Checkpoint VSX: Architecture, Components & Configuration
What is Checkpoint VSX?
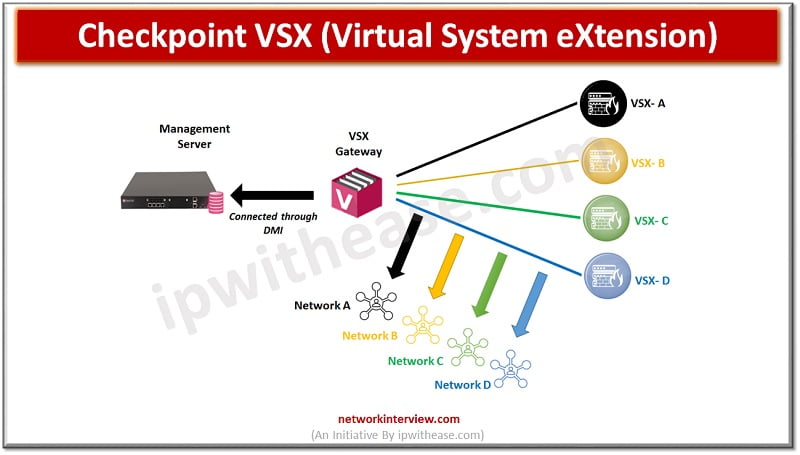
Checkpoint VSX full form is Virtual System eXtension (VSX), a product that runs multiple virtual firewalls in the same hardware firewall.
You can purchase hardware appliances with Licence of Virtual firewall. Using one hardware you will be able to create multiple firewalls, meaning virtual systems. These virtual systems (VSX) can act like a firewall, one VSX means one firewall. If you create multiple VSX means you are creating multiple firewalls for several locations.
Admin needs to create a VSX gateway which further checks the packet and forward it to correct VSX. Every VSX has its own topology and security policies.
Advantages of Using VSX Firewalls
- Cost effective: low cost is required to implement multiple VSX
- Less Work: we can manage the work through a single hardware firewall. It helps to reduce total time and work in managing multiple hardware firewalls.
Main Components for VSX
VSX Gateway: Communicates with the Management Server. It acts as a mediator which lies between VSX and management server/MDS
Management Server/MDS: VSX Gateways communicate with the management server /MDS for the purpose of managing, configuring, and deploying all virtual devices.
DMI: Dedicated Management Interface which is used to connect MDS and VSX Gateway over a physical network. Like if MDS and VSX gateway devices are in the same Data Center then a physical connectivity between MDS and VSX gateway can be performed via DMI.
- DMI uses a separate interface which is restricted to the management traffic.
- Its segregate management interface to the routing, production traffic
- Main Components for VSX
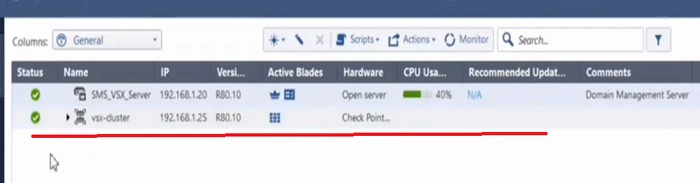
VSX Architecture
In the above image VSX A is connected to Network A, VSX B to Network B and so on..
VSX -Virtual system is a security and routing domain that provides the functionality of security Gateway with full firewall and VPN facilities.
Every Virtual system maintains its own security blades and licences, security policies, VPN policies and routing which means a virtual system acts like a separate firewall.
How communication happens among VSX, VSX Gateway and Management Server
- Management server redirects traffic to the internet. Via management server we are performing configuration activities.
- When we initiate communication from the management server, it forwards the request to VSX Gateway and through VSX gateway traffic moves to the VSX.
- However, VSX Gateway first checks to which the traffic is pointed based on the subnet details.
- Once traffic reaches the VSX system, policy/routing and other configuration will be parsed.
