
Google Account Security – Gmail Security
Introduction to Google Account Security
Nowadays, for a user it is mandatory to create a Google Account, in order to use the Gmail, Google Hangouts, Google Meet and Blogger Applications or Web Site Services. On the other hand, a Google Account is not required if the user just wants to use Google Search, YouTube, Google Books, Google Finance and Google Maps Applications.
Google’s interface for accessibility is very convenient on accounts due to its versatility which makes it a lucrative option compared to other online services. Unfortunately, all the benefits can be easily “Hacked” if a Google account’s security is overlooked.
In normal conditions, this is a scenario that must be avoided at any cost. Google is aware of this situations and has introduced mechanisms to help users to secure their accounts.
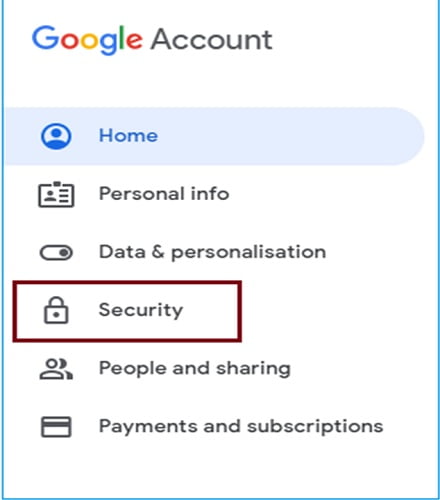
Methods for Increasing Google Account Security
(and in turn your Gmail security)
Today, in the cybersecurity space many experts have dug in these kind of security methods that are effective against “Hacker” attacks. Although they can be used in other type of accounts as well, they provide increased security which makes need for 3rd party tools for extra security meaningless.
- Reinforce Google Account Password: The easiest precaution, but very crucial for your “front door” reinforcement. Try to avoid passwords such as your name, the name of your parents, wife or child. Also, prefer evading from using your birthday, your street address, or anything else that can be easily be found on any social media profile like (Facebook, Twitter, etc.).
- Enable Two-Factor Authentication: Another very successful measure for strong account security. By enabling two-factor authentication, every user is prompted for an additional security prompt. Most commonly used approaches in this type of authentication are creation of a password sent to your mobile phone via SMS or a USB dongle can be also be used, where a button should be pressed in order to gain access.
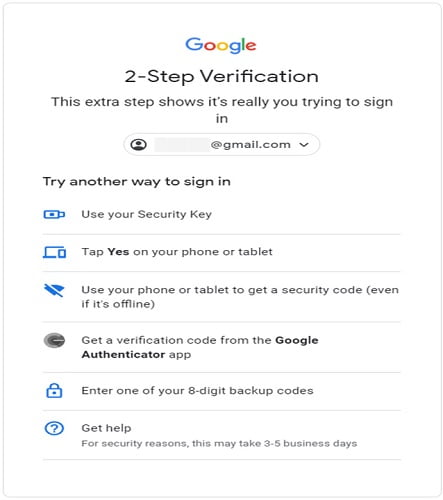
- Proof of Identity: Google’s strategy is that whenever a suspicious activity is detected wrt a user’s account, the user will unfortunately will not be able to log in. Therefore, the user should consider the verification options (Proof of Identity) for authentication purposes provided to Google. To be more specific the required information that have to be provided is the “Recovery Phone” and the “Recovery Email”.
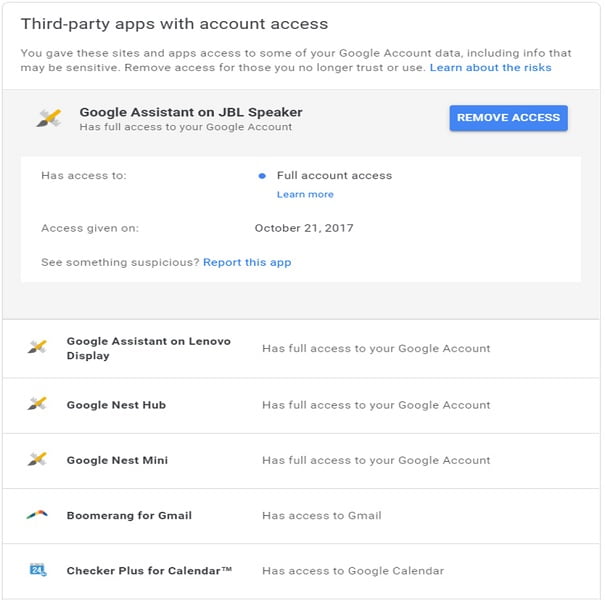
- Review Third Party Services: Depending on the situation, when the user sets up an application or a web site, Google Account Data can be accessed by external agents. In order to control the authorization of this data, the user should consider the legitimation of this Third-Party access by visiting “Google’s Third-Party Apps Overview” settings.
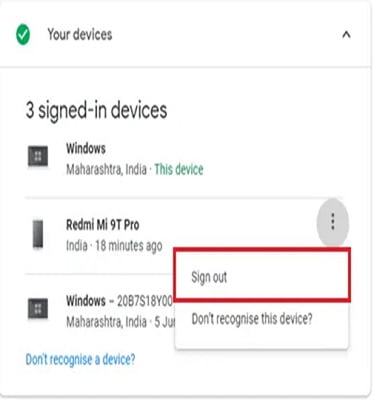
- Review Connected Devices: Another successful precaution measure for securing your Google Account is related to physical devices that have granted access. There is a setting called “Google Device Activity Page”, where a log is available and the user can have the real map of related activities. If someone has “Hacked” your Google Account, all the devices information will pass away and he can easily be identified.
- Enable Google’s Advanced Protection Program: Google has introduced a new program that is most suited for users such as business leaders, IT Administrators, Activists, Journalists and anyone who’s identity is public and needs to be protected. Unfortunately a lot of restrictions are put in place and makes things complicated enough.
A USB Key Dongle is necessary or a Mobile Phone Action is required in order to have access to your email(s) and personal data.
Conclusion of Google’s Security and Compliance
Google Account protection is more than just security. Google provides strong contractual commitments in user’s Data Privacy. High technological infrastructure is designed to support applications and services according to Cybersecurity Highest Standards.
In this article we addressed the most essential ways of protecting Google Account privacy and hopefully all the readers will now know how to enable them.
For the reasons above, five million organizations across the globe, trust Google for keeping their most valuable asset – their information. This professional relationship is encouraging Google to continue investing on new technologies and platforms, in order to allow users to benefit from these services in a secure and transparent manner.
We encourage all the readers to follow the guidelines addressed above and do not hesitate to contact the local Police Department (Cyber Department) in case they observe a suspicious activity in their accounts.
Continue Reading:



