What is Penetration Testing or Pen Test?
To have faster time to market and bring in business agility organizations are more and more relying on technology. Technological advancements have one side facilitated business to grow faster and quickly adapt to changing needs of businesses and on other side it has given tremendous opportunity to armatures and professional hackers to gain access of business systems, steal data, destroy data or hold companies data for Ransom.
Today we look at penetration testing technologies which have been adapted and widely used by businesses as a protective measure to protect and save sensitive data and information from hackers by identifying potential weaker systems and back doors which can be an easy gateway for sensitive data leakage or compromise.
Definition of Penetration Testing/ Pen Test
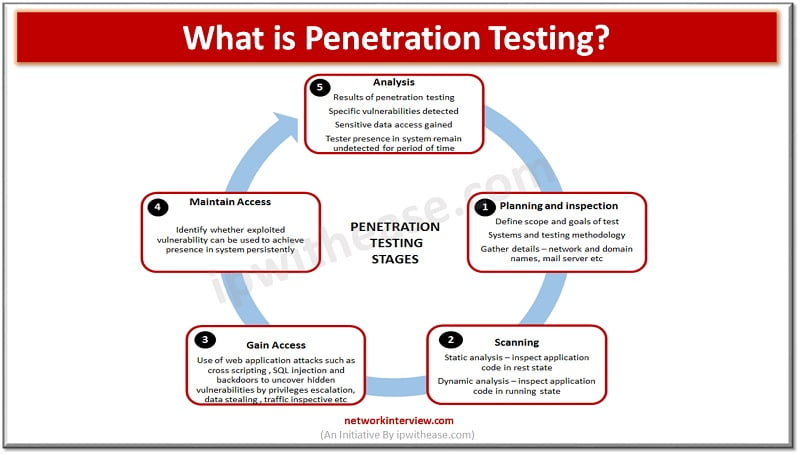
Penetration testing or so called ‘Pen test’ help to identify the source of potential exploit or vulnerabilities that can compromise computer systems from various viewpoints. Penetration testing is of two types – Internal and External.
- An external penetration test is used to prevent and detect attacks by testing the effectiveness of security controls.
- An Internal pen test is performed to restrain the attacks from within the organization from employees such as suspicious email attachment open by an employee in a phishing mail or some unauthorized device plugged into the network to gain access to information which is restrictive /sensitive in nature. This kind of test helps to understand amount of damage that an intruder can incur.
The goal of an amateur of professional hacker is to gain access to company sensitive information either to steal it or destroy. It is important and crucial to secure company data from potential hackers by just having strong passwords and updated firewalls we cant contain these risks entirely so it is important to have a regular testing in place to ensure control security controls are strong enough to withhold attempts of hacking and protect organizations from negative impact of illegal hacking resulting in systems downtime, data stealth, data destruction issues in a proactive manner.
Classification of Penetration Testing
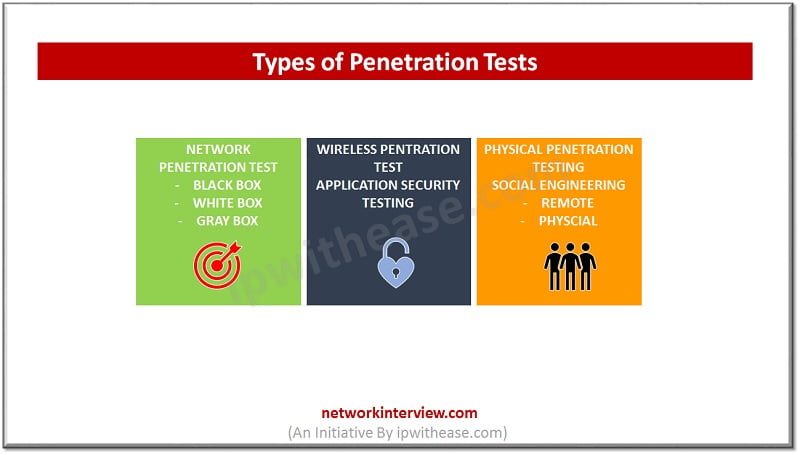
Penetration test tools and methodology depends on type of operating systems and applications that needs to be assessed for security risks. Pen testing may include assessment of social engineering attacks apart from software tools-based assessments.
Pen test contains various types of tests as listed below:
- Blind tests or Black box test – Little details are given to penetration testers about the device being exploited for bind test to identified vulnerabilities which otherwise remain undiscovered.
- White box tests – Extensive details of security controls given to penetration testers so to help in improving vulnerabilities.
- External tests – Identification of vulnerabilities at global level carried on domains facing software.
- Double blind tests – it is also known a covert test done on sensitive data for which assessments are restricted to be shared within internal security teams.
- Internal tests – performed within the boundaries of an entity to identify the security weakness which can be potentially be exploited by internal personnel.
Benefits of Penetration Testing
Some of the benefits of Penetration testing listed here:
- Revealing potential vulnerabilities – main objective of Pen testing is to identify the hidden weakness in systems and network infrastructure. The pen test identifies the pattern in actions and habits of employees within organization that could lead to malicious breaches and systems compromise. Pen test identifies vulnerabilities in systems hardware and software and give insight into how to improve policies and give recommendations to secure systems.
- Present real risks – Pen tests try to exploit vulnerabilities hidden in systems and present the action which you can see in real world when hacker is trying to attach in real world. It will try to impersonate the real-world hacker attempts and detects whether they are successful or not so that we can assess the risk associated with the said vulnerability. These experts are also referred as ‘White hackers’
- Testing cyber Defense capabilities – Pen test tests the effectiveness of security controls and when the attacks are identified immediate actions are taken to contain them – such as beginning of investigations, blocking intrusions etc.
- Business continuity – Pen test helps to ensure business continuity for organizations by well ahead planning how to handle hacking attempts and how to plug in potential system weaknesses to ensure systems are available 24*7 in terms of communication and resource access.
- Third party estimation – Pen test also helps to get organization a third-party mandate on security which help to mobilize additional funds from the management to secure systems like a recommendation coming from an expert is more convincing to the stakeholders.
- Establish trust – It helps to establish trust of business partners and clients. We can assure them their sensitive data is secure with us with stronger security controls.
Penetration Testing Tools and Software
Some famous and widely user penetration testing tools are listed here:
Wireshark – Also named as Ethereal 0.2.0 it an award winner network mapper developed by 600 professionals it can catch and analyse data packets it is an open source tool and compatible with various operating systems such as Windows, Sun Solaris, FreeBSD and Linux. It offers offline and online review of live capture, identifies protocol of source and destination, and inspects the smallest information on the network and having optional colouring rules for faster and intuitive analysis.
Netsparker – is an automated application server for pen testing. This tool can recognize vulnerabilities ranging from Cross site request to SQL injection and majorly used by blog designers, web interface and web services developers. Supports search capability for web-based applications for 1000+ (less than in a day), capable of searching SQL and XSS bugs in software applications, it can create legal application of web and reporting to address regulatory requirements.
John the Ripper Password Cracker – it guesses the weaker passwords and automatically detects variations in passwords, discovers inside database password vulnerabilities, personalized cracker , helps to discover online documentation.
Aircrack – is configured to hack vulnerabilities inside wireless connections it taps the incoming packets and export them to word files for analysis. It supports multiple OS and WEP dictionary-based attack frameworks. It is compatible with multiple operating systems, meant for wi-fi testing, it creates a fake wireless network, de-authenticate and replay attacks.
Nessus – Present an analysis of network vulnerabilities such as poor passwords, data corruption errors etc. , per 1 million test the error quotient is .32 errors per device, help to customize files contain vulnerability forms, preference mitigation etc.
SQL map – is a SQL injection control tool it is open source and detects and exploits vulnerabilities to monitor them, offer assistance on all aspects of injection – Union , time, stack, Error and Boolean.
Continue Reading:
Common Types of Attacks on Routers
Tag:Security



