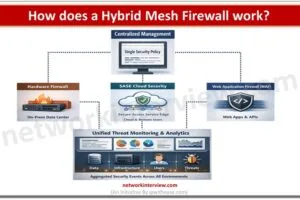
Intro to Cisco FTD Firewall (Firepower Threat Defense)
In the evaluation of next generation firewalls (NGFW), the next leap made by Cisco FTD is (Unified Firepower threat defence) software which includes not just NGFW but also Next generation Intrusion prevention systems (NGIP), Advanced Malware protection (AMP) and many more new features all unified in a single software image. One image is what Cisco targeted for its Next generation firewalls with Cisco FTD.
In today’s blog we will cover in detail about Cisco Unified Firepower threat defence software, its features, use cases, architecture.
Cisco FTD (Firepower Threat Defense)
Cisco acquired Sourcefire in the year 2013, they are the top leader in the cybersecurity industry with Intrusion detection systems, intrusion prevention systems, and Next generation firewalls. The Sourcefire is based on Snort which is an open-source network intrusion detection and prevention system. Cisco, after acquiring Sourcefire, leveraged its technology and released Firepower 2100 series, 4100 series and 9300 series.
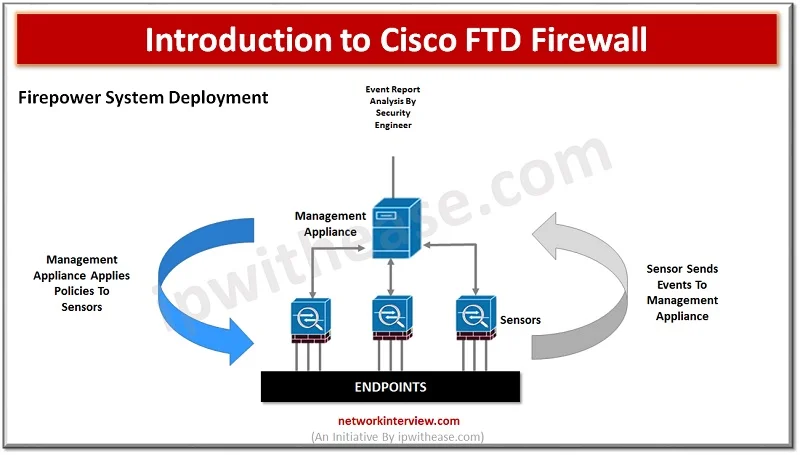
A Firepower system deployment comprises two appliance types:
- a management appliance
- a sensor appliance
Sensor inspects network traffic and sends any events to management appliance. Management appliance manages all kinds of security policies for the sensor.
In Firepower FTD Cisco converges all Sourcefire features such as ASA firewall, Intrusion prevention and detection system, Malware protection into a single unified storage image. The Firepower system gives many security features as described below:
- Firepower core software – is the core part of software including the snort engine for Intrusion detection and prevention , web server for GUI, database for event storage, hardware firmware. Core software image would depend on the hardware platform it is installed on.
- Snort / Sourcefire rules – Snort engine uses a special rule set to detect and prevent intrusion attempts. Each rule has a set of conditions based on which action is taken on the data packet.
- Vulnerability database (VD) – stores vulnerability information and fingerprints of several applications, services, and operating systems. Fingerprint is used to discover application, service and OS and correlate application and network discovery data with vulnerability information in database.
- Geolocation database (GeoDB) – stores geographical information and its associated IP addresses. You can view the name and flag of the country that originated the intrusion attempt to take quick action.
- URL filtering database – websites can be categorized on the basis of their targeted audience and purpose. System enables control to access a certain type of website based on its reputation level.
- Security intelligence feed (SIF) – Talos component shares intelligence data through security intelligence feed
- Local malware detection – FTD can detect viruses in files. FTD uses the CalmAV engine for local analysis of files.
- Integration – Firepower systems can be integrated with various technologies such as Cisco identity services engine (ISE), Microsoft Windows Active directory server, Event Streamer (eStreamer) , and syslog server.
Cisco Firepower Features:
- Stateful firewall inspection capabilities
- Static and dynamic routing
- Next generation intrusion prevention systems
- URL filtering
- Application visibility and control
- Advanced malware protection
- SSL decryption
- Captive portal (Guest web portal)
- Multi domain management is supported
- Rate limit can be implemented
- Site to site VPN between FTD appliances and FTD to ASA
- Multicast routing shared NAT
Cisco FTD Installation
Use a valid CCO account to download software.
Visit: Downloads Home>Products>Security>Firewalls>Next-Generation Firewalls (NGFW)>ASA 5500-X with Firepower series and choose Firepower Threat defense software.
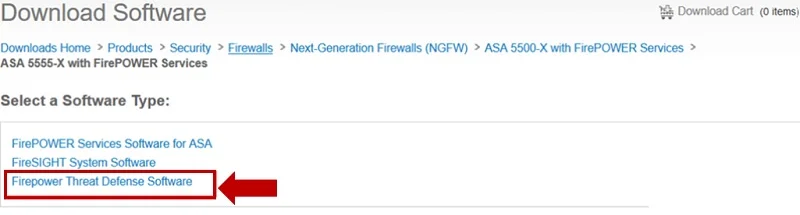
Now, Select and download the latest boot image and system version.
Now reboot ASA appliance and during the boot process press Break or Esc to interrupt boot.
Boot interrupted.
Management0/0
Link is DOWN
MAC Address: 00f6.63da.e807
Use? for help.
rommon #1>
Once the boot is interrupted, we need to configure necessary parameters on ASA firewall to download the Cisco Firepower Threat Defense boot image. Connect to ASA console port and check that Cisco ASA is running rommon version v.1.1.8 or greater. If the version is lower than upgrade is required.
Issue tftpdnld command on rommon console to download boot image of the ASA firewall.
rommon #7> tftpdnld
Post successful download of firewall and booting with boot image it is now ready to accept system image.
FirewallCK-boot> setup
Welcome to Cisco FTD Setup
[hit Ctrl-C to abort]
Default values are inside []
Provide input for below
Enter a hostname [FirewallCK]: FirewallCK FTD
Do you want to configure an IPv4 address on the management interface? (y/n) [Y]: y
Do you want to enable DHCP for IPv4 address assignment on the management interface? (y/n) [Y]: n
Enter an IPv4 address: 11.30.1.129
Enter the netmask: 255.255.255.0
Enter the gateway: 11.30.4.150
Do you want to configure a static IPv6 address on the management interface? (y/n) [N]: n
Stateless autoconfiguration will be enabled for IPv6 addresses
Enter the primary DNS server IP address: 11.30.4.150
Do you want to configure a Secondary DNS Server? (y/n) [n]: n
Do you want to configure Local Domain Name? (y/n) [n]: y
Enter the local domain name: firewall.ck
Do you want to configure Search domains? (y/n) [n]: n
Do you want to enable the NTP service? [Y]: n
Please review the final configuration and with this initial configuration complete and it is ready to download FTD system image and begin FTD installation.
Continue Reading:
Types of Firewall: Network Security