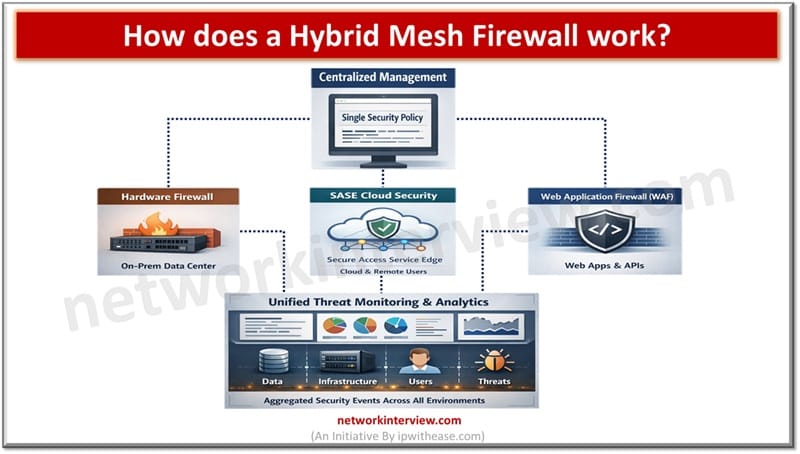
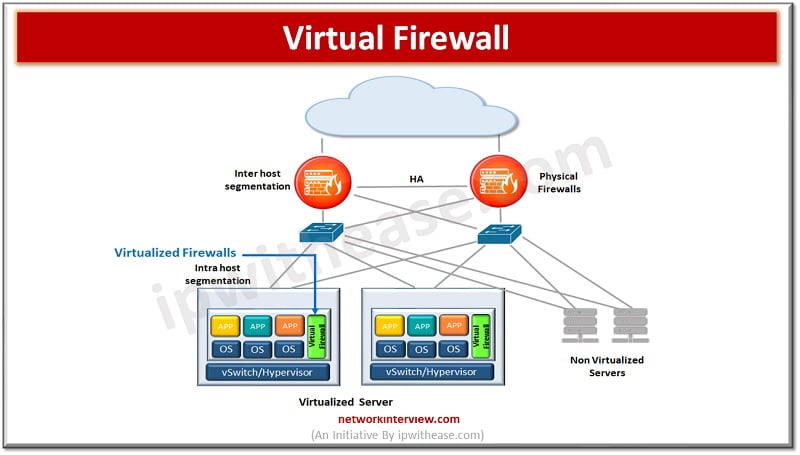
A hybrid mesh firewall is designed for modern day IT environments and unifies all branches, combines all isolated defenses into one single intelligent system which provides real time threat protection to enterprises. All organizations rely on firewalls for perimeter security …
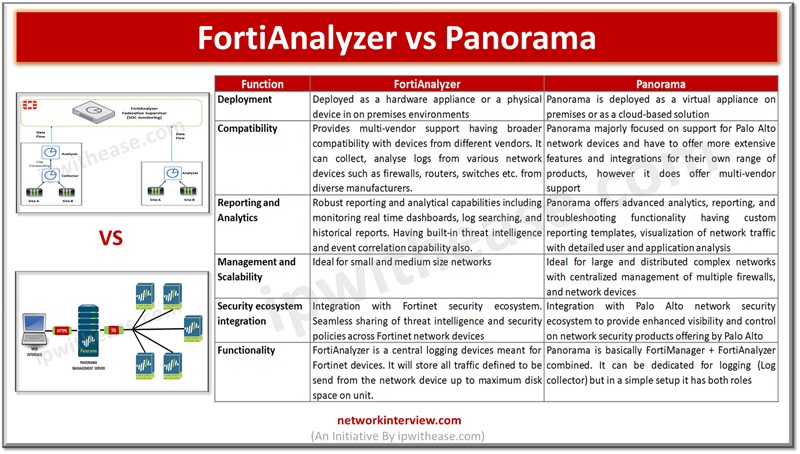
Centralized management of firewalls is a common requirement for all IT network administrators. The centralized management enables management of firewalls having diverse hardware, scaling capabilities, performance parameters such as log throughput, concurrent sessions, interfaces and capability management. Palo Alto Panorama …
FortiManager is a centralized management platform made by Fortinet for administering lots of Fortinet devices (mainly FortiGate firewalls) from one place. Instead of logging into each firewall individually, FortiManager lets you manage them all through a single console. FortiManager comes …
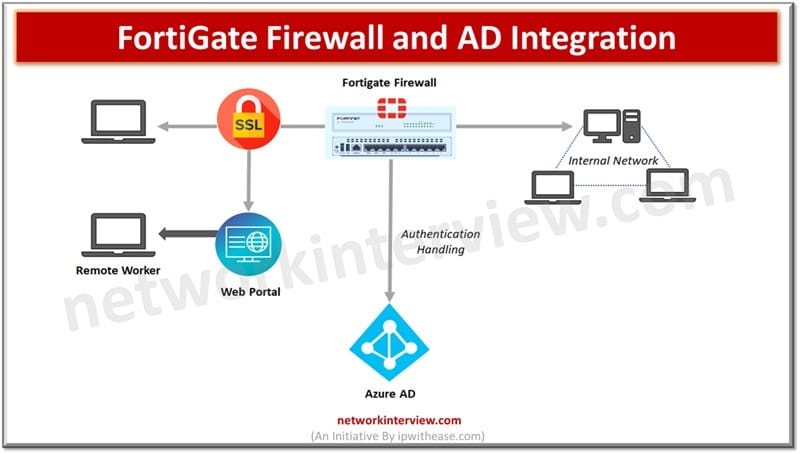
Integration of a FortiGate firewall with Active directory provides a strong defense on authentication and authorizations. In today’s digital IT landscape cyber threats are constantly evolving and getting more and more sophisticated which calls for ensuring a robust network security …
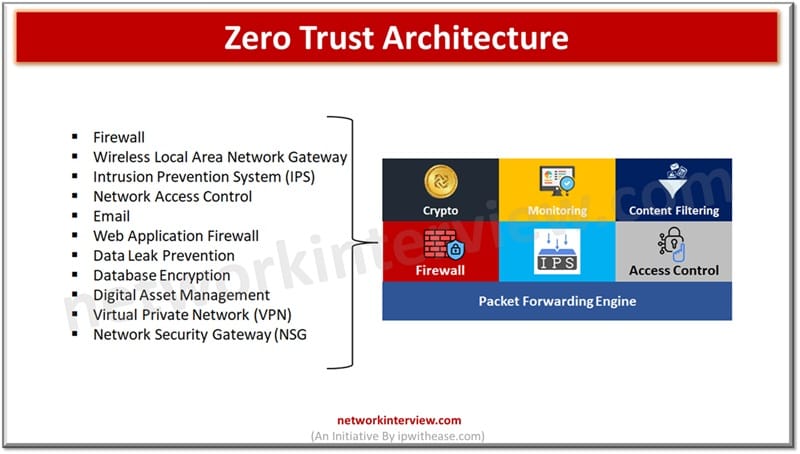
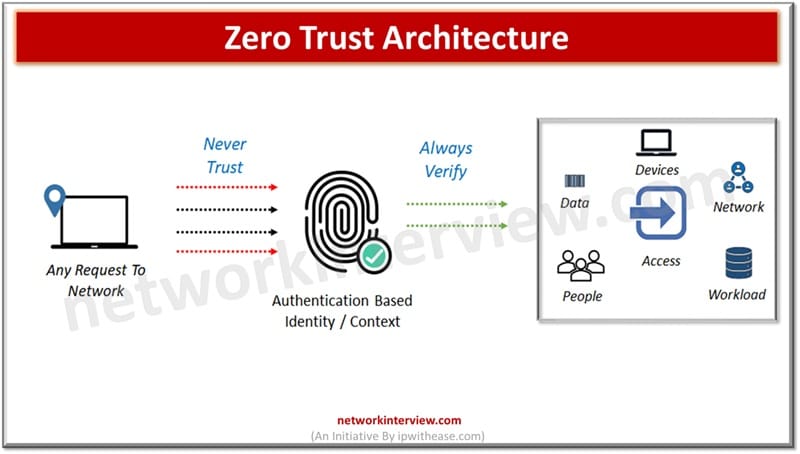
Traditional networks relied on authenticating once and getting inside and access to all resources. The modern networks operate on ‘Zero trust’ architecture which is a security framework working on the principle of no user, no device, no application is trusted …
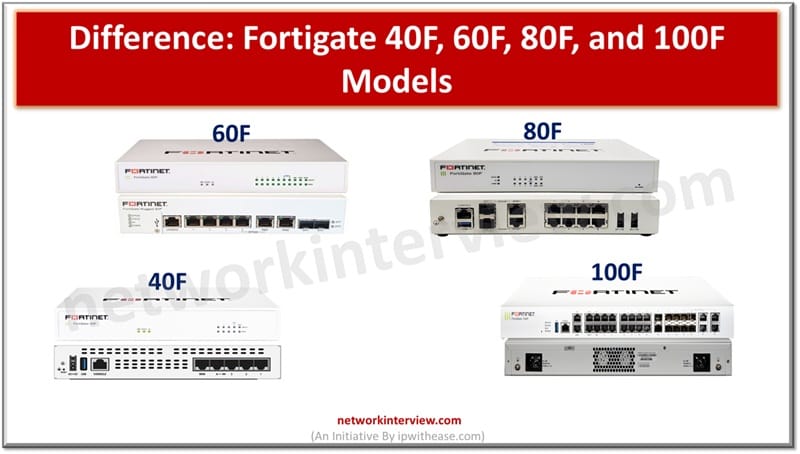
