Palo Alto vs Checkpoint Firewall: Detailed Comparison
Attackers are constantly looking for vulnerabilities to penetrate your networks. Protection against direct, external threats require extensive network security functions deployed on the edge. Protections on the edge are provided by stateful and next generation firewalls (NGFWs) which offer features like URL and content filtering, intrusion prevention systems, protection against distributed denial of service attacks , malware detection and encryption. There are two leading platforms when it comes to cyber security Checkpoint and Palo Alto. Both offer NGFWs solutions.
Today we look more in detail about two most popular company’s firewalls, Palo Alto vs Checkpoint, their key differences, features etc.
About Palo Alto Firewall
Palo Alto is a cyber security firm based out of California founded in 2005. They offer a wide range of products with an advanced enterprise firewall product , a network security control center, advanced endpoint protection systems, a cloud-based threat analysis service, a range of analytics and cloud storage products.
They also operate a threat intelligence and security consulting team known as team 42 which comprises cyber threat researchers and security tech experts and analyse to discover and help to prevent new threats such as malicious software and new attacks of bad actors. The company had acquired Morta Security, Cyvera, CirroSecure, LightCyber, Evident.io, Secdo, RedLock, CloudGenix, Expanse, and many other cybersecurity firms.
Palo Alto firewalls are used by a number of organizations and data centres to keep networks safe and secure from advanced level of security threats. Palo Alto firewall is used to identify, control, and inspect SSL encrypted traffic and applications. It offers monitoring applications, threats and contents. It offers a real time content scanning system for protection from viruses, data leakage, online threats, spyware and application vulnerabilities.
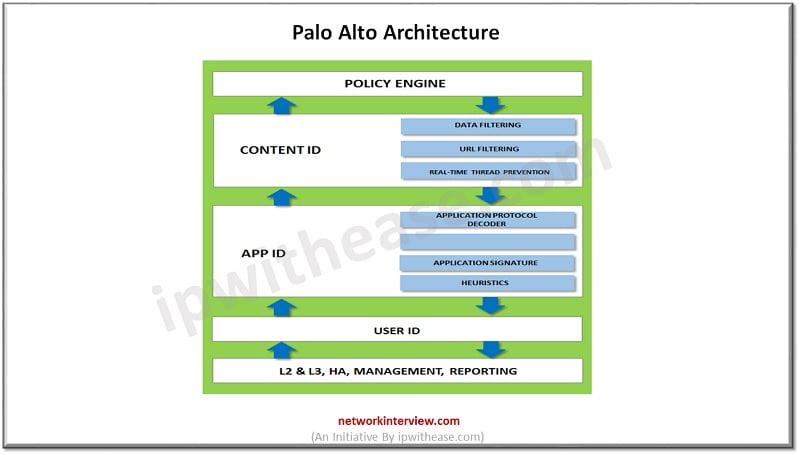
Features of Palo Alto firewall:
- Inspects all traffic including all applications, threats and content and tie that traffic to user regardless of location or device type
- Identify users in all locations irrespective of device type and OS
- Offers policy-based decryption to allow to decrypt malicious traffic leaving aside sensitive traffic encrypted
- URL filtering to provide protection against web-based threats
- DNS security to enable predictive analysis , machine learning and automation to block DNS attacks
About Checkpoint Firewall
An American – Israeli company specialized in cyber security software for varied purposes including network, endpoint, cloud, mobile, and data security. Checkpoint in 1993 came with a firewall product called Firewall-1. Checkpoint firewalls are designed to control traffic between external and internal networks.
Checkpoint firewall is part of software blade architecture which gives features like data loss prevention, application control, intrusion detection and prevention, VPN and mobile device connectivity, internet access and filtering.
