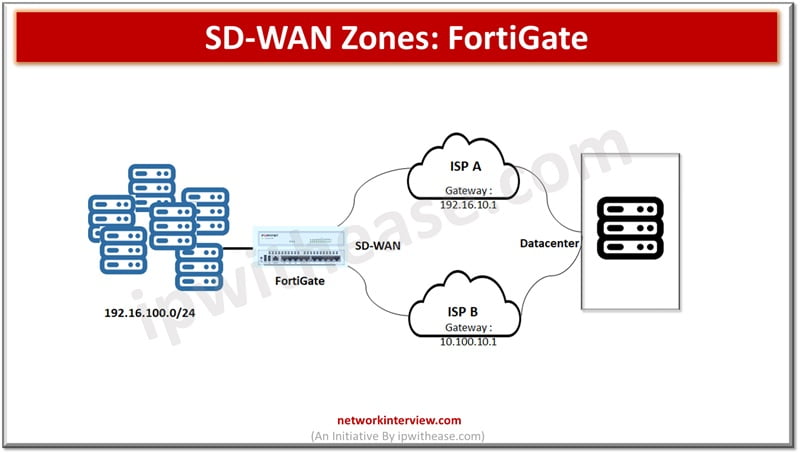
SD-WAN is a software defined networking approach wherein hardware is separated from the control plane. SD-WAN is an ideal technology for cloud and on prem deployments. It is a consolidation of transport connections, underlays, monitor and load balancing traffic across …
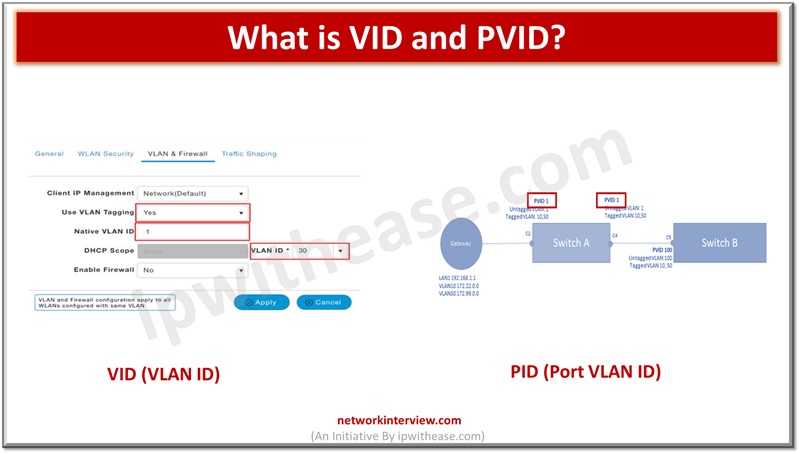
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. **STAY TUNED** Short Interview Questions: Que 11 What is VID and PVID?
Imagine the scenario that you have an amazing script on paper and want to make a video out of it. That’s where you tend to stop, since the overhead associated with visuals, recordings, anchor, foreground and background creation and such …
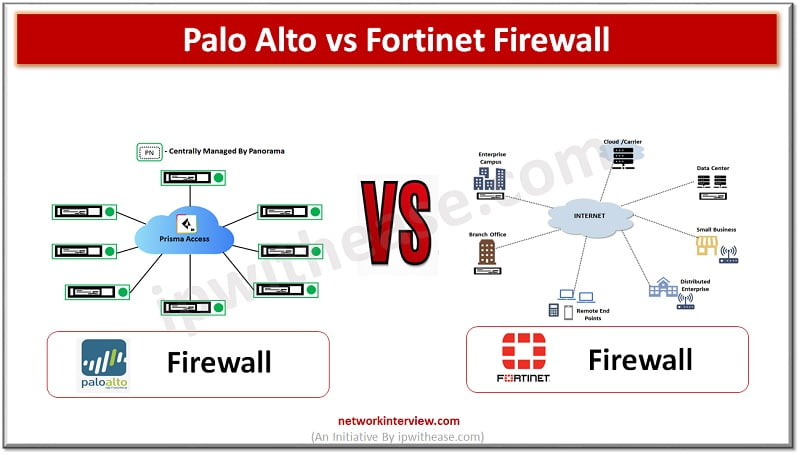
Attackers are constantly looking for vulnerabilities to penetrate your networks. Protection against direct, external threats require extensive network security functions deployed on the edge. Protections on the edge are provided by stateful and next generation firewalls (NGFWs) which offer features …
(Diagram depicting Palo Alto vs Fortinet Firewall) Organizations need to keep pace with rapid increase in technology demands such as remote working, anywhere connectivity, lower latency , increased availability along with protection of infrastructure from a never ending list of …
Application aware security is the need of the IT enterprises. Companies are replacing the old and outdated firewalls with Next generation firewalls which are application aware and this evolution can be attributed to web 2.0 where web-based applications and services …