Fortigate 40F, 60F, 80F and 100F models differ in performance and scalability and are meant to address all types of businesses. While choosing a firewall one has to have a balanced approach and consider functionality and fit. Fortigate Next generation …
Artificial intelligence (AI) is leveraged to enhance threat detection and prevention by applying machine learning techniques and using intelligent algorithms. AI is empowering cybersecurity and helping in analysis of vast amounts of data, identification of threat patterns at a scale …
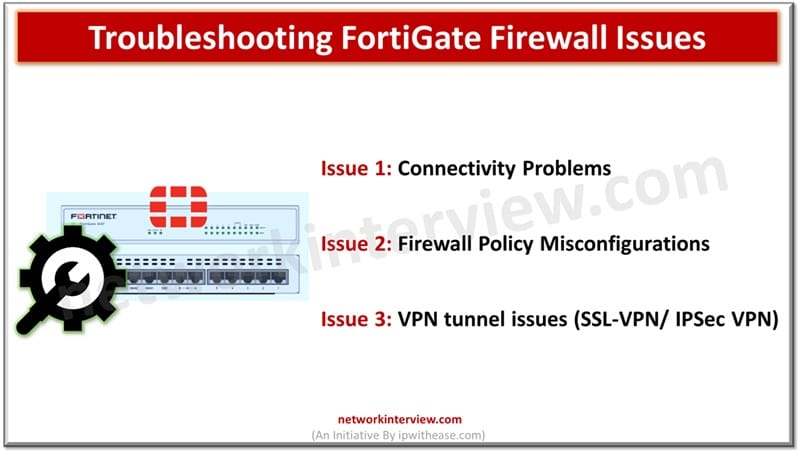
Like any other devices, firewalls do face disruptions and issues. For network administrators network disruptions due to firewall issues is critical as suddenly users cannot access critical resources, application failures occur, and expectation is to restore services to As-IS state …
Firewalls are the network’s first line of defense and provide protection from threats coming from the outside world. A strong, well built and secure firewalls provides an effective means to neutralize cyber threats. The cyber threats have increased multi-fold with …
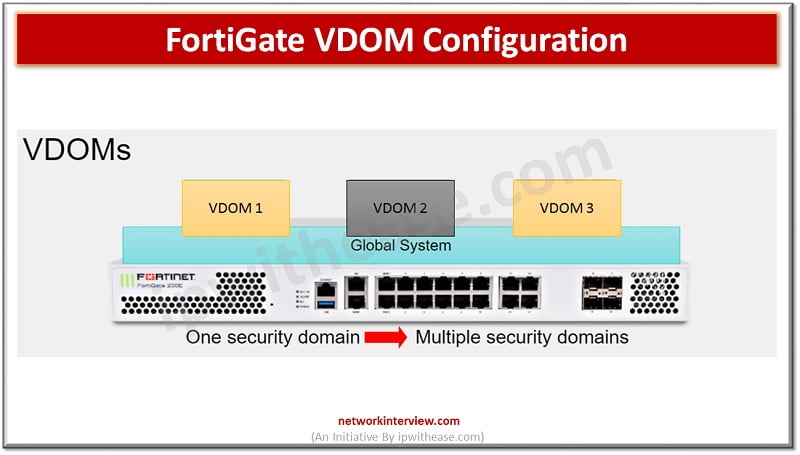
Understanding FortiGate VDOM FortiGate VDOM or Virtual Domain split FortiGate device into multiple virtual devices. Each VDOM has independent security policies, routing table and by-default traffic from VDOM can not move to different VDOM which means two interfaces of different …
The Evolving Cyber Threat Landscape Attack surfaces multiply faster than most organizations can patch. Last year, global ransomware incidents spiked over 37%, according to multiple threat intelligence reports, and IoT devices are still shipping with laughably weak security controls. Supply …
