VPN Encryption: How does it work? What types are there?
Security is of paramount concern while using the Internet and its services. Have you ever thought about how secure your data is over the Internet while working? When I am connecting to the Internet, we are taking ISP services so my ISP sees what all I am sending over this channel. Is there a way to establish a secure communication tunnel for online activity and my location? So, it is just like driving a car with shades on from one place to another without anyone seeing you.
Today we look more in detail about VPN (Virtual private network), why it is needed and how it works, what are the different types of VPNs and VPN encryption method.
What is VPN?
VPN software is established using an encrypted virtual tunnel between your system and a remote server residing on a public network such as Internet. This creates a secure connection and hides IP address, disguises your location, and protects web activity from prying eyes. A VPN uses encryption techniques to protect data privacy and security.
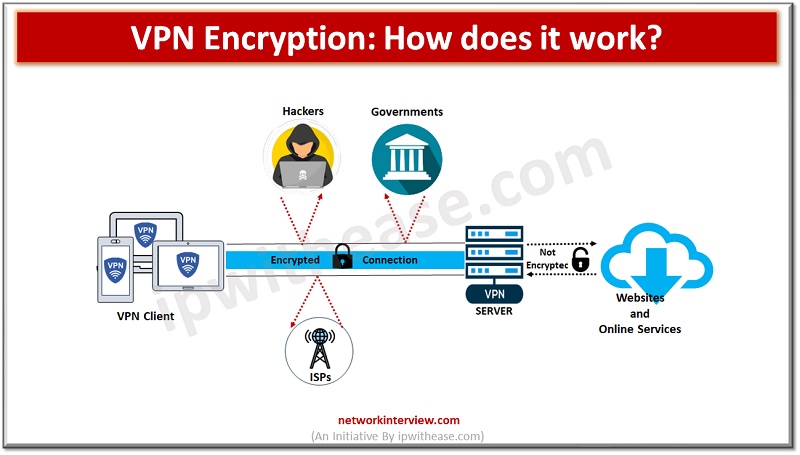
How does VPN Encryption work?
- When a website or remote application is accessed via VPN software on the system it encrypts the connection request using an encryption cipher. The connection data is sent to the chosen VPN server where it is decrypted.
- The VPN server establishes connection with the website and sends connection requests on behalf of the user. The request information is sent back to VPN server by website
- This information is encrypted by VPN server and send to user system
- VPN application decrypts the information and requested application or website responds to user request
VPN software masks the IP address from the website and hides the online activity from ISP. The website or application you access only sees a request of connection coming from a VPN server. VPN services use encryption ciphers and connection protocol for conversion of web traffic into incomprehensible code. It changes a normal plain text into a secret code to hide user identity, location and activity.
Encryption Ciphers used in VPN
An encryption cipher is just an algorithm which encrypts or decrypts data. Ciphers are usually paired with specific key length. The longer the key length the more secure the encryption technique is. For example, AES-256 is the most secure encryption algorithm. VPNs usually used two types of encryption keys – symmetric and asymmetric.
Symmetric Encryption Key
Symmetric Encryption Key provides both the parties communication using the same keys. Plain text is converted into ciphertext with the help of encryption key and unlocked or decrypted using the same key. This approach is however not considered good while sending data to another destination – a VPN server.
Asymmetric Encryption Key
Asymmetric Encryption Key uses two different encryption keys – a public key to encrypt the message and a private key to decrypt the message. The public key turns a message into a code and sends it to the owner of the private key, the only one who can decode it.
VPN Encryption Types
Let’s look more in detail about some more VPN encryption types. There are ciphers which use 64, 128 and 256 bits. The more bits a cipher has, the more secure it is.
Blowfish
Blowfish is one of the oldest forms of VPN encryption standard with 64-bit blocks. The current version of blowfish enables 128-bit encryption.
ChaCha20
ChaCha20 was published by Daniel Bernstein in 2008. It is a relatively new VPN encryption cipher. It takes 256-bit length and is also considered three times faster than AES and not yet certified by NIST unlike AES.
Camellia
Camellia is a very powerful cipher available with the OpenVPN security protocol. It supports 64-, 128- and 256-bit encryption however, it is not that extensively tested.
Advanced Encryption standard (AES)
AES is the most widely used standard for encryption in VPNs. It has both 128 bit and 256 bit support. The 256-bit encryption standard is considered most secure and it splits 256 pieces of common text into 256 blocks making it practically impossible for hackers to brute force attack to steal information. AES uses multiple rounds of transportation, substitution and mixing.
Continue Reading:
VPN vs Proxy vs Tor: What’s the Difference?
Tag:Security



