What is SDP (Software Defined Perimeter)?
Agility and innovation are key ingredients for digital transformation. However, agility requirements are hindered by telco-controlled SD WAN or MPLS networks. Slow moving ISPs and need to deploy expensive custom hardware, telco circuits, and VPNs create roadblocks and stop transformation in its tracks. Most of the network architectures were not built for today’s multi-cloud, hybrid networks leading to disparate security hardware and processes which define them to be practically secured.
Since the beginning of digital era companies have used firewalls to enforce perimeter security and users were confined to firms own building but with a growing mobile workforce there is a surge in the variety of devices used to access resources, change in architecture to support transformation, and explosive growth of clouds – private, public and hybrid the traditional philosophy of perimeter is slowly diminished and reached to point of obsolesce.
Today we look more in detail about SDP or Software defined perimeter, its features, advantages, use cases etc.
Software Defined Perimeter
The physical boundary or perimeter model does not exist anymore. The perimeter is not just a physical location of an enterprise any more if the traditional perimeter is breached or compromised an attacker can very easily access an organization’s privileged internal network which means what lies inside the perimeter is no longer secure and safer as it was thought earlier. This is resulting in companies dumping traditional perimeter security or network methods such as MPLS and implementing software defined perimeters. Software defined perimeters control access to resources based on identity.
SDP is a security framework which controls access to resources on the basis of identity. Establishing a perimeter via software instead of hardware lets organizations hide its infrastructure to the external world irrespective of where it is located and only enables authorized users to access it.
The framework is based on the Department of Defence (US DOD) Defence information systems agency (DISA) on ‘need to know model’ from 2007 wherein all endpoints were given access to infrastructure based on authentication and prior authorization. In 2013 cloud security alliance (CSA) released its SDP working group guidance while incorporating elements of DISA’s work with security standards from the National Institute of Standards and Technology (NIST) and other organizations. SDP is also sometimes known as ‘black cloud’ because it obscures systems by cloaking them within the perimeter so external users can’t see it.
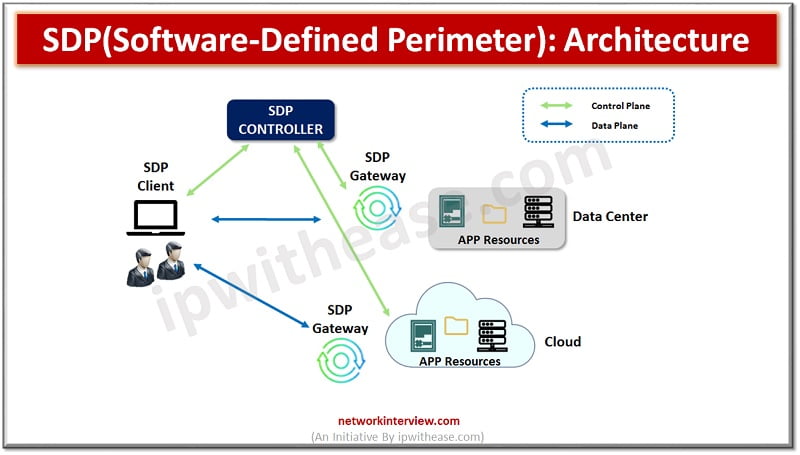
Software Defined Perimeter (SDP): Architecture
SDP creates a secure perimeter based on policies to isolate services from unsecured networks. Access control Principle Of Least Privileges (POLP) is used to secure devices and give users and devices only access which is required to perform the task in hand. It offers on demand, dynamically provisioned, air-gagged, network segmentation of network resources which mirrors a physically defined network perimeter but uses software instead of a hardware appliance. Unauthorized users and devices cannot connect to protected users.
Components of SDP Architecture
There are two main components of SDP architecture:
SDP controllers and SDP hosts.
- An SDP controller decides which SDP hosts can communicate to each other.
- An SDP host can either initiate a request for connection or accept a request for connection.
The SDP hosts communicate via SDP controller which determines which hosts they can connect to. Some SDP architectures also use gateways and act as the accepting host between two devices /users getting connected. The entire communication is encrypted, often using virtual private network (VPN) tunnels between controllers, hosts and gateways.
Features of Software Defined Perimeter
- Secure access which enables DevOps users to isolate workloads and access to key resources
- Network or application segmentation minimizes attack surface and malware propagation inside cloud and data centres
- Provides secure, easy and direct access to cloud applications and easy access to resources from user own device
- Enables privileged and third-party access to systems from any location in limited and secure manner
Use cases of Software Defined Perimeter
- SDP supports variety of devices and let virtual perimeter define authentication for laptops, personal computers, mobile and IoT devices
- SDPs can be used to restrict broad network access and let devices only access specific devices or hosts as per permitted policy
- Risk based policy can be defined using SDP
- Enablement of control of services, applications to limit attack services
- Application isolation can be achieved using SDP
- Securing hybrid or public clouds
Quick facts !
As per Markets and Markets forecast the global software defined perimeter (SDP) market size to grow from USD 2.9 billion in 2019 to USD 13.8 billion by 2024.
Continue Reading:
Tag:Security