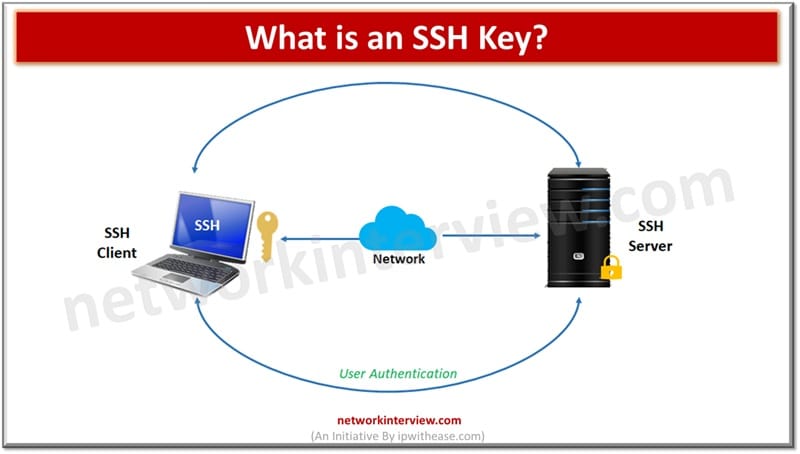
Modern cloud infrastructure highly relies on SSH keys and they are the foundation of secure access management in the cloud ecosystem. The SSH keys establish secure communication between servers and clients and provide faster access as compared to traditional password-based …
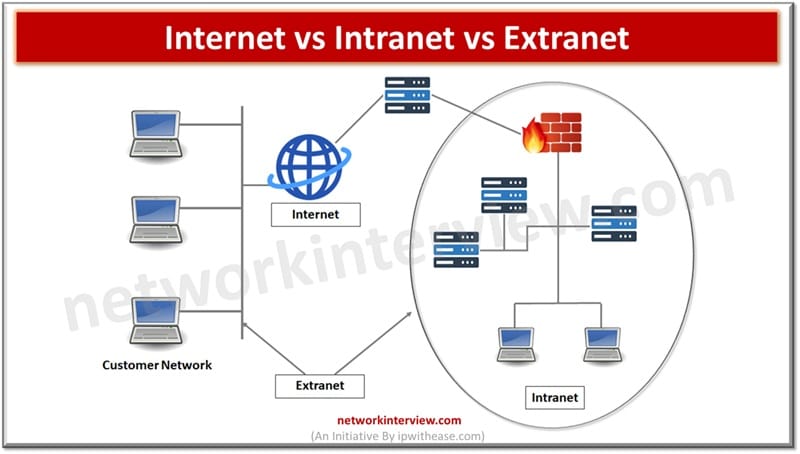
Networks are crucial in today’s digital world as they allow exchange, acquisitions and knowledge across organizations or within organizations. Every network meets a specific requirement as per its scope – connecting internal organizations, public ecosystem and secure connectivity with external …
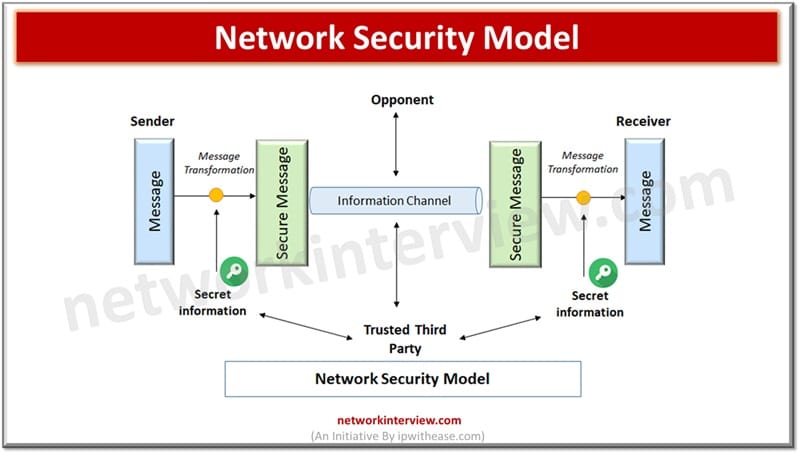
The moment we think about the power of the public Internet as the most viable and cheap medium of fastest communication, network security comes to mind as a matter of concern. Though fast, cheap and reliable but if not properly …
NAT-Network Address Translation NAT is a process that enables a single device such as a firewall or router to act as an agent between the internet or public network to LAN or private segment. NAT is usually use for below …
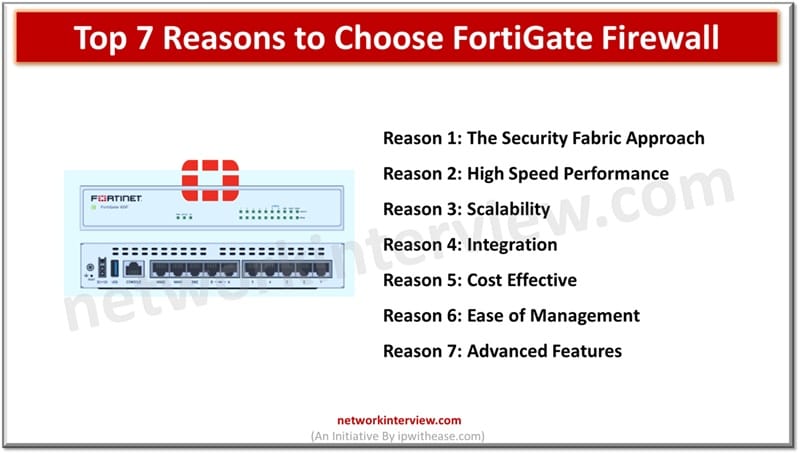
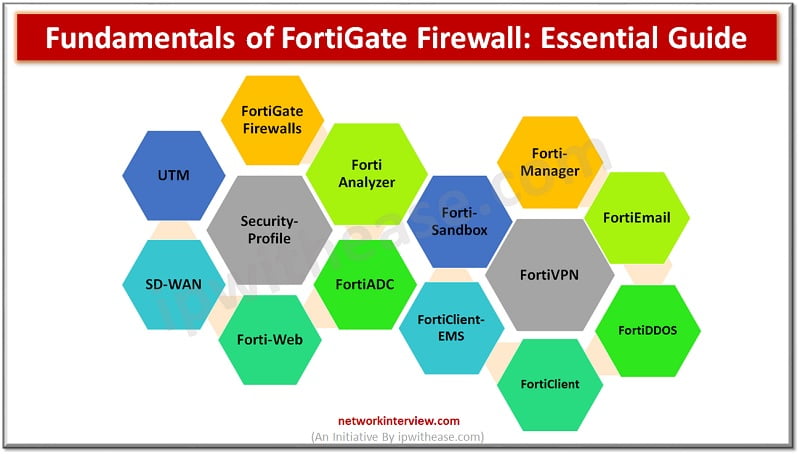
FortiGate fundamentals and principles involve high security infrastructure and provide a secure set up to the client. FortiGate Firewall is the most respected and highly used security product in the market. It uses artificial intelligence and machine learning to achieve …
With the widespread use of Internet and cloud computing, social networking, e-commerce applications, a large amount of data gets generated daily. Data security is a very crucial aspect of network security as more and more people are using the Internet …