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. **STAY TUNED** Short Interview Questions: Que 10 What is the difference between WiFi 6 and …
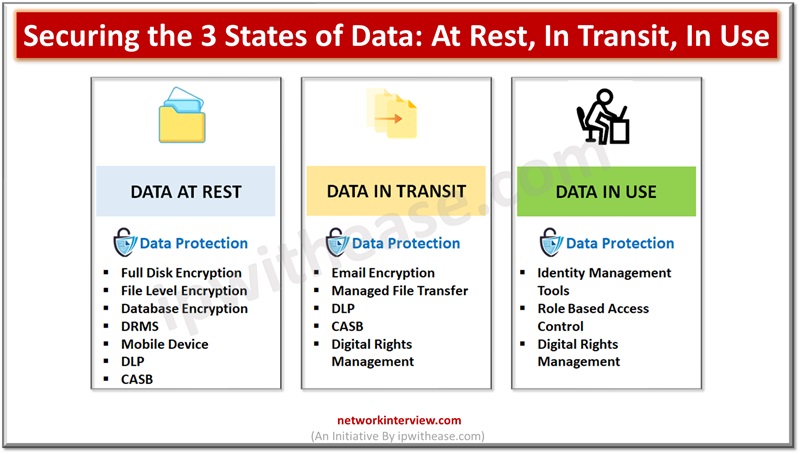
Data is the key differentiator for businesses and enterprises hold a trove of business secrets, customer personal data, and other sensitive information vital for businesses. Hackers’ prime target is this data for their personal gain , and organizations struggle to …
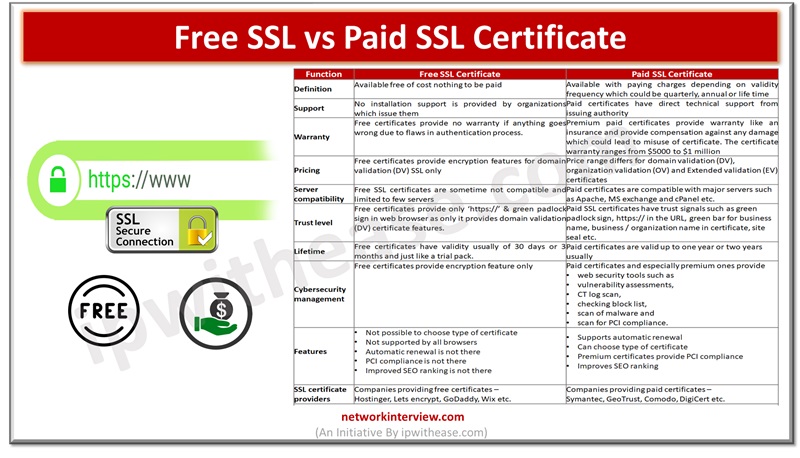
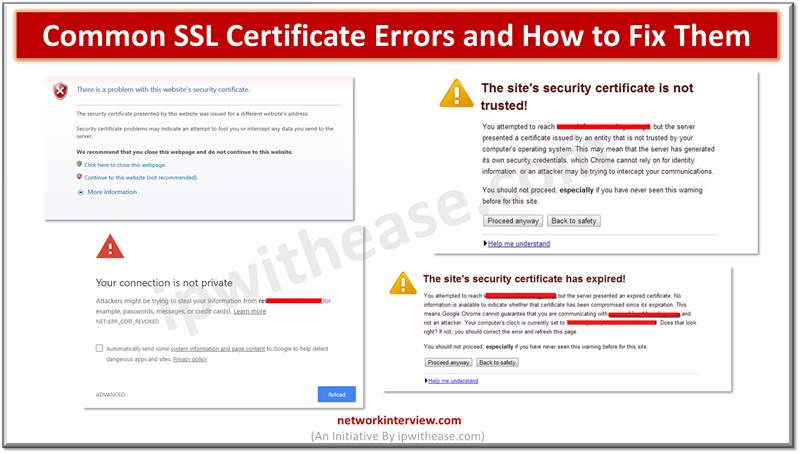
As cyberattacks are on rise and thousands of Internet users and organizations are targeted by attack vectors, safety and security of data is a major cause of concern. The secure socket layer (SSL) certificates are widely used by websites for …
Secure Socket layer (SSL) certificates are used widely by organizations to secure websites and every business needs to have a valid SSL certificate to safeguard client’s security and credibility of brand. Secure Socket layer (SSL) is an encryption protocol and …
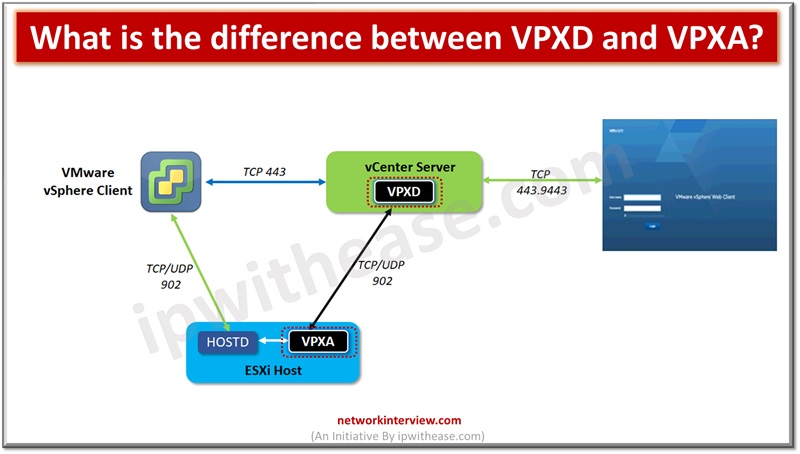
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. **STAY TUNED** Short Interview Questions: Que 9 What is the difference between VPXD and VPXA? …
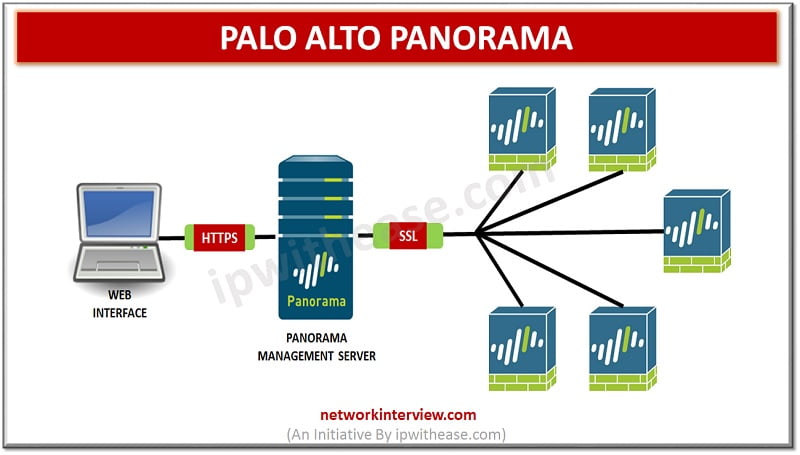
Introduction to Palo Alto Panorama Palo Alto Panorama is the centralized management server that offers a global visibility and control over the multiple Palo Alto Networks next generation firewalls from web interface console. Panorama manage multiple Palo Alto Networks firewalls …
Project management is crucial for ensuring a seamless execution of a project, right from its initiation to completion. If you are seeking to enhance the efficiency of your project by using a project management tool, you may consider opting for …
