Vulnerability Assessment and Penetration Testing: What’s the difference?
Introduction
Vulnerability assessment is the way to identify weakness in the system. Vulnerability itself means “Weakness” and Vulnerability assessment means how to find weakness in a system and create a report accordingly. On the other hand, Penetration testing is used to identify vulnerable areas of an organisation and exploit it by performing multiple tests to identify the loopholes and its mitigation process.
Vulnerability assessment and Penetration testing both are also recognized as VAPT.
Vulnerability assessment tools discover which weaknesses are present and where these weaknesses are located. Penetration testing exploits the vulnerability of a system through unauthorized access or malicious activity and tries to identify which errors pose a threat to the application.
Sometimes organizations suffer from massive attack or loss that could have been evaded if protection measures were taken at the right time. Incidents contain events such as attack in network infrastructure due to low security configures in devices, data loss, unauthenticated and unauthorised access, information leakage and many others. VAPT helps to provide an analysis to proactively identify the vulnerability of the organisation’s system and provide appropriate action accordingly.
Moreover, it saves time and money to solve the further issues related to cyber attack.
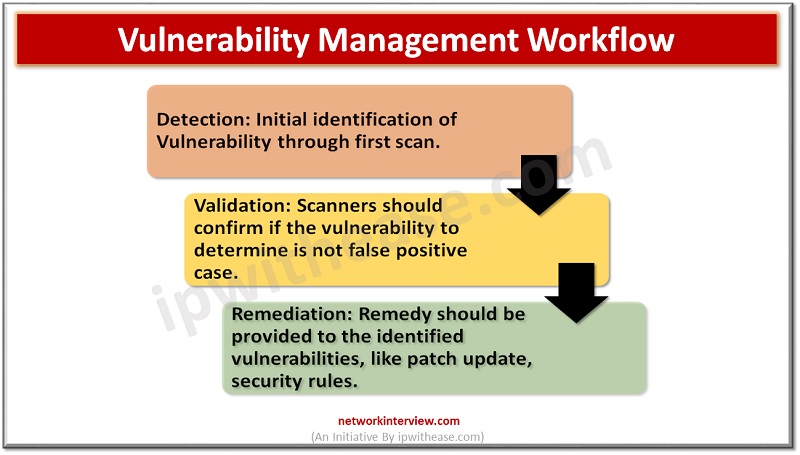
Let’s discuss the steps for Vulnerability Assessment.
Performing Vulnerability Assessment
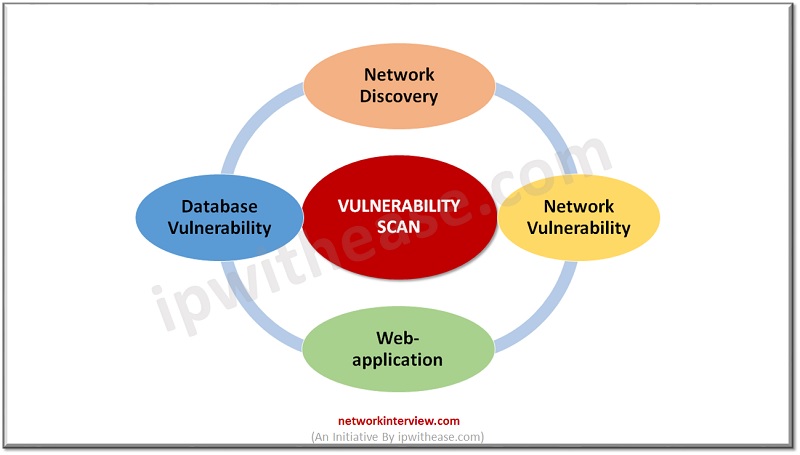
Vulnerability assessment starts with vulnerability scan. Scan can probe systems, network infrastructure, servers, web-applications that may be exploited by any hacker or intruder. Scan tools perform scanning on a periodic basis and generate reports which show differences between the scans, performed on different dates, time, month and provide an overview of risk in the environment to the administrator.