Firewalls have evolved a lot since their inception. The gatekeeper or epitome of perimeter security used to enhance network security. Initial days firewalls were simple packet filters which examined packets of information passing through them and blocked which did not …
Firewalls are the backbone of all networks and they have come a long way from traditional packet-based filtering firewalls to Next generation firewalls having convention firewall with network device filtering functions involving deep packet inspection, intrusion prevention system (IPS), TLS …
Centralized network management and analysis of network devices is one of the vital requirements of enterprise networks. Individual network component monitoring in larger networks brings a lot of overhead in terms of skills, resources, expertise and not a viable solution …
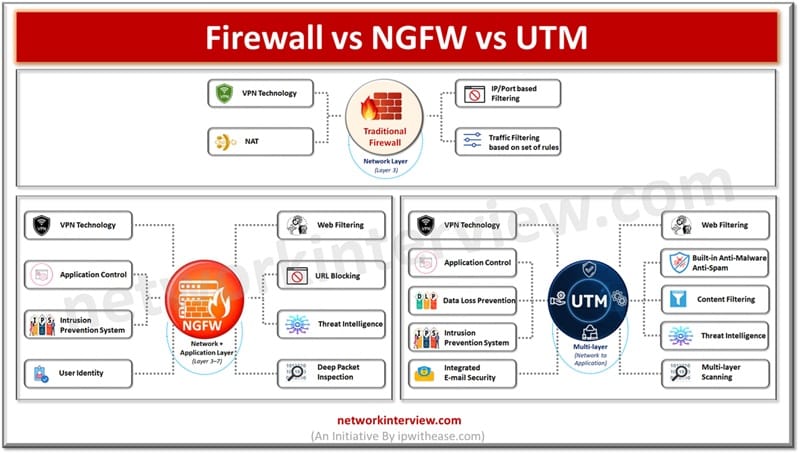
In today’s article we will understand the difference between traditional firewalls, Network generation firewalls (NGFW) and Unified threat management (UTM), their key features. Firewalls sit on the boundary of the network entry point and provide protection against malicious threats originating …
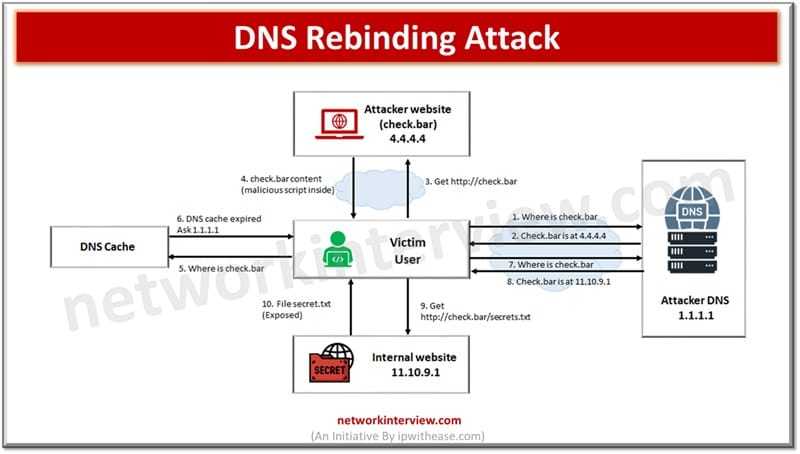
A DNS rebinding attack tricks a browser into bypassing same-origin policy, thereby allowing attackers to access internal networks or devices through malicious DNS responses. In networking systems are addressed with a unique numerical value which is known as IP address. …
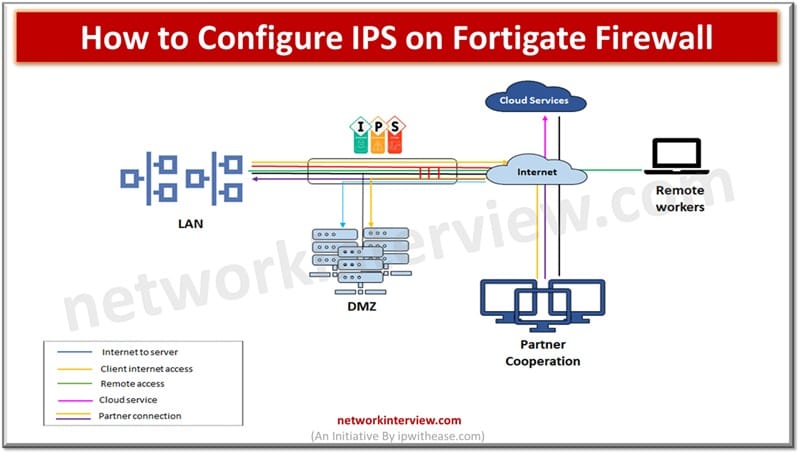
To configure IPS on a FortiGate firewall, enable an IPS sensor in the relevant security policy. Then, apply or customize the sensor under Security Profiles > Intrusion Prevention. Intrusion prevention systems or IPS provide security for the networks and hosts …
