Palo Alto Prisma Cloud: Comprehensive Cloud Security
Cloud native technologies are helping Development teams to build and deploy applications faster than before. However, this open architecture increases challenges to Security teams. Cloud workloads are spread-out across
- Virtual Machine
- Containers
- Serverless and many points in between security devices
They can spin up and be destroyed in a matter of a minute. This dynamic distributed hardware makes it hard to identify resources, configuration, monitoring alerts, control permissions and Identity Access. Moreover, it can ensure compliance like HIPPA, SOC2 and PCI.
What is Prisma Cloud?
Palo Alto Prisma Cloud is a comprehensive platform which simplifies security across the cloud native network.
This Cloud Native Platform brings together a comprehensive security and capabilities by delivering Full Life Cycle Security and Full Stack Protection. Prisma Cloud enhances Visibility, Secure Data, perform Threat detection and Workload Protection.
In Palo Alto Networks we know the future will run into the Cloud technology so Prisma helps us to secure the Cloud hub and secure your future technologies that way.
Prisma Cloud gives us below questions to think about Cloud Security:
- How can cloud provide security to users
- How can we protect cloud-based infrastructure?
- How can the Cloud help us to deliver better security?
To answer the above questions, we should understand what exactly Prisma Cloud is. Nowadays 8 out of 10 applications are moving to the Cloud Network. Everything is managed by a Cloud provider or DevOps team.
Prisma Cloud can identify essentially configuration errors, particular workload has got out of compliance and needs to be corrected as per Governance rule and regulation to meet those Compliance. Prisma Cloud could do lots of different things (shown in below image)
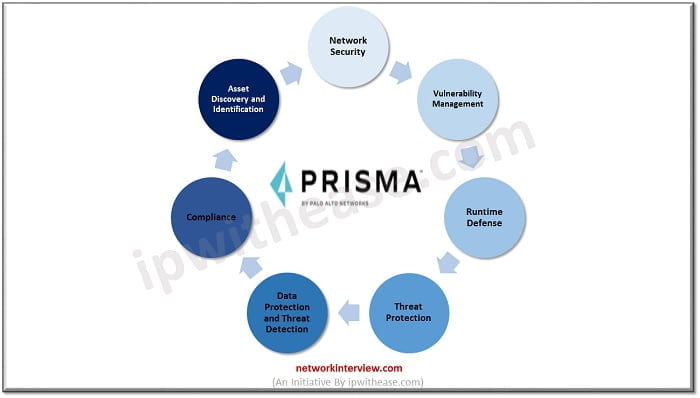
Let’s discuss some key-points of Prisma Cloud
- Supports Multiple Cloud Infrastructure Platforms: It supports deployment of multiple cloud infrastructure from using single CONSOLE. Like you can implement and monitor your network which are hosted on different cloud services Like Azure, AWS and Google.
- Policy Scan and Monitoring: Prisma can scan policies which are implemented on multiple Cloud network and compare those policies with compliance standards. It notifies the administrator if any policy violation happens.
- Anomaly Detection: Prisma cloud uses machine learning to detect the malicious behaviour of traffic. Prisma can check the traffic pattern and take necessary action accordingly. Every traffic pattern is categorised by severity of risk and relevant business impact. Furthermore, risks are aggregated based on the severity and alerts can be customised by the administrator to get the notification on the dashboard.
- Compliance Report: Prisma Cloud can generate policy violation and threat identification report which further discussed with CISA and risk management team to prohibit the risk factor and mitigate any compliance issue.
