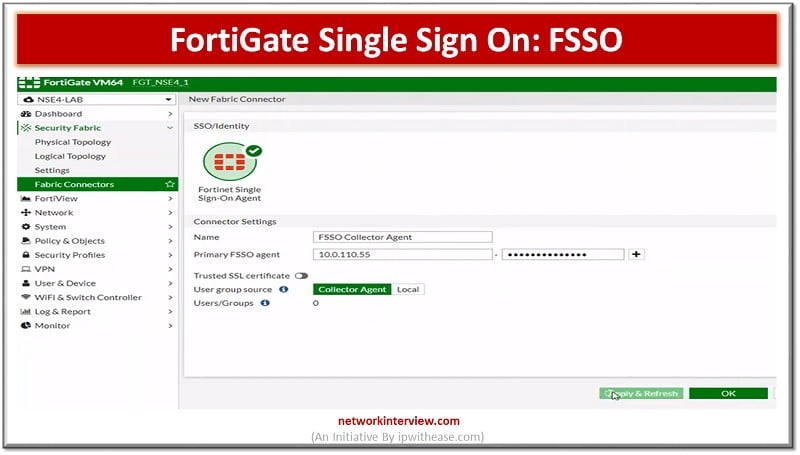
Single Sign On & FortiGate Single Sign On Single Sign On (SSO) is a process that allows users to automatically log into every application after being identified, regardless of platform, technology, and domain. FortiGate Single Sign On (FSSO) is a …
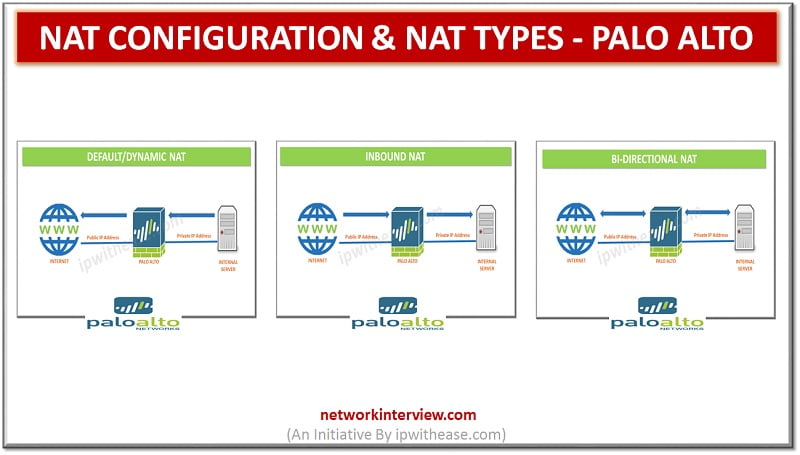
In the previous post we discussed the Architecture of Palo alto firewall. Now, we will discuss the NAT configuration and NAT types in Palo alto. Network Address Translation (NAT) allows to translate private, non-routable IP addresses to one or more …
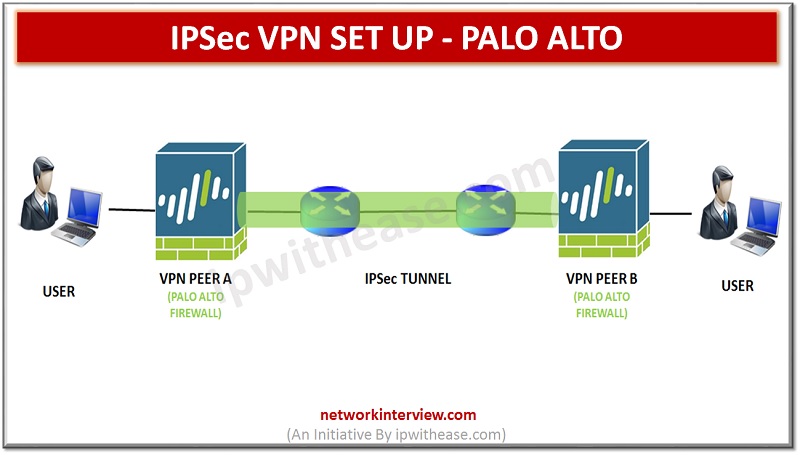
Site-to-Site VPN Overview A VPN connection that allows you to connect two Local Area Networks (LANs) securely is called a site-to-site VPN. Route based VPN can be configuring to connect Palo Alto Networks firewalls located at two sites or to …
Overview In our previous article, we studied IPSec VPN Set Up. In this article we will run through CLI commands and GUI steps to configure an IPSec VPN, including the tunnel and route configuration on a Palo Alto Networks firewall. …
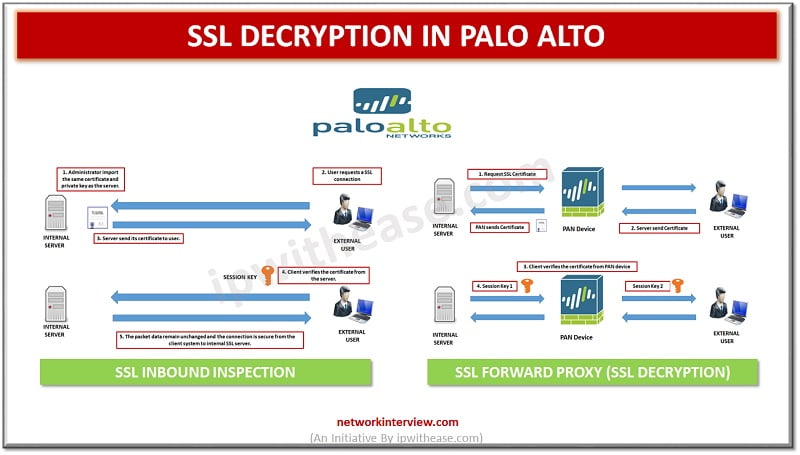
Before digging deep into Palo alto SSL Decryption, let’s first understand what is Decryption? What is Decryption? Palo Alto firewalls can be decrypt and inspect traffic to gain visibility of threats and to control protocols, certificate verification and failure handling. …