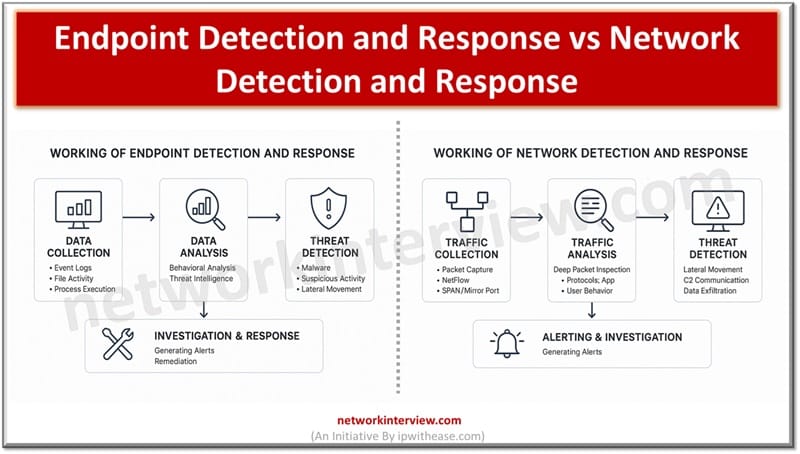
Endpoint Detection and Response focuses on monitoring and responding to threats on individual devices like laptops and servers. Whereas, Network Detection and Response monitors network traffic to detect and respond to threats across the entire network infrastructure. Constant threats and …
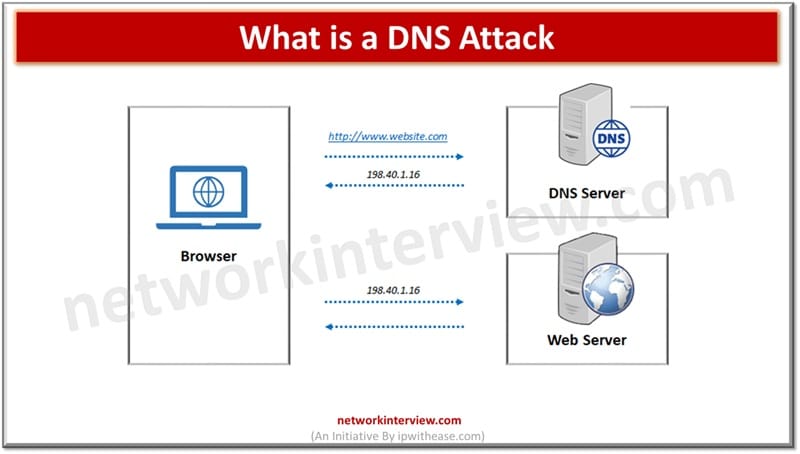
DNS (Domain name system) operates at the layer of OSI model in traditional networking. DNS is a very important protocol and backbone of the Internet, it translates human readable domain names to its corresponding numeric IP address which is used …
Since organizations are moving away from the traditional IT landscape to cloud computing, cloud-based assets, remote working models, the perimeter based old and traditional model of security is not sufficient enough for protection of data and sensitive systems. The modern …
With increased penetration of cloud computing, AI, machine learning cyber security incidents are on rise. Organizations are working towards reduction of risks associated with new upcoming technologies and trying to strike a balance between business growth and data security. Third …
Troubleshooting Palo Alto packet flow issues can be complex. In this blog, we will discuss some common Palo Alto Packet Flow Troubleshooting issues and troubleshooting steps. Palo Alto Packet Flow Troubleshooting Issues 1. Incorrect Security Policies Issue: Traffic is being …
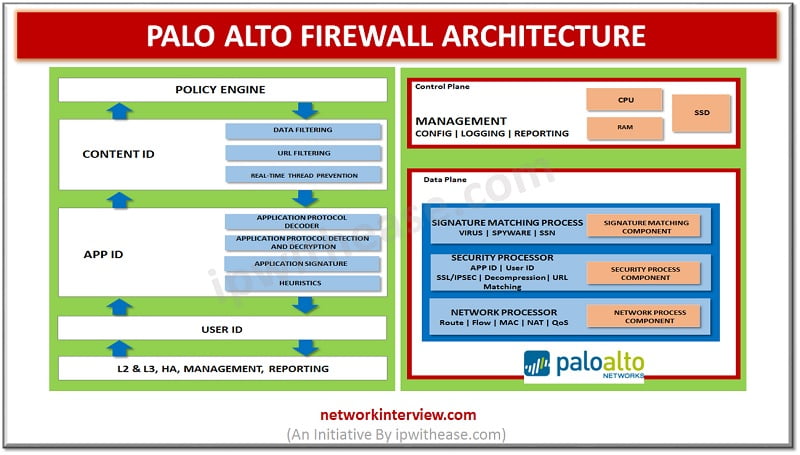