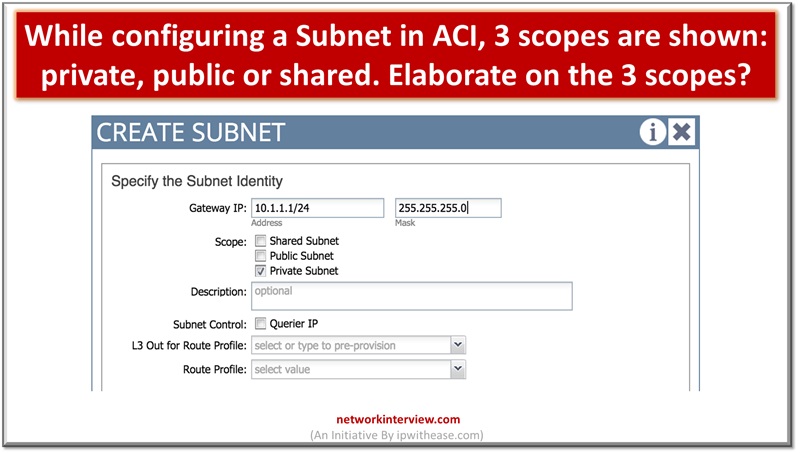
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. *STAY TUNED* Short Interview Questions: Que 8 While configuring a Subnet in ACI, 3 scopes …
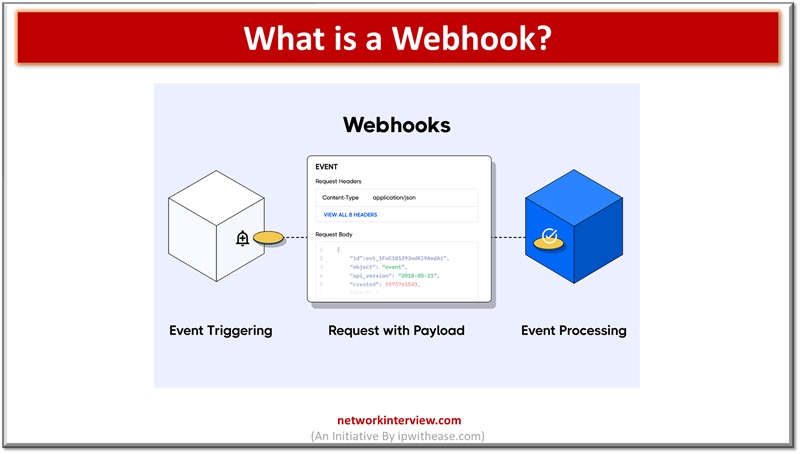
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. *STAY TUNED* Short Interview Questions: Que 7 What is a Webhook?
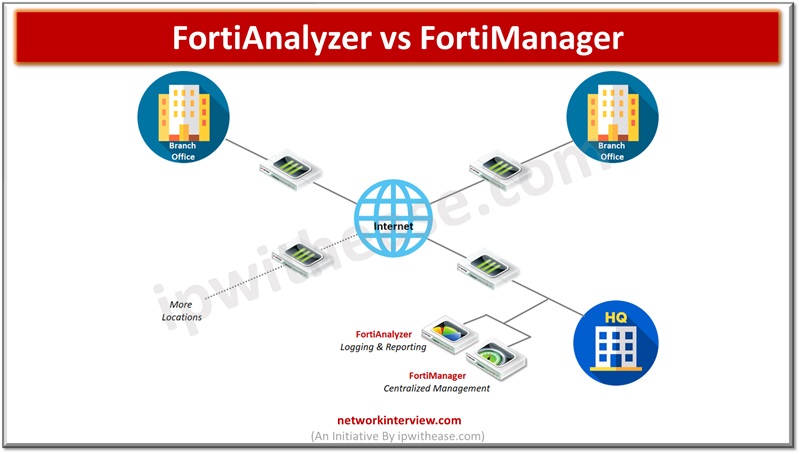
FortiAnalyzer: Security Management Platform FortiAnalyzer aggregates log data from one or more Fortinet devices and creates a single platform to view all the reports and events. It can fetch logs from the Fortinet devices once devices are registered to FortiAnalyzer. …
In the realm of professional photography, headshots hold a special place. They are more than mere portraits; they serve as the visual introduction to individuals across various fields. Whether you are a business professional, an actor, a model, or a …
As the world continues to change at a fast rate, the electronics industry is also actively in an ever-changing era characterized by remarkable transformations. Among these transformations is the growing demand for sustainability, especially at this time when the emission …
Managing the cyberthreat landscape is quite a bigger concern for enterprises. As more and more organizations are adopting cloud ecosystems, organizations reliance on security of their data and information for 3rd party SaaS providers is at an all time high. …
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. *STAY TUNED* Short Interview Questions: Que 6 What is MEth interface in Huawei Switch?