- Traffic will be allowed/deny by the VSX based on the configuration in the VSX
Configure VSX Gateway Through MDS
1. Login into MDS -> Smart Console Checkpoint
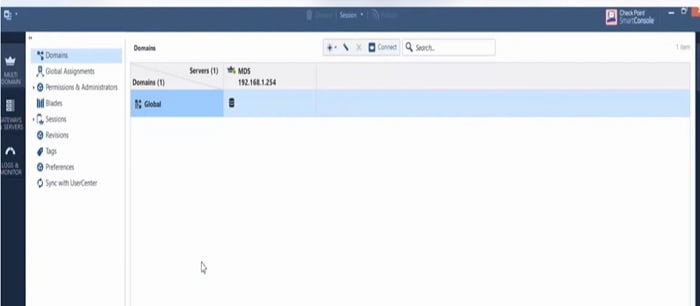
2. First you need to create a Domain in the MDS Server. Domain is nothing but a security management server through which security blades are managed for VSX. Go to “ * ” option and select Domain.
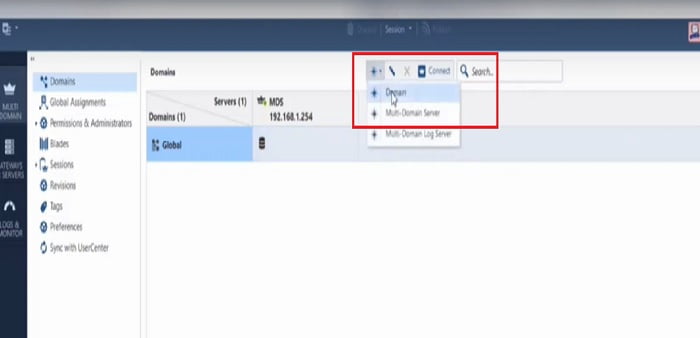
3. Give Name to New Domain. Here we have given name -> SMS1-VSX1
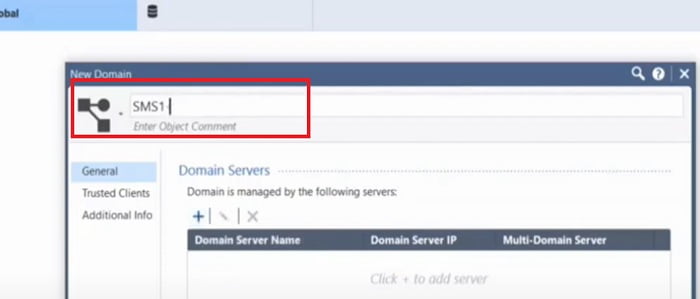
4. Add Domain Server name and configuration details by selecting + tab. In this section Domain server and address details will be shared.
