Micro segmentation vs Network Segmentation
Micro segmentation vs Network Segmentation
Over many years, Perimeter security has been considered the key to presenting a robust and secured network ecosystem . This was considered a suitable methodology when the network attacks were not so advanced and North-South traffic was the major traffic type. However, with advancement in technology, new attack types are knocking the doors. Infact, substantial growth in East-West traffic communication across workloads has diverted the attention towards rollout of what we call microsegmentation. In this article we will brief through Network Segmentation and Micro-segmentation and what are their differences.
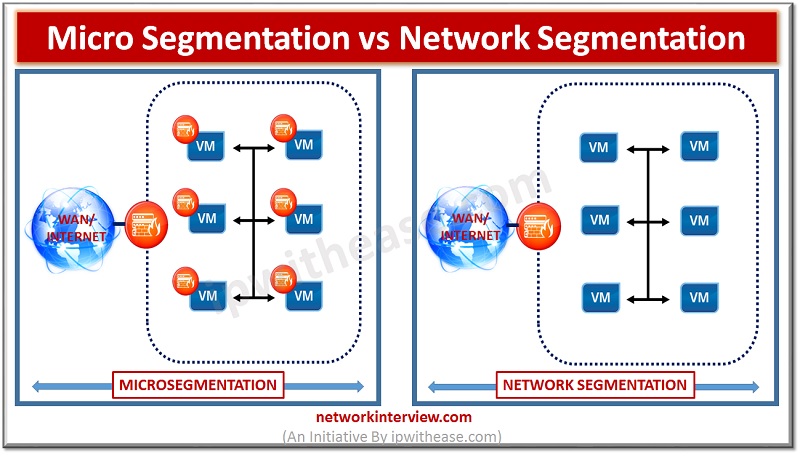
To start with, concept of Micro-segmentation logically divides the Data Centre into distinct security segments upto individual workload level. The granularity level at which micro-segmentation works is upto VMs and individual hosts unlike Network Segmentation. Network segmentation creates sub-networks (using VLANs, Subnets and Security Zones) within the overall network to prevent attackers from moving inside the perimeter and attack the production workload.
Related – Microsegmentation vs Zero Trust
Microsegmentation works on the notion that by controlling this traffic, you can minimize the risk of security threats and create a zero-trust security model. It requires centralized management and can be applied to individual machines providing a more secure environment without the additional overhead of host-specific configuration. If the centralized management is not used , it would become cumbersome (rather nightmare) to attend the security policies across various VMs or hosts. When it comes to network segmentation, it is not mandatory to perform central management via orchestrators. Infact, Policies in former are pretty granular while in latter, policies are network/ Zone or segment level. Further, policies and permissions for microsementation are based on resource identity
Below are some of key benefits we can achieve via microsegmentation –
- Enforce granular tier-level segmentation within the same application group. Hence greater security
- Enforce policy upto Layer 7
- Critical applications will keep safe, even in the case of a breach at perimeter
On the other hand, Network segmentation provides below benefits –
- Enforce security at perimeter to protect against entry of attacks.
- Simpler to implement than Micro-segmentation
Another thing to note here is that microsegmentation requires highly Skilled resources who understand application level visibility to employ Microsegmentation. While medium level of proficiency is required to deploy network based segmentation solution.
Comparison Table: Micro segmentation vs Network Segmentation
Below table enumerates difference between Microsegmentation and Network Segmentation –
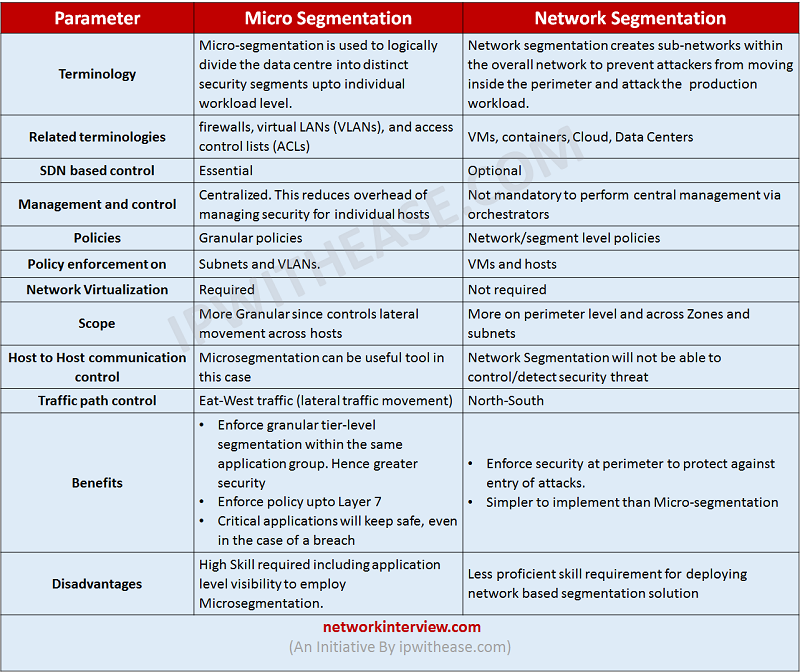
Parameter | Micro Segmentation | Network Segmentation |
| Terminology | Micro-segmentation is used to logically divide the data centre into distinct security segments upto individual workload level. | Network segmentation creates sub-networks within the overall network to prevent attackers from moving inside the perimeter and attack the production workload. |
| Related terminologies | firewalls, virtual LANs (VLANs), and access control lists (ACLs) | VMs, containers, Cloud, Data Centers |
| SDN based control | Essential | Optional |
| Management and control | Centralized. This reduces overhead of managing security for individual hosts | Not mandatory to perform central management via orchestrators |
| Policies | Granular policies | Network/segment level policies |
| Policy enforcement on | Subnets and VLANs. | VMs and hosts |
| Network Virtualization | Required | Not required |
| Scope | More Granular since controls lateral movement across hosts | More on perimeter level and across Zones and subnets |
| Host to Host communication control | Microsegmentation can be useful tool in this case | Network Segmentation will not be able to control/detect security threat |
| Traffic path control | Eat-West traffic (lateral traffic movement) | North-South |
| Benefits | •Enforce granular tier-level segmentation within the same application group. Hence greater security •Enforce policy upto Layer 7 •Critical applications will keep safe, even in the case of a breach | •Enforce security at perimeter to protect against entry of attacks. •Simpler to implement than Micro-segmentation |
| Disadvantages | High Skill required including application level visibility to employ Microsegmentation. | Less proficient skill requirement for deploying network based segmentation solution |
Download the Comparison table.
Tag:comparison, Security