Vulnerability Scan further divided into four different categories
- Network Discovery Scan
- Network Vulnerability Scan
- Web-application Vulnerability Scan
- Database Vulnerability Scan
1. Network Discovery Scan
As the name indicates, Network discovery is used to scan the IP subnets, IP addresses, open network ports and associated application ports which are open in the network.
Common techniques to identify open ports on remote machine or remote system are as follows:
- TCP SYN Scanning: Test SYN flag and scanned port by sending SYN packet. If the tester receives a response with ACK flag which means the port is open and the system/network device is vulnerable.
- TCP Connect: If the tester is able to access the system on a specific port which means the remote system is open to connect with the unknown sender.
- TCP ACK: Sends TCP ACK packet to check if traffic is allowed by any in-between Firewall.
- Xmas Scanning: send a set of packets which has FIN, PSH and URH flag if accepted by the network devices which means multiple interface security is not allowed in the network devices.
Most common scanner is Nmap which helps to identify the connection status in the network by performing a scan.
2. Network Vulnerability Scan
Network Discovery scan only focuses on open ports in the network whereas network vulnerability scan detects and investigates the vulnerability in a deeper way. Network Vulnerability tool has a huge database of known vulnerabilities which is used to identify if a system is weak in terms of security.
Scanner matches the vulnerability in its database and checks the criteria with the found vulnerability and generates the analysis based on the output of analysis.
Scans are further divided into low-risk scan and high-risk scan. Nessus is the device which is a commonly used vulnerability scanner in industries.
3. Web Vulnerability Scan
Focus areas of Web Vulnerability Scan are servers which have handled multiple applications. Firewalls and other network devices provide protection to those servers and their applications from the outside world. Attackers often try to get access to the application through unauthorized approaches. Here, Web-Vulnerability scanners perform appropriate tasks to avoid any malicious attack on the servers.
When administrators run the scanner tool in the network, the tool examines the web application using computerized techniques that operate inputs and other restrictions to identify web vulnerabilities.
Task performed during Web-Vulnerability Scan:
- Initially scan all the known applications in the web server and create a report accordingly.
- Scan new applications which are recently deployed and check the vulnerability.
- Scan modified applications that are customised by the administrator as per the requirement of code.
- Scan unknown applications and try to find any bug or malicious code in the server.
- Scan all the applications altogether on a repeated basis and create a comparison report to analyse the pattern of traffic flow for the servers and respective applications.
4. Database Vulnerability Scan
Databases cover the most delicate and sensitive data and are worthwhile targets for hackers and attackers. Databases are protected by firewalls, local servers, routers from direct external access. Most common attack performed on a database is SQL Injection Attack. Database vulnerability scanners are the tools that perform professional scan to databases and associated servers.. sqlmap is an open source commonly used scanner that allows tester team to probe scanning on the database servers.
Penetration Testing
Penetration testing is a practical way to exploit the system along with management approvals. Vulnerability assessment focuses more on reports and identification of weakness in the system whereas Pentest (Penetration Testing) emphasizes on a practical approach to hijack the system and try to identify the root cause of vulnerability. Penetration tests are performed by trained and experienced professionals.
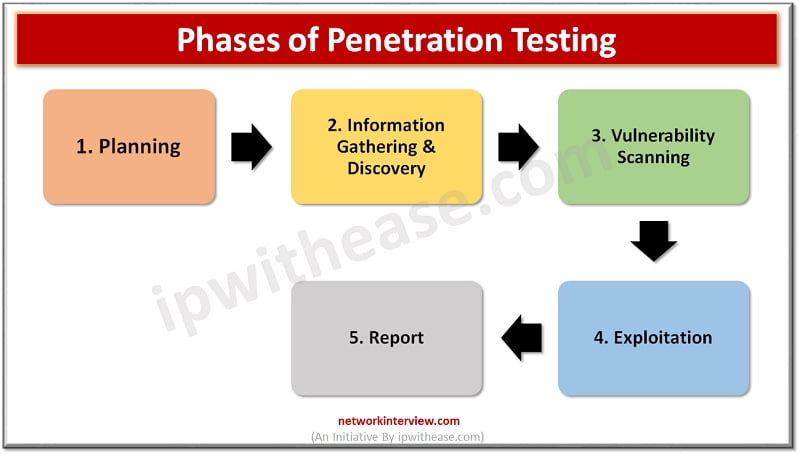
- Planning: Most time-consuming phase in which tester and management discussed the scope of the test.
