Positive Security Model vs Negative Security Model
Introduction : Positive Security Model & Negative Security Model
Achieving highest level of security and being one step ahead from the hackers has always been a significant challenge for any IT company. Security is always a hot discussion topic whenever an IT administrator contemplates on secured communication across organizational assets.
There has always been a balance to be maintained between security and convenience for the users. Setting up a right level of security can be a constant challenge. Most of us have seen that most of social sites and ones containing threads to our network are restricted, users feel that it is an inconvenience rather than something worthwhile or beneficial for business.
There are many methods by which we can provide security in the organizations, but most common solutions are Positive and Negative security models. Both these models have the same base structure, and both operate according to a set of simple rules. These rules can be Access control lists (ACL’s), Antivirus signatures etc. Both the model’s way of working is entirely different/ opposite.
Positive Security model
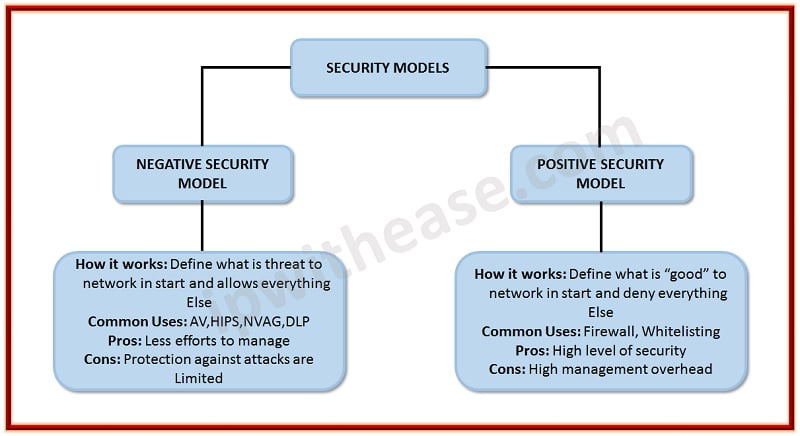
- It is also called a “whitelist model”.
- The Positive Security model starts with the approach of “block everything” in the start and what you allow is positive. This model builds upon by permitting specific, approved traffic, action and other functions. Due its positive behavior and allowing only that traffic “which is positive” this model is mostly used by operating systems and firewalls and they feel safer.
- Positive security model also helps to curb zero-day attacks.
- Allow wanted Transactions
- Everything else is Denied
- For better understanding of Positive model think of a private party where only guests are invited. The people invited by the host are allowed in, anyone else is not. This would be the positive model.
- Positive model is useful when you know what type of content you offer and you are well aware that what you need to allow HTTP or HTTPS for your webserver of FTP for your file transfer server and these content on their servers never changes so that why a positive security model is used.
- A positive security model that’s gets more functional will slowly become a negative model.
Negative security model
- It is also called a “blacklist model”.
- A negative security model Is completely opposite to the positive security model, here in negative security model “allow everything” in the beginning and then further constructed by blocking functions based on Known previous attacks and unwanted content and behaviors.
- Security increases when a rule gets added into the policy. In the start negative security model will allow the traffic and as more restrictions are added, security increases. The traffic that passes through will be matched against a “bad” filter (a blacklist) and if there is a match it will be blocked and if not, it will be permitted.
- Lock unknown attacks
- Everything else is allowed
- Block only known bad traffic
- For better understanding of negative model think you were in a public bar and everyone is be invited. As long you are not making any trouble you could enter and leave anytime, if you start causing problems you would be thrown out and banned entering the bar again. This would be a negative model.
- Negative security model is useful when you have an R&D department which introduces new services on new ports daily basics, If all those requests are denied from the start then every time new network changes are required, In such cases negative model is best to use as attacks that are known to the network will continue to be blocked and department doesn’t have to request changes all the time.
- The Negative model is most efficient for anti-virus, anti-spam and environments that’s changes a lot.
- A negative security model when more secure will gradually become positive security model
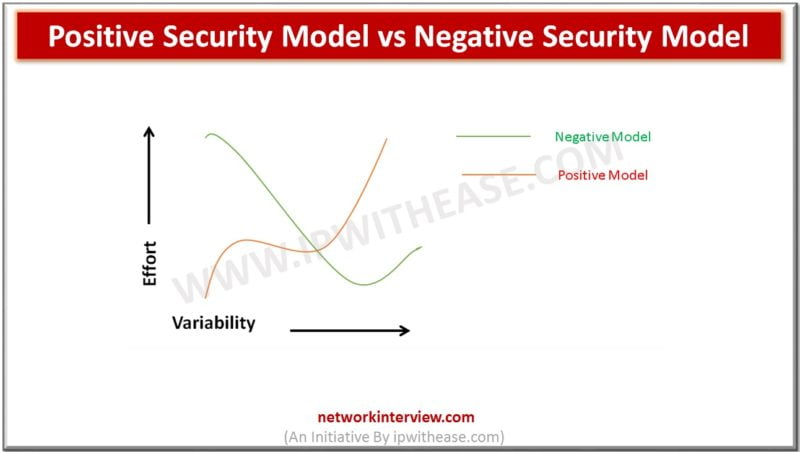
Security experts’ arguments on these models are always a debatable, some experts things that Positive Model is preferred as it started with most secure posture and gradually increases its functionality, where as some experts claim that Negative model is preferred because it starts off from the most functional posture and slowly increases its security.
Continue Reading:
Positive Security Model: Need & Usage
Tag:comparison, Security