Network architecture refers to the structured approach of network, security devices and services structured to serve the connectivity needs of client devices, also considering controlled traffic flow and availability of services. Network devices typically include switches, routers and firewalls. Palo …
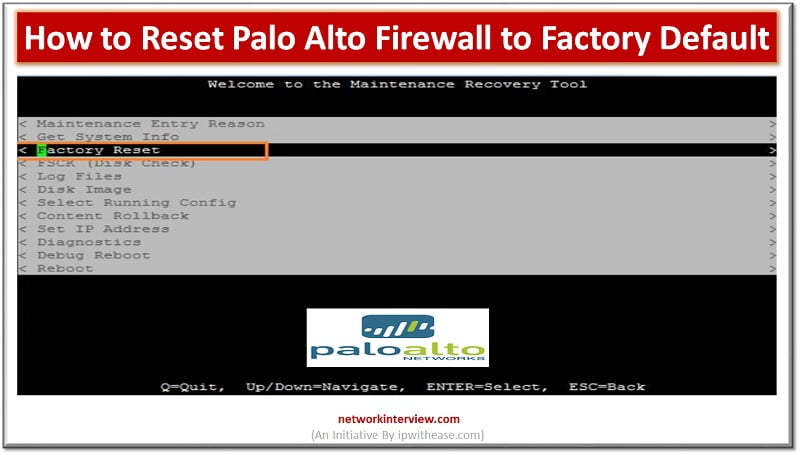
Introduction to Reset Palo Alto Firewall Firewall is a network security device which grants or rejects network access to traffic flowing between untrusted zone (External networks) to trusted (Internal networks) zone. Starting from initial days of Stateful inspection firewalls and …
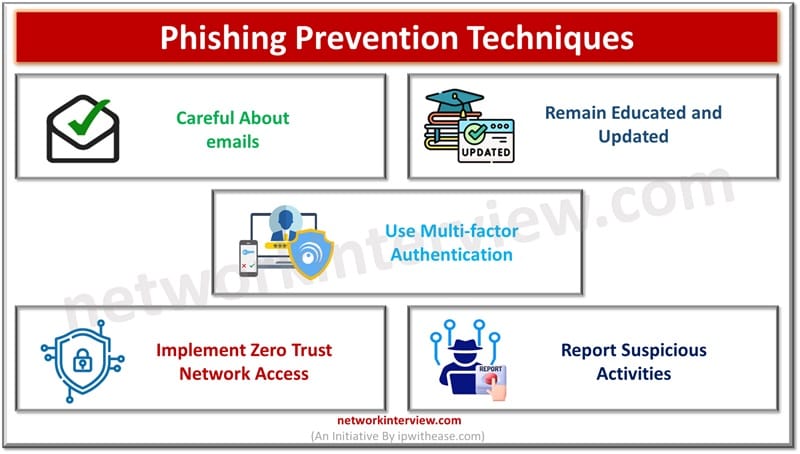
The amount and intensity of cybercrimes is growing exponentially based on social engineering techniques as humans are the weakest link in the chain of security and easy target of compromise. This is further fueled by remote operations. Most companies focus …
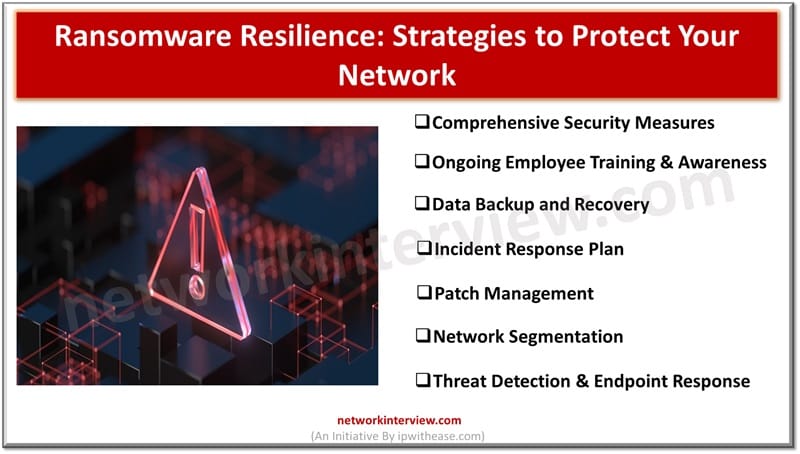
A resilient approach towards security and protection of digital assets is the need of the hour. The approach focuses on protection of hardware infrastructure and business applications to eliminate all vulnerabilities which could impact organizations, customers, and other stakeholders. Businesses …
This is the era of digital dominance and ransomware threat looms largely on enterprises and individuals. It is a kind of digital arrest which has emerged as the most menacing threat in recent years. Cybercriminals have targeted businesses, hospitals, government …
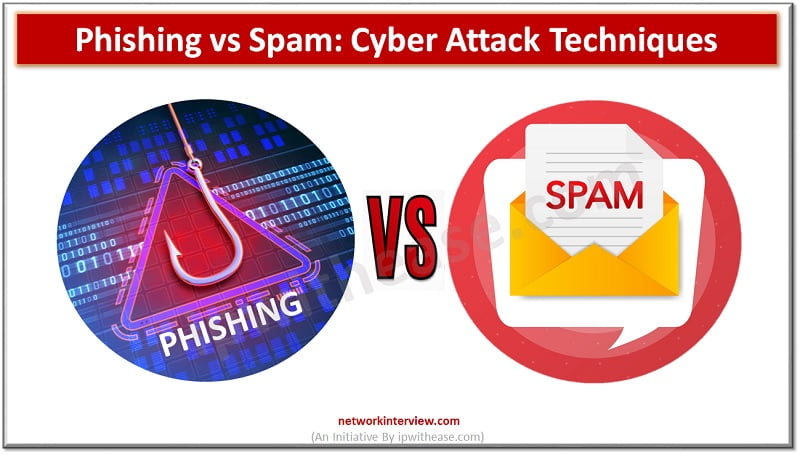
Cyber Attack Technologies Various forms of cyber attacks are prevailing these days and method of attack sophistication has reached new levels where now attackers are not limited only to fake websites, messages or emails but also focus is on theft …
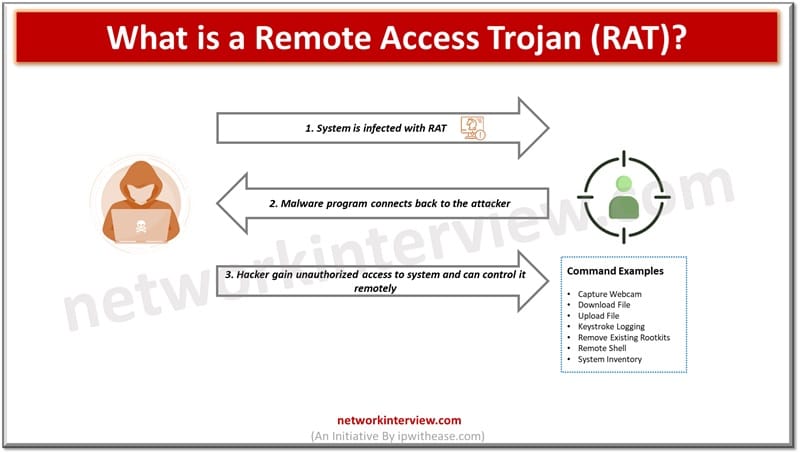