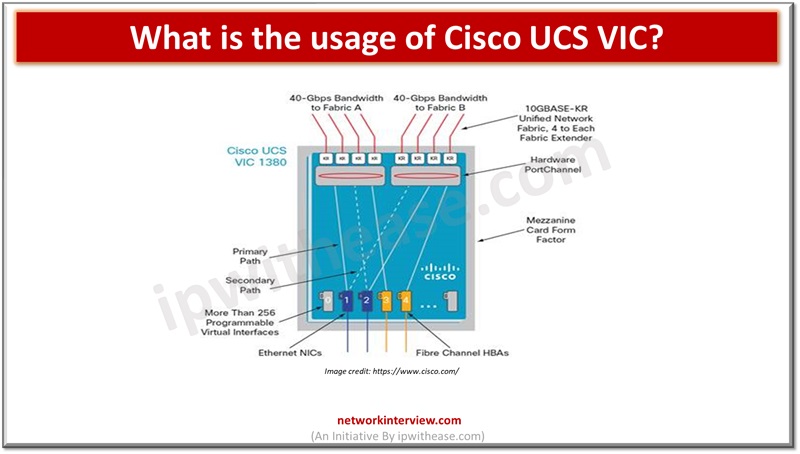
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. *STAY TUNED* Short Interview Questions: Que 5 What is the usage of Cisco UCS VIC?
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. *STAY TUNED* Short Interview Questions: Que 4 What is FortiGate Connector for Cisco ACI?
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. *STAY TUNED* Short Interview Questions: Que 3 What is difference between Cisco APIC-M2 and APIC-M3? …
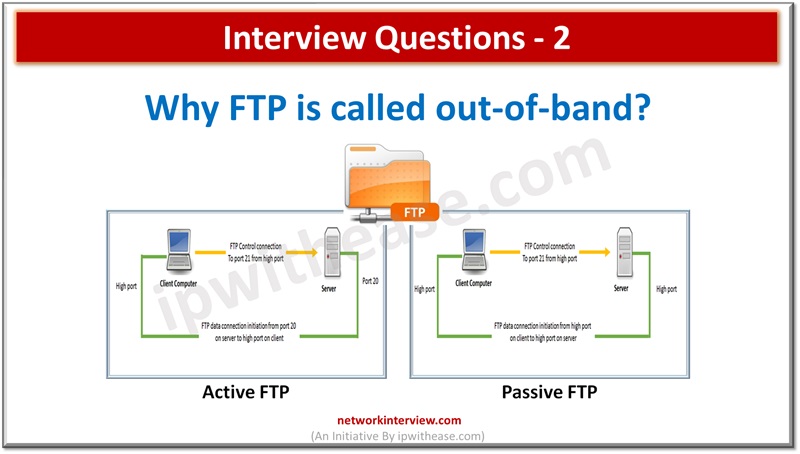
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. *STAY TUNED* Short Interview Questions: Que 2 Why FTP is called out-of-band?
This is a series of short interview question & answers that will help you in understanding the basic IT concepts to most advanced IT technologies. **STAY TUNED** Short Interview Questions: Que 1 What does the term DDI mean in Networking?