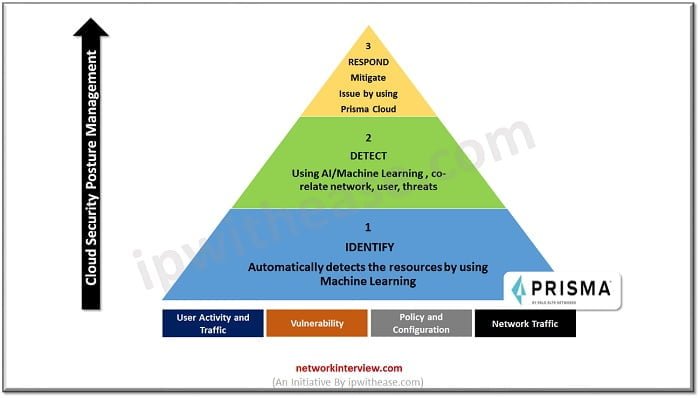
Palo Alto Prisma Cloud Dashboard Features
Prisma Cloud Dashboard provides you below features
- It provides and measure Cloud Security Capabilities
- Progress Report and Alerts
- Increase operationalization to modify the errors
1. Dashboard: It covers Asset, Alerts, Compliance, and policies
2. Inventory: Alerts and Compliance of assets which are managed by PrismaCloud
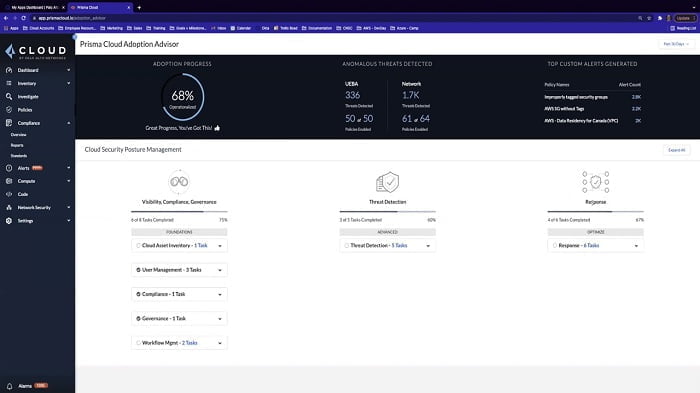
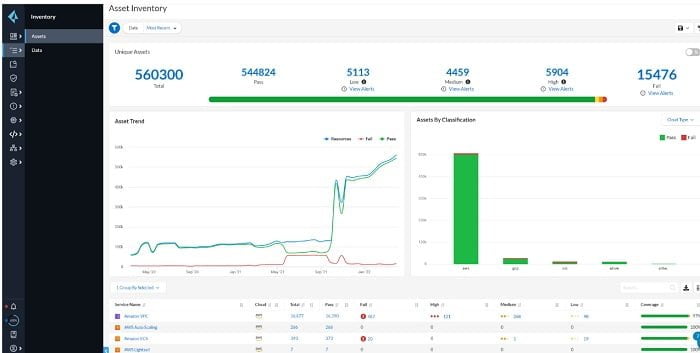
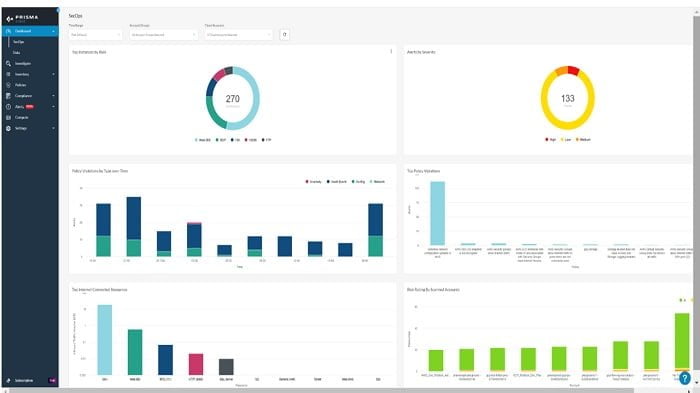
3. SecOps: It represents the performance of assets which are connected to Internet.
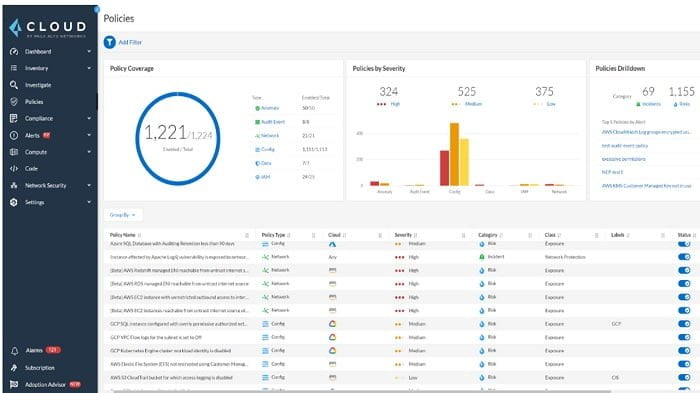
4. Prisma Cloud Policies: It provides predefined policies which can adhere to PIC-DSS, HIPPA, SOC2 and Governance. You can customise Prisma Policies according to network requirements.