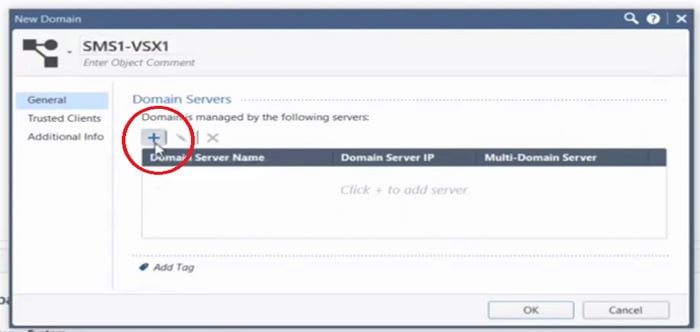
5. New Domain Server along with server IP address. We have given 192.168.1.20 IP addresses to the VSX domain server.
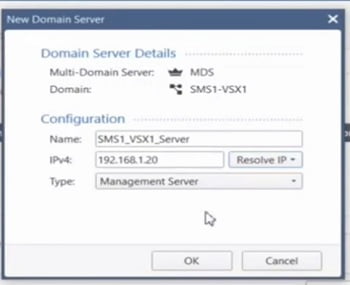
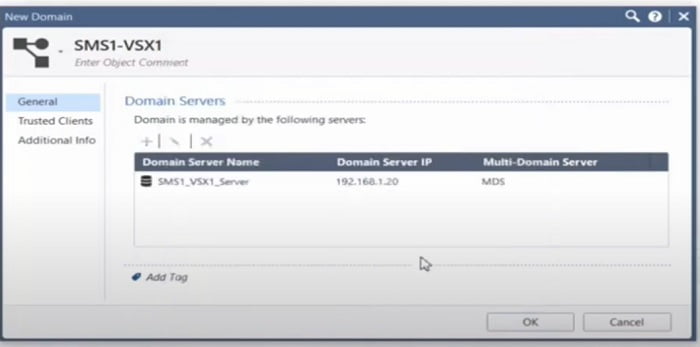
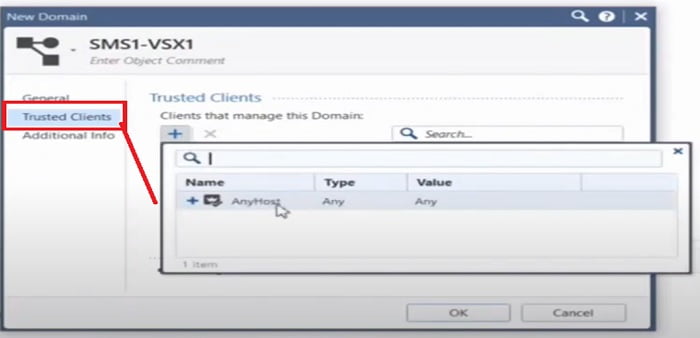
6. Add trusted subnets which admin wants others to access the VSX management
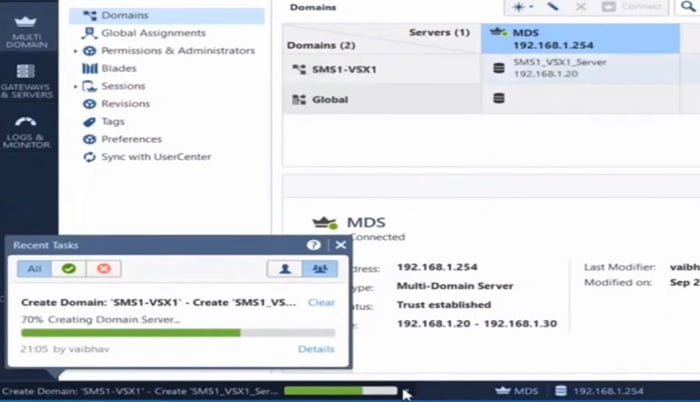
7. Now install the changes in Checkpoint Smart Console
8. VSX Domain has been created and seen in the Smart Console
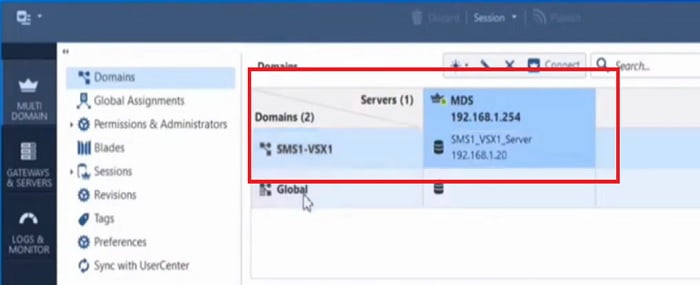
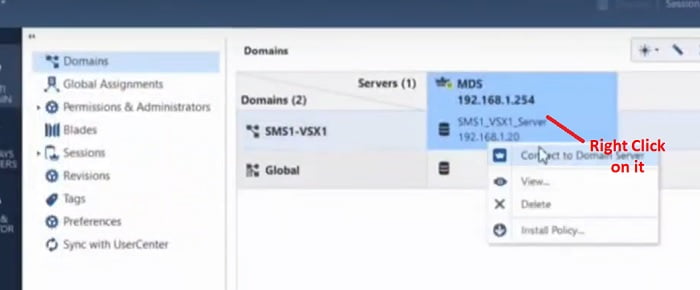
9. Right click on the Smart Domain and connect to the Domain Server from Smart Console
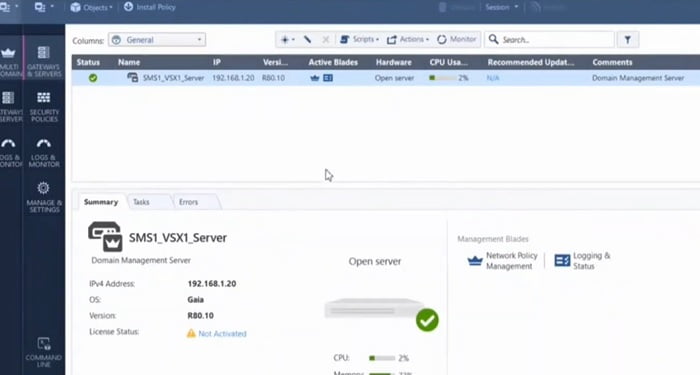
10. Domain Server dashboard look like as below
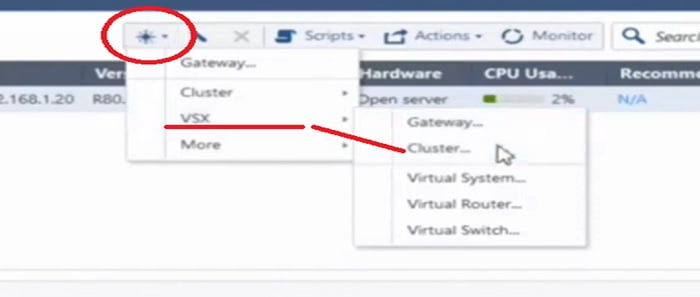