Remote access and control over systems remotely is widely used to provide technical support to users or work outside the boundaries of offices. With the rise of remote working however, especially during Covid-19 pandemic had allowed attackers to use remote …
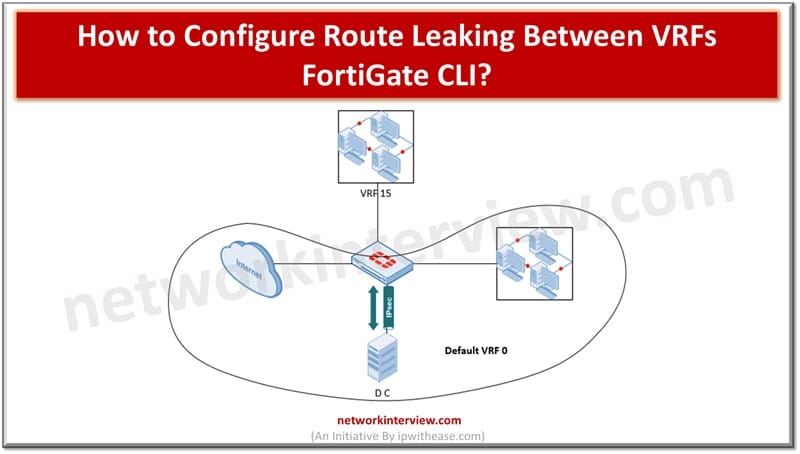
Cloud hosted workloads require customer traffic isolation and separate routing at logical level but through common hardware. Using virtual route forwarding (VRF) technique multiple routing tables can be created within the same router. VRF is used to divide routing functionality …
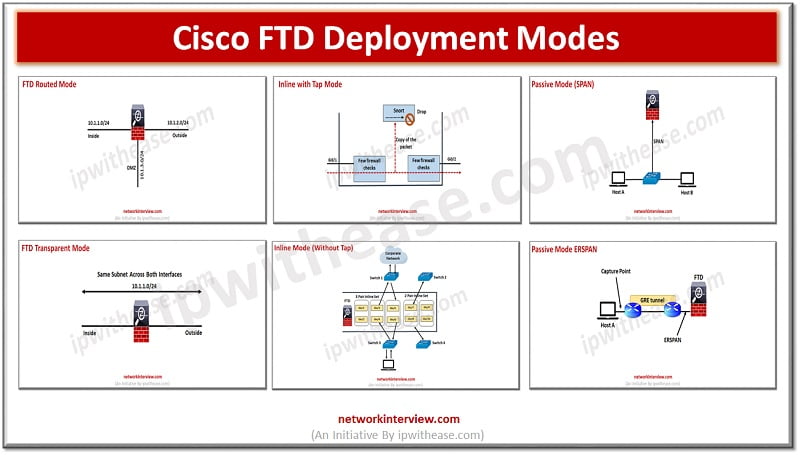
(FTD Deployment Modes: Routed, Transparent, Inline, Inline with tap, Passive SPAN, Passive ERSPAN) Cisco FTD design and deployment implementation involves setting up firewall, SSL inspection, NAT, IPS and active/standby HA. Deployment model determines placement of FirePower into the network as …
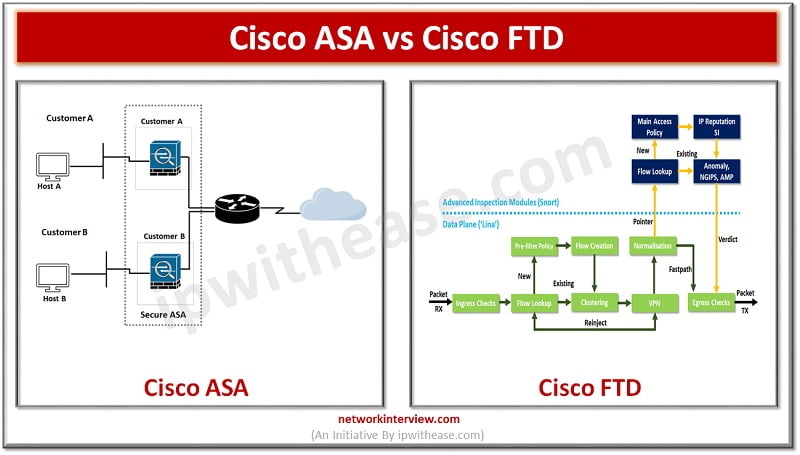
The Cisco Firepower Threat Defense (FTD) and Cisco Adaptive Security Appliance (ASA) are two types of security appliances that provide various features and capabilities to companies. These appliances were created with the intention of safeguarding businesses from cyber threats. Today …
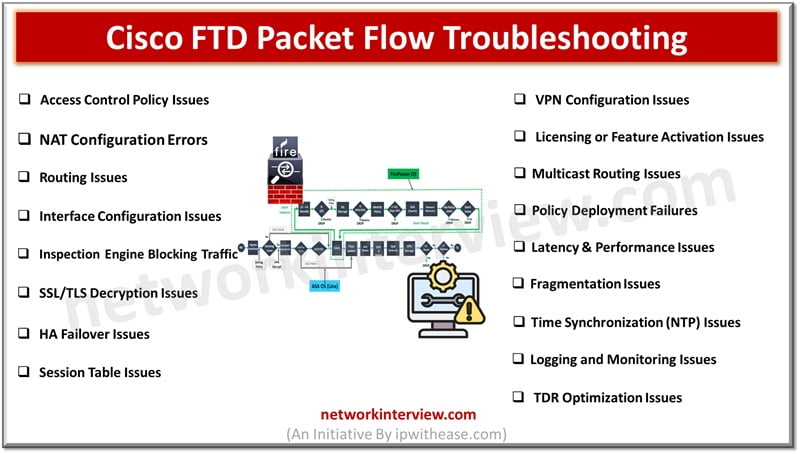
Troubleshooting Cisco FTD Packet Flow issues can be complex. Here is a summary of common Cisco FTD Packet Flow troubleshooting issues and the associated troubleshooting steps. Cisco FTD Packet Flow Troubleshooting Issues 1. Access Control Policy Issues Issue: Traffic is …
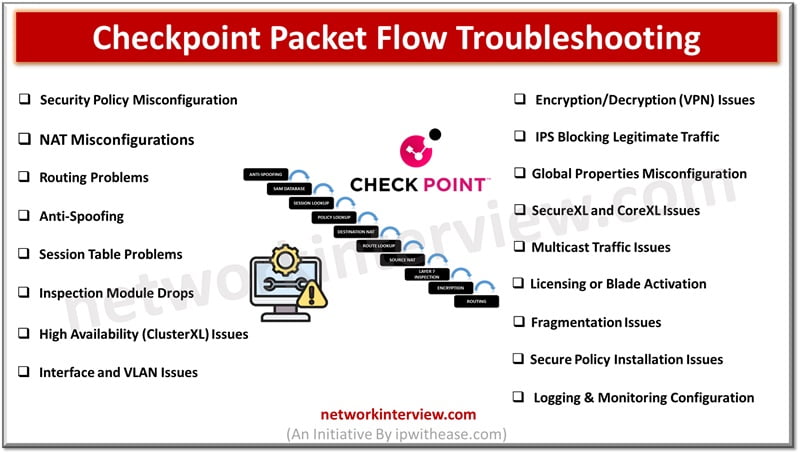