5. Threat Detection: It can detect Vulnerabilities in CSPM (Cloud Security Posture Management) and CWPP (Cloud Workload Protection Platform)
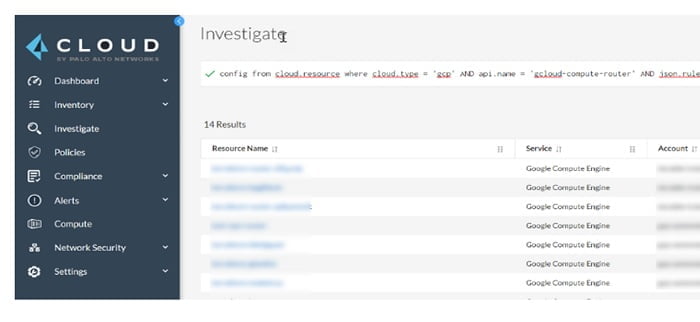
6. Investigation: Investigate logs and error in Prisma Cloud
Compliance Dashboard: It shows Compliance chart and standards. We can customise the report and charts in this Dashboard.
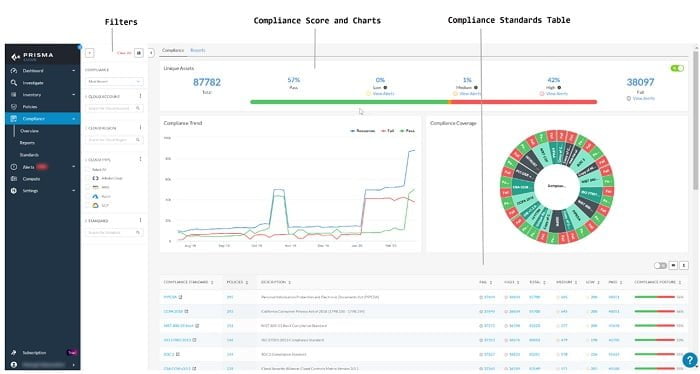
Prisma Cloud Network Security: It provides network security logs that are exposed to public cloud network.
Prisma Cloud Onboarding
To add your account to Prisma Cloud first you need to add your Cloud Vendor (AWS, Azure, Google) to Prisma Cloud. Please find the steps below