11. Select Gateway object -> VSX -> Cluster (as we have lab for VSX Cluster)
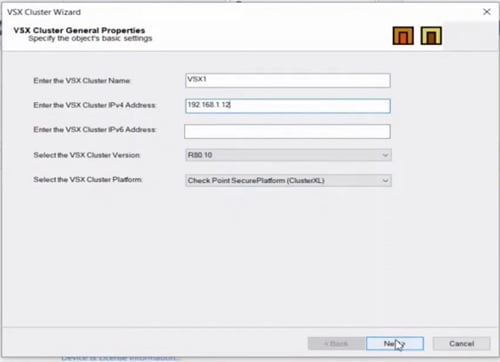
12. Provide cluster IP addresses , select cluster version and VSX Cluster platform
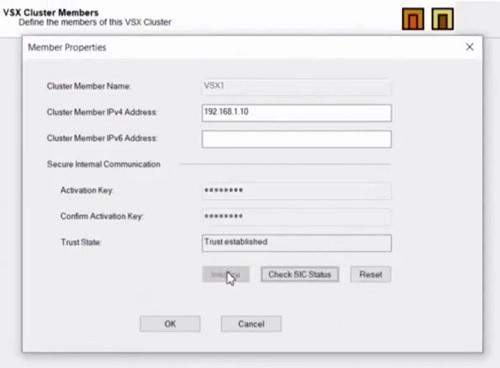
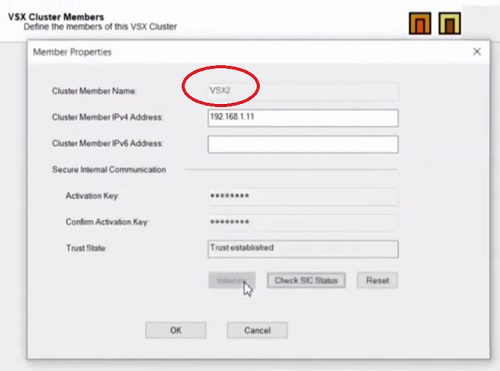
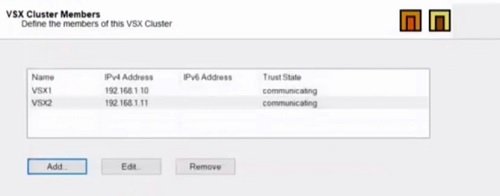
13. Click next and add Cluster members IP Addresses, here we have created Cluster Member VSX1 and VSX2. Establish trust through SIC. Now Click Next to add Interfaces
14. We are not selecting any interfaces here as it is not required as per our lab
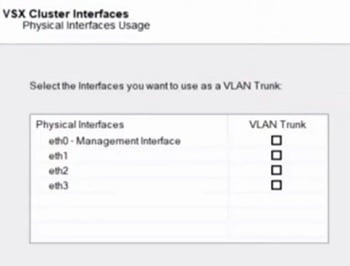
15. Add cluster member state synchronisation port and IP address for internal cluster communication. Below IP addresses are only for internal cluster communication

