MD5 vs CRC – Detailed Comparison
Difference Between MD5 and CRC
MD5 and CRC are 2 of most commonly used hashing algorithms, infact while comparing files and including other use cases. In this article. We will understand both the concepts of hashing algorithm and how one scores over the other.
Errors and Error detection
When bits are transmitted over the physical media, they get corrupted due to interference and network problems. The corrupted bits changes from 0 to 1 or 1 to 0, data being received by the receiver and are called errors.
Error detection techniques are responsible for checking any error has occurred or not in the frame that has been transmitted.
In this error detection technique the sender needs to send some additional bits along with the data bits. The receiver will check based upon the additional redundant bits. If it finds data is identical, it removes the redundant bits and pass the message to the upper layers.
There are three main categories for detecting errors:
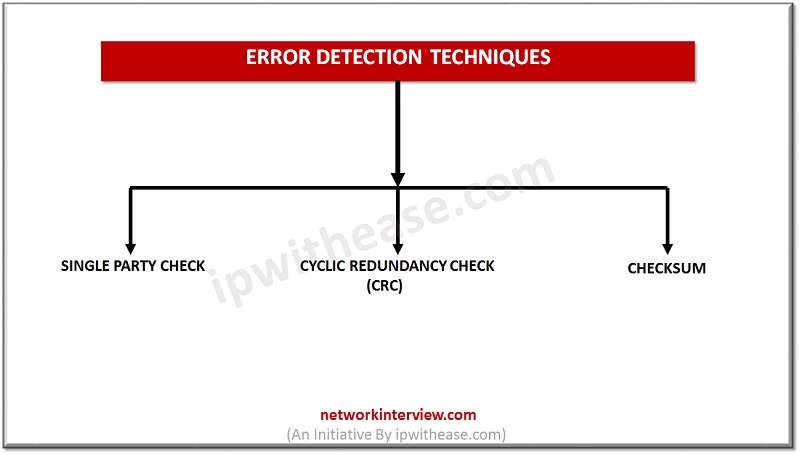
Cyclic redundancy check (CRC)
- CRC is based on binary division.
- In CRC, a sequence of redundant bits, known as cyclic redundancy check bits, are appended to the tip information of knowledge of information unit so the ensuing data unit becomes precisely dividable.
- At the destination, the incoming information unit is split by identical variety. In this step there is no remainder, the data unit is assumed to be correct and therefore accepted.
- A remainder indicates that the info unit has been broken in transit and so should be rejected.
Steps Involved
Error detection victimization CRC technique involves below enlisted steps-
Step-01: Calculation of CRC at Sender Side
At sender side,
- A string of n 0’s is appended to the info unit to be transmitted.
- Here, n is one but the amount of bits in CRC generator.
- After division, the rest therefore obtained is termed as CRC.
- It may be noted that CRC additionally consists of n bits.
Step-02: Appending CRC to Data Unit
At sender side,
- The CRC is obtained once the binary division.
- The string of n 0’s appended to the info unit earlier is replaced by the CRC remainder.
Step-03: Transmission to Receiver
The fresh fashioned code word (Original information CRC) is transmitted to the receiver.
Step-04: Checking at Receiver Side
At receiver side,
- The received code word is divided with identical CRC generator.
- After division remainder will check.
The following two cases are possible-
If remainder is zero meaning no error receiver accepts the info. If remainder is none zero receiver reject information it suggests that some error occurred.
Introduction to MD5 Algorithm
The MD5 hash function was originally designed for use as a secure cryptographic hash algorithm for authenticating digital signature, data integrity and detect unintentional data corruption.
MD5 message digest algorithmic program is the fifth version of the Message Digest algorithmic program, that developed by Ron Rivest to provide 128 bit message digest. MD5 produces the message that is digest through 5 steps i.e. padding, append length and divide input into 512 bit blocks.
How does the MD5 Algorithm works?
MD5 produces output of 128-bit hash. This secret writing of input of any size into hash values undergoes five steps and every step has it’s a predefined task.
Step1: Append Padding Bits
- Padding suggests that adding additional bits to the initial message. Therefore in MD5 original message is cushiony such its length in bits is congruent to 448 modulo 512.
Overall bits are sixty four less being a multiple of 512 bits length. Padding is finished, though the length of the initial message is already congruent to 448 modulo 512.
- Padding is done even if the length of the original message is already congruent to 448 modulo 512. In padding bits, the only first bit is 1 and the rest of the bits are 0.
Step 2: Append Length
After padding, 64 bits are inserted at the end which is used to record the length of the original input. Modulo 2^64.
Step 3: Initialize MD buffer
A four-word buffer (A, B, C, D) is employed to reason the values for the message digest.
Here A, B, C, D are 32- bit registers and are initialized within the following means.
Step 4: Processing message in 16-word block
MD5 uses the auxiliary functions that take the input as 3 32-bit variety and produces a 32-bit output and these functions use logical operators like OR, XOR, NOR.
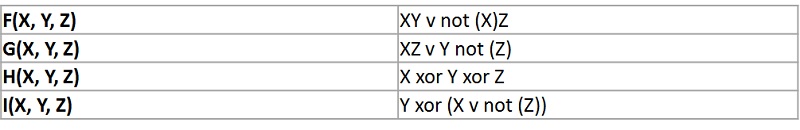
The content of 4 buffers are mixed with the input auxiliary buffer and sixteen rounds are performed victimization sixteen basic operations.
Output
Buffer A, B, C, D contains the MD5 output beginning with lower bit A and ending with higher bit D.
Example
Input: This is an article about the cryptography algorithm
Output: e4d909c290dfb1ca068ffaddd22cbb0
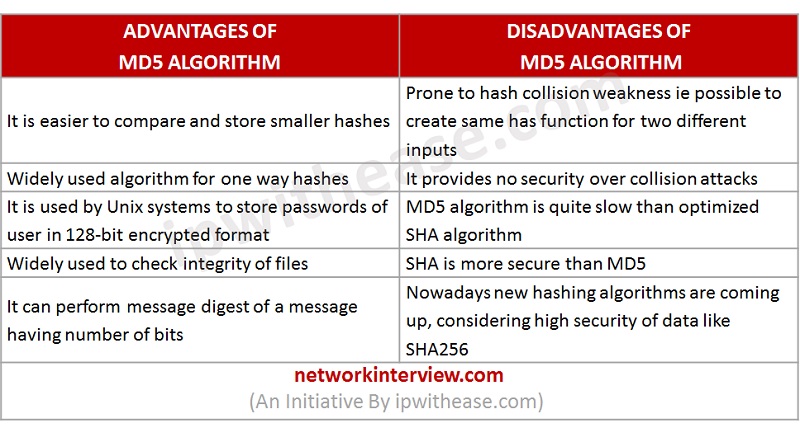
Key Highlights CRC Vs MD5
- It performs at data link layer and transmission layer of OSI model. It checks sequence of redundant bits at sender and receiver side. If remainder is zero then no error if non-zero then some error.
- MD5 is 128 bit hash algorithm to generate password. It is easy to generate and compare hash value.
Tag:comparison, Security