1. Login into your Prisma Cloud Account
2. Go to Setting
3. Select New Cloud Account
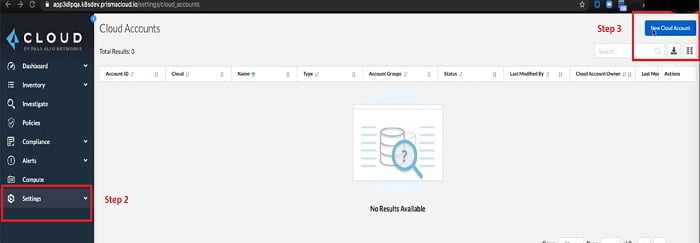
4. It will prompt multiple Cloud Vendors in the list, select your Cloud Service Provider. Here I am selecting AWS.

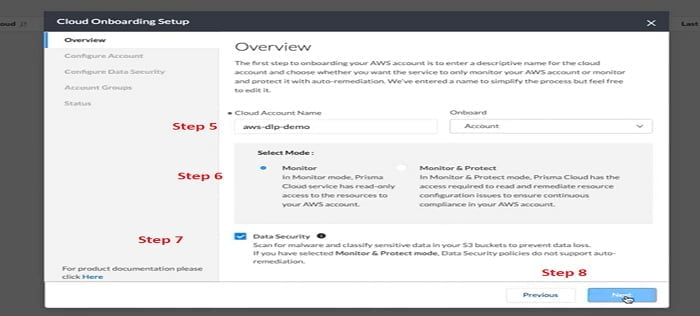
5. Name your AWS Cloud name
6. Select Mode of Cloud i.e, Monitor (Default Service Account with Read-Only Access) OR Monitor & Protect Account (Prisma can read the configuration and apply mitigation as to avoid Compliance Issue)
7. Select Data Security option which scan malware
8. Select Next
9. From the Configure Account step we can select Create Stack, we will use CloudFormation template to create the resources that are required on AWS account. So, the Prisma Cloud should have the necessary APIs and the Cloud Trail SNS data
10. Select Cloud Stack
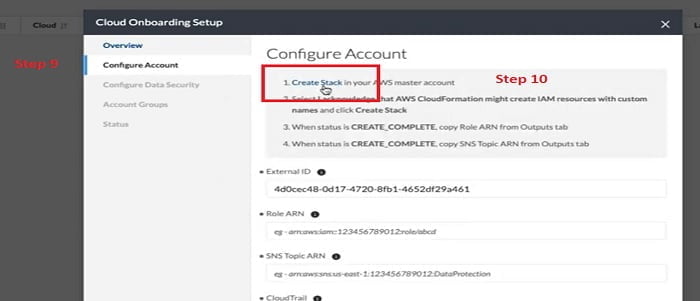
Once we select Create Stack it will navigate to the Console of the AWS Account, we can monitor the Stack creation process.
You can mention Stack Name, Prisma Cloud Role Name with DLP. After verifying the configuration, you can select Create Stack.
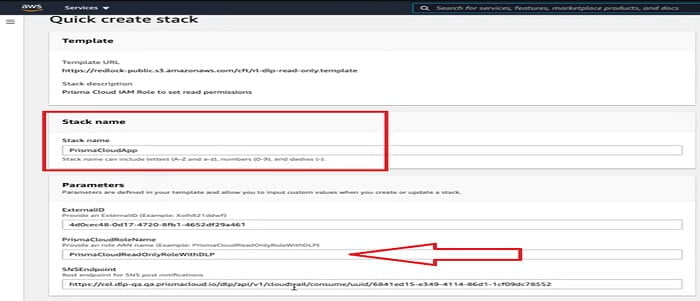
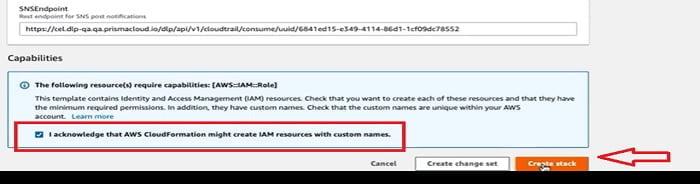
Now a new Stack has been created. Make sure there is no errors have occurred.
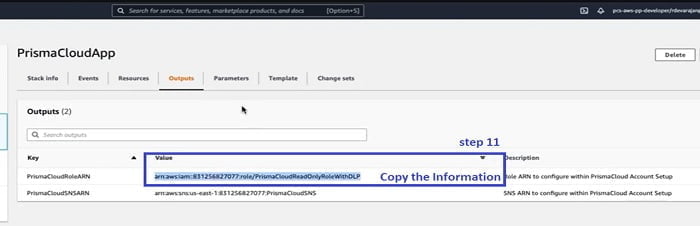
If I click to the Output TAB, two new resources are created
- The RoleARN: It is required to access your S3 buckets
- The SNSARN: It is required for Forward scan event notifications
Now we need to go to the Prisma Cloud window (step 9) and add those values in Role ARN tab and SNS topic ARN tab.