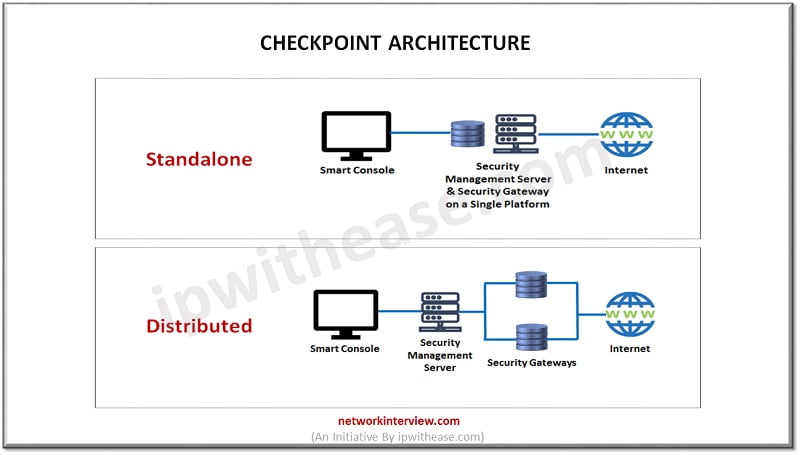
Features of Checkpoint firewall:
- Checkpoint NGFW can be installed on specific appliances or in virtual mode
- Checkpoint NGFW contains IPS software blade which provides geo protection as well as frequent , automated threat definition updates
- Offers centralized management and role-based administration
- Combines perimeter, endpoints, cloud and mobile security with application control, advanced URL filtering and data loss prevention capabilities
Comparison Table: Palo alto vs Checkpoint Firewall
Below table summarizes the differences between the two types of firewalls:
Function | Palo Alto Firewall | Checkpoint Firewall |
| Software | Uses PAN OS | Checkpoint Software blade |
| Firewall throughput | 2Gbps (App ID enabled) | 4 Gbps (Ideal testing condition – Stateful, 2.1 Gbps in real testing condition) |
| IPSec VPN throughput | 500 Mbps | 2.25 Gbps |
| IPS Throughput | 1000 Mbps | 1.44 Gbps (460 Mbps IPS real testing condition) |
| Connections per Second supported | 50 000 | 48 000 |
| Total Connections | 2 50000 | 3 200 000 |
| Unicast IPv4 Routing Protocols and static routing | BGP, RIP, OSPF static routing | RIP, OSPF, BGP, static routing, PBR |
| Firewall Mode: Router or Bridge | L1, L2, L3 | L2, L3 |
| High availability | Active /Active , Active/Passive | Cluster XL |
| Real time threat prevention | Alerts are generated post infection few minutes later. Infection alert is sent so cyber security team can take action on it. | Checkpoint prevents Patient-0 and malware is blocked before entering into network. |
| Security priority | Inspects part of traffic for threats exposing customers to risk. | Inspects 100% traffic for threats. |
| Application awareness | Limited visibility comparing only 3500 applications | Wider visibility of high-risk applications and shadow IT about 8600 applications |
| Preventive protection | Do not have capability and can scan documents with its post infection scan engine. | Provide users sanitized version of documents for safe work environment. |
| Response to vulnerabilities | 128 days on an average to fix | 6 days on an average to fix |
| clear view of threats | Don’t have capability for MITRE ATT&CK framework | MITRE ATT&CK framework to prevent cyber attacks |
| SSH and SSL usage | First firewall to decrypt, inspect and control SSL and SSH . Policy control over SSL allows personal use of applications securely (like twitter, Facebook) | No SSL decryption , inspection and control (inbound and outbound) |
| SSH controls ensure it is not being used to tunnel other applications | No way to identify intended use of SSH | |
| Security score | Cyber security rating of 13/20 | Highest score in NSS lab BPS 2019 |
| Features | SSL decryption to examine SSL concealed threats | Patient zero prevention |
| Automatic failover support | 100% traffic inspection | |
| URL filtering | Robust intrusion prevention system | |
| Change management function | ||
Download the comparison table: Palo Alto vs Checkpoint Firewall
Quick Facts !
Palo alto has global share of 18.9% in Year 2021 whereas Checkpoint market share is 9.1%
Continue Reading:
Palo Alto vs Fortinet Firewall: Detailed Comparison
Types of Firewall: Network Security
Tag:comparison, PaloAlto, Security