Project management systems play a crucial role in the achievement of business success. Whether you are involved in software development, product creation, or construction planning, it is essential to efficiently plan, execute, and monitor projects. These systems serve as your …
Cisco Certified Network Associate or CCNA is one of the most popular networking certifications that validates fundamental networking skills. With increasing demand for networking professionals, CCNA certified candidates are in high demand. To land a networking job role, candidates need …
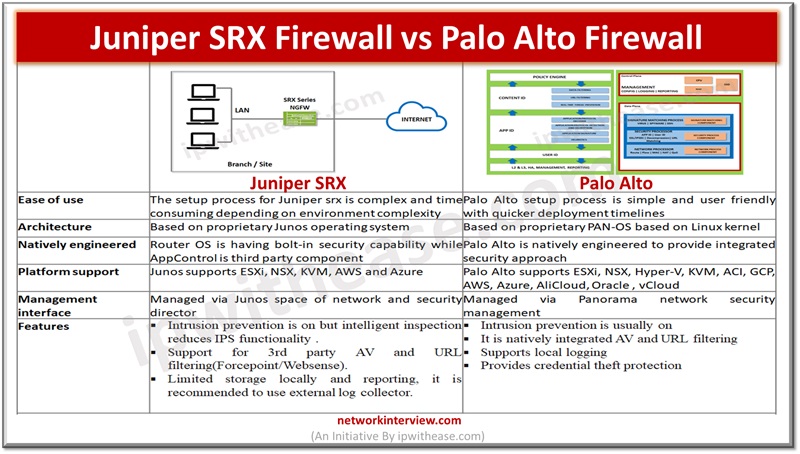
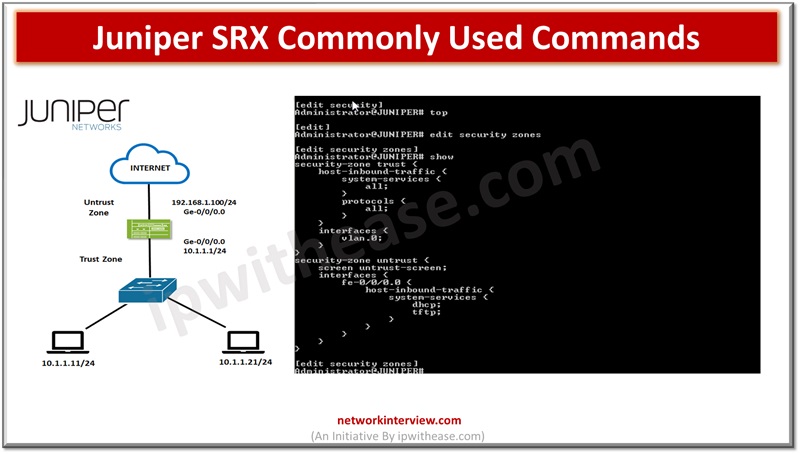
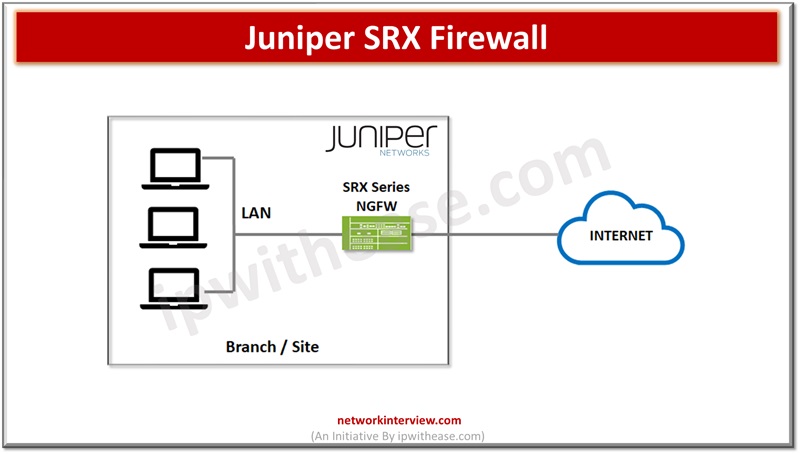
In the previous articles, we have studied the basics of Juniper SRX firewall, its architecture, installation, modes, security policies etc. Today, we will discuss the command line interface of Juniper SRX. Commonly Used Commands: Juniper SRX Here are some commonly …
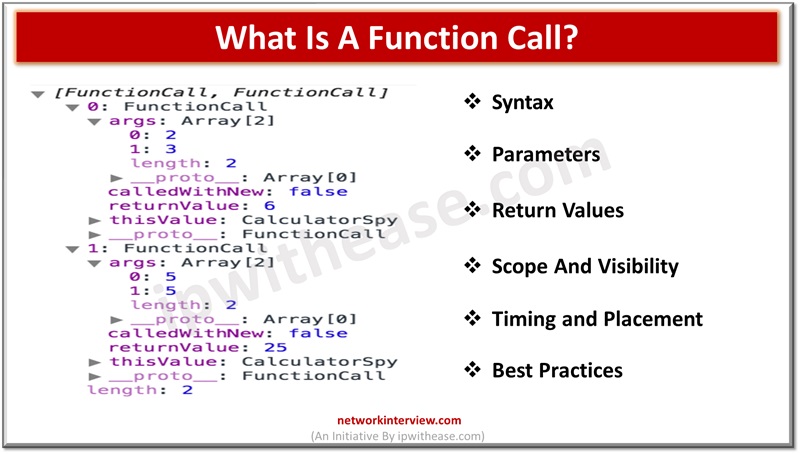
In software development, functions are the backbone of clean, reusable, and maintainable code. But to truly excel in programming, one must understand how to write functions and how to effectively wield the power of function calls. Let us unravel the …
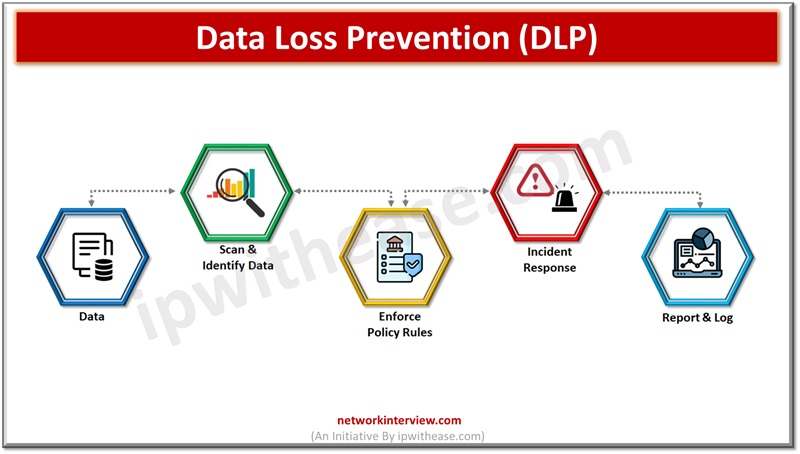
Data is the lifeline of organizations and they rely on a variety of data to run their businesses. Since data is critical to run businesses, it is important to safeguard it from unauthorized access, improper usage. Different approaches are adopted …
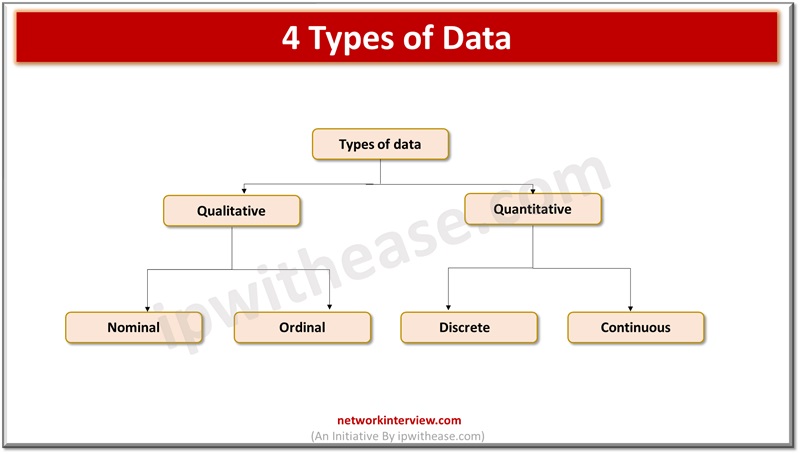
As the world is advancing and relying on businesses, users are shifting towards availability of data to make quick and efficient decisions. Data is new ‘fuel’ for the world today. Everywhere and in every field be it medicine, logistics, manufacturing, …
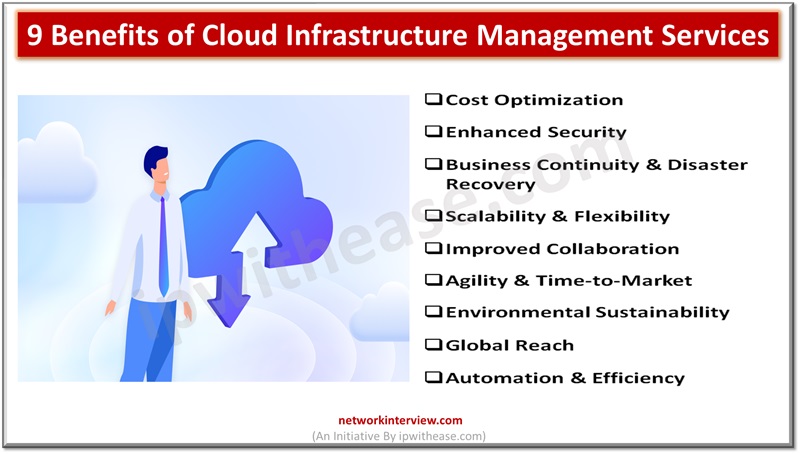
Cloud infrastructure has become an omnipresent force, exerting a profound impact on individuals worldwide, both directly and indirectly. Directly, individuals interact with cloud services in their daily lives, from storing personal files on platforms like Google Drive to streaming entertainment …
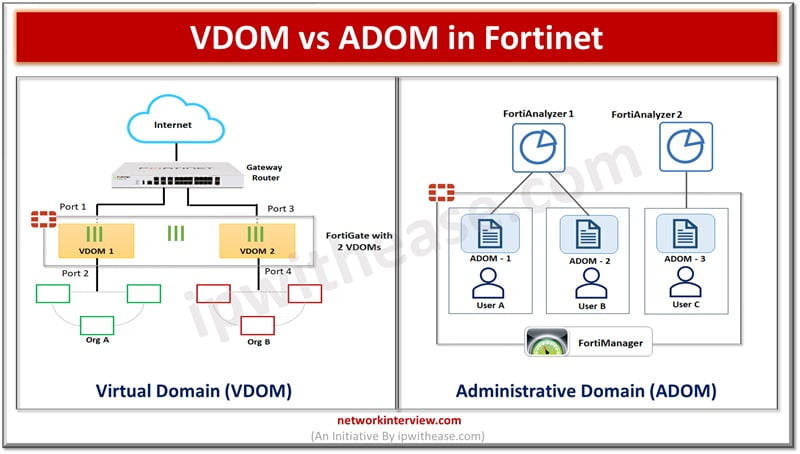
Majority of organizations are moving to cloud based infrastructure to run their IT operations. Cloud service providers require to provide multi-tenancy services and require to have products which support multi-tenant scenarios. Networking is one of the crucial aspects of the …
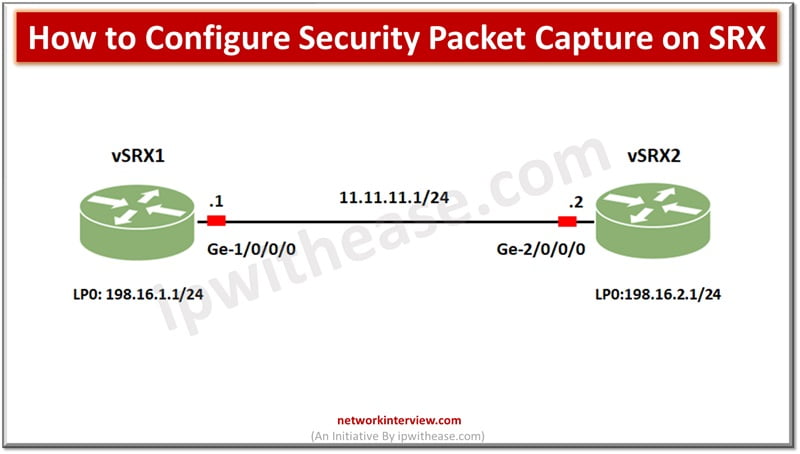
For debugging network issues capturing packet traffic is a very useful utility. It helps to analyse network traffic and help in network monitoring and logging. Packets are captured in binary form without any changes and you can read packet information …
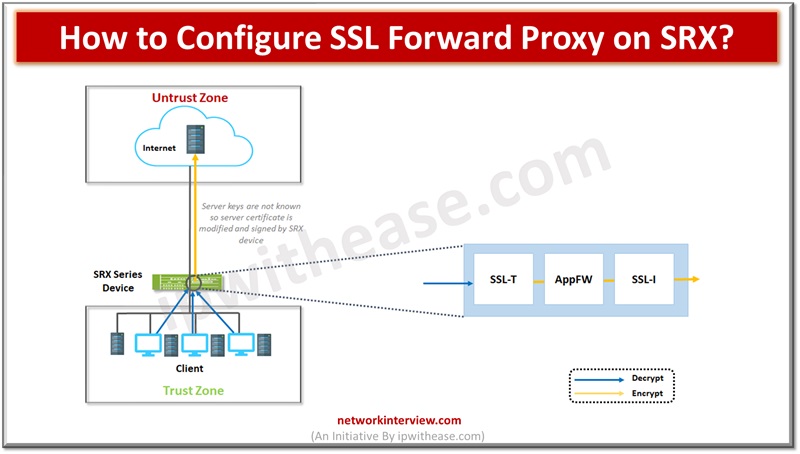
Network protection is enabled from malware by utilizing the SSL proxy component. It is used to prevent malware which is hidden in encrypted traffic. It is used to perform SSL encryption and decryption between server and end client in a …
The realm of Search Engine Optimization (SEO) is incredibly dynamic, constantly reshaping to accommodate new algorithms, user behaviors, and technology advancements. As we enter 2024, new trends emerge, redefining digital marketers’ strategies for improved online visibility and rankings. Below, we …
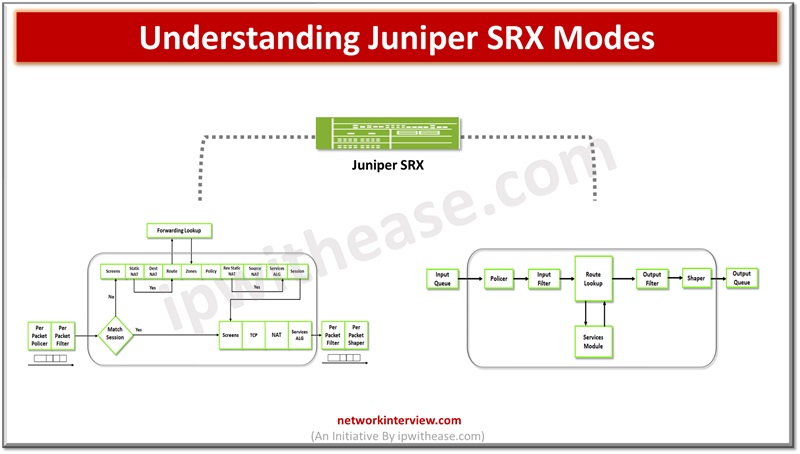
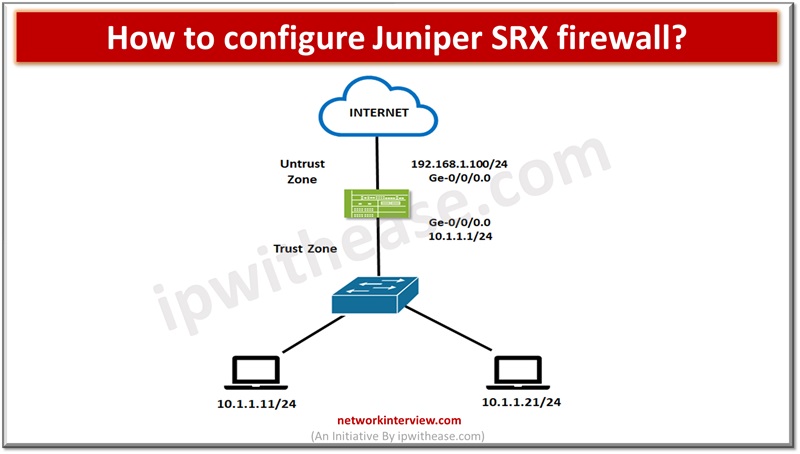
Firewalls perform the processing of traffic for packets which enter and exit a device. Juniper SRX firewalls have a wide variety of filtering and traffic shaping features including policies, screens, network address translation (NAT) and services based on flow. Processing …
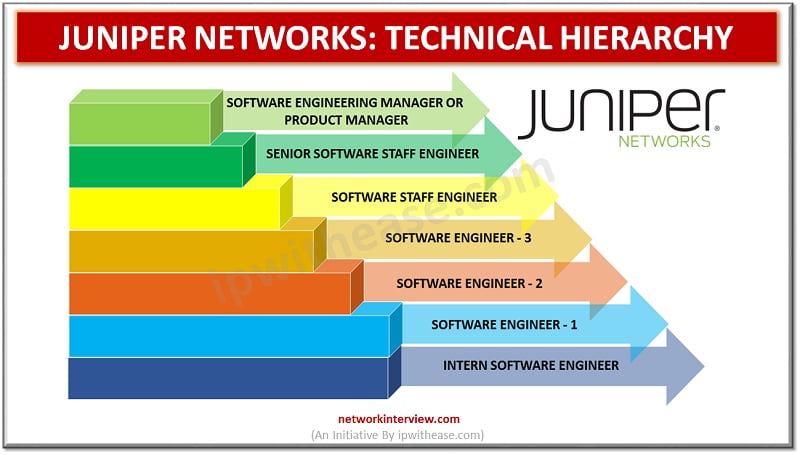
After graduation, engineers always wonder about good job opportunities. But you should know about the Hierarchy and working environment before you select a company. Are you an engineering graduate planning to get a job in Juniper Networks? Want to know …
Businesses of all types and sizes have one aim in common: to not just survive but thrive. To accomplish this, they need data from the digital information that is now the lifeblood of every organization. New and young businesses, in …
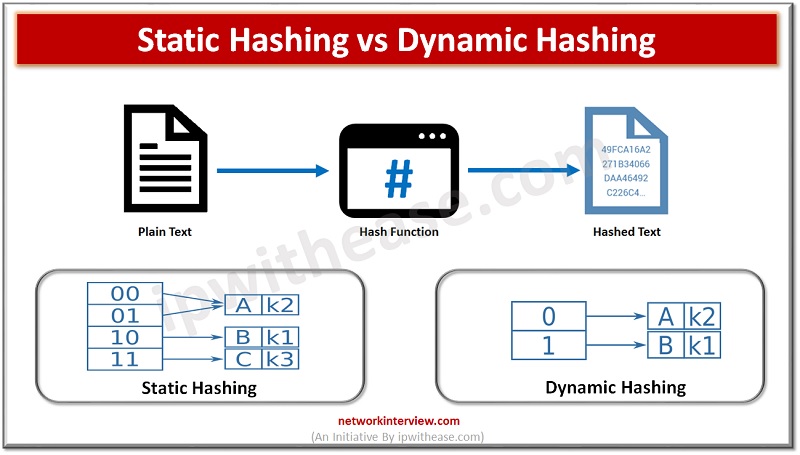
Introduction to Hashing Data structure often contains a lot of data that is difficult to search through. Hashing is an effective solution that can be used to map these large datasets to much smaller tables by utilizing a unique Hash …
The freelance workforce has become an integral part of the modern business landscape. As organizations increasingly turn to freelancers for specialized skills, managing and optimizing this flexible workforce becomes crucial. This article explores five proven ways to streamline your freelance …
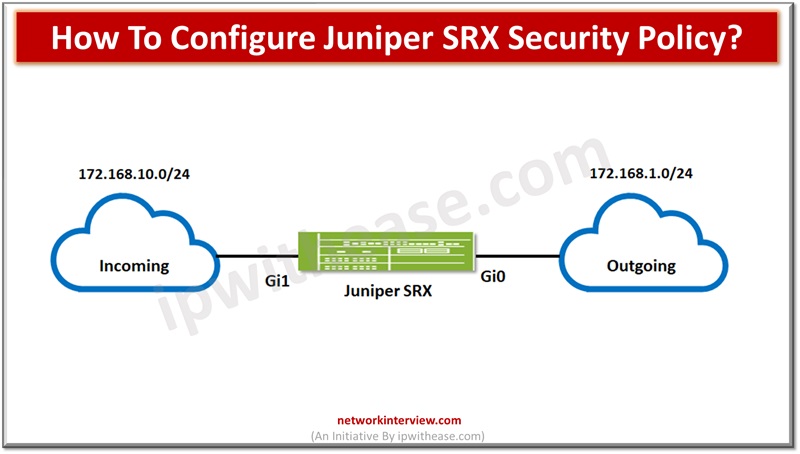
To secure networks network administrators create security policies for network resources within the business required to establish security level for network resources. All standard firewalls allow creation or setting up baseline and advanced security policies to enforce rules for transit …
We can’t imagine a network without a firewall, they are the staple of almost every network in the IT landscape. The firewalls provide protection to nearly every network-based transaction. Over a decade the underlying technology has changed rapidly as the …
All communication in Internet world is govern by OSI (Open Systems Interconnect) framework. There are seven layers in OSI model and each layer performs a set of functions to ensure data delivery to its intended recipient. The layer 3 or …
Network based security landscape is changing drastically and becoming more and more complex and dynamic in operations. New challenges in the cyber security domain related to web based and social network applications, sophisticated cyber-attacks, social engineering attacks are on rise …