Understanding Juniper SRX Modes
Firewalls perform the processing of traffic for packets which enter and exit a device. Juniper SRX firewalls have a wide variety of filtering and traffic shaping features including policies, screens, network address translation (NAT) and services based on flow. Processing could be packet based and flow based depending on the requirements.
Today we look more in detail about Juniper SRX next generation firewalls mode of traffic processing, how traffic processing happens in those modes and its characteristics.
Traffic Processing in Juniper SRX
Traffic which enters and exits from firewall is processed as per configured features such as screens, packet filters and security policies. Packets entering or exiting the device have both packet based and flow-based processing.
Flow-Based Processing
Packets undergo flow-based processing post packet-based filters and some screens applied before. All flow-based processing happens on a single flow on a single service processing unit (SPU). SPU processes flow of packets according to security features and services configured in.
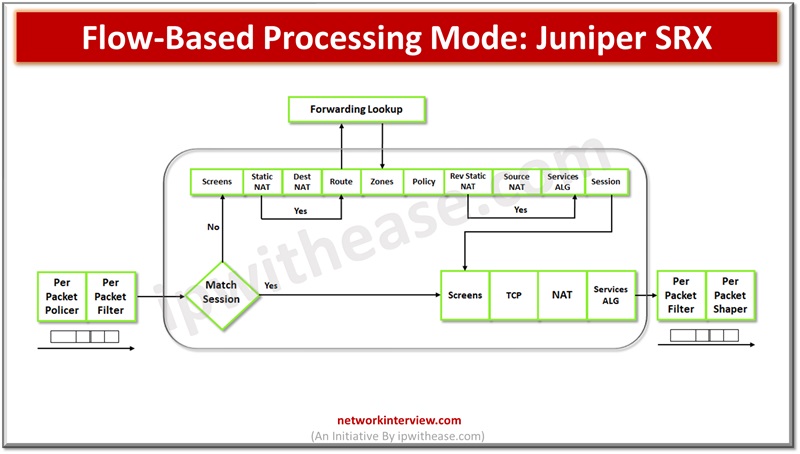
A flow comprises a stream of packets which are related and meet a matching criteria and share characteristics. Flow based processing or stateful processing performs creation of sessions. Session is created for first packet in flow for the purposes:
- To store security measures applies to flow of packets
- Caching information about state of flow
- Allocation of resources for features of flow such as NAT
- Framework for features such as firewall features and ALGs
Processing happens in the context of flow including
- Policies, NAT, zones management
- Authentication and AIGs management
Packet-Based Processing
Packet-based processing happens when it is removed from the queue from the input interface and before putting back on the queue for its output interface. Packet based flow processing applies stateless filters, CoS features and screens having discrete packets. On receiving packets at an interface, sanity check, packet-based filter, CoS features and some screens it is applied to.
While a packet leaves the device at an interface, sanity check, packet-based filter, CoS features and some screens it is applied to.
Packet filters and CoS features are associated with interface or interfaces impacting packets are allowed to transit system and apply special actions.
Packets which enter and exit the firewall perform packet-based processing. Stateless or packet based, packets are treated discreetly. Each packet is analysed individually. Stateless packet-based forwarding happens without regard to flow or state information on a packet-to-packet basis.
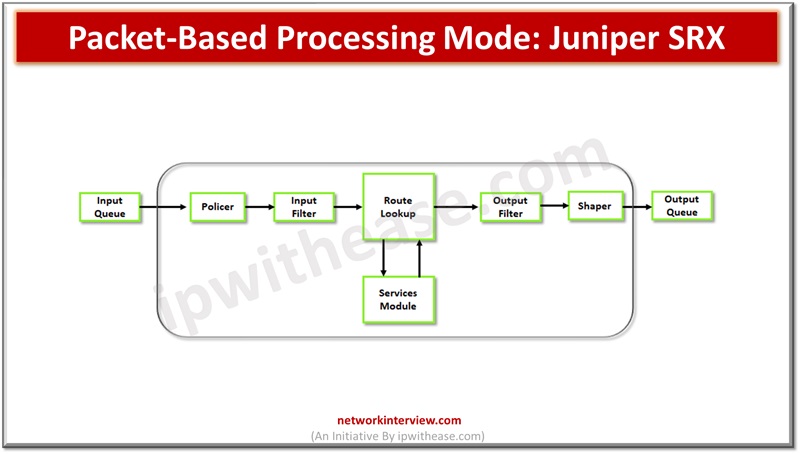
When a packet enters devices, classifiers, filters, and policies apply. The egress interface of the packet is identified via a route lookup. When the egress interface is identified for the packet, filters are applied and the packet is sent to the egress interface for queuing and scheduling happens for transmission. Packet based forwarding does not need information of previous or subsequent packets which belong to a given connection and packet specific allow or deny of traffic happens.
Comparison: Packet-based and Flow-based Processing Modes
Below is the comparison between packet-based and flow-based processing modes in Juniper SRX firewalls:
JUNIPER SRX FIREWALL | ||
| Feature | Packet-Based Processing Mode | Flow-Based Processing Mode |
| Basic Operation | Processes each packet individually as it arrives | Aggregates packets into flows and processes them |
| Traffic Handling | Treats each packet as an individual entity | Groups packets into flows based on session |
| Stateful Inspection | Performs stateful inspection on each packet | Inspects packets within context of established flows |
| Resource Usage | Consumes more system resources due to per-packet processing | Consumes fewer resources as it aggregates packets into flows |
| Efficiency | Suitable for environments with low to moderate traffic | Suitable for environments with high traffic volumes |
| Performance | Offers lower performance compared to flow-based mode | Offers higher performance due to flow optimization |
| Session Tracking | Tracks sessions at the packet level | Tracks sessions at the flow level |
| Security Policy Enforcement | Enforces security policies on a per-packet basis | Enforces security policies within the context of established flows |
Download the comparison table: Packet-based vs Flow-based Processing Modes
Final Words
In summary, packet-based processing mode handles each packet individually, while flow-based processing mode aggregates packets into flows and processes them accordingly. Flow-based processing offers better performance and efficiency, especially in high-traffic environments, by reducing resource consumption through flow optimization. However, packet-based processing may be more suitable for environments with lower traffic volumes or specific security requirements.
Continue Reading:
How To Configure Juniper SRX Security Policy?
How to configure Juniper SRX Firewall? Step by Step Guide
Tag:Juniper SRX, Security