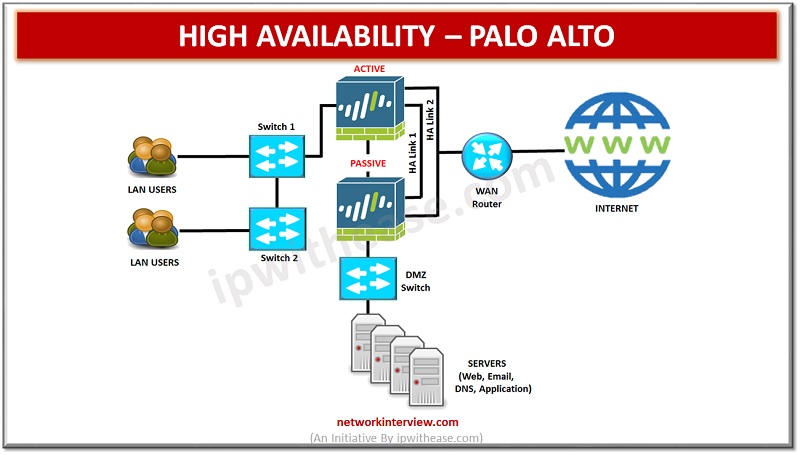
High availability (HA) refers to a system or component that is operational without interruption for long periods of time. High availability (HA) is measured as a percentage, with a 100% percent system indicating a service that experiences zero downtime. High …
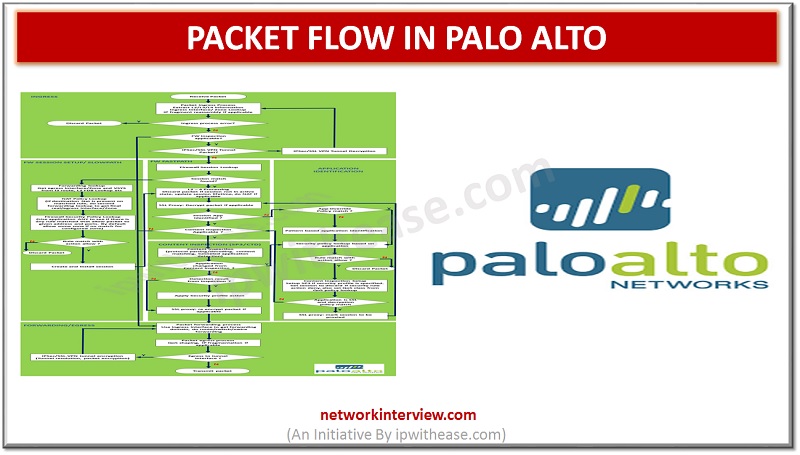
In this article, we will discuss on Packet handling process inside of PAN-OS of Palo Alto firewall. Introduction: Packet Flow in Palo Alto Packet passes through the multiple stages such as ingress and forwarding/egress stages that make packet forwarding decisions on …
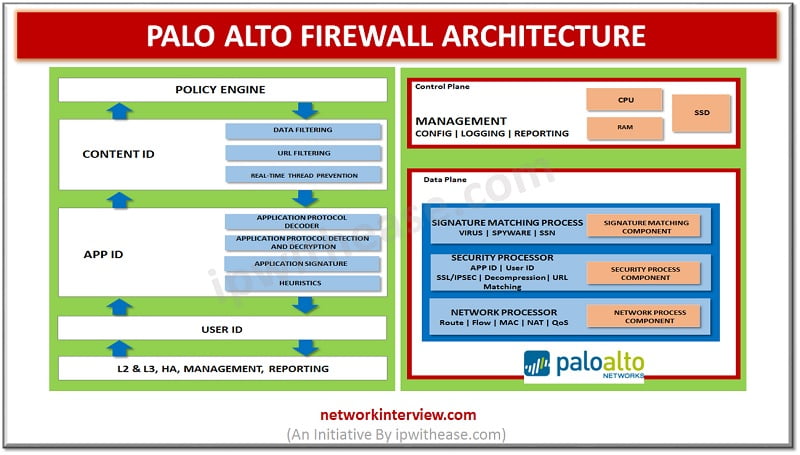
Introduction to Palo Alto Firewall is a network security device that permit or denies network access to traffic flows between an untrusted zone and a trusted zone. Palo Alto Firewall is one of the globally coveted and widely preferred Security …
Introduction Palo Alto has been considered one of the most coveted and preferred Next generation Firewall considering its robust performance, deep level of packet inspection and myriad of features required in enterprise and service provider domain. When troubleshooting network and …