NAT Configuration & NAT Types – Palo Alto
In the previous post we discussed the Architecture of Palo alto firewall. Now, we will discuss the NAT configuration and NAT types in Palo alto.
Network Address Translation (NAT) allows to translate private, non-routable IP addresses to one or more globally routable IP addresses, thereby saving an organization’s routable IP addresses. Palo Alto firewall supports NAT on Layer 3 and virtual wire interfaces. In PAN-OS, NAT policy rules instruct the firewall what action have to be taken.
Palo Alto NAT Policy Overview
NAT rule is created to match a packet’s source zone and destination zone. Zones are created to inspect packets from source and destination. Palo Alto evaluates the rules in a sequential order from the top to down. Palo Alto firewall checks the packet and performs a route lookup to find the egress interface and zone. Next, it verifies the packet and matches one of the NAT rules that have been defined in zones, based on source and destination zone. Policy is created and then applied to match the packet based on source and destination address.
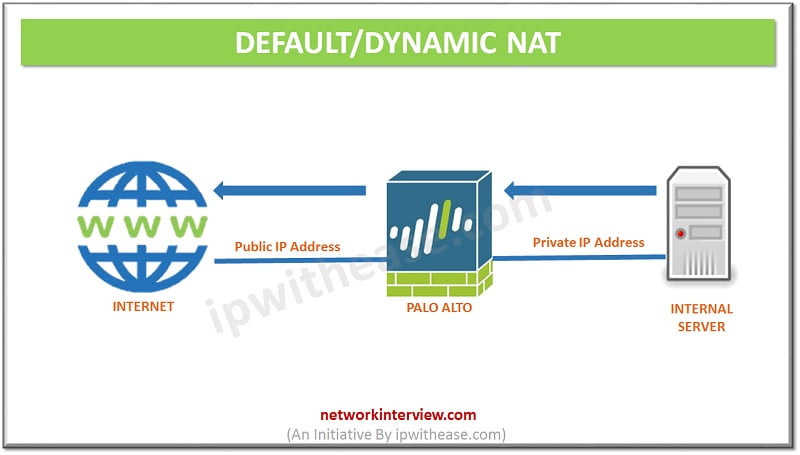
One to one NAT is called in Palo Alto as static NAT. Palo Alto Firewall reads the pre-NAT parameters like
- Pre-NAT IP address
- Pre-NAT zone
Step by Step process – NAT Configuration in Palo Alto
STEP 1: Create the zones and interfaces
- Login to the Palo Alto firewall and navigate to the “network tab”.
- Create the three zones
- Trust
- un trust A
- un trust B
- Create the layer 3 interfaces and tie them to the corresponding zones along with the IP addresses.
STEP 2: Configure layer 3 routing
- Navigate to the virtual router workspace and configure any layer 3 requirement of your network.
STEP 3: Create the NAT statements
- Define the NAT statements on the firewall. Go to the policies tab and select the NAT workspace.
- Our purpose is to allow traversal of traffic from the internal user subnet going into the lab devices on “un trust B” using the routable private IP space.
STEP 4: Create the matching security rule
- Every NAT rule should be paired with a corresponding security rule. Go to the security workspace on the policies tab.
- As established earlier, the pre-NAT IP is preserved at least on how the firewall processes the packet so the security rule will still utilize the pre-NAT IP addresses.
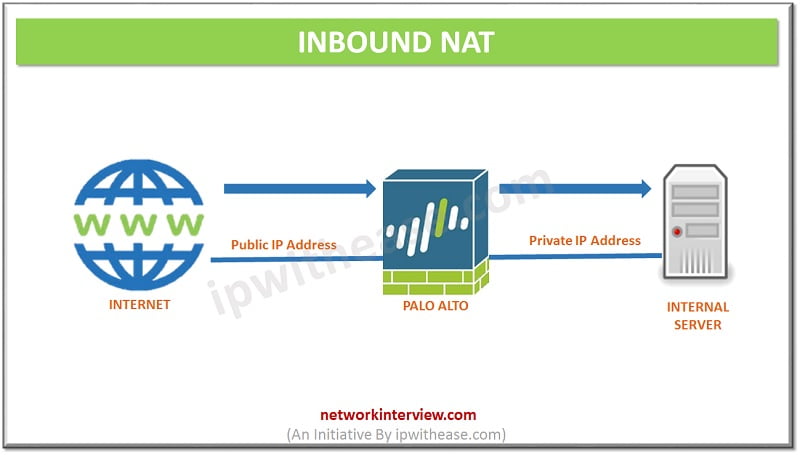
NAT Types – Palo alto
1. Many-to-One, Hide NAT, Source NAT
Hide NAT is the most common use of address translation. It hides all internal local LAN subnets behind a single external public IP. NAT policy will translate subnet originating from the trust zone, going out to the untrust zone and will change the source address to the IP assigned to the external physical interface. It will also randomize the source port. When packets are received back from destination, it will automatically be reverse translated and the firewall maintains a state table tracking all active sessions and their NAT actions.
2. Many-to-Many NAT
In this NAT type, the address is changed from Interface to translated address. Palo Alto Firewall selects an IP from the available pool based on a source IP address. Source address will remain the same for all translated IPs. Source port is randomized. If the source ports remains the same (depends upon application where a specific source port may be require) the translation type is Dynamic NAT, which will preserve the client’s source port per translation.
3. One-to-One NAT, Static NAT
This is one to one mapping of internal IP with external global IP. Webserver is mapped with single global IP to get access from internet. One-to-one NAT policy translates and forwards incoming connections to the specific server. Following are two ways to achieve this: –
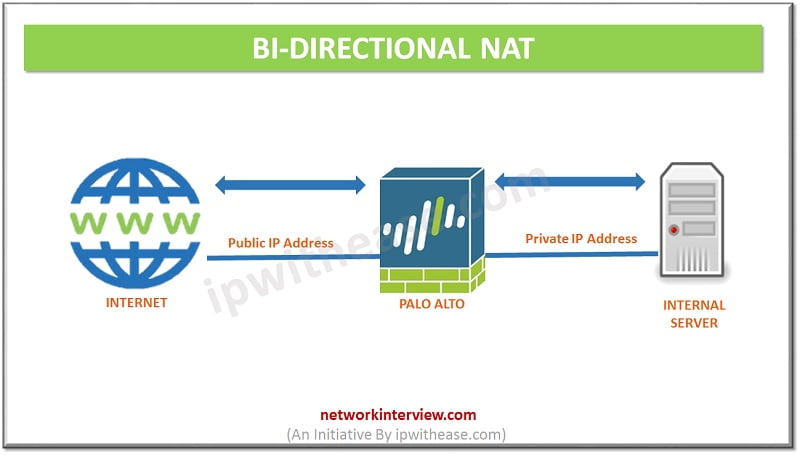
Bi-directional policy:
In a bi-directional policy, flag is set which allows the system to create an (invisible) implied inbound policy. Bi-directional policy will source from trust and will be destined for untrust, with a source address set to the server’s internal IP and Source Translation being its public NAT address. Policy created with a source zone of untrust and destination of any, destination IP of the public NAT address and translation to the server’s IP address.
Uni-directional policy:
Uni-directional NAT policy has less control than bi-directional NAT policy and it allows for PAT or Port Address Translation. With PAT, we get a great benefit when only a single public IP address an be used for multiple internal services.
Related – NAT Type 1 vs 2 vs 3
Source and Destination NAT
In case of U-Turn situation, internal hosts need to connect to an internal server that is on the same network as the client, on its public IP address. To be able to reach internal resources on a public IP, a new NAT policy needs to be created to accommodate trust to untrust translation.
Further, asymmetric loop is created if server receives a packet with the original source address and it then sends reply packets directly to the client. The flow will be Client -> Palo Alto Firewall -> Server -> Client and the firewall session will be terminated as it violates TCP sanity checks. Solution is to add source translation to the firewall IP, so the server’s reply packets are sent to the firewall allowing for stateful sessions.
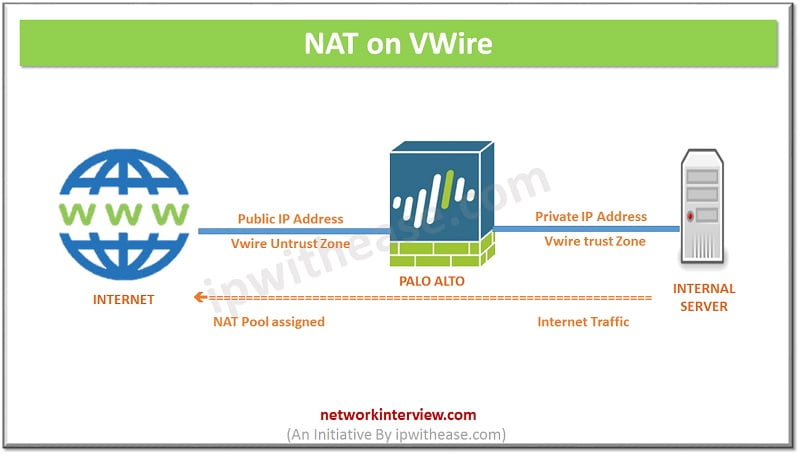
NAT on a VWire
VWire is a Virtual wire, which provides benefit of security transparently to the end devices. Because interfaces in a VWire do not have an IP address assigned, hence IP address must be assigned from pool. When performing NAT on VWire interfaces, Source address is translated to a different subnet on which the neighboring devices are communicating.
Conclusion
NAT in PAN OS allows use to create a rule that instructs the firewall what to do with packet, which packet are from trusted or untrusted zone, which packet port need translation and what the translated addresses and ports are.