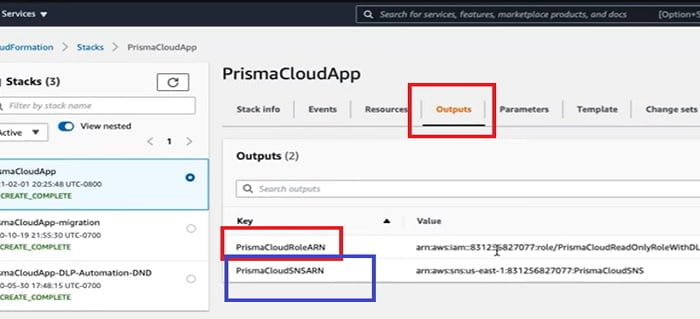
11. We can copy RoleARN from AWS Account and paste in Prisma Cloud Onboarding setup.
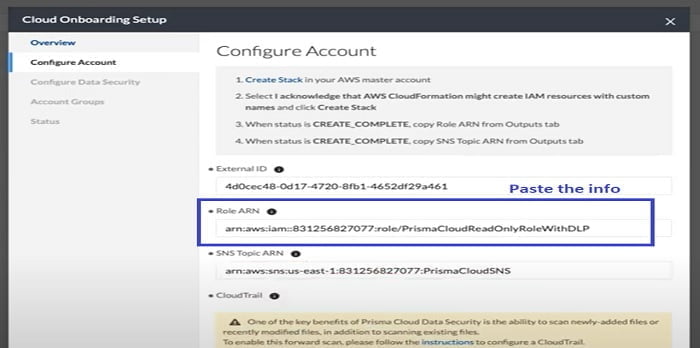
12. Similarly, we can copy SNSARN information and paste it to SNS Topic ARN.
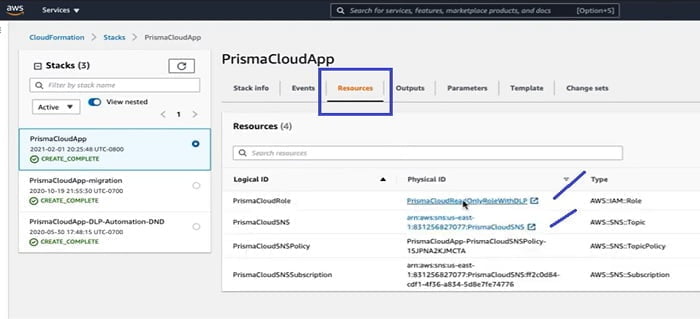
Now go to Resources TAB and check if the RoleARN and SNSARN are created there.
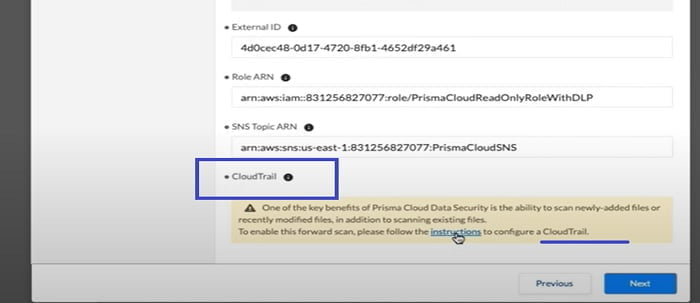
Now the next step is to create Cloud Trail from the Setup tab. We configure Cloud Trail to monitor right events and SNS Topics so that Prisma Cloud Data Security Module when new objects are added to storage and forward scanning is triggered to pick up any new or modified files.
As shown in the below link in the dialogue box, it takes you to Tech Docs, online documentation where steps are mentioned to follow the entire On-boarding procedure for AWS/admin guide.
13. Let’s go back to the AWS console and select Cloud Trail in the option. Now we are navigated to Cloud Trail service page.
