Metasploit Project: Penetration Testing Software
Introduction to Metasploit Project
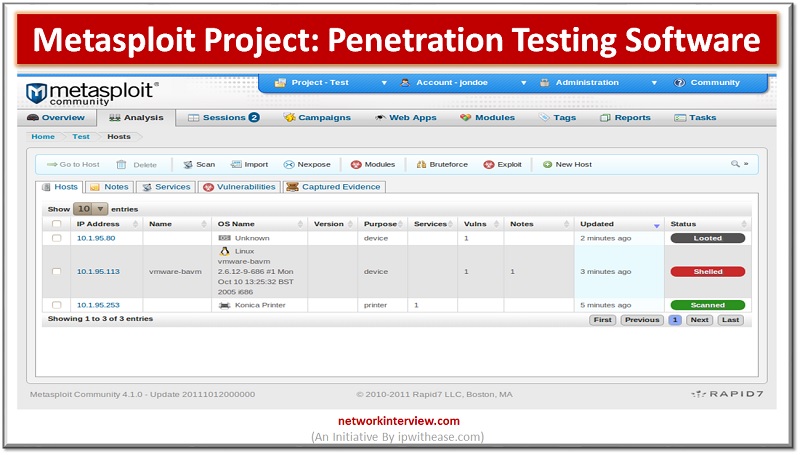
In the worldwide IT security community, we define the Metasploit Project as a computer security project that mainly provides information about security vulnerabilities and helps in penetration testing and development of the IDS Signatures. It is owned by Rapid7 which is located in Boston, a Massachusetts based security company.
The most famous open source sub-project of the Rapid7 company in the industry is called Metasploit Framework. Which is mainly a software tool, used for developing and executing exploit code against a remote target computer machine.
Metasploit’s Framework Editions & Services
Nowadays, there are several interfaces for Metasploit Framework available in the market. The most popular editions are maintained on the official websites of Rapid7 and Strategic Cyber software companies.
- Metasploit Framework Edition: This is the free version of the utility, it contains a command line interface, a third-party import, a manual exploitation service and a manual brute forcing interface. Despite the fact that it is the free edition of the Metasploit project from Rapid7, it also includes Zenmap (a famous security scanner and also a compiler for Ruby: the language in which this edition of Metasploit was initially written).
- Metasploit Pro: According to the official website history, in October of 2010, Rapid7 company added Meta sploit Pro, as an open core commercial Meta sploit edition for penetration testers. At a first glance, Meta sploit Pro adds into Meta sploit Express new software features such as Quick Start Wizards-MetaModules, creating and managing social engineering campaigns, web applications code testing, an advanced Pro Console, dynamic payloads for antivirus evasion, integration with Nexpose for adhoc vulnerability scans and VPN pivoting.
Metasploit Pro Advantages vs the Free Framework Edition
It is quite obvious that the paid edition offers advanced services and below we define the most essential:
- Create a Project: One and most advanced option in the paid version is the ability to create a project in order to store the data that you collect from your targets.
- Gather Information: Another advantage of the Metasploit Pro, is the ability to use the Discovery Scan service, the Nexpose Scan service or the Import Tool in order to extract to Metasploit Pro with the needed list of targets, all the running services and finally the open ports associated with these targets.
- Exploit: In addition to the above, in the Pro version the user can choose between the option of smart exploits or manual exploits in order to launch attacks against target machines. Furthermore, the user can execute brute force attacks in order to escalate account privileges and gain access to exploited computer machines.
- Perform Post Exploitation: Another advantage of Meta sploit Pro, is the ability to provide to the user with advanced tools in order to interact with open sessions on an exploited computer machine. For example, the user can view shared file systems on the compromised target, resulting in clean identification of information about internal system applications.
- Clean Up Open Sessions: Another crucial advantage for network performance, is the simplified use of the Clean Up option that closes all the open sessions on an exploited target and removes evidence of any data used during the penetration test. Finally, this step restores the original settings on the target system.
- Generate reports: Finally, the ability to use the reporting engine in order to create a report that details the findings of the last but not least penetration test is included in Meta sploit Pro. Providing several types that lets the user determine the type of information that the report includes.
Conclusion
Hopefully, this article has been able to describe just how much services the Meta sploit Project places in every user’s hands. The framework is not simply limited to the edition type of the content it is published, for those that are willing to get their hands dirty any component of the framework can be modified to suit a specific task. The article covered all the main functions of the paid vs the free version and addressed all the available sub tools and functionality in the software packages offered by Rapid7 software company.
Armed with this basic knowledge along with more research, the software can create any user’s own exploits and perform Penetration Testing like never before.
Finally, the IT Security community would be pleased if more advanced open source platforms are created or more support will be funded for existing platforms.
Continue Reading:
Top 10 Penetration Testing Tools & Software
Vulnerability Assessment and Penetration Testing