- Information gathering and discovery: In this phase tester/team performs reconnaissance to identify system functions and conducts network discovery scans to determine open ports in the network. It could be both a manual and automatic tool.
- Vulnerability scanning: examinations of system weaknesses by using methods like network vulnerability scans, web vulnerability scans, and database vulnerability scans.
- Exploitation: use manual and automated exploit tools to check and identify system security.
- Reporting: Both testing team and administration evaluates the output of penetration testing and makes recommendations for improvements to system security.
Penetration testers may be inside employees or external testers who perform these tests as part of their duties or external consultants hired to perform penetration tests.
Categories of Penetration test
The Penetration test are generally categorized into three groups:
- White Box Penetration Test: attackers know the background of the network, he/she has detailed information of the system in which testing will be performed. In this approach knowledge of internal data structure, backend sources and architecture will be shared and analysed by examiner,
- Black Box Penetration Test: No prior information of network infrastructure is shared with the tester. External attacker performs an attack without any prior information of the target system.
- Gray Box Penetration Test: It is the combination of white box and black box testing. Advantages and disadvantages of both black box and white box testing are used in this technique.
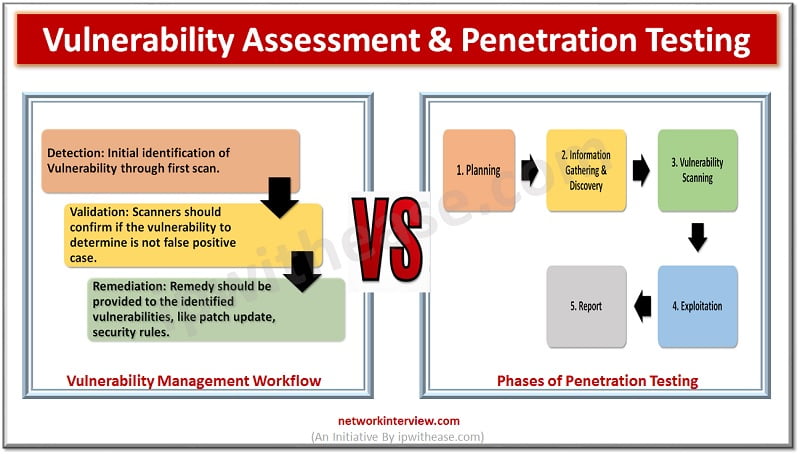
Comparison: Vulnerability Assessment vs Penetration Testing
Finally let’s illustrate the difference between Vulnerability Assessment and Penetration Testing
Feature | Vulnerability Assessments | Penetration Testing |
| Definition | It is a process of identifying, quantifying, and prioritizing the vulnerabilities in a system. | It describes the intentional launching of simulated cyber attacks by white hat penetration testers to gain the access of network. |
| Work | Identify the weakness of system and generate report of vulnerability scans. | Eliminate the vulnerability of system and provide report to higher management. |
| Type of Network | Target non-critical environment. | Target real network and critical systems. |
| Scope | Perform scans by using automatic tools and provide report according to the output of analysis. | Documentation of requirement, review and then perform test in the live network. |
| Time-Consume | It is a constant process, however less time consuming. | Less time consumed. |
| Cost | Moderate | High |
Download the comparison table: Vulnerability scan vs Pen test
Conclusion
VAPT has different functionalities and methods, so it depends upon the infrastructure and organisation’s network architecture to select the best approach according to the requirement. A vulnerability assessment tries to expand and improve security of a system and develops a more documented method to achieve a secure network. On the other hand, penetration testing only gives a picture of your security program’s weakness and mitigation.
But professionals suggest that, as a part of the security management system, both techniques should be performed regularly to confirm a secured environment.
Thanks for reading!!!!
Continue Reading:
Top 10 Penetration Testing Tools & Software
Common Types of Attacks on Routers
Tag:comparison, Security