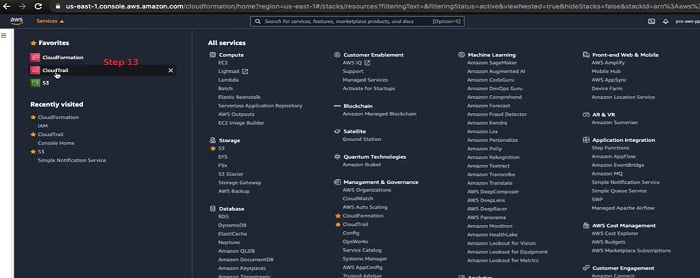
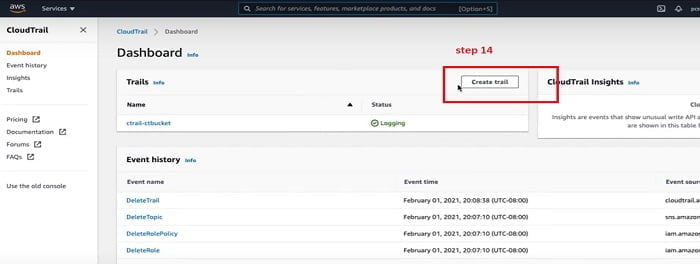
14. We get started to Create Cloud Trail.
15. Give name to the CloudTrail, we have mentioned ctrail-demo, select other options for S3 and Trail log folder.
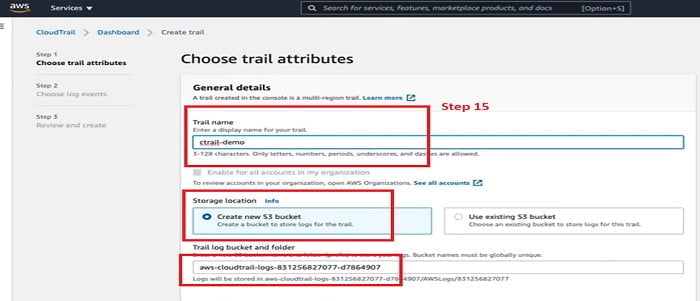
16. Please refer all the steps mentioned in below image and when your are finished, Click Next.
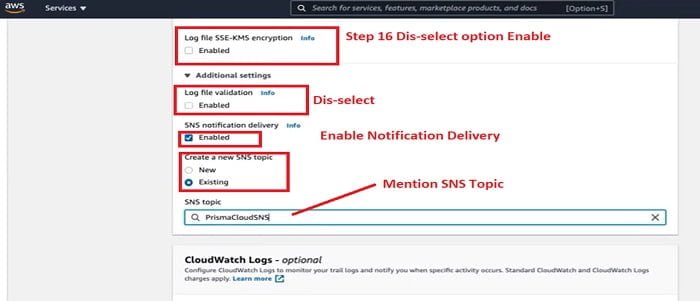
17. In the Choose Log Events sections select event types, dis-select API read mode.
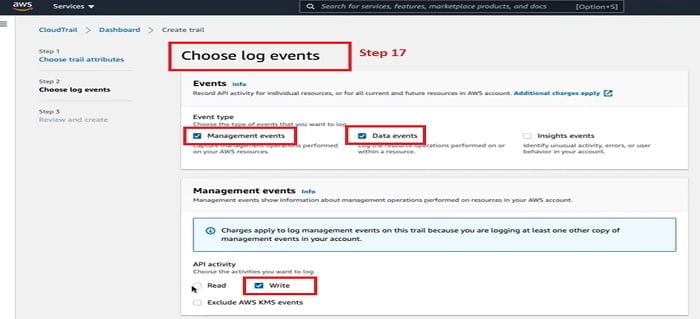
18. In the Data event follow below image and select the mentioned, red-marked options. Click Next
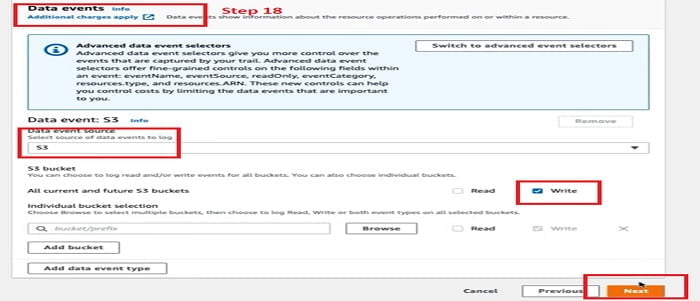
19. It further moved to the review page. Review your configuration and click Create Trail TAB.
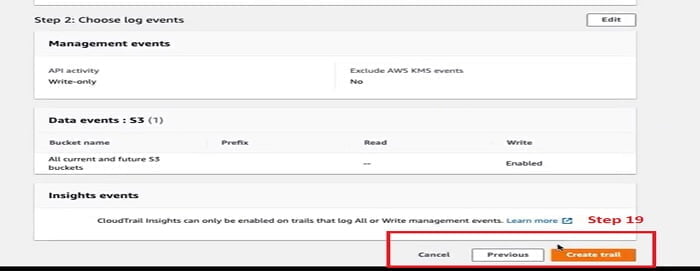
Now we have seen from the table that Trail has been created and logging successfully.
