Spear Phishing vs Whaling: Cyber Attacks
Cyber Attacks
Cyber attacks are on rise since Covid 19 at a more rapid pace compared to before. Various forms of cyber attack techniques being used by hackers to gain access to organizations resulting in devastating effects such as unauthorized purchases, stealing of identities and funds etc. resulting in loss of reputation , customer trust , financial losses to the organizations.
Social engineering attacks are one for of cyber attacks which are most common it occur when attacker or hacker masquerading as a trusted entity trick victim into opening an email, instant message, or a text message and click on a malicious link which lead to installation of malware into victim system as a part of ransomware attack or disclosure of sensitive information. Sometimes these attacks are targeted over specific people such as the CEO or CIO of the organization.
Today we look more in detail about two famous social engineering attack forms – Spear phishing and whaling, how these attacks are carried out , how to identify such attacks, steps that can be taken to avoid not being a victim of such attacks and so on.
What is Spear Phishing?
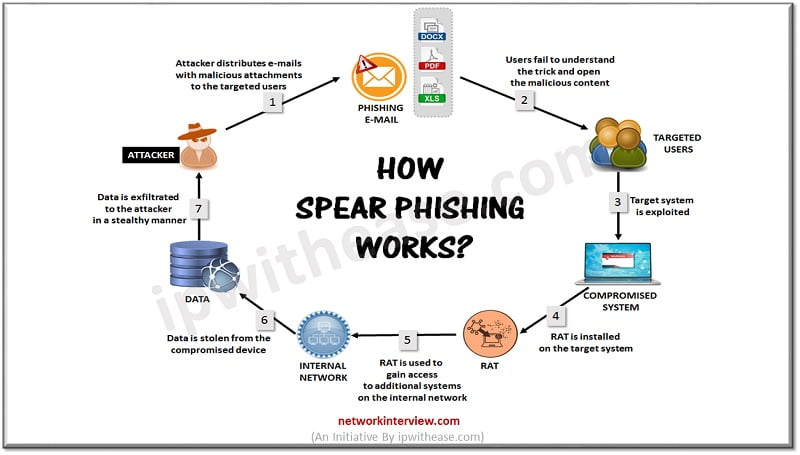
Phishing attacks can take several forms such as spear phishing, whaling, Email phishing, vishing , smishing etc. Spear phishing is a targeted attack onto a specific person or organization as compared to random users. It requires specific information about the organization and its employees including its key personals and power structure.
The attacker pretences a trusted individual in this form of attack and tricks victim to click on a spoofed email or text message, which will install a malicious code on victim system and attacker can get access to sensitive personal or professional information from victim such as names, contact numbers, mailing addresses, social security numbers, credit card numbers etc. The objective is to gain access to sensitive information to facilitate further financial fraud or any other cybercrime.
What is Whaling?
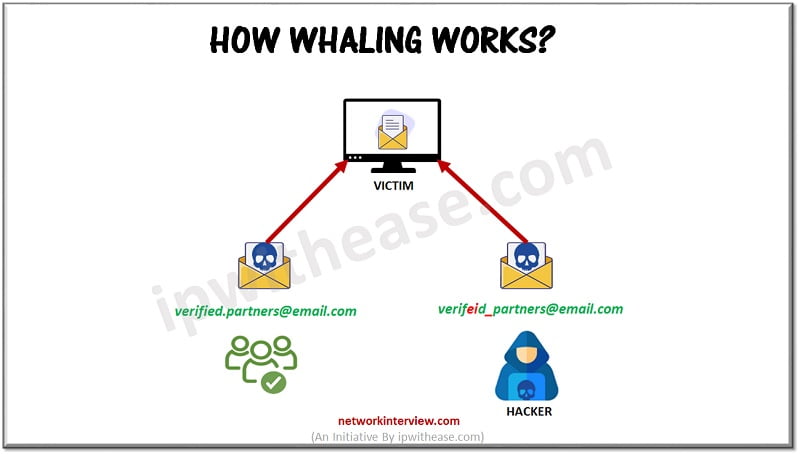
Whaling is a form of phishing attack which is targeted at high profile end users such as senior staff members in an organization, politicians or celebrities. The targeted person would be someone important in organization structure such as CEO, COO or CTO who could be holding critical and sensitive information about business.
The attacker sends an email pretending to be a customer or someone in the organization. The message would be so specific that it may seem very legitimate for the victim to click containing malicious code which will install a ransomware onto his/her system. Or redirect to a website which is under the control of a hacker. Like someone receiving a message on behalf of organization CEO , CIO will not tend to ignore or disregard such requests which may be asking some confidential information such as disclosure of admin passwords, buying Apple cards for customers etc.
Mitigation from Phishing Attacks
The most effective measure to safeguard your system or network from phishing attacks is:
well aware and educated users on social engineering attack techniques. Spear phishing emails are tough to detect so it is good to have a look at destination or any clickable link in the mail before actually clicking them.
Other measures may include:
two factor authentication and strong password management policies.
Comparison Table: Spear Phishing vs Whaling
Below table summarizes the difference between the two types of attacks:
FUNCTION | SPEAR PHISHING | WHALING |
| Target | Targeted at specific organization or group rather than random persons. | Targeted attacked on senior or high-level executives, politicians or celebrities. |
| Goal | Access corporate financial information and other sensitive information to facilitate another financial or cyber-attack on the business. | Retrieve high level credentials of a business such as company accounts, trade secrets, admin accounts etc. |
| Aim | Aimed at low profile targets. | Aimed at high profile targets. |
| Technology and technique | Attackers research on their targets on the internet. Attackers may use slightly more sophisticated technology. | Whaling attacks have reconnaissance phase and uses sophisticated technology. |
| Examples | An email stating vendor specific payment failure due to incomplete details and a link is provided in mail to retry payment again. | A carefully crafted mail seems to be coming from organization high profile personnel such as CEO, CIO asking employees to procure Apple cards for customers. |
Download the comparison table: Spear Phishing vs Whaling
Continue Reading:
Phishing vs Spam: Cyber Attack Techniques
Cyber Security vs Network Security: Know the difference
Tag:comparison, Security



