Introduction to Crowdstrike
Introduction to Crowdstrike
Threat Intelligence and Endpoint Protection is of paramount importance for organizations especially in the scenario where organizations have moved their IT infrastructure over cloud and sophisticated hackers are moving beyond malware to breach organizations. Increasingly relying on exploits, zero-day vulnerabilities, and hard to detect methods such as credentials theft, and tools which are already part of the victim environment such as PowerShell.
A traditional anti-virus system which relies on definition/ signature updates , next generation antivirus (NGAV) such as Crowdstrike Falcon have additional capabilities such as endpoint protection and response (EDR), cyber threat intelligence and managed threat hunting capabilities- comprising a small sensor which is cloud managed and delivered.
In this article we will learn more about Crowdstrike, its features, advantages and how it works and how it has changed the way people looked at antivirus solutions way before.
What is Crowdstrike?
Traditionally organizations used endpoint security solutions which operated via an on-premises hub and spoke model, endpoints were protected via agents managed from the central console; this created silos because endpoints outside the network perimeter can’t be managed.
Crowdstrike was built ten years ago with the aim of becoming the Salesforce of security as the co founder and CEO George Kurz and by 2011 they entered in native security market by offering first of its cloud native platform to protect endpoint devices such as desktops, laptops, mobile phones, servers and tablets. It has revolutionized end point protection by unifying antivirus , endpoint detection and response and 24/7 managed hunting service – all bundle into one single lightweight agent (20 MB footprint only).
Crowdstrike Falcon is a single lightweight agent architecture cloud-based solution for endpoints protection which offers real time protection and visibility across enterprises to prevent attacks on endpoints on or off the network. It collates trillions of endpoint related events using its proprietary crowdstrike threat graph database to identify threats in real time across the globe. Crowdstrike protects against all cyber attack types including sophisticated signature less AI and indicator of attack (IoA) based threat prevention to stop known and unknown threats in real time.
Features of Crowdstrike Falcon
- Prevents both commodity and sophisticated attacks irrespective of its is malware or not , endpoint is on or off
- Gain real time insight into applications and processes running across the environment, ensure nothing is missed and response is provided
- Proactively hunt advanced threat activity in a fast and efficient manner
- Protection of all workloads, from mobile devices to traditional endpoints running windows, MacOS, and Linux , cloud workloads , servers and containers in hybrid multi cloud data centres
- Eliminate bloat and massive performance impact which traditional anti-virus solutions bring in and replace it with a single lightweight agent meant for speed
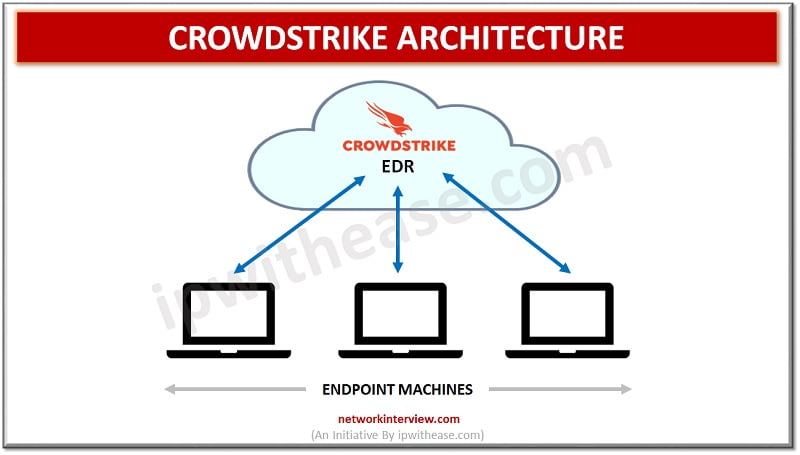
Crowdstrike Architecture
Cloud native endpoint security is controlled via a central console in the cloud and connects to devices via agents placed on endpoints themselves. These agents work independently even if the agent is offline.
Crowdstrike architecture comprises two components –
- lightweight agent
- cloud based dynamic graph database called threat graph.
The lightweight agent collects information and streams data to the cloud. It does local endpoint prevention and detection.
The threat graph processes, correlates, and analyses endpoint related events in real time and maintains an index of the events. It continuously analyses the malicious activity by applying threat graph AI and analytics.
Crowdstrike has ten cloud modules across three categories namely :
- Endpoint security
- Security and IT operations
- Threat Intelligence
Endpoint security modules help to defend against malware and malware free attacks, provide endpoint activity visibility, insight into USB devices
Conclusion
Crowdstrike Intelligence offerings give customized intelligence which is accessible and easy to use. It offers tailor made solutions depending on organization requirements and help to improve response capabilities and reduction in risk to breaches.