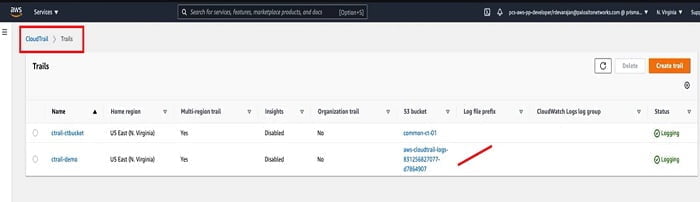
20. Let’s move forward to the next step once CloudTrail configuration is completed.
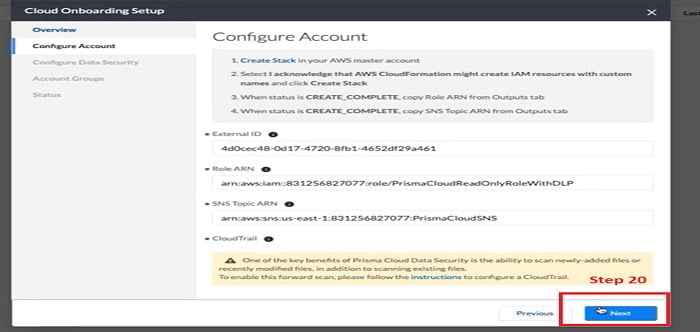
21. Now we will configure Data Security. You have all the S3 bucket options to select for account. OR you can customise and select a specific bucket list as per your requirement.
Select option Forward OR Forward and Backward option
Forward option: Forward scan is enabled by default and cannot be disabled
Forward & backward scan: when you select backward scan, Prisma Cloud starts scanning all existing files in the bucket in a batch operation.
Depending on the files in the bucket, backward portions may cost more for organisation.
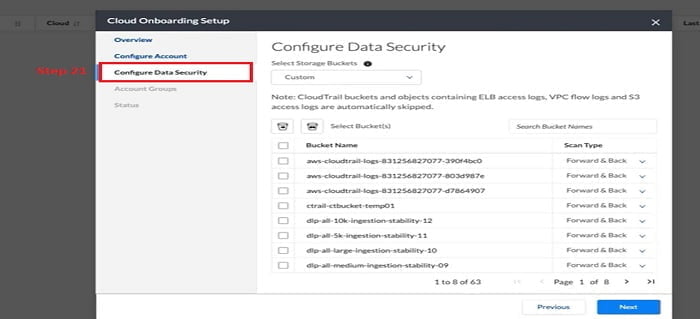
22. Select Default Account from the option and click next.
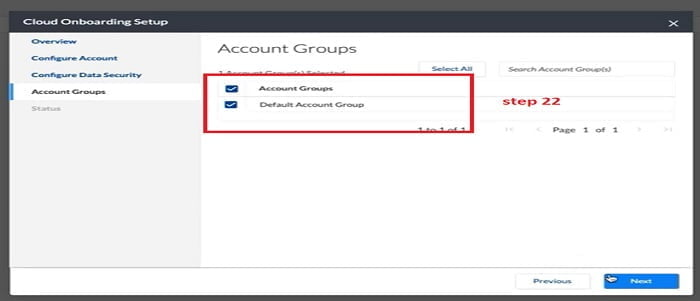
23. Now we can check the status of services which we have configured for the Prisma Cloud account. It monitors the Prisma Cloud status with an AWS account.
For Data Security status of CloudTrail and Storage MUST be healthy. Once status is Green you can proceed for the Done option.
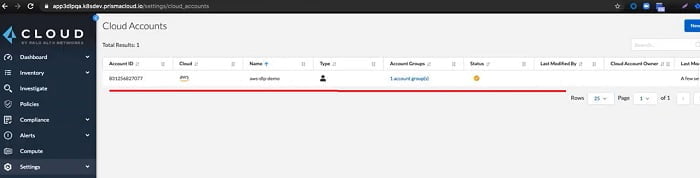
Your account on Prisma Cloud is ready.
Continue Reading:
Palo Alto Prisma SD WAN: CloudGenix SD WAN