Troubleshooting Checkpoint Packet Flow issues can be complex. Here are common Checkpoint Packet Flow troubleshooting issues and steps to address them. Checkpoint Packet Flow Troubleshooting Issues 1. Security Policy Misconfiguration Issue: Traffic is dropped due to incorrect or missing security …
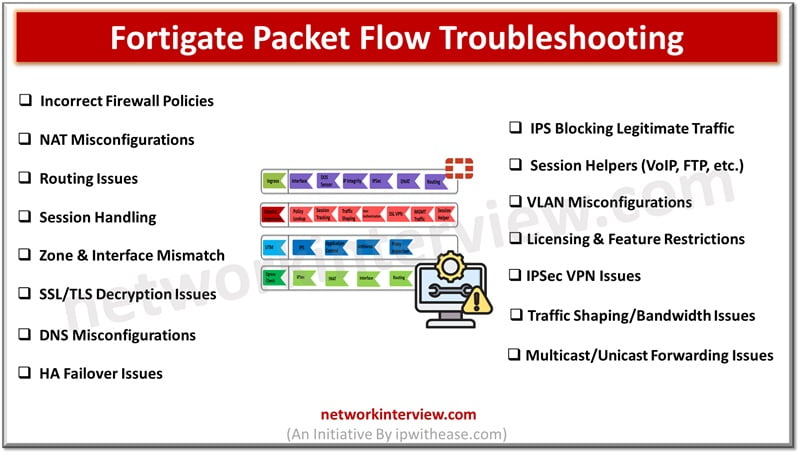
Troubleshooting Fortigate Packet Flow issues can be complex. Here’s an overview of common Fortigate Packet Flow troubleshooting issues and steps to resolve them. Fortigate Packet Flow Troubleshooting Issues 1. Incorrect Firewall Policies Issue: Traffic is dropped due to misconfigured firewall …
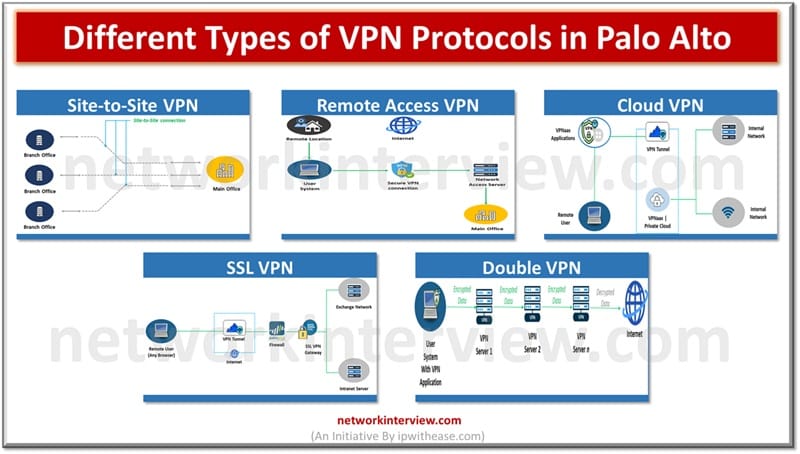
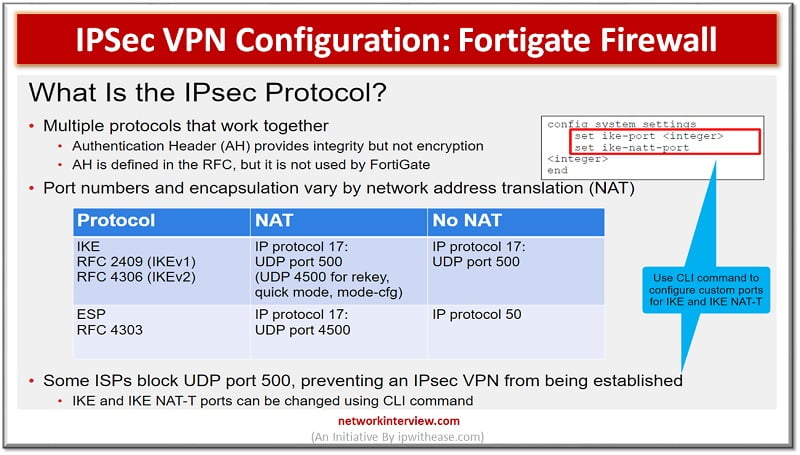
Objectives IPSec IKE Site to Site VPN between two FortiGate Sites Phase I and Phase II Parameters Tunnel Configuration Troubleshooting Commands IPSec VPN Configuration: Fortigate Firewall IPsec: It is a vendor neutral security protocol which is used to link …
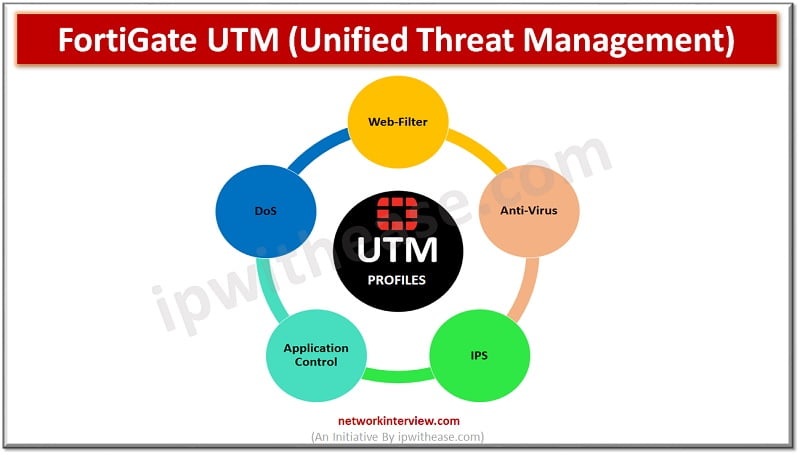
UTM-Unified Threat Management UTM (Unified Threat Management) is a feature of a firewall in which multiple security profiles combine and provide protection from threats and attacks. These features are antivirus, web filtering, IPS, anti-spam etc. UTM is the consolidated solution …
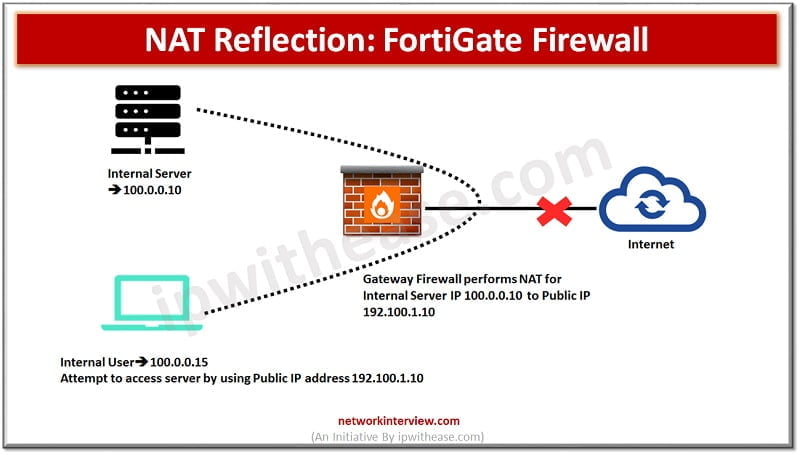
What is NAT Reflection? We use Hairpin NAT or NAT reflection when our aim is to access an internal server from an internal workstation of a client by being able to access the Public IP that would be bound to …
FortiGate firewalls are the primary line of defence against security threats coming from open Internet. The increasing sophistication in cyberattacks make it difficult to solely rely on firewalls for network protection. The NGFW firewall like FortiGate provides unified threat management …