16. Select firewall management access rules which you want to add in the VSX cluster
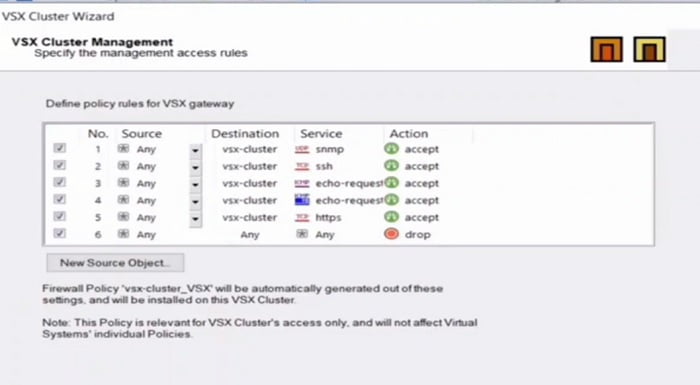
After selecting Firewall policies, we will finish the installation
Now Configure Virtual System Configuration
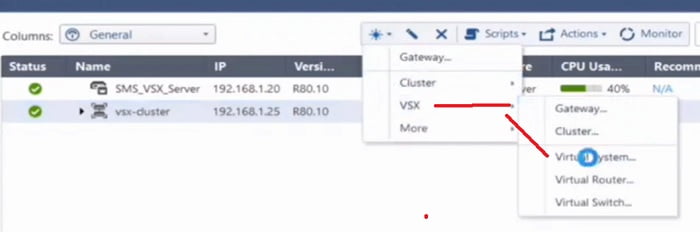
1. Now got to the * tab and select -> VSX -> VSX System
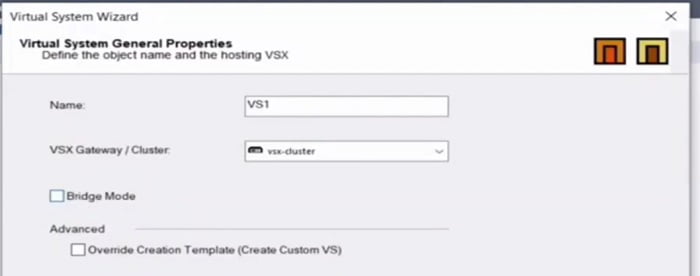
2. Name Virtual System VS1 and add Gateway cluster (which is created above)
3. Add Virtual System Network Configuration in the setup
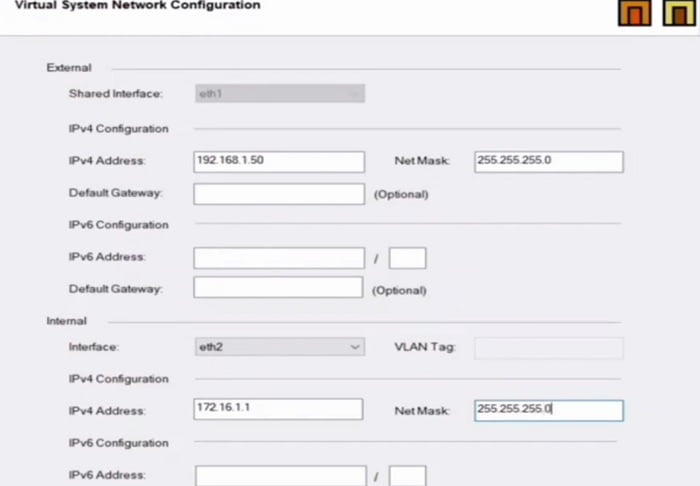
4. Finish the setup.
Now VSX Gateway and Cluster is ready to use through Smart Console and Dashboard!
Continue Reading:
Checkpoint Firewall Policy: Rules & Configuration
Understanding Checkpoint 3-Tier Architecture: Components & Deployment
Tag:Checkpoint, Security