What is Multi-Factor Authentication (MFA) & How Does it Work?
Companies of all sizes are becoming increasingly aware of the need for stronger user authentication to reduce the risk of cyber attacks. This is particularly true in light of recent high-profile attacks on accounts from Internet users such as celebrities, sports stars, politicians and journalists.
In response, many organizations have begun to implement more secure authentication methods. Multi-factor authentication (MFA) is one such technique that offers a strong level of assurance that users are who they say they are. This article explains what multi-factor authentication is and how it works.
Keep reading to discover more about this effective way to keep your company’s data safe from malicious hackers.
What Is Multi-Factor Authentication?
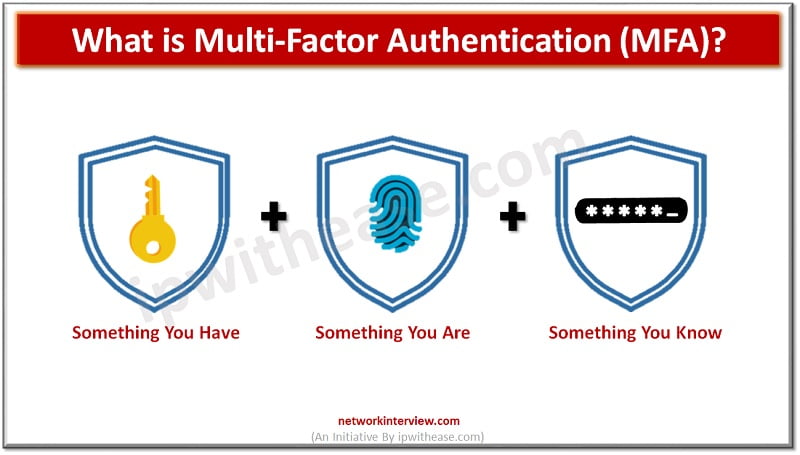
Multi-factor authentication (MFA) is a method of verifying the identity of individuals by using two or more of the following authentication factors: Something they know, something they have, or something they are. These factors can be used together to provide strong authentication.
For example, you may use your fingerprint and a passcode to authenticate to your smartphone. Multi-factor authentication is widely used to verify the identity of users for online services. With multi-factor authentication, you’re required to provide more than just a username and password to log in.
You may be asked to enter a one time passcode sent to your mobile device or a code generated by an application installed on your smartphone. The idea is that if someone steals your password, they still can’t get into your account unless they have the other authentication factors.
How Does Multi-factor Authentication Work?
A very common example of MFA is when you log into your email account using a login page, and there’s an additional box that asks you to enter a code that’s been sent to your phone. MFA also comes in many other forms that can be used for various login requirements for online services, such as:
- By entering a password and a code sent to a smartphone, users can increase their account’s security by requiring two factors for authentication.
- A six-digit code generated by an application installed on your smartphone.
- A token that you plug into a USB port on your computer.
- By using an app that scans an image and compares it to an image on your computer screen.
MFA Types
There are many different types of MFA authentication methods. The following are the most common types:
- One-time password (OTP) – This is a type of MFA that requires users to enter a one-time password generated by an authentication server. This is often used with computers that don’t have a way to plug in a second authentication factor.
- Time-based One-time password (TOTP) – This type of MFA is similar to OTP, except that it generates a constantly changing code that expires after one use.
- Universal second factor (U2F) – This type of MFA uses a small device that users plug into their computers. It can be used with almost any device that hosts a login screen.
- Biometrics – This type of MFA uses fingerprints, retinal scans, facial recognition or other biological characteristics to verify a person’s identity.
Drawbacks of MFA
As you can see, MFA is a very effective way of protecting your company’s data and resources. However, organizations that rely on it heavily may experience a reduction in user productivity and satisfaction. This is because it can be cumbersome to have to remember multiple login methods, and they can encounter problems if they don’t have the right devices with them at all times.
MFA is a very useful security feature, but it should not be used in isolation. Companies also need to look at their other security features and be sure they’re not relying on just one method that can fail.
Difference between MFA and Two-Factor Authentication
MFA and two-factor authentication (2FA) are both authentication methods that require more than just a username and password to log in. There are some key differences between the two, though.
- MFA uses at least two authentication methods and 2FA uses two different types of authentication methods.
- MFA authentication methods are generally more secure than 2FA authentication methods because MFA authentication methods can be more difficult to break.
- When you’re deciding which type of authentication to use, you should consider your company’s needs. If you’re looking for a way to improve security, you may want to implement MFA. If, on the other hand, you want to ensure that no one can log in if they accidentally lose their password, then 2FA is better.
Wrapping Up
Multi-factor authentication is an effective way for companies to protect their data and resources. It is a great tool to use in addition to other security measures to ensure that users have the strongest login method possible.
There are several different types of MFA authentication methods available, and it’s important to use them in addition to other security features implemented by your organization. No single security feature is foolproof and it’s important to use multiple methods to protect your business as much as possible.
Continue Reading:
WEP vs TKIP vs CCMP: Understanding what each encryption technique offers
What is Blockchain technology?
Tag